Chapter 3. Understand security, compliance, privacy, and trust in Microsoft 365
Microsoft 365 was originally conceived as a product that would present users with familiar tools—such as the Office productivity applications—and enable them to collaborate in new ways, more easily, more efficiently, and using any device at any location. This is a wonderful aspiration, but the product’s designers soon realized that this idea of universal collaboration raised security, compliance, privacy, and trust issues that had to be addressed before the ideal could be realized.
Typically, these issues are the main impediment to the full adoption of Microsoft 365 for many IT professionals. The idea of storing sensitive data in the cloud and allowing workers to use their own devices to access that data is terrifying to administrators for whom security is becoming a greater issue every day. However, the Microsoft 365 designers have taken great pains to address these issues, and they have created a product that, when used correctly, should satisfy the concerns of even the most skittish IT directors.
Skills in this chapter:
Understand security and compliance concepts with Microsoft 365
Understand the need for unified endpoint management, security usage scenarios and services
Skill 3.1: Understand security and compliance concepts with Microsoft 365
At one time, enterprise security could be thought of as a perimeter surrounding an organization. Data remained largely within the organization’s sites and could be protected from unauthorized access by firewalls and physical barriers. Even when data began to be 102accessible beyond the organization using Internet websites and portable devices, these potential attack vectors were still owned and managed by the company.
The assets that an organization needs to protect, now referred to as its digital estate, have grown enormously in recent years and so have the enterprise’s means of ingress and egress. This digital estate certainly includes the company’s data, but it also includes the users who access the data and the systems and devices by which they access the data. All three of these assets are potential weak points in an enterprise security system, as shown in Figure 3-1. All three need protection.
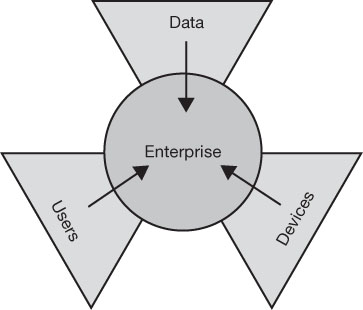
FIGURE 3-1 The enterprise asset types needing protection
The commitment to the cloud required by adopters of Microsoft 365 creates a new attack vector. However, to fully protect the company’s data, IT administrators now have to be concerned with the cloud, and they must be concerned with security for devices that are not directly owned by the organization, not located within the organization, and, in some cases, owned by users who are not even employees of the organization.
Therefore, the primary storage for an organization’s data can be located in the cloud or on servers kept on-premises. In many cases, the data is split between the two. That means administrators must be responsible for the security of both. However, in addition to the primary storage locations, the devices that workers use to access the data are potential attack vectors as well. The increasing adoption of the Bring Your Own Device (BYOD) paradigm complicates the process of securing data that might be stored in someone’s pocket on a device that might not be fully manageable by the enterprise administrators.
The security problem also extends beyond the logical extremities of the enterprise to the partners, clients, and consultants with which employees share data. These people use their own systems and devices that are even farther out of reach of the enterprise administrators. All these attack vectors can provide intruders with a way into the enterprise network, and once sophisticated intruders are inside, they often manage to stay there and extend their influence.
While there are always a certain number of casual cybercriminals who are relatively easy to repulse, the serious, professional penetration attempts that often afflict large enterprises can be incredibly sophisticated and take place over long periods of time. Microsoft 365 includes a powerful array of security tools that make it possible for administrators to implement various types of protection over the company’s data and the devices that access it, but these tools are not simple turnkey solutions. Enterprise administrators must design a security plan that prioritizes the sensitivity of the company’s data, assesses the vulnerability of the systems and devices on which the data is stored, identifies the users and their data needs, and specifies how the Microsoft 365 tools will be used.
Risk management
Typically, information is the most valuable resource a business possesses. When considering security measures for an enterprise network, the ultimate end of these measures is to protect the information. Protection against unauthorized users or devices is really just a means of protecting the data that those users can access and store on those devices. Computers and other hardware devices have monetary value, but the physical security measures of a data center—for example, the electronic door locks, the security guards, and the fire suppression systems—are there primarily to protect the information stored on the hardware and not so much the hardware itself.
The process of creating a security plan for an enterprise is known as risk management, which is the act of identifying the assets that need protection, determining the potential dangers to those assets, assessing the impact of those dangers to the organization, and implementing protective measures appropriate to the assets and the threats. Microsoft 365 includes a large collection of tools that can help with all phases of this process. The security technologies in Microsoft 365 are divided into four areas, as follows:
Security management
Identity-based protection
Information protection
Threat protection
The technologies in each of these areas are shown in Figure 3-2. An organization that is seeking to secure its enterprise network is unlikely to need all these technologies. Consider these to be a toolkit from which administrators can select the right tool for each task. Microsoft’s Core Services and Engineering Operations (CSEO) group has chosen the technologies protruding from the wheel shown in Figure 3-2.

FIGURE 3-2 Microsoft 365 security technologies used by the Microsoft CSEO group
Therefore, the first step of the risk management plan is to identify the types of information the organization possesses and determine the value of each information type to the business.
Identifying and valuing information assets
Companies often generate vast amounts of data, which conform to various levels of sensitivity. It is usually not practical for an organization to implement the ultimate level of security over all their data, so it is necessary to classify the information according to its function and value. Therefore, the risk management process should begin with an inventory of the organization’s information assets and a determination of each asset’s value to the company, taking into account its need for confidentiality, integrity, and availability. The factors to consider when compiling such an inventory are shown in Table 3-1.
TABLE 3-1 Risk factors for asset inventory
RISK FACTOR |
DESCRIPTION |
EXAMPLE |
Confidentiality |
Access and disclosure of sensitive information by unauthorized persons |
What if users’ passwords or Social Security numbers were stolen? |
Integrity |
Modification or damage of sensitive information by unauthorized persons |
What if the company’s payroll information or product designs were changed? |
Availability |
Prevention of access to sensitive information by authorized users |
What if the company’s client list or website was rendered inaccessible? |
The definitions used for information types will be specific to the nature of the business, as will their value to the business. For example, in the case of a company that uses its website to provide support information to customers, an attack that renders the site unavailable for several days would be an inconvenience. For a company that sells its products exclusively on the web, however, the unavailability of its e-commerce website for several days could be disastrous.
For a large enterprise, this type of asset inventory is typically not the exclusive province of the IT department. It will likely require the involvement of personnel from various departments and at various levels of the organization, including management, legal, accounting, and even clients and partners outside the company.
The value of an information resource might not necessarily be expressed in monetary terms. The result of a data threat might be lost productivity, the creation of additional work to restore or re-create the data, fines or penalties to government or regulating agencies, or even more intangible effects, such as bad public relations or lost customer confidence.
To quantify the inventoried assets, the best practice is to create a graduated scale that considers all the risk factors particular to the business. A general numerical scale from 1 to 3 or a risk gradation of low, medium, or high would work, with a larger number of grades if the security measures the administrators choose to implement warrant it.
The value or sensitivity of a data asset will determine the nature of the security mechanisms administrators use to protect it. Some types of data might be subject to legal or contractual compliance specifications, which impose strict limits on where and how they are stored and who can access them. The security requirements for this most sensitive data might define the highest value on the risk scale, which can call for extreme security measures such as on-premises storage in a secured data center, data encryption and redundancy, and highly restricted access permissions.
Other types of sensitive data might not even be subject to broadly categorical security mechanisms, such as those applied to file folders or specific file types. Microsoft 365 includes the Azure Information Protection (AIP) tool that can apply labels to documents containing sensitive information. Administrators can configure the labels to trigger various types of security, such as watermarks, encryption, and limited access. While users and administrators can manually apply the labels to documents, AIP is also capable of detecting sensitive information in documents and automatically applying labels to them. For example, when a user creates a Word document, administrators can configure AIP to detect values that appear to be credit card numbers, as shown in Figure 3-3, and apply a label to the file that calls for a specified degree of protection.

FIGURE 3-3 AIP configuration
Data that does not greatly threaten confidentiality, integrity, and availability is at the low end of the risk scale. This data will require some protection, but the security at the low end of the scale might be limited just to file system access permissions.
Inventorying hardware
Once the data sensitivity and the value of the data has been assessed, the next step of the risk management plan design process is to consider the technology used to store, access, transmit, and process that data. This includes the servers or cloud services where the data is stored when at rest, the client systems and devices used to access the data, the network components that carry the data between the various systems, and the applications that process the data.
In the same way that the data itself is inventoried in the previous phase, there should be an inventory of all the hardware involved in the storage of the data. This information can be used to locate the precise source of a security breach and to help prevent unauthorized devices from accessing secured company resources.
The primary storage locations for all sensitive company information should be servers located in a secured environment, such as a data center or server closet, or a cloud service, which should have its own security policies detailed in the service contract. However, the process of compiling an inventory of client systems and devices can be significantly more complicated. Workstations located at the enterprise sites are presumably already inventoried, but home computers and employees’ mobile devices, such as smartphones and tablets, need to be considered. Also, computers and devices belonging to people outside the organization, such as partners, consultants, temporary workers, and customers, need to be considered.
Administrators should document every device that comes into contact with company data. The inventory should include information such as the following:
Make The manufacturer of the device
Model The manufacturer’s model name and number for the device
Serial number The manufacturer’s serial number for the device
Owner The person or organization that is the owner of the device
User The person or persons who use the device to access company data
Location The place where the device is installed or if mobile, the location of the person responsible for it
Service ID The owner organization’s assigned ID number, if applicable
Operating system The operating system installed on the device
OS version The version and build of the operating system running on the device
Network provider The provider used by the device to access the Internet or the company network
Applications The applications on the device that are used to access company data
Information used The specific types of company data that the device can access
For workstations owned by the organization, this information is typically compiled during the system’s deployment process and can probably be imported into the inventory. For systems and devices owned by employees, the information-gathering process should be required before any access to sensitive company data is permitted.
Verification of the inventory information can be difficult for users who are frequent travelers or home computer users, but in the modern management model implemented by Microsoft 365, tight control of hardware devices is an essential element of enterprise security. For devices owned by people who are not employees of the organization, such as customers, the diplomatic aspects of enforcing these policies can be even more difficult, but administrators might be able to mitigate them by creating a risk level that provides these users with access only to a limited class of information that is not extremely sensitive.
In addition to the systems and devices that access company data, networking technology can also present an element of risk. The most obvious potential attack vector is wireless network devices, which are vulnerable to outside attacks in a variety of ways. Microsoft 365 includes Microsoft Intune, which enables administrators to create Wi-Fi network profiles that contain preshared keys and other security measures that prevent unauthorized devices from connecting to a company wireless network. There are also some extremely sensitive data types that can require special handling even for wired networks, such as compliance regulations that require network cables to be enclosed in sealed conduits for protection against wiretapping. Hardware-based security devices, such as firewalls, should also be included in the inventory.
When hardware that accesses sensitive information is compromised, the data is presumed to be compromised as well. Administrators can use the hardware inventory to ensure that the operating systems and applications on the devices are kept up to date with security patches and that antivirus and other security tools are updated. Administrators can also use Microsoft 365 tools to create compliance policies so that devices cannot access network resources unless they meet specific requirements, including up-to-date software.
