Chapter 6. Router Security
Be the change you wish to see in the world.
—Mahatma Gandhi
Everyone is getting online as rapidly as possible in whatever way they can; if you are reading this book, you are probably the person your family calls to “fix” the Internet. Perhaps the best T-shirt I never bought was the “No, I will not fix your computer” from ThinkGeek.com, as shown in Figure 6-1.
Figure 6-1. No, I Will Not Fix Your Computer

The point is that most people do not understand that the Internet operates because of routers. They think that individuals have more control and security than they do because their PC connects to the Internet. Of course, this is not the case—there are no guarantees on the Internet, which is a wild and fast place. Everyone tries to do a good job, but unexpected events occur.
As people seek to leverage the unparalleled possibilities of Internet communications, they need secure solutions that
• Protect internal networks from intrusion
• Provide secure Internet and remote access connections
• Enable network commerce through the World Wide Web
Today, the Internet is the focus of powerful new technologies that dramatically enhance communications with remote customers, suppliers, partners, and employees. Users must be confident that network transactions—especially over public networks—are secured.
Cisco IOS Software runs on over 80 percent of Internet backbone routers and an equally high percentage of corporate network routers that connect to the Internet. Cisco IOS Software provides complete network services and enables networked applications. Cisco IOS security services offer many options for building custom security solutions for Internet, intranet, and remote access networks to provide end-to-end network security.
A critical part of an overall security solution is a network firewall, which monitors traffic crossing network perimeters and imposes restrictions according to security policy. As discussed in Chapter 5, “Firewalls,” firewalls are not routers, and they are used to connect the Internet to your corporate network. Routers used to connect to the Internet are known as edge routers; they form the outermost perimeter of your network.
Perimeter routers are found at any network boundary, such as between private networks, intranets, extranets, or the Internet. Firewalls most commonly separate internal (private) and external (public) networks.
The Cisco IOS Firewall Feature Set, available as a Cisco IOS Software option, provides an advanced security solution that protects networks from security violations. This integrated router security solution provides one element in a system of security solutions available from Cisco Systems.
This chapter discusses the use of routers, the purpose of a firewall IOS, and what it is. Where within your network will you be applying this type of protection? This chapter explains the use and placement of this type of security technology and its advantages and disadvantages.
A firewall is a security device that sits on the edge of your Internet connection and functions as an Internet Border Security Officer by constantly looking at all the traffic entering and exiting your connection, looking and waiting for traffic to block or reject in response to an established rule. The firewall plays the role of law and protection in a lawless global web, ever vigilant in its mission to protect the internal network resources that connect to it.
In contrast, the edge router provides connectivity to the Internet for businesses, and most people view it as a necessary device that provides them with connectivity. Having a router, however, means that it will handle (route) every single packet that wants to enter or leave the network. It is the role of the firewall to determine what is permitted or denied. However, if you have a router as the first layer into your network, shouldn’t you use that router as part of your layered security strategy?
Of course, you should. You have paid for the router, spent time configuring it, and blindly trusting that it is inherently secure is a mistake. Even if your company spent tens of thousands of dollars on other security solutions, the router handling everything might not have had its configuration hardened to protect it and your network. The router is essentially in the default out of the box (OOB) condition. Consider that an attacker gained control of your router. Because that router literally sees every single IP packet, what might the attacker learn? What might he then be able to do? The router is a smart network device that holds a key position and handles crucial information. Network security is often thought of in terms of servers, firewalls, VPNs, and how to protect IT resources. This chapter covers how to protect the router and then expand its capabilities to further protect your network with an additional layer of security through the use of the Cisco Firewall Feature Set IOS.
By securing the router and thus increasing your network’s security, you can accomplish the following:
• Prevent routers from unintentionally leaking information about your network to attackers
• Prevent the disabling of your routers (and thus your network) by attackers or accidental misconfiguration
• Prevent the use of your routers as platforms to launch an internal attack or to be used to attack others
• Reduce the load on the firewall and internal network as bad packets and thus stop associated attacks at the edge of your network
• Quickly activate an additional layer of security to further protect your network
These accomplishments revolve around the security and functionality of the router and your network. As such, they are concerned with the big picture; however, the firewall feature set available for routers has additional security benefits.
Not everyone wants to spend the money, time, effort, or expertise needed to correctly configure the firewall functionality on a router. The reality is that many companies allow the firewall to be the stateful packet inspection device. However, everyone should use a router as a layer in the defense of his network. The discussion and debate should center not on “if” but “how” the router should be configured. Here are three ways to configure your edge router:
• Router with basic configuration—Get the router, put a basic configuration in it, connect it to your LAN and the Internet, and you are finished. There is nothing fancy here, and absolutely no security or value to your network!
• Router as a choke point—As discussed in Chapter 3, “Overview of Security Technologies,” all routers come with the capability to filter traffic based on access control lists (ACLs). Access lists can be developed to filter traffic based on type and destination at the router turning it into a choke; if the traffic is not permitted, it is denied! This is the minimum that should be accomplished!
• Router as a packet inspector—To have the router perform more advanced filtering, this type of router is deployed with the firewall feature set on it. This router is the best of the three, and it is also the most difficult to achieve. Anything in life that is worth having is never free—you must work for it!
This chapter does not cover what a router secures or protects with a basic configuration because it does nothing to help increase your network’s security. Rather, this chapter focuses on how a router functions as a choke point through the use of static access lists and as a screening device through more advanced access lists.
Edge Router as a Choke Point
A choke point came to the world of networking courtesy of the Internet’s military heritage. A choke point refers to a single point in which everything will try and either enter or leave your network. In this application of the term choke point, it is a router. The edge router is the single point from which the entire Internet gains access to your network. The router then is also a single point of failure, but that is an entirely separate discussion.
Edge routers that operate as choke points increase your network’s security by restricting the flow of data between your network and the Internet (or another network).
A successful network security implementation is based on understanding what happening in the network. This knowledge forms the basis of what should be used to filter network activity so inappropriate activity can be identified. Network activity should be restricted to permit acceptable service only. Chokes provide a great way of implementing a coarse level of control, and monitoring that can be fine-tuned using intelligent filters, such as proxy and stateful firewalls.
