6
System and Network Security
“A computer is only secure when it's turned off, and not really even then!”
Bill Gates
– Recalling the basic concepts and challenges of IT security.
– Defining the threats and attacks to which a business's IT system can be exposed.
– Describing various security mechanisms.
– Understanding security management systems and corresponding norms as well as the concept of a security policy.
6.1. Introduction
These days, business IT systems are more and more widely distributed and rely on computer networks to connect the headquarters with its various subsidiaries, as well as teleworkers, retail establishments, etc. This remote access has encouraged the decentralization of businesses and their opening up to the entire world, and has become increasingly sophisticated with new wireless access technologies (GSM, 4/5G, Wimax) and the complete opening up of the Internet network.
Of course, IT networks are necessary for businesses as they enable trade and increase these businesses' competitiveness. Nevertheless, they also carry enormous risks such as the interception of messages, data theft, loss of system and network access, hacking, etc. A wide range of security and safeguarding mechanisms have been introduced in order to reduce the risks faced by businesses as much as possible.
6.2. Definitions, challenges and basic concepts
IT security is made up of all of the technical, organizational, legal and human procedures deployed to maintain and ensure the security of the hardware and software resources of an enterprise's IT system.
Security represents a major challenge for any business and its partners. There are in fact multiple challenges to a company's competitiveness and even survival in an atmosphere of increasingly sophisticated attacks and threats:
– short-term challenges: giving all authorized users access to the information they need;
– intermediate-term challenges: these have to do with the consistency of the enterprise's information system;
– long-term challenges: keeping users' and clients' trust for a good business brand image.
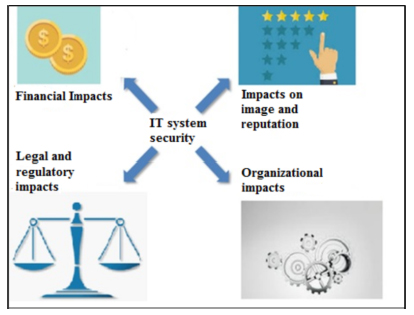
Information is as important an asset as those related to the classic production system (physical assets, human assets, financial assets, etc.). It is even a strategic asset that must be protected. Information security can be defined as a system implemented to ensure the protection of this information and its related assets with the goal of mainly ensuring the following services or objectives:
– availability: ensuring that authorized users have access to information and related resources when desired;
– integrity: ensuring precision and accuracy of information during storage, processing and transmission;
– confidentiality: ensuring that only authorized persons can access information.
In addition to the concept of CIA (Confidentiality, Integrity and Availability), other principles or services may be necessary for the protection of information, such as:
– authenticity: the fact of an entity actually being what it claims to be;
– nonrepudiation: the fact of not being able to deny a transaction that has been made. It consists of obtaining proof of the transmission of information, or of its receipt;
– traceability: this is the characteristic that preserves traces of the condition and movements of information. It involves retracing histories and the use or localization of information by means of a documenting mechanism.
Security can be broken down to encompass multiple levels:
– prevention: protects a business's assets from being attacked;
– detection: determining when, how and by whom an asset has been damaged;
– reaction: being able, after a security-related incident, to restore assets or reduce the impact of the incident.
IT system security encompasses physical security against theft and incidents of force majeure (fire, earthquake, floods), software security (operating systems and applications), human security (employee awareness) and organizational security.
IT system security generally involves measures against threats, vulnerabilities and attacks:
– threats: events likely to occur that would be harmful to the business's resources;
– vulnerabilities: characteristics inherent to an asset that may constitute a weakness or flaw related to IT security. These vulnerabilities can be organizational (no security policy), human (staff not trained), software-related (design and programming errors) or hardware-related (use of unreliable products);
– attacks: malicious actions that harm the security of an asset. An attack represents the concretization of a threat and/or requires the exploitation of a vulnerability.
