9
Avoiding Behavior Tracking Applications and Browsers
In the previous chapter, we discussed how to implement cyber anonymity and prerequisites to maintain cyber anonymity. When your objective is to maintain cyber economy, you need to think about multiple layers and plan accordingly. To do that, we need to understand the scope and implement the correct internet connection, as that is the medium to connect to cyberspace. When the medium is secured, you need to prepare a device and applications to maintain cybereconomy, as devices and applications track you in different ways.
This chapter explains how to maintain cyber anonymity and discusses the areas and techniques that we can use to maintain cyber anonymity. As we already know, applications and browsers track our behavior using multiple methods, including cookies and location tracking. When interacting with the internet, we also overexpose ourselves and share sensitive information intentionally or unintentionally, which attackers use to their advantage. We are going to discuss how to maintain cyber anonymity and the areas and techniques that we can use to maintain cyber anonymity in the following topics:
- Avoiding behavior-tracking applications and browsers
- Using secure messaging apps
- Using disposable emails and contact numbers
- Using virtual machines and virtual applications
Avoiding behavior-tracking applications and browsers
In the previous chapter, we discussed how to disable tracking in popular operating systems and some of the most popular apps. Without our knowledge, some apps can still track us, even if we configure cookies to maintain privacy. These apps are programmatically designed to collect information, especially the various web apps we access today. We discussed what web apps can do nowadays in previous chapters. One of the mechanisms that we can use to improve security is anti-tracking browser extensions. There are various anti-tracking browser extensions out there developed by individual developers, companies, and communities. When you access content on a web application or web page, some of the elements on the web page, known as trackers, are designed to collect details about your browsing habits and other information and send it back to third parties. These apps and sites violate privacy and consume lots of resources including your bandwidth to load the pages, as trackers need lots of bandwidth to communicate between the end user devices and the third-party activity tracker. Most web apps and sites collect your information for advertising purposes, but they may have other intentions. Some web apps use this information to provide meaningful content and easy access to information that you are looking for, but some apps can have more dubious intentions.
On the bright side, even though these web apps collect your information, there are various tools and plugins that can be used to make your browsing activity more private. Most of these tools and plugins are designed to let users know what type of information is collected by these apps, and they minimize annoying ads and save resources such as bandwidth from undesired usage.
Tracking is not only active when you are browsing the internet but also when you play games on the internet, watch movies on streaming services such as YouTube, chat with your friends on social media, read emails you have received – especially on free email services such as Gmail and Yahoo – and use apps that are downloaded on app service portals such as Google Play, Microsoft Store, or the iOS App Store. No matter what you do, you will create a digital footprint in cyberspace. Basically, if you have not taken proper precautions, every moment you spend in cyberspace will see you tracked. For example, if you are planning to buy a refrigerator and look at a few options, it’s not really a coincidence if you suddenly start getting advertisements for refrigerators on YouTube, news websites, and so on. Mostly, your browser cookies are directly responsible for this, and the rest is done by the trackers. When you access any website, a large number of cookie files are loaded onto your browser for different purposes. Currently, there are a few arguments going on related to allowing users to decide whether they want to be tracked or not by the apps that are installed on their devices. Some larger companies are against this option, as it can prevent the possibility of understanding user behavior and they will not be able to perform targeted advertisements. One such initiative is to introduce an option called app tracking transparency (ATT) with the iOS 14.5 mobile operating system, which allows users to decide whether they want to be traced or not. This initiative is also challenging to implement, as most apps track you with lines of code and not openly.
So, what’s the remedy for tracking? There are a few ways we can protect ourselves from different kinds of tracking, as follows:
- Configuring your browsers not to track you – we discussed this in the previous chapters.
- Using secure browsers – we discussed secure browsers in previous chapters.
- Secure extensions to browsers – installing and configuring secure extensions on browsers can protect you from tracking. As soon as a web application starts tracking, you will be notified. Some browser extensions even block these tracking activities.
- Desktop applications to protect you from tracking – there are desktop applications designed to block various types of tracking that come from different sources, and they notify you when doing so.
Since we have already discussed protecting yourself from tracking cookies and using safe browsers, in this chapter we will be focusing on some of the very effective browser extensions and desktop apps that we can use to protect us from tracking. As we know, browsers are client programs that we primarily use to access the internet. Since browsers are the main way to access the internet, if we can block tracking from the browser itself, we should be able to stop tracking at the root.
Browser extensions
Browser extensions can be treated as add-ons, plugins, or additional tools connected directly to a browser. Therefore, we can directly protect ourselves from being tracked by using proper extensions. It’s important that we select an extension that is not tracking us, as these extensions can be developed by companies and individuals for different objectives. We are going to go through some of the most popular and trustworthy extensions to see how they work and the advantages and disadvantages of these extensions. Most of these extensions are free, do not utilize a considerable number of resources, and are compatible with most of the popular browsers.
First, we need to know how to install a browser extension. The process is straightforward – you can either search for the desired extension on the web or install it on your browser directly from the extension provider. For example, if you need to install Disconnect, you need to access https://disconnect.me/disconnect and hit Get Disconnect.
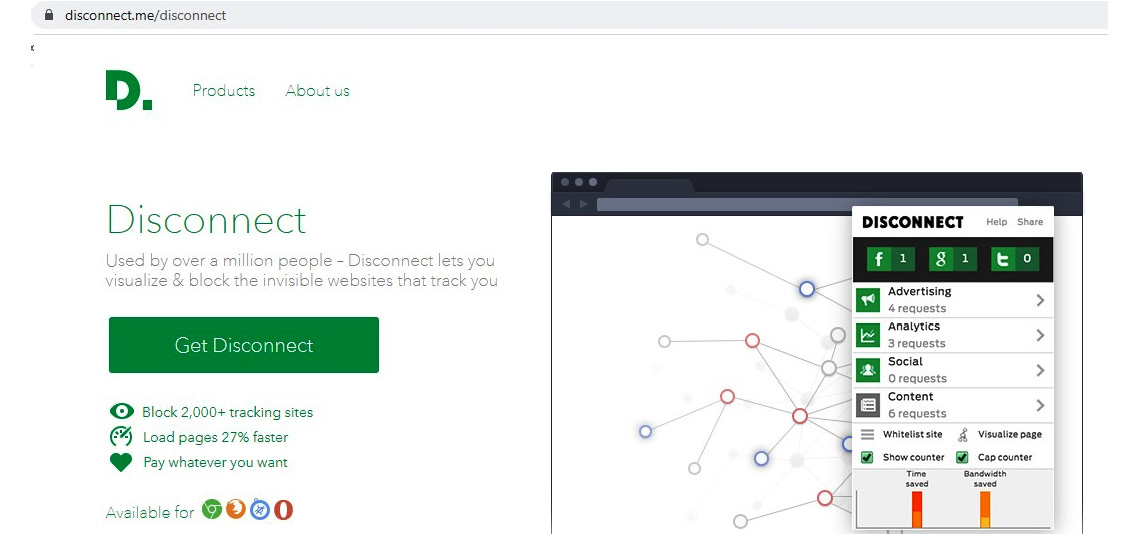
Figure 9.1 – Installation of Disconnect on a browser
When you click on Get Disconnect, it will take you to the browser extension installation window. You will see this window when you are trying to install any browser extension in the future. For some browser extensions, you can use a search engine with the extension name. There are also websites with browser extension lists. When you search and click on Get Extension, you will be redirected to the browser extension page shown in the following figure.
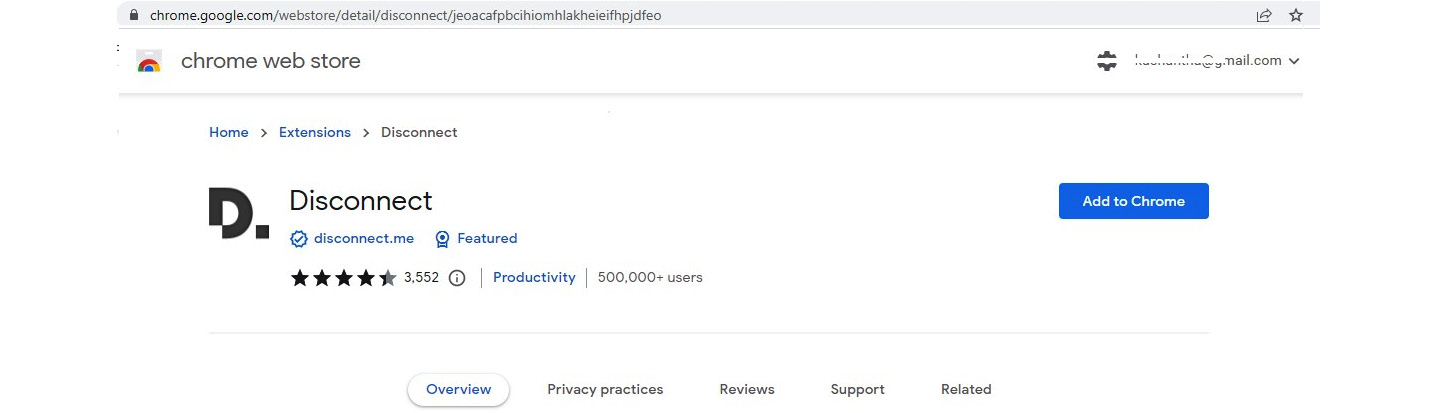
Figure 9.2 – Installing the extension on the Chrome browser
Clicking on Add to Chrome will install the Disconnect browser extension on the Chrome browser. Installation steps are very similar on other browsers. In some browsers, after the installation of the extension, you need to enable it to see it on the browser.
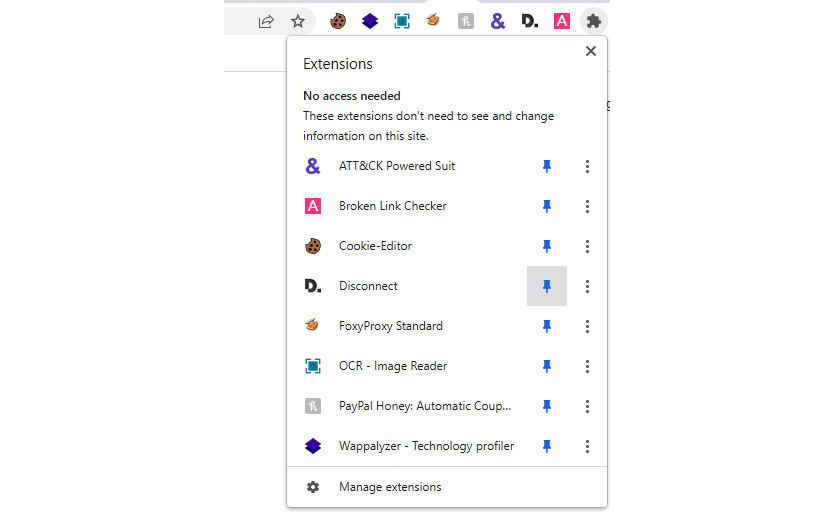
Figure 9.3 – Enabling an extension on the Chrome browser
Once the extension is installed, you might need to enable and pin it to the browser to work. Once pinned, you will see the browser extension on the browser menu. By clicking on the extension icon, you can access the features of the extension.
There are many browser extensions commonly used to prevent tracking and data collection from users by competitors and advertising companies. Some of the browser extensions are not trustworthy, as they also collect information from the users. The following list of extensions is carefully selected based on trustworthiness and functionalities:
- Disconnect – Disconnect is a highly recommended browser extension to protect privacy. In 2016, Disconnect was recognized by The New York Times as the best privacy tool and one of the top 20 best Chrome extensions by Lifehacker. Disconnect also won an innovation award for best privacy and security tool at South by Southwest in 2015 and was listed as one of the best 100 innovations of the year by Popular Science. Disconnect supports a range of popular web browsers. Once you have installed the extension to the browser, when you access any website, it will block trackers and show you what Disconnect has controlled.
