10
Building Zero Trust Architecture with Hybrid Cloud Security Patterns
This chapter discusses the reference architectures and patterns for implementing the zero trust model. The principles for zero trust are also discussed in detail. We will discuss use cases requiring the zero trust model and how to use the hybrid cloud security patterns to protect critical data using zero trust security practices. The following diagram illustrates the zero trust pattern:
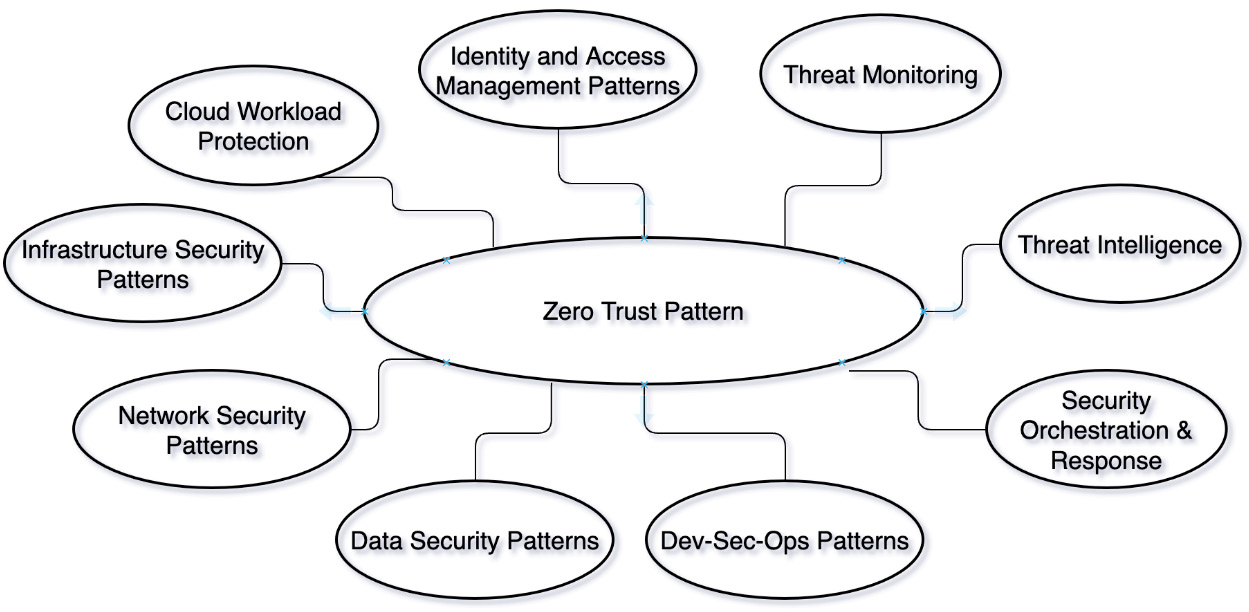
Figure 10.1 – Zero trust pattern
The topics discussed in this chapter include the following:
- Zero trust model
- Principles of zero trust
- Reference architecture for zero trust
- How to use hybrid cloud security patterns to take a zero trust approach
Zero trust pattern
Let’s get started!
Problem
How to implement security for a dynamic, distributed, and varied infrastructure, users, endpoints, applications, and data deployed in a hybrid multicloud environment.
Context
With digital transformation, the way enterprises operate has changed. The enterprise boundaries have become thin, enabling business collaboration across customers and partners. Most enterprises use multicloud as a strategy for innovation at speed, scale, performance, availability, and resiliency.
