CHAPTER 2: KEY FRAMEWORKS AND STANDARDS SUPPORTING GOVERNANCE OF ENTERPRISE IT
‘The nice thing about standards is that you have so many to choose from.’13
Andrew S Tannebaum (1981)
Computer Networks, 1st Edition, p. 168
In this chapter, under basic headings, many key frameworks and international standards that are the basis for COBIT 5 are briefly discussed and footnote references are provided to sources of further information – mostly readily accessible on the Internet for free.
Governance of enterprise IT is concerned with both governance and management and requires a broad range of practices to be included. ISACA has always been very good at recognising such practices and has always used well-known frameworks and international standards as the basis for the development of COBIT. For example, COBIT®4.1 was quoted by ISACA as being based on more than 40 other frameworks and standards and COBIT 5 is claimed to be based on more than 80 frameworks and standards.
IT Governance
As explained in Chapter 1, IT Governance is the original but still popular term for Governance of Enterprise IT (GEIT) and Corporate Governance of IT.
ISO/IEC 38500: 2008 Corporate Governance of Information Technology
An international Standard based on an Australian Standard, AS 8015-2005, that specifies the three activities to be conducted by board members and senior executives who are accountable and responsible for corporate governance of IT.
1. Evaluate
2. Direct
3. Monitor
The Standard also specifies the six key principles of corporate governance of IT:
1. Responsibility
2. Strategy
3. Acquisition
4. Performance
5. Conformance
6. Human Behaviour
ISACA has adopted the three activities Evaluate, Direct and Monitor of ISO/IEC 38500 and these are governance practices of each of the five processes in the Governance Domain of COBIT 5. These governance practices are titled:
• evaluate the governance system
• direct the governance system
• monitor the governance system.
However, the six key principles of ISO/IEC 38500 have not been formally adopted by COBIT 5, although COBIT 5 does support the adoption of these principles and explains how COBIT 5 guidance enables each of these principles14.
Two standards related to ISO/IEC 38500 are under development by ISO TC/SC JTC1. Targeted for publication in 2016 is ISO/IEC 3850115 Corporate Governance of IT Implementation Guide, and ISO/IEC 3850216 Governance of IT – Framework and Model may be ready for publication in 2014.
IT Service Management
In this section the following will be discussed:
• ITIL 2011 Edition
• ISO/IEC 20000: 2011
IT Infrastructure Library (ITIL) 2011 Edition17
ITIL, which was first published in 1989, is almost certainly the most deployed framework in the world for IT. An indicator of the level of deployment is the fact that by the end of 2012 the number of people holding an ITIL Foundation Certificate exceeded two million and each month 20-25,000 people are passing the ITIL Foundation exam.
ITIL is concerned with best practices for the delivery of IT services to businesses and is based on three key areas:
• Services – IT applications that support business processes and activities
• Processes – these processes are used to control and manage IT services
• Functions – organisational units in the IT department
ITIL 2011 Edition is service lifecycle based:
• Service Strategy
• Service Design
• Service Transition
• Service Operation
• Continual Service Improvement
ITIL has 26 processes (Table 2.1) and four functions (Table 2.2).
| Lifecycle Phase | ITIL Processes |
| Service Strategy | Strategy management for IT services |
| Demand management | |
| Portfolio management | |
| Business relationship management | |
| Finance management for IT services | |
| Service Design | Design coordination |
| Service level management | |
| Service catalogue management | |
| Availability management | |
| Capacity management | |
| Information security management | |
| Supplier management | |
| IT service continuity management | |
| Service Transition | Transition planning and support |
| Change management | |
| Release and deployment management | |
| Service asset and configuration management | |
| Knowledge management | |
| Service validation and testing | |
| Change evaluation | |
| Service Operation | Incident management |
| Request fulfilment | |
| Problem management | |
| Access management | |
| Event management | |
| Continual Service Improvement | Seven-step service improvement process |
| Functions |
| Service Desk |
| Technical Management |
| Application Management |
| IT Operations Management: • IT Operations Control • Facilities Management |
ITIL is listed in the COBIT 5: Enabling Processes book as providing related guidance to 15 of the 37 COBIT 5 processes – see Appendix A.
