Essentials First: Vulnerability Analysis
This section looks at some of the tools that are freely available to attackers. The fundamental truth this section teaches is that the bad guys have good tools. Previous chapters touched on many of the specific attack tools; however, attackers have a broad toolset with which they can launch multilevel attacks against your network. When an attacker gains a foothold in your network, it is leveraged to exploit another aspect of your network.
Attackers, for example, can, do, and will take advantage of weak authentication and authorization, improper allocations, poor security implementation, shared privileges among users or applications, or even poor employee security habits to gain unauthorized access to critical network resources.
Throughout this book, you have seen many ways to allow even the best security procedures and technologies to be circumvented. To understand how this is done, you must spend some time understanding the exact methods and tools the attackers use. Perhaps it is exciting to see an attacker’s tools; however, if any network resource is your responsibility, you must ensure that you use these tools to assess your network’s security. It is extremely important that you use these tools on behalf of your network so that vulnerabilities can be detected and found before an attacker uses them against you. You can count on these tools being used in your network—the decision you must make is who is going to use them first?
Fundamental Attacks
Leading-edge security technologies, policies, and procedures can quickly have their effectiveness nullified if those who are responsible for network security do not understand the methodology and tools that will be used against your network. This chapter discusses some of the methodologies and various tools that attackers use, how they operate, and the tools and techniques you can use to protect your network resources against these hacker tools.
Even the best security technologies and procedures can be rapidly nullified unless you know the precise methods and tools being employed against you. Therefore, it is crucial to be able to identify the various tools of the hacker trade, how they operate, and what kinds of protections thwart these attacks. This includes a thorough knowledge of the common tools and techniques discussed in the sections that follow.
IP Spoofing/Session Hijacking
This type of attack occurs when an attacker creates a packet with a different IP address to gain entry to a system. This attack exploits trust relationships by allowing the attacker to assume a trusted host’s identity. The header for each IP packet contains the source and destination IP address of the packet. By forging the header so that it contains a different IP address, an attacker can make it appear that the packet was sent from a different machine. The machine that responds will respond back to the forged source IP address. For this attack to be successful, the attacker must determine the “patterns of trust” for the target host—that is, for example, the range of IP addresses that the host trusts. After the attackers determine the pattern of trust, they can move on to the next step of the attack by either compromising the host or disabling it in some manner. These types of attacks are often used as the first step in the overall attack strategy. IP address spoofing is most frequently used in denial-of-service (DoS) attacks—the types of DoS attacks are covered in more detail in a few pages.
Note
Because attackers spoofed an IP address (that is, made it up so the target trusts it—the address could be a local LAN address, whereas the attackers are not local), the attackers might not see the response from the target. This means that the attackers are blind to their success, which is why this is usually a first step. It is common to blindly exploit vulnerabilities in this matter and, after the host is compromised, move to the next step.
IP Spoofing/Session Hijacking Tools
A variety of tools accomplish exploitation through IP spoofing/session hijacking. A quick Google search on “IP Spoofing Tools” returned more than 139,000 hits. The list that follows describes just a few:
• Dsniff: A collection of tools for network auditing and penetration testing specifically known as Dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, email, files, and so on). arp spoof, dns spoof, and macof facilitate the interception of network traffic.
• Hunt: A program for intruding into a connection, watching it, and resetting it. Hunt was an outgrowth of similar products such as Juggernaut, but it has several features that cannot be found in these products.
• Ettercap: A powerful Apple OS X, Windows, and UNIX-based program employing a text-mode GUI, easy enough to be used by script kiddies. All operations are automated, and the target computers are chosen from a scrollable list of hosts detected on the LAN. Ettercap can perform four methods of sniffing: IP, MAC, ARP, and public ARP. It also automates a variety of other tools.
• TotalSpoof: A free and useful utility that enables you to spoof websites. This spoofing enables the hacker to fool a website that has security into thinking that the hackers are already in the site so that the site logic will not check the authentication credentials again and enable entry into the secure site.
Prevention
Preventing these kinds of attacks is as important as understanding them and the tools that are used. Virtual private networks (VPN) are effective against IP spoofing because a VPN encrypts the original IP addresses as they are transmitted across the network. If either the data or the source address proves to be tampered with, the packet is deleted. This prevents an attacker from penetrating a system without access to the VPN encryption keys.
