Proxies and Application-Level Protection
Stateful packet inspection firewalls are enhanced versions of basic firewalls that just do packet filtering. The devices discussed here provide additional enhancements by analyzing the packets at the application layer. As you can see, we started with simple packet filters, added more advanced stateful packet inspection, and now we look even deeper into the packet at the application data contained within the packet.
You can use several types or technologies to provide application layer protection, and they are known by many different names. Although each technology operates slightly differently, their goal is the same: to increase the security of your network.
Application-level firewalls provide the most secure type of data connections because they can examine every layer in the TCP/IP model of the communication process. To achieve this level of protection, these firewalls—also known as proxies—actually mediate and control connections by intercepting and inspecting every connection. If the proxy determines that the connection is allowed, it opens a second connection to the server from itself on behalf of the original host, as shown in Figure 5-8. This sort of functionality is commonly seen when users surf the Internet; their computers talk to a proxy that, in turn, talks to servers on the Internet on their behalf.
Figure 5-8 Placement and Packet Flow of a Proxy
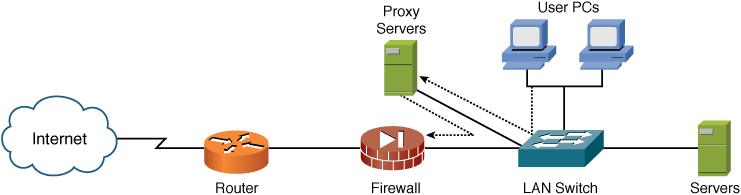
The data portion of each packet must be stripped off, examined, rebuilt, and sent again on the second connection. As shown in the list and in the following sections, different types of firewalls can be used to accomplish this:
• Standard proxy firewalls: A proxy firewall does not route packets; it simply forwards them, and it operates at the application layer of the TCP/IP model. Functionally, a proxy firewall receives packets from one interface, inspects the packets according to the defined rule set (perhaps access to porn is blocked), and passes the packets out to the firewall if the request is permitted (checking the weather). A connection is never made from the outside to the inside by PCs; as far as the PCs inside the firewall know, all their information comes from the proxy firewall.
• Dynamic proxy firewalls: Originally developed from the concepts described for standard proxy firewalls, a dynamic proxy firewall was designed to take the benefits of standard proxies and add the benefits of packet filtering. A dynamic proxy firewall performs a complete inspection of the packet; when a connection is first made and, after it is approved, the faster and weaker packet filtering mechanism handles all additional packets. To summarize, connections are first inspected at the application layer and then at the network layer.
Because these proxy firewalls have full visibility into the application layer of the TCP/IP model, they can look for more specific pieces of data than any other type of technology discussed thus far. For example, they can tell the difference between an email and Java data contained within a packet, as shown in Figure 5-9.
Figure 5-9 Proxy Packet Inspection
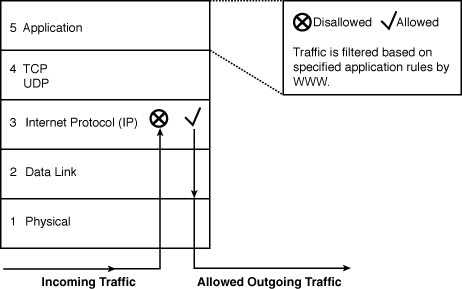
As the packet is inspected upon being received by the proxy server in Figure 5-9, all aspects of the TCP/IP header information is removed from the actual data and just data is inspected. The information gathered by this inspection would then be compared against the proxy server rules, and the packet would then either be denied or permitted based on this comparison. If the packet were deemed as something that should be permitted, the proxy firewall stores the connection information from the headers, rewrites the headers, and retransmits the packet accordingly. If the packet were denied, it would be thrown in the bit bucket. Often, the proxy gives users a web page stating why the website they were trying to go to is not allowed; for example, a reference to the Acceptable Usage Policy (AUP).
Note
Have you ever heard the phrase bit bucket? It is a lighthearted way of saying trash or garbage can. When saying that a packet is thrown in the bit bucket, this actually means that the router, firewall, or proxy has chosen to discard the packet; because all data is ultimately only bits (1s and 0s), this is proof that nerds have a sense of humor.
Limitations of Proxies
Hopefully by now you have realized that implementing any technology and especially security has limitations or drawbacks that you must consider. The folks that sell and market these devices would be thrilled if you believe that their new security gizmo is perfect for solving all your problems. Reality is frequently not the rosy picture they would like you to believe, and proxy firewalls are no different. Following are some of the limitations of proxy firewalls:
• Reduced performance: This thorough examination and handling of packets means that proxy firewalls are secure and generally slower than normal processing. Reduced performance could result because of the inspection of essentially every part of every packet being subjected to this level of security.
• Not always current: As new protocols and applications are developed, proxy servers must be expanded to recognize what is acceptable. This expansion means that, to stay current, new software must be developed and tested; this takes time and results in a security device that might not always be current.
From a security standpoint, the most secure firewall is a standard proxy firewall that inspects all traffic on an application layer. However, that is not always the most practical solution in many of today’s networks. Careful planning and understanding of the required network security and the traffic therein is important for developing a strong security solution. For example, a landscaping company has different security needs than a company that builds electronic components for the military. You should be aware of your application-level traffic through baselines and apply only the necessary security controls applicable to your baselined traffic until things evolve.
Of the two types of firewalls discussed—stateful and proxy—it is crucial that you use at least one of them as part of your layered approach to network security and defense in depth. Add to them the presence of packet filtering on your edge router and a firewall device that also uses NAT, and you will have developed the beginning of a layered defense. The following section examines how you can also use content filters to protect your network and its users.
