Many enterprises have multiple identity stores; this can include LDAP, Active Directory, as well as application specific databases. Oracle Virtual Directory (OVD) allows us to provide a virtual LDAP layer on top of these disparate identity stores and presents a single unified view across these data stores.
In this recipe, we will configure OVD to provide a virtual LDAP layer on top of Oracle Internet Directory (OID), and then configure OVD as the authentication provider for WebLogic.
You will need to have an instance of OID installed and configured; you will also need to create the demo user and add them to the Administrators group as described in the previous recipe.
You will also need to have installed and configured an instance of Oracle Directory Services Manager (ODSM), OVD, and Oracle SOA Suite running on Oracle WebLogic.
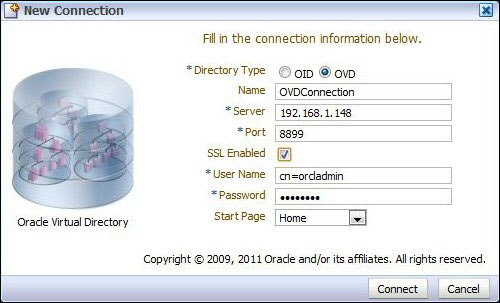
- The first step is to launch ODSM and create a connection to OVD. Enter the URL
http://host:port/odsminto your browser's address field.Next, click on Create a New Connection. This will open the New Connection dialog. Enter the details specified in the following table:
Field
Value
Directory Type
OVD
Name
OVDConnectionServer
hostname or IP address of OVD server
Port
8899(default OVD admin SSL port)SSL Enabled
checked
User Name
cn=orcladminPassword
Your Password
Start Page
Home
- We can configure OVD to connect to a variety of identity stores, including LDAP, Active Directory, an OVD local store, or database. In this recipe, we will create an adapter for an LDAP server and configure it to connect to the OID server used in the previous recipe.
Within ODSM, select the Adapter tab, and then click on the Create Adapter icon. This will launch New Adapter Wizard.
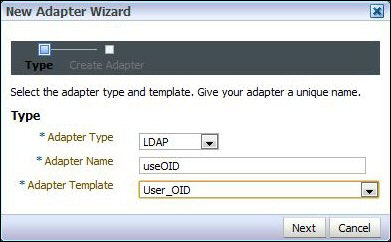
Click on the Create Adapter button in the left-hand side pane.
Select Adapter Type as LDAP, give it the name
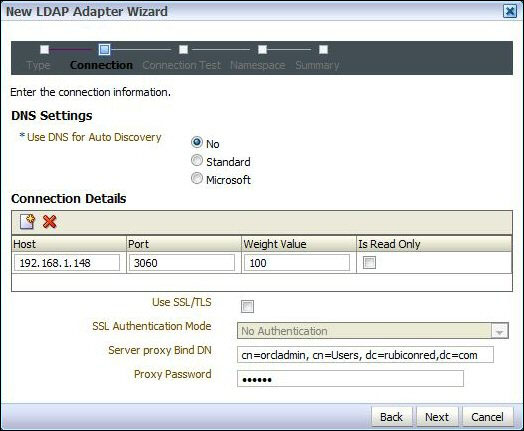
useOID, and select User_OID as the Adapter Template. Then click on Next. - This will open New LDAP Adapter Wizard. Leave Use DNS for Auto Discovery set to No and click on the Add Host icon.
Enter the OID hostname and port for your OID server and leave Weight Value set to 100.
For Server proxy Bind DN and Proxy Password enter the admin DN (
cn=orcladmin, cn=Users, dc=rubiconred,dc=comin our example) and password for your OID server.Leave Use SSL/TLS unchecked and click on Next.
- OVD will now test the connection to the OID server. You should see Success!! Oracle Virtual Directory connected to all hosts.
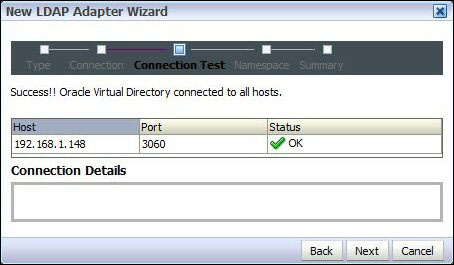
If Status is not OK, select Status to get details of the error.
- If the Status is OK, click on Next. This will take us to the Namespace page. Here we need to map the namespace of where we want to connect in the tree of the base directory (OID) to the namespace we want to appear in OVD.
In this demo, we are using the same namespace (
dc=rubiconred,dc=com) in both the directories. Set Pass Through Credentials to Always and click on Next.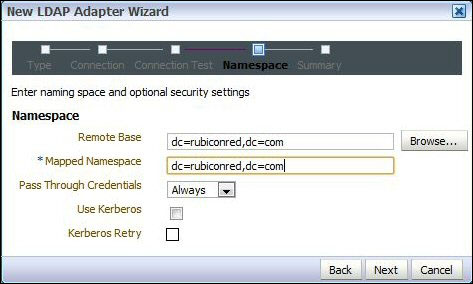
- Review the values and if everything is fine click on Finish.
