Defenses Against Windows Password Attacks
As with most technologies available today, there are many types of defensive measures organizations can take to help prevent password attacks. In addition to some of the defensive measures discussed in the following paragraphs, even more resources are available at the Microsoft TechNet[M] Web site. A combination of many of the defenses discussed will help protect your organization against unauthorized access.
Implementing security from a password perspective is probably one of the most critical decisions an organization can make. If passwords policies are too strict, employees will start writing down passwords and storing them in weak areas. Additionally, help desk calls will increase due to users locking out accounts due to failed logon attempts or requests to have passwords reset as sometimes people tend to forget usernames and passwords when they are expected to remember too many. On the other hand, if passwords and password policies are too weak, attackers will be more successful and will have an easier time gaining access to valid account credentials. In this section, we explore some of the considerations for implementing password policy program and other controls to help reduce the risk of password attacks.
Defense-in-Depth Approach
Implementing defensive mechanisms in layers helps reduce the likelihood of a successful attack against your organizations' assets. Although many password-based attacks are conducted directly against operating systems, a good defensive network posture can mitigate many of the direct assaults against these assets. By implementing various controls at the desktop and throughout the network, attacker advances can be severely impeded. These concepts are often referred to as defense-in-depth and have been an industry-recommended approach to security for many years. Protecting company assets should not stop at the border router or firewall but be implemented at multiple layers and points deep within the network and reaching all the way to the user's desktop.
To relate to the concept of defense-in-depth as it applies to network security, we can compare similar concepts used for implementing physical security at your local bank or credit union. One of the first things many people may notice when driving on to bank or credit union property is the strategic deployment of Close Circuit TV (CCTV) systems for monitoring and recording activities. These cameras usually monitor entrances to the bank property, drive-through lanes, building entrances and exits, and the parking area. CCTV systems are usually implemented to record activities for later review in the event a security incident occurs. As compared to the network security plan, these would be equivalent to Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) providing early detection of suspicious activities alerting administrators of pending attacks.
Another defensive control we may notice when entering a bank is that the doors are built of quality material and have latch protection in place to prevent tampering with the latch mechanism. This is considered the external protection that prevents users from entering the bank unless the bank is open to service customers during normal hours of operation. The locks may also access cards, pincodes, and proximity devices to further restrict access. This would represent something similar to an organization's border routers and firewalls. These types of controls not only detect possible attacks but can also prevent attacks in real time by blocking suspicious traffic, similar to entrances at the bank.
The next layer of defense we find within the bank or credit union deals with internal controls. Additional CCTV systems are usually deployed within the banks to detect malicious activities that may be occurring within the secure perimeter. Just as insider attacks can occur at banks, they can happen on your network. This is one of the reasons it is important to implement IDS and IPS monitoring systems inside your network in addition to outside the network perimeter.
Finally, additional controls are implemented inside the bank to protect employees, customers' assets, and other valuables. These may include door with access controls between the customers and the teller line, a vault door, and keys for access to safety deposit boxes. Within a network environment, these may be internal firewalls, multifactor authentication, logical access controls, desktop antivirus software, firewalls, and host-based IDS implementations.
These examples provide some interesting views on how a defense-in-depth methodology can impact the security of your network and significantly reduce the rate at which an attacker can move undetected within your organization. It is important not just to deploy a defense-in-depth architecture but also to review its effectiveness and its design on a regular basis. Why is this important? Because the threat landscape is constantly evolving and what was effective a year ago may not still be effective today. Additionally, security is a process and not a product. We as security professionals cannot walk into our favorite security hardware supplier and ask for a product that will protect all aspects of our environment. Each layer of security adds to the overall security of your network and assets. Now that we have explored what defense-in-depth is we can focus our attention on specific defenses helping reduce the likelihood or successful password attacks against Microsoft operating systems.
Microsoft and Third-Party Software Patching
Software is developed by humans, and humans are not exempt from making mistakes that can have disastrous consequences. Developing software frequently involves many lines of code and development efforts may include a single individual or large teams of developers who are trying to breathe life into a new application. Every organization has a different process and methodology for developing and managing code and different requirements for quality assurance and verifying the quality and how secure the written code actually is. Many times the number of errors can be compounded by the eagerness to bring new applications to market for increased revenue, for business advantage, or for the sake of satisfying customer demand.