Packet Analyzers
A packet analyzer (also known as a network analyzer or protocol sniffer) is a tool that intercepts and logs traffic passing over a digital network or part of a network. As data streams flow across the network, the sniffer captures each packet and decodes and analyzes its content according to the appropriate RFC or other specifications. Sniffers generally come either software-based (for PCs/PDAs) or hardware-based (on a dedicated computer). Using sophisticated network sniffers that can decode data from packets across all layers of the OSI model, attackers can steal usernames and passwords and use that information to launch further attacks. In general, attackers can use sniffers by compromising the corporation’s physical security—say, walking into the office and plugging a laptop into the network. Many sniffers have built in “expert systems” that determine critical network data without the user having to need any skills beyond clicking a button.
With the growing use of wireless networks, someone in the parking lot with a wireless device can access the network. By using sniffers, attackers can obtain valuable information about usernames and passwords across public or private networks—in particular, from applications such as FTP, Telnet, and others that send passwords in the clear. Protocols such as SMTP, IMAP, and POP3 are used for remote access to email applications via simple username and password authentication techniques and are especially susceptible to sniffer attacks. Because users tend to reuse passwords across multiple applications and platforms, attackers can potentially use the acquired information to obtain access to other resources on the network, where their confidentiality could be compromised.
Denial of Service (DoS) Attacks
DoS attack methods overload networks by making so many requests that regular traffic is slowed or completely interrupted. These attacks methods have existed since the Internet became open to the public—not only in theory, but also in practice. Although DoS attacks have been around for decades, the ugly offspring Distributed Denial-of-Service attacks are much newer, first seen in late June/early July 1999.
A “standard” DoS attack does not involve breaking into the target; instead, the attacker’s goal is to simply overload the target (router or web server) with so much fake traffic that it cannot cope. When the target cannot cope, genuine users cannot connect and are therefore denied service.
Smurf Attacks
A smurf attack is a type of DoS attack that exploits the use of the Internet Control Message Protocol (ICMP, aka ping) and the IP’s network and broadcast addresses. A smurf attack’s purpose is to disable a target host or network by consuming all its resources; aside from this, it causes no permanent damage. Every IP subnet has two special addresses:
• The network address, which is the first address in the subnet
• The network broadcast address, which is the last address in the subnet range
The IP network address serves as the identity address of a given subnet in the IP routing table. The IP broadcast address was devised as a method for sending information to all the hosts in a given subnet. Most IP implementations respond to messages with the network or broadcast address as the source address. This support is known as directed broadcast. This feature is also data used for legitimate purposes.
Fraggle Attack
Fraggle is an attack similar to a smurf attack, but instead of using ICMP, it uses UDP. The attack broadcasts a spoofed UDP packet to the network, which in turn replies to the victim’s system. The larger the network, the larger the amount of traffic redirected to the victim’s system.
SYN Flood Attack
In TCP/IP, a three-way handshake occurs whenever a client attempts to connect to a service, such as FTP or HTTP. The three-way handshake is defined as follows:
1. The client sends a packet with the SYN (synchronization) flag in the TCP header set to the service.
2. The service responds with a SYN-ACK (synchronization-acknowledgment).
3. The client sends a handshake to the service (a SYN-ACK transaction) and the session is considered established so data begins to flow.
Note
Richard Stevens (TCP/IP Illustrated, p. 231) explains the format of the SYN packets and is an excellent resource for those wanting to understand the details of TCP/IP.
A SYN flood attack is when the client does not respond to the service’s SYN-ACK, thereby tying up the service until it times out. In this type of attack, the client never responds because the client’s source address is forged (spoofed). The attacker’s goal is to send SYN packets to the service faster than it takes for the service to timeout waiting for the client’s SYN-ACK response. This causes the service to become so busy acknowledging the SYNs and waiting for the client that it cannot answer requests for service from legitimate users and therefore denies them service.
Teardrop Attack
A teardrop attack uses fragmented UDP packets. The first fragment is fine, but the second packet overwrites part of the first fragmented packet. This results in a memory error, and the system crashes.
Distributed Denial-of-Service
A Distributed Denial-of-Service (DDoS) attack generates false traffic from multiple hosts across the Internet. A DDoS attack uses multiple computers throughout the network that it has previously infected with a DDoS daemon (program); these computers are then known as zombie computers.
Note
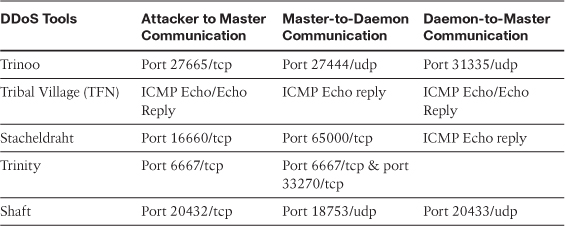
A DDoS daemon is a specialized computer program designed for use in controlling and coordinating a DDoS attack. As of this writing, there are five known programs: Tribal Village (TFN); Tribe Flood Network 2K (TFN2K); Trinoo; Stacheldraht, which is German for “barbwire”; and Trinity. You can learn more about these programs by visiting the following URLs:
http://staff.washington.edu/dittrich/misc/trinoo.analysis
http://staff.washington.edu/dittrich/misc/tfn.analysis
http://staff.washington.edu/dittrich/misc/stacheldraht.
