Dangers with Windows Password Attacks
What are the dangers associated with password attacks? Well, it is almost anything that you can imagine. Remember, passwords are designed to restrict access to information that only authenticated and authorized people are allowed access to. Passwords are implemented at many places within corporate networks. For instance, what if an attacker gained access to the password that protects customer data stored on a Microsoft SQL Server database? It is feasible that an attacker may be able to copy entire transaction histories, delete database contents, modify values, and ultimately cause serious service disruptions.
As part of an enterprise-wide risk assessment and identified threat scenarios, stakeholders must consider the threats facing the organization. This is going to be one of the best things your organization can do to help identify the dangers associated with successful attacks. Once a password attack is successful, organizations must consider the possibility of all confidentiality and integrity being lost depending on the scope of the attack and access gained. Depending on the contingency plan in place, mitigating controls, and the availability of reliable backup data, this impact can be great.
So far we have looked into a lot of the background about how Microsoft implements passwords and password security and how some types of password attacks may be conducted against Microsoft Windows targets. In the following scenarios, we will explore some of the common attacks that are performed by attacker to gain access to passwords and password hashes. You will also learn about some of the most common tools used to conduct these attacks and quickly be able to identify how dangerous these attacks can be. Some of the tools we will be using during these scenarios are listed in Table 1.2.
Table 1.2. Windows password cracking tools
| Password cracking and attack tools | |
|---|---|
| John the Ripper | Ophcrack |
| RainbowCrack | Cain & Abel |
| Fgdump | Hydra |
| L0phtcrack | |
Although the tools listed in Table 1.2 are some of the most popular tools in use today, it is important to understand many more tools are available. In some cases, tools are developed for very specific tasks and password attacks depending on the attackers' goals. Password cracking tools, logon crackers, and tools used for enumeration are widely available, and as new protocols and services are developed, you can be certain more tools will be developed.
Scenario 1: Obtaining Password Hashes
Mark is a long-time employee for a factory that manufactures and sells sporting equipment and cool gear for fans of football and various other sports. The company has done a great job with keeping employees happy and motivated with some great benefits and super discounts on equipment and memorabilia. However, as it approaches the final weeks of football season and the big game nears, it turns out sales have been increased more than ever before. This causes upper management to start requiring overtime so the company can keep up with customer demand. Unfortunately, Mark learns he and his friend Ross have to work late on Sunday and will be missing the big game.
Mark finds this very disturbing and decides to take his frustrations out on his manager. Mark is a computer enthusiast who enjoys learning things on his own; as a matter of fact, over the last few weeks he has been fascinated about getting administrative access to computers by using publicly available exploits. At first, he just tested systems in his home to see how this whole “buffer overflow thing” works, but after he learned the power he could have, he was hooked.
During one of his late night shifts at the warehouse, Mark jumps on his computer and installs a few hacking tools he is familiar with. One of these tools is an open-source framework called Metasploit. After identifying that his boss's computer is missing multiple operating system patches, Mark decides to configure Metasploit to use an exploit and payload that will allow him to leverage one of the vulnerabilities he identified.
As you can see in Figure 1.1, Mark was able to exploit his boss's computer system and open up a remote session so he can perform some further exploration. Since Mark still does not know his boss's logon credentials, he decides to use Metasploit to obtain a copy of the password hashes stored on the system.
FIGURE 1.1. Obtaining Hashes with Metasploit
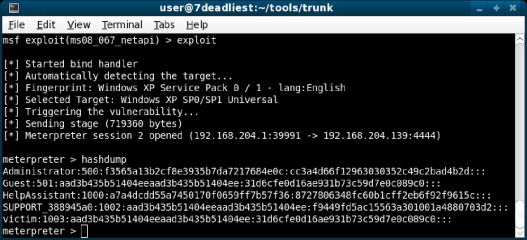
Mark then takes the passwords home with him and cracks them offline to obtain the plain-text passwords. Once the plain-text passwords are obtained, Mark can use them as he likes. It is important to note that in this case, as shown in Figure 1.1, Mark has been able to obtain the passwords not only for his boss's account, appropriately named “victim,” but also for the local “Administrator” account. This provides Mark with full control over the computer as well as over his boss's account.
