Wireless Communication Policy
The purpose of this policy is to secure and protect the information assets owned by Granite Systems. Granite Systems provides computer devices, networks, and other electronic information systems to meet missions, goals, and initiatives.
Granite Systems grants access to these resources as a privilege and must manage them responsibly to maintain the confidentiality, integrity, and availability of all information assets preventing disclosure, alteration, and destruction.
This policy specifies the conditions that wireless infrastructure devices must satisfy to connect to Granite Systems network. Only those wireless infrastructure devices that meet the standards specified in this policy or are granted an exception by the Information Security Department are approved for connectivity to the Granite Systems network.
Scope
All employees, contractors, consultants, and temporary and other workers at Granite Systems, including all personnel affiliated with third parties that maintain a wireless infrastructure device on behalf of Granite Systems, must adhere to this policy. This policy applies to all wireless infrastructure devices connected to a Granite Systems network or reside on a Granite Systems site that provides wireless connectivity to endpoint devices including, but not limited to, laptops, desktops, smart phones, and personal digital assistants (PDAs). This includes any form of wireless communication device capable of transmitting packet data in 802.11 and Bluetooth networks, spectrums, and channels.
The Information Security Department must approve exceptions to this policy in advance.
Policy Statement
General Network Access Requirements
All wireless infrastructure devices that reside at a Granite Systems site and connect to a Granite Systems network, or provide access to information classified as Granite Systems Confidential, Granite Systems Highly Confidential, or Granite Systems Restricted must
a. Abide by the standards specified in the Wireless Communication Standard
b. Be installed, supported, and maintained by an approved support team
c. Use Granite Systems approved authentication protocols and infrastructure
d. Use Granite Systems approved wireless encryption protocols
e. Maintain a hardware address (MAC Address) that can be registered and tracked aiding in MAC spoofing controls
f. Not interfere with wireless access deployments maintained by other support organizations
Lab and Isolated Wireless Device Requirements
All lab and wireless infrastructure devices that provide access to Granite Systems Confidential, Granite Systems High Confidential, or Granite Systems Restricted information must adhere to the guidelines specified in the section “General Network Access Requirements” and isolated wireless devices that do not provide general network connectivity to the Granite Systems network must
a. Be isolated from the corporate network (that is, it must not provide any corporate connectivity) and comply with the DMZ Lab Security Policy or Internal Lab Security Policy.
b. Not interfere with wireless access deployments maintained by other support organizations.
Home Wireless Device Requirements
a. Wireless infrastructure devices that provide direct access to the Granite Systems corporate network must conform to the Home Wireless Device Requirements as detailed in the Wireless Communication Standard.
b. Wireless infrastructure devices that fail to conform to the Home Wireless Device Requirements must be installed in a manner that prohibits direct access to the Granite Systems corporate network. Access to the Granite Systems corporate network through this device must use standard remote access authentication.
Enforcement
An employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment. A violation of this policy by a temporary worker, contractor, or vendor might result in the termination of their contract or assignment with Granite Systems.
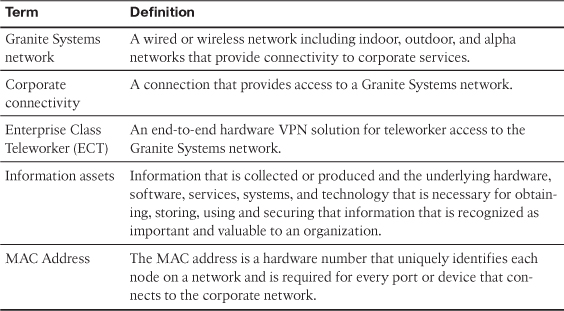
Definitions
Revision History
The next section covers the security policy that is necessary when corporate business partners or other third parties need to connect to your organization’s network—a sensitive situation, indeed.