ISO/IEC 20000: 2011 Information technology service management system
ISO/IEC 20000 was originally developed in 2000 as British Standard BS 15000 using ITIL V2 as its main source of ITSM practices. It was developed as the basis for certification of organisations for IT service management. To gain certification an organisation has to be externally audited for compliance with the Standard, which confirms that the organisation is using recognised ITSM practices for the delivery of IT service management. BS 15000 was internationalised as ISO/IEC 20000 in 2005. However, in 2011, it was upgraded to reflect developments in IT service management practices in the decade since BS 15000 was first introduced and the revision particularly took on board more fully the concepts of management systems that are formally used in other standards: in particular, ISO9000 (Quality) and ISO/IEC 27001 (Information security). ISO/IEC 20000 describes a service management system (SMS) – See Figure 2.1 – that must be in place in its entirety for an organisation to gain an ISO/IEC 20000 certificate18. Certification is reassessed every three years and surveillance audited at least annually in the interim period. More than 600 organisations in the world held the APM Group ISO/IEC 20000: 2011 certificate in September 2013.
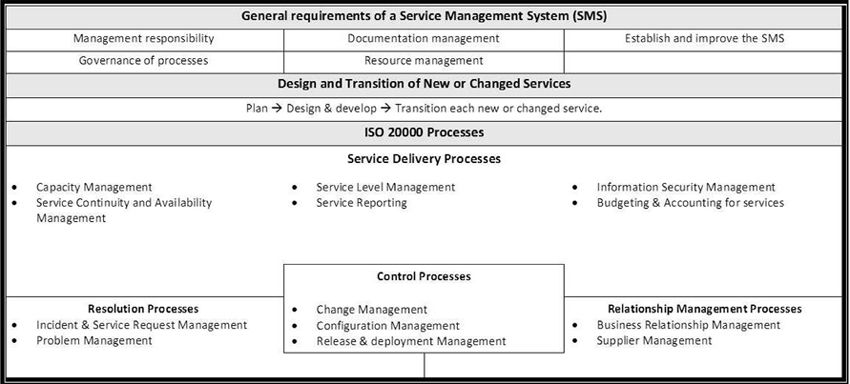
Figure 2.1: Service management system (SMS) for ISO/IEC 20000: 2011
The 13 processes used in ISO/IEC 20000: 2011 are referenced by COBIT 5 as being guidance for 13 of the COBIT 5 processes. See Appendix A.
Project Management
In this section the following will be discussed:
• PRINCE2® 2009 Edition
• PMBOK® 5th Edition (2013)
PRINCE2 2009 Edition
PRINCE2, an acronym for PRojects IN Controlled Environments, was first published in 1996 and is a process-based method for managing projects of any kind. In 2009, it was upgraded to PRINCE2 2009 Edition to reflect developments in approaches to project management practices. In particular, it has reduced the number of processes and removed sub-processes, which are now called activities. It also discusses how PRINCE2 interacts with other frameworks from the UK Cabinet Office19: Managing Successful Programmes (MSP®) and Management of Risk (M_o_R®).
PRINCE2 is adopted worldwide as a project management framework and is the framework of choice for most organisations in Europe.
The processes in PRINCE2 2009 Edition are listed in Table 2.3.
Table 2.3: PRINCE2 (2009) Processes
| PRINCE2 Processes |
| Directing a Project |
| Starting up a Project |
| Initiating a Project |
| Managing Stage Boundaries |
| Controlling a Stage |
| Managing Product Delivery |
| Closing a Project |
| Planning |
PRINCE2 is referenced by COBIT 5 as providing guidance for two of the 37 COBIT 5 processes – see Appendix A.