The hardware security elements of a risk management plan can go beyond the capabilities of the tools in Microsoft 365. Protecting the hardware can include other mechanisms, including the following:
Physical security Software-based security measures cannot fully protect the data stored on a computer if intruders have physical access to the machine. Even if the intruders can’t compromise the data, they can always destroy it, which can be just as damaging to the organization. Physical measures, even those as simple as a locked door, are basic elements of any risk management plan. For mobile devices, which are always vulnerable to loss or theft, administrators can use Microsoft Intune mobile device management to implement the ultimate hardware solution: remotely erasing the data from the device.
High availability In addition to malicious or criminal intrusion, hardware devices are also liable to failures from wear and tear or destruction from natural disasters, such as fires, earthquakes, and extreme weather. High-availability measures, such as RAID arrays, redundant servers, and duplicate data centers, can preserve data against loss and ensure that the data remains available to users. For Microsoft 365 data stored in the cloud, the Microsoft Global Network maintains data centers at locations throughout the world, as shown in Figure 3-4, providing subscribers with a 99.9 percent availability rate.
Disaster recovery Data backups and cloud synchronization can enable sensitive data to be restored, even after an attack or a disaster renders the original data or the hardware on which it is stored unusable.

FIGURE 3-4 Microsoft Global Network data center locations
Classifying users
The third element of the digital estate that must be considered when creating a risk management plan is the people who actually access the data. Users, whether deliberately or inadvertently, are a constant vulnerability—if not an actual threat—to the organization’s data. After quantifying the organization’s information assets and their value and after inventorying the hardware used to store, access, transmit, and process the information, the next step is to list the people who have access to the information.
The people with access to the organization’s information certainly include employees who are authorized to create, view, and modify the data. However, a risk management team must consider the possibility of other individuals accessing the data as well. Anyone with physical access to computers on which data is stored or from which it is accessible is a potential threat. This includes cleaning and maintenance staff, repair people, and even security guards. Even if an individual doesn’t have the credentials needed to sign on to a computer, it is still possible for a person to steal or destroy the computer or remove a hard drive from it.
A risk management plan should include a list of everyone who has access to sensitive information and what exact information they can access. Access control policies should be designed to provide users with permissions only for the data they need and no more. Within the organization, administrators often do this by defining roles, granting the roles access to the required data, and then assigning individuals to those roles. This simplifies the process of authorizing new users, moving users to other jobs, and deauthorizing departing users. Administrators can then create an orderly lifecycle for each individual user’s identity, as shown in Figure 3-5.

FIGURE 3-5 Identity lifecycle for an individual user
Every person who is granted access to company data should have an individual user account, including people who are working on-site temporarily. Any convenience that might be realized by creating generic guest accounts and assigning them to temporary users as needed will be nullified by the difficulty these accounts can cause when investigating an incident involving data loss or unauthorized access.
The plan must also include the means of ensuring that the individuals signing on to computers are actually the people they purport to be. Password policies can ensure that users create passwords that are sufficiently long and complex and change them regularly. Microsoft 365 also includes several enhanced authentication mechanisms, including multifactor authentication options calling for a fingerprint scan or a code sent to a mobile phone in addition to a password.
Users with administrative privileges present a greater potential threat to company data. The risk management plan should include policies that require administrators to use standard user accounts for all typical work functions and administrator accounts only for tasks that require the additional privileges. This not only helps to protect the company data from accidental damage or deletion, but it also reduces the possibility of unauthorized software installation, whether intentional or not. Privileged access user accounts should have their own lifecycle policies with more stringent monitoring and control, as shown in Figure 3-6.
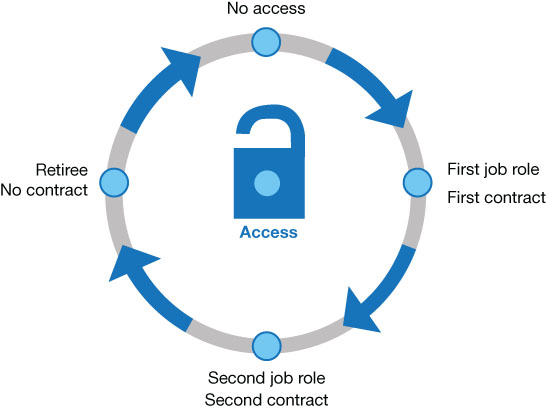
FIGURE 3-6 Lifecycle for a privileged access user account
Of course, even authorized users can be a threat, and the risk management plan should define the specific means by which new employees are vetted, which should include national (or international) background checks, credit histories, and confirmation of degrees and other credentials. For organizations working with data that is extremely sensitive, more extensive investigation of new hires might be in order.
Internal users are a major source of security incidents, although the incidents can be unintentional as well as deliberate. Disgruntled workers and industrial espionage are certainly legitimate causes of data theft or loss, but simple slips, such as leaving a signed-on computer unattended, can be equally dangerous. In addition to addressing malicious threats, a risk management plan should devote sufficient attention to accidental threats.
Anticipating threats
Arguably, the most difficult part of the risk management planning process is trying to anticipate all the possible threats that could afflict the company data in the future. The three basic risk factors for the data—confidentiality, integrity, and availability—can be exploited in any number of specific ways, but the general threat categories are listed in Table 3-2.
TABLE 3-2 Risk management threat possibilities
CONFIDENTIALITY |
INTEGRITY |
AVAILABILITY |
Theft of data by internal employee |
Accidental alteration of data by internal user |
Accidental damage or destruction of data by internal user |
Theft of data by external intruder |
Intentional alteration of data by internal employee |
Intentional damage or destruction of data by internal user |
Inadvertent disclosure of data |
Intentional alteration of data by external intruder |
Intentional damage or destruction of data by external intruder |
|
|
Damage or destruction of data by natural disaster |
The core of the risk management process is to anticipate potential threats in detail and use the information gathered earlier in the data, hardware, and user inventories to estimate the severity and likelihood of each threat. For example, the threat of the company’s client sales figures being disclosed when a travelling user misplaces his smartphone is far more likely than the threat of a competitor breaking into the company headquarters at night and hacking into a workstation to steal the same information. The severity of the threat in the two scenarios is the same, but the loss of a smartphone is the more likely occurrence, so administrators should expend a greater effort at mitigating that possibility.
In another example, a competitor’s burglary attempt might result in the theft of those same client sales figures; in another scenario, this same burglary attempt might cause deliberate damage to the company’s web servers, taking the company’s e-commerce site down for several days. The likelihood of these scenarios is roughly the same, but the web server damage is the far more severe threat because it interrupts the company’s income stream. Therefore, the more severe threat warrants a greater attempt at prevention.
Microsoft 365 provides tools that administrators can use to predict, detect, and respond to security threats. However, a comprehensive risk management plan goes beyond these types of tools and incorporates policies and includes purchasing policies, hiring policies, building policies, and administration policies.
Updating the plan
Risk management is not a one-time event; it must be a continual process to be effective. Security threats continue to evolve at a rapid rate, so the protection against them must evolve as well. At least once a year, the risk management team should repeat the entire assessment process, updating the inventories of all the organization’s information, hardware, and human assets to ensure that no changes have occurred without the company’s knowledge. The team must update the threat severity and likelihood matrix as well. New or updated threats will require new security tools, procedures, and policies to provide protection against them.
In addition to the internal updates of the risk management plan, an organization might want to engage outside contractors to perform a vulnerability assessment, which is an evaluation of the threats in an organization’s security infrastructure. Depending on the size of the organization and the current nature of its possible threats, a vulnerability assessment can be a minor and relatively inexpensive procedure or an elaborate and costly undertaking.
Some of the specific types of vulnerability assessments are as follows:
Network scan Identifies avenues of possible threats through internal network and Internet connections, including router, firewall, and virtual private network (VPN) configurations
Wireless network scan Evaluates the organization’s Wi-Fi networks for vulnerabilities, including improper configuration, antenna placement, and rogue access points
Host scan Identifies vulnerabilities in servers, workstations, and other network hosts, including port and service scans, configuration settings, and update histories
Application scan Examines web servers and other Internet-accessible servers for software vulnerabilities and configuration issues
Database scan Identifies database-specific threats in database servers and the databases themselves
Another possible method of assessing security vulnerabilities in an organization’s risk management system is to have a penetration test performed. A penetration test is a procedure in which an outside contractor is engaged to attempt an attack on the company’s systems to ascertain whether the potential vulnerabilities identified in the risk management process are actual vulnerabilities and to assess the organization’s response procedures.
Key security pillars
Microsoft 365 provides a variety of security tools and services that enterprise administrators can use to protect the various elements of their organizations. Based on the information gathered during risk management planning, the team can establish priorities that dictate the degree of security required and the specific elements that require priority attention. A comprehensive security implementation must distribute protection among the four primary pillars supporting the enterprise infrastructure, as shown in Figure 3-7.
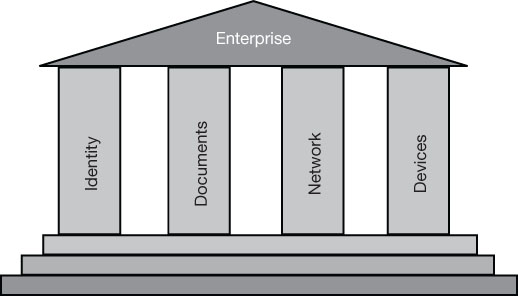
FIGURE 3-7 The four key security pillars
These pillars are as follows:
Identity The process by which a user is authenticated and then authorized to access protected resources
Documents The functions by which the organization’s data resources are protected from unauthorized access
Network The wired and wireless media that carry data signals, the components that provide Internet connectivity, and the protocols used to encode the signals, all of which are potentially vulnerable to attack
Devices The computers, smartphones, and other devices that access documents and other data via the network
These four elements function together to enable users to access the data they need, and Microsoft 365 includes tools that can provide protection in each of these areas. Depending on the needs of the organization and the possible threats identified, administrators can modify the degree of protection applied at each of these pillars. The tools and procedures that Microsoft 365 provides for these four main security areas are described in the following sections.
Identity
It’s easy to build a perfectly secure house; just omit all the windows and doors. Your possessions will be safe, but you won’t be able to get at them. In the same way, it would be easy to build a perfectly secure network by establishing a formidable perimeter around the sensitive resources and not letting anyone at all through it. This would be pointless, of course. Workers need access to those sensitive resources, and identities are the basis of that access. In enterprise networking, an identity is a collection of attributes that uniquely describe a security principal, that is, a specific individual and the resources that individual is permitted to access.
For data to be secure, the most fundamental types of protection are ensuring that the individuals accessing the data really are who they claim to be and that the individuals have been granted appropriate levels of access to the data they need. The process of confirming a user’s identity on the network is called authentication, and the process of granting a user access to specific data or services is authorization. Securing the identities of the network’s users is the process of making these procedures as safe and impenetrable as they can be.
The identities of an organization’s users are the prime target for cybercriminals because stealing a user’s name and credentials enables the attacker to access everything that the user knows about the company. News stories regularly report thefts of large blocks of identities from major companies, which endanger not just the companies’ sensitive data but their employees’ personal lives as well. For example, the theft of the names, addresses, and Social Security numbers that are part of any organization’s human resources records leave users open to credit fraud and numerous other criminal intrusions. For the organization, identity theft can be catastrophic in many ways, resulting in data theft, damage, or destruction that can prevent the company from doing business and cost it vast amounts of money.
