In NetScaler environments, RADIUS is commonly used for two-factor authentication, and is the protocol to choose when integrating with One Time Password (OTP) servers.
The ports used by Radius are as follows:
- UDP 1812: Authentication
- UDP 1813: Radius Accounting
- UDP 1645 and 1646: Legacy ports for the same purpose that some servers might use
When authenticating, the exchange will start with an access-request from the NetScaler to the RADIUS server. To this, the server can respond with one of three responses, given as follows:
- Access-Accept: All is good and the User is through
- Access-Reject: Either the RADIUS server parameters, such as the secret, are not configured correctly, or the User credentials are incorrect
- Access-Challenge: This is what you will see when using an OTP solution, the NetScaler has received a prompt for additional credentials
The following is a screenshot of a successful RADIUS (Access-Accept) authentication:

aaad.debug again proves handy in the case of RADIUS troubleshooting:
The IP, shown in the preceding screenshot following @, will be that of the radius server. This will then be followed by the result, such as sending accept or sending reject:

If the server settings are misconfigured, you will see something like the following screenshot. The 4003 indicates that the server did not respond in a timely fashion:
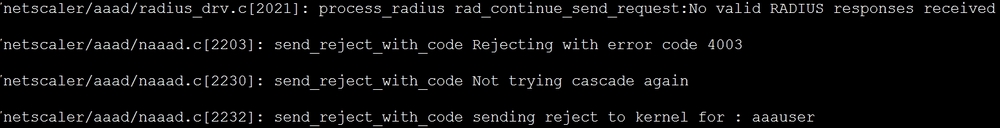
Error code 4003 is just one of several possibilities. The following table, taken from one of the Citrix blogs, covers a more complete list of error codes:
|
Error Code |
Definition |
|---|---|
|
4001 |
Invalid credentials |
|
4002 |
Login not permitted |
|
4003 |
Server timeout |
|
4004 |
System error |
|
4005 |
Socket error talking to authentication server |
|
4006 |
Bad (format) for username |
|
4007 |
Bad (format) for password |
|
4008 |
Password mismatch (when entering new password) |
|
4009 |
User not found |
|
4010 |
Restricted login hours |
|
4011 |
Account disabled |
|
4012 |
Password expired |
|
4013 |
No dial-in permission (RADIUS-specific) |
|
4014 |
Error changing password |
|
4015 |
Account locked |
Source: Enhanced Authentication Feedback on https://www.citrix.com/blogs/
The enhanced authentication feedback is an option to show the RADIUS error to the end User as part of the authentication process, but this is not enabled by default as it might provide too much information, in general to an attacker regarding what is failing. You can enable this using the following command:

