Microsoft Security
When you talk about Microsoft security, it is not an easy thing to pin down. With the many operating systems, back office products, database servers, and so on, you need to focus this beam a little. Then the problem becomes how can you narrow this beam and make sure it is accurate and pertinent. This is a difficult task. Following are broad categories and an overview, which include links to the more specific items as they pertain to Windows XP or Microsoft Windows 7.
Anything older than Microsoft Windows XP and Microsoft Windows Vista is not included. Microsoft Windows XP is still a stable operating system, somewhat secure (if updates are applied regularly), and viable in the workplace. Microsoft Windows 7 is becoming the new de facto system in office environments; it is more stable, secure, and up to date than Microsoft Windows XP and requires less maintenance to maintain its security posture.
Security Policies
Are we talking about account policies, local policies, or audit policies? And then which operating system? Microsoft Windows 2003 Server or Microsoft Windows XP Professional? To be fair, the major components of three operating systems are covered: Microsoft Windows XP Professional, Microsoft Windows Server 2003, and Microsoft Windows 7 Professional.
Microsoft Windows XP Professional
For Microsoft Windows XP Professional, there is a security guide detailing various aspects of authorization and access control. The Microsoft Windows XP Professional operating system includes a number of features that you can use to protect selected files, applications, and other resources from unauthorized use. These features include access control lists (ACL), security groups, and local and group policies. These tools provide a powerful access control infrastructure for your organization’s network infrastructure. If you have Microsoft Windows XP Professional systems deployed as your working desktop environment, we highly recommend reading through the security guide (http://technet.microsoft.com/en-us/library/bb457115.aspx).
Microsoft Windows Server 2003
For Microsoft Windows Server 2003, you can manage and secure several features through Group Policies—things such as account settings, event audit settings, software environment, wireless, and so on. When you edit security settings in a local GPO, only the security policy settings on that computer are affected. When you edit security policy settings in a GPO in Active Directory directory service, the policy settings affect sites, domains, and organizational units (OU) to which the GPO is linked. Some settings, such as password policy settings, are operative only at the domain level. You can find some guidelines at the following sites:
• Security and Protection Overview: http://technet.microsoft.com/en-us/library/dd582586(WS.10).aspx
• Security Policy Settings: http://technet.microsoft.com/en-us/library/cc739328(WS.10).aspx
• Security Policy Planning and Architecture Best Practices: http://technet.microsoft.com/en-us/library/cc739214(WS.10).aspx
Microsoft Windows 7
There have been many changes and improvements to Windows 7 over Windows XP and Windows Vista. These changes include new features such as BitLocker, AppLocker, multiple active firewall profiles, user account control, Internet Explorer security features, auditing enhancements, safe unlinking in the kernel pool, Windows Biometric Framework, smartcard support, and service accounts. Table 4-2 gives a brief overview.
Table 4-2 Security Improvements in Windows 7
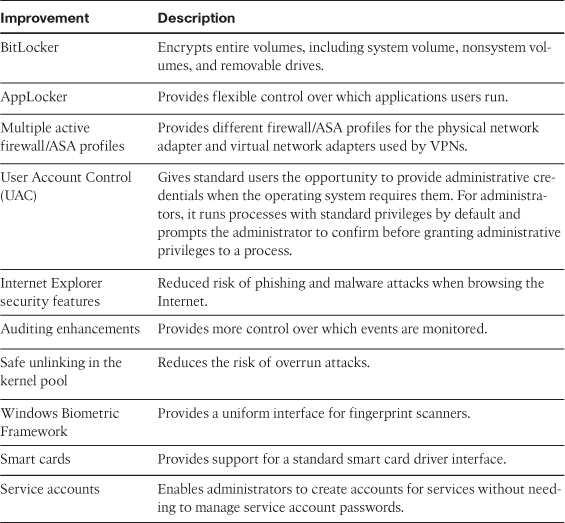
The collection of Windows 7 security and protection guidelines, which you can find at http://technet.microsoft.com/en-us/library/dd571075(WS.10).aspx, provides detailed information about security features listed in Table 4-2. These features enable the IT professional to design, deploy, and maintain Windows 7 desktop environment in a secure fashion.
However, Windows 7 is not only deployed at the office, but also many individuals use Windows 7 at home. If you need help and how-to security information for using Windows at home, see Windows Help and How-to at http://go.microsoft.com/fwlink/?LinkId=168437.
Windows Server 2008
Microsoft has replaced the Windows Server 2008 security guide with the more intuitive Windows 2008 Security Compliance Management Toolkit, as part of its Security Management Compliance Toolkit series. You can find the toolkit at www.microsoft.com/download/en/details.aspx?DisplayLang=en&id=17606.
Many tools Windows Server 2008 deploys can assist the administrator in planning, deploying, and administering a Windows 2008 server securely. Following is a link that provides guidance for everything from managing user accounts to diagnosing overall system security: Windows 2008 Security Tools: http://technet.microsoft.com/en-us/library/cc722416(WS.10).aspx.
Microsoft Security Compliance Manager
Similar to the Cisco Validated Design (CVD) program mentioned earlier in the chapter, Microsoft has the Security Compliance Manager. This product provides centralized security baseline management features, a baseline portfolio, customization capabilities, and security baseline export flexibility. This enables you as an administrator or the chief information security officer (CISO) to increase your organization’s capability to efficiently manage the security and compliance process for the most widely used Microsoft technologies.
The Security Compliance Manager is the next evolution in security from Microsoft. It incorporated its previous guidance and documentation into this tool. This tool enables you to access and automate all your organization’s security baselines in one central place.
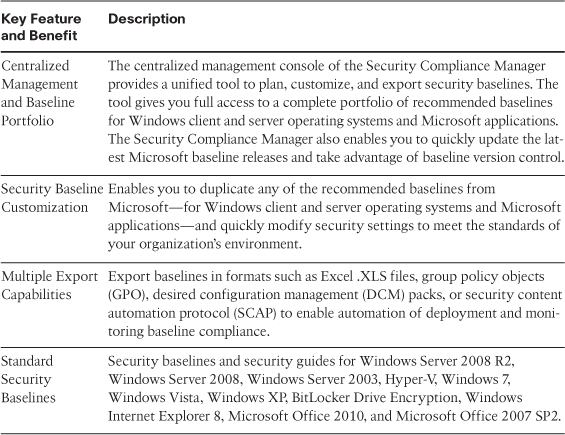
This tool enables you to access the complete database of Microsoft recommended security settings, customize your baselines, and then export them in various forms, including XLS, Group Policy Objects (GPO), Desired Configuration Management (DCM) packs, or Security Content Automation Protocol (SCAP). Table 4-3 outlines the key benefits and features of the Microsoft Security Compliance Manager.
Table 4-3 Microsoft Security Compliance Manager Key Features and Benefits
Following is a link to the Security Compliance Manager: www.microsoft.com/download/en/details.aspx?displaylang=en&id=16776, which you should download, install, and use.