The attacks that attempt to steal user identities can be extremely simple or incredibly sophisticated. A major security breach for an organization can begin with one intruder calling an unsuspecting user on the phone and claiming to be Jack Somebody from account maintenance in the IT department and talking the employee into disclosing the user’s login name and password. Once the intruder has one user’s credentials, it becomes easier for the intruder to gain others. This sort of lateral movement within the organization’s security infrastructure can be a slow and methodical process that eventually yields access to an identity with high-level access to the network and leads to a major security event. This is why administrators should take pains to protect all the organization’s identities, not just the ones with elevated privileges.
In Microsoft 365, Azure Active Directory (Azure AD) allows administrators to create user identities and performs the authentication and authorization processes, as shown in Figure 3-8. Azure AD is a directory service that is a cloud-based alternative to Active Directory Domain Services (AD DS), which has been the on-premises directory service for Windows networks since 1999. The primary objective in creating Azure AD is the ability to service identities and perform authentications and authorizations for cloud-based resources. This is an essential element of administering Microsoft 365.
FIGURE 3-8 Azure Active Directory admin center
An Azure-based Active Directory implementation is necessary for Microsoft 365 because AD DS is limited to providing on-premises security functions. Users must have access to the on-premises network to sign in to their organization’s AD DS domain controllers. The only way a remote user can authenticate to the company network using AD DS is to establish a connection to an on-premises server, such as a virtual private network (VPN) connection. Azure AD is strictly cloud-based and enables users working anywhere and with any device to sign in to the organization’s Microsoft 365 network and gain access to its services. Another advantage of a cloud-based directory service is that administrators can create identities for people outside the organization, such as partners, clients, vendors, or consultants, who need occasional or restricted access to company resources.
Note: Using Azure AD with AD DS
Azure Active Directory and Active Directory Domain Services are not mutually exclusive. For an organization that already has an AD DS infrastructure in place, it is possible to deploy Azure AD and create hybrid identities by synchronizing the two directory services. For more information, see “Understand identity protection and management,” later in this chapter.
Creating an identity in Microsoft 365 is a simple matter of supplying name values in a form like the one from the Azure Active Directory Admin Center shown in Figure 3-9. The Microsoft 365 Admin Center contains a similar form that also enables the creator of the identity to assign product licenses, such as a Microsoft 365 license, to the user. While creating identities is a quick and easy process, securing them can be considerably more complicated.
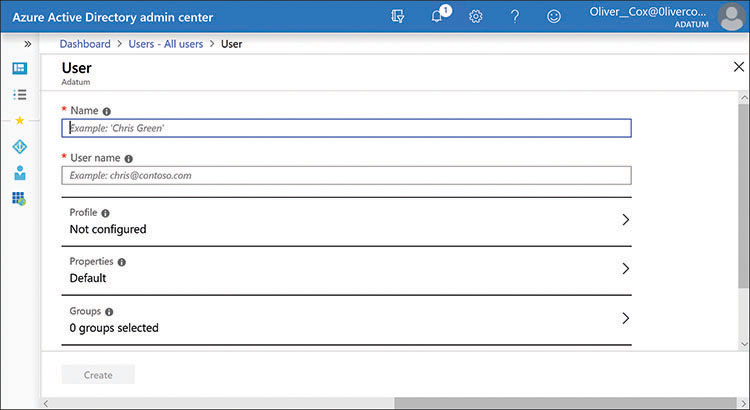
FIGURE 3-9 Creating an Azure AD user account
The traditional means of authenticating a user’s identity is for the individual to supply an account name and a password. In Microsoft 365, administrators can create password policies that compel users to create long and complex passwords and change them frequently. However, passwords are always subject to potential weaknesses that make them an unwieldy authentication mechanism, including the following:
Users might have difficulty remembering long or complex passwords and write them down in unsecured locations.
Users might share their passwords with coworkers for the sake of convenience.
Users with dedicated accounts that have elevated privileges might overuse their administrative passwords for everyday tasks.
Users might supply the same passwords for multiple services or resources, compounding the damage if a password on one server is compromised.
Users might be tricked into supplying their passwords by phishing or social engineering attacks.
Users’ identities might be compromised when their passwords are subjected to replay attacks, in which an intruder retransmits a captured password to gain access to a protected resource.
Users’ passwords might be compromised by malware that captures keystrokes and transmits them to an intruder.
Some users can be relentlessly clever in discovering ways to evade the password policies imposed on them.
Because some of the weaknesses of password-based authentication are caused by human failings rather than technological failings, the process of strengthening user passwords is often an educational one. Administrators can devise policies to mitigate some password weaknesses, though urging users to abide by them can be difficult.
For example, a 20-character, randomly generated, administrator-assigned password would be extremely difficult for attackers to compromise, but it might be equally difficult to put down the outright insurrection that could result from the users forced to use them. Because of the complications inherent in the use of passwords, Microsoft 365 supports other types of authentication mechanisms that administrators can use instead of (or along with) passwords.
Windows Hello for Business is a desktop authentication mechanism that can replace passwords with certificate or key pair authentication using a PIN or a biometric credential, such as a fingerprint scan or an infrared facial recognition process. Microsoft Authenticator is a mobile device app that enables users to sign in to a Microsoft account using a combination of authentication mechanisms, including PINs, biometrics, and one-time-passcodes (OTPs).
Note: Identity Protection
For more information on protecting identities, see “Understand identity protection and management,” later in this chapter.
Documents
As noted earlier in this chapter, virtually all the security mechanisms in Microsoft 365 are ultimately intended to protect the enterprise’s information, and documents are one of the primary containers for that information. The traditional method for securing documents is to apply access control permissions to them. Permissions take the form of access control lists that are stored as attributes of individual files and folders. An access control list (ACL) consists of multiple access control entries (ACEs), each of which specifies a security principal, such as a user or group, and the permissions that grant the principal certain types of access to the file or folder.
Permissions specify who can access documents and what actions users can perform. For example, a user might be able to read a document but not modify it, while another user might not even be able to see that the document exists. Permissions have been around for decades, and they enable users and administrators to restrict access to particular documents, but they must be applied manually and are difficult to manage for a large document collection. Someone also must keep track of which documents contain sensitive information that requires additional protection.
Microsoft 365 therefore includes security mechanisms, such as Azure Information Protection (AIP) and Data Loss Prevention (DLP), which can protect documents in other ways. The process of identifying documents containing sensitive data and securing them consists of the following four steps:
Discovery The location of documents containing sensitive information, either by automatic detection based on established data patterns or by prompting users to apply classification labels
Classification The application of labels to documents containing sensitive information that indicate what types of protection should be applied to them
Protection The implementation of specific security mechanisms to documents based on the classification labels that have been applied to them
Monitoring The process of tracking document access trends, activities, and events and taking action when necessary
The process of discovering documents containing sensitive information is highly dependent on the nature of the organization, the types of businesses it is engaged in, and the policies or regulations with which it must comply. Tools like Data Loss Prevention have preconfigured sensitive information types that enable the automated discovery of documents that contain common data patterns, such as credit card and Social Security numbers. Also, administrators can create customized sensitive information types that can discover documents that contain specific industry-based keywords and data patterns.
Like a physical label, the sensitivity labels provided by tools like AIP and DLP can warn users that a document contains sensitive information and recommend that certain actions be taken. The labels persist with the documents as they travel to different systems and are opened in other Office applications—even those on other computing platforms. However, AIP and DLP labels can also be configured to apply various types of protection, like those shown in Figure 3-10. The labels can cause documents to be encrypted, both at rest and in transit; limited to use with specific applications; restricted to specific users or devices; or configured to expire and even be deleted after a specified lifespan.
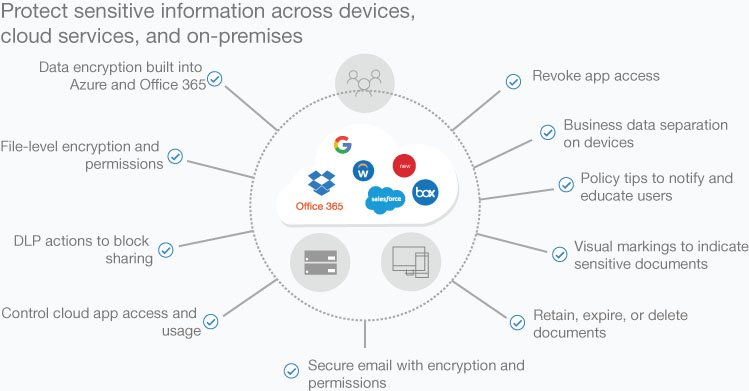
FIGURE 3-10 Microsoft 365 document protection mechanisms
Once the document classification and protection phases are complete, it is still the responsibility of administrators to monitor the reports and alerts that are generated by the security tools. For example, repeated attempts to access or share protected documents by the same user or device can indicate the presence of a security breach, even if the attempts fail. The monitoring process should include remediation as well so that an administrator who notices anomalous behavior can intervene by revoking document access privileges or quarantining files.
Network
The traditional network security model calls for the construction of a perimeter surrounding the enterprise premises; this traditional model has servers, workstations, and users all located inside the perimeter and firewalls protecting them by filtering out unwanted traffic. Remote users could connect to enterprise resources only by establishing a secured connection to a remote access server located in a DMZ on the perimeter network. A Microsoft 365 installation places substantial and potentially vulnerable resources outside the perimeter in the cloud, requiring a revised network security model.
Remote users might still connect to on-premises servers for some functions, but others will connect directly to cloud services. Also, the new emphasis on mobile devices means that users will be accessing enterprise resources from a wider variety of locations, including public locations, such as hotels and coffee shops, over which the company has no control.
The Microsoft 365 deployment process begins with an assessment and possibly a redesign of the network to ensure that Internet bandwidth and proximity to the nearest Microsoft cloud endpoint is optimized. Also, adapting the security model to a network infrastructure that includes cloud services requires a shift in emphasis from perimeter security to endpoint security, in which the focus is placed more on securing the locations of the data and the locations of the users accessing the data than on the network medium connecting them.
Note: Microsoft 365 Deployment
For a more detailed examination of the Microsoft 365 deployment process, see “Understand the concept of modern management,” in Chapter 2, “Understand core Microsoft 365 services and concepts.”
While the security perimeter around the existing data center must remain in force, the load on the firewalls might be substantially decreased by the migration to cloud services. In some cases, firewall barriers might have to be weakened deliberately to enable Office 365 traffic to reach the cloud. However, this does not mean that the standard means of protecting the firewalls themselves, such as changing their administrative login names and passwords on a regular basis, can be abandoned.
Endpoint network security means that the protective features built into the Microsoft 365 cloud services take on a more prominent role in the enterprise security strategy. Microsoft 365 administrators do not have control over the network traffic reaching the cloud services, nor can they erect a perimeter around every remote or mobile device that accesses the enterprise services. Therefore, instead of trying to block malicious traffic with firewalls, security comes from mechanisms such as multifactor authentication, Data Loss Prevention, and Cloud App Security.
This does not mean that the networks themselves cease to be vulnerable or that they can be left unprotected. Administrators must be wary of the threats that have always afflicted networks, including unauthorized packet captures, unprotected Wi-Fi networks, and rogue access points. For example, if an enterprise allows both managed and unmanaged devices to access company resources—regardless of the policies they use to control that access—it is still a good idea to keep the managed devices on a separate wireless network from the unmanaged ones. Also, internal Wi-Fi networks must still be protected by appropriate security and encryption protocols, and their administrative passwords and preshared keys must be modified on a regular basis.