As shown in the following diagram, a typical enterprise IT landscape consists of many resources spread across multiple clouds accessed by users using multiple channels, such as web or mobile, using various endpoint devices. Enterprise applications and data are also shared with their customers and partners:
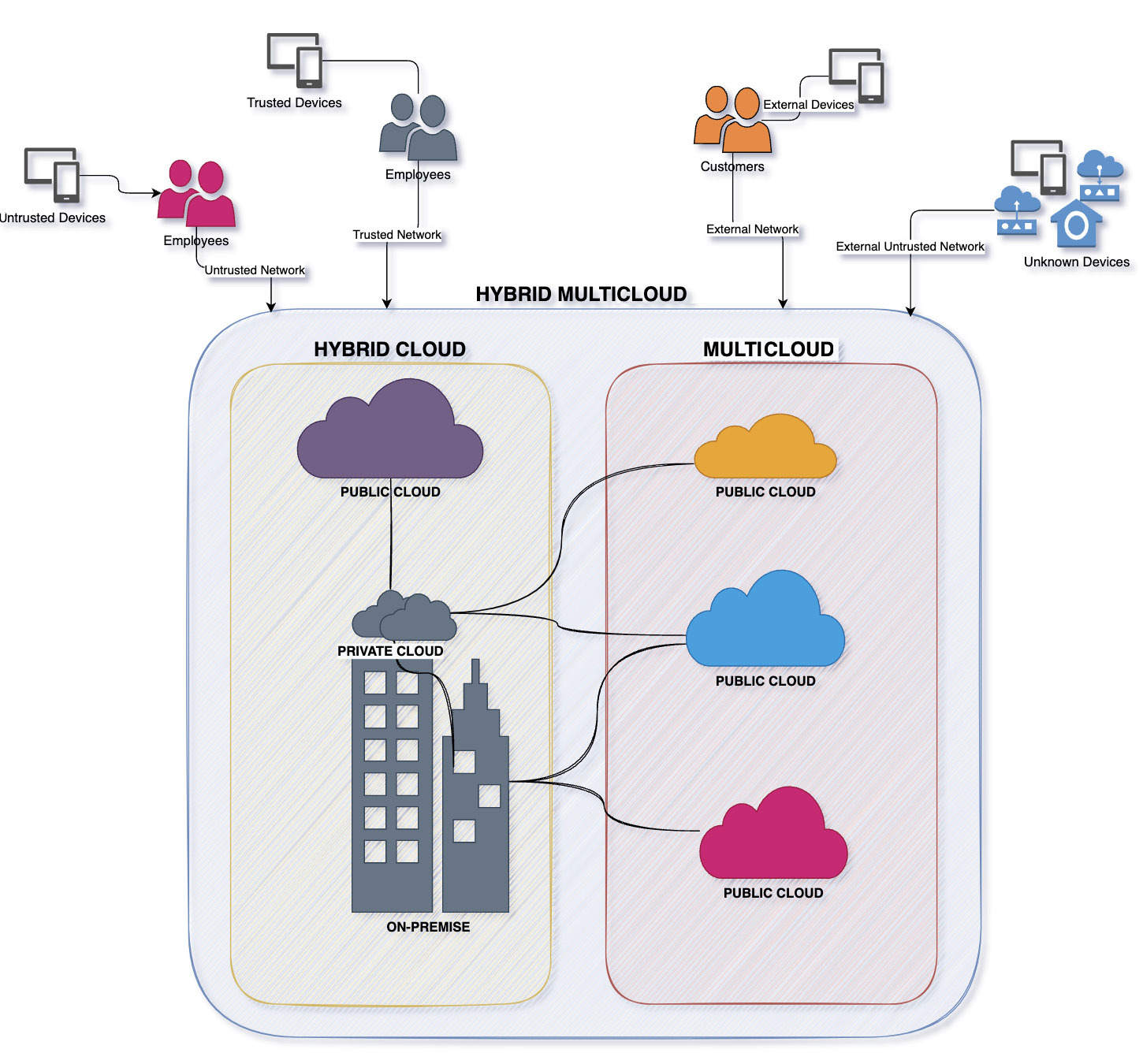
Figure 10.2 – Typical enterprise IT landscape
Traditional security that was more focused on perimeter protection has become obsolete or deficient in its capabilities to protect diverse and distributed assets. This model of perimeter-based network security controls, such as firewalls and VPNs, automatically trusts users who are inside the network. But with the vanishing perimeters and collaboration across enterprises the threats can arise from within the internal network. Also, post-pandemic, there are more users connecting to the enterprise application remotely from their homes or unknown networks. Enterprises need to enable secure access to enterprise resources for remote users and workers. Enterprises now also need to be able to rapidly form (and dissolve) partnerships. At the same time, they need to protect the internal network from insider attacks, as well as managing the risk of resource access from unmanaged and jailbroken devices. Perimeter-based defense is not equipped to address this use case. Insider threats are another macro trend or use case that enterprises are trying to address. Enterprises, especially in the blockchain, cryptocurrency, defense, and financial service industries, need protection or look to solve this issue as part of their modernization. All these lead to high chances that the traditional approach of centralized protection mechanisms will be breached. The biggest risk with the traditional model is that it will not be able to sustain the dynamic changes in terms of variety and scale in a hybrid multicloud environment.