The next day Mark goes in to work for his night shift at the warehouse and decides to log into his boss's computer and crafts an e-mail to the entire company, stating: “All employees who are working on the day of the big game will be paid triple overtime and receive three extra vacation days for your hard work and devotion.”
Okay, so Mark wasn't as malicious as he could have been, but I think we can understand how easy it was for him to pull off this attack. Although the attack itself is not necessarily glamorous, it is an effective way for attackers to gain a foothold within your organization. Once an attacker has identified vulnerabilities where exploits can be used to gain access to the operating system, it takes very little time to obtain information that can be used for further attacks. In this case, our attacker compromised the computer system and was able to obtain and crack the password hashes from the compromised system.
Scenario 2: Pass the Hash
In the last scenario, we explored the possibilities of gaining access to system passwords by leveraging an unpatched vulnerability in a Microsoft operating system. By leveraging the vulnerability, Mark was able to gain access to the password hashes, take them home, and crack them offline. Moreover, Mark was able to return to work later in the week and use the cracked passwords to gain access to and send malicious e-mails from his boss's e-mail account. This seems like a lot of work for an attacker to go through, doesn't it? Cracking passwords can sometimes take a few seconds, but in many cases it can take hours; there must be a simpler way.
Thankfully, the team over at Metasploit has implemented the ability to use previously captured password hashes for follow-on attacks as part of the Metasploit framework. Let's assume, instead of Mark taking his boss's password home to crack offline, he simply wants to gain access to other people's computers and snoop around a bit. Using the windows/smb/psexec exploit, Mark is able to use the password hashes he has already obtained against other computers in the network.
Wait a minute! “That is silly!” you say. People aren't supposed to reuse passwords between systems.
Correct you are. However, to simplify administration of computing systems, many administrators reuse passwords so they can make more efficient use of time or to provide a sense of consistency within the network environment. Since Mark is a pretty smart guy and he has been reading up about password attacks, he knows there is a very strong chance the Information Technology (IT) department is reusing passwords.
In Figure 1.2, the attacker has configured Metasploit to use the windows/smb/psexec exploit with the windows/meterpreter/bind_tcp payload. In Additionally, he has set the target to be a computer on the network with the IP address 192.168.204.129. The attacker then sets the SMBPass option to the value of the Administrator account hashed password he obtained in Figure 1.1. After the exploit and payload is ready to go, the attacker uses the exploit command to attempt gaining access to the other computer on the network. Success!
FIGURE 1.2. Configure Metasploit for Pass the Hash

On the last line of the output from Figure 1.2, you will notice a meterpreter session has been opened and the attacker can now perform whatever action he wishes under the context of the credential he used in the attack. In this case, it happened to be the Administrator account, which will give him full control over the target system.
After some poking around, he is able to determine the system he is logged into appears to be an SQL server as shown in Figure 1.3. Furthermore, the system is a Windows 2008 server with Service Pack 2 installed.
FIGURE 1.3. Successful Pass the Hash Attack

The attacker has been able to fully compromise an otherwise secure host by reusing local administrator credentials obtained from another system on the network. From this example, what are the primary reasons for failure?
- Unpatched systems allowed the attacker to gain a foothold within the network.
- Password reuse between systems allowed the attacker to gain additional access within the network.
Steps to reduce the likelihood of this type of attack are covered in the section “Defenses against Windows Password Attacks.” But overall, it should be pretty clear that missing patches and password reuse can be a very deadly combination when faced with these types of threats.
Scenario 3: Timed Attacks to Circumvent Lockouts
We discussed the use of password and lockout policies earlier in the section “Password and Lockout Policies of this chapter Policies.” Part of the discussion explained how different policies and procedures can help reduce the probability an attacker will be successful with password guessing and dictionary attacks. Figure 1.4 displays some of the password policy options discussed earlier and an example of a poorly configured policy.
