Security Scanners
When hackers want to breach your systems, they typically look for well-known security flaws and bugs to attack and exploit, some of the most common of which have been discussed in earlier chapters of this book. A true attack, which has the end goal of penetrating and controlling the target system, relies on the attacker gathering the most accurate and comprehensive view of an organization’s security. As attackers evaluate the network, they exploit vulnerabilities to determine precisely how to get control of valuable information assets.
Attacking vulnerabilities used to be a time-intensive procedure that required a lot of knowledge on the part of the attacker. Today, however, automated tools have changed all that. Gone are the days of having to figure out the publicly available exploit codes and maintaining them all to be effective. Now a Google search provides anyone with enough information to be dangerous.
You might be wondering whether we are talking about the role of attackers and commiserating with them about how hard it is to control the data. Or perhaps we are talking about how network administrators are faced with such a daunting task. Actually, we are talking about both, and the point is that this is no longer the biggest concern. Today, attacks have been scripted and published, and companies have formed to automate the detection of attacks and exploit vulnerabilities. This section looks at the most comprehensive of these tools that, included with the individual tools covered elsewhere in this book, should provide you with excellent resources to detect vulnerabilities and begin correcting them.
Features and Benefits of Vulnerability Scanners
Applications that perform security scan and vulnerability assessments do the scanning and calculations in the background. Frankly, the focus here is not in how vulnerabilities are detected, but on what is vulnerable. The following four categories summarize the value of these scanning tools:
• Scan and detection accuracy: Scans and reported vulnerabilities must be accurate with minimal false positives—defined as normal activity or configuration that the system mistakenly reports as malicious. The opposite also holds true then: There can be no false negatives—defined as malicious activity that is not detected.
• Documentation and support: Must be clear, concise, well written, and easy to understand (like this book). This includes reporting documentation and application operation so that users can figure out how to make the application work and see the documented findings in the report.
• Reporting: The most important aspect of a vulnerability scanner is when you need to know the next steps after a vulnerability has been detected (that is, what was detected and how to fix it); thus, a report must be customizable, useful, and accurate.
• Vulnerability updates: New vulnerabilities are constantly being released and, with today’s technology, every system should have a way to automatically update.
Freeware Security Scanners
Your corporation needs to have the capability to scan for attacks, identify them, and notify you that they are occurring. To help bridge the gap between nothing and a robust multifeature solution, several different freeware security scanners are available. You can pull one off the Internet and implement it.
Metasploit
The Metasploit Framework is a penetration testing toolkit, exploit development platform, and research tool that provides useful information and tools for penetration testers, security researchers, and IDS signature developers. The framework includes hundreds of working remote exploits for a variety of platforms. It is written in the Ruby scripting language and is provided on the BSD license. The latest version is 3.5.0. You can find more information about Metasploit on www.metasploit.com. It is also part of BT5, as mentioned in Chapter 1, “There Be Hackers Here.”
NMAP
Network Mapper (NMAP) is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
NMAP uses raw IP packets to determine what hosts are available on the network, what services (application name and version) those hosts offer, what operating systems (and OS versions) they run, what type of packet filters or firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks but works fine against single hosts.
NMAP runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. In addition to the classic command-line NMAP executable, the NMAP suite includes an advanced GUI and results viewer (Zenmap); a flexible data transfer, redirection, and debugging tool (Ncat); and a utility for comparing scan results (Ndiff).
The most recent version is 5.35DC1. You can read more about NMAP and its functionality at http://nmap.org.
SAINT
SAINT is a product suite that offers a complete solution to evaluate the threats and vulnerabilities that affect your network. It consists of SAINTscanner, SAINTexploit, SAINTmanager, and SAINTwriter.
SAINTscanner scans your network to detect anything that could allow an attacker to gain a foothold, create a DoS, or obtain access to sensitive information. SAINT offers heterogeneous scanning that identifies vulnerabilities across operating systems, desktop applications, network devices, web applications, and databases.
