Chapter 2. Security Policies
“...Being defeated is often a temporary condition. Giving up is what makes it permanent....”
—Marlene vos Savant
By the end of this chapter, you should know and be able to explain the following:
• What role does a security policy play in my network?
• How do I create a security policy?
• How do I deal with any security policy violations?
• What security policies are appropriate for my organization?
• What are the Security Standards and do they apply to my organization?
Being able to answer these key questions will enable you to understand the overall characteristics and importance of a network security policy.
Having clear, definable, enforceable, and up-to-date security policies is the most essential first step in protecting and securing your people, property, network, and data. Policies provide the foundation for defining acceptable and appropriate behavior within your organization and network. At the most fundamental level, policies form the “rule of law,” which is the legal maxim stating that no one is immune to the law, or in this particular circumstance, no one is immune to the policy. Short- and long-term contractors and consultants can be tied to policy via service-level agreements (SLA) with similar verbiage.
Consider a security policy that is analogous to rules and laws found in your neighborhood. What would life be like to live within these boundaries? If you wanted to accomplish anything worthwhile, it would be unbearable. Viewed in this light, a security policy defines what is acceptable, or not, inside and outside your network. This is a fundamental definition of the role of security policy, yet there are many additional reasons that define a security policy’s usefulness:
• Establishes expectations for standards, procedures, and guidelines
• Defines appropriate behavior
• Communicates an operational and business consensus
• Provides a foundation for HR action if unacceptable behavior occurs
• Defines roles and responsibilities of each group in securing the company
• Assists in prosecuting legal action if unacceptable behavior occurs
• Provides definitions for concepts and ideas crucial in securing your network
• Allows for required tools to be defined by justifying funds for network security
Having a security policy enables everyone within a company to clearly understand who is responsible for what and establishes a foundation for the policies and processes of each department within your organization, with an emphasis on “protect” from a corporate perspective. For example, customer service understands its roles and responsibilities in protecting sensitive customer information; human resources understands what is expected of employees; and manufacturing and development knows how to protect the results of expensive research and development. Of course, the greatest achievement of a security policy is what a security policy means to an IT department when trying to manage users and assets. From the security policy, the IT staff knows what to configure on servers, the tools it needs, rules for firewalls, virtual private network (VPN) secure remote access settings, and so on—the list is endless.
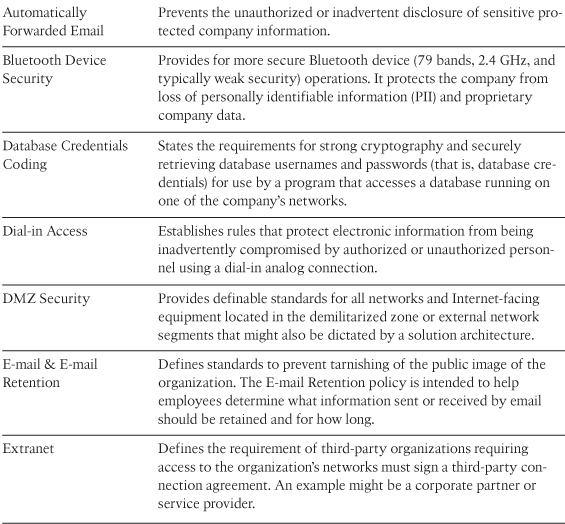
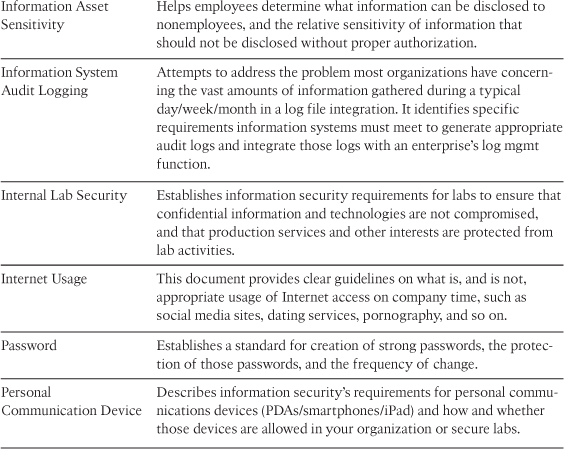
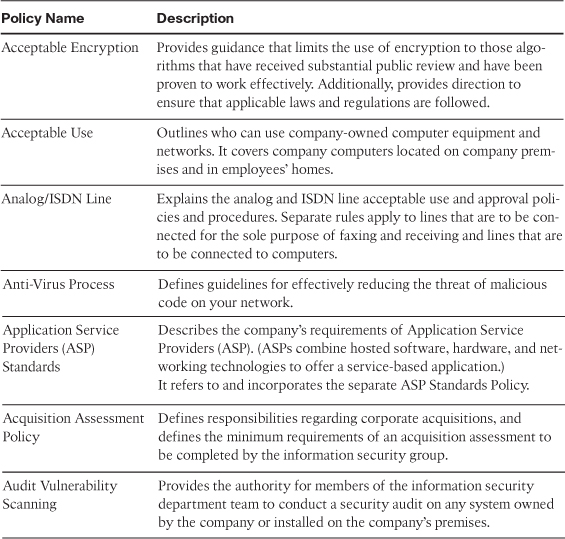
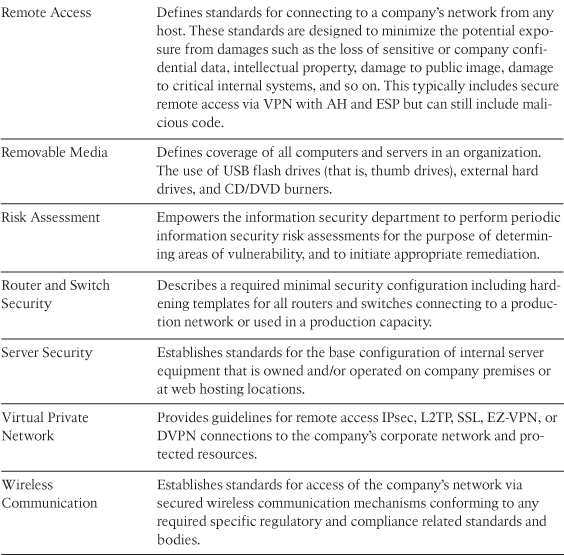
You might wonder what some of the most commonly used security policies are and what areas of IT should consider using a policy. The System Administration, Networking, and Security (SANS) Institute Security Policy Project and SANS certification (GIAC Fundamentals of Security Policy [GFSP]) provide a starting point to policy creation, templates, and process (www.sans.org/security-resources/policies/). SANS provides a variety of security policies, some of the more common of which are described in Table 2-1.
Table 2-1 Common Security Policies
In addition to knowing what is expected, every person or department in a company is affected by a security policy and can make an impact individually protecting corporate reputation, brand, and assets. As you can see from the following list, each group within an organization is affected:
• Generic user: Because users access network resources, your policy impacts them the most.
• Management team: This group (and the executive sponsor for the information security policy program) is ultimately concerned with the protection of corporate resources and data while monitoring the financial impact.
• Accountants, legal, and investors: Understand that the company’s responsibility to protect itself depends on such policies while recognizing the positive impact a security policy can have enabling the business and tying together the technical and business requirements.
• Security management team: This group’s role is defined in the policy to pinpoint what group is tasked with security policy enforcement.
The following section discusses what could be viewed as the critical first question for designing a security policy: who and what to trust.