One of the easiest avenues for an attacker to take for gaining unauthenticated access to systems is by leveraging previously identified and undisclosed vulnerabilities. These vulnerabilities allow attackers to bypass authentication all together, and depending on the level of access obtained from exploiting the vulnerability, an attacker may be able to obtain LM and NT hashes that can be used against other systems that may otherwise be secure.
This is a primary reason it is vital to ensure a proactive patch management policy and procedure is developed and followed. Administrators have access to many tools to ensure systems and software packages are patched as new vulnerabilities are identified. Some of these tools may be managed by Active Directory group policies, such as the Windows Server Update Services[N] (WSUS) offering from Microsoft. Another alternative is Systems Management Server[O] (SMS) or the next generation of this product called System Center Configuration Manager 2007.[P]
Ntechnet.microsoft.com/en-us/wsus/default.aspx
Owww.microsoft.com/SMServer/default.mspx
Pwww.microsoft.com/systemcenter/configurationmanager/en/us/default.aspx
It is not enough to ensure the Windows operating system is patched; third-party software is also vulnerable to exploitation. Depending on what level of privileges the third-party software is running under, an attacker may again be capable of obtaining access to password storage. Ironically, some third-party software installed on systems intended to provide protection, such as backup software and antivirus software, have also been identified as having vulnerabilities in the past.
Organizations must closely track what software is installed on their networks, as well as the patch level of the software. It is a very good idea to determine if third-party software is capable of providing notification of new software releases to administrators. Administrators must be proactive in testing and ensuring patches are implemented quickly to reduce exposure to threats.
Part of reducing the complexity of maintaining applications involves ensuring policies are distributed to employees to explain why installing random software downloaded from the Internet is not allowed. Enforcement of the policies and education of end users will help reduce the avenues of attack. Always ensure technical controls are implemented to help detect and prevent applications from being installed without formal review and approval of the administrator and security staff.
Logical Access Controls
Another way organizations can help prevent successful password attacks is to limit access to and the amount of administrative and authentication interfaces available and restrict access to the interfaces from authorized locations. For instance, if a Windows server has Remote Desktop enabled for administration, only specific IP addresses or ranges of IP addresses should be allowed to connect to the Remote Desktop service for performing maintenance. This helps reduce the attack surface and limits the types of attacks an attacker can perform.
These types of controls can be accomplished by implementing access control lists (ACL) on firewalls and routers. Implementing management subnets and Virtual Local Area Networks (VLANs) can also provide another form of segregation of management, production, voice, and user networks.
Logging Security Events
In Scenario 3: Timed Attacks to Circumvent Lockouts, we explored an attack that should have caused a lot of logs to be generated due to failed logon attempts. Many times, organizations do not spend enough time implementing detective controls as it applies to tracking access and logon violations. Logging is an important part of security that allows administrators to be notified of potentially dangerous attack against its network and assets. Logging once properly configured and implemented can also help an organization by reducing the reaction time from when an attack begins and when an administrator is notified and can deploy countermeasures. Reducing the active attack window is vital to helping preserve the stability and integrity of the network.
When implementing a logging initiative, it is vital to ensure usability of the logging system and redundancy. System logs should be configured to log critical security events to centralized and redundant servers. Logging and time stamping logs to a centralized server can help ensure logs are able to be viewed in the event an attacker attempts to clear the local system logs. Time stamping logs and using a synchronized time server on network hosts may allow administrators or forensic analysts to trace the attacker's steps back through the network to help identify the initial breach point.
Lastly, implementing logging is not something that is done and forgotten about. Administrators should constantly be making adjustments to the logging system to reduce logging traffic that can be considered “white noise.” White noise is where too much is being logged and administrators cannot make heads or tails of all the data presented to them via the logging system. Situations may exist where so much logging is done that it actually camouflages the attacker's efforts. Ensure logging is implemented, but make sure it does not cause more harm than good.