PMBOK®
PMBOK®, the Project Management Body of Knowledge, was first published in 1987 but in 2013 was updated to PMBOK® – 5th Edition.
PMBOK® – 5th Edition has five process areas:
1. Initiating (two processes)
2. Planning (24 processes)
3. Executing (eight processes)
4. Monitoring and Controlling (11 processes)
5. Closing (two processes)
and 10 Knowledge Areas.
1. Project Integration Management
2. Project Scope Management
3. Project Time Management
5. Project Quality Management
6. Project Human Resource Management
7. Project Communications Management
8. Project Risk Management
9. Project Procurement Management
10. Project Stakeholders Management
Each Knowledge Area contains processes that are part of the five Process Groups. In total PMBOK® – 5th Edition has 47 processes (five new processes were added). The Knowledge Area called Project Stakeholder Management is a new addition to the 5th Edition. It increases the focus on identification and engagement of stakeholders.
PMBOK® is adopted worldwide as a project management framework and it is the framework of choice in North America.
PMBOK® is referenced by COBIT 5 as providing guidance for three of the 37 COBIT 5 processes – see Appendix A.
Risk Management
From an IT governance perspective, risk management frameworks are designed to identify and analyse IT-related risks and determine how to mitigate, manage and monitor them while ensuring there is alignment with enterprise risk management.
There are many standards and frameworks covering risk management including:
• COSO ERM20 (Enterprise Risk Management (2004) from the Committee of the Sponsoring Organisation of the Treadway Commission.
• Risk IT™21 (2009) from ISACA. One of the ISACA frameworks used to build COBIT 5.
• Management of Risk (M_o_R)22 (2002 with latest 2010) from The Cabinet Office23.
• OCTAVE®24 (2001 and onwards) (Operationally Critical Threat, Asset and Vulnerability Evaluation) from the Software Engineering Institute at Carnegie Mellon University.
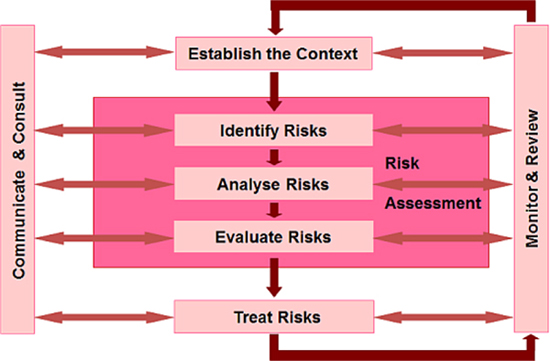
• ISO 31000:2009 Risk Management – Principles and Guidelines. It covers principles, a risk management framework and a risk management process shown in Figure 2.2.
ISO31000 is referenced by COBIT 5 as being guidance for one of the COBIT 5 processes. See Appendix A.
Figure 2.2: ISO31000 Risk Management Process (After ISO/IEC 31000)
Value Delivery
Value delivery enables business benefits to be realised from IT investments.
Value delivery frameworks are:
Val IT™ V2.025 (2008) from ISACA. One of the ISACA frameworks used to build COBIT 5.
Management of Value (MoV™)26 (2010) from the UK Cabinet Office27.
Information Security
Information security is principally covered by the ISO/IEC 27000 series of standards, although readers may find it interesting to look into two other frameworks that are related to ISO27000: MEHARI28 and The Standard of Good Practice for Information Security.
MEHARI was developed originally in 1996 for chief information security officers, CIOs, risk managers and auditors by CLUSIF (Club de la securité de l’information français), based in Paris, France. It provides a comprehensive set of tools for risk analysis and risk management principally covering information security. It includes a risk assessment model and a security services reference manual for building a security framework. The latest version (2010) is aligned with ISO27002.
The Standard of Good Practice for Information Security (2013)29 from the Information Security Forum (ISF), founded in 1989, is a highly readable, annually updated and practical 372-page book that addresses information security from a business perspective.