The value of edge routers being configured as choke points is that they can prevent access to specific devices and applications in a performance-friendly way. This increase in security is typically provided through the use of standard and extended access control lists that can address traffic concerns at Layers 2, 3, and 4 of the OSI reference model. The fact that their performance does not normally suffer results from the fact the router must read the contents of the IP packet anyway to make a decision on where to forward the packet. It does not take much more work to toss out the packet or permit it into the network.
The use of ACLs gives network engineers a high degree of control and filtering capabilities over packets traversing the router. Figure 6-2 demonstrates a common example of the rules and placement of a choke router. On a side note, can you figure out what network device is missing from this figure?
Figure 6-2. Edge Router as a Choke Point

This edge router that is acting as a choke point into the corporate network permits only the following traffic into the corporate LAN:
• Inbound mail delivery to the e-mail (SMTP) server at IP address 64.24.14.61
• FTP file transfers to the FTP server at IP address 64.24.14.60
• DNS (zone transfers via UDP and name lookup requests via TCP) to the DNS server at IP address 64.24.14.61
• TCP and UDP traffic above port 1023 to allow outbound connections from the private network to function
• Only specific types of ICMP
• All other traffic is denied access to the edge router
As a user on the corporate LAN, the edge router permits only you to establish connections out to the Internet as follows:
• SSH [port 22]
• DNS [port 53]
• FTP [ports 20 and 21]
• HTTP [port 80]
The use of a choke point router to limit access (both in and out) for known services (below port number 1023) leaves the network largely exposed. Because the majority of today’s applications utilize ports above 1023 and not all IP stack and application implementations follow the 49152 through 65535 dynamic/private port guidelines, filtering above 1023 can affect the operation of applications that you want to function and, therefore, cannot deny this port range.
Did you discern what was missing in this figure? If you guessed a firewall performing stateful packet inspection (SPI) and network address translation (NAT), you were correct and are making progress toward becoming a security guru!
Limitations of Choke Routers
Choke routers are useful and can protect your network as previously demonstrated; however, they are only part of the solution and are likely to stop only a script kiddie. An experienced attacker or one who has already read this book understands that the network is not completely protected. Some of the limitations of choke routers are as follows:
• Choke routers running regular IOS cannot look at the higher layers of the OSI reference model (Layers 5–7). However, use of enhanced IOS facilitates the use of Network Based Application Recognition (NBAR), which allows a router to detect and block many of the more common worms. You can find a useful article regarding this point at: http://certcities.com/editorial/columns/story.asp?EditorialsID=76.
• Choke routers do not adequately address protocol and application security concerns; you would have no idea if your connections were being spoofed.
• Choke routers do not have the ability to perform SPI without potentially serious upgrades.
While choke routers do not address the preceding concerns, they are quite valuable for implementing broad network and service access policies (that is, what users on the Internet can access).
Caution
![]()
Creating static ACLs require some thought and a lot of testing. A poorly written ACL can have adverse effects on the network in terms of performance and service availability. A strongly recommended practice is to write the ACL out on paper first to ensure that you have it designed to accomplish your filtering goals. Also, do not ask for help on your ACLs until you have repeated the mantra—there is an implicit deny all at the end of every ACL that the Cisco IOS does not display. The Cisco TAC will thank me for including that requirement because everyone forgets it—myself included, at times!
Edge Router as a Packet Inspector
By now, you should readily agree that using your edge router as a part of your layered security strategy will bring benefits to your network. Using the edge router as a choke point is certainly useful; however, there are some limitations to its use that might be important to you. Perhaps your company is involved in government contracts, so you must have the highest possible level of security. Or perhaps you are working for the government. Regardless, the next level up in security is the use of Cisco Firewall Feature Set (FFS) on the edge router.
At the heart of Cisco’s Firewall Feature Set IOS is Context-Based Access Control (CBAC). CBAC is a stateful packet inspection engine that extends the router’s filtering capability to the application layer (Layer 7) of the OSI reference model. It accomplishes this by using CBAC-based access lists. (Get used to access lists because they never go away; they only get reconstituted for another new cool technology.)
As the heart of the Firewall Feature Set tracks TCP, ICMP (as of Cisco IOS Software Release 12.2.15T), and UDP-based application packet, CBAC flows between hosts on either side of the firewall (router), thus performing SPI, which qualifies the use of the firewall features in its title; however, this type of IOS is no replacement for a dedicated stateful firewall.
Note
![]()
Routers that perform “firewall-like” operations are sometimes referred to as “routerwalls.” Remember, the key term here is “firewall-like,” which means that it can sort of function as a firewall but should not be used to replace a bonafide, dedicated firewall appliance.
CBAC is a hybrid of security architectures rather than a single pure implementation, such as a dedicated firewall. This hybrid architecture gives the FFS IOS the flexibility to function as both a router and firewall, making it ideally suited for use in providing increased security on the edge of your network. The edge of your network is truly the best place for this type of security technology.
Note
![]()
The Cisco Firewall Feature Set IOS is supported on almost every Cisco router platform. The caveat is that additional memory is typically required to deploy and use this version of IOS. In many cases, your router will need two things to run the Firewall Feature Set IOS: additional memory and appropriate IOS software license. For some reason, Cisco memory has not been reduced in price like PC memory; therefore, you will be incurring additional cost. However, I strongly recommend that you look for bundled deals that contain the router, memory, and IOS that you need.
Benefits of the Firewall Feature Set
Although the goal of this book is not to provide a lot of marketing hype, this technology begs an exception because it is the Cadillac of IOS.
The Firewall Feature Set IOS is particularly useful for businesses that are interested in a cost-effective way of extending perimeter security across all network boundaries, specifically branch-office, intranet, and extranet perimeters. In addition, it is appropriate for small and medium-sized businesses that need a cost-effective router that includes an integrated firewall with intrusion-detection capabilities. Some benefits of the Cisco IOS Firewall Feature Set are
• Dynamic filtering—CBAC allows return path filtering for TCP, UDP, and ICMP that creates dynamic stateful entries based on the bidirectional communication sessions in the filtering of access lists when a conversation is first established. CBAC allows the creation of these, provided there are permit statements in extended access lists that are unique. This eliminates the need to leave any statically open ports; in other words, CBAC will open ports dynamically only when traffic matches an ACL. The ports that are opened dynamically are limited in lifespan (the duration of the conversation) and only to specific hosts, thus limiting the opportunity for external attacks. Some of the filtering capabilities include the following:
— Standard and Extended Access Control Lists (ACLs)—Apply controls over access to specific network segments, and define which traffic passes through a network segment or the router, thus protecting your network.