6.3. Threats/attacks
Attacks include any action that may compromise the security and functioning of an IT system. There are multiple motivations for attacks including the theft of sensitive information, disruption of system operation, use of system resources for other purposes, etc.
The process of an attack begins with the collection of information pertaining to the system targeted, and then the determination of corresponding vulnerabilities, followed by the execution of the attack proper and finally removal of the traces of this attack.
Attacks can be grouped into four categories.
6.3.1. Access attacks
Any attempt to access information by an unauthorized person. This type of attack affects confidentiality of information. Sniffing, social engineering and password hacking are examples of this type of attack.
6.3.2. Modification attacks
Any attempt to modify information. This type of attack targets information integrity. Viruses, worms and Trojan horses are examples of this type of attack.
6.3.3. Saturation attacks
The intent of this type of attack is to overwhelm a company's server and paralyze its website for several hours, thus blocking access to it without necessarily altering its content. These attacks target the availability of information. TCP SYN flood attacks, smurfing, ping flood attacks and UDP flood attacks are some examples of this type of attack.
6.3.4. Repudiation attacks
These attacks target responsibility. In other words, repudiation consists of denying that an event or transaction has actually taken place. Frauds such as MAC spoofing, IP spoofing and man-in-the-middle are examples of repudiation attacks.
6.4. Security mechanisms
Security mechanisms are means deployed to detect, prevent and fight against a security attack on the assets of an IT system.
An IT system with its professional and system assets needs security mechanisms to ensure basic levels of security, that is, availability, integrity and confidentiality, and, if possible, the remaining levels of security, authenticity and nonrepudiation, as well.
There are various defensive resources available. We generally do not limit ourselves to a single means of securitization, but rather tend to favor a deep defense approach which consists of installing multiple security technologies in order to reduce the risk that any one security component will be compromised or break down.
The concept of deep defense is based on the superimposition of multiple levels of defense in order to have layers of security ready to act if the business's primary security mechanism has been attacked.
6.4.1. Encryption tools
These days, the goal of encryption is to address issues of communications security in general and to provide a number of security services such as confidentiality, authentication, integrity, etc.
Encryption algorithms, hash functions, electronic signatures and digital certificates are some of the best-known examples of these tools.
6.4.2. Antivirus programs
These programs detect and eliminate viruses, worms and Trojan horses, as well as other malware that can infect computers.
6.4.3. Firewalls/IDS and IPS
6.4.3.1. Firewalls
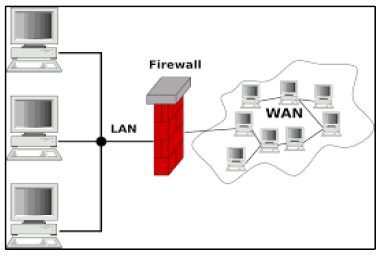
Hardware or software firewalls are used to isolate areas of a network and to authorize only certain flows in by filtering packets exchanged, in order to prevent intrusions.
This filtering of packets takes place in the TCP/IP layer. Incoming and outgoing packets are examined in terms of their source and destination IP addresses and their port numbers in order to be authorized to pass or not. Packet filtering functions with positive filtering rules, that is, what should be authorized must be defined, and anything not explicitly authorized is automatically forbidden.
This static packet filtering is enriched by additional rules to create what is called Stateful Packet Inspection (SPI). SPI verifies that incoming data packets are related to data packets previously sent, that is, that they belong to a session initiated by the secured local network.
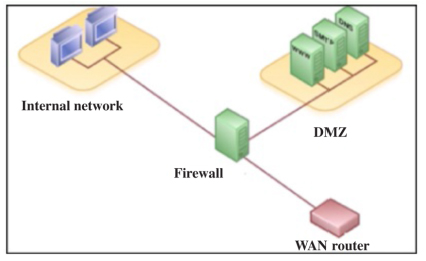
Most businesses have web and e-mail servers they wish to make accessible to external visitors. These servers are thus placed between the private network and the Internet on a separate segment of the network. This segment is governed by less rigid security rules and is thus accessible from the outside, but relatively isolated from the local network. Its objective is to prevent exterior access to private machines in the business's internal network. This isolated network segment is called a demilitarized zone (DMZ).