Innovating at speed requires rethinking security and compliance in the multicloud context. There is a need to look at the security model differently to mitigate risks with assurance and demonstrate continuous compliance and protection against threats.
Solution
The zero trust pattern is an emerging model or approach that helps address the previously discussed challenges using a foundational set of components and functions. This model is based on certain principles that ensure effective implementation of the architecture pattern. These principles include the following:
- Never trust, always verify: The important aspect of this principle is that you don’t trust anything – people, processess, and technology, as well as network, compute, and storage – until they prove that they are trustworthy. The traditional security model is based on trust. A user or application that has once gained trust and access to the resources gets access to multiple other resources within the network. The trust-based model does not protect against insider attacks on an application or data. In a zero trust model, no user, application, or resource is trusted until verified. The network, user, or application is asked to prove the trust and is verified for every request before providing access to the resource. With this principle, the trusted zone is minimized where implicit trust works, and in all other cases, trust needs to be verified explicitly.
- Enable least privilege: In this principle, no subject (user or application) shall be given more privileges than what’s needed to complete the task. This means no over-provisioning of access to any resource on the cloud and it is controlled more by the function of the subject as opposed to its identity.
- Assume breach: This principle assumes that the trust is fundamentally flawed and all parts of the system are vulnerable to attacks. With an assume breach mentality, the enterprise assumes cyber-attacks will happen and plans the defense strategies accordingly. In this active defense model, the enterprises shift their focus toward continuous monitoring, security, and compliance.
The NIST publication (link provided in the References section) discusses the various aspects of the zero trust model focused on protecting resources (assets, services, workflows, network accounts, and so on) and addresses the requirements of accessing any cloud resource from anywhere on any device to provide a reliable and secure experience.
Based on the use cases and general deployment models, the core set of capabilities required to implement a zero trust security pattern includes the following:
- A control plane that provides the way to define and manage security policies. This is often backed by a policy engine and administration capabilities. This is also referred to as the Policy Administration Point (PAP) and Policy Decision Point (PDP).
- A system that supports adaptive identity and policy-driven access control. In a zero trust model, the user is not automatically trusted and there is a need to continuously verify and authenticate users no matter where, when, and how they access a system. This identity and access management system identifies the user or application requesting access to the resource and manages the authentication and authorization. The system detects any anomalies in the access patterns and steps up the authentication as needed through Multifactor Authentication (MFA). The system also provides finer authorization controls at the resource level and keeps an audit trail of the overall process. A data plane that includes a mechanism to apply policy-enforced context-specific security for the application and data acts as the Policy Enforcement Point (PEP).