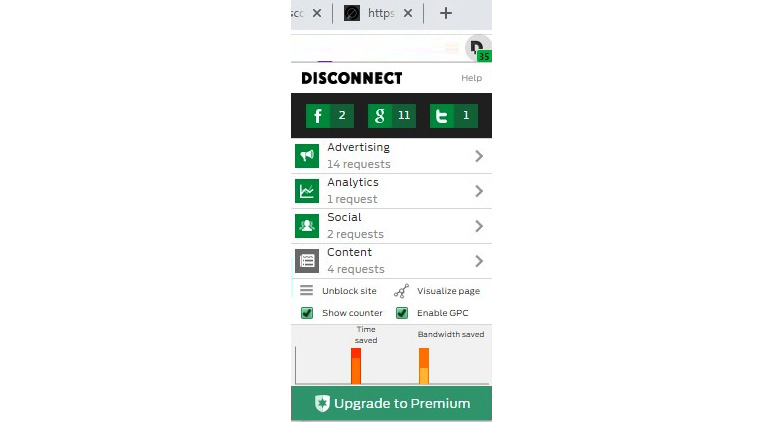
Figure 9.4 – A basic version of Disconnect blocks many trackers
As you can see in the preceding figure, Disconnect has blocked 35 trackers, including Facebook, Google, and Twitter-related trackers. Even the basic version of Disconnect can block a range of trackers accessing your information, including Facebook, Google, and Twitter-related trackers. Disconnect also supports major browsers, including Google Chrome, the Samsung browser on mobile phones, Opera, Safari, and Firefox. Once Disconnect blocks different types of trackers and add-ons from websites, they will load much faster than usual, which saves user bandwidth. Disconnect helps to block a large number of tracking websites, improves website loading time by up to 27%, supports website blacklisting and whitelisting, and has a built-in dashboard that visually displays a range of information, including bandwidth and other information. The only disadvantage is that the basic version has limited capabilities.
When you click on the Disconnect toolbar button, it will show you the total number of tracking requests you received on every page you visited in real time. Disconnect will show you in green the number of requests that it blocked. Disconnect will show you in a gray color the requests that are not blocked. You can click a button to see and block or unblock the requests.
In the Analytics section, you can view different types of sites that send requests and the status of whether a request is blocked or not. In the Options section, you can whitelist or blacklist the site that you are on; this information will be stored in Disconnect and used when you access the site the next time. On the dashboard, you can see the time and bandwidth you saved, and the number of Wi-Fi requests secured by Disconnect if you are connected using a Wi-Fi network.
- Ghostery – Ghostery is another safe browser extension that provides a cleaner, safer, and faster web surfing experience. As we discussed earlier, most websites completely rely on tracking and tracker cookies. Some websites even wouldn’t work if you block their trackers. For example, when you enable Disconnect and block ads, eBay will not work as usual, as it completely relies on tracker cookies to provide a better experience for its customers. Ghostery offers “smart blocking” that can unblock certain harmless trackers if functionality is reduced when trackers are blocked. It automatically blocks or unblocks accordingly.
Ghostery is similar to Disconnect; it provides a simple interface but if you need a more detailed view, you have that option too. Ghostery offers a range of security features known as “boosted features” that offer advanced privacy protection, which block trackers, anonymize your data, and block ads and are totally customizable. Ghostery insights provide a state-of-the-art web analytics tool that provides real-time statistics on the performance of every page you visit. The ad-free private search engine provides zero history tracking, zero ads, and no tracing when you search on the web. All these features come as standard with the Ghostery privacy suite.
You can install the browser extension by visiting https://www.ghostery.com/ghostery-browser-extension and selecting the respective browser from the drop-down menu. Currently, Ghostery supports Google Chrome, Mozilla Firefox, Safari, Edge, and Opera browsers. Ghostery’s free browser extension provides basic browser protection, whereas Ghostery Plus provides a subscription-based service, which provides basic browser protection and advanced device protection. Once you have installed the Ghostery extension on your browser, you might need to enable and pin it to the browser using the same steps we discussed previously for Disconnect installation. Let’s try to access a website and see how Ghostery responds to it.
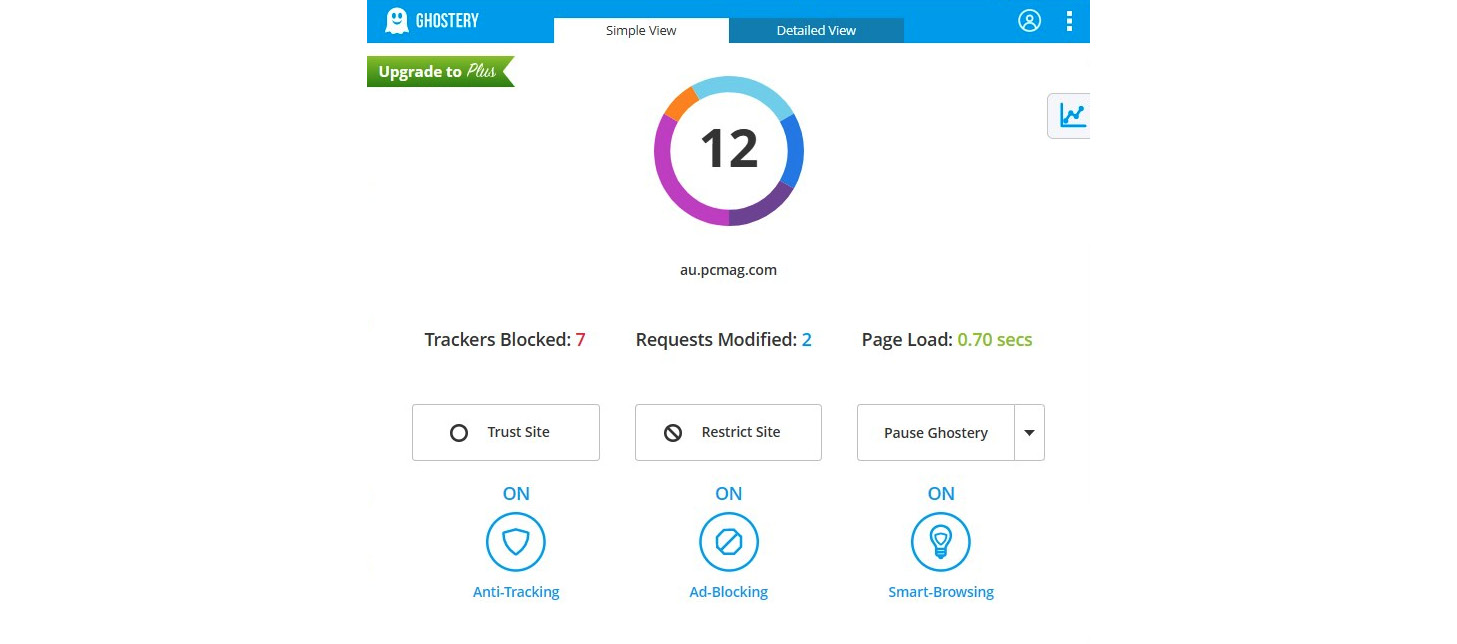
Figure 9.5 – A simple view of Ghostery blocking many trackers
As you can see from Figure 9.5, Ghostery has blocked seven trackers, modified two trackers, and loaded a page faster. You are given the option to trust the site (which is similar to whitelisting in Disconnect), restrict the site (which is similar to blacklisting in Disconnect), or pause Ghostery for a desired duration. Also, note that smart browsing is on by default. You can turn it on or off, as well as anti-tracking, ad-blocking, or smart-browsing, from the extension itself quite easily. If you click on the detailed view, you can individually block or allow different trackers. You have the option of restricting the same tracker on all sites or only on the specified site by simply clicking on the detailed view of Ghostery.
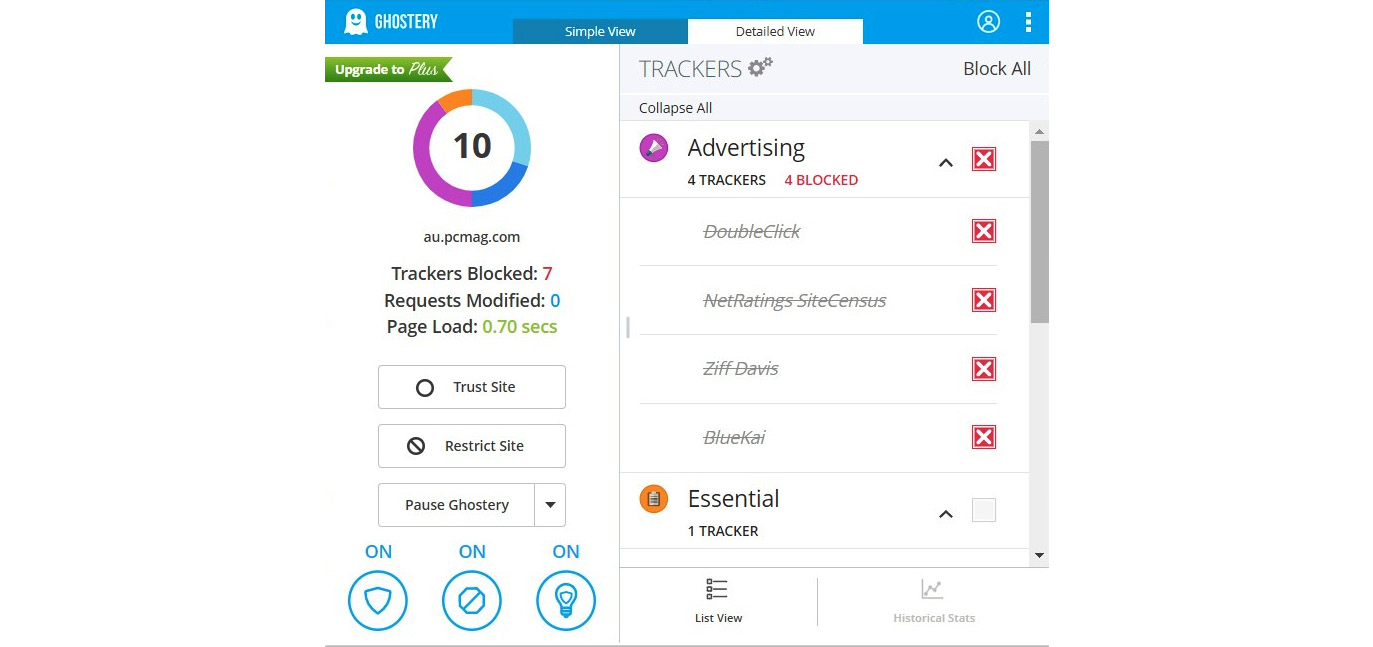
Figure 9.6 – The detailed view of Ghostery provides advanced features
The basic version of Ghostery offers a range of features, but historical stats will only be available once you have upgraded Ghostery to the paid version. The unique set of features offered by Ghostery includes award-winning artificial intelligence-based anti-tracking technology, informing you about what companies are tracking you, and an open source anti-tracking browser extension for a range of popular browsers (as discussed before), increasing the page loading speed by decluttering pages. The easy-to-use interface of Ghostery displays the status of the web page at the bottom of the Ghostery extension, although some websites that use counter-anti-tracking methods might not be identified by Ghostery and might cause Ghostery to not work as expected.