SAINTexploit is the penetration testing component that is integrated with SAINTscanner. SAINTexploit automates the penetration testing process, examines vulnerabilities discovered by the scanner, exposes where the attacker could breach the network, and exploits the vulnerability.
SAINTmanager is a remote management console for organizations that want to centrally manage multiple scanners and help manage the vulnerability life cycle.
SAINTwriter is the report writer. It is built in to all SAINT’s products for reporting on vulnerability assessment, penetration testing, trouble tickers, and vulnerability management.
You can find more information on SAINT and its entire suite of products at www.saintcorporation.com.
Nessus
Nessus is to vulnerability detection what Snort is to IDS: an open source solution supported by a community of Internet volunteers. You can learn more about Nessus at www.nessus.org.
In Their Own Words
The following section is a direct quote from the Nessus web page on how it describes its product:
The “Nessus” Project aims to provide to the Internet community a free, powerful, up-to-date and easy to use remote security scanner.
A security scanner is software, which will audit remotely a given network and determine whether bad guys (a.k.a. “crackers”) may break into it, or misuse it in some way.
Unlike many other security scanners, Nessus does not take anything for granted. That is, it will not consider that a given service is running on a fixed port—that is, if you run your web server on port 1234, Nessus will detect it and test its security. It will not make its security tests regarding the version number of the remote services, but will really attempt to exploit the vulnerability.
Nessus is very fast, reliable and has a modular architecture that allows you to fit it to your needs.
Scan and Detection Accuracy
Scans and reported vulnerabilities must be accurate, with minimal false positives—defined as normal activity or a configuration that the system mistakenly reports as malicious. The opposite also then holds true: There can be no false negatives—defined as malicious activity that is not detected.
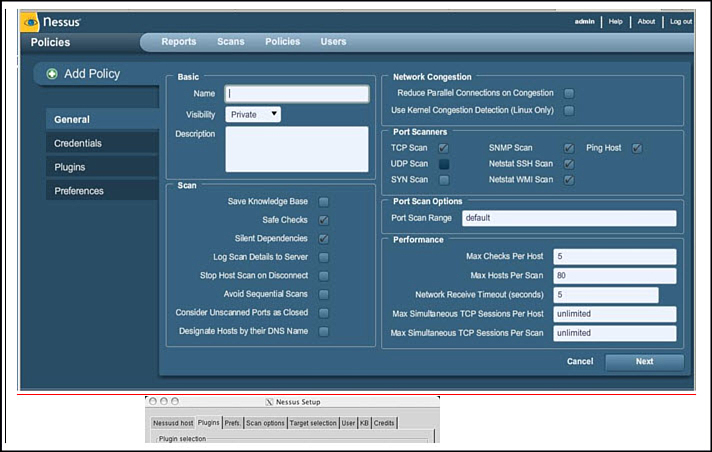
Nessus has good capabilities to detect vulnerabilities and is accurate in the vulnerabilities it detects and finds. Being an open source project, Nessus is constantly being watched, tested, studied, and improved upon. Technical support can be purchased through Tenable Network security. With so much visibility, this product has become configurable for those with the knowledge to understand its underpinnings. Figure 12-2 shows the Nessus setup screen and its flexibility, strength, and many possible options.
Figure 12-2 Nessus 4.2.2 Vulnerability Policy Screen
Documentation and Support
Documentation must be clear, concise, well written, and easy to understand. This includes reporting documentation and an application operation so that users can figure out how to make the application work and see the documented findings in the report.
Nessus documentation is excellent. The installation and configuration guides are online and easily downloaded for all operating system platforms. It took me 10 minutes to download, obtain a key, and register the software for my Microsoft XP Pro laptop and then, another 30 minutes to download and install the plug-ins. There was no need to add or remove any third-party software. No MAN pages to wade through, and no fumbling around a command-line interface.