http://packetstormsecurity.org/distributed/TFN2k_Analysis-1.3.txt
These zombie computers all work together as a zombie network to send out bogus connection messages, thereby increasing the amount of open connections with which the target must deal. This prevents legitimate users from accessing the services being offered. A DoS attack can be conducted using various bogus connection techniques. Table 12-1 provides a listing of the various DDoS tools and the ports used to communicate between the various components.
Table 12-1 DDoS Tools Communication Matrix
DoS attacks are easy to implement and can cause significant damage, thereby disrupting a server, website, or network’s operation and effectively disconnecting them from the Internet. DoS attacks attack the work differently based on the type of attack and which section of the network architecture are being targeted. Following are types of attacks:
• Bandwidth
• Logic
• Protocol
For example, a SYN flood is a protocol attack that uses fictitious, half-open TCP connection requests that exhaust the resources of the targeted system.
Preventing DoS Attacks
You might be wondering how you can defend against DoS attacks. This is perhaps one of the most difficult attacks to defend against because many of the attacks come in the form of traffic that would be considered a normal occurrence on your network. Perhaps one of the most common defenses is to rate limit certain types of traffic. For example, you might want to allow ping (ICMP); however, too much of it could be considered a DoS attack, so you would rate limit ICMP. In contrast, you must carefully watch other types of traffic. Perhaps limiting HTTP (web) traffic to your Internet e-commerce site would be a mistake!
There is no surefire method by which you can protect yourself 100 percent against DoS attacks. They (the attackers) continually take advantage of bugs and exploits present in the operating system, JavaScript, and Internet browser (Mozilla, Internet Explorer, and so on); even the Adobe Flash Player is not immune to vulnerabilities. The best method I have found is to keep an organization’s computing environment up to date with the latest security patches, allow only necessary traffic into, and out of, your network by using defense in depth, (honeypots, ACLs, firewalls, and DMZs), and monitor the traffic coming in from outside by using an IDS or IPS. Having to effectively defend against every DoS attack type strikes fear into your IT and security staff. Carefully consider these restrictions, their impact on your business, and the risk mitigation should an attacker successfully launch a DoS attack. I’ve said it before and I will continue to say it: You must educate your staff on the risks and how to identify and protect your assets.
Other Types of Attacks
When planning an attack on someone, be it a nation or corporation, you must use all weapons you have to obtain your objective. It is the same way with hackers and malcontents who want nothing more than to disrupt your corporation’s day-to-day business for political gain, personal vendetta, or boredom. The following sections describe a few other attack types or vectors that you need to be aware of.
Ping of Death
A ping of death attack uses the characteristics of ICMP to the attacker’s benefit. The compromised hosts are directed to attack the designated target via a continuous stream of ping packets. This causes an incredible number of ping requests coming from thousands of compromised hosts to begin impacting the host. This is certainly an unwelcome scenario, but the attacker has also altered the ICMP packet (ICMP echo request). Each packet does not contain the compromised host’s source address; instead, each packet’s source address is the target’s address. (That is, the source and destination address are the targets.) The target system then transmits a response (ICMP echo reply) to each packet, which is destined to itself, thus causing traffic to increase exponentially until the target crashes because of its inability to handle such a high volume of traffic. To take this further, imagine if a broadcast were allowed onto a LAN with the target’s source address. The real caveat implicit in this attack is that the traffic appears completely normal and is typically allowed into any network and through firewalls, and so on. You can see this attack in action with a properly positioned sniffer or probe.
Man-in-the-Middle Attacks
In a Man-in-the-Middle (MitM) assault, the attacker places himself in the middle of a communication flow between two hosts: usually a server and a client. The attacker then intercepts messages transmitted between the two hosts. The attacker can look for a variety of things. Perhaps he wants to see how much money is in your bank account, your password to the fantasy football website, or even block the connection. The interesting part and point of concern here is that if the attacker does not alter anything, you will not know that the packets are being intercepted by an attacker in the middle!
Network sniffers, such as Ettercap (http://ettercap.sourceforge.net/), are often used to accomplish this type of attack. You can also find that MitM attacks can be used to reconstruct public cryptic keys. This discussion is beyond the scope of this text; however, protecting passwords and keys is always a good idea in case you need another reason for a password policy.