The ISO27000 series30 consists of a large number of standards of which two: ISO/IEC 27001 and ISO27002 are the main parts. Also, recently published in 2012, ISO/IEC 27013 explains how to integrate the implementation of ISO/IEC 27001 and ISO/IEC 20000:
ISO/IEC 27000: 2012. Information technology. Security techniques. Information security management systems. Overview and vocabulary.
ISO/IEC 27001: 2013. Information technology. Security techniques. Information security management systems. Requirements.
ISO/IEC 27002: 2013. Information technology. Security techniques. Code of practice for information security management.
ISO/IEC 27003: 2010. Information technology. Security techniques. Information security management system implementation guidance.
ISO/IEC 27004: 2009. Information technology. Security techniques. Information security management. Measurement.
ISO/IEC 27005: 2008. Information technology. Security techniques. Information security risk management.
ISO/IEC 27006: 2011. Information technology. Security techniques. Requirements for bodies providing audit and certification of information security management systems.
ISO/IEC 27011: 2008. Information technology. Security techniques. Information security management guidelines for telecommunications organisations based on ISO/IEC 27002.
ISO/IEC 27013: 2012. Information technology. Security techniques. Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1.
ISO/IEC 27031: 2011. Information technology. Security techniques. Guidelines for information and communication technology readiness for business continuity.
ISO/IEC 27032: 2012. Information technology. Security techniques. Guidelines for cybersecurity.
ISO/IEC 27033-5: 2013. Information technology. Security techniques. Network security. Securing communications across networks using Virtual Private Networks (VPNs).
ISO/IEC 27034-1: 2011. Information technology. Security techniques. Application security. Overview and concepts.
ISO/IEC 27035: 2011. Information technology. Security techniques. Information security incident management.
ISO/IEC 27037: 2012. Information technology. Security techniques. Guidelines for identification, collection, acquisition and preservation of digital evidence.
ISO/IEC 27001 is referenced by COBIT®5 as being guidance for five of the COBIT®5 processes. See Appendix A.
Enterprise Architecture (EA)
Enterprise architecture is a framework, first established 25 years ago, that enables business strategy to be achieved using information systems and information technology by specifying how business processes across the enterprise will be developed and standardised to use information systems and information technology. Enterprise architecture can be viewed as a set of domains. There are several enterprise architecture frameworks and each has a slightly different view of the domains, but the general principles are similar.
Enterprise architecture domains can be summarised as shown in Table 2.4.
Table 2.4: Enterprise Architecture Layers (Based on TOGAF® 9.1)
| Enterprise Architecture Domain |
Description |
| Business architecture | Processes used by the business to meet its business strategy, governance and business outcomes |
| Application architecture | How specific applications are designed to conduct business processes and how they interact with one another |
| Data architecture | How the enterprise databases (or data warehouse) are organised and accessed by applications |
| Technical architecture | Hardware and software infrastructure including networks that supports applications and their interactions |
Enterprise architectures commonly used are:
• TOGAF® – The Open Group Architecture Framework31
• Zachman Framework for Enterprise Architecture32
• CEAF – Commission Enterprise Architecture Framework33
• FEA – Federal Enterprise Architecture34
A comparison of three of these enterprise architectures was provided by Microsoft in 200735, although it did not include CEAF.
ISACA states in the COBIT 5: Enabling Processes book that TOGAF® 9 provides related guidance for two of the 37 COBIT 5 processes – see Appendix A. In addition, COBIT 5: A Business Framework for the Governance and Management of Enterprise IT also states that FEA and CEAF in addition to TOGAF® were used as inputs to COBIT 5.
Quality
Historically, there have been many frameworks and standards concerned with quality and all of them are still widely used:
• The Deming Cycle36 – post Second World War from the US and into Japan, particularly. Known by everyone as Plan – Do – Check – Act (PDCA).
• Juran’s Managerial Breakthrough37 – mid-1960s, also in Japan.