— Lock and Key–Dynamic ACLs—Grant temporary access through firewalls upon user identification (username/password).
— Per User Authentication and Authorization—Provides the ability to control user access by IP address and interface as determined by the security policy. This is known as authentication proxy.
• TCP sequence numbers tracking—CBAC monitors the outbound communication session sequence numbers and the inbound communication session that TCP uses to track the state of the communication stream. This sequence number tracking provides protection against man-in-the middle and other session hijacking attacks because incorrect sequence numbers get packets discarded. As discussed in previous chapters, this is the essence of SPI.
• Tracking of communication session states—CBAC tracks half-open, open, and closed TCP sessions to provide defense against TCP-SYN DOS attacks. Session number and transmission per minute rates are tracked using high and low, administrator-defined thresholds.
• UDP and ICMP connection tracking—These two protocols are difficult to monitor because they do not have the characteristics that are necessary to be tracked statefully, like TCP. This does not alleviate the need to do so; therefore, CBAC tracks them through the use of dynamic filtering and timers that approximate conversation status. At press time, this technique is perhaps one of the most advanced means of validating the transmission of these protocols.
• Session logging—As a security device, a firewall must protect first and foremost. However, trailing ever so slightly behind protection is the ability to log and provide an audit trail. Important functionality to include in session logs includes details about transactions—communication termination, time stamps, source host, destination host, ports, and total number of bytes transmitted. This information is useful, depending on the culture of your company and has a variety of uses. CBAC provides support for per-application auditing in real time. Reporting is provided through the standard IOS logging mechanism with support for local and remote reporting to a syslog server.
• Application specific monitoring—CBAC examines packet flows for many application-specific protocol violations, along with single-path TCP, UDP, and ICMP flows. If CBAC detects a violation, the conversation is blocked and the relevant channels are closed. Application packet inspection is available for the following protocols, which have been the targets of many vulnerabilities:
— CU-SeeMe (Port 7648)—Peer-to-peer videoconferencing.
— FTP (Port 21)—Client-server File Transfer Protocol.
— H.323 (Port 1720)—Packet-based multimedia communication protocol (VoIP) that inspects Q931 and H.245 control messages to open additional UDP channels for video and audio data; this also includes SIP (Port 5060) Session Initiation Protocol.
— ICMP Inspection—Throughout this book, you have seen the uses of ICMP to troubleshoot network issues and by attackers to discover your network topology and exploit your network. The firewall feature set employs packet inspection to trust only the ICMP messages generated from within the internal network.
— MCGP (Port 2427)—Media Control Gateway Protocol (VoIP).
— MSRPC (Port 135)—Microsoft Remote Procedure Call Protocol (provides system-to-system process communication).
— Net show (Port 1755)—Microsoft’s streaming media platform.
— R-EXEC (Port 512)—Berkeley remote command protocol (UNIX).
— R-SHELL (Port 514)—Berkeley remote shell protocol (UNIX).
— RTSP (Port 544)—Real-Time Streaming Protocol (multimedia and VoIP).
— SMTP (Port 25)—Simple Mail Transfer Protocol for detecting invalid SMTP commands; eliminates requirement for external mail relay in “demilitarized zones.”
— SQLnet (Port 1521)—Client-server middleware for client-to-database and database-to-database communication. Inspects redirect messages from Oracle listener processes; opens port for clients to connect to servers.
— Stream Works (Port 1558)—Streaming media platform (now owned by Real Networks).
— SUNrpc (Port 111)—Sun Microsystems’ remote procedure call protocol (NFS).
— Real Audio (Port 7070)—Real Networks’ streaming media platform.
— Telnet (Port 23)—Virtual terminal protocol.
— TFTP (Port 69)—Trivial File Transfer Protocol.
— VDOlive (Port 7000)—Streaming media protocol.
• Java applet blocking—At the edge router, you can set the level of protection in place against Java applets. The router can be configured to filter or completely deny access to Java applets that are not embedded in an archive or compressed file—you decide.
• Virtual private networks (VPNs)—Provide secure data transfer over the Internet; reduce implementation and management costs for remote branch offices and mobile users/employees; enhance quality of service and reliability; standards-based for interoperability. VPNs are becoming extremely popular with the increasing prevalence of high-speed broadband Internet access at reasonable costs. Chapter 7, “IPSec Virtual Private Networks (VPNs),” covers VPNs in greater detail.
A robust and layered security policy entails more than setting up a firewall. Cisco FFS IOS Software is an ideal method for implementing increased security at the edge of your network, thus allowing easier enforcement of security policies and increased network security. The FFS also offers a means of providing forensic analysis of connections in the event of a security breach or suspected breach.
Content-Based Packet Inspection
As discussed in Chapter 5, many dedicated firewalls have security defined on a per-physical interface level. This is the concept of an interface that connects to outside your network to the Internet—for example, versus an interface that connects to the inside of your network. An interface connected to the public Internet clearly has a higher security requirement than an internal interface. This belief is similar across every type of firewall. Remember, it is important to know who to trust and who not to trust.
The Cisco IOS Firewall Feature Set, however, operates on a router, and the mass of gray matter in San Jose had a divinely inspired moment that allowed them to take the mission of a router (route packets) and that of a firewall without the dependency of trust. A firewall innately understands trust through its use of inside and outside interfaces. A router running FFS must be manually configured to understand trust. For example, you might decide to not allow inbound (defined as “from the outside in”) Telnet, so you should set up an ACL to block TCP Telnet port 21, or also not allow SNMP traffic into a network from the Internet.
This means that the FFS does not function entirely like a true firewall, but you have probably already figured that out.
The FFS allows for the inspection of a packet’s contents, which is extremely effective when securing your network. Consider that if you allow port 80 (HTTP) in, security is intact as long as it is going to your web server, right? Wrong! You have a false sense of security. Attackers know that if you have a website, you must allow HTTP traffic to reach it; therefore, they send HTTP packets with the contents of packets containing malicious code designed to attack the web server. Yikes! Is that a newsflash for you? Do not despair—CBAC is there!