FIGURE 1.4. Ineffective Lockout Policy

In this example, we see there is no password lockout policy implemented, meaning an attacker can conduct exhaustive attacks against the system without ever locking the account being attacked. Of course, attacks such as these should cause a lot of logs to be generated due to failed logon attempts, which would normally notify administrators of suspicious activities. However, from experience gained while performing penetration tests, all too often logging is not implemented or reviewed. In as such, there is a very good change an attack such as this is not noticed until far after the attack has taken place.
“But my network has a lockout policy in place. So, I am safe,” you say. Well, let's not get too far ahead of ourselves here. Let's assume you have implemented a password and lockout policy with the following settings:
- Account Lockout threshold: five invalid logon attempts
- Account lockout duration: 30 minutes
- Reset account lockout after: 30 minutes
This policy will allow up to a maximum of five failed logon attempts before the account is locked. Once locked, it will remain locked for a period of 30 minutes, at which time it will be unlocked and further logon attempts can be made. In the event multiple logon attempts are made but the account is not locked out, the lockout counter will be reset to 0 after 30 minutes.
This policy is certainly better than the policy depicted in Figure 1.4 but still vulnerable to password guessing and dictionary attacks. Scripts exist that allow attackers to define the number of password attempts to try before stopping and waiting for the “Reset account lockout counter after” timer to expire. Why would an attacker use such a script?
Even though many times event logs are not reviewed and attacks may go unnoticed, administrators can be tipped off to an attack by an increase of calls to the help desk due to users complaining about their accounts being locked out.
Using a script to automate several attempts every 31 minutes will allow attackers to make continuous attacks without locking out accounts and reduce the odds an attack is detected. In the example, if the lockout threshold is five and the “Reset account lockout after” time is set to 30 minutes, an attacker will be able to guess one to four passwords every 31 minutes without raising too much suspicion. With a well put together password list, a successful logon may be possible in a fairly short amount of time.
Scenario 4: LSA Secrets
After an attacker has gained access to a system, he may attempt to find information stored in other places on the system. This may include browsing the file systems and attempting to find documents with additional credentials.
Earlier in the section “Windows Passwords Overview,” we discussed how LSA secrets can store information about services and passwords that may be stored in plain text. Figure 1.5 depicts an attacker who has used Cain & Abel to access the LSA secrets stored on a system.
FIGURE 1.5. LSA Secrets with Cain & Abel
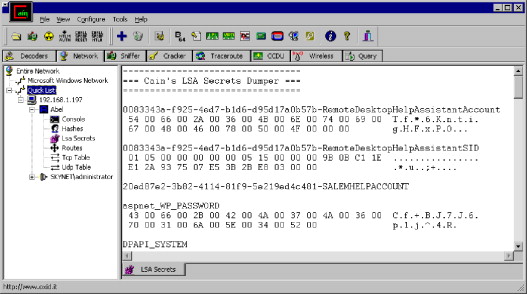
This tool not only provides access to the LSA secrets stored on a target system but also obtains the current password hashes as well as the password history for past passwords. Cain & Abel will dump all of the LSA secrets stored in the registry and display them in an easy-to-read format.
Future of Windows Password Attacks
As demonstrated by the previous attack scenarios, Windows password attacks have been a staple of gaining access to Windows operating systems and Active Directory domains for a very long time. Although Microsoft continues to improve its implementation of password security mechanisms and address weaknesses by way of reducing the presence of weak default configurations, these types of attacks are not likely to disappear anytime within the near future.
Part of the reason the attacks will remain fruitful for attackers is because sometimes administrators are forced to pick functionality and convenience over security. Although this may not always be due to the decision of administrators, but pushed upon them from management and other business influences. Excessive password policies may cause additional overhead and loss of productivity for business units. This is usually something noticed by upper management and may result in modifying policies to be more flexible, ultimately reducing the effectiveness of some password security initiatives. The payoff of such modification is financially driven and not always in the interest of robust security initiatives.
Lack of awareness of the impact password attacks can have is also another reason password attack will be successful for many years to come. In some cases, administrators, Chief Information Officers (CIOs), Chief Security Officers (CSOs), and other members of the organization may not really understand what is at risk and what kind of damage a successful password attack can cause. Investigating real-world threats and understanding current attack methodologies is an important part of identifying the types of controls needed to implement an effective defense.