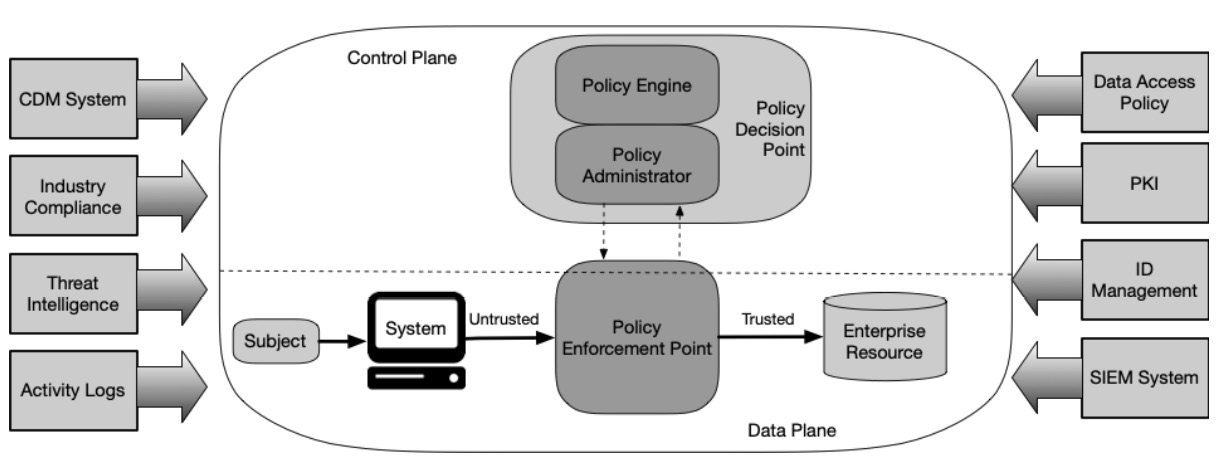
Figure 10.3 – Zero trust pattern (taken from https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf)
- Context-specific and policy-enforced application and data security. The context includes several factors, such as the user, device, network, time of day, resource for which access is requested, and classification of the resource based on the sensitivity. Based on the determined context and dynamically updated policies, access is allowed or denied to the resource with technical assurance based on zero trust.
- A zero trust pattern also supports the continuous security model, where the system learns continuously through the observability inputs (logs, monitoring, and tracing) from across all layers from multiple clouds. The analytics of this massive amount of data is often backed by machine learning models that enable the system to decide dynamically on the requests for accessing a cloud resource. The system also automatically updates or adjusts the policies based on the new context and resources identified.
Using hybrid cloud security patterns for zero trust
All the security components in the security architecture need to be rethought – identity, network, app, data, devices, and analytics for the cloud-based workload to implement a zero trust model.
But you can use all the hybrid cloud security patterns that we have learned about in this book to implement a zero trust pattern.
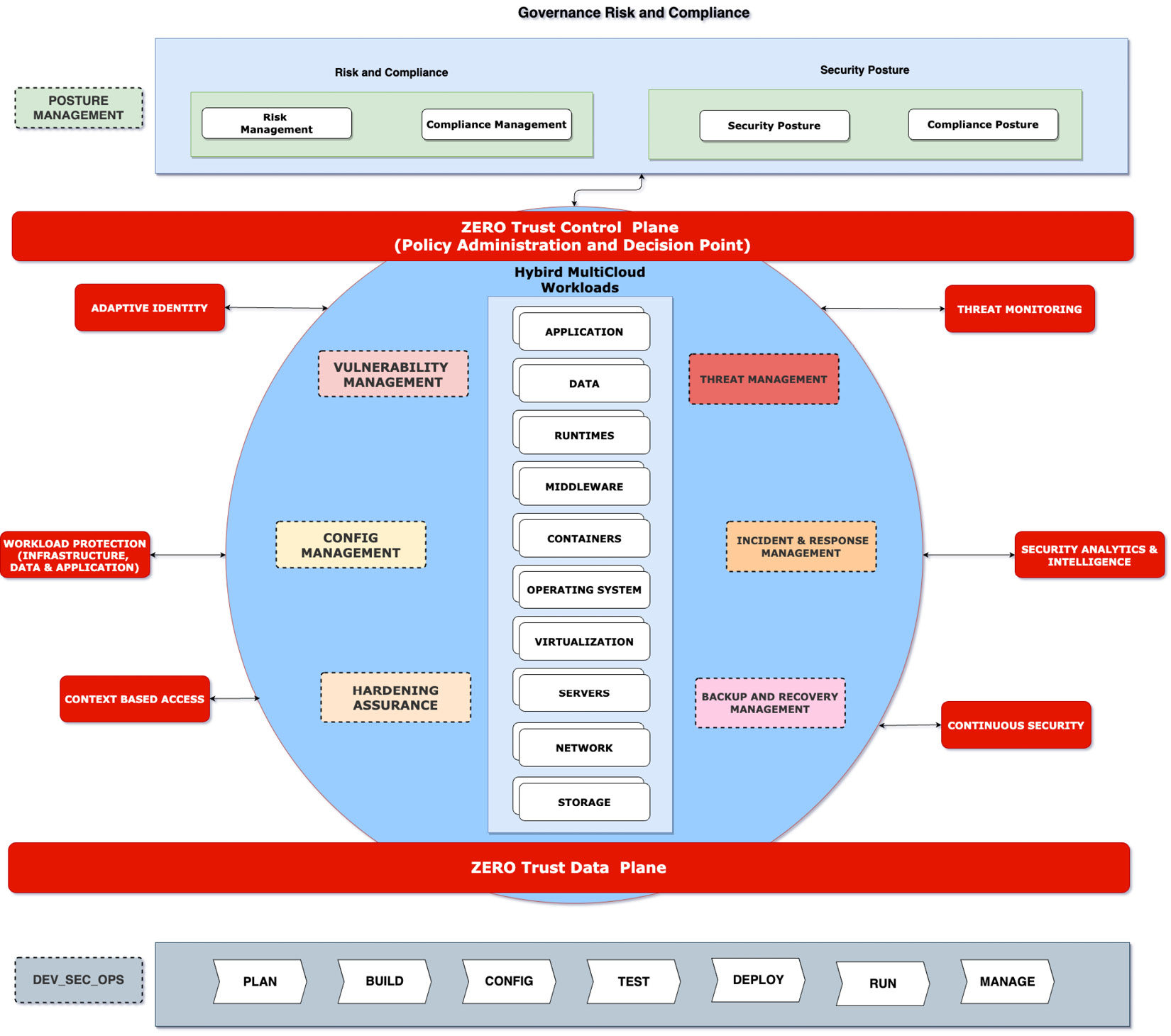
Figure 10.4 – Using hybrid cloud security patterns for the zero trust pattern
The preceding diagram provides the mapping of the several patterns and shows how to overlay them on a zero trust model. The following points discuss the content from previous chapters of this book and how they can be used in a zero trust pattern:
- Digital transformation and shared responsibility model: In Chapters 1 and 2, we discussed the digital transformation of enterprises and the vanishing of perimeter-based access controls, enabling a collaborative environment across customers, partners, and cloud providers that underlines the need for a shared responsibility model for a zero trust pattern. These chapters also discussed the governance, risk, and policies that hybrid multicloud deployments need to address from an industry and regulation perspective.
- Identity and access management: In Chapters 3 and 4, we learned about the patterns for cloud and application identity and access management. These chapters covered the standards-based model to address the authentication and authorization needs of a cloud application. These patterns, combined with patterns for the detection of anomalous user behavior based on the risk context across assets – privileged users, devices, data, and so on – can be used as an adaptive identity capability. The idea is to enable least privilege access by discovering and assessing risk across data, identities, endpoints, apps, and infrastructure.
- Infrastructure security: In Chapters 5 and 6, we learned about patterns to provide isolation to varying degrees and security for bare metal, VMs, containers, and serverless compute types. We also discussed patterns for trusted compute and securing the hybrid cloud network infrastructure. We learned about how to isolate network traffic based on purpose and target environments and network protection for cloud workloads. This provides the core capability in the zero-trust pattern to do microsegmentation and create smaller secure zones.