Using the IOS IDS, CBAC, allows for the inspection of packet contents based on a simple concept: inspection precedes access. After the inspection, the packet can be filtered accordingly, as shown in Figure 6-3.
Figure 6-3. CBAC Security Controls
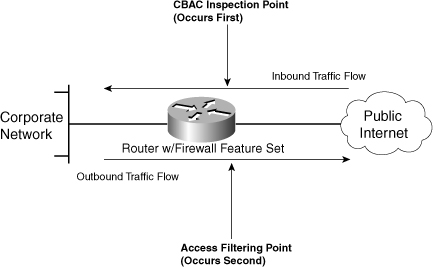
Of course, you can have multiple points of inspection in the form of ACLs. The only requirement of the FFS and CBAC is that the filtering must occur after the inspection. Having the FFS determine access based on conversation direction maintains the capability for the router to continue to function primarily as a router.
From a design standpoint, you must do some careful thought and traffic analysis before implementing CBAC, particularly in environments requiring the use of an “explicit permit” access model. Now, take a look at the security process followed by a router equipped with the FFS IOS. This list is also reflected in Figure 6-4.
Figure 6-4. Cisco’s Firewall Feature Set IOS in Action!
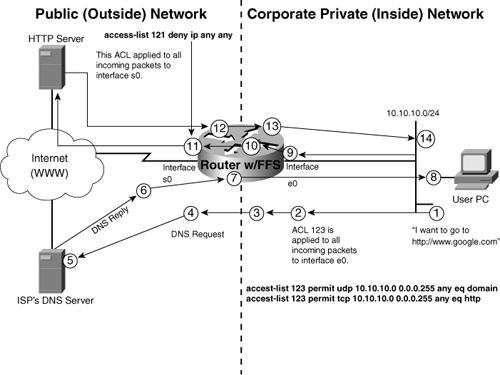
- A user is on the inside of a corporate network; from his PC he types http://www.google.com in his web browser and presses Enter.
Before the connection with the Google website can be established, the user’s PC issues a DNS domain name lookup to translate the URL to an IP address.
- The DNS lookup packet arrives at the router’s inside Ethernet interface. The DNS packet (a UDP datagram) is evaluated against access list 123, which looks at all incoming packets to the inside router’s Ethernet interface.
If the DNS packet is permitted by access list 123, it is forwarded; if not, the router discards the packet automatically (implicit deny all).
- After the DNS lookup packet is permitted by access list 123, it is inspected by CBAC, which inspects the packet and records the state information in its state table, specifically:
Source IP Address and Port Number
Destination IP Address, Port Number and Protocol
- CBAC takes the state data it gathered and dynamically creates a temporary permit statement to access list 121 (applied on serial interface to all packets that want to enter the router). The new access list permit statement permits only the return traffic from the destination host (DNS Server in this example) to the user’s PC when it has the same protocol and port numbers. The rule is prepended (put in front of) the static statements that are already in access list 121. Remember that UDP is not connection-oriented, so this poses some challenges in tracking a connection, unlike TCP, which has a connection set up.
- The DNS lookup packet (UDP port 53) is forwarded out of the router’s serial interface, processed by the DNS server, and a reply is sent back to the user’s PC. The dynamic UDP DNS entry remains in access list 121 for five seconds. If the router does not receive a reply within that five-second period, the temporary access list statement for this connection is cancelled.
- When the DNS reply packet arrives inbound to the router’s serial interface, it is evaluated against the inbound access list 121 and is permitted because it belongs to an established session that was tracked and will be permitted by CBAC.
- When permitted to enter the routers serial interface, the CBAC inspects the DNS reply AC and forwards it to the user’s PC. Because the session is UDP-based, the state entry remains for the default timer and is then removed, along with the dynamic ACL entry.
- The DNS reply arrives at the user’s PC now that it knows the IP address of the Google web server. Now that the PC knows the website’s IP address, the initial HTTP session is initiated. Because HTTP (WWW) uses TCP, the first packet sent is a SYN (synchronization) to begin the synchronization using the TCP 3-way handshake.
- The HTTP packet arrives at the router’s inside Ethernet interface. It is evaluated against the outbound access list 123 and is permitted because it is a HTTP port 80 packet.
- When the HTTP packet is permitted by access list 123, it is inspected by CBAC, which inspects the packet and records the state information in its state table, specifically:
Source IP Address and Port Number
Destination IP Address, Port Number and Protocol
- The packet is forwarded on to the destination web server. Based on the state table information, a temporary return traffic permit access list entry is prepended to access list 121. Because HTTP uses TCP, this temporary entry remains for up to 30 seconds for a SYN-ACK (synchronization-acknowledgment) response from the destination web server. If no reply is received within the time limit, the dynamic entry is retracted and the state table entry purged.
- When the reply packet arrives at the router’s serial interface, it is evaluated against the inbound access list 121 and accepted because the temporary permit entry has been added by CBAC.
- After being permitted to enter the router’s serial interface, CBAC inspects the packet for protocol-specific violations. If the header or data field information contain a known violation, CBAC discards the packet and closes the session. If the packet is error-free, it is forwarded onto the origin host.
- In the case of HTTP and other multisession protocols, in which several communication sessions are created to complete a task, CBAC continues to update the state table and serial interface access list accordingly.
All the CBAC-created temporary access list entries are removed when each communication session is completed, depending on the type of protocol being used:
• ICMP and UDP sessions are removed based on configurable inactivity timers.
• TCP sessions are removed five seconds after the exchange of FIN packets. In the event of an RST packet, the session is terminated and corresponding ACL entries are removed immediately.
— Starts deleting half-open sessions when its counters reach 500.
— Stops deleting half-open sessions when its counters see the number drop to 400.
• A huge number of “half-open” sessions being seen in a large chunk could mean that a DoS attack has begun in the form of a port scan or some other type of scan that uses incomplete, “half-open” sessions to gather information.
Intrusion Detection with Cisco IOS
The Cisco IOS Firewall IDS acts as an in-line intrusion detection sensor, watching packets and communication sessions as they flow through the router and scanning each packet to see whether it matches any of the IDS signatures.
