SNMP v3
Simple Network Management Protocol Version 3 (SNMP v3) is defined by RFC 3411–RFC 3418. It has primarily added security and remote configuration enhancements to SNMP. As of 2004, the Internet Engineering Task Force (IETF) recognizes SNMP v3 as the de facto standard version of SNMP. The IETF deemed it a full Internet standard, the highest maturity level for an RFC, and consider all previous versions of SNMP to be obsolete. The IETF cut them off like Michael Corleone said to his brother, “...you’re nothing to me now. You’re not a brother; you’re not a friend. I don’t want to know you or what you do....”
SNMP v3 is derived from, and builds upon, the original SNMP and SNMP v2. All versions share the same basic structure and components: managed nodes, an agent (software that runs on managed devices), and a network management system (NMS) (software that runs on the manager).
A managed node, or device, is a device that implements an SNMP interface that enables unidirectional (read-only) or bidirectional access to information specific to itself. Managed devices exchange node-specific information with the NMS. These managed nodes can be any type of device; examples are routers, access servers, switches, IP Phones, IP video cameras, computers, or printers.
An agent is a network-management software component that resides on a managed device. An agent has local device-specific knowledge of management information and translates that information into an SNMP-specific form.
An NMS executes applications that monitor and control managed devices. An NMS provides the bulk of the processing and memory resources required for network management.
Security Built In
SNMP v3 provides confidentiality, integrity, and authentication to the SNMP suite; confidentiality by encrypting the packets to prevent snooping by unauthorized personnel; message integrity to ensure that a packet has not been tampered with in transit from the managed device; and authentication by verifying the message is from a valid source.