ARP Spoofing (aka ARP Poisoning)
ARP spoofing is one way in which a MitM attack can be successful if executed on either a wired or wireless LAN. The process of updating a target computer’s ARP cache with forged entries is referred to as ARP poisoning. This technique involves the attacker constructing a forged ARP request and reply packets to change the Layer 2 Ethernet MAC address to one of his choosing. By the attacker sending forged ARP replies, a target computer could be convinced to send frames destined for Host B to instead go to the attacker’s computer first so that they can be recorded and read. When done properly, Host A has no idea that this ARP redirection took place, as shown in Figure 12-1.
Figure 12-1 Man in the Middle: ARP Spoofing
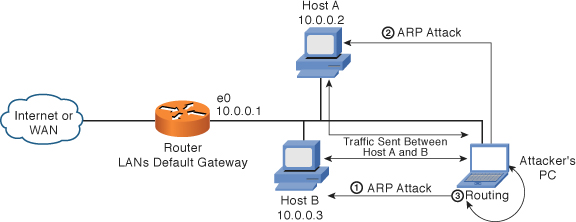
IP spoofing plays an important role in MitM attacks. In IP spoofing, an attacker intercepts a legitimate communication between two parties. The attacker then controls the flow of communication and can eliminate or alter the information sent by one of the original parties without either the sender or receiver being aware, By doing so, an attacker can fool a victim into disclosing confidential information by spoofing the identity of the original sender.
Back Doors
A back door, or trapdoor, is a secret way of gaining access to a program, operating system, BIOS, or network service. You often see these types of back doors in computer games where a certain phrase or key combination provides you unlimited money, power, health, and so on. Back-door entry to resources can be accidentally or intentionally opened by users or by design; consider the following examples:
• Deliberately placed by system developers to allow quick access during development and not turned off before release.
• Placed by employees to facilitate performance of their duties because the “proper procedure” made them think it made their jobs harder, so there must be a smarter and easier way. Users might not be as technical as your IT staff, and often they find back doors because they do not have a preconceived notion of how something should work.
• Normal part of standard “default” operating system installs that have not been eliminated by OS hardening, such as retaining default user logon ID and password combinations. Again, vendors do not want technical support calls, so they make it as easy and open as possible. This means that your IT staff must review and harden every server!
• Placed by disgruntled employees to allow access after termination. In many cases, an employee suspects that the loss of his job is coming, which makes him angry and feel unappreciated, so he wants to ensure that he can strike back as necessary when the time comes.
• Created by the execution of malicious code, such as viruses or a Trojan horse that takes advantage of a vulnerability in an operating system or application.
As discussed previously, these attacks and tools are the most common types of vulnerabilities used by attackers. Understanding them will better allow you to understand the tools and techniques discussed in the following section.
LAND (Local Area Network Denial) Attack
A LAND attack is a DoS that consists of using a type of IP spoof-based attack where the source and destination address are the same. This attack crashes some TCP/IP implementations that do not know how to handle the packet. This is a rarity in terms of appearance in the real world but is a standard signature on ISS, NFR, Dragon, and Cisco Net Ranger and IDS-IOS.
Xmas Tree Attack
In an Xmas tree attack, a TCP packet sent to any known service port sets all the code flags (URG, ACK, PSH, RST, SYN, and FIN). An alternative version of this attack is a TCP packet without any flags set. Both cases are the result of packet craft and do not exist in the wild.
Ping Pong Attack
Following are two variations on the ping pong attack:
• A flood of spoofed packets to the echo service (UDP/TCP port 7), which is a simple service that echoes back any data sent to it.
• Sending a spoofed UDP message that appears to be from the chargen service port to the echo (UDP port 7) service on another system. The chargen service responds to any packet sent to the service port with a 72-byte random character string. After the spoofed connection is established, the echo port sends traffic to the chargen port and a loop develops.
Both variations consume CPU resources; enough attacks cause the system to becomes CPU-bound and crash.
Firewalking
Many people consider firewalls immune to attacks or standard techniques that enable attackers to figure out their rule sets to bypass them. That belief was true for a while; however, new techniques are always being developed and, in this context, firewalking is a concept that enables the attacker to send specially crafted packets through a firewall to determine what ports and services are permitted through the firewall. Attackers with this knowledge can make their port scans hidden and thus map your network through your firewall.
Firewalking works because IP packets contain a field that prevents them from being sent around a network forever. This field is known as Time-To-Live (TTL). When this field reaches zero, the packet is discarded. In firewalking, this field is set to a value that enables the packet to get beyond the firewall and then be dropped by a host or device after the firewall. What enables this to happen is that the TTL value is one of the first things checked and, if its value is zero, a device sends back a packet acknowledging that it is being dropped without the original packet ever actually being processed.
