7
Virtualization and Cloud Computing
“You don't need to be physically out in the world anymore to participate in it. I'm 90% virtual.”
Karl Lagerfeld
– Understanding the concept of virtualization
– Learning the virtualization domains
– Determining the advantages and disadvantages of virtualization
– Understanding the different types of virtualization
– Understanding the concept of cloud computing
– Learning the different service models pertaining to cloud computing and their typologies
7.1. Introduction
The setting up or upgrading of IT infrastructures requires significant financial investment for every business. In an increasingly difficult economic climate, any solution that enables a reduction in costs is more than relevant. This category includes virtualization, which helps businesses to create an IT infrastructure that is easy to manage and low cost, thus eliminating dependence on a single hardware provider and ensuring more resilient, flexible and agile IT functions.
Additionally, cloud computing, based on the concept of virtualization, is of great interest to businesses insofar as it enables a new way of organizing information systems as well as another approach to managing different IT resources. The goal remains higher profitability for the business, as well as scalability and the capacity for expansion.
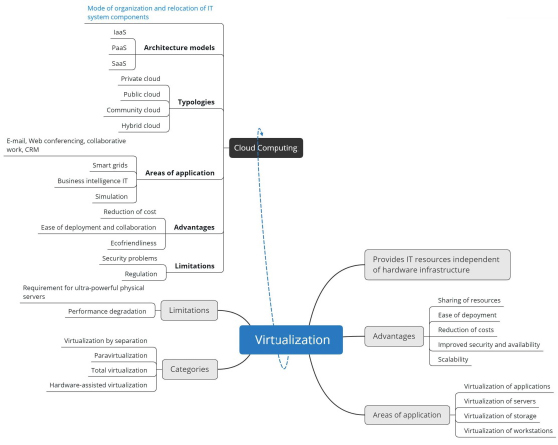
7.2. Virtualization
7.2.1. Definition
Virtualization includes a range of technologies offering IT resources that can be used flexibly and on demand, independently of the underlying hardware infrastructure. It can be seen as a layer that separates the operating system from the hardware so that the various resources can operate more efficiently. This layer helps to create an environment suited to specifications instead of adapting specifications to fit within the limitations of the hardware environment.
A piece of IT hardware is initially designed to make a single operating system and several applications function. Virtualization makes it possible to bypass this limitation and run multiple operating systems on the same hardware support, thus optimizing the use of hardware resources.
Virtualization can affect the entirety of the hardware environment, that is, the processor, memory, hard disk, peripheral devices and network components, so that each virtual machine has its own virtual resources. Consequently, every virtual machine is completely independent and will not be disturbed or disrupted by the functioning of other virtual machines (shutdown, startup, installation of programs, etc.) that may coexist on the same physical machine.
7.2.2. Benefits of virtualization
Virtualization technology offers a number of benefits:
– pooling of resources: the setting up of multiple logically separated systems on a single physical machine optimizes the use of these systems;
– ease of configuration, deployment, upgrading and migration of virtual machines;
– ability to test a new system without disrupting the base operating system;
– reduction of operating energy consumption: using less hardware results in lower electricity consumption and fewer upkeep and maintenance operations;
– improved security: network security is increased because guest operating systems are not visible to attackers;
– improved availability: a cluster can be formed of two physical servers with virtual machines, which can be automatically copied from one server to another in the event of problems. Moreover, the snapshot or instant capture function of a virtual server makes it possible easily to reinstall a server configuration;
– improved prevention and management of malfunctions as well as system activity resumption thanks to automatic recovery. Virtual servers can be simply restored in the event of problems due to their portability, since the physical server sees them as a series of files;
– scalability via the rapid deployment of new application servers;
– the supervision function is greatly simplified and centralized; a single monitoring software program supervises all virtual servers.