Devices
If one of the two main innovations of Microsoft 365 is the use of cloud-based services, the other is the ability of users to access those services using many different types of devices that run on various computing platforms and work at any location that has Internet access. As noted earlier, VPN connections have long enabled remote users to access the company network from home or while traveling, using a laptop or desktop. VPNs use a technique called tunneling to protect the data as it is transmitted over the Internet. In subsequent years, there were a few mobile devices—nearly always supplied to users by the company—that were able to access a remote network, but with limited utility, such as email only. Today, Microsoft 365 enables remote users working with desktops, laptops, tablets, and smartphones to access virtually any enterprise service or resource that they could access using an on-premises workstation. The trick, however, is not just to make this access possible, but to make it secure as well.
Device security in Microsoft 365 therefore must address two relatively new issues:
Mobile devices that frequently operate outside of the organization’s protective perimeter
The increasing use of mobile devices that are not selected and owned by the company
Because mobile devices can access any and all sensitive information maintained by the enterprise, it is essential that there be some means to protect that information from the threats to which all mobile devices are subject, including loss, theft, and misuse.
While administrators can still use traditional access-control measures, such as file system permissions, to regulate who is able to work with the organization’s sensitive data, it is the Azure Active Directory and Microsoft Intune services that are primarily responsible for ensuring that the devices used to access that data are safe. Microsoft 365 supports a large number of mobile computing platforms, including the following:
Windows 10
Android
Android enterprise
iOS
macOS
The interaction between mobile devices and the Microsoft 365 cloud services is a complex one, as shown in Figure 3-11; however, as you can see in the diagram, Microsoft Intune functions as a clearing house for many of these services and uses Azure AD for authentication and authorization.
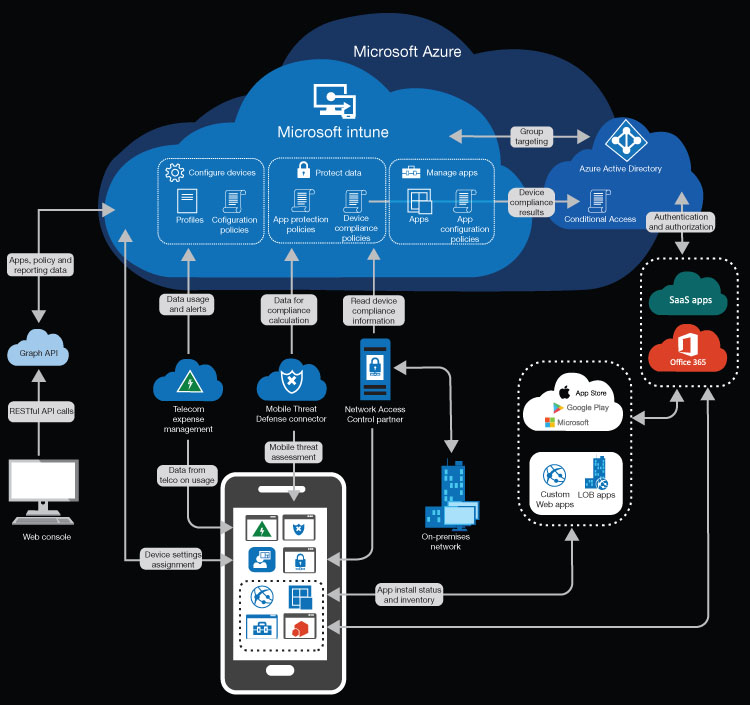
FIGURE 3-11 Microsoft Intune service architecture
Even though the organization might support a BYOD (Bring Your Own Device) policy for its users, it is essential that those devices be subject to some form of enterprise endpoint security. This is the primary function of Microsoft Intune, which is Microsoft 365’s endpoint management tool; administrators use Intune to enroll users’ devices and exercise some degree of management on them. By creating health compliance policies using Intune, enrolled devices can be checked for adherence to those policies before Azure AD authorizes them to access enterprise services and information. This is known as conditional access. Because Azure AD and Intune both operate in the cloud, they can function outside of the enterprise’s premises perimeter, just like the mobile devices, and they can control access to the other Microsoft 365 services from any location.
The process of securing devices begins with their enrollment using Microsoft Intune, at which time an administrator must decide what type of management will be imposed on the device. Mobile Device Management (MDM) grants the organization nearly complete control over the device, requiring the user to comply with all the enterprise policies. MDM even allows an administrator to perform a remote wipe of the entire device if it should be lost or stolen, which ensures that any sensitive data is not compromised further.
MDM is intended primarily for use on company-owned devices; it can be problematic to some users who might not like the idea of granting the organization such comprehensive control over their personal property. For example, MDM policies might require smartphone users to sign on with a password or use another authentication mechanism every time they use their phones—something which users might find to be inconvenient.
The alternative is Mobile Application Management (MAM), which provides administrators with control over specific applications running on a device, but it does not provide control over the entire device itself. For example, a similar policy in MAM might require the users to sign in when using Microsoft Exchange to access their email, but they don’t have to sign in every time they turn on their phones. MAM also enables administrators to wipe company data from the phone, but only the data associated with the managed applications can be wiped.
Cloud App Security is another Microsoft 365 tool for mobile and other devices; Cloud App Security is a cloud access security broker application that scans network resources to detect the cloud applications that users are running, and it detects unauthorized Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) products that might be in use. The object here is to detect “shadow IT”—that is, cloud applications that have not been approved by the IT department and which could be a threat to enterprise network security.
Cloud Discovery is the process by which Cloud App Security examines traffic logs from firewalls and proxy servers and compares the information to Microsoft’s cloud app catalog, which contains more than 16,000 cloud applications. The catalog includes an assessment of each application as a potential threat, and scores are based on more than 70 risk factors.
Once Cloud App Security has compiled a report of the cloud applications being used, administrators can then sanction the applications they want employees to use and unsanction those they do not want them to use. For the sanctioned applications, Cloud App Security supports the use of APIs supplied by the cloud application providers. These APIs enable Cloud App Security to function as an intermediary between cloud applications and the enterprise’s users, as shown in Figure 3-12, by accessing activity logs, user accounts, and data sources. Cloud App Security can then use this information to monitor usage, enforce policies, and detect threats.

FIGURE 3-12 Interactions of Cloud App Security with an enterprise network and cloud applications
Quick check
Which of the following is not one of the four key security pillars protecting the enterprise infrastructure?
Identity
Documents
Cloud
Devices
Quick check answer
Cloud is not one of the four key security pillars. The correct fourth pillar is Network.
Skill 3.2: Understand identity protection and management
Identities are the fundamental security issue in Microsoft 365 or any network environment. Identities are the doors and windows that provide ingress and egress to the enterprise network environment. They are essential if anyone is going to be able to actually use the information stored by the enterprise services. Therefore, protecting those identities from improper use is a major priority in the design, implementation, and maintenance of an enterprise network.
An identity is a logical representation of a user in a network environment. To users, an identity is a name that they type to sign in to the network, along with a password or some other means of authentication. To administrators, an identity is a collection of attributes associated with a particular individual, as shown in Figure 3-13. The sign-in name is one of those attributes, but there can be many others, including personal information, such as a home address, telephone number, job title, and so on.

FIGURE 3-13 User attributes in the Azure Active Directory Admin Center
An identity also typically includes a list of the groups to which the individual is a member. Administrators use groups to assign rights and permissions to individuals. When a group is assigned rights and permissions to access network resources, all the group’s members automatically inherit those rights and permissions. This is an efficient alternative to assigning multiple rights and permissions to each user identity individually.
Identities
Every computer or mobile device has the capability to maintain a user’s identity and employ it to protect the device from being accessed by anyone else. However, when a user wants to access applications, services, or data from his or her company’s network, another identity is needed; this identity is created and maintained by the network’s administrators and stored on the network itself, not on the user’s computer or other device.
On-premises identities
Beginning with the Windows 2000 Server release, enterprise identities were stored in Active Directory, which is an on-premises directory service that is still a part of the Windows 2019 Server product, although it is now called Active Directory Domain Services (AD DS). Installing the AD DS role on a computer running Windows Server enables it to function as a domain controller, which contains an object-oriented database of user identities and other network resources, including groups, computers, and applications. AD DS is a domain-based hierarchical database that uses container and organizational unit objects to separate users and other resources into logical collections, which usually represent the departmental or geographic divisions of the company.
Typically, enterprise networks have multiple domain controllers, which administrators configure to synchronize the contents of their AD DS databases with each other, for fault tolerance and high availability purposes. AD DS uses multiple master replication, which means administrators can create or modify users and other objects on any domain controller, and the changes will be replicated to all of the other domain controllers, as shown in Figure 3-14.
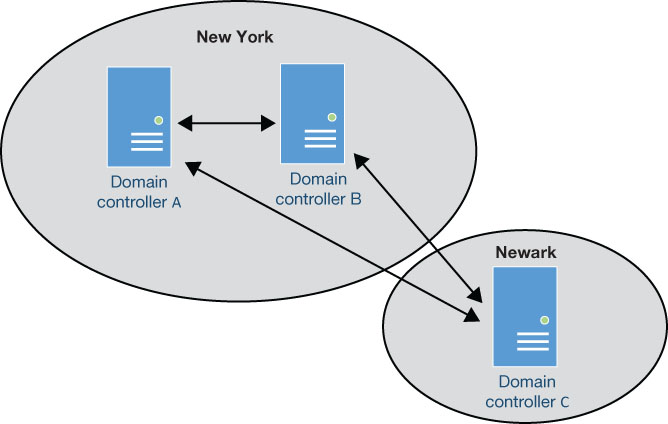
FIGURE 3-14 Active Directory Domain Services multiple master replication
Administrators can create AD DS user objects using graphical tools, such as Active Directory Users and Computers, as shown in Figure 3-15, or command-line tools, such as the New-ADUser cmdlet in Windows PowerShell. The user objects in AD DS are strictly on-premises identities. Domain controllers must be located within the network perimeter and are not directly accessible from the Internet. When users access on-premises resources, their identities are authenticated and authorized by the nearest domain controller, which uses a protocol called Kerberos to perform a complicated ticket-based authentication procedure. Users outside the network perimeter can only perform an AD DS sign in to the network by establishing a VPN connection to a remote access server. This provides users with a presence on the internal network, which enables them to access internal resources.
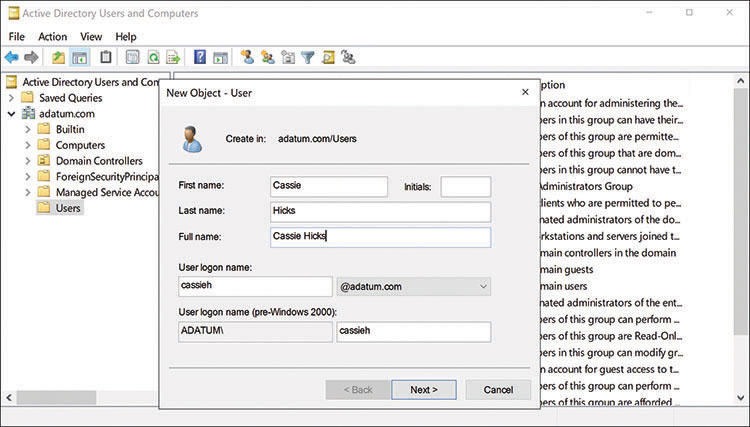
FIGURE 3-15 The New Object – User dialog box in the Active Directory Users And Computers console
Cloud identities
Because AD DS can only perform its functions when both the user and the resources to be accessed are located on-premises, it is not a viable solution for cloud-based applications and services. Therefore, Microsoft had to devise an alternative authentication and authorization solution for its cloud-based products, such as Microsoft 365. This solution is Azure Active Directory (Azure AD), a cloud-based directory service alternative (or companion) to AD DS in which administrators create cloud identities.