- In Chapter 7, we learned about the core patterns that can be used to protect data at rest, in transit, and in use. These patterns combined with multicloud key orchestrator and encryption can be leveraged to provide context-based access and protection for data. The protection patterns need to follow the never trust, always verify policy with context-aware access control to all apps, data, APIs, endpoints, and hybrid cloud resources
- The zero trust model underlines the need for security to be dealt with early in the development and deployment life cycle, as discussed in Chapter 8. Shifting left security with DevSecOps and continuous monitoring of threat and vulnerability management are core tenets of a zero trust pattern. Zero trust mandates the need for continuous security through identifying vulnerabilities and control configurations for cloud resources to facilitate the management of risks.
- Automated response to anomalous behavior and continuous improvement of policies based on threat patterns is a core component of zero trust. Assume breach, identify threats, and automate responses with CSPM and SOAR capabilities, discussed in Chapter 9, will not only stop the immediate attack but also dynamically adapt access controls.
- The zero trust model brings together siloed detection of threats and management to a central platform with intelligence to dynamically protect all cloud resources based on context-based policies.
Known uses
The following are the known uses:
- The AWS guiding principles for building zero trust focus on bringing together identity and network capabilities where possible. The model recommends taking a use case-centric approach. There are several use cases, such as workforce mobility, software-to-software communications, and digital transformation projects, that can benefit from the enhanced security provided by zero trust.