7.2.3. Areas of application
7.2.3.1. Virtualization of applications
The virtualization of applications consists of adding an additional software layer between an application and the operating system through which all file reading, modification or system registry files must pass in order to redirect them transparently toward a virtual location. The end goal is to improve portability and compatibility of applications by isolating them from the host operating system. In this way, multiple applications can function on a single operating system without encountering compatibility problems, in the registry, for example. It is also possible for multiple versions of one application to run on a single operating system. Wine, PlayOnLinux and CrossOver are some examples of this.
7.2.3.2. Virtualization of servers
The principle here is to make multiple virtual servers function on a single physical server in order to optimize the use of its capacity. Studies have shown that servers use an average of 15% of their capacity. This technique enables a business to save in terms of physical infrastructures, specifically with regard to space occupied, electricity consumption, climate control and staff needed for administration.
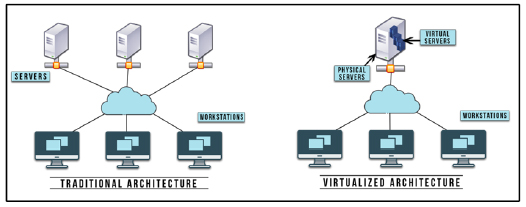
Figure 7.1. Virtualization of servers. For a color version of the figure, see www.iste.co.uk/helali/systems.zip
7.2.3.3. Virtualization of storage
The objective of this is to provide advanced functionality in terms of storage. The principle is that various storage resources are brought together into a single logical storage device. This procedure, also called storage abstraction, enables the user (server, application or workstation) to access only one logical storage resource through an intermediary layer composed of servers, software and network switches, which intercepts outgoing server traffic and transfers it to physical storage devices according to specific protocols.
This virtualization ensures independence between the management of the physical storage system (disks, storage bays) and its attached servers, and enables applications to separate the physical management of disks (and storage bays) from the servers that use them, which also reduces the high cost of storage management.
Storage virtualization enables:
– the addition of a new storage device without interruption of service;
– the conglomeration of multiple heterogeneous storage devices into a single logical storage entity;
– dynamic reallocation of storage space according to application server needs.
This virtualization is used in NAS and SAN networks.
7.2.3.4. Virtualization of networks
The virtualization of networks is based on the abstraction of hardware network resources in software form. It separates network services from the hardware on which they operate. Physical network resources, specifically switches and routers, are thus accessible via the intermediary of a centralized management system. This procedure increases the network's productivity and efficiency.
More specifically, it involves transforming certain network functionalities (firewall, NAT, etc.) into software programs. In this way, the deployment or updating of new network functionalities is greatly simplified and less costly as well.
The management of these virtualized network functions is carried out by a network controller called an SDN (Software-Defined Network) controller, which controls the network, improves its performance and automates its services.
7.2.3.5. Virtualization of workstations
Workstation functionality is supplied based on a virtual infrastructure. This approach is beneficial because it ensures centralized, simplified administration of IT facilities as well as the substitution for traditional workstations with clients that are both more cost-effective and more eco-friendly.
In addition, it fulfills the need for continuous access from anywhere, a mobility requirement that is increasingly omnipresent for businesses today. Thus, traditional desktops, which are cumbersome and become obsolete within 2-3 years, are replaced by virtual desktops, or VDI (Virtual Desktop Integration).
This form of virtualization also relieves businesses of the need to manage their own IT facilities and the associated maintenance burden. Each user can access his or her own work environment hosted on virtual servers in datacenters.
7.2.4. Categories of virtualization
Virtualization, a way to supply a number of IT resources independent of the hardware platform, can be broken down into four categories according to Figure 7.2.
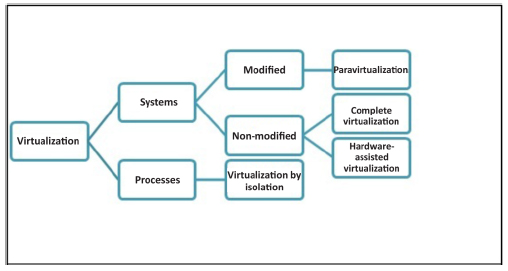
Figure 7.2. Categories of virtualization
7.2.4.1, Virtualization by isolation
This category can pertain to applications or processes and is based on confining the execution of applications to well-defined contexts using a specific software program, making it possible to run several instances of the same application. Open VZ provides an example of process virtualization.