Cisco developed its Cisco IOS Software-based intrusion detection capabilities in the Cisco IOS Firewall Feature Set with flexibility in mind so individual attack signatures could be disabled in case of false positives. Also, while it is preferable to enable both the firewall and intrusion detection features of the FFS CBAC security engine to support a network security policy, each of these features can be enabled independently and on different router interfaces.
The Cisco IOS Firewall Feature Set includes intrusion detection technology in addition to basic firewall functionality. The Cisco FFS IOS acts as a limited in-line intrusion detection sensor, watching packets and sessions as they flow through the router (this is the inline aspect of its operation—scanning each packet to determine whether the contents match any of the IDS signatures it knows about). When the router detects suspicious activity—in other words, when it believes that a packet contains an attack signature—it responds accordingly before network security can be compromised and logs the suspicious activity by using syslog and by communicating directly with a server running the Cisco Secure IDS Software.
Note
![]()
System Message Logging (syslog) provides a means for the system and its running processes to report various types of system state information. There are three classes of system state data: error, informational, and debug. Cisco IOS Software provides an extensive system message and error reporting facility. In fact, IOS uses over 500 service identifiers known as “facilities” to categorize system state data for error and event message reporting. System logging data is an important resource in diagnosing problems in general and, when issued by the firewall feature set, it allows for the reporting of events.
The Firewall Feature Set has limited intrusion detection capabilities because the attack signatures that allow it to identify various attacks are coded into the IOS and cannot change unless a new version of IOS is created with new signatures. The router would then require having the newer IOS uploaded to it. This contrasts with a dedicated IDS device that can have new signatures loaded rather easily. In practice, this means that the engineers responsible for your network’s security must ensure that the attack signatures are always as current as possible. The network administrator can configure the IDS-enabled router to choose the appropriate response to various threats. When packets in a session match a signature, the IDS system can be configured to take the following actions:
• Send an alarm to a syslog server or a Cisco Secure IDS Director (centralized management interface)
• Drop the offending packet
• Reset the TCP connection
Security best practice procedures recommend that you use the drop and rest actions together. In practice, this would mean that when the FFS IDS receives a packet that matches on its IDS attack signatures, the packet is dropped, thereby preventing it from reaching the targeted device in your network. Because attacks come in the form of multiple packets, simply dropping only one packet is not enough to protect your network. The FFS IDS will proactively send a reset to the device that sent the offending packet, thereby causing the connection to drop. This combination response is effective because the specific packet and the communication session are dropped.
When to Use the FFS IDS
Cisco IOS Firewall IDS capabilities are ideal for providing additional visibility at intranet, extranet, and branch-office Internet perimeters. Networks of all sizes and complexity will enjoy a more robust protection against attacks on the network and can automatically respond to threats from internal or external hosts.
The Cisco IOS Firewall with intrusion detection is intended to satisfy the security goals of all customers and is particularly appropriate for the following scenarios:
• Enterprise customers who are interested in a cost-effective method of extending their perimeter security across all network boundaries—specifically branch-office, intranet, and extranet network perimeters.
• Small and medium-sized businesses that are looking for a cost-effective router that has an integrated firewall with intrusion-detection capabilities.
• Service provider customers that want to set up managed services, providing their customers with firewalling and intrusion detection, all housed within the necessary function of a router.
FFS IDS Operational Overview
By now, it should be apparent that understanding packets is fairly important in networking. This is a realization that comes slowly for some people; however, after you accept this truth, networking should become much easier to understand. Everything is a packet, and all network devices are designed to do something with a packet. Sometimes, this is forwarding the packet to its destination, inspecting it, or even altering it in some way to accomplish a goal. This understanding is something that many hackers have figured out, and they use this knowledge to serve the dark side. That is melodramatic, but truthful because it is no fun rebuilding a server at 3:00 a.m. because it has been compromised, or dealing with a rampant virus that brings a network to its knees. This book is not designed to make you an expert at packets, but it introduces you to many of the fundamental truths of network security that provide a solid understanding of how the real world functions. If you need to learn more, you can build on this beginning. That being said, you do not have to live at the packet level; simply knowing that it is there and that it functions is the basis for everything networking.
Note
![]()
Perhaps the person I respect the most who educates people about living at the packet level is Laura Chappell. Visit her and her many online resources at http://www.packet-level.com/.
Cisco developed its Cisco IOS Software-based intrusion detection capabilities in the Cisco IOS Firewall with flexibility in mind so individual attack signatures could be disabled in case of false positives. Also, although it is preferable to enable the CBAC security engine’s firewall and intrusion detection features to support a network security policy, each of these features can be enabled independently and on different router interfaces.
The Cisco IOS IDS acts as an in-line intrusion detection sensor, watching packets as they traverse the router’s interfaces and acting upon them in a definable fashion.
The Cisco IOS Firewall’s Intrusion Detection System (Cisco IOS IDS) identifies the most common attacks using signatures to detect patterns of misuse in network traffic (attack signatures). The Cisco IOS Firewall Feature Set’s intrusion detection signatures were chosen from a broad cross-section of intrusion detection signatures. The signatures represent severe breaches of security, the most common network attacks, and information gathering scans.
In Cisco IOS IDS, signatures are categorized into four types:
• Info atomic signature—Atomic signatures can detect patterns as simple as an attempt to access a specific port on a specific host, such as a port scan.
• Info compound signature—Compound signatures can detect complex patterns, such as a sequence of operations distributed across multiple hosts over an arbitrary period of time. In general, both kinds of informational signatures detect attackers’ information-gathering activities.
• Attack atomic signature—Detect patterns where an attacker is attempting to access a single host device.
• Attack compound signature—A signature that detects complex attack activities that are spread across multiple hosts over an arbitrary period of time.
The intrusion detection signatures included in the Cisco IOS Firewall were chosen from a broad cross-section of intrusion detection signatures that represent the most common network attacks and information gathering scans that are not commonly found in an operational network.