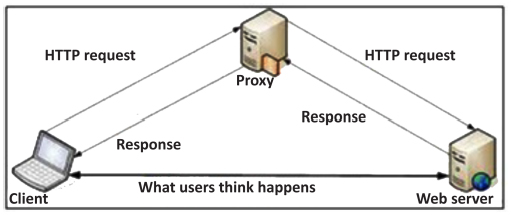
Proxies are a specific type of firewall consisting of an intermediary or proxy server that relays requests from the internal network to an external network, generally the Internet. These proxies also offer other functionalities such as caching, authentication, anonymization and more refined filtering using advanced filters.
6.4.3.2. Intrusion detection systems (IDS) and intrusion prevention systems (IPS)
IDSs/IPSs detect and warn of malicious behaviors by monitoring processes, for example, or observing certain aspects of user and program behavior to detect suspicious activity based on pre-established rules or statistics. Honeypots are practical tools to detect intrusions.
6.4.4. VPNs
These are virtual private networks constructed over a public network (the Internet). They provide secure, cost-efficient WAN links using encryption and tunneling techniques and are being used with increasing frequency by businesses. A tunnel is a logical connection between arbitrary end points which are VPN clients, servers or gateways.
There are two methods of creating tunnels. In the first one, the tunnel is established in layer 3 of the OSI layer model. Another method directly involves layer 2 of the OSI layer model, with the data packet from layer 3 being encrypted and then addressed with the physical address.
There are also site-to-site VPNs and remote access VPNs. The main protocols are PPTP, L2TP, IPSEC and MPLS. The choice depends on the performance and security requirements of the business in question:
– PPTP (Point-to-point Tunneling Protocol): a data link layer protocol responsible for data encryption and compression. It is included in Windows operating systems since it was developed by Microsoft. Its use is especially recommended for remote access.
– L2TP (Layer 2 Tunneling Protocol): a more advanced version of PPTP and L2F. The structure and advantages of these two non-standardized methods have been adopted and standardized into L2TP. While PPTP supports only the IP, IPX and NetBEUI protocols, the L2TP protocol has the advantage of being able to transport any network protocol into the PPP frame structure. This means that it also has a significant overload and thus a low net data output. The L2TP protocol works well with point-to-point virtual private networks as well as remote access connections to service providers.
– IPSEC: a protocol that secures data exchange in the network layer. It is an extension of the Internet protocol (IP) that includes encryption and authentication mechanisms. This makes it possible to transport secured IP packets cryptographically over public, unsecured networks. It is based on two mechanisms. The first mechanism, AH (Authentication Header), is designed to ensure the integrity and authenticity of IP datagrams. The data transmitted is not encrypted, so this mode does not guarantee confidentiality of exchanges. The second mechanism, ESP (Encapsulating Security Payload), ensures authentication as well as confidentiality via data encryption. Both mechanisms are based on the IKE (Internet Key Exchange) protocol, which manages the keys used.
IPSec has two operating modes: transport and tunnel.
Transport mode is relatively easy to set up but has the disadvantage of not masking the IP address since the external header is produced by the IP layer. This mode is usually used between two hosts. In tunnel mode, data passes through the battery of protocols until it reaches the IP layer, and then the IPSec layer adds a new header to it, thus ensuring address masking. Tunnel mode is recommended for use between two security gateways (router, firewall, etc.) in order to link two remote sites, for example.
88 Systems and Network Infrastructure Integration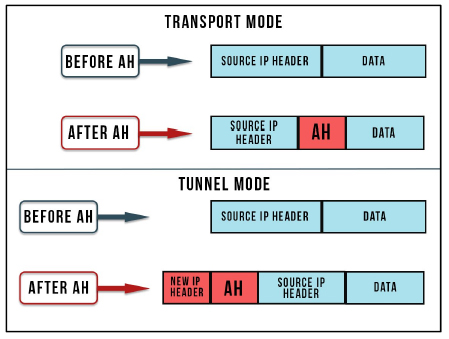
Figure 6.5. IPsec operating modes with AH mechanism. For a color version of the figure, see www.iste.co.uk/helali/systems.zip
– MPLS (Multi-Protocol Label Switching) combines the advantages of switching with routing. It operates between layers 2 and 3 of the OSI layer model and is based on label switching. VPN creation is one of its multiple functions. Practically speaking, to create client VPNS, each client flow must be isolated. To do this, the MPLS label is now composed not of one label but of two; the first (exterior) label identifies the path toward the destination LSR (Label Switch Router) and changes with each hop, while the second (interior) label specifies the VPN-ID assigned to the VPN and is not modified between the source LSR and the destination LSR.
The components of MPLS VPNs are as follows:
– the CE router (Customer Edge router) represents the client router connected to the IP backbone via an access service (LS, Frame Relay, ATM, etc.);
– the PE router (Provider Edge router) is the backbone router to which CEs are connected. It enables a CE to belong to a given VPN. The role of the PE consists of managing VPNs by cooperating with other PEs and switching frames with P routers;
– the P router (Provider router) is responsible for MPLS frame switching.
The operator manages the VPNs in the backbone via PEs. Each PE assigns a VRF (Virtual Routing and Forwarding Table) to each of its user interfaces. The VRF is a routing table assigned to a VPN which gives the paths toward the IP networks corresponding to this VPN.
6.4.5. Other means of security
6.4.5.1. VLANs
These make it possible to structure networks into zones sealed by activity, thus improving the security of the overall network infrastructure. VLANs represent an example of logical segmentation technology used to divide up the broadcast domain and to ensure that each VLAN can communicate with another VLAN only after routing configuration and installation of ACLs corresponding to the company's security policy.
6.4.5.2. Means of authentication
This can be done via login and password or by a chip card or biometry. In the first case, a strict policy of the choice and management of passwords must be implemented. Authentication can also be carried out via electronic certificates. In this case, the IEEE802.1X protocol can be jointly deployed with a Radius-type server.
6.4.5.3. Logical access control
This specifies the actions a previously authenticated user is authorized to take with the IT system's various resources. It depends, naturally, on the physical access control. There are several models of logical access control available, including MAC (Mandatory Access Control), DAC (Discretionary Access Control) and RBAC (Role-Based Access Control).
6.4.5.4. Physical security of equipment and premises
This consists of providing for the deployment of barriers, alarm systems, surveillance cameras, locks and other physical mechanisms to manage physical access to a business's premises, servers, computers and network equipment.
6.4.5.5. NAT (Network Address Translation)
This is a mechanism that makes it possible to replace the private IP addresses of machines in the local network with public addresses during traversal of an NAT router. The main objective of this technology is to compensate for the shortage of IPv4 addresses. Moreover, it enables internal local network IP addresses to be masked, thus improving security.
6.4.5.6. NAC (Network Access Control)
NACis a protective concept that provides:
– clear recognition of attempts to access and identify devices and users;
– verification that security policies adopted are in place;
– isolation and, as far as possible, automatic correction of violations of established policy;
– creation and management of policies and assessment of incidents and data collected.
6.4.5.7. Logging and audit
Logging allows traces of various activities to be retained; more precisely, who did what, when and for how long for each incoming and outgoing connection. Logging makes security more dynamic as it is regularly reviewed in order to monitor developments in systems, networks and risks.
6.4.5.8. Backups
Backups keep an intact, functional copy of an information system's data and documentation, allowing activity to be resumed in the event of an incident. Data storage technologies such as Storage Area Networks (SANs) or Network Attached Storage (NAS) are more suitable for a modern information system. Backup and restoration procedures and devices should be chosen according to need, strictly implemented and regularly verified.