Figure 7.3. Virtualization by isolation. For a color version of the figure, see www.iste.co.uk/helali/systems.zip
7.2.4.2. Paravirtualization or type 1 hypervisor
A hypervisor functions directly on hardware, thus avoiding using a complete host operating system and limiting itself to the basic kernel services of common operating systems, in this case the management of virtual machine memory and scheduling. In this situation, the guest operating system is modified and acknowledges that it has been virtualized and then relies on the hypervisor to access the hardware resources of the physical server. This category of virtualization shows high performance but is costly. Examples include VMsphere(ESXi), KVM and Microsoft Hyper V.
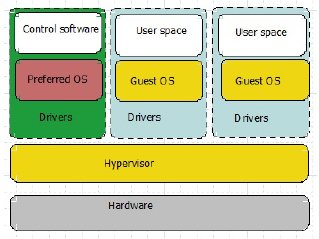
Figure 7.4. Paravirtualization. For a color version of the figure, see www.iste.co.uk/helali/systems.zip
7.2.4.3. Complete virtualization
This type of virtualization is also called a type 2 hypervisor. It is based on an emulator running on a classic operating system used to manage the memory and scheduling of virtual machines. The hardware is completely simulated. Other operating systems can be installed; these will think they are communicating directly with the hardware. This type of virtualization enables multiple systems to cohabitate on a single physical machine while remaining partitioned from one another. However, it is not very high-performing. Guest operating systems are not aware that they are virtualized. Examples of this approach include VirtualBox, Oracle VM and HyperV.

Figure 7.5. Complete virtualization. For a color version of the figure, see www.iste.co.uk/helali/systems.zip
7.2.4.4. Hardware-assisted virtualization
This represents an improvement on complete virtualization using the processor extensions AMD-V and Intel VT. The simplicity of function of applications and the available of high-performance administrative tools have contributed greatly to the success of this type of virtualization. Examples of this category include VMWare, VirtualBox and Virtual PC.
7.2.5. Limits of virtualization
Despite the significant benefits of virtualization technology, there are some disadvantages.
The physical machine or server hosting various virtual machines must be extremely powerful and equipped with state-of-the-art technologies. It must possess several processors, consistent memory and high storage capacity. These characteristics are, of course, very costly.
The major issue with virtualization is the possibility of the physical server encountering problems or breaking down. If this happens, the virtual machines become unavailable.
Performance may be reduced by the use of virtualization, which can hinder applications from running, as virtualization itself takes up around 30% of the machine load. However, this drop in performance will have more or less of an effect depending on the type of virtualization adopted.
A security breach in the hypervisor exposes all virtual machines to security risks. Virtual systems become preferred targets for attackers, especially if they are not regularly updated and patched.
7.3. Cloud computing
7.3.1. Definitions
Wikipedia defines cloud computing as a concept that consists of siting IT processes on remote servers that are traditionally executed on local servers or at a user workstation.
NIST (National Institute for Standards and Technology) defines cloud computing as access via a telecommunications network, on demand and by self-service, to shared, virtualized IT resources. It is a relocation of a business's IT infrastructure.
Cloud computing represents an economic IT model that enables the use of software and hardware resources involving servers that are not owned by a company via the Internet, generally by payment-on-demand and according to the company's needs. The goal is to share IT resources including computational power, storage space and network functionalities.
7.3.2. Leverage factors and generic principles
Several factors have contributed greatly to the emergence and success of the cloud computing paradigm.
Successive developments in IT systems, such as the increasing of computational power with new processors, the meteorically swift development of Web technologies, the opening up of companies to the Internet and the current trend toward decentralization have led logically to cloud computing. The current environment, which is highly competitive and based on cost reduction, the appearance of new, increasingly sophisticated terminals, etc., provides an ideal context for cloud computing.