Although the Nessus Project began as a free remote security scanner, in 2005, Tenable Network Security (the company that was co-founded by the Nessus developer) changed Nessus 3 to a proprietary license. In 2008, Tenable revised the feed license, which enables home users full access to the plug-in, and began charging for a professional license. What does all that mean? It means Nessus 4.2.2 is free of charge for personal or home use; however, in an enterprise environment this software license must be purchased and registered before you can use it. Technical support can be purchased for both the home and professional versions; however, there is a mailing list and forum that has many of the core Nessus programmers, and they can be helpful.
Reporting
The most important aspect of a vulnerability scanner is when you need to know the next steps after a vulnerability has been detected (that is, what was detected and how to fix it); thus a report must be customizable, useful, and accurate.
Nessus creates reports in a variety of formats; the most useful is HTML. These reports are fully hyperlinked with complete analysis of the vulnerabilities detected, their level of risk to your network, and great, pretty pictures that can visualize the vulnerabilities. On a downside, the reports are UNIX-centric and full of contextual and grammatical errors, not something that you can share without serious editing. The information is accurate, just not as polished as a commercial product.
Vulnerability Updates
New vulnerabilities are constantly being released and, with today’s technology, every system should have a way to automatically update.
Nessus is kept up to date via scripting that can be automated to ensure that it has the latest signatures. Nessus runs on the following platforms: Microsoft Windows, Mac OS X, Linux, FreedBSD, Solaris, and iPhone.
Nessus is a good vulnerability scanner that has exceptional functionality as a result of its open source status. There are some excellent resources available for Nessus. You can find other related links at the following URLs:
www.securityprojects.org/nessuswx/
Nessus 4.2.2 Home Edition is freely available for download and requires no purchase because it is open source software.
Retina Version 5.11.10
Retina is eEye’s premiere security scanner that leads its suite of security products. eEye offers several products that focus on securing the Microsoft product line. You can learn more about Retina at www.eeye.com.
In Their Own Words
The following section is a direct quote from the eEye corporate web page on how it describes its vulnerability scanner, Retina:
Retina, founded from over a decade of technology innovation by eEye’s world renowned security research team, is an integrated end-to-end vulnerability and compliance solution designed to help organizations with protection and compliancy by defining and monitoring relevant IT controls.
Retina monitors both patch and configuration vulnerabilities and compliance to predefined configuration baselines and provides automated notification of violations. The environment is assessed, capturing established security controls along with any vulnerabilities or configuration violations that impact the network. Detailed reports providing prescriptive guidance and recommendations are then forwarded and response is initiated to ensure that corrective action can be taken in a timely fashion.
Retina’s management console is a fully integrated and rich Internet-enabled application for security and compliance management. Now you can simplify the management of distributed, complex infrastructures while protecting your mission critical assets from evolving threats with a single unified management system.
Scan and Detection Accuracy
Scans and reported vulnerabilities must be accurate with minimal false positives—defined as normal activity or configuration that the system mistakenly reports as malicious. The opposite also holds true, then: There can be no false negatives—defined as malicious activity that is not detected.
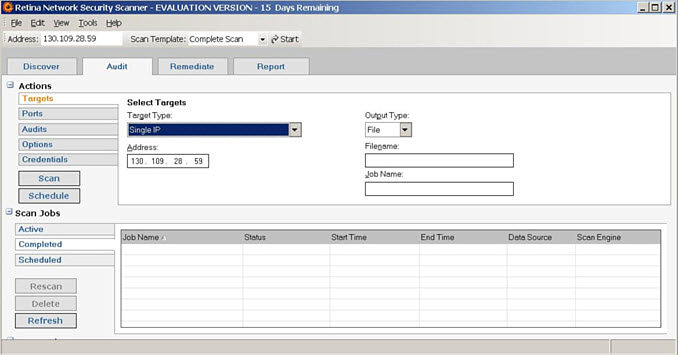
Retina has an excellent presentation interface for the execution of scans; it is intuitive and comes with a variety of other tools, so it can be used for more than just a vulnerability scanner. One of the best features that Retina provides is the easy customization, scheduling, and penetration audit customization. What sets Retina apart is the capability to create scanning policies with different scans for different devices. For example, you can scan Internet servers differently than employee PCs. Figure 12-3 shows an example of targeting a specific device in Retina.
