Bad things happen, whether accidentally or on purpose, and we want to protect our MariaDB database against both. Threats come in many different forms and come from many different places, including—but not limited to—physical threats, filesystem threats, network threats, and user threats.
The topics that we will cover in this chapter include the following:
- Security layers
- Securing MariaDB in 10 seconds
- Connecting safely
- Server security
- Building security
- Internal network security
- Internet security
You can think of the data in your database as being at the center of a set of rings, as illustrated by the following figure:
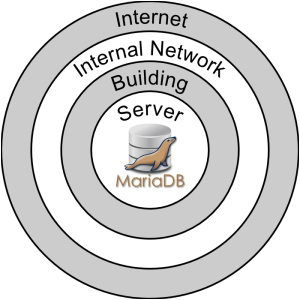
The outermost ring is the Internet. This is the outside world. If we are running a business, this is where our customers are. It's also where many attacks originate.
The next two rings are our Internal Network and the Building where our MariaDB database server is located. Internal corporate networks can span several buildings, but if we're a small business or a hobbyist, the network might just be a single building or even a room or two inside a building or a house. We need to be as careful regarding the security on our internal network as we are on the external Internet, especially seeing as more attacks come from inside networks than from the outside world.
Physical security is also important. If an attacker can simply walk in and take the server or computer where our MariaDB database is present and walk out with it, none of our network and other security measures will mean anything. It's trivial for an attacker to gain access to our data if they have physical access to the machine.
The next ring is the Server on which MariaDB is running. Questions that we should ask about security on the server include things like, "who can log in?", "where can they log in from?", "who has the administrative rights?", "does it have monitoring and backup systems in place so that we can keep an eye on it?" The answers to all of these questions depend on factors that are beyond the scope of this book, but we should try to find out the answers.
For example, if you know that only three other people have login access to the server, we could tighten up security to a level—such as requiring SSH keys to login—that might be unacceptable on a server that has hundreds of users or is shared with other departments. Knowing who the administrators of the server are is useful because we want to know who to call if something goes wrong. It's the same for the backup and monitoring systems; we need to know where they are and how to access them because if we don't, they won't be of much use to us when a problem occurs.
Now we're inside the server and have come to the center of the rings—the MariaDB database itself. If it looks like MariaDB is sitting right at the center of a bullseye, that's because it is. Security starts here and there's no better time to secure our MariaDB installation than right now. We'll begin by working our way from the inside out.