• Kaizen38 – the Kanji (Japanese) word for improvement also started post Second World War in Japan.
• Total Quality Management (TQM)39 devised by Feigenbaum and based on PDCA.
• Six Sigma40 – 1981 at Motorola in Japan.
• Baldridge National Quality Program (BNQP)41 – 1987 as an excellence award for quality in the US.
• Lean42 – late 1980s in Toyota, Japan. Often used with Six Sigma, now as Lean Six Sigma43, devised in 2002.
• European Framework for Quality Management (EFQM)44 – 1992 and notable for recognising continual improvement before it appeared in ISO9000.
• ISO900045 – originally 1987, based on BS5750 (1979), but currently ISO 9001: 2008 – notably devised the Quality Management System (QMS)
ISO9001 is referenced by COBIT 5 as being guidance for one of the COBIT 5 processes. See Appendix A.
Maturity Assessment
In this section the following will be discussed:
• CMM®
• CMMI®
• ISO/IEC 15504
CMM®
The Software Engineering Institute (SEI) at Carnegie Mellon University, having initially devised a capability maturity model in 198646 to assess software development projects for the US Department of Defense, then published in 1993 the full Capability Maturity Model (CMM®), a maturity assessment framework for assessment of software development projects.
It was soon recognised by many people that the CMM® approach could be used for general business and IT process assessment and this was the approach used by ISACA to create the COBIT Maturity Model that was used for all COBIT processes up to and including COBIT 4.1.
CMMI®
In 2002, SEI superseded CMM® with Capability Maturity Model Integration (CMMI®)47 to extend to other activities, not only software development.
The following are the current versions of CMMI® (2010):
• CMMI-DEV is used to assess and improve engineering and development processes in an organisation that develops products.
• CMMI-SVC is used to assess and improve management and service delivery processes in an organisation that develops, manages and delivers services.
• CMMI-ACQ is used to assess and improve supplier management processes in an organisation that deals with multiple suppliers for its business.
CMMI® fulfills the requirements of ISO15504.
ISO15504 Process Capability Model
Like CMM®, ISO15504 was initially designed to address assessment of software development.
It started as a framework called SPICE48 (Software Process Improvement and Capability Determination), which was developed initially by an international working group, starting in 1993, for assessing and improving software development. This became the international Standard ISO15504 in 2004.
In particular, ISO15504 covers the assessment process and defines a process assessment model (PAM) that requires a process reference model (PRM) to be devised and specifies how the PRM should be structured. The Standard can be used for process capability assessment and for process improvement.
There is clearly competition between the well-established and respected CMMI® and the later-to-market ISO15504. Although CMMI® incorporates many of the concepts of ISO15504, it is not an international standard. ISACA, therefore, made the decision that COBIT 5 should use ISO15504 and in Chapter 8 we discuss how ISO15504 is used to assess and improve COBIT 5 processes.
Internal Controls
Internal controls are put in place by enterprises to transmit governance policies throughout the enterprise to ensure fiduciary control of financial and accounting information, with the aim of meeting operational and profitability targets while complying with regulations.
COSO
A framework for internal control was established in 1992 by the Committee of the Sponsoring Organisation of the Treadway Commission (COSO). The latest version is Internal Control–Integrated Framework (2013)49. The framework is separate from, but complementary to, the COSO ERM framework for enterprise risk management.
COSO was seen as an important framework to include in COBIT when the first version of COBIT was being developed between 1991 and 1996.
COSO is referenced by COBIT 5 as providing guidance for four of the 37 COBIT 5 processes – see Appendix A.
Sarbanes-Oxley Act
The Sarbanes-Oxley Act (2002), known colloquially as SOX, was introduced in the US to control enterprise board activity following Enron and Worldcom frauds. It applies to enterprises registered on the New York Stock Exchange (NYSE) and NASDAQ Stock Market. Section 40450 of SOX is important because it covers the assessment of internal controls on financial reporting. IT services are fundamental to the creation of financial reports and hence must have appropriate internal controls and be assessed. After SOX was published, ISACA produced a guide, IT Control Objectives for Sarbanes-Oxley, and COBIT has been recognised as the framework to use to meet SOX requirements and pass Public Company Accounting Oversight Board (PCAOB)51 assessment.