Implementing Password and Lockout Policies
Implementing customized password and lockout policies can be one of the best things an organization can do to prevent successful attacks. As discussed earlier in the section “Password and Lockout Policies,” the importance of implementing a solid overall policy can significantly reduce successful password attacks if implemented properly.
There is no single solution for defining a password and lockout policy that will work for every organization; however, following some best practices can get your organization headed in the right direction. Table 1.3 provides an overview of some good suggestions for organizations to consider.
Table 1.3. Policy recommendations
| Enforce password history | 10 passwords remembered |
|---|---|
| Maximum password age | 45 days – may be shortened or lengthened depending on how often the password is used and the sensitivity of the data accesses with the password |
| Minimum password age | 7 days |
| Minimum password length | 10–15 characters – be prepared for higher help desk call volumes and passwords to be written down if a lengthy password is required |
| Password must meet complexity requirements | Enabled |
| Account lockout threshold | 3–5 failed attempts |
| Reset account lockout after | 8 hours – may be shortened or lengthened depending on how often the password is used and the sensitivity of the data accesses with the password |
| Account lockout duration | 8 hours – may be shortened or lengthened depending on how often the password is used and the sensitivity of the data accesses with the password |
For some further descriptions and of insight behind some of the logic behind password security and recommendations, additional reading can be found at Microsoft's Web site.[Q]
Qtechnet.microsoft.com/en-us/library/cc784090(WS.10).aspx
Disable LM Hash Storage for Domain and Local Systems
As discussed earlier in the section “Windows Passwords Overview,” there have been numerous weaknesses identified in LM hash password storage. Administrators may consider configuring Active Directory and SAM databases from storing the LM hashes altogether to help with limiting the success of password attacks against password storage mechanisms.
Before administrators can configure policies to modify registry settings, an analysis should be performed to determine what type of impact disabling LM hash storage may have as far as backward compatibility is concerned. The three primary methods of preventing the storage of LM hashes are to require passwords that are of 15 characters or longer, implementing a domain policy that prevents the storage of LM hashes, and modifying the registry to implement the NoLMHash policy.
SYSKEY Considerations
Depending on the network and its administrative practices, it may be a good idea to enable some of the advanced configuration options within SYSKEY. Figure 1.6 depicts the initial window presented when running the SYSKEY command from the Windows command prompt.
FIGURE 1.6. System Key Configuration

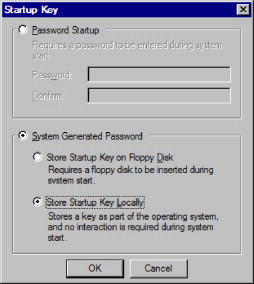
Figure 1.7 displays some of the advanced options that are available to help protect access to the system hashes. Some of the options require additional passwords to be provided during the start-up process and the use of a floppy disk during system startup. In some cases, if SYSKEY is implemented locally, it is possible to boot the operating system using reset disks to change or remove passwords for local user accounts including the local administrator.
FIGURE 1.7. System Key Options
For full details on how to configure SYSKEY on systems, please refer to the Microsoft Support Web site.[R]
Rsupport.microsoft.com/kb/310105
Summary
This chapter provided you with a strong understanding of how Microsoft's Windows operating systems handle and store passwords within the local computer and in Active Directory. Understanding how LM, LM hashes, NTLM, SYSKEY, SAM, and password policies work will provide you with the information needed to start developing a solid foundation for password security.
During our discussion of the dangers associated with password attacks, we explored several scenarios to illustrate how some of the attacks can be performed and what type of data an attacker can obtain. Though only a few scenarios were presented, you should have a good understanding of how the attacks can be performed using various methods. Password attacks are not always just about trying different passwords and usernames, but can be very fine tuned depending on the situation presented to the attacker. These attacks are made easy by the use of several well-known tools as listed in Table 1.2.
In our discussion of how to protect your organization against password attacks, we took a look at implementing defensive controls by using defense-in-depth techniques. We also explored some of the recommended guidelines as provided by Microsoft documentation and how certain steps can reduce the likelihood of an attacker being successful at password attacks and obtaining valid credentials.