Cloud computing represents a method of organizing and relocating the components that make up an IT system. It is based mainly on the concept of virtualization. The end user is able to execute applications according to his or her own needs without knowing where the servers or the data used are located.
Cloud computing is characterized by the following features:
– continuous and up-to-date availability of services;
– bespoke operation, with payment made according to consumption;
– dynamic allocation of capacity according to load for better management of traffic peaks and sharing of resources.
7.3.3. Architecture models
Cloud computing is generally broken down into three main service models that differ according to the degree of outsourcing adopted by the company's IT system. These three models illustrate three levels of virtualization and can also be considered delivery models.
The objective of the cloud concept is to set up a service between a client and a service provider while ensuring the continuity and quality of this service. To achieve this goal, methods in all levels involved have been developed, including:
– the application, used by the client;
– the platform, or the environment that executes the application;
– the infrastructure, which constitutes the platform support.
7.3.3.1. IaaS (Infrastructure as a Service)
Hosting concerns a virtual infrastructure made up of servers, network resources, storage solutions, etc. It is the equivalent of a real infrastructure and is made available by the cloud provider. The client purchases its resources according to need. Thus, the whole infrastructure part of the client company is outsourced. This model is the base for the following two models, Amazon EC2 and Google Cloud Storage, which are examples of this model.
7.3.3.2. PaaS (Platform as a Service)
The cloud provider offers the whole development platform, hosting company applications as well as management and testing environments accessible through a browser with no need to use other software programs. The degree of outsourcing is higher than that of the IaaS model. This model is more relevant to applications developers, as it provides them with a customized development framework. It also serves as a base for the SaaS model. An example of a PaaS is Google App Engine.
7.3.3.3. SaaS (Software as a Service)
Business applications are transferred to the cloud provider, meaning that all necessary software programs are functional without any prior installation or updating, and require no maintenance on the part of the client. This model supplies the highest degree of outsourcing and is based mainly on the principle of standardization of hosted applications. SaaS platforms are based on SOA (Service Oriented Architecture); examples include Gmail and Office 365.
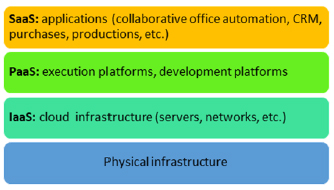
The cloud is a solution that provides space for virtual placement of server or network infrastructures, development or execution platforms, applications, etc. A cloud supports different layers of the service model, from infrastructure to the end client.
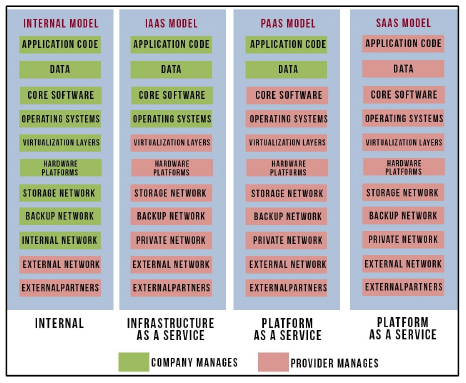
Figure 7.7. Distribution of responsibility for cloud computing service delivery models. For a color version of the figure, seewww.iste.co.uk/helali/systems.zip
To further explain cloud service models, an analogy called “Pizza as a Service” is often used as a tangible visual illustration.
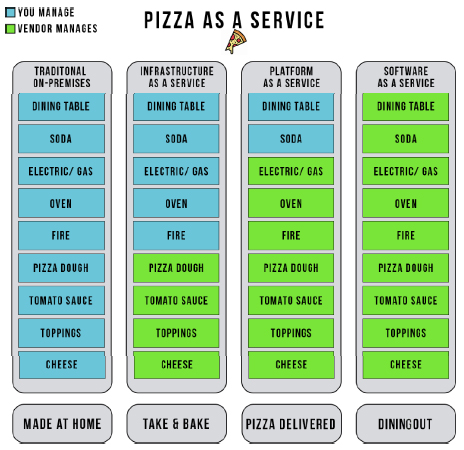
Figure 7.8. Pizza as a Service analogy. For a color version of the figure, see www.iste.co.uk/helali/systems.zip
7.3.4. Types of cloud
Two classification criteria are used to categorize the types of cloud:
–Criterion one: who manages the cloud, the cloud provider or the company?