Sarbanes-Oxley was identified by ISACA as being used to assist with the development of COBIT 5. ISACA plans to publish Sarbanes-Oxley using COBIT 5 in the second quarter of 2014. This will be an updated version of the COBIT 4.1 version published in 2006.
Basel III Framework
Basel III52, the 2010-11 update to Basel II, is a framework for internal control systems in banking organisations. It has to be implemented between 2013 and 2018 and has banks worldwide complying with it.
ISACA published a guide, IT Control Objectives for Basel II that used COBIT 4.1.
Basel III was identified by ISACA as being used to assist with the development of COBIT 5.
Cultural Change Enablement
Cultural change enablement is a process to ensure stakeholders recognise and are committed to the need to change their culture, ethics and behaviour in order to be able to change the way the enterprise operates. Cultural change enablement is vital in order to successfully implement any changes to an enterprise’s business activities including changes to IT such as the desire to implement governance of enterprise IT (GEIT).
The most commonly adopted approach to cultural change enablement is Kotter’s 8 Steps to Transformation53.
Kotters 8 steps are:
1. Establish a sense of urgency of the need for change
2. Form a guiding coalition of stakeholders
3. Create a vision of where the enterprise wants to be
4. Communicate the vision to everyone
5. Empower people to act
6. Plan and implement quick wins
7. Consolidate improvements and make further changes
8. Institutionalise the changes
Kotter’s 8 steps have been used by ITIL for more than a decade and ISACA introduced it during COBIT 4.1 for implementing the governance of enterprise IT.
Kotter’s cultural change enablement was identified by ISACA as being used to assist with the development of COBIT 5.
Semiotic Framework
COBIT 5 has an Information Model which includes the Semiotic Framework.
Semiotic Framework (or Semiotic Ladder)
Here are the steps, or layers (Table 2.5), based on Stamper’s54 Semiotic Ladder that is discussed in detail in Chapter 5.
Table 2.5: Steps (i.e. Layers) of the Semiotic Ladder
| Social World | social aspects |
| Pragmatic | usage |
| Semantic | meaning |
| Syntactic | structure |
| Empiric | information access channel |
| Physical World | information carrier/media |
Stamper, in 1973, recognised that he needed to update Morris’ (1938)55 semiotic model of Syntactic, Semantic and Pragmatic layers to take into account the introduction of information technology. Stamper added Empiric and Physical levels so that information theory introduced by Shannon56 in 1948 was incorporated, that is, the physics of signs, that is, the hardware used to transmit, receive and process them and the empirics of signs that covers patterns, variety, noise, channel capacity, codes and so on. The ladder from Physical World to Social World covers data (Empiric and Syntactic) and information (Semantic and Pragmatic) that becomes knowledge in the Social World. The Physical World is where everything that can be empirically observed takes place. Information structures at the Pragmatic level is used to construct Social World activities such as creation and agreement of contracts, interpretation of a business case or management decision making based on balanced scorecard reports.
Business Continuity Management
The International Standard ISO22301:2012 (formerly a British Standard BS25999-2 published in 2007) specifies the requirements for a Business Continuity Management System (BCMS) to protect a business from disruptive incidents in addition to reducing the likelihood that such incidents might occur. Like other management system standards, ISO22301 uses Plan, Do, Check, Act (PDCA) as its core approach with key activities that cover business impact analysis (BIA), strategy, planning, exercising and improvement.
BS25999-2:2007 is referenced by COBIT 5 as being guidance for one of the COBIT 5 processes. See Appendix A.
_______________
13 In this chapter 33 standards and frameworks are briefly discussed.
14 ISACA® (2012) COBIT®5: A Business Framework for the Governance and Management of Enterprise IT, Appendix E, pp. 57–60.