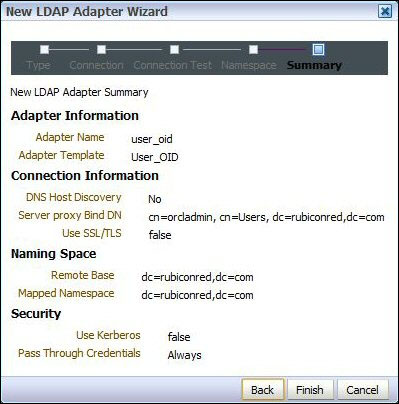
- The next step is to create an authentication provider in WebLogic to connect to OVD.
- Log in to Oracle WebLogic Server Admin Console (
http://host:port/console) with the user that has an administrator privilege, such asweblogic.Once logged in, within Domain Structure select Security Realms. Next, select myrealm. This will display the settings for myrealm.
Click on Lock&Edit to edit the session. Then select the Providers tab, and within that select the Authentication tab. This will list the authentication providers currently defined for myrealm.
- Click on the New button to create a new authentication provider. This will open the authentication provider configuration page.
Enter a name, such as
OVDProvider, and select the OracleVirtualDirectoryAuthenticator type as the authentication provider type and click on OK.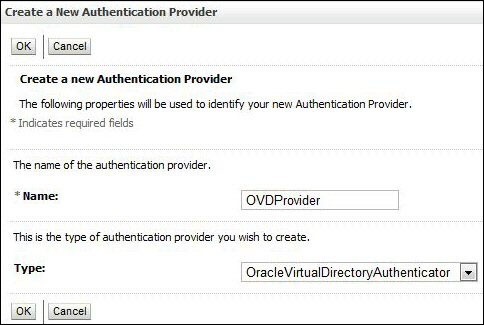
This will return us to the list of authentication providers; we can see here our newly created OVD authentication provider.
- The Authentication Providers are listed in the order in which they will be called. We need to move the OVDProvider authentication provider to the top of the list.
To do this, click on Reorder, ensure OVDProvider is selected; then click on the up arrow to move it to the top of the list and then click on OK.
- Now, we need to configure our OVD Provider to connect to our instances of OVD; select OVDProvider from the authentication provider list, and click on the Configuration tab. From here, select the Provider Specific tab.
Here, we need to provide our OVD specific connection details, as well as the location of our users and groups within the identity store, as detailed in the following table:
Field
Description
Host
The host of the machine hosting Active Directory.
Port
The port number on which Active Directory is listening.
Principal
The admin DN (for example
cn=orcladmin) that the WebLogic server should use to connect to OVD.Credential
The credential (password) used to connect to OVD.
User Base DN
The base Distinguished Name of the tree in the
LDAPdirectory that contains users.Group Base DN
The base Distinguished Name of the tree in the
LDAPdirectory that contains groups.Next select the Common tab, and set the Control Flag to SUFFICIENT and click on Save.
- Finally, we need to set Control Flag to SUFFICIENT for our default authenticator.
Select Default Authenticator from the authentication provider list, click on the Configuration tab, and then select the Common tab. From here set Control Flag to SUFFICIENT and click on Save.
- The final step is to put our changes into effect. Within Change Center, click on Activate Changes. Next, shutdown and restart the Oracle WebLogic Admin Server and related managed servers.
This is similar to our first recipe, in that WebLogic is still authenticating against OID, the difference being that it is now going via OVD, as this has been defined as the first authentication provider.
When we log in as the demo user, WebLogic will attempt to authenticate the user against OVD, which in turn will pass the request to OID. Assuming the password is correct the authentication will be successful and return control to the application.
When we log in as weblogic, authentication will fail against OVD, but because the OVD authentication provider is defined as SUFFICIENT, WebLogic will attempt to authenticate the user against the embedded LDAP at the point at which it succeeds and control is returned to the application.
It may seem a bit pointless having WebLogic go via OVD to authenticate a user against OID. However, OVD offers a number of advantages. Firstly it can be used to present non-LDAP data as LDAP data to WebLogic (or any other LDAP client); this includes identity information available via a web service call or in a database (such as PeopleSoft HR or Seibel UCM).
In addition, where an enterprise has multiple identity stores we can use OVD to present a single unified view.
Although you can configure multiple authentication providers for Oracle WebLogic, the Oracle Platform Security Service does not support multiple LDAP authentication providers.
As a result, the provider you want to use for Human Workflow authentication must be the first one listed in the order of authentication providers. Using OVD allows us to work around this limitation.