Microsoft 365 relies on the Azure Active Directory service for its identity management, and all the Microsoft 365 services use Azure AD for authentication and authorization. Microsoft 365 subscribers (as well as Office 365 and Windows Azure subscribers) become Azure AD tenants automatically. When a user accesses an Office 365 application in the cloud, as shown in Figure 3-16, Azure AD is the invisible intermediary that confirms the user’s identity with the authentication mechanisms the Microsoft 365 administrators have selected. In the same way, Azure AD authorizes the user’s access to the application and to the files the user opens in the application.

FIGURE 3-16 Azure Active Directory provides authentication and authorization services for Microsoft 365 applications and services
Unlike AD DS, it is not necessary for administrators to install multiple domain controllers for Azure AD or configure directory replication. An Azure AD tenancy is automatically replicated to multiple data centers in the Microsoft Global Network. Also, unlike AD DS, Azure AD uses a single master replication model. There is only one primary replica of an Azure AD tenant, and all new users and account modifications are written to that primary replica. The changes are then automatically replicated to multiple secondary replicas at different data centers, as shown in Figure 3-17. All incoming read requests are handled by the secondary replicas, using the replica closest to the requesting user, application, or service. Because there are many secondary replicas, the Azure AD service is always available. Because there is only one primary replica, it works differently by using a deterministic failover procedure.

FIGURE 3-17 Azure Active Directory single master replication
To create users in Azure AD, administrators can use several different tools, including the Microsoft 365 Admin Center and the Azure Active Directory Admin Center. Azure ID’s authentication and authorization are also token-based, but the protocols and procedures that Azure AD uses are different from those that AD DS uses. Instead of Kerberos, Azure AD uses OAuth 2.0 or OpenID Connect.
Hybrid identities
It is important to understand that Azure Active Directory is not intended to be a replacement for Active Directory Domain Services, nor are the two interchangeable. If an organization has internal servers and an on-premises AD DS implementation, they should not expect to be able to migrate their user identities from AD DS to Azure AD and then deprecate their AD DS domain controllers. It is equally important to understand that Microsoft 365 requires Azure AD; it is not possible to use AD DS identities to authenticate and authorize users for Microsoft 365 applications and services. The converse is also true; it is not possible to use Azure AD identities to provide authentication and authorization services for on-premises resources.
It is, however, possible to use Azure AD and AD DS together, creating what are known as hybrid identities. A hybrid identity is a user account that exists in both the Azure AD and AD DS directories with the same set of attributes. The usual scenario for the use of hybrid identities is an organization that has an existing AD DS infrastructure, but which is considering an expansion into the cloud by using Software as a Service (SaaS) products, such as Office 365. The organization might have hundreds or thousands of on-premises identities, but the prospect of having to re-create them in Azure AD and then maintain two identities for each user could be a deciding factor in the organization choosing not to use cloud services.
Hybrid identities are a solution to this problem. Because the assumption is that the AD DS identities already exist, creating hybrid identities is a matter of synchronizing them from AD DS to Azure AD. To do this, administrators must install a tool called Azure AD Connect on the on-premises network, which accesses the AD DS directory on a domain controller and replicates all the user accounts it finds to Azure AD (along with their passwords and other attributes).
Note: First Synchronization
When Azure AD Connect synchronizes on-premises AD DS identities to Azure AD for the first time, new cloud identities for the users are created, but product licenses are not automatically assigned to them. Therefore, in a new Microsoft 365 hybrid identity deployment, administrators must add Microsoft 365 licenses to the users in Azure AD after the first synchronization is complete. The administrators can add licenses to Azure AD users individually, but the process can also be performed dynamically by making the license assignment a result of group membership.
Passwords in AD DS are stored as a hash (a one-way mathematical algorithm that cannot be reversed to extract the password), and by default, Azure AD Connect applies another hash algorithm to the AD DS hash. Thus, the password transmitted by Azure AD Connect to the cloud is secured by it being a hash of a hash. The passwords in Azure AD are never stored in plain text, nor are they ever encrypted using a reversible algorithm.
After the initial synchronization, Azure AD Connect continues to detect changes made to the AD DS identities and replicates those changes to the corresponding Azure AD identities in the cloud, as shown in Figure 3-18. Therefore, administrators managing hybrid identities must use the AD DS tools, such as Active Directory Users and Computers, to make changes to the on-premises user accounts. Because the identity replication flows in only one direction—from AD DS to Azure AD—no one should make changes directly to the cloud identities using the Microsoft 365 tools.

FIGURE 3-18 Azure AD Connect identity synchronization
Note: Azure AD Application Proxy
While Azure AD is not a replacement for AD DS, it can provide remote users with access to internal web applications using a feature called Application Proxy. Application Proxy consists of a service that runs in the cloud and a connector that administrators install on an on-premises server. When remote clients attempt to access the internal web application with a URL, they are directed to an Azure AD sign-in page, where they authenticate using an Azure AD identity. The clients then pass the token they received as a result of the sign-in to the Application Proxy Service, which forwards it to the Application Proxy Connector on the internal network. The connector then forwards the user’s request to the internal web application, which returns its response to the client through the connector and the Application Proxy Service.
Hybrid identities can simplify the identity management process for administrators, but they can also simplify the user experience as well. For administrators who are adding cloud services to an existing on-premises infrastructure, the main objective should be to make user access to the cloud applications as invisible as possible. One way to do this is to implement single sign-on (SSO) so that users can authenticate with their familiar AD DS credentials and receive access to the cloud services without having to sign in again, either at the Azure AD level or in the individual applications. Another option, called seamless single sign-on, enables users connected to the enterprise network to be automatically signed in without any interactive authentication. Seamless sign-on is compatible with the password hash synchronization and pass-through authentication methods, but it is not compatible with the federated authentication method.
During the process of installing Azure AD Connect, an administrator must select the authentication method that Azure AD will use to provide the users with access to cloud resources. There are three options to choose from, as follows:
Azure AD Password Hash Synchronization The simplest form of the Azure AD Connect authentication methods, which requires no additional infrastructure to implement. Azure AD Connect creates a hash of each user’s AD DS password hash and applies it to the corresponding Azure ID identity. This enables users to access both on-premises and cloud resources using the same password, as shown in Figure 3-19. Azure AD Connect updates the cloud identity passwords every two minutes without interrupting a session in progress when a password change occurs. Because the password hash synchronization model is fully implemented in the cloud, it shares the high availability of the other Microsoft cloud services. To ensure continuous operation, Microsoft recommends the installation of Azure AD Connect on two or more servers as a standby, preferably at different locations.

FIGURE 3-19 Azure AD password hash synchronization
Azure AD Pass-Through Authentication Avoids all cloud-based password validation by using a lightweight pass-through authentication agent installed on on-premises servers. (Microsoft recommends three.) When users sign in to Azure AD, their requests are forwarded to the agent, which forwards them in turn (in encrypted form) to a domain controller for validation of the users against their on-premises identities in AD DS, as shown in Figure 3-20. The agents require only outbound access to the Internet and access to an AD DS domain controller, so they cannot be located on a perimeter network. The end result is the same user experience as password hash synchronization, but this method avoids the storage of user passwords in the cloud in any form and enables administrators to enforce on-premises Active Directory security policies, such as disabled or expired accounts, and it allows sign-in hours and complies with contracted security requirements. It is also possible to deploy password hash synchronization in addition to pass-through authentication to function as a backup in the event of an on-premises failure that prevents the agents from functioning.
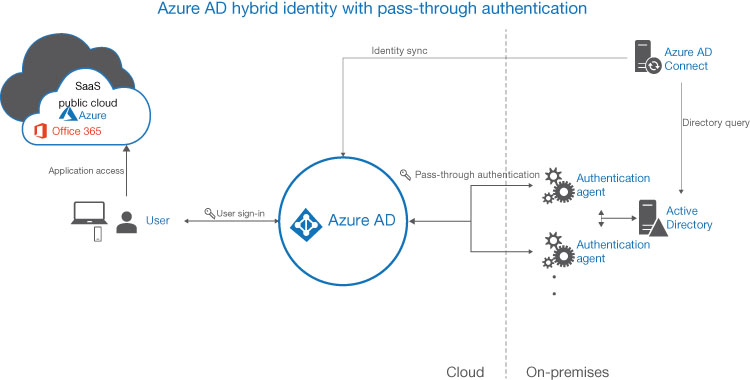
FIGURE 3-20 Azure AD pass-through authentication
Federated Authentication Offloads the authentication process to an external solution that the organization trusts, such as Microsoft Active Directory Federation Services (AD FS). The configuration and management of the authentication process— as well as the user experience—are the responsibility of the federated system; Azure AD is not involved. Depending on the security requirements of the organization, the sign-in process with the federated system might be simpler or more complicated than that of Azure AD. The federated system typically consists of a load-balanced cluster of servers—called a farm—for high availability and fault-tolerance purposes. Because the federation servers require access to both Azure AD and AD DS domain controllers, the servers themselves (or proxy intermediaries) must be located in the DMZ of an on-premises perimeter network, as shown in Figure 3-21. Organizations typically opt for the federated authentication option because they want to (or are compelled to) use an authentication method that Azure AD does not support, such as certificates or smart cards. The additional hardware, software, and administrative infrastructure that the federated authentication method requires can be a significant extra expense; in many cases, organizations that choose this option do so because they have already invested in the infrastructure. It is also possible to deploy password hash synchronization in addition to federated authentication, so that it functions as a backup in the event of an on-premises failure that prevents federation servers or their proxies from functioning.
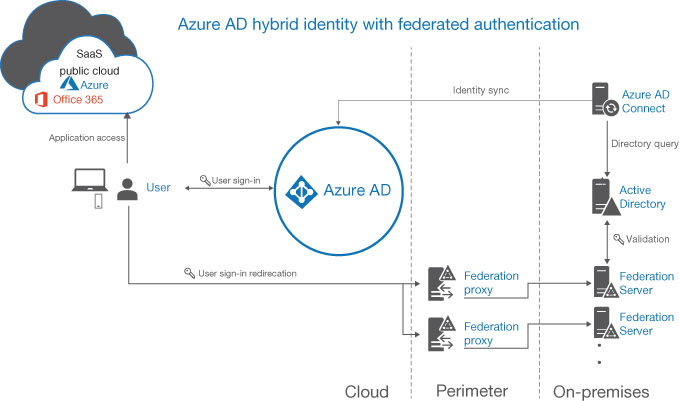
FIGURE 3-21 Federated authentication
Important: Selecting an Authentication Method
Selecting a cloud authentication method for hybrid identities is a critical decision for administrators because it provides users with access to all the cloud resources and is the basis for many other security features in Azure AD. It is also important to note that it is difficult to change the authentication method after the deployment is complete, so administrators should consider their options carefully.
Authentication
If identities are the doors and windows in the enterprise network environment, authentications are the locks that keep them secure. An administrator can grant a specific user the permissions needed to access a file, an application, or a service, but this means nothing unless there is some way to ensure that the individual using those permissions is really the person to whom they were assigned. Authentication is how individuals actually prove their identities.