- uBlock Origin – uBlock Origin is a wide-spectrum content blocker that optimizes CPU and memory consumption as a primary feature according to the developers. Once you install uBlock Origin, it will automatically enforce the following features:
- uBlock origin filter lists
- Easy lists – advertisements
- EasyPrivacy – tracking
- Peter Lowe’s ad server list (ads and tracking)
- Online malicious URL block list
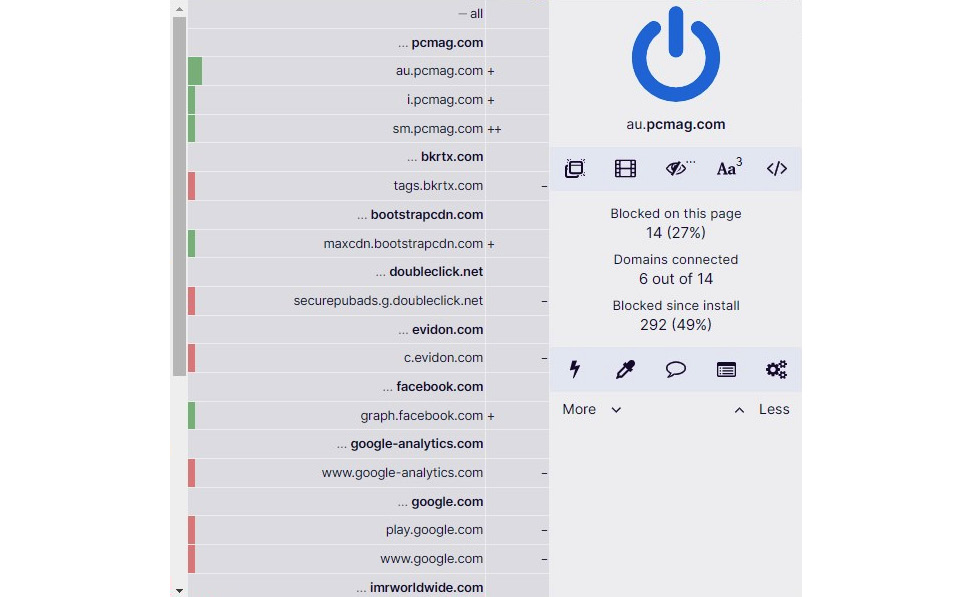
Figure 9.7 – uBlock Origin features
Most importantly, uBlock Origin is free and open source with a public license. Basically, this means people from the tech community volunteer to maintain it and work hard to keep other people safe from ads and tracking. You can install uBlock Origin by visiting https://ublockorigin.com and clicking on the Get uBlock Origin link. The original browser extension on uBlock Origin was first developed by Raymond Hill back in 2014 to maintain a community-maintained block list and add additional features to improve privacy. uBlock Origin is an open source ad blocker that provides CPU - and memory-efficient technology and supports a range of popular browsers. uBlock Origin has attracted the attention of over 5 million active users of Firefox and over 10 million active users of Google Chrome, winning the prestigious IoT honor of “Pick of the Month” by Mozilla. At the time of writing, uBlock Origin is continuously maintained and under development by the founder and lead developer, Raymond Hill, and remains an industry-leading, open source, cross-platform browser extension that provides privacy from ads and trackers. Apart from being an anti-tracking extension, it also provides a pop-up window blocker, a large media element blocker, and a cosmetic filter disabling feature, and it blocks remote fonts and disables JavaScript on websites.
- Privacy Badger – Privacy Badger is another privacy-related browser extension that helps users to stop adversaries and other third-party trackers from tracking and secretly obtaining user behavior information while they are surfing the web. As we discussed earlier, larger companies have the ability to trace your behavior using multiple tracking mechanisms, including third-party cookies. If an advertiser is tracking your activities on multiple websites and pages that you are visiting without your consent, Privacy Badger has the capability to block the advertiser from tracking you. From an advertiser’s point of view, it’s like you have suddenly disappeared.
Privacy Badger was developed to be used as a single extension to block a range of adversaries and trackers once they have violated user consent. Importantly, Privacy Badger will work without any additional settings or configurations by the end user. It has a set of algorithms that decide whether a website is tracking a user or not. Conventional browser extensions simply block ads while Privacy Badger mainly concentrates on privacy. For example, no ads will be blocked by Privacy Badger if they are not tracking the user. However, trackers will be blocked by Privacy Badger by default. Privacy Badger is purely a tracker blocker.
You can install Privacy Badger by visiting https://privacybadger.org and clicking on the respective browser. Privacy Badger supports a range of popular browsers, including Google Chrome, Mozilla Firefox, Opera, and Edge.
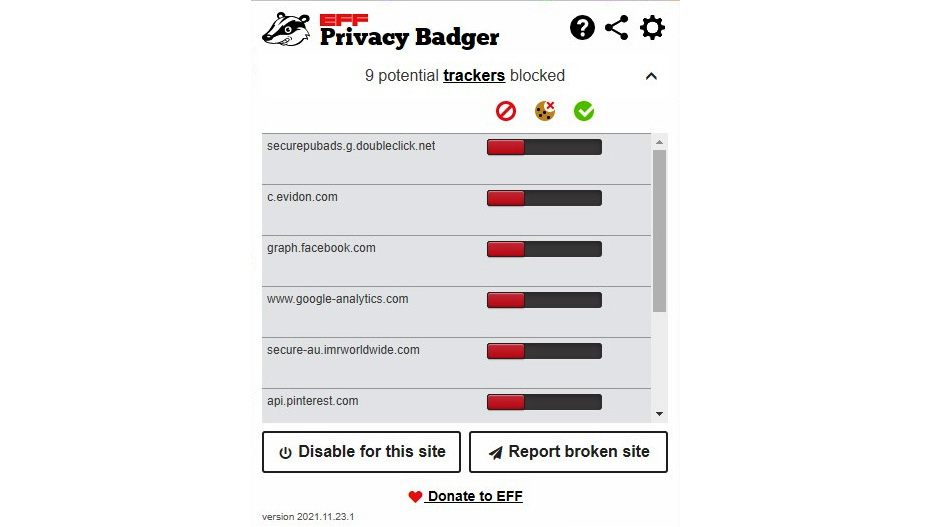
Figure 9.8 – Privacy Badger blocks trackers by default
Privacy Badger supports Global Privacy Control (GPC) – a specification that provides control to users to notify companies that they would like to opt out of them keeping, sharing, or selling their data. Privacy Badger supports GPC by sending every company that users are interacting with a do not track (DNT) signal. When DNT was developed, most companies simply ignored it, so the Privacy Badger browser extension acts as an enforcer of the DNT signal.
Privacy Badger is very easy to configure; it blocks a range of trackers, including invisible trackers. It will not block ads if they are not tracking you, although it is capable of blocking a range of ads. The only drawback of Privacy Badger is that is consumes a noticeable amount of memory.
- AdGuard – AdGuard is a collection of open source, free, and shareware products developed by a Moscow-based software development company known as AdGuard Software Limited. One of the AdGuard apps, ApGuard DNS, supports Microsoft Windows, macOS, Linux, iOS, and Android. AdGuard also has a browser extension. It operates with a large number of filters that includes over 5,000 rules, which ensures that no information is collected without user permission. AdGuard blocks ads, trackers, and other types of tools that are designed to collect user data.
Figure 9.9 – The AdGuard range of products to improve privacy
AdGuard has different offerings, including browser extensions to improve privacy. AdGuard has been developed as a desktop application with a range of features, including the following:
- Ad blocking – blocks all kinds of ads.
- Safe browsing – protection against malware. AdGuard checks each web page you surf for malware.
- Privacy protection – AdGuard protects you from all kinds of trackers and analytical systems that have been developed to spy on you.
- Parental control – AdGuard protects children online by removing obscene material and blocking inappropriate websites, and it provides parents with a customizable block list.
- Protect personnel data – AdGuard has a dedicated module developed to protect your data.
- Disguise your presence online – AdGuard supports not only hiding your online presence but also, if required, disguising your online presence and browsing anonymously.
You can download the AdGuard browser extension at https://adguard.com/en/adguard-browser-extension/overview.html. This is AdGuard’s lite version that effectively blocks all types of ads and allows safe, fast, and ad-free browsing.
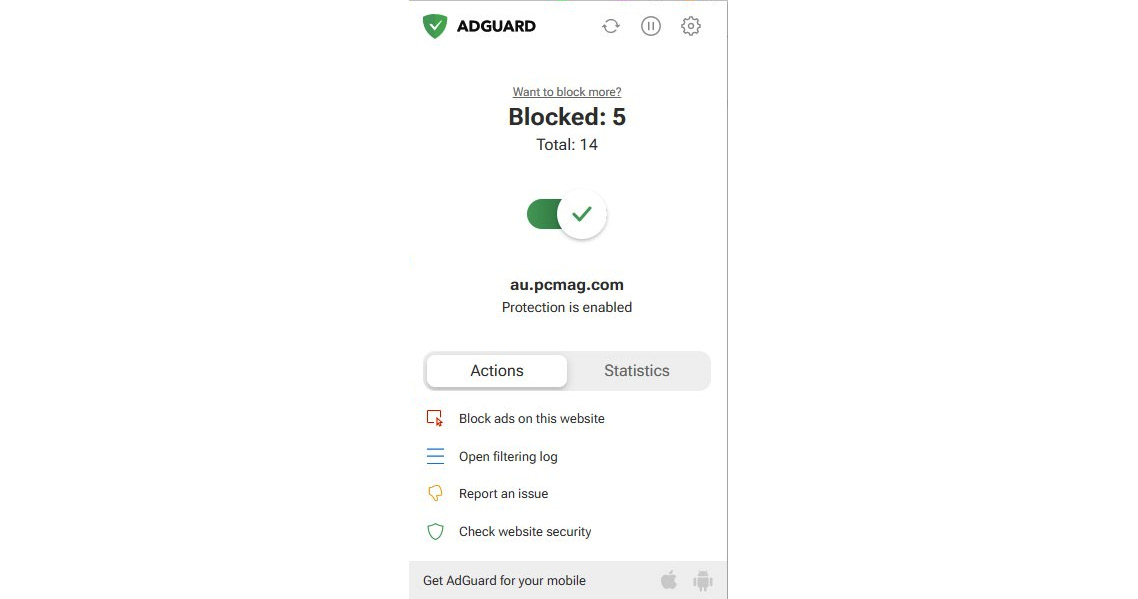
Figure 9.10 – The AdGuard browser extension to block ads
AdGuard provides you with a range of actions through its browser extension to block ads on a specific website straight away, and you can check the security of the website. When you click on the Check website security option, it will redirect you to AdGuard’s security report of the respective site. AdGuard maintains a database of websites that can produce security reports. A report contains the trustworthiness of the site, child safety settings, and other information related to safe browsing indexes maintained by Google and Yandex. If you go to the statistics, it will show you how many websites were blocked in the past. AdGuard maintains a filtering log that has real-time information about filtering.
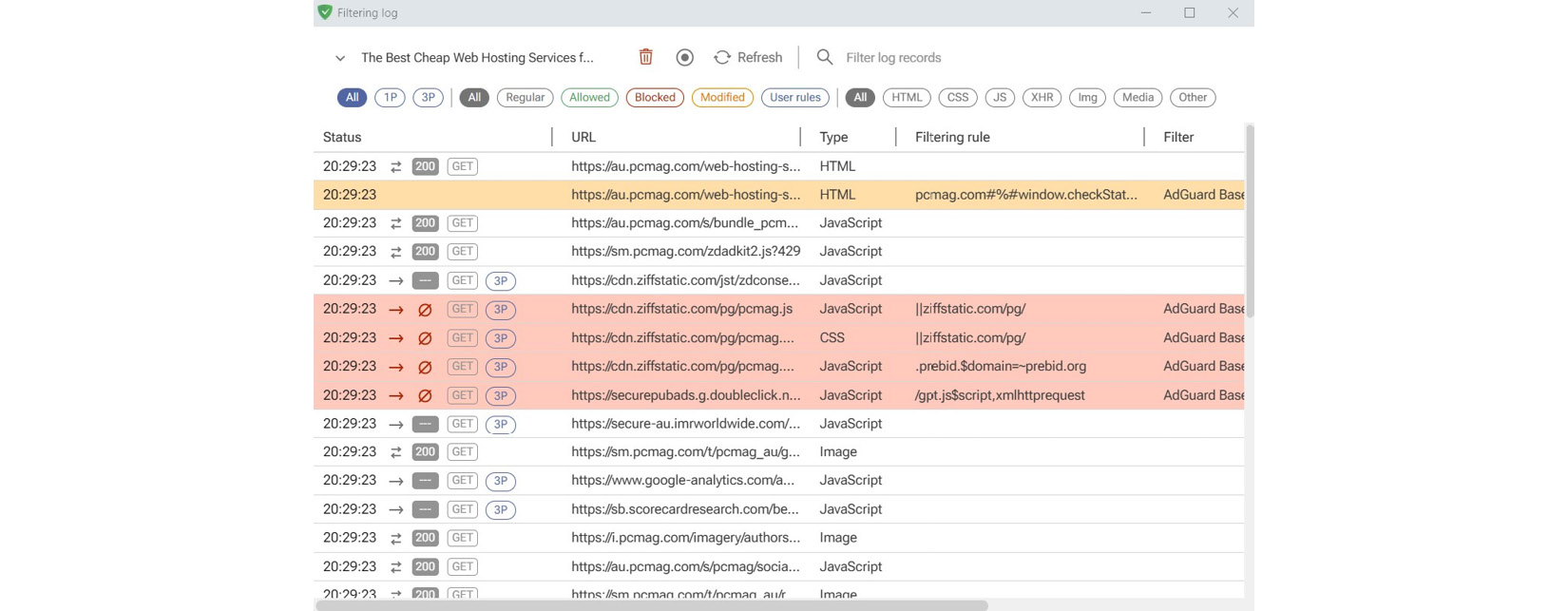
Figure 9.11 – The AdGuard filtering log
When you click on the filtering log, it will show you the real-time status of the filtering, including AdGuard filters and filtering rules. This shows you how many trackers and ads were blocked by AdGuard.
