Security First Design Concepts
Network security can be a hydra (many-headed beast) with regard to potential attacks and threats against the network. The resources and opinions on this subject are incredible, and opinions vary greatly depending on whom you ask. For example, in 2004 when I wrote the first edition of this book, a simple Google search on “designing a secure network” returned almost half a million results. In 2012, that same search string returns more than five and a quarter million hits. It is no wonder that conflicting security concepts bombard people, causing a great deal of confusion. To be honest, if you were to look up network security books, any bookstore also reveals almost as many!
The point is that experts in each area of network design have written so much on designing secure network architecture that to try to do the subject justice here is beyond the scope of this book. Books and websites deal with every aspect of network security, server security, application security, and so forth. We endeavor to provide you with a strong foundation upon which to build the security knowledge required for your role or network.
This book illustrates good network security design principles to build the strongest possible foundation. However, it covers some important design concepts of which you must be aware:
• Layered security: A network that implements layered security truly understands that a single point of defense is doomed to eventual failure. Thus, as Figure 5-1 demonstrates, consistently implementing security throughout a network at as many points as possible is considered good design. This concept of layering a network’s security is the single-most important design concept in this chapter and is often referred to as Defense in Depth.
Figure 5-1 Layered Security Points (Defense in Depth)
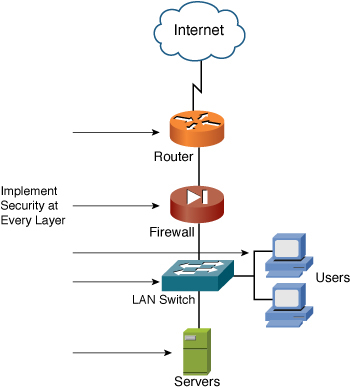
• Controlling access: The network is ultimately your responsibility and, as a result, you determine what is allowed into and on your network. One highly recommended practice is to make access decisions with the mindset of “block everything, and allow only what is needed to conduct business.” This has also been referred to as the Policy of Least Privilege (POLP). This is the default action of Cisco firewalls and access control lists (ACL).
• Role-specific security (Role Based Access Control [RBAC]): When deciding upon access and privilege (that is, trust), one of the most useful templates to use is based on a user’s role within the organization. For example, a web developer would clearly need access to the organization’s website, whereas an administrative assistant would not.
• User awareness: Stories abound about users writing down passwords, changing them five times in a row, and then using their original password again. It is not that users are intentionally bypassing security; they do not understand the purpose of the security and may have become complacent. Okay; let’s be honest; some users definitely try to bypass security, but more on that later! Thus, user awareness through training and visibility is essential to get users to understand the importance of security. One great idea for getting users to attend training and learn why it is important is to serve ice cream with all the trimmings. This method appeals to a basic human love of sweets, but it is also effective and fun; you will become a popular person! It is crucial to have your user truly aware of security and supportive of security policies; making security training a pleasant experience can help make that happen.
• Monitoring: Perhaps one of the most forgotten aspects of security is monitoring. Many organizations believe that it is enough simply to have security. They forget that monitoring their systems to ensure that they remain secure and are not subject to attack is also crucial. The truth is, security devices report every little thing, and it’s hard to do an effective job if you’re not listening and monitoring what they are saying. One of the ways to achieve this is to “tune” the device; another is to have every device on the network report to a central device that you tune and monitor. It is much easier to monitor one device than ten. Cisco has an effective product for this, referred to as Cisco Security Manager. More information on the Cisco Security Manager is available at www.cisco.com/en/US/products/ps6498/index.html. Chapter 11, “Intrusion Detection and Honeypots,” discusses the methods used to monitor for attacks: intrusion detection systems (IDS). A strongly recommended practice is to include provisions for IDS when designing a network’s security solution in wired or wireless networks.
• Keep systems patched: Patching or updating systems is a fundamental task that is often forgotten by system administrators with their busy schedules. Fortunately, many newer operating systems can remind you when new updates are available. For example, I use an Apple Mac Book Pro running OS X (aka Snow Leopard); within this operating system is a built-in functionality that automatically checks for updates, as shown in Figure 5-2.