- Microsoft integration guidance leverages software and technology partners capabilities to build zero trust solutions. The implementation of the model and principles is discussed in the link provided in the References section. Importantly, as shown in Figure 10.5, security policy enforcement is at the center of the zero trust architecture. This includes MFA with conditional access, which takes into account user account risk, device status, and other criteria and policies that you set. Policies that are configured for each of these components are coordinated with your overall zero trust strategy. Device policies determine the criteria for healthy devices and conditional access policies require healthy devices for access to specific apps and data. Threat protection and intelligence monitor the environment, surface current risks, and take automated action to remediate attacks:
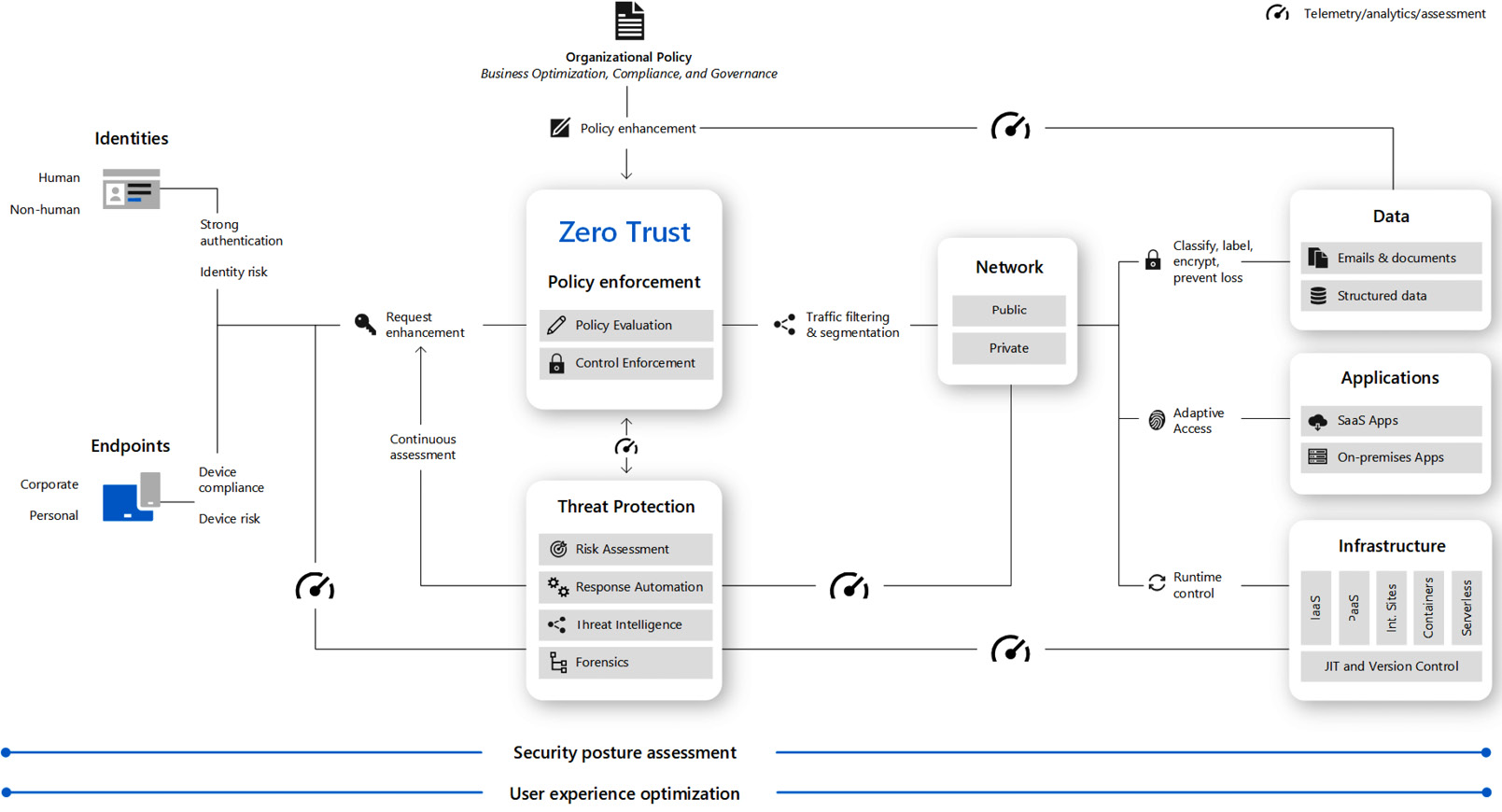
Figure 10.5 – Microsoft zero trust guide (taken from https://docs.microsoft.com/en-us/azure/security/fundamentals/zero-trust)
- Google’s BeyondCorp model and a few start-ups have built systems and platforms on top of the zero trust principle to establish the integrity and trust level explicitly. This is based on the organization’s risk threshold and tolerance to provide access to assets and data systems. This is a new approach where the traditional perimeter-based protection with firewalls is changed to context-based access. This supports one of the other macro trends that companies are trying to address – secure and remote access for employees to enterprise resources. This requirement has been amplified during the COVID-19 pandemic, when most employees access corporate resources from different places.