There are three basic means of authenticating an individual’s identity. The individual must supply one or more of the following:
Something you know A piece of information that only the individual possesses, such as a password or PIN
Something you are A characteristic that is unique to the individual, such as a fingerprint or a facial scan
Something you have A unique item that the individual possesses, such as an ID card or a smart phone
Password authentication
A password is something you know, and this has been the standard means of authenticating users’ identities for many years. Password authentication costs nothing to implement, and it can be relatively secure. However, there are many possible flaws in the password authentication model. For example, passwords can be forgotten, shared, written down, easily guessed, or overly simple.
To prevent users from creating passwords that provide too little security, there are policies that specify rules for the creation and maintenance of passwords. Operating systems and directory services, such as Azure AD and AD DS, include tools that administrators can use to create and enforce such policies.
In Azure AD, user accounts are subject to the following password policies:
Characters allowed Specifies the characters that users are permitted to use when creating passwords, including upper- and lowercase alphabetical characters, numbers, blank spaces, and most symbols.
Password restrictions Specifies that passwords must have from 8 to 256 characters and must contain three of the following four character types: uppercase, lowercase, number, and symbol.
Passwords expiry duration Specifies that passwords expire in 90 days by default. The value can be modified using the Set-MsolUser PowerShell cmdlet.
Password expiry notification Specifies that the user will receive a password expiration notification 14 days before the password is set to expire. The value can be modified using the Set-MsolPasswordPolicy PowerShell cmdlet.
Password expiry Specifies a default value of False, indicating that the password will expire after the Passwords expiry duration interval. The value can be modified using the Set-MsolUser PowerShell cmdlet.
Password change history Specifies that users cannot reuse the same password when changing passwords.
Password reset history Specifies that users can reuse the same password when resetting a forgotten password.
Account lockout Causes users to be locked out of their accounts for one minute after 10 unsuccessful but unique sign-in attempts. Additional unsuccessful attempts result in longer lockout intervals.
In AD DS, administrators can configure password settings using Group Policy. The available settings have slightly different names, but their functions are essentially the same.
These password policies are designed to prevent users from creating passwords that are overly simple for the sake of convenience, but password security is difficult for administrators to enforce. Users can still create passwords that would be easy for attackers to guess by using their children’s names and birthdays, for example. There is also no software setting that can prevent users from writing their passwords down or sharing them with their coworkers.
As threats to network security become ever more severe, administrators have sought for ways to enhance the security of the authentication process. There have been alternative authentication methods available for many years, which could conceivably augment or replace passwords, but until relatively recently, these technologies were too expensive or inconvenient to be practical for the average user base. The increased need for identity protection has brought these authentication technologies to a wider market, however, resulting in lower prices, and the need is increasing constantly. Microsoft 365 includes the ability to enhance the security of the authentication process in a variety of ways.
Multifactor authentication
Multifactor authentication is a procedure in which users prove their identities in two or more ways. Typically, in addition to a password—something you know—they supply a different authentication factor: something you are or something you have.
SOMETHING YOU ARE
The something you are is usually some type of biometric scan. The Windows Hello for Business feature in Windows 10 supports multifactor authentication with biometric scans as one of the factors. It is also possible to use the Microsoft Authenticator app for mobile devices as a biometric scanner that enables users to access Microsoft 365 resources with no password.
Fingerprint readers are inexpensive and are becoming an increasingly common feature on laptops and other mobile devices. There are also aftermarket keyboards for desktop computers with integrated fingerprint readers as well. Fingerprint scans do not provide impenetrable security; fingerprints can conceivably be duplicated, and a scan of a finger would presumably still work, even if it was not attached to its owner. However, in combination with a password, fingerprint scans provide a multifactor authentication solution that could not be penetrated casually.
Facial recognition is another type of biometric scan that Windows Hello can use for multifactor authentication. Cameras are all but ubiquitous in modern society, so it would seem that the hardware costs of a facial recognition system are minimal. This is not the case, however, at least with Microsoft’s facial recognition products. Facial recognition raises questions both of security and of privacy. If a computer can recognize a person’s face as a security factor, what would stop an intruder from holding up a picture of the person to the camera? And where is the image of the user’s face being sent to accomplish the authentication?
Microsoft has answers to both questions. Windows Hello for Business supports the use of facial recognition for user authentication, but it requires a camera with a separate infrared light source and near infrared sensor. The main problem with facial recognition systems on personal devices is that people might use them in any kind of lighting. Near infrared imaging provides a consistent image regardless of the visible light conditions. Windows Hello also does not store images of the user’s face and never transmits them to other locations for authentication. When a user first enrolls in Windows Hello, the Windows Biometric Framework processes a facial image within the device and stores it as an enrollment profile. In subsequent authentication attempts, the system performs the same process and compares the results to the profile.
SOMETHING YOU HAVE
While the something you have in multifactor authentication can be a smart card or some other form of identification, in Microsoft 365, it is usually a cell phone. This is a more practical option because most people today carry cell phones with them, while card readers far less common.
It has already become common for Internet websites to require a secondary authentication factor, usually in the form of a code (called a one-time password or OTP) sent to the user’s cell phone as a call or SMS text. The user supplies the code in the website and authorization is granted. Microsoft 365 supports this method for multifactor authentication of users’ Azure AD identities, among others.
The cell phone-based options for Azure AD Multifactor Authentication (MFA) are as follows:
SMS Text Of OTP Code To Mobile Phone After the user completes the password authentication, Azure AD sends a text message containing an OTP code to the user’s preconfigured telephone number. The user types the code into the sign-in screen to complete the authentication.
Automated Voice Call To Mobile Phone After the user completes the password authentication, Azure AD generates an automated voice call to the user’s preconfigured telephone number. The user answers the call and presses the phone’s # key to complete the authentication.
Notification To Mobile App After the user completes the password authentication, Azure AD sends a notification to the Microsoft Authenticator app on the user’s smartphone. The user taps the Verify button in the app to complete the authentication.
Verification Code In Mobile App The Microsoft Authenticator app generates a new OATH verification code every 30 seconds. After the user completes the password authentication, the user types the current verification code from the Microsoft Authenticator app into the sign-in screen to complete the authentication.
Of course, cell phones can be lost, stolen, or destroyed, so any authentication method that relies on them is not going to be completely secure, but in combination with a password, they provide a significant barrier against the standard attacker. Multifactor authentication is not required for Microsoft 365, but it is rapidly becoming a de facto standard for network security, largely because many administrators are finding that they have reached the limit of password authentication, as far as users’ tolerance is concerned.
Administrators can enable multifactor authentication for specific users using the Azure Active Directory Admin Center. When the users next sign on, a screen informs them that more information is required. Another screen, shown in Figure 3-22, then enables them to enter a phone number and specify whether the initial contact to a user should be through a code sent to the user’s cell phone or through a mobile app, such as Microsoft Authenticator.
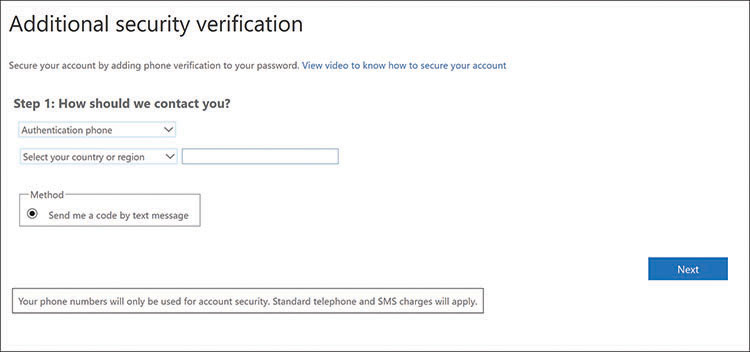
FIGURE 3-22 The initial Multifactor Authentication configuration interface
After the initial successful multifactor authentication, another screen appears, as shown in Figure 3-23, on which the users can select from among the cell phone–based authentication options listed earlier and configure a phone number or the Authenticator app.

FIGURE 3-23 The second Additional Security Verification - App Passwords screen
Identity protection
All identities are a potential source of risk for the entire network, no matter what level of privileges they possess. Once attackers compromise one identity, it becomes relatively easy for them to spread laterally within the enterprise and compromise others. For that reason, administrators should make every effort to protect all identities, not just the ones with administrative privileges.
One of the key innovations of Microsoft 365 is the greater emphasis on proactive threat detection and remediation. Azure AD can provide this type of security for user accounts with a feature called Azure AD Identity Protection. Identity Protection works by evaluating the sign-in activities of individual user accounts and assigning them risk levels that increment when multiple negative events occur. There are two risk levels associated with each identity, as follows:
Sign-in risk The probability that an unauthorized individual is attempting to authenticate with another person’s identity
User risk An accumulated probability that a specific identity has been compromised
Azure AD Identity Protection recognizes the following risk events and modifies an identity’s two risk levels based on the order and frequency in which they occur:
Atypical travel The user signs in from a location that is not typical for the user or that is geographically impossible, based on the user’s other recent sign ins. Azure AD takes into account the travel time between the locations and gradually develops its own profile of the user’s habits, which helps to prevent the occurrence of false positives (that is, conclusions of risk from sign-in patterns that are common for that user).
Anonymous IP address The user signs in from a browser that suppresses the user’s IP address, such as Tor or a virtual private network (VPN) client. The user signing on might or might not be the owner of the identity, but Azure AD considers the anonymity itself to be suspicious.
Unfamiliar sign-in properties The user signs in from a client that has unfamiliar properties, such as a new location or an unusual IP address or autonomous system number (ASNs), based on the user’s previous activities. For new identities, there is a period of information gathering that lasts at least five days, during which Azure AD makes no risk assessments using this criterion.
Malware linked IP address An identity is associated with an IP address that has previously been used to contact a known bot server on the Internet. The system is then assumed to be infected with malware and considered to be a risk.
Leaked credentials An identity is determined to use credentials that are known to have been compromised. Microsoft gathers information about such credentials from numerous sources, including law enforcement agencies, security consultants, and illicit websites.
When these events occur, Azure AD evaluates them and modifies the behavior of the authentication process according to criteria established by administrators. There are obviously many possible combinations of behaviors that Azure AD might have to take into account when evaluating the risk levels of an identity. For example, if the same risk events occur repeatedly, the risk levels will continue to rise until a drastic reaction might be required, such as blocking all access to the identity.
The basic Azure AD Identity Protection process is illustrated in Figure 3-24.

FIGURE 3-24 The Azure AD Identity Protection risk evaluation process
As an example, when a user attempts to sign in with a simple password from an anonymous IP address, Azure AD determines that it is a risk and assigns it a sign-in risk level of medium. This risk level causes Azure AD to implement a Conditional Access policy that imposes a specific action, such as requiring multifactor authentication during the sign-in process. If the user successfully completes the multifactor authentication, the user risk level remains unchanged.
However, if the user fails to complete the multifactor authentication, Azure AD considers this to be a possible indication that the identity has been compromised and raises the user risk level. The next time the user attempts to sign on, the process might proceed completely normally, with no sign-in risk detected; however, the user risk level associated with the identity persists, and Azure AD might be configured to prompt the user to change the password as a result.
Azure AD Identity Protection is included only with the Azure Active Directory Premium P2 plan, which is supplied with the Microsoft 365 Enterprise P2 edition.