Tip
![]()
The following URL lists attack signatures in numerical order by their signature number in the Cisco Secure IDS Network Security Database. After each signature’s name is an indication of the type of signature (information or attack, atomic or compound):
The following describes the packet auditing process with Cisco IOS IDS:
- You create an audit rule, which specifies the attack signatures that should be applied to packet traffic and the actions to be taken when a match is found. An audit rule can be as flexible and specific as needed to meet the goals of your security policy. An example rule follows in which you suspect or want to prevent the spamming of e-mail messages, so the IDS is configured to audit all SMTP traffic and ensure that there are no more than 100 recipients:
ip audit smtp spam 100
- You apply the audit rule to an interface on the router, specifying a traffic direction (in or out). The following example applies the audit rule to look at all inbound SMTP traffic to the router:
ip audit smtp in
- If the audit rule is applied to the in direction of the interface, packets passing through the interface are audited before the inbound ACL has a chance to discard them. This allows an administrator to be alerted if an attack or information-gathering activity is underway, even if the router would normally reject the activity. It is considered best practice to apply IDS audit rules inbound because they are inspected.
- If the audit rule is applied to the out direction on the interface, packets are audited after they enter the router through another interface. In this case, the inbound ACL of the other interface might discard packets before they are audited. This could result in the loss of IDS alarms, even though the attack or information-gathering activity was thwarted.
- Packets going through the interface that match the audit rule are audited by a series of modules, starting with IP; then either ICMP, TCP, or UDP (as appropriate); and finally, the application level.
- If a signature match is found in a module, the following user-configured actions occur:
— If the action is alarm, the module completes its audit, sends an alarm, and passes the packet to the next module.
— If the action is drop, the packet is dropped from the module, discarded, and not sent to the next module.
— If the action is reset, the packets are forwarded to the next module, and packets with the reset flag set are sent to both participants of the session, if the session is TCP.
If there are multiple signature matches in a module, only the first match fires an action. Additional matches in other modules fire additional alarms, but only one per module. IDS can reset only a TCP-based connection because this protocol has a SYN ACK and the all-powerful RST, which the IDS can send back to the attacker’s TCP-based session and shut down that application. UDP is not connection-oriented, so this is not something that can be reset—thus the need for ACLs on a blocking device such as a router or PIX Firewall.
FFS Limitations
CBAC enhances the effectiveness of IOS routers as security devices. Used in conjunction with other available security enhancements, IOS routers can be used for more than packet forwarding, thus increasing their ROI and allowing administrators to cost-effectively implement more secure networks. Of course, there is no perfect security device. That being said, there are some operational issues and limitations to CBAC of which administrators should be aware:
• Intrusion detection’s performance impact depends on the configuration of the signatures, the level of traffic on the router, the router platform, and other individual features enabled on the router such as encryption, routing, and so on. Enabling or disabling individual signatures does not alter performance significantly; however, signatures that are configured to use ACLs have a significant performance impact because the more you ask the router to inspect a packet, the greater its effect on router performance.