Figure 5-2 MAC OS X Automatic Update Functionality
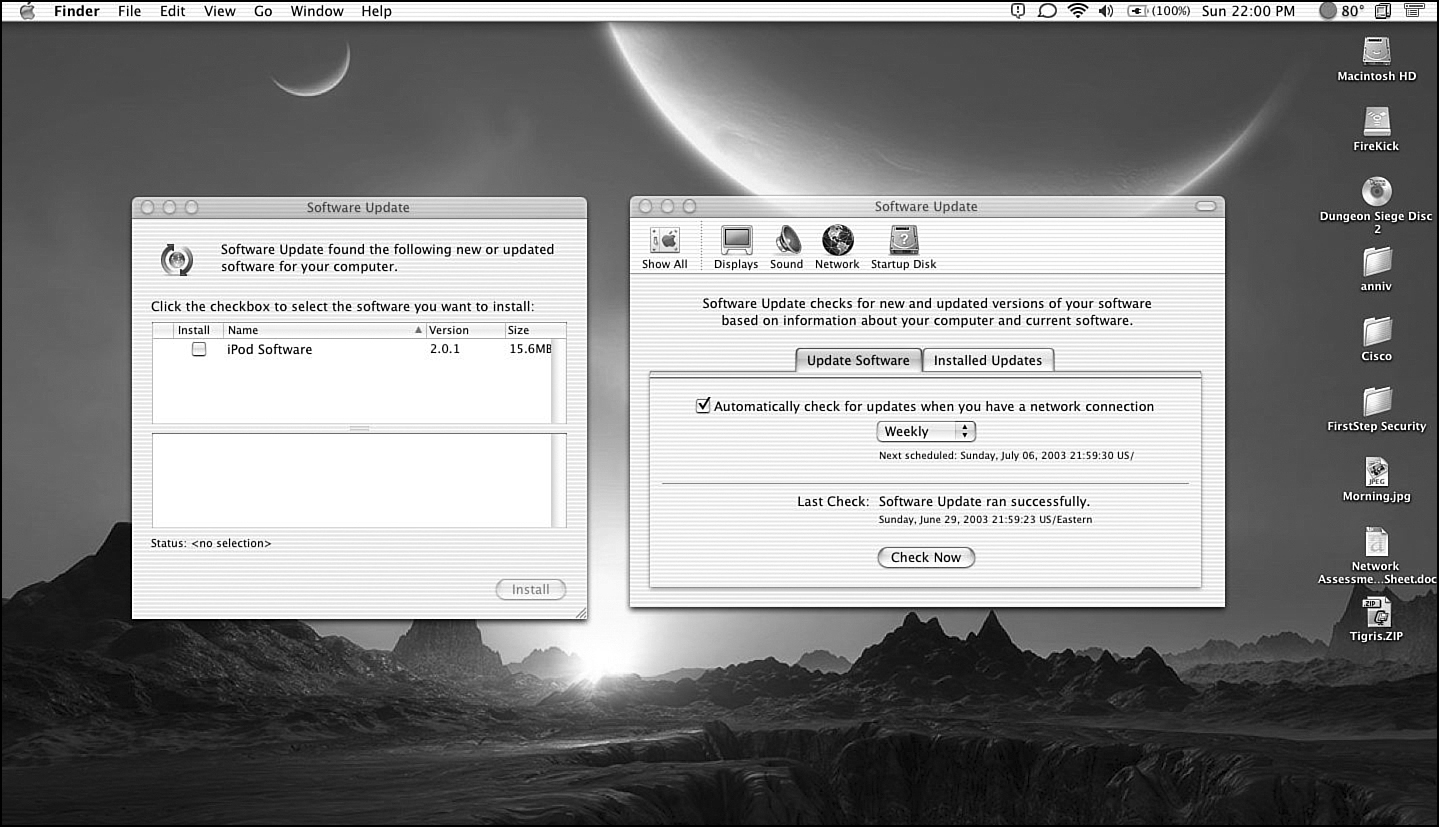
The only downside in this example is that I do not yet have an Apple iPod, which would require this update. Regardless, you can understand the point: Always make the time to check for patches for your systems because hackers are always pushing to find and exploit. For Windows users, Microsoft has also included this automatic update functionality in newer versions of its operating systems. The trouble is that Microsoft set the auto updates to occur at 3 a.m. by default. This is great if you leave your computer on 7x24, but if you’re like most people, you shut it off when done using it. The moral to this story is that auto updates are good, but be proactive to ensure that they are happening, and at the right time! Patches must also be tested before inserted into production networks, and not all systems are as patch friendly as others. You need to understand where your patches are coming from (in some cases they are hashed) so that you can be sure they are not malicious code masquerading as a patch to one or more of your critical systems. Apple handles updates in a more elegant manner, as shown in Figure 5-2.
• Incident Response Teams: Security concerns will inevitably be brought to you in some form or another. Perhaps your systems have become the target of an attack or you have detected that the compromise and damage has already been done. This aspect of design deals with how an organization responds to an attack and deals with whatever situation it experiences. It is best to include and consider incident response teams and the process of responding in practice rather than when you are under pressure and the situation is extreme. So, design it now; the benefits come later. Practice makes perfect, and dry runs can help point out a plan’s flaws that do not seem evident at the time the plan and policy is written.
These first-step security design considerations will enable you to understand how to begin securing any network. The next section begins to discuss the specifics of how you can use security technologies and their roles in protecting a network.