AdGuard also provides a desktop application that you can install on Windows, Android, iOS, or macOS devices to protect you from privacy-related attacks.
Anti-tracking software
In previous topics, we discussed various types of browser extensions that can be used while browsing to block trackers and ads. Sometimes, users might accidentally allow some trackers and ads while browsing. In that case, simple browser extensions might not be effective. Then, another option is to block trackers and ads from other possible layers. Anti-tracking software can be the option for these types of cases:
- DuckDuckGo – DuckDuckGo is a popular internet search engine among the security community that emphasizes protecting searchers’ privacy and completely avoids filtering the scope of personalized results. DuckDuckGo empowers users to seamlessly control their personal information online without any trade-offs. DuckDuckGo offers a no-cookie incognito mode, which does not allow cookies to track user activities in incognito mode. DuckDuckGo allows users to access the internet without being tracked or traced.
DuckDuckGo is a search engine and a browser that keeps your data safe and unreachable from advertising companies that use your personal data for advertising purposes. DuckDuckGo also offers a browser extension mode where you can very easily integrate DuckDuckGo into the browser of your choice. When it comes to performance, DuckDuckGo provides faster access, as it disables ads, cookies, and traces and provides complete anonymity. DuckDuckGo comes with an attractive user interface that allows users to access any website without being tracked. As we discussed before, many websites track user data, location, and cookies to collect a lot of information. But with DuckDuckGo, your privacy will be ensured while you are surfing the web. Some users find DuckDuckGo search results are not always accurate, the reason being that DuckDuckGo is not using your private data to refine the results any further.
If you access https://duckduckgo.com, you can add DuckDuckGo to your browser as an extension.

Figure 9.12 – The DuckDuckGo search engine and browser extension
Adding DuckDuckGo as a browser extension is straightforward, as we discussed earlier. But if you need to install DuckDuckGo as an app, you need to visit https://duckduckgo.com/app and install it on the specific operating system that you are using. DuckDuckGo not only protects your privacy by blocking trackers and ads but also forces websites to establish encrypted connections, when possible, to protect users’ data that is communicated between the browser and the server.
- Cliqz – Similar to DuckDuckGo, Cliqz is a web browser and a search engine, and provides privacy-oriented services developed by Cliqz GmbH and Hubert Burda Media. Cliqz is available as a desktop application as well as a browser extension. Cliqz provides quick searches with privacy optimization and offers anti-tracking and anti-phishing for a range of operating systems, including Windows, Android, Mac, iOS, and Firefox.
Cliqz works as a first-class doorman, protecting you from unwittingly revealing your data. Just like a doorman, the software only gives access to you, not trackers, ads, and other adversaries. Cliqz comes with anti-tracking, ad-blocker, and anti-phishing capabilities. Cliqz also offers encryption to protect you from sniffing and man-in-the-middle attacks. Cliqz claims that it never collects user data, and its certification company, TUV, has approved Cliqz's architecture in terms of data protection. The Cliqz browser and all integrated function modules are open source. You can download Cliqz by accessing https://downloads.cliqz.com/CliqzInstaller-en.exe. It is also available in the Mac, iOS, Android, and Amazon app stores.
- Brave – Brave is a free and open source browser that was developed with security in mind. We discussed the Brave browser in a previous chapter.
- AdGuard desktop app – We discussed the AdGuard browser extension previously. You can get the AdGuard desktop app by accessing https://adguard.com/en/welcome.html.
- Avast AntiTrack Premium – You can download Avast AntiTrack Premium by accessing https://www.avast.com/en-au/antitrack#pc. Avast AntiTrack Premium blocks trackers from collecting and sharing user data, hides users’ online footprints, avoids targeted ads and price manipulation, and provides faster and safer seamless browsing on a range of browsers, including Chrome, Edge, Opera, and Firefox. Avast AntiTrack Premium uses a disguised user profile technique, which masks a user’s digital footprint, preventing advertisers from identifying who you are. Avast AntiTrack Premium provides seamless browsing without any disruptions such as breaking web pages and annoying alerts. Some web pages can break when you enable anti-tracking browser extensions. Avast AntiTrack Premium helps to access any web page without breaking and hides your online footprint and browsing history. Avast AntiTrack Premium automatically clears users’ histories, cookies, and browsing data.
Avast AntiTrack Premium was developed initially as an antivirus software that is user-friendly, and it provides an exclusive summary of trackers blocked by the software. Another feature that comes with Avast AntiTrack Premium is an app that supports anonymous browsing, preventing trackers and data collection while surfing the web. This is also capable of effectively blocking a range of scripts that try to collect and track information. The program automatically changes a user’s digital footprint to maintain anonymity after deleting tracking attempts.
- Tor – Tor is the best of the free browsers and anti-tracking software. It is available on Windows, Mac, and Linux platforms and uses anonymous proxies to maintain a high level of anonymity, which we will be discussing in detail in the next chapter.
Browser extensions and anti-tracking applications can protect websites from tracking and collecting information from you.
When you access web applications and sites, they create cookies in a browser; some cookies are direct cookies, while other cookies are third-party cookies that collect and share information about you with third parties. While avoiding tracking apps and protecting ourselves using browser extensions and anti-tracking tools allows us to surf the web safely, there can still be cookies and scripts created within a browser when you access web applications and websites to collect information about you. Sometimes, attackers and advertising companies can be very tricksy. They might use legitimate websites to store scripts, cookies, and other tracking components within browsers when you access the web. The solution is to use tracking-removal tools to remove cookies and temporary files created when web browsing. There are different kinds of tracking-removal tools available to do this, but some tools can also track you to collect information. Most of these tools are commercial tools, but they also offer free versions with limited features:
- CCleaner – CCleaner is one of the best tracking-removal tools available and provides a simple yet effective way of removing cookies, temporary files, recently opened documents, and web history on all web browsers. Even if you use multiple web browsers, CCleaner can remove temporary files created on all browsers in one go. As well as removing the tracking-related files on the system, CCleaner removes unnecessary temporary and log files, which makes a device operate much faster. As well as removing items from your device cookies, junk files, cache, and temporary files, it also helps to remove persistent malware that may have been stored on your system. There are two versions of CCleaner, a free version and a professional version; the free version is good enough for our purposes. You can download CCleaner from https://www.ccleaner.com/ccleaner/download.
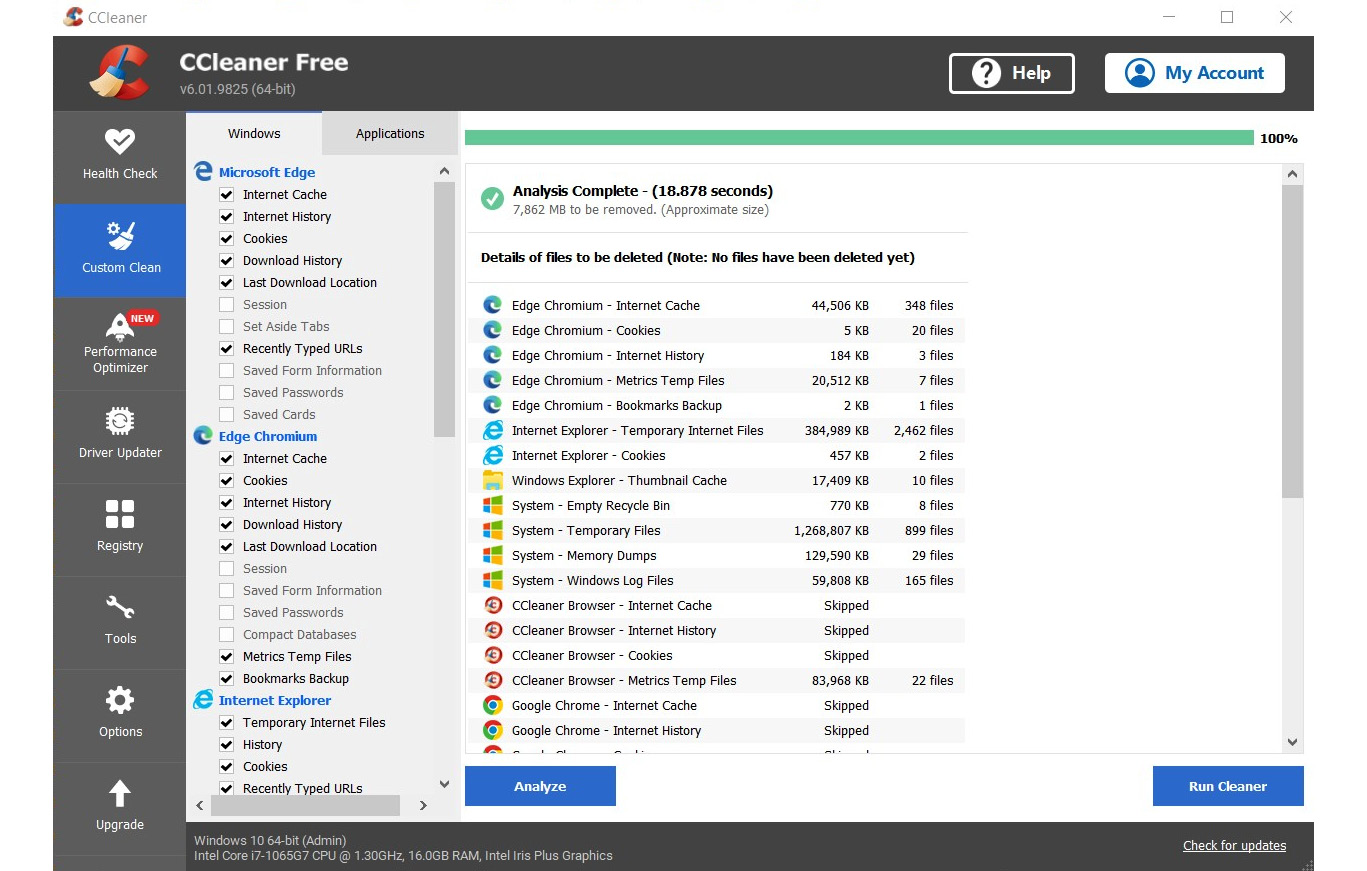
Figure 9.13 – CCleaner scans and removes temporary files created in browsers
As the preceding figure shows, CCleaner scans all the browsers installed on a system, analyzes the files, and prompts you for action. If you want, you can run the cleaner to clean the files from the system with just one click. It also includes a special browser that can be used without tracking. While the professional version provides a wider range of features, the free version provides interesting features, including a PC health check that automatically analyzes, tunes, and fixes device performance, an app controller that increases the performance of a device, and privacy protection that removes tracking and browsing data.
