Edge Router as a Choke Point
A choke point came to the world of networking courtesy of the Internet’s military heritage. A choke point refers to a single point at which everything will try to either enter or leave your network. A great example of this concept is the real history of the Battle of Thermopylae, which as portrayed in the movie 300 showed a narrow point, the pass of Thermopylae, aka The Hot Gates, being defended by a unified force of Greeks against an enormous Persian host.
In today’s world of network security, the term choke point means the edge router. The edge router is the single point from which the entire Internet gains access to your network. The router then is also a single point of failure, but that is an entirely separate discussion.
Edge routers that operate as choke points increase your network’s security by restricting the flow of data between your network and the Internet (or another network). A successful network security implementation of an edge router as a choke point is based on understanding what is happening in your network. This knowledge forms the basis of what should be used to filter network activity so that inappropriate activity can be identified. Network activity should be restricted to permit acceptable services only. Chokes provide a great way of implementing a coarse level of control and monitoring that can be fine-tuned using intelligent filters, such as proxy and stateful firewalls.
The value of edge routers configured as choke points is that they can prevent access to specific devices and applications in a performance-friendly way. This increase in security is typically provided through the use of standard and extended access control lists that can address traffic concerns at Layers 2, 3, and 4 of the OSI reference model. Because their performance does not normally suffer results from the fact that the router must read the contents of the IP packet anyway to make a decision on where to forward the packet. It does not take much more work to toss out the packet or permit it into the network.
The use of ACLs gives network engineers a high degree of control and filtering capabilities over packets traversing the router. Figure 8-2 demonstrates a common example of the rules and placement of an edge router. As a side note, can you figure out what network device is missing from this figure?
Figure 8-2 Edge Router as a Choke Point
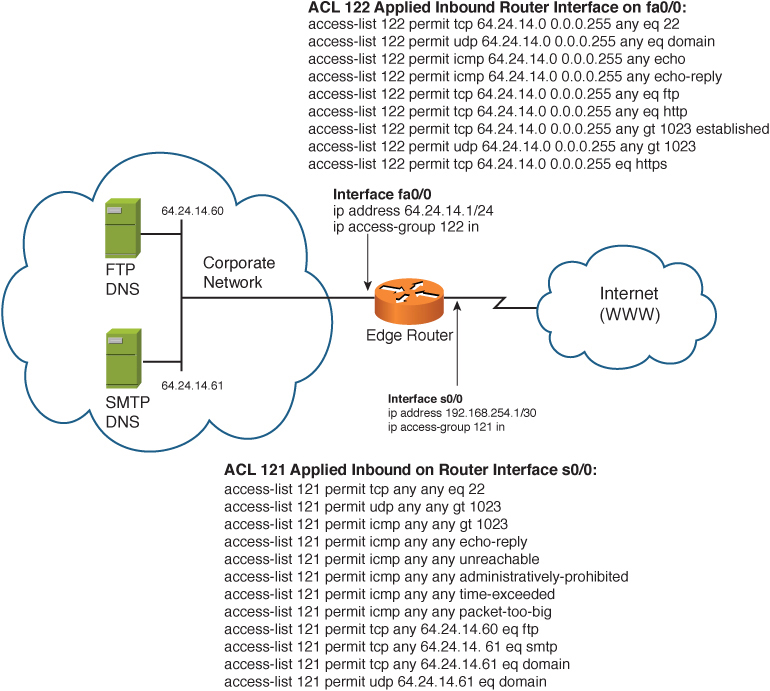
This edge router acting as a choke point into the corporate network permits only the following traffic into the corporate LAN:
• Inbound mail delivery to the email (SMTP) server at IP address 64.24.14.61.
• FTP file transfers to the FTP server at IP address 64.24.14.60.
• DNS (zone transfers via UDP and name lookup requests via TCP) to the DNS server at IP address 64.24.14.61.
• TCP and UDP traffic above port 1023 to allow outbound connections from the private network to function.
• Only specific types of ICMP.
• All other traffic is denied access to the edge router.
As a user on the corporate LAN, the edge router permits only you to establish connections out to the Internet as follows:
• SSH (TCP port 22)
• DNS (UDP port 53)
• FTP (TCP ports 20 and 21)
• HTTP (TCP port 80)
• HTTPS (TCP port 443)
The use of a choke point router to limit access (both in and out) for known services (below port number 1023) leaves the network largely exposed. Because the majority of today’s applications use ports above 1023 and not all IP stack and application implementations follow the 49152 through 65535 dynamic/private port guidelines, filtering above 1023 can affect the operation of applications that you want to function and, therefore, cannot deny this port range.
Did you discern what piece of equipment was missing in Figure 8-2? If you guessed a firewall performing stateful packet inspection (SPI) and network address translation (NAT), you were correct and are making progress toward becoming a security guru! But did you also notice that given the importance of email, you are not permitting it in your ACLs? Knowing whether a site needs or has email is important. Again, know the network’s traffic needs before you begin implementing any ACLs.
Limitations of Choke Routers
Choke routers are useful and can protect your network as previously demonstrated; however, they are only part of the solution and are likely to stop only a script kiddie or someone who has already read this book and understands that the network is not completely protected. Remember, this security is another layer the attacker must overcome. Some of the limitations of choke routers are as follows:
• Choke routers running regular IOS cannot look at the higher layers of the OSI reference model (Layers 5–7). However, use of enhanced IOS facilitates the use of Network Based Application Recognition (NBAR), which enables a router to detect and block many of the more common worms. You can find a useful article regarding this point at http://certcities.com/editorial/columns/story.asp?EditorialsID=76.
• Choke routers do not adequately address protocol and application security concerns; you would have no idea whether your connections were being spoofed.
• Choke routers can have the capability to perform Stateful Packet Inspection (SPI) based on zones; however, this might require upgrades to support this feature, which is found in Cisco IOS 12.4(6)T and later.
Although choke routers do not address the preceding concerns, they are quite valuable for implementing broad network and service access policies (that is, what users on the Internet can access).
Caution
Creating static ACLs require some thought and a lot of testing. A poorly written ACL can have adverse effects on the network in terms of performance and service availability. A strongly recommended practice is to write the ACL out on paper first to ensure that you have it designed to accomplish your filtering goals. Also, do not ask for help on your ACLs until you have repeated the mantra—there is an implicit deny all at the end of every ACL that the Cisco IOS does not display. The Cisco TAC will thank me for including that requirement because everyone forgets it—myself included!