![]()
Exam Tip
The additional security provided by Azure AD Identity Protection is applicable only to cloud-based identities, not to the on-premises identities in Active Directory Domain Services. Microsoft’s increased emphasis on cloud-based solutions, such as Office 365 and now Microsoft 365, means that the latest innovations in security and other areas are not being ported to the traditional on-premises versions. It is for this reason that Microsoft is recommending that enterprise networks shift more of their applications and services away from on-premises servers and into the cloud. When preparing for the MS-900 examination, candidates should be conscious of this emphasis on the cloud and be careful to distinguish Microsoft’s cloud-based products from its on-premises products.
Protecting documents
The fundamental purpose of identities is to protect documents and other data. When protecting identities, the threat of lateral penetration forces administrators to apply equal protection to all of them, regardless of their privileges. When protecting documents, however, the security can and should be more selective. While an enterprise might have hundreds or thousands of identities to protect, it might easily have hundreds of thousands or millions of documents, and this makes applying equal protection to them all impractical. Therefore, it is important for administrators to identify the documents containing sensitive data, which require more protection.
As discussed earlier in this chapter, Azure Information Protection (AIP) and Office 365 Data Loss Prevention (DLP) are tools that enable administrators and users to apply classification labels to documents and specify security measures that are applied to the documents based on those labels. While these tools can, in some cases, detect sensitive data within documents based on criteria that administrators specify, there are many other cases in which it is up to the users to apply the labels correctly to their own documents.
Note: Information Protection and Data Loss Prevention
For more information on Azure Information Protection and Office 365 Data Loss Prevention, see the “Documents” section, earlier in this chapter.
The technological aspects of implementing tools such as AIP and DLP are relatively straightforward; however, the administrative, cultural, and educational aspects of the implementation can be more troublesome, especially in a large enterprise. For these tools to function effectively, the classification labels representing the various levels of data sensitivity must be understood by everyone involved and applied consistently throughout the organization.
When the intention is to create a single classification label taxonomy that the entire enterprise will use, it makes sense for representatives from all areas and all levels of the enterprise to have a say in the design of that taxonomy. Unless the terms used for the labels mean the same thing to everyone, there is a chance that documents could be labeled incorrectly, or worse, not labeled at all when they should be.
With the labeling taxonomy agreed on and in place, the next step in the deployment—as with all new programs—should be a pilot deployment. With a small group of representative users applying labels to their documents, and with DLP configured to classify a subset of the company’s documents automatically, careful monitoring of the labeling process and evaluation of the classified documents will almost certainly disclose some incorrect labeling, requiring modifications to the tools themselves or to the users’ procedures. Successive iterations of the taxonomy and the DLP algorithms will likely be needed before the system is completely reliable.
The final phase of the deployment—and arguably the most difficult one—will be educating all the users in the organization in what the labeling system is, how it works, and why it is necessary. This is particularly true for users that are not involved in the technology behind the system. Document protection is not a problem that administrators can solve with technology only; the human factor is also a critical part.
Quick check
Which of the following elements is responsible for creating hybrid identities by replicating on-premises identities to the cloud?
Azure AD
Azure AD Connect
Password hash synchronization
AD DS
Quick check answer
Azure AD Connect is a software tool that runs on the on-premises network and replicates Active Directory domain Services identities to Azure Active Directory in the cloud, creating hybrid identities.
Skill 3.3: Understand the need for unified endpoint management, security usage scenarios and services
At one time, enterprise network security consisted of company-owned computers, deployed and managed internally, and protected using password policies, firewalls, antivirus software, and, for a few remote users, dial-up and virtual private network connections. Network administrators controlled all the equipment, and a generation of Client Management Tools (CMTs) appeared, such as Microsoft’s System Center Configuration Manager (SCCM). SCCM provides a unified management solution that enables administrators to inventory hardware, deploy operating systems and applications, update software, manage licenses, and remotely control computers all over the enterprise.
Unfortunately, management platforms like SCCM are designed for use with on-premises computers only, and they communicate over local area networks (LANs). As mobile computing devices became increasingly common, a new management platform was needed, one that could function through the cloud. Mobile Device Management (MDM) was the first iteration of that new platform. MDM products typically exercise complete control over the mobile devices they manage, and as a result, it became common for organizations using the products to own the devices as well.
However, workers often had problems with the usability constraints imposed on them by company-owned, company-managed devices. These problems only became more severe as people began to purchase their own smartphones and find them easier to work with than their MDM-managed company devices. This eventually resulted in the BYOD (Bring Your Own Device) concept, which certainly pleased users but made the lives of administrators more difficult.
To provide adequate security on devices the company does not own, a new evolutionary step in the management products was needed, and enterprise mobility management (EMM) tools, such as Microsoft Intune, were the result. Using Intune, administrators can enroll, configure, and manage mobile devices on several different operating system platforms, wherever the devices happen to be. Administrators can even intervene when a threat to security occurs, by blocking a device’s access to the company network and erasing any sensitive information stored on it.
However, despite the advances in mobile computing and mobile device management, on-premises devices, applications, and services have not gone away, and they still need to be managed. CMTs and EMMs are different types of management platforms in many fundamental ways. Both require administrators to have a significant amount of training and experience, but the two generally do not overlap. A need arose for a management platform that could work with both on-premises and cloud-based devices, as shown in Figure 3-25; this management platform also needs to be extendable to include new technologies as they develop, such as wearables and the Internet of Things (IoT). This new platform has come to be known as unified endpoint management (UEM).
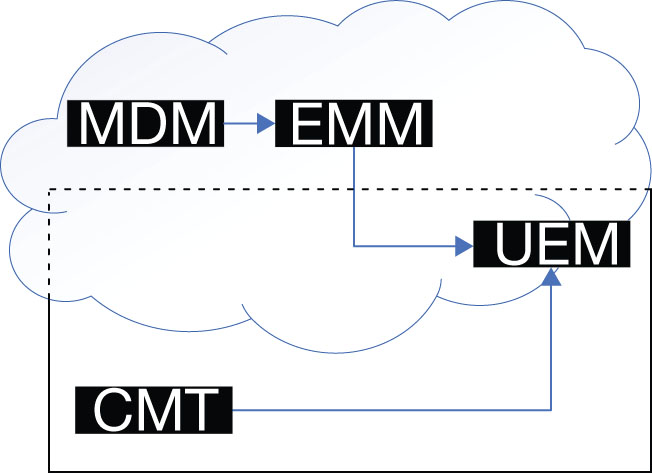
FIGURE 3-25 Development of Unified Endpoint Management
The term endpoint has come to be used to refer to any user device, including desktop computers, laptops, printers, tablets, smartphones, as well as newer technologies, such as wearables and Internet of Things devices. The object of unified endpoint management is to eliminate the need for separate management tools for on-premises and mobile devices. An ideal UEM solution is a “single-pane” administration platform that can manage the applications, identities, resources, updates, security, and policy compliance for all the endpoints in the enterprise, regardless of their locations, device types, or operating systems.
Note: Internet of Things
As mobile networking moves beyond the now ubiquitous smartphone, the next evolution appears to be the Internet of Things (IoT), in which mobile computing devices are embedded in various types of tools, appliances, and systems. Home and building automation is a growing market for IoT devices, including thermostats, light switches, and refrigerators, as well as large-scale industrial and utility systems.
In the health care industry, IoT devices can monitor patients’ conditions both inside and outside hospitals, including heart rate, blood pressure, and blood glucose monitors; also, they can control implanted devices, such as pacemakers and defibrillators. Automobiles and other vehicles are also common applications for IoT, which can provide location monitoring, toll collection, and traffic control services.
All these device types require management by network administrators and could conceivably be as much of a security threat as any of the other mobile computing devices in use today. One can only imagine the chaos that could result if an attacker managed to penetrate a hospital network or a city’s power grid, for example.
In Microsoft 365, UEM is implemented in the Enterprise Mobility + Security (EMS) product, which includes a suite of tools that can work together to provide a comprehensive management solution for both on-premises and cloud-based endpoints. The relevant tools in EMS include the following:
Azure Active Directory Premium The cloud-based directory service that manages identities and provides authentication and authorization for all the Microsoft 365 applications and services, including all the EMS management tools
Azure AD Connect An on-premises tool that replicates user identities on AD DS domain controllers to Azure AD identities stored in the cloud so that users can sign in through the cloud and administrators can take advantage of the Azure AD identity security features
Microsoft Intune A cloud-based enterprise mobility management (EMM) service that enables administrators to enroll mobile devices, deploy apps, and enforce security policies
System Center Configuration Manager (SCCM) An on-premises CMT that administrators can use to inventory computer hardware, deploy operating system images on internal workstations, manage applications, apply software updates, and enforce device compliance policies
Azure Information Protection (AIP) A cloud-based tool that enables users and administrators to apply classification labels to documents and implement various types of protection based on the labels, such as access restrictions and data encryption
Microsoft Advanced Threat Analytics (ATA) An on-premises platform that captures network traffic and log information and analyzes it to identify suspicious behaviors related to multiple phases of the attack process
Cloud App Security A cloud-based service that analyzes traffic logs and proxy scripts to identify the apps that users are accessing—including unauthorized apps—and enables administrators to sanction or unsanction individual apps and connect to APIs supplied by cloud app providers to perform Cloud App Security analyses
Azure Advanced Threat Protection A cloud-based threat prevention, detection, and remediation engine that uses machine intelligence look for security threats unique to the Azure environment by analyzing user behavior and comparing it to known attack patterns
Note: Microsoft ATA
For more information on Microsoft Advanced Threat Analytics, see the “Describe analytics capabilities in Microsoft 365” section in Chapter 2, “Understand core Microsoft 365 services and concepts.”
Microsoft 365 and Directory Services
A directory service is a software product that stores information about network resources for the purpose of unifying them into a single, manageable entity. For example, the Domain Name System (DNS) is a directory service that associates the names of network resources with their corresponding network addresses.
As noted in the “Identity” section, earlier in this chapter, Azure Active Directory (Azure AD) and Active Directory Domain Services (AD DS) are the directory services that store and manage user identities for the various Microsoft 365 components. Azure AD stores its directory information in the Microsoft Azure cloud, and AD DS is stored on computers running Windows Server that have been configured to operate as domain controllers.
Azure Active Directory
Azure AD is available in three plans, as shown in Table 3-3. All the Microsoft 365 products include either the Premium P1 or Premium P2 plan.
TABLE 3-3 Azure Active Directory licenses
AZURE ACTIVE DIRECTORY LICENSE |
INCLUDED WITH |
Azure Active Directory Free |
Office 365 or Microsoft Azure subscriptions |
Azure Active Directory Premium P1 |
Microsoft 365 Enterprise E3 and Microsoft 365 Business |
Azure Active Directory Premium P2 |
Microsoft 365 Enterprise E5 |
The Azure Active Directory Premium P1 plan supports the following features and services:
Unlimited directory objects Enables administrators to create cloud identities for an unlimited number of users.
User and group management Enables administrators to create and manage user and group identities using cloud-based tools, such as the Azure AD admin center and the Microsoft 365 Admin Center.
Cloud authentication Enables users to sign on to the network using hybrid identities stored in the cloud and with password hash synchronization or pass-through authentication.
Synchronization with AD DS using Azure AD Connect After installing the Azure AD Connect tool on an AD DS domain controller or on-premises server, on-premises identities can be replicated to the Azure AD directory in the cloud. This creates hybrid identities that enable users to access both cloud-based and on-premises resources with a single sign-on.