Figure 6-7 and Figure 6-8 show the configuration of SNMP (versions 1 and 3) on the same Cisco ASA. Figure 6-7 shows the configuration of a basic SNMP v1 implementation, whereas Figure 6-8 shows the SNMPv3 implementation. The differences in the built-in security are quite extensive, as the figures reveal.
Figure 6-7 SNMPv1 Implementation/Configuration
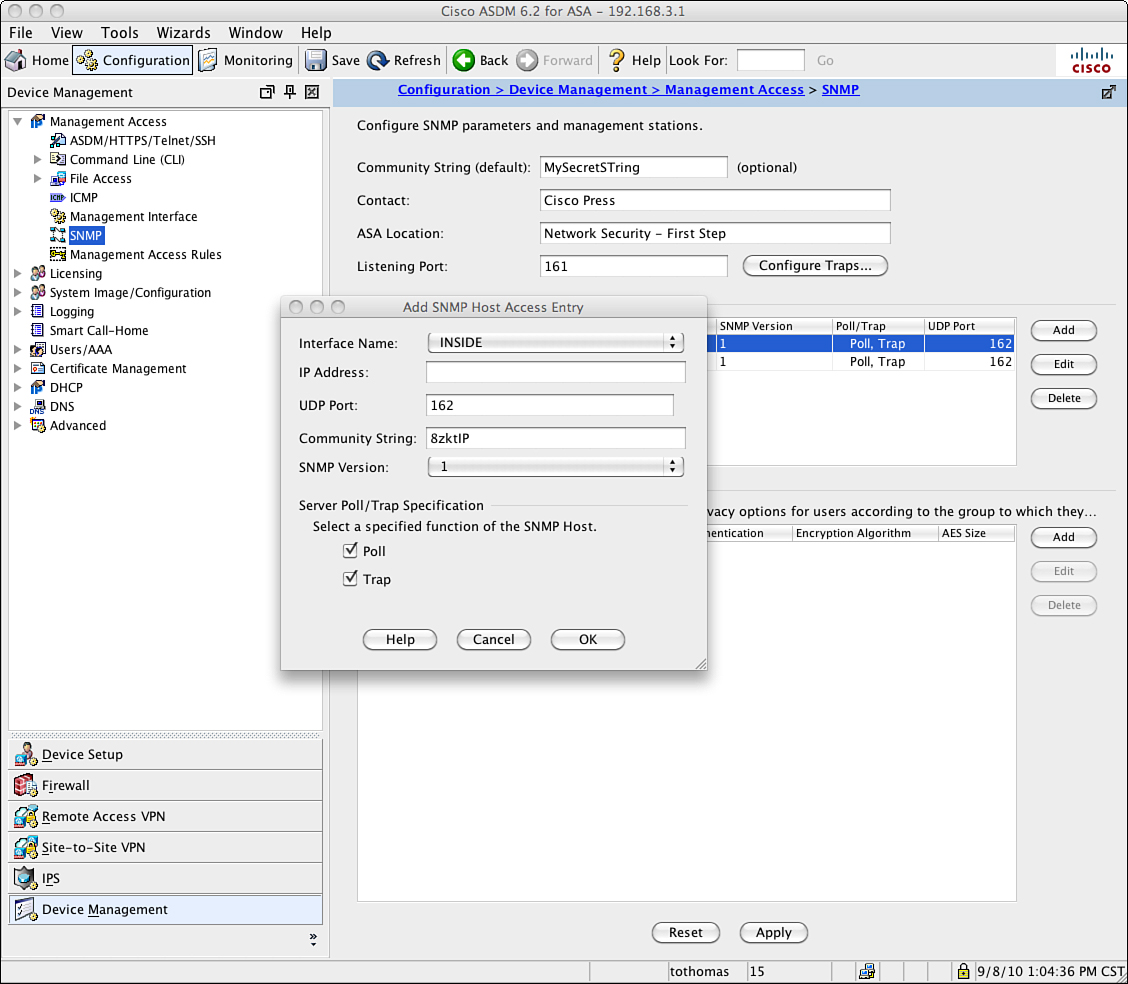
Figure 6-8 SNMPv3 Implementation/Configuration
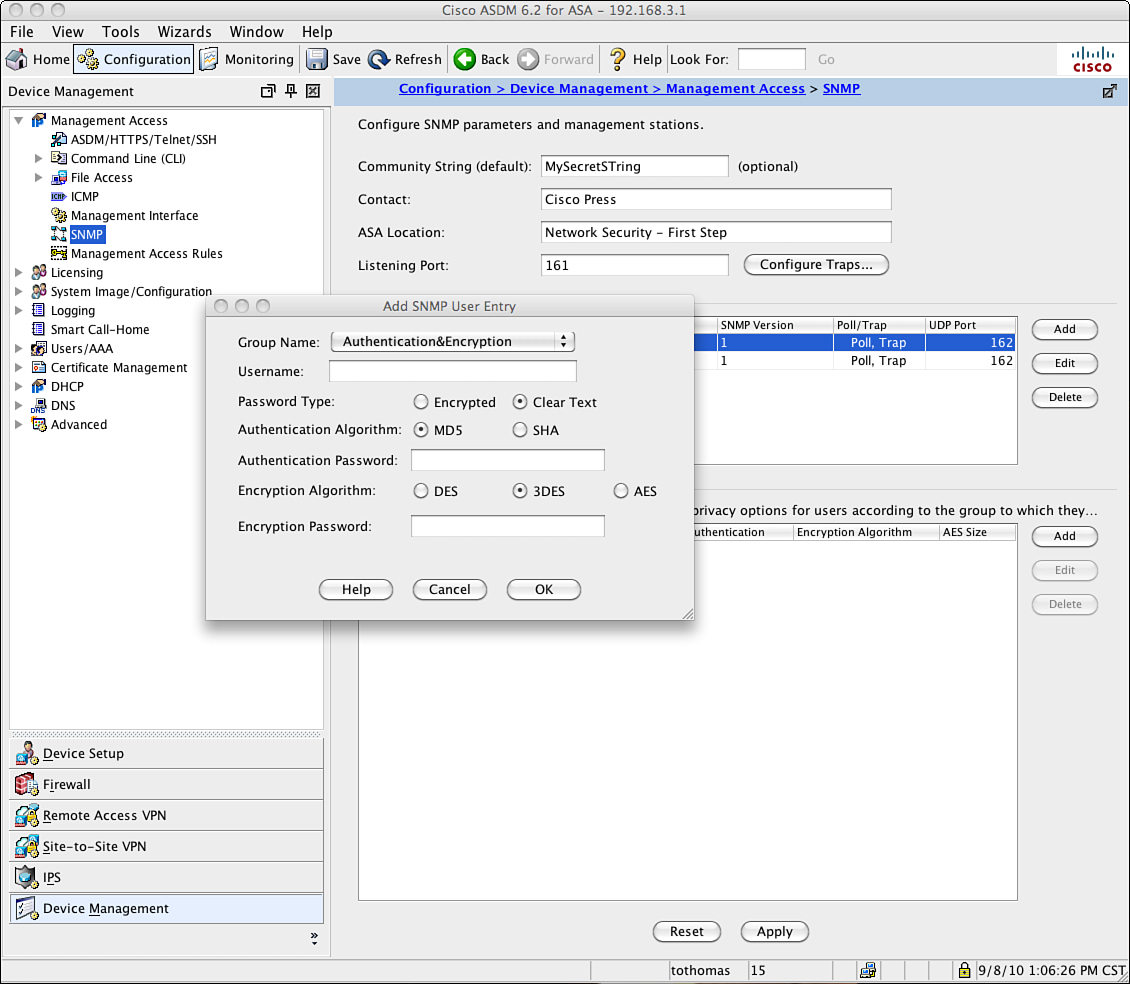
With the original version of SNMP, the most security that you could do was establish a different community string and port number. The hope was that the hacker trying to get into your network got distracted by something shiny. With SNMPv3 (see Figure 6-8) you have options to set up various authentication algorithms (MD5 and SHA) and then encryption algorithms for the transfer of data (DES, 3DES, or AES). As mentioned several times before, do not use DES. In this instance you want to use 3DES or AES. In this case, we have chosen to use 3DES. You also have the option to send your password encrypted or clear text—do not do this. Even though you set your authentication and encryption levels high, it is still highly suggested you encrypt your password.
Even with all the built-in security enhancements for SNMPv3, the protocol still has several security implications that you should be aware of:
• It is subject to brute force and dictionary attack tools for guessing the community strings, authentication strings, encryption strings, and encryption keys.
• It is mostly used over UDP, which is a connectionless protocol and vulnerable to IP spoofing attacks.
Our advice to you is to implement this protocol only if absolutely necessary. Otherwise, go into every device that you have and rename the public and private community strings and disable SNMP if you can—this is standard practice for all U.S. military and governmental agencies. This is a critical step for your company to consider and implement, making sure that it is supported in your policy infrastructure.