- SUPERAntiSpyware – SUPERAntiSpyware is an AI-powered software that can detect and remove potentially harmful tools, trackers, and software applications from your system, including malware, keyloggers, hijackers, rootkits, Trojans, spyware, adware, ransomware, worms, and potentially unwanted programs (PUPs). If you are using Microsoft Defender, which is built in as the antivirus solution in Windows operating systems, SUPERAntiSpyware can boost it. This tool was developed to work with existing antivirus programs, and it will not slow down a system, as it uses a very small amount of your hardware resources.
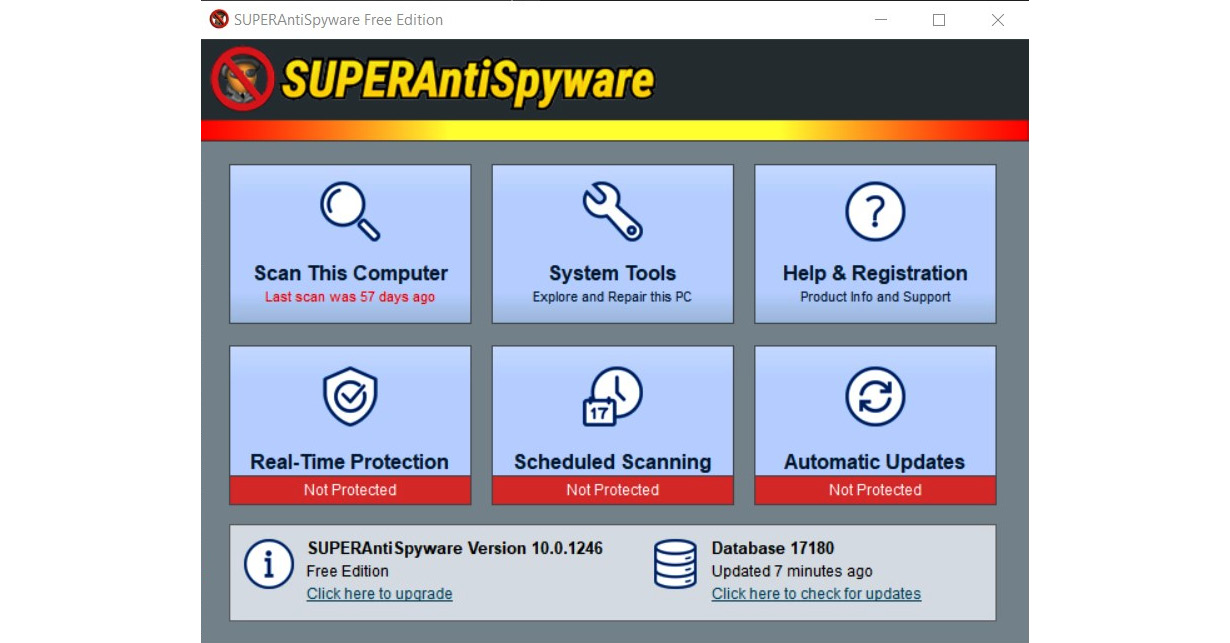
Figure 9.14 – SUPERAntiSpyware scans a computer for harmful files
You can download SUPERAntiSpyware at https://www.superantispyware.com. SUPERAntiSpyware has a free version and an AI-powered Professional X edition. Even the free version is good enough for tracking removal, but the Professional X version has an attractive set of features not included in the free version, including an AI-backed, real-time scanning engine that is capable of blocking over 1 billion malicious threats, securely deleting malicious files, analyzing a system in depth, cleaning up browser cookies and popups, and stopping ransomware and trackers.
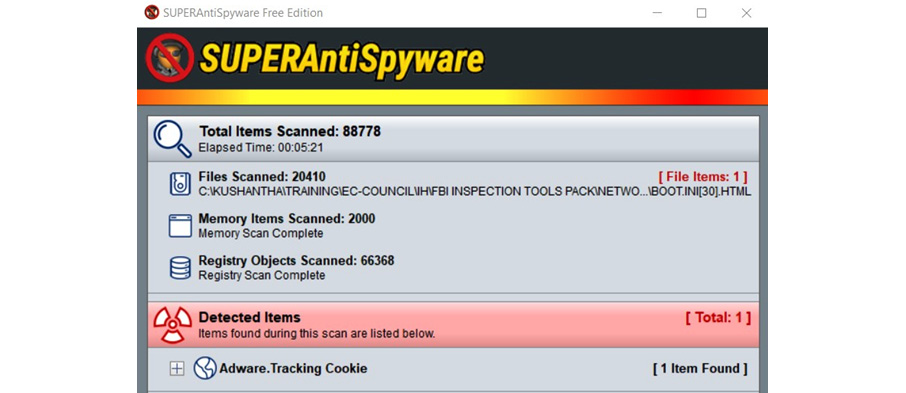
Figure 9.15 – SUPERAntiSpyware scans and removes PUPs
SUPERAntiSpyware can be a very effective tool to remove trackers, including adware and potentially harmful software.
Using secure messaging apps
In the previous topic, we discuss how to avoid browsers and applications from tracking our online behavior. Most browsers and applications track us without our knowledge or consent. Another area to concentrate on when it comes to privacy is communication and collaboration. We typically share private and personal information with our loved ones and people we trust. Communication and collaboration play major roles today, as everyone is connected virtually with each other by various applications, irrespective of geographic location. Traditionally, people met in person to maintain social networks. This was followed by telephone communication.
In today’s world, various communication applications and social media are the main ways we maintain social networks. Users typically perform one-to-one communication or one-to-many communications, using various communication tools. These communication tools support video-, audio-, and text-based communication with one recipient at a time, known as a private chat, or with many recipients at a time, called group communication. Typically, these communications can often include personal, private, and confidential information shared with the recipients. Mainly, we need to understand who we are communicating with, especially when communicating in a group.
Sometimes, there can be users in a group that we assume we can trust, but there can be complete strangers in the same group. For example, I have a practice of saving numbers on my phone whenever I receive a call from an unknown number for the first time. I can then call the person back later or identify the same caller next time. Let’s say I get a call from someone that was a student when I taught certified ethical hacker training in Australia, and his name is John. I would save his number as “John CEH student Australia.” When he phones me the next time, I know that it’s him. If the same student phoned me again from a different number – using multiple numbers is common these days – I will save the second number under the same contact. Now, I have two numbers saved under the “John CEH student Australia” contact. Let’s say I need to create a group known as “CEH students Australia.” Using my chatting application, I will create a group and add contacts to the group. Now, I believe all the contacts in the “CEH students Australia” group are students who were attendees of my certified ethical hacker training. But what if John had use one of his friends’ mobile phones to call me in the second instance? I assumed both numbers are owned by John; that’s the reason I saved both numbers under his name. But the second number is someone else’s. If I start sharing confidential information, assuming all the contacts in the group are trustworthy, I’m making a mistake.
This can happen to anyone, especially with large groups. When it comes to maintaining privacy on communication and collaboration apps and tools in cyberspace, we need to look at these areas. Otherwise, we will be compromising our privacy on these apps. Users have a responsibility when it comes to communication and the application has a responsibility as well.
When dealing with chatting and collaborating apps, we need to look at two aspects:
- One is securing the contacts properly and validating them before we start disseminating information about groups.
- The second aspect is using a secure communication app for communication.
When it comes to communication and collaboration there is a range of apps available that support multiple operating systems, including Windows, Mac, and Linux desktop operating systems and Android, iOS, and Windows mobile operating systems. Messaging apps provide a range of communication and collaboration capabilities, including simple chat, video and audio communication, file sharing, screen sharing, group communication, and location sharing. Typically, messaging apps provide an easy way of maintaining social relationships with colleagues and keeping in touch with family and friends. However, while providing a range of benefits, we need to be aware of online privacy and security concerns related to messaging apps.
When it comes to privacy and security, the potential violations and concerns are as follows:
- Third parties may have access to and can read messages.
- Companies who introduce apps can read and have access to messages.
- Companies who introduce apps can collect information about the users.
- Governments uses apps to collect data about the users and the contents of their messages.
- Interception of communications.
- Access to shared files within the apps by companies and third parties.
- Data collected, including live location information of the users.
To avoid these privacy concerns, we need to evaluate messaging apps before we start using them for communication and collaboration. There are many apps available in all the app stores, including Microsoft Store, Google Play Store, Apple Store, Amazon Store, and desktop app stores, that support communication and collaboration. There are commercial and free apps available for this purpose. Some apps are even open source, developed by communities, and their source code is available to the public. When evaluating these apps for privacy and security, the key considerations should be the following:
- End-to-end encryption – this is when messages can only be read and understood by the sender and the recipient.
- Privacy policy – what does the privacy policy of the app specify it does to protect the privacy of the users?
- Storage encryption – whether the storage of the app is encrypted.
- Status of the source code – is the source code openly available for experts and communities to review to see whether any segments of the code are malicious?
- Use of data – even if the app provides E2E encryption, companies can still collect your data, including locations, duration of communications, device types, and phone numbers.
- Privacy features (self-destruction messages) – users can set a timer for a message to disappear from communication after a preconfigured time. Even when sending an image, users can decide the amount of time it will be displayed before disappearing from a chat.
Encryption
While discussing various ways to maintain anonymity, we looked at how to improve privacy. When it comes to privacy, encryption is a technology or process that we can never exclude. Simply, we cannot talk about privacy in cyberspace without encryption. I’m providing a basic explanation about encryption here to help us understand more about the technologies we can use to improve privacy. Encryption is a process that encodes information so that it can only be accessible by authorized users. Encryption converts human-readable plain text (in encryption, plain text refers to information in a raw format or its original representation) to ciphertext (ciphertext is a converted alternative format that cannot be read or understood by humans), which can only be deciphered as plain text by authorized parties. For this purpose, an algorithm is commonly used to cipher and decipher the text. Since everyone uses industry-standard algorithms, users can use a key to encrypt the message. If a user needs to decrypt the message, they require the key.
There are two versions of encryption:
- Symmetric encryption – when using symmetric encryption, the same key will be used to convert plain text to ciphertext and vice versa. Symmetric encryption is commonly used to encrypt stored data. Typically, the same user will encrypt and decrypt the data. The challenge when using symmetric encryption to secure data in transit is sharing the key because, without it, the recipient will not be able to decipher the data.
- Asymmetric encryption – when using asymmetric encryption, two keys, a “public key” and a “private key,” are used to encrypt and decrypt messages. The public key will be distributed among other users while the private key is kept with the original user. When using asymmetric encryption, if one key is used to encrypt a message, the other key of the same key pair can be used to decrypt the message and vice versa. Typically, asymmetric encryption is used to secure data in transit, as symmetric encryption is not practically viable for data in transit, where key sharing between a sender and receiver is a challenge. To implement asymmetric encryption, the keys first must be distributed among the participants for communication. Typically, this is done using digital certificates. Public key infrastructure is a term commonly used for an environment that is ready for asymmetric encryption.
When using messaging tools, users don’t have to enter keys to encrypt and decrypt data, as it will be managed by the messaging software in the background.
As we discussed, there are many messaging apps available in app stores that support many operating systems, including mobile operating systems such as Android and iOS, and desktop operating systems such as Windows and Mac. Even though all messaging apps provide similar capabilities, some apps have been proven to be more secure than others and provide users with a higher level of privacy. Let’s look at some of the popular messaging apps to see the level of privacy that they provide and what the weak messaging apps are when it comes to privacy and anonymity:
- Signal – Signal is a messaging tool that supports cross-platform and E2E encryption for voice and text messages. Signal has a reputation as the most secure messaging app in the industry. It is a free app that is available on a range of platforms, including Windows, Mac, and Linux. As with most messaging tools, Signal requires a phone number to use it. Signal was founded in 2013 but received its highest attention in 2020/2021 when WhatsApp released an updated privacy policy about using user data. Signal is not owned by a large tech company, so they do not rely on ads or targeted marketing. All types of conversations on Signal are, by default, covered by E2E encryption, which means no one, including the company, will have access to conversations except the users who are part of them. Signal also provides self-destructive messages and strives not to collect any information about the user, so the data is only stored on their local device. Due to stronger security, other apps including WhatsApp use Signal’s strong messaging protocol for their most secure modes.
- Telegram – This was introduced in 2013 by Russian entrepreneur Pavel Durov and supports multiple operating systems, providing similar types of functionalities as other messenger apps. Telegram provides E2E encryption; not even companies, governments, third parties, or hackers have access to messages, only the users in the conversation. This feature is available when Telegram clients call each other, but there isn't a “secret chat” feature. Telegram's extended usage of cloud services to store data means that it stores your chats and files on a secure server, so users can retrieve them easily using any device or operating system. There is an option to “self-destruct” messages when using Telegram; videos and photos can be sent to a recipient with a predefined time to self-destruct once the recipient has received the message. Another favorable feature that Telegrams offers is, once you deactivate your account or are inactive for a certain period, typically 6 months, your account information, including chats and files stored on the secure server, will self-destruct.
- WhatsApp – this app does not require any introduction, as over 1.5 billion users worldwide use WhatsApp. WhatsApp was one of the first apps to introduce E2E encryption to provide privacy, but when WhatsApp was acquired by Facebook, it introduced some level of suspicion regarding the privacy of users. WhatsApp doesn’t store information on the WhatsApp servers and allows iOS and Android users to back up messages on the cloud. WhatsApp is owned by Facebook, so data is shared with advertisers for targeted ads.
- Viber – Viber is another popular chatting app operated by a large Japanese company, Ratuken. Users can make phone calls and video calls using Viber. It supports up to 250 users in a group. Viber supports encrypted voice and video calls. Initially, it only supported one-to-one communication encryption, but now it supports encrypted group communication. Viber shows the level of encryption by a color code. When communication is encrypted, Viber shows a green color; a gray color shows communication is encrypted but the contact is not marked as trusted. Red shows failure to authenticate the contact.
- Line – Line is a free communication app, introduced by Japanese internet company Naver for its own staff after the 2004 tsunami. Even though it was introduced to the public in Japan, the later popularity of Line took the app international. Line offers E2E encryption, and users can use the phone number they use to log in to Facebook to register on the app. One of its advantages is that users can communicate without disclosing their contact numbers. That gives users a kind of privacy where they can communicate with people only using their Line ID. In some countries, the Line app provides the capability to find nearby users of the same app with its “Near me” feature, where users can scan and initiate communication with people nearby without disclosing their contact numbers.
- Wire – Wire was introduced by a Switzerland-based company and claims to be a very secure messaging app. Switzerland is generally considered a country with very strict privacy laws. This is one of the reasons that Wire is considered a secure messaging app when it comes to privacy concerns. Wire is also available on Android, iOS, macOS, Windows, and web-based apps, and works on most of the popular browsers. Wire always uses E2E encryption and has an open source messaging app that is available on GitHub to audit if required. Wire only requires an email address for registration; a phone number is not a requirement. Wire also claims that it doesn’t collect or sell analytical data of Wire users to third parties.
- Threema – Threema is another messaging app that does not require an email address or phone number to register, which is a big plus point when it comes to anonymity. Threema provides all the standard features of a communication app, including voice, video, and group chat. Threema is not a free tool; it has a one-time fee that users need to pay, and they can then use the app forever. Threema is also an open source communication app that provides E2E encryption so that only the sender and receiver can view messages. It does not require any of your personal data and was developed with protection and privacy in mind. Threema generates very little metadata and is claimed to be totally Swiss-made and General Data Protection Regulation Act (GDPR)-compliant. Threema is even available in on-premises mode, so companies can have their own secure communication tool, and nothing will be shared externally.
- Wickr Me – founded by a set of security researchers, Wickr Me is the only tool to provide true anonymity. There are a few versions of Wickr aimed at various audiences, such as as Wickr Pro, Wickr RAM, and Wickr Me. The latter is the app they designed for personal users. Wickr Me doesn’t require a phone number or email address to register and does not collect data about users. Wickr Me is more of a collaboration app than a communication tool, as it allows you to share screens and your location with your contacts. Wickr Me provides full E2E encryption for all communications, including videos and pictures. All data is locally encrypted within a device; no one has access to the stored data except the users. Wickr Me offers E2E encryption by default, removes metadata from communication so that files will not transmit with metadata, and has an open source app that offers self-destructing messages. Wickr supports multifactor authentication and does not log or collect user information, including IP addresses.
- Dust – Dust provides users with the opportunity to delete previously sent messages, so messages can be deleted from other mobile phones even after delivering the message. Nothing will permanently be stored in its servers or local devices. They provide E2E encryption for communication. Dust also provides self-destructive messages, allows you to send private messages to your contacts, and you can send messages to a group that are delivered as individual private messages (known as “blasts”). Another interesting feature is that whenever a recipient takes a screenshot using the app, the sender will be notified. In addition to the security and privacy features of Dust, it also offers a privacy protection feature when you surf the web and allows you to implement stealth searching.
- iMessage – iMessage is Apple’s proprietary messaging service and is only available on Apple platforms such as iOS, macOS and iPadOS, providing E2E encryption between users. As with WhatsApp, iMessage provides you with an option to back up messages to iCloud. This can be a bit tricky, as iCloud backup uses encryption keys managed by Apple. In other words, anyone who compromises your iCloud could access backed-up iMessage data. iMessage has a few interesting features, such as being able to define how long a picture or video should appear before it self-destructs and the number of times that recipients can view it before it is gone.
These are the most popular messaging apps that are available on the most popular platforms. They have their own pros and cons when it comes to privacy. Depending on your requirements or required level of privacy and anonymity, you can decide which app suits you. Open source apps can typically be trusted, as they maintain a high level of transparency.
Using disposable emails and contact numbers
One of the common ways of exposing ourselves in cyberspace is via emails and contact numbers. For example, there are many requirements to share our email address, contact number, or both to receive activation links, download e-books, access various services, and so on. When we share our email address or contact numbers, companies or attackers use them for various types of malicious purposes. Some companies sell collected information to advertising and marketing companies. Some attackers misuse this information and use it for other attacks.
We need to know the ways to protect ourselves against these attacks without exposing our private email addresses and contact numbers. But this becomes an issue when we need to provide a contact number or email address to gain access to these services. The solution to this is to use virtual numbers and throwaway email addresses. Some services providers such as Yahoo.com provide throwaway email addresses, similar to an alias; once your communication with the service is over, you can disable the email addresses so that they are no longer available for communication.
Another option is using disposable email address. Many disposable email address providers provide disposable email addresses to receive emails temporarily without registration. These email addresses are available either for a certain temporary period or until you refresh the browser. You can just use these email addresses to receive emails or any sort of information, and then you can just forget about them. This is a good way of receiving activation links or download links. Once you have received the link, you can access content without disclosing your real email address, so even if an attacker or company shares or sells this email address, it doesn’t matter. However, if you need to reuse the email address, then you need to again register on the services, although most services are available without registration.
The following is a list of disposable email service providers:
- www.mailinator.com
- www.10minutemail.com
- www.temp-mail.org
- www.guerrillamail.com
- www.mohmal.com
- www.throwawaymail.com
If you visit www.temp-mail.org, it automatically generates a disposable email address that can be used to receive any activation link or download link.

Figure 9.16 – Disposable email address to receive emails
This will prevent attackers from collecting authentic email addresses using different tricks, including providing you with interesting links and registering you on their websites. Once you have used the temporary email address, you can just close the browser.
Keeping your personal contact number safe is extremely important today, as many services use your number to identify and authenticate you. In the past, contact numbers kept on changing. When you moved from one service provider to another, your contact number changed, and when you moved from one city to another, your number changed; it was like your postal address, which changed when you moved from one house to another. But now, in most countries, your contact number is like your passport number or identity number, which never changes. In most countries, you can even change a service provider or phone package without changing the number. Some countries, such as Australia, even have government services that authenticate you by a contact number. When you call them, their systems automatically identify your number, and they can access your information. This makes the contact number more sensitive to privacy breaches than ever before.
If you need to provide a contact number to receive a one-time password (OTP) or code, then there are multiple options available that allow you to do so without disclosing your real contact number. There are many online and free SMS receiving services to use. First, let’s look at free online services that can be accessible without any registration over a browser:
- https://receive-sms-online.info/
- https://receive-smss.com/
- https://smsreceivefree.com/
- https://pingme.tel/
- https://www.freereceivesms.com/en/au/
- https://www.receivesms.co/
- https://receive-sms.cc/
All these services provide a similar service; once you access one of the preceding links, you typically need to select the country in which you want to receive the message. For example, receive-SMS-online.info is a free service based on a real SIM and shows the content of the SMS messages you receive to a SIM via a web interface. These numbers are based on real SIMs, but the contents of the messages are shown publicly. If you want to receive a code or OTP, you can use online SMS receiving services. Most of the services do not filter or restrict anything. Since the numbers that these services use are publicly available, some services might have already used them.
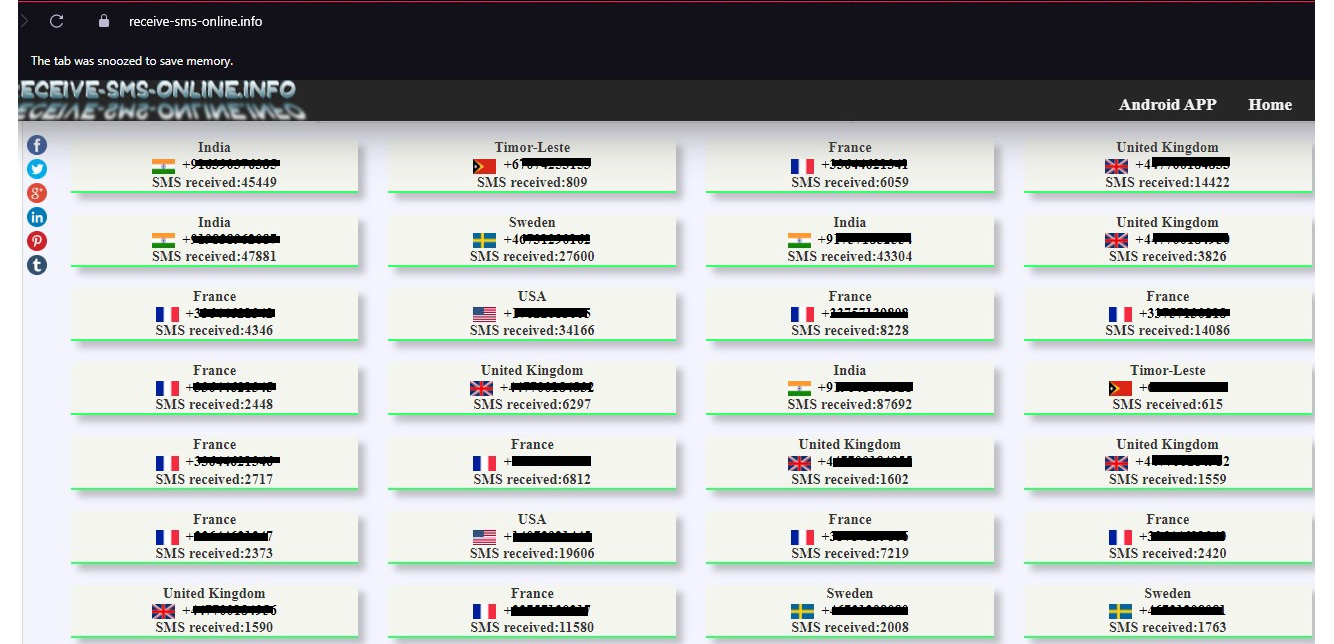
Figure 9.17 – Receiving an SMS for any country
When you access one of the links given previously, you will need to select the country in which you would like to use the number. You can decide based on the country or the number that you would like to use. Once selected, you will be redirected to a web page that receives SMS messages for the selected number.
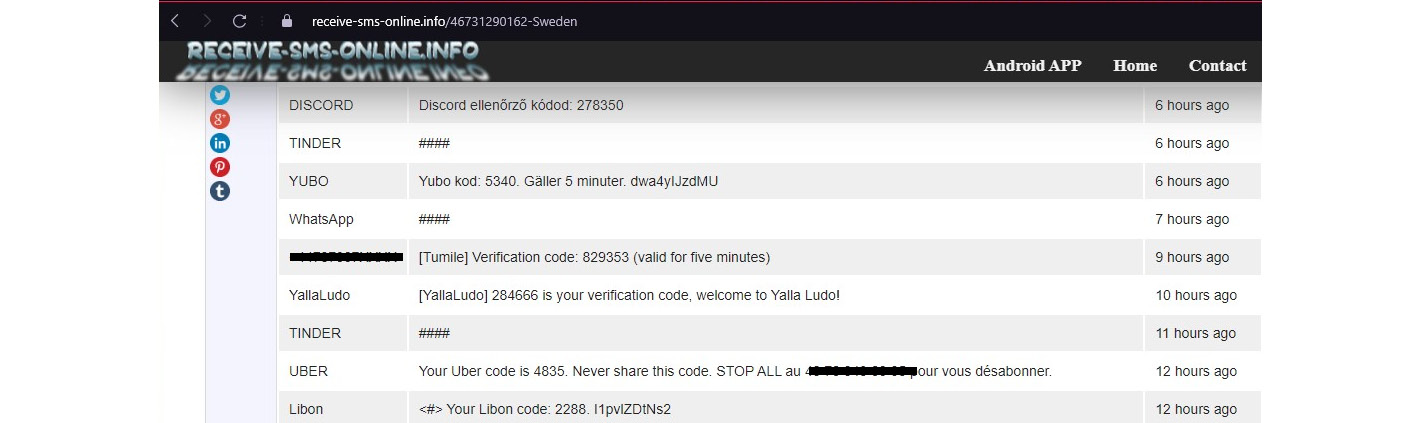
Figure 9.18 – Receiving an SMS for any country
Then, you will see the messages received by the number on the web page; when you use this number on any service, it will display the messages sent to the number publicly. The disadvantage is that all the messages sent to this number will be visible to the public. For some requirements, it’s okay to receive messages publicly, as only you can use the code sent to the number for a specific service.
Burner phone
We need a contact number for various reasons, including contacting an emergency service, catching up with family and friends, contacting for official purposes, business requirements, registering with various services, and banking and tax purposes. On top of that, if you want to sell something online or wanted to sell your car, you advertise information with a contact number so that buyers can reach you. When you do this, not only buyers but also various adversaries can get your number easily. Then, you will start receiving promotional calls and text messages, as there are companies that deliberately collect contact numbers for advertising purposes, which is annoying.
Let’s say you wanted to register on a dating app and use your contact number. If you use your permanent number, if you change your mind and deactivate your account, the people you connected with on the dating site can still reach you with your number. Sometimes, attackers can even use your number for other attacks. Another problem is that when you use a smartphone, your phone number is integrated with various apps, including messaging apps. Once people get your number, they can search for you on popular apps such as WhatsApp, Line, and Viber. They also can find your profile pictures set up on these messaging apps and other information, depending on the app. This makes it easy for an attacker to gather information about you.
The solution to this issue is a burner phone. Usually, the term burner phone refers to a disposable phone with no contract number that is used for a temporary purpose. Typically, it is a prepaid mobile number with a super-cheap handset that you buy on the go, from a shop or supermarket. Some burner phones include a SIM for a certain call time. After the defined period is over, the number will expire. Mostly, these types of packages are used by tourists. For example, if you want to sell something on an online marketplace such as Facebook, you can use a burner phone. Once the item is sold, you can switch off the phone. Since you are using a prepaid number, it will not charge you on monthly basis. Whenever you need, you can top up and start using it. Some packages even support changing numbers. These cheap handsets don’t have an option to connect to the internet or install apps. You can usually only call and text using a burner phone. Once done with it, you can get rid of the phone and the number. A burner phone provides stronger privacy as it does not keep any metadata within it. When the phone and SIM are destroyed, there are no traces left.
Virtual numbers
As we discussed, freely available services can be used to receive messages without exposing your number, or you can use burner phones to maintain privacy. But if you don’t want others to see the message, you cannot use public SMS receiving services. If you already have an Android or iPhone, you might not want to carry another device, such as a burner phone, with you. Then, the only option available is a virtual number or second number that you can get on your phone.
There are many apps available in app stores that provide a second or temporary number for this purpose. When you download an app, you can obtain a number that can be used as a virtual number. You can use the virtual number to make or receive calls. You can also send or receive SMS messages, depending on the service that you subscribe to. Some services even provide temporary numbers that you can change from time to time:
- Burner – Burner is an app that is available for both Android phones and iPhones but is limited to US and Canadian numbers. It provides a 1-week trial, including 20 minutes of talk time and 60 text messages. If the plan is not upgraded, Burner will be disabled with the number. There are a few subscription plans offered with monthly and annual subscriptions. The Premium subscription offers three numbers with unlimited calls and texts within US and Canada. When you use Burner to call, you will be redirected through Burner, which is known as relaying. When someone calls you, in reality, they are calling Burner; then, they will be automatically relayed to your phone. The Burner app also provides app-level privacy where you can configure a PIN number to use Burner, which can also be integrated with built-in fingerprint or facial recognition on the phone. Burner also provides the option of selecting desired phone numbers from a given list. Using Burner, you can make and receive calls, and send and receive SMS messages.
- Flyp – Flyp is another virtual number app available on both Android and iOS. You can select five numbers based on area codes in the US and Canada. Every number gets unlimited calls and texts. Flyp provides a 7-day trial before you have to upgrade the app. Flyp has a great privacy feature where you can define who can call you back. You can create a list of contacts that can call and text you; calls from other numbers will be automatically blocked.
- 2ndLine – 2ndLine is available for Android phones. Once you install the app, you can select local numbers for the US and Canada with unlimited texts and talk time. Importantly, 2ndLine supports calling and sending text messages from your phone or tablet using your data or Wi-Fi connection. Once you have downloaded the app and picked a phone number, you can access calling and texting features. There is a list of numbers that you can select from. The number from 2ndLine is an additional line to your phone, so you don’t have to carry two mobile phones. The paid version provides affordable rates for international calling and texting. You will receive texts to the 2ndLine app, so you can separate personal and other numbers.
- Dingtone – Dingtone is available on both Android and iOS app stores, and you can use it as a second phone number, which provides you with unlimited texts and calling. Number reservation is free, and you can reserve multiple numbers. Dingtone provides business-grade telephone features such ass call forwarding, voicemails, and number blocking. Calling and texts are free within US and Canada and between Dingtone users. Dingtone uses data or Wi-Fi to operate. Dingtone provides affordable international calling rates.
- TextNow – TextNow can be easily used as a second phone number that provides free calling and text messages. TextNow is available in both Android and Apple app stores. TextNow uses data connectivity or Wi-Fi for its service, and you can select a number based on an area code or preferred number. TextNow offers a virtual mobile network service where you will receive a SIM card for the number, with free calls and texts within the US and Canada. This SIM comes with a data bundle that can be used to connect to the TextNow network. Especially for mobile phones with a dual SIM, this is an impressive option.
- CoverMe – CoverMe is another Android-based app that provides a virtual number to be used as a second number and secure communication over Voice over Internet Protocol (VOIP) or voice over data networks. CoverMe supports encrypted voice calls, which makes it a very secure app. It supports app-level security by configuring a PIN number. CoverMe works over a data network or Wi-Fi connection. It provides an encrypted secure storage vault on smartphones that cannot be accessed without a PIN number.
- Phoner – Phoner provides a range of additional features, including the ability to mask and hide your caller ID, call forwarding, and voicemails. Phoner is available in Android and iOS app stores and as a web-based application. You can select your second number from a series of randomized numbers. Phoner provides numbers from different countries, but the pricing differs from country to country. Phoner provides an option to send documents as faxes.
- Hushed – Hushed is a very popular virtual phone app that is available on both Android and iOS. Hushed provides virtual numbers for over 40 countries. Hushed uses data connectivity or Wi-Fi networks to operate, so you can start calling from anywhere where data connectivity is available, and it provides a 3-day free trial before you will need to upgrade to a paid plan. Pricing can be different based on the country of the number you selected.
- Google Voice – Google Voice is completely free, but it does not offer complete privacy. The main objective of Google Voice is to provide a second number for call routing. In other words, Google Voice can route calls to all your numbers. You get a permanent secondary number for free that can route calls to all your numbers, including your home number, office number, and mobile number. You can pick up calls from anywhere.
- Line2 – Line2 is designed for small companies or small teams and provides unlimited calls and text messages. Using Line2, you can build a cloud-based telephone solution irrespective of location. Line2 supports both Android and iOS and provides an extension for every team member so that they can call each other and transfer calls.
Using virtual machines and virtual applications
We discussed how we can create a virtual machine with proper network configuration in Chapter 8, Understanding the Scope of Access. Once you have created a virtual machine, it can be used for multiple purposes. Remember that virtual machines also work like physical machines on a network. When you check your virtual machine from the network perspective, there is not much difference between the physical machine and the virtual machine. Both will have IP addresses assigned, run an operating system, and have applications installed. When we concentrate on the privacy factor, it provides the advantage that we can revert the virtual machine to a previous state whenever we want, or we can simply reset the virtual machine every time we need to. It will look like we're using a new system every time we access the network.
Once you revert a virtual machine, all the trackers, cookies, and scripts that attackers plant will be removed from the system. From an attacker’s perspective, once you revert the virtual machine, your traces will have disappeared. Another advantage of using virtual machines is isolation. Even if your web surfing opens the door for malicious code or malware onto a system, you are still safe. Once you have reverted the virtual machine, they all will be removed. There are various virtualization platforms that you can use to build your virtual machine. It’s always a good idea to create a snapshot from the virtual machine so that you can revert to a previous state whenever you want. In Chapter 8, Understanding the Scope of Access I explained how to configure a VMware virtual machine.
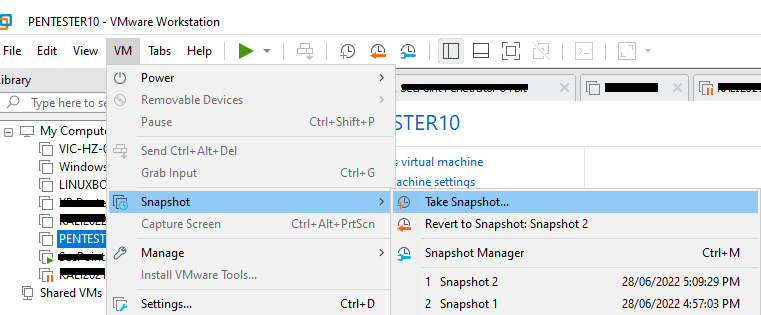
Figure 9.19 – Creating a snapshot of a virtual machine
You can create a snapshot easily on a VMware virtual machine. Just select the virtual machine, go to the VM menu, and select the Take Snapshot… option. This creates a snapshot of the virtual machine. As you can see in the preceding screenshot, there are two snapshots created.
Whenever you want to revert the virtual machine, you can simply go to the same menu and click on the Revert to Snapshot option. Then, the virtual machine will be restored to the previous state, clearing all the traces. This is an advantage of using virtual machines. In simple words, the virtual machine will not create additional protection for anonymity, as on the internet, what others see are packets. It doesn’t matter whether the access is virtual or physical in cyberspace. But virtual machines allow you to revert to a previous state, or in other words, every time you access the internet, it’s like a brand new entry without any previous states.
We previously discussed preventing tracing and ads at the browser or application level by using anti-tracking applications or browser extensions. Using virtual machines, we can prevent tracing at the operating system level. For example, if you create a snapshot just after the fresh installation of an operating system and then you access the internet, by reverting to a previous state, you can remove all the traces, cookies, temporary files, and caches created within the system within a few seconds. If, next time, you access the internet using the same virtual machine, there won’t be any traces of the previous access. In a worst-case scenario, you even have the option to delete the virtual machine completely and recreate another one with minimum effort, unlike rebuilding a physical machine. It’s like having a second machine; deleting and creating virtual machines do not have an impact on your daily activities and you won’t lose your important data.
As a best practice, what you can do is use your usual computer with browser extensions enabled to access the internet, and then you can clear the artifacts created in your device using CCleaner frequently. If there are any suspicious links or artifacts to check for, you can use your virtual machine.
Once we have taken actions to protect ourselves at the operating system level, then we can think of the application level. As we discussed, applications keep traces of our various activities. When it comes to applications related to privacy, there are two types of apps that we can consider:
- Portable applications
- Virtual desktops and applications
Portable applications
The term portable applications refers to applications or software that do not require any installation. In other words, all required files to run the software are typically stored in a single folder or single executable. You can even keep portable applications on a single USB drive, bringing all the required software wherever you go. Previously, you could carry all your software on a CD or DVD; as few people nowadays use CDs or DVDs, you can use a USB instead. Most importantly, you can use the applications and software on any computer and it will feel like it’s your computer, as all the required software is present on the USB. When it comes to privacy and anonymity, the best part is that portable software does not store any settings in the Windows registry. Portable software is fully functional like installed software, so we don’t have to worry about reduced functionality in portable software.
There are advantages to using portable applications for cyber anonymity, including the following:
- Installation is not required – since installation is not required, the footprint of the application on the device is considerably low. Since the portable applications use a single folder, they are easy to clear.
- No or minimum additional files – typically, portable software doesn’t need any additional files, as all the required dependency libraries are bundled with the portable application, except typical runtime files available on the operating system.
- No traces created – portable apps don’t keep or create artifacts or footprints on a device; they keep all artifacts and footprints within themselves. When you use the same USB stick with the app on another computer, you will see the artifacts still available on the portable app. If required, simply deleting the portable app or the folder containing the app will remove all the traces and artifacts created by the app, unlike installed apps.
- Easy to clean – since all required portable apps can be stored in a single USB stick, you can bring them wherever you travel, use them on any computer without creating any artifacts on the computer, and destroy all the traces by just deleting or formatting the USB stick properly.
Portable apps have become very popular due to these advantages, and now it’s not hard to find portable applications. Many of these portable applications can be located and downloaded for free from https://portableapps.com/apps. Portableapps.com offers its own app store, with a collection of apps to select from with proper categories, and you can launch an app straight away without any limitations. Alternatively, some leading software vendors offer portable versions of the same software. It is recommended to download portable apps from trustworthy sources as they may contain bundleware (bundleware is software that comes with additional software as a bundle, which can be malicious or dubious). Downloading from a direct software vendor or portableapps.com is recommended, as portableapps.com scans all the apps available on the site frequently with antivirus engines before publishing them on the site.
These portable apps can save you time while protecting you from traces created while surfing the web. A combination of these tools can be an ideal way of surfing the web. Let’s say you want to surf the web without leaving any traces of your presence. You can download the following portable apps to a sanitized USB stick:
- Opera GX portable edition – to access the internet on a faster and more reliable level.
- Eraser – remove and sanitize data without creating traces.
- USB Oblivion – this is an impressive app that removes all traces and evidence that are created in the USB drive that you connect to a Windows device. The reason is whenever you connect a USB to an external drive on a Windows device, it keeps track of the device, including device information. USB Oblivion removes this evidence, including registry entries created on the USB drive.
When you have these three portable apps, you can maintain anonymity while surfing the internet. Let’s imagine you have these portable apps on a sanitized USB stick. You can insert the USB stick on the physical machine and connect the drive to your virtual machine. It’s easy if you are using the VMware workstation that we created earlier. The only thing you need to do is connect the USB drive to the virtual machine.
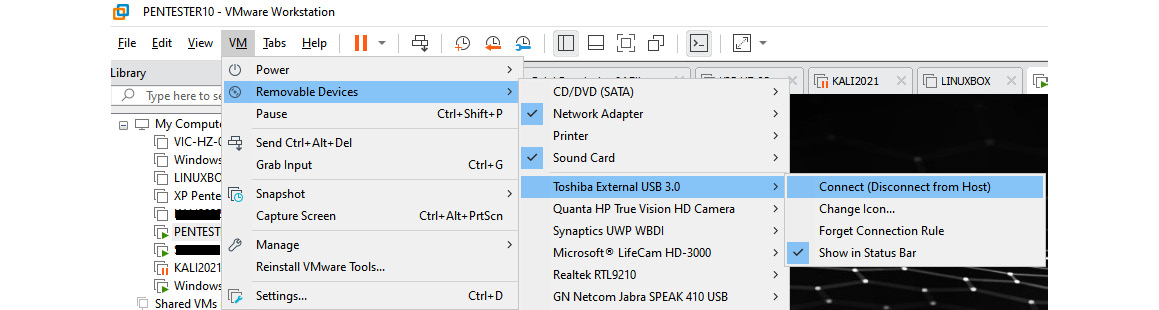
Figure 9.20 – Connecting a USB drive to a virtual machine
Once you have connected the USB drive to the virtual machine on the VMware workstation, you can log in to the virtual machine. When you go to File Explorer, you can access the drive. Then, you can access the folder that contains the Opera GX browser or any browser of your choice and open it within the virtual machine. This prevents any artifacts from being created on the virtual machine; even if they are created, we always can revert the virtual machine. Once you complete the work, you can run USB Oblivion to remove the traces created on the USB drive from the virtual machine. Later, if you want to, you can completely wipe the USB drive using Eraser.
There are many interesting portable applications that improve privacy and can be downloaded from portableapps.com, including the following:
- USB Oblivion – this will remove all traces of the USB drive you connected from the device.
- Eraser – the Eraser app can totally shred any data that you want to delete permanently.
- O&O ShutUp – this is a great small tool with which you can configure a range of settings, including tracking Windows 10 in a single window.
- BleachBit – BleachBit is pretty much like other history cleaners but provides more options to remove specific entries across a wide range.
- No Autorun – this tiny portable app prevents you from automatically executing scripts and applications when connecting USB drives to a device.
- fSekrit – fSekrit can save any text file you created encrypted with a password.
- HistoryView/MUICacheView – these portable apps can retrieve browsing history and recent items in a single window.
Virtual desktop and applications
Virtual applications are applications that are optimized to run in a virtualized environment, typically without the requirement to be installed first. An application can reside on the cloud or on-premises but execute on the local device. Using virtual apps provides user privacy and safety, as data will not be stored locally. There are different ways of providing application virtualization. Desktop and application virtualization provides an extra layer of security. In today’s world with complex requirements in personal and enterprise systems, virtualization is the best way to handle safety and privacy. On personal and enterprise systems, we have different device form factors such as laptops, desktops, and mobile devices. These devices use different operating systems such as Windows, Linux, Android, and iOS. When you look at the ownership of devices, some are owned by companies whereas others are owned by users. If users access organizational data from their own devices, the privacy and safety of data can be challenging. Even for personal requirements, we might use multiple devices with different ownership to access our data.
Desktop virtualization is the best way to handle this, as it provides access to data using any device type and any operating system, but once you access the data, it will remain in a virtual environment. For example, even if you have access to the data, you will not be able to copy it from the virtual application and paste it into the local device. This separates personal data and organizational data. In other words, desktop and application virtualization provides a range of privacy and security for users, including the following:
- Resource centralization – information and data remain in a single place even though users are given access from anywhere using any device. You can even configure copy-paste protection, where users will not be able to copy organizational data and paste it into personal storage, even if the same device is used.
- Access by any device – users can access resources using any device, including desktops, laptops, or mobile devices, with any operating system. Once you install a remote agent such as Virtual Desktop, you are ready to gain access.
- Policy-based access control – since resources are stored in a central location, strict access control policies can be configured and monitored. You can configure policies or use preconfigured policies to protect your data. Data will be in complete isolation.
- Workspace flexibility – with desktop and application virtualization, users can work from anywhere if they have a decent internet connection.
- Privacy and safety – this completely prevents data loss, as users will not have direct access to data even though they work with it, as the real data is located and processed in a central location. Even external employees and contractors can work with organizational data without violating compliance requirements.
Desktop and application virtualization can even be a solution for individuals. There are different cloud-based service providers that provide desktop virtualization for individuals:
- V2 Cloud – this cloud-based virtual desktop infrastructure provides a virtual desktop as a service. You can create and manage desktops in the cloud efficiently and cost-effectively, and users can access data, business applications, and documents from anywhere and any device without compromising security.
- Shells – Shells offers a personal cloud computer that can start in minutes without compromising your data, even if your personal device is stolen or compromised. You can keep your data on the cloud and Shells provides automatic backups that keep your data safe. Shells also provides E2E encryption. You can get your Shells subscription for under US $5 per month and enjoy a hassle-free desktop experience from any device and operating system of your choice.
- Kamatera – another desktop virtualization solution on which you can decide the size and the operating system. Once you create the cloud PC of your choice, you can start accessing and using it from any device and operating system.
- Amazon WorkSpaces – Amazon WorkSpaces provides another desktop as a service where you can access cloud desktops that manage your data, applications, and documents securely without compromising security.
- Cloud PC – Cloud PC or Windows 365 is a Microsoft solution for desktops as a device in the cloud, but it’s still only available as business and enterprise licensing models, even though there is no restriction for individual use.
As well as cloud solutions, there are various on-premises solutions that you can build and use within your infrastructure that provide similar functionalities. As an example, Microsoft Remote Desktop Services provides desktop virtualization with which you can keep data centrally and provide access to users.
When it comes to individual requirements, cloud solutions and on-premises solutions might not be ideal for privacy considerations. The solutions we discussed previously definitely help small, medium, and enterprise-level organizations to protect their data and maintain data privacy and compliance standards, while leveraging the benefits of utilizing the personal devices of users. Companies do not need to invest in devices, as they can use user devices to access virtual desktops and applications while keeping their data protected. That is one of the reasons companies encourage users to use their own devices, known as bring your own device (BYOD). The major concern that many organizations have is data privacy and safety, when users are allowed to use their own devices to access organizational data. Desktop and application virtualization provides the solution for this. Even Microsoft desktop virtualization provides an application virtualization solution where users will not even realize that they are using a virtual application, as it provides the same experience and the same interface that they used to have when using the installed application, yet still provides data privacy and maintains the required compliance standards.
Summary
In this chapter, we discussed different ways and techniques that we can maintain cyber anonymity. We discussed methods to maintain cyber anonymity by using virtual machines at the operating system level. Then, we discussed how we can maintain cyber anonymity at the application level, including application and desktop virtualization. Since we mostly access cyberspace using web browsers, we discussed how to prevent tracking on browsers using browser extensions. Browser extensions can prevent tracking and ads while displaying blocked trackers. There are anti-tracking tools that are capable of blocking trackers at the application level. When the trackers create cookies and scripts for use later or by other applications, we can remove them using trace removal programs. When you go through these methods, you will understand that tracking is possible in multiple layers. When it comes to cyber anonymity, we need to plan and maintain all these layers. Leaving traces on even a single layer will provide enough information to attackers to carry out an attack. We discussed how we can protect ourselves in different layers and maintain cyber anonymity.
This chapter explained how to maintain cyber anonymity and areas and techniques that we can use to maintain cyber anonymity under the following topics:
- Avoiding behavior-tracking applications and browsers
- Using secure messaging apps
- Using disposable emails and contact numbers
- Using virtual machines and virtual applications
By now, you will understand the behavior-tracking techniques and different types of secure messaging apps that can be used to communicate without compromising privacy. Also, you will understand the importance of disposable email addresses and contact numbers. We discussed the importance of virtualization in cyber anonymity and the importance of maintaining cyber anonymity in all the layers.
The next chapter explains the tools and techniques that can be used to maintain cyber anonymity.