- IBM’s zero trust framework, as described in the following figure, combines security architecture with a zero trust governance model. The security controls are established and managed at the enterprise level, which combines people, processes, and technology. The framework has the three steps of defining context, verifying and enforcing, and resolving incidents. The Define Context step is where the security policies are set. The Verify & Enforce step implements policy enforcement. Resolve Incidents deals with operations and implements continuous security monitoring solutions and automated responses:
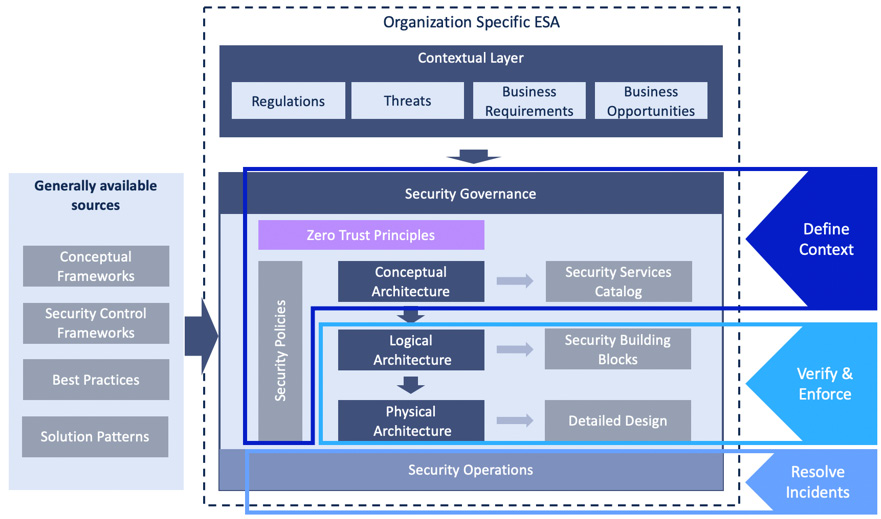
Figure 10.6 – IBM zero trust governance model (taken from https://www.ibm.com/in-en/topics/zero-trust)
- The Open Group has published the Zero Trust Core Principles, which introduces zero trust to leaders in business, security, and IT. This whitepaper provides a foundation on the drivers for zero trust, their implications, and the role of zero trust. The Open Group Zero Trust Commandments is the document built on the Zero Trust Core Principles to present a non-negotiable list of criteria for zero trust. The Open Group guide Axioms for the Practice of Security Architecture discusses axioms distilled from years of experience in the practice of security architecture during the formative decades of the discipline. They are designed to be timeless statements with broad applicability, including zero trust, regardless of how digital technologies and threats continue to evolve. The ZTA Working Group of The Open Group is an industry-wide initiative to establish standards and best practices for zero trust as the overarching information security approach for the digital age.
Summary
In this chapter, we learned about the principles of a zero trust model and the key components needed to build a reference pattern supporting the model. We also learned how to use the hybrid cloud security patterns that we discussed in earlier chapters to establish the right level of governance, configurations, controls, policies, protection, and automation and use them to build a solution with the zero trust approach. Hybrid cloud security patterns combined with zero trust models help combat cyber security threats and attacks to accelerate the digital transformation of enterprises. There are more macro and micro patterns that will be discovered in this journey and I shall look to capture them in the subsequent editions and present them to you. I hope you enjoyed reading this book as much as I did writing it. Please get in touch with me with your comments and input.
References
Refer to the following for more information about the topics covered in this chapter:
- NIST publication – Zero Trust Architecture: https://www.nist.gov/publications/zero-trust-architecture
- Guiding principles for building Zero Trust on AWS: https://aws.amazon.com/security/zero-trust/
- How Zero Trust Will Change Your Security Design Approach: https://securityintelligence.com/posts/how-zero-trust-will-change-your-security-design-approach/
- IBM Zero trust security solutions: https://www.ibm.com/in-en/security/zero-trust
- Microsoft Zero Trust architecture: https://docs.microsoft.com/en-us/azure/security/fundamentals/zero-trust
- Microsoft Zero Trust Guidance Center: https://docs.microsoft.com/en-us/security/zero-trust/
- Zero Trust and BeyondCorp Google Cloud: https://cloud.google.com/blog/topics/developers-practitioners/zero-trust-and-beyondcorp-google-cloud
- The Open Group ZTA Working Group: https://www.opengroup.org/forum/security-forum-0/zerotrustsecurityarchitecture
- The Open Group Zero Trust Core Principles: https://publications.opengroup.org/security-library/w210
- The Open Group Axioms for the Practice of Security Architecture: https://publications.opengroup.org/g192
- The Open Group Zero Trust Commandments: https://publications.opengroup.org/g21f
- What Is Zero Trust and Why Is it So Important?: https://www.cyberark.com/resources/blog/what-is-zero-trust-and-why-is-it-so-important
- The Key Components and Functions in a Zero Trust Architecture: https://cpl.thalesgroup.com/blog/encryption/key-components-function-in-zero-trust-architecture