• For auditing atomic signatures, there is no traffic-dependent memory requirement. For auditing compound signatures, CBAC allocates memory to maintain the state of each session for each connection since by definition compound signatures are going to multiple machines. Memory is also allocated for the configuration database and for internal caching.
• CBAC inspection is not performed on packets with the source or destination address of the firewall interfaces. This impacts the router’s operation two different ways:
— vty (that is, Telnet) sessions between administrators and the firewall are not inspected.
— Management, authorization, and accounting (TACACS/RADIUS) traffic is not inspected because it too is destined to the router’s interface.
• Encrypted packet payloads, such as those used in VPNs, are not inspected unless the router is the encrypted link endpoint.
In general, having the more advanced functions available does increase the security of your router and network. However, these functions do not address the best practices in making the router a secure device when you are not employing them. The following section discusses this aspect of securing a router because, given the cost and effort needed to maintain the FFS, you are likely only going to deploy it at the edge of your network; therefore, protecting the inside devices is covered next.
Secure IOS Template
So far, this chapter has covered the different ways of securing your router and using it as a supplement to a dedicated firewall. This section explores how to harden your router and some of the best practices available for making the router a more secure device on your network. For the sake of brevity, you will not see coverage of every single ACL and command that is possible to secure your router. There are a couple reasons for this choice:
• The physical constraints of this book do not allow it, so content must be prioritized. Some of the items that are left out are specific to certain businesses in networking (ISPs, for example); most networks easily use the remaining items.
• Certain parts of the recommendations such as TACACS and RADIUS are covered in previous chapters, so there is no need to cover them again here.
This section is not meant to teach you how to secure your router with brief explanations so that you can decide which commands are appropriate for your network. You can apply these commands and suggestions today!
The complete Secure IOS Template can be found online at the INRGI website:
http://www.inrgi.net/security/secure_ios_template.htm
This website has all the latest commands and suggestions because security is an ever-changing world!
Tip
![]()
The Cisco SDM Security device manager is a mature, sound GUI tool that is now a shipping standard with the security/VPN routers. This GUI offers a robust setup and configuration of VPN and CBAC; it also does a router analysis and locks down the router, but it offers suggestions to the user about how to do it:
http://www.cisco.com/en/US/products/sw/secursw/ps5318/index.html
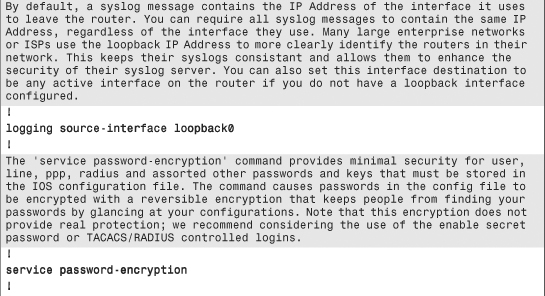
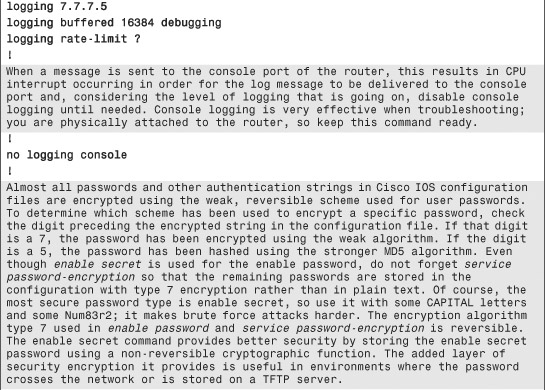
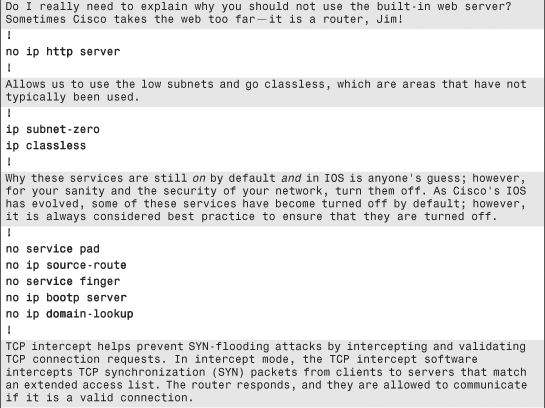
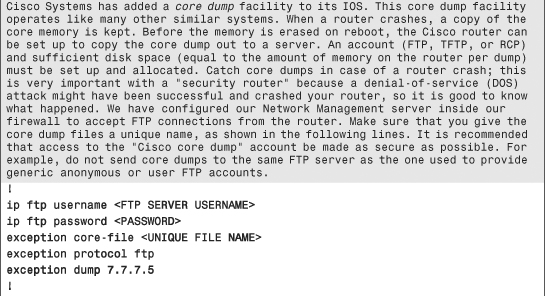
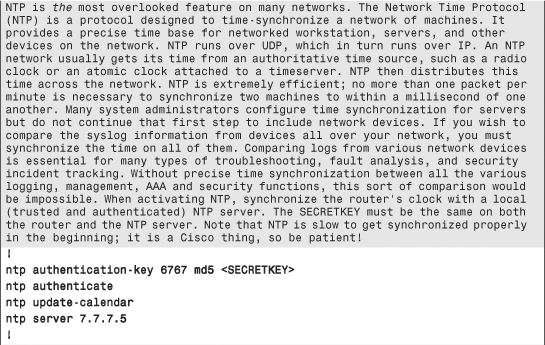
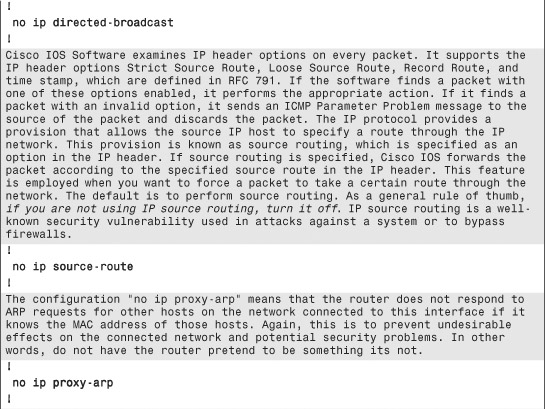
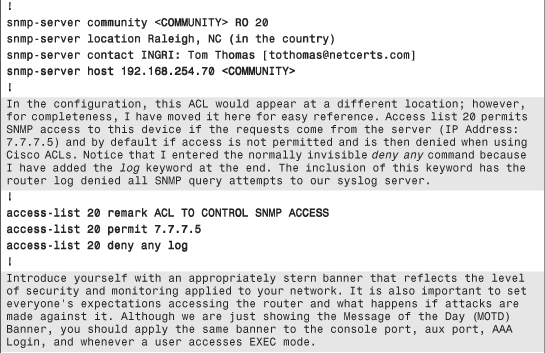
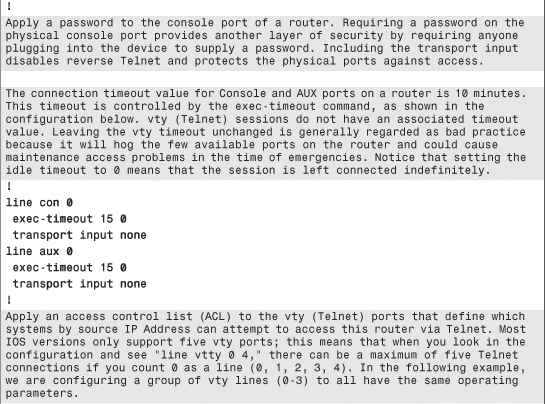
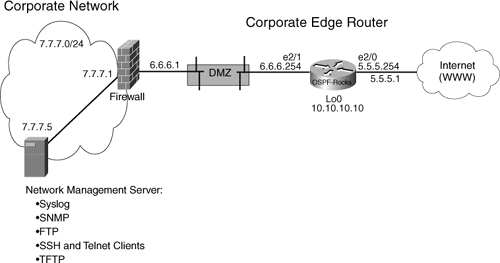
The configuration commands in Example 6-1 are in bold text so they stand out from the supporting comments, which are highlighted for readability. The secure template assumes the topology in Figure 6-5.