Seamless single sign-on Enables users with hybrid identities that are connected to the on-premises network to sign in with no interactive authentication procedure.
Support for federated authentication Enables administrators to offload the Azure AD authentication process to a federated service, such as Active Directory Federation Services.
Multifactor authentication using phone, SMS, or app Enables administrators to require that users supply two or more forms of identification when signing in with an Azure AD identity, such as a password plus a biometric scan or a one-time code sent to the user’s smartphone.
Support for hybrid user access to cloud and on-premises resources Enables users with hybrid identities to access both cloud-based and on-premises resources after a single Azure AD authentication.
Self-Service Password Reset Enables users with cloud-based identities to modify their passwords without administrator assistance.
Device write-back from Azure AD to AD DS identities Enables devices registered in Azure AD and modified cloud identity passwords to be copied to an AD DS container. Ordinarily, Azure AD Connect only synchronizes data from AD DS to Azure AD.
Application Proxy Enables cloud-based remote users to access internal web applications by forwarding their requests to a connector running on an on-premises server.
Dynamic groups Enables administrators to create rules specifying the attributes a user account must possess to be automatically added to a group.
Group naming policies Enables administrators to create policies that specify a format for group names. For example, group names can be required to specify a function, a department, or a geographic location.
Conditional access Enables administrators to specify conditions that mobile devices must meet before they are granted access to cloud-based resources, such as sign-in risk, client app in use, the state of the mobile device, and the location of the device.
Microsoft Identity Manager Provides identity and access management, including synchronization of users, groups, and other objects for AD DS and Azure AD, as well as third-party directory services.
Azure Information Protection Premium P1 Enables users and administrators to classify and label documents based on the sensitivity of the data they contain.
Security and activity reporting Provides administrators with reports that list potential threats, including risky sign-ins and audit logs that document user activities.
With these features and services, the Azure Active Directory Premium P1 plan enables administrators to manage an organization’s cloud-based resources, as well as identify, predict, detect, and remediate a wide variety of security threats. However, the Azure Active Directory Premium P2 plan supports everything included in the P1 plan and also provides the following additional security features:
Azure AD Identity Protection Evaluates users’ sign-in activities, quantifies their risk levels, and takes action based on those levels.
Privileged Identity Management Enables administrators to regulate access to sensitive resources by granting temporary privileges to specific users, requiring additional security measures, and receiving notifications when the resources are accessed. The objective is to prevent users with administrative privileges from using them unnecessarily.
Cloud App Security A cloud-based service that analyzes traffic logs and proxy scripts to identify and monitor the apps that users are accessing.
Azure Information Protection Premium P2 Expands on the capabilities of the Premium P1 plan by automating the process of identifying, classifying, and labeling documents.
Azure Information Protection is included in all the Microsoft 365 plans, but it is also available with other Microsoft products in a free version with limited functionality and as a separate subscription in two plans of its own, called Premium P1 and Premium P2. Each subscription level adds features, as shown in Table 3-4, and includes all the features of the lower subscription levels.
TABLE 3-4 Azure Information Protection subscriptions
PLAN |
INCLUDED WITH |
DESCRIPTION |
Free |
No purchase necessary |
Allows consumption of AIP-protected content by users with accounts that are not associated with Azure identities |
Azure Information Protection for Office 365 |
Office 365 Enterprise E3 and above |
Provides protection for Office 365 services using custom templates and supporting Office 365 Message Encryption |
Azure Information Protection Premium P1 |
Microsoft 365 Business Microsoft 365 Enterprise E3 Microsoft Enterprise Mobility + Security E3 |
Provides the ability to use on-premises connectors, track and revoke documents, and manually classify and label documents |
Azure Information Protection Premium P2 |
Microsoft 365 Enterprise E5 Microsoft Enterprise Mobility + Security E5 |
Provides support for policy-based rules and automated classification, labeling, and protection of documents |
Active Directory Domain Services
Active Directory Domain Services (AD DS) is an object-oriented, hierarchical directory service that functions as an internal authentication and authorization provider for Windows networks. Because it is not located in the cloud like Azure AD, the primary source of protection for AD DS is the firewall and other perimeter protection surrounding the on-premises network. AD DS domain controllers are Windows servers that are located inside the network perimeter; they must not be deployed in a DMZ or in any other way that leaves them open to access from the Internet.
Also, unlike Azure AD, an AD DS directory must be designed, deployed, and maintained by the network administrators. The service is provided as a role in the Windows Server operating system, which administrators must add after the installation of the operating system itself. An AD DS directory does not include any of the built-in maintenance and fault tolerance found in Microsoft’s cloud services.
Typically, AD DS domain controllers perform no other function other than acting as DNS servers. For example, it is not considered secure to use domain controllers as application or file servers. To ensure fault tolerance and high availability, administrators must install multiple domain controllers, preferably at different sites. The domain controllers replicate the contents of the directory among each other on a regular basis.
Unlike Azure AD, AD DS is a hierarchical directory service that enables administrators to create a directory that emulates their company’s departmental or geographical infrastructure, as shown in Figure 3-26.

FIGURE 3-26 An Active Directory Domain Services container hierarchy
Forests, trees, domains, and organizational units are all types of AD DS objects that contain other objects, such as users, groups, and computers, as shown in Figure 3-27. As with a file system, permissions flow downward through the hierarchy. Permissions granted to a container object are inherited by all the objects in that container and by all subordinate containers beneath it. Administrators can design the AD DS hierarchy however they wish.

FIGURE 3-27 AD DS objects in an organizational unit
In AD DS administration, there is a lot more work left to the network administrator than there is in Azure AD. In Azure AD, one can begin creating users and groups immediately after establishing a tenancy, with no need to install and maintain domain controllers or design an infrastructure. There are also no concerns about physical security with Azure AD, because Microsoft is responsible for its data centers and for maintaining the computers that provide the services. The initial cost outlay for an Azure AD directory is also minimal. AD DS requires the purchase of server computers and the Windows Server operating system, but there are no ongoing subscription fees.
Although AD DS uses an infrastructure that is substantially different from Azure AD, it performs the same basic services by authenticating users and authorizing their access to network resources. However, AD DS does not support many of the advanced security features found in Azure AD. For example, it has no internal support for multifactor authentication, although it is possible to use an external authentication service for some additional authentication factors. AD DS also does not include Azure AD Identity Protection, Conditional Access, and Azure Information Protection.
Because domain controllers are often connected to the same network as workstations and other less sensitive systems, they can be vulnerable to a lateral attack from an intruder who has gained access to another system on the network. As a result, even though the domain controllers themselves might be protected, any of the typical attack vectors to which on-premises computers are susceptible can pose a threat to the AD DS implementation. For example, any computer on the network that is not current in its operating system and application updates or that lacks virus or malware protection can be a target for attack and a launch point for a further invasion of the AD DS directory.
AD DS is also more vulnerable to credential theft than Azure AD because of unsafe use of privileged credentials. Administrators of an on-premises network can sometimes be careless about using their privileged identities to perform everyday tasks, such as browsing the Internet or signing on to computers that are not fully secured. In Azure Active Directory Premium P1, these are practices that can be addressed with the Privileged Identity Management feature, but Microsoft has not integrated the Azure AD security tools into AD DS.
![]()
Exam Tip
For MS-900 examination candidates who are new to these technologies, it can be easy to confuse the capabilities of the cloud-based Azure Active Directory (Azure AD) and the on-premises Active Directory Domain Services (AD DS). It is important to know that AD DS is a hierarchical directory service, provided with the Windows Server operating system, that requires a fairly extensive design and implementation process. Azure AD, by contrast, is subscription-based, is not hierarchical, and requires virtually no setup. Candidates should also be conscious of which features are provided in the Azure Active Directory Premium P1 and Azure Active Directory Premium P2 plans, and with the different functionalities of the Azure Information Protection Premium P1 and Azure Information Protection Premium P2 plans.
SCCM and Intune co-management
System Center Configuration Manager (SCCM) is Microsoft’s Client Management Tool for on-premises networks. The product, first released in 1994 (under the name Systems Management Server), provides a comprehensive management solution for on-premises systems by providing the following features:
Operating system deployment Deploys operating system images to client workstations over the network using a variety of scenarios, both automated and interactive.
Software update management Deploys updates of operating systems, applications, device drivers, and system BIOS firmware to entire fleets of devices.
Hardware and software inventory Performs comprehensive inventories of the hardware in and the software installed on client computers.
Application deployment Provides user-based application deployment to multiple device types using various delivery mechanisms, including local installations, App-V, and RemoteApp.
Endpoint protection For Windows 8.1 and earlier, provides a System Center Endpoint Protection antimalware client; for Windows 10, provides a management client for the built-in Windows Defender antimalware engine.
Client health monitoring Provides centralized monitoring and reporting of client health and activities, with the ability to generate alerts and perform remediations.
Compliance management Enables administrators to create a configuration state baseline for clients, evaluate them for compliance, and generate alerts or perform remediations.
SCCM is an excellent CMT solution for on-premises systems, but it doesn’t support the management of cloud-based mobile devices by itself. Therefore, to achieve a true Unified Endpoint Management solution with Microsoft products, a combination of SCCM and Microsoft Intune is needed, in an arrangement called co-management.
An SCCM deployment consists of at least one server on the network, a Configuration Manager console, and the installation of a software agent on each client to be managed. The process of deploying SCCM on an on-premises network is not a simple one, requiring schema modifications to Active Directory Domain Services and a Microsoft SQL Server installation, as well as the installation of the SCCM server and the individual clients.
The typical scenario envisaged for co-management is an enterprise that has already made a significant investment in an SCCM infrastructure and is planning to add Microsoft 365. Microsoft Intune, the enterprise mobility management tool that is included in the Enterprise Mobility + Security component, provides advanced management capabilities that administrators often want to use for their on-premises systems, as well as their cloud-based mobile ones.
Co-management is an SCCM feature that links the on-premises systems to Microsoft Intune in the cloud and enables administrators to manage their on-premises computers with both the SCCM and Intune consoles. By adding co-management capabilities to their internal infrastructure, administrators can then take advantage of the following Microsoft 365 features:
Hybrid Azure AD By creating hybrid identities for on-premises users, they can access both cloud-based and on-premises resources with a single sign-in, as well as use Microsoft 365 features such as Windows Hello for Business and Self-Service Password Reset. Administrators can take advantage of Intune’s device-based conditional access and automatic device licensing.
Conditional access The conditional access capability in Intune goes beyond the compliance management capabilities in SCCM by providing more comprehensive device evaluation, as well as detection and remediation of security threats.
Remote actions Microsoft Intune enables administrators to manage devices connected to the network, wherever they are located, using cloud-based controls that can inventory, restart, or reset a device, delete company data, or take remote control.
Client health Client health monitoring in SCCM is limited to devices that are actively connected to the internal network. With Intune, client health is monitored whenever the device is accessible from the cloud. Intune provides timestamped records of each client’s health and its readiness for application installations and updates.
Windows Autopilot Administrators can choose to deploy new devices using Windows Autopilot rather than the image deployment process that SCCM uses. This can eliminate the need for administrators to create and maintain boot and system images for various hardware combinations.
For Windows 10 devices to be co-managed, they must have the SCCM client agent software installed on them, and they must be enrolled in Microsoft Intune. For an existing SCCM installation, the process of implementing co-management with Intune consists of the following basic steps:
Create hybrid identities for the SCCM client users by installing Azