VPN Overview
A VPN is an encrypted network connection that uses a secure tunnel between endpoints via the Internet or other network, such as a WAN. In a VPN, dial-up connections to remote users and leased-line or Frame Relay connections to remote sites are replaced by local connections to an Internet service provider (ISP) or other service provider’s Point of Presence (POP). The increasing prevalence of Internet broadband connections to small remote offices and homes makes the use of cheaper access to the Internet attractive. As discussed, after the initial investment in VPNs, the cost to add more sites or users is minimal.
VPNs enable each remote user of your network to communicate in a secure and reliable manner using the Internet as the medium to connect to your private LAN. A VPN can grow to accommodate more users and different locations much easier than a leased line. Scalability is a major advantage that VPNs have over typical leased lines. Unlike leased lines, where the cost increases in proportion to the distances involved, the geographic locations of each office matter little in the creation of a VPN.
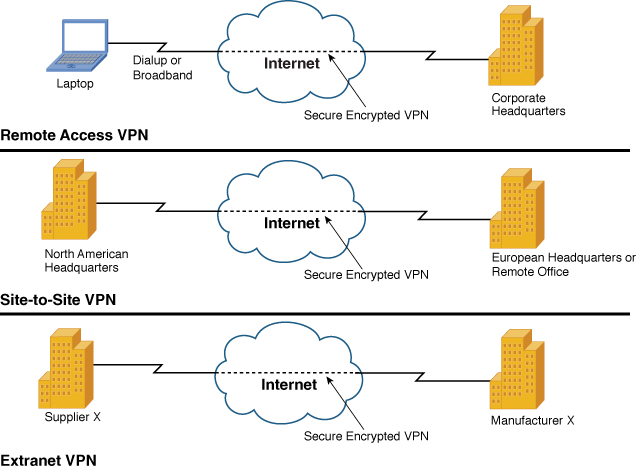
A VPN enables a private intranet to be securely extended through IPsec encryption across the Internet or other network service, facilitating secure e-commerce and extranet connections with mobile employees, business partners, suppliers, and customers. Following are three main types of VPNs:
• Remote Access VPNs: Enables remote users to securely connect to a central site across the Internet. This type of VPN is a user-to-LAN connection that enables employees who need to do so to connect to the corporate LAN from the Internet. Their systems use special VPN client software that enables a secure link between themselves and the corporate LAN. Typically, a corporation that wants to set up a large remote access VPN provides some form of Internet dial-up account to its users using an ISP. The telecommuters can then connect to the Internet and use their VPN client software to access the corporate network. A good example of a company that needs a remote access VPN would be a large firm with hundreds of salespeople in the field. Remote access VPNs are sometimes referred to as soft (as in software-based) VPNs, virtual private dialup networks (VPDN), or client-based VPNs. Some of the fastest growing uses of them are as follows:
• VPN-capable mobile devices such as smartphones or tablets.
• The Cisco VoIP CIPC (Cisco IP Communicator) SoftPhone application also works well over a VPN, turning your PC into a secure telephone.
• Site-to-site VPNs: Used to extend a company’s private network to other buildings or sites through the use of dedicated equipment so that remote employees at these locations can use the same network services. These types of VPNs are considered actively connected at all times. Site-to-site VPNs are sometimes referred to as hard (as in hardware-based) VPNs, intranet, or LAN-to-LAN (L2L) VPNs.
• Extranet VPNs: Enable secure connections with business partners, suppliers, and customers for the purpose of e-commerce. Extranet VPNs are a type of site-to-site VPN with the addition of firewalls to protect the internal network. A good example would be companies that work closely with suppliers and partners to achieve common goals such as supply and demand relationships—for example, when one company has a demand for supplies and the supplier fulfills the demand based on the company’s needs. Working across an extranet, these two companies can share information more quickly, and the firewall rules ensure that access is happening only to the shared resource.
All these VPNs aim to provide the reliability, performance, quality of service, and security of traditional WAN environments using lower cost and more flexible ISP or other service-provider connections. Figure 9-1 illustrates the three types of VPNs.
In Figure 9-1, all the VPNs use the Internet. You can also use VPN technology within your network to provide an additional layer of security to control access to sensitive information, systems, or resources. For example, you can use VPN technology to limit access to financial systems to certain users or to ensure that sensitive or confidential information is sent in a secure way. In this scenario, VPNs can encrypt and further secure traffic to sensitive systems. The following section discusses the placement of VPNs and the specific associated benefits.
VPN Benefits and Goals
A well-designed VPN can greatly benefit any company. Some of the benefits of implementing a VPN in your network include the following:
• Before the advent of VPN technologies, employees in remote locations would need to get an expensive connection such as a Frame Relay T1 to reach their company’s network. You might want to reduce telecom costs with local broadband connections to the Internet through which users use a VPN client. Depending on the number of employees in the field, this alone can be a huge cost savings. For many smaller companies with limited financial breathing room, VPNs can be a practical solution when remote access is needed.
• You want to increase the productivity of your users by enabling them to securely access network resources regardless of their geographic location.
• You want to reduce the operational costs associated with dedicated WAN connections by replacing them with direct Internet connections such as business class broadband, through which remote sites connect via a site-to-site VPN.
• You want to simplify your network’s topology by adding VPNs strategically throughout your network.
• You want greater flexibility in deploying mobile computing, telecommuting, and branch office networking; easier e-commerce and extranet connections with business partners, suppliers, and customers’ external Internet access; and internal intranet and extranet access provided using a single secure connection.
• You want to reduce office costs by having users work from home three days a week. Home users typically have higher production and less stress.
Before implementing a VPN, you should spend some time contemplating what you want to accomplish with your VPN. During this exercise, before choosing a solution provider or hardware and software, you should consider which features are most important. Security, which is mentioned later, is one of the most important features of your VPN.
Caution
It is possible to have unencrypted VPNs that rely on some other type of encryption or routing for security—for example, MPLS VPNs. Only under specific circumstances are these VPNs the appropriate solution for a network. Best practice dictates that you always encrypt your traffic over a VPN; failure to do so could be disastrous, and the responsibility will rest squarely on your shoulders.
VPN Implementation Strategies
VPN implementation strategies are extremely varied because every vendor these days has a “VPN solution” for you! Some of the solutions are what they claim to be, and others have raised concerns among the security community, as discussed in Chapter 8, “Router Security.” This section looks at some of the different potential components available from Cisco, and how you can use multifunction devices such as a Cisco Adaptive Security Appliance (ASA) to fulfill a VPN role:
• Firewalls: Firewalls are crucial to the security of your network. If you did not have a firewall in place before reading Chapter 7, “Firewalls,” you probably do now. Today, all Cisco firewalls support the combining of VPNs with stateful packet inspection (SPI). Solutions range from standards-based site-to-site VPNs leveraging the Internet Key Exchange (IKE) to IP security (IPsec) VPN standards. Cisco ASA firewalls encrypt data using 56-bit Data Encryption Standard (DES), 168-bit Triple DES (3DES), or up to 256-bit Advanced Encryption Standard (AES) encryption. Obviously, you want to use AES because it is the most secure! An amazing piece of technology, the Cisco ASA Firewall combines dynamic Network Address Translation (NAT), content filtering, stateful packet inspection, firewall, and VPN termination capabilities into a single piece of hardware. Instead of using Cisco IOS Software, the ASA has a highly streamlined OS that trades the capability to handle a variety of protocols for extreme robustness and performance by focusing on security services.
• VPN-capable routers: Cisco routers can be upgraded to have the capability to use VPNs. These upgrades come in some form of the following, depending on the router model in question: IOS, memory, or dedicated VPN hardware. You can gain some unique features with the provision of scalability, routing, security, quality of service (QoS), and dynamic multipoint VPNs. Based on Cisco IOS Software, there is a router suitable for every situation, from small office/home office (SOHO) access through central-site VPN aggregation, to large-scale enterprise needs.
• Client software: Simple to deploy and operate, the Cisco VPN Client establishes secure, end-to-end encrypted tunnels to the VPN devices listed here. With this thin design, IPsec-compliant software can be preconfigured for mass deployments, and the initial logons require little user intervention. The client software is available for the following operating systems: Windows 32 and 64 bit, Linux, Solaris, and Mac OS. Cisco has also worked with other manufacturers to include VPN software in many of today’s mobile devices.
Depending on the type of VPN (remote access or site-to-site), you must use specific software and hardware components to build your VPN. However, you should also consider the following:
• Manageability: Manageability of a VPN concerns the amount of effort needed to successfully maintain the established network connectivity. Specifically, PC Magazine rates manageability by the “ease-of-use factors for remote and local management options, including whether the device provides a browser-based interface or command line access” (PC Magazine, 2002).
• Reliability: Obviously, if the VPN software or hardware is unavailable when you need it, you are losing productivity and probably money. When choosing a solution, you should request up-time statistics for comparison and build a redundant solution if business needs dictate.
• Scalability: As a company’s business grows, so does its IT requirements. To quickly and cost-effectively grow your VPN infrastructure, you need to choose a solution that has scalability in mind. The last thing an IT manager wants to do is start from scratch and replace a VPN infrastructure because of a bottleneck in its growth potential.
When selecting the right device to provide VPN services to your network, you must be aware of the limitations.
Split Tunneling
Many VPN users are already behind firewalls, and they need to access resources only through a VPN. Traditional VPNs do not enable users to also access network resources on their local segment while they connect to their corporate VPN at the same time. This becomes an issue when, for example, these users must access a system via a VPN and print to a local network printer. To correct this potential problem, a feature has been introduced known as split tunneling.
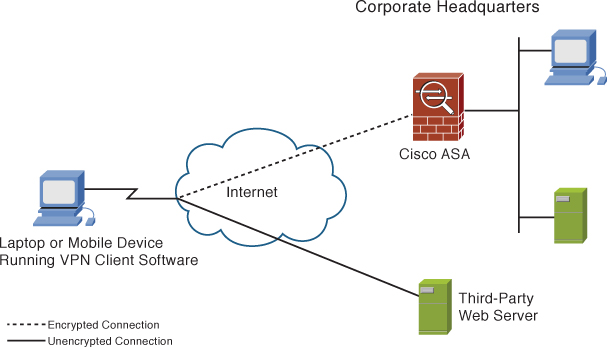
Split tunneling occurs when remote VPN users or sites are allowed to access a public network (the Internet) at the same time that they accesses the private VPN, without placing the public network traffic inside the tunnel first. This is not always the best feature to enable, however, because it could enable an attacker to compromise a computer connected to two networks. Figure 9-2 illustrates an overview of how split tunneling works.
Figure 9-2 Split Tunneling Overview