Figure 12-3 Selecting a Target Range in Retina
Documentation and Support
Documentation must be clear, concise, well written, and easy to understand. This includes reporting documentation and application operation so that users can figure out how to make the application work and see the documented findings in the report.
Retina documentation is included in the Windows help file and appears to be complete, answering many of the questions a typical user would have. It does not contain many in-depth how-to’s, but it provides enough examples that their lack is not a hindrance. A web-based form submitted to the eEye technical support team provides only support options for users.
Reporting
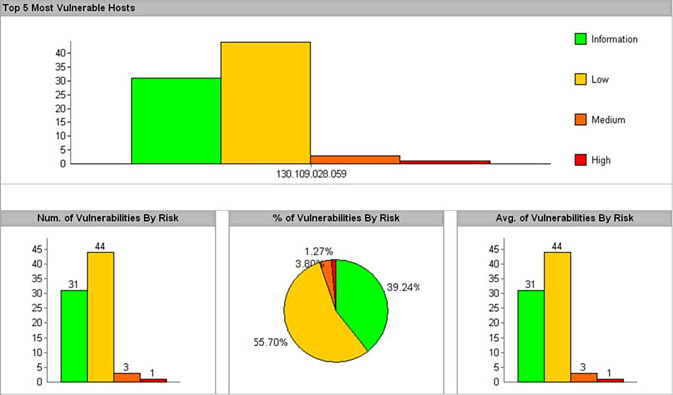
The most important aspect of a vulnerability scanner is when you need to know the next steps after a vulnerability has been detected (that is, what was detected and how to fix it); thus, a report must be customizable, useful, and accurate. Figure 12-4 shows the summary of vulnerabilities after Retina completes its scan of your network.
Figure 12-4 Vulnerability Summary by Risk Level
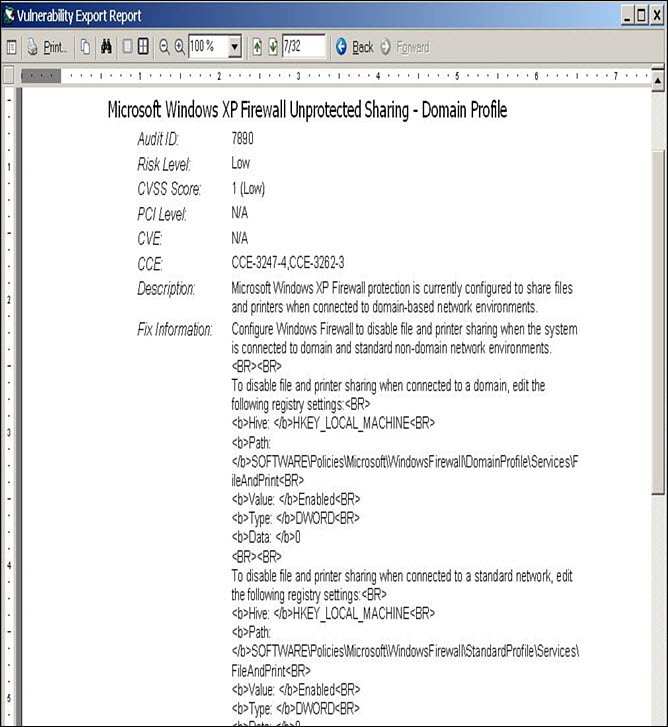
Like Nessus, Retina provides an overview of the detected vulnerability along with links to additional information and corrective actions, such as a Microsoft hotfix. Figure 12-5 shows specific detected vulnerability information, what the risk is, and where to find the manufacturer’s fix.
Figure 12-5 Vulnerabilities Details
Vulnerability Updates
New vulnerabilities are constantly being released and, with today’s technology, every system should have a means of updating itself automatically.
Retina is exceptional is this regard; it can be configured not only to update its list of vulnerabilities, but also the application itself. Curiously, the open source movement has missed the boat on that feature. Retina takes a bit of getting used to, and it is an effective vulnerability scanner.
