Essential Wireless Security
As discussed, there are some possible means of securing your wireless network beyond WEP. It is unlikely, however, that anyone has a RADIUS server ready and waiting to be used; therefore, you need to identify steps you can take immediately to increase the security of your wireless network. The attention to the pitfalls of wireless LANs has inspired some organizations to ban wireless LANs altogether. However, security-conscious organizations are fortifying their wireless LANs with a layered approach to security that includes the following:
• Putting the wireless network behind its own routed interface so that you can shut off access at a single choke point if necessary.
• Regular monitoring and discovery of rogue access points and potential associated vulnerabilities of nearby APs.
• Physical and logical AP security to ensure that someone cannot walk up to an access point and alter its configuration without your knowledge.
• Changing the SSID and then picking a random SSID that gives away nothing about your company or network.
• Disabling active SSID broadcasting, making your wireless invisible to prevent accidental association is important; however, decloaking can be done with KisMET and other tools. If attackers have the time (which they usually do), it won’t take long to decloak your SSID. KisMET is on the BackTrack 5 distribution and was cited earlier in this chapter as an excellent tool for this.
• Configure your AP to rotate encryption keys every ten minutes or less.
• Encryption and authentication, which might include a virtual private network over wireless.
• Using 802.1X for key management and authentication.
• Looking over the available EAP protocols and deciding which is right for your environment.
• Setting the session to time out every ten minutes or less.
• Establishing and enforcing wireless network security policies.
• Implementing proactive security measures that include wireless intrusion protection and detection in a layered approach is important.
• Deploying smart cards or tokens is a strong form of security and can be used with other security needs in your network, such as VPN access. However, the drawback here is that these solutions can be expensive.
• Regular software updates that keep the AP software up to date and regularly patched.
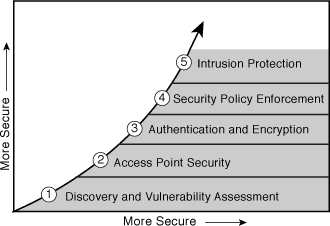
As shown in Figure 10-8, these steps and recommendations can be illustrated as a phased approach, which enforces the concept of first knowing what the vulnerabilities are and moving forward from that point.
Figure 10-8 Stages of Securing Your Wireless Network