Figure 6-5. Secure Template Topology
Example 6-1. Secure IOS Template

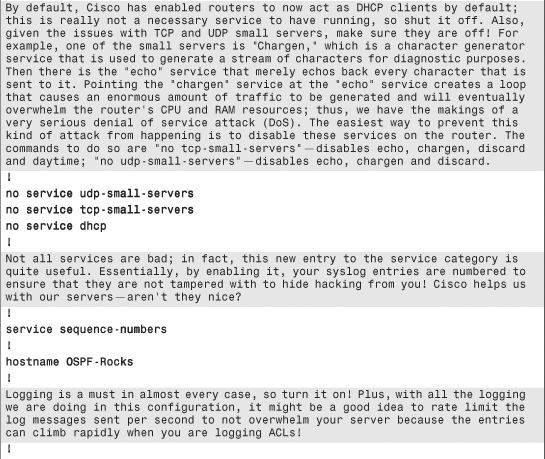


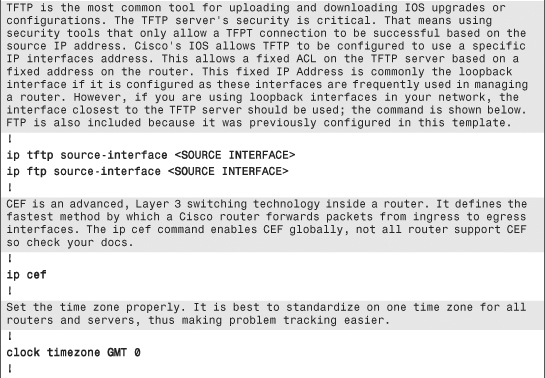
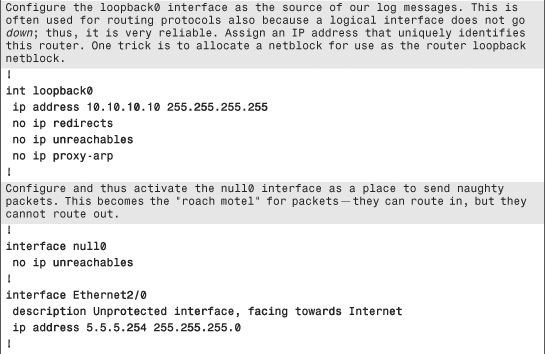

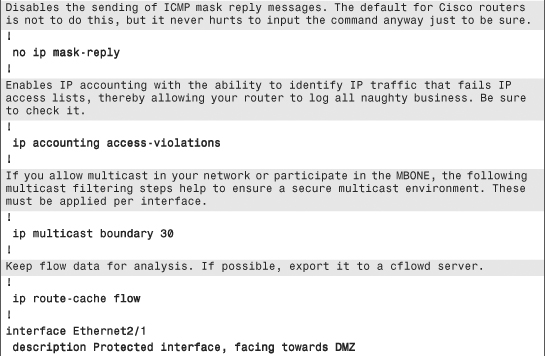
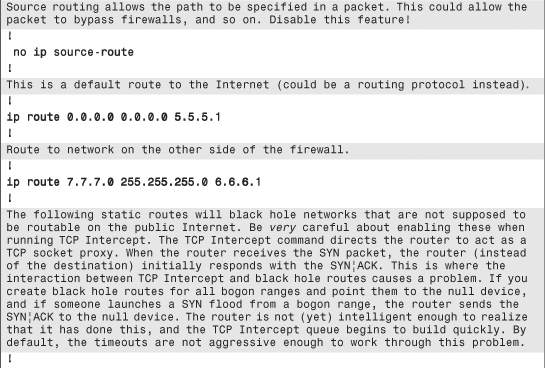
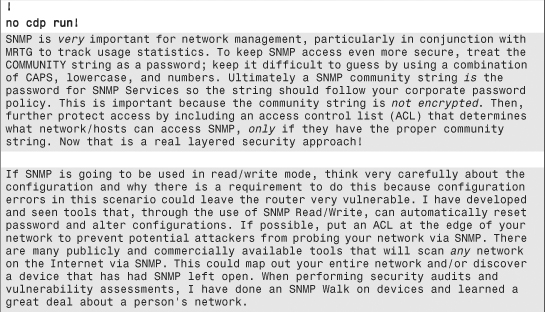
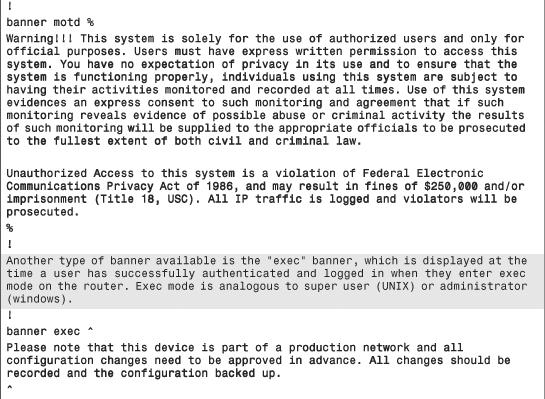
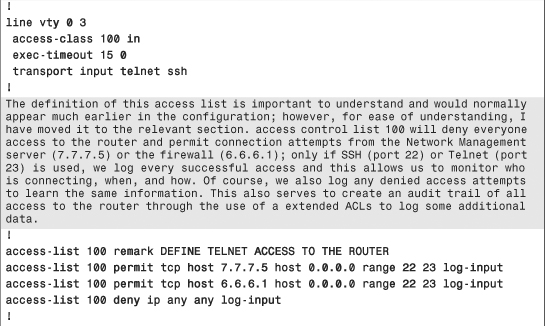
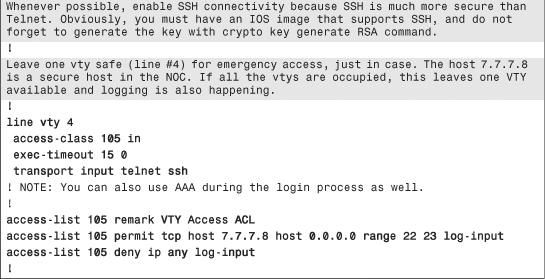
Chapter Summary
This chapter discussed ways and places in which a router can be used with a deeper purpose than it might have been implemented with. To this end, the chapter examined how a router can be used to prescreen your network as a choke point of entry. The next level was to have the router act as a more advanced packet inspection tool through the use of the Cisco IOS Firewall Feature Set and coupled with the Intrusion Detection feature. Both of these advanced technologies are not a replacement for dedicated devices of the same kind; however, they do offer a higher level of security in your network by adding additional layers of inspection and protection.
Next, the chapter focused on some of the more fundamental methods you can use immediately to secure the router itself. This information was presented in a real router configuration file, thus giving you a point of reference when comparing your router configurations with the suggestions provided here. The following chapter examines the steps you can take to use VPNs to increase network security.
Additional resources on security can be found online at
Increasing Security on IP Networks—An old, but essential document on some of the essentials to security and IP based networks: http://www.cisco.com/univercd/cc/td/doc/cisintwk/ics/cs003.htm
The Cisco INTERNET SECURITY ADVISORIES—An online list at the Cisco website of all its security advisories, including tutorials and details about how to protect yourself from some of the worst vulnerabilities on the Internet today (Cisco.com account required) at http://www.cisco.com/warp/customer/707/advisory.html.
Chapter Review Questions
1. Because every company that connects to the Internet has a router, should you deploy security on those routers?
2. What is the value of edge routers being used as choke points, and how effective can they be in increasing your network’s security?
3. What technology is at the heart of the Cisco Firewall Feature Set IOS?
4. How does the firewall feature set employ dynamic filtering of packets using ACLs?
5. Can the Cisco IOS IDS have multiple points of packet inspection?
6. Temporary access control lists have timers associated with them. Define how they function based on protocol (ICMP, UDP, and TCP)?
7. What is the difference between atomic and compound signatures?
8. What happens when an attacker uses chargen and echo together? How would you stop this from occurring in a Cisco router?