6.4.5.9. Training and awareness
Information system security involves a human and social component that is as important as the technological component. Even the best protection methods will fail if they are in the hands of inexperienced, untrained, ill-informed users. Therefore, the managers of technical infrastructures and networks must work to inform, train and increase awareness among users with regard to security issues. They must also stay informed about new attacks and threats, subscribe to alert bulletins from CERT and other organizations that broadcast information on security and to specialized journals, consult specialized forums regularly, attend conferences on the subject and, above all, apply the lessons learned.
6.5. Security management systems: norms and security policies
6.5.1. Norms
Security is multidisciplinary. It has multiple aspects, in this context ethical, legislative, technological, methodological and normative.
The securitization of an information system is a relatively arduous task requiring an IT security management system to guide it.
A management system is defined by the ISO as “a system enabling the establishment of a policy and objectives and the attainment of these objectives”. It can be considered as a set of organizational measures and techniques targeting specific objectives. These systems are based on reference sources that formalize policies and procedures so that they can be subsequently audited.
The implementation of these information security management systems, or ISMS, requires material, human and financial resources, an investment that is justifiable insofar as these security management systems increase reliability. Moreover, the fact of being audited or even certified by a standardization organization increases trust and confidence in a business on the part of its partners.
The 2700X family of ISO norms sets the standards for information security management systems (ISMS). We are referring more specifically here to norm ISO27001, which sets requirements for the setup of an ISMS, and norm ISO27002, which provides a catalogue of best practices for information security management.
Norm ISO27001 relies on a process-based approach, and more precisely on the Deming wheel process, or PDCA model (for Plan, Do, Check, Act):
– the Plan phase consists of defining the perimeter to be secured, gauging the risks and selecting security measures;
– the Do phase consists of planning how risks will be addressed, designing significant indicators, training personnel and managing incidents;
– the Check phase uses controls, audits and review to regularly assess the current state of the information system's security;
– the Act phase involves the implementation of corrective, preventive and improvement-related actions in the event that the predetermined objectives have not been met.
6.5.2. The idea of security policy
The ITSEC (Information Technology Security Evaluation Criteria) European standard defines a security policy as being “the laws, rules, and practices that govern the way in which sensitive information and other resources are managed, protected, and distributed within a specific system”.
It is concretized by a set of reference documents which include the security rules to be applied and complied with. It also defines the security objectives set by the business and the mechanisms and procedures deployed to ensure them.
The securitization of an organization or enterprise's network and system infrastructures must be based on the security policy in effect. The choice and implementation of different security mechanisms and solutions depends on the corresponding security policy.
6.6. Chapter summary
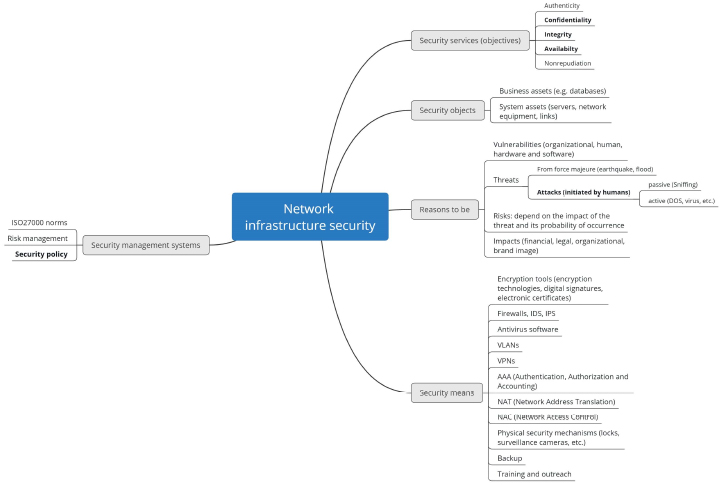
Note
- This chart is also available at www.iste.co.uk/helali/systems.zip