– if the company manages the cloud with its own resources, it is an internal cloud,
– if the cloud provider manages the cloud with its own resources, it is an external cloud.
– Criterion two: who benefits from the service provided by the cloud?
- if the cloud is dedicated exclusively to the company's own needs, it is a private cloud,
- if the cloud is open to the public or to other companies, it is a public cloud.
Four typologies have been established:
– internal private cloud: the company sets up its own infrastructure and offers its services for its employees;
– external private cloud: the company operates an infrastructure rented to a cloud provider and hosts its professional services;
– internal public cloud: pertains to cloud providers. Internal services are offered within the company and to external clients;
– external public cloud: a cloud managed by third-party cloud service providers and made available to partners or clients of the company in question.
Another classification of the types of cloud is also widely used, specifically:
– public cloud: a cloud made available to the public at large. It is external to the company, accessible via the Internet and can be shared among multiple companies. An external service provider with corresponding infrastructures is responsible for managing it. The payment method is pay-as-you-go;
– private cloud: takes the form of an internal cloud structure proper to the company;
– community cloud: a particular type of private cloud that is open to partners of the company (service providers, clients, banks, etc.);
– hybrid cloud: combination of a private cloud and a public cloud that provides the benefits of both types.
7.3.5. Areas of application
Cloud computing is used today by both companies and private individuals. It is a technology that has rapidly become widespread and is experiencing great popularity. Several uses are currently proliferating:
– WEB2.0 applications: e-mail, web conferencing, collaborative work, CRM (Customer Relationship Management), development and testing environment;
– intelligence applications;
– simulation;
– grid computing;
– home automation;
– audiovisual media;
– automotive industry;
– industrial control of machines and procedures.
Many manufacturers and publishers have become involved in the field of cloud computing and have thus become cloud providers, such as Sun, HP, IBM, Oracle, SAP, Google, Yahoo and Amazon.
Table 7.1 some cloud technologies grouped according to service delivery model (SaaS, PaaS, IaaS).
Table 7.1. Some examples of IaaS, PaaS and SaaS technologies
| Private internal | Private external | Public internal | Public external |
|---|---|---|---|
| SaaS | |||
| Collaborative spaces | Google Apps, CRM Amazon | CMS: Content Management System | Facebook, LinkedIn |
| PaaS | |||
| Web development (ViFiB) | Oracle PaaS | Free Cloud Alliance | Azure, Kawet mobile app platform |
| IaaS | |||
| VMware | Virtual infrastructures OVH, Amazon | Free Cloud Alliance | Google Drive, Dropbox |
7.3.6. Advantages and limitations
Cloud computing has numerous advantages for businesses:
– reduction of costs: usage determines costs. We only pay for what we have consumed. This approach enables a company to reduce its expenditures and to be more competitive. This automatic adaptation to demand is called elasticity;
– ease of deployment and innovation: elasticity enables companies to experiment and easily deploy new approaches at lower cost and with lower risk;
– contribution to Green IT by reducing electricity consumption;
– ease of collaboration: cloud computing enables a company to collaborate more efficiently with its clients and partners thanks to shared workspaces in cloud communities.
However, cloud computing is not without limitations. Some of these limitations include:
– dependence on a reliable, fast Internet connection as well as increased load on networks, which will be more heavily used;
– security issues: enormous quantities of data can be stored in a cloud provider's servers. This data, some of which is confidential, is transferred to the Internet network and can be stolen or hijacked, with potentially disastrous consequences for companies and cloud service providers;
– regulations can impose constraints, as both cloud service providers and businesses must be aware of and comply with the laws in effect, which can vary from one country to another.
7.4. Chapter summary
Note
- This chart is also available at www.iste.co.uk/helali/systems.zip