15 www.iso.org/iso/home/store/catalogue_tc/catalogue_detail.htm?csnumber=45263
16 www.iso.org/iso/home/store/catalogue_tc/catalogue_detail.htm?csnumber=50962
18 www.isoiec20000certification.com
19 The UK Cabinet Office sold 51% of its ownership of Best Practice Frameworks to AXELOS in 2013.
20 www.coso.org/documents/COSO_ERM_ExecutiveSummary.pdf
21 www.ISACA.org/Knowledge-Center/Research/ResearchDeliverables/Pages/The-Risk-IT-Framework.aspx
23 The UK Cabinet Office sold 51% of its ownership of Best Practice frameworks to AXELOS in 2013.
25 www.ISACA.org/Knowledge-Center/Research/ResearchDeliverables/Pages/Val-IT-Framework-2.0.aspx
26 www.best-management-practice.com/Value-Management-MoV/
27 UK Cabinet Office sold 51% of its Best Practice Frameworks such as MoV™ to AXELOS in 2013.
28 www.clusif.asso.fr/en/clusif/present/
29 www.securityforum.org/shop/p-71-167
30 www.iso27001security.com/html/iso27000.html
32 www.intervista-institute.com/resources/zachman-poster.pdf
33 http://ec.europa.eu/dgs/informatics/ecomm/doc/ceaf_guide_v1_1.pdf
34 www.whitehouse.gov/sites/default/files/omb/assets/fea_docs/FEA_CRM_v23_Final_Oct_2007_Revised.pdf
35 http://msdn.microsoft.com/en-us/library/bb466232.aspx
36 http://ocw.mit.edu/courses/engineering-systems-division/esd-60-lean-six-sigma-processes-summer-2004/lecture-notes/6_3_pdca.pdf
37 http://books.google.co.uk/books/about/Juran_s_quality_handbook.html?id=beVTAAAAMAAJ&redir_esc=y
39 http://searchcio.techtarget.com/definition/Total-Quality-Management
40 www.motorolasolutions.com/web/Business/_Moto_University/_Documents/_Static_Files/What_is_SixSigma.pdf
43 www.amazon.co.uk/What-Lean-Sigma-Michael-George/dp/007142668X
44 www.efqm.org/the-efqm-excellence-model
46 Humphrey, W. S. (1988), ‘Characterizing the software process: A maturity framework’ IEEE Software 5 (2), pp. 73–79.
47 http://cmmiinstitute.com/cmmi-getting-started/
48 SPICE is still used as a name and SPICE conferences are held annually: 2013 in Bremen, Germany.
49 www.coso.org/documents/990025P_Executive_Summary_final_may20_e.pdf
50 https://na.theiia.org/standards-guidance/Public%20Documents/Sarbanes-Oxley_Section_404_--_A_Guide_for_Management_2nd_edition_1_08.pdf
51 http://pcaobus.org/about/pages/default.aspx
52 http://www.bis.org/bcbs/basel3.htm
53 Kotter, J.P., (1996), Leading Change, Boston, Harvard Business School Press.
54 Stamper, R. K. (1973), Information in Business and Administrative Systems, London, Batsford.
55 Morris, C. (1938), ‘Foundations of the Theory of Signs’. International Encyclopedia of Unified Science, ed. Neurath, O., Chicago, University of Chicago Press, Vol. 1, No. 2. (Reprint: Chicago, University of Chicago Press, 1970-71), Reprint: Morris, C., Writings on the General Theory of Signs, The Hague, Mouton, 1971, pp. 13–71).
56 Shannon, C.E. (1948), ‘A Mathematical Theory of Communication’, The Bell Systems Technical Journal, 27, pp. 379–423, 623–656. Available at http://cm.bell-labs.com/cm/ms/what/shannonday/shannon1948.pdf (Accessed 5 September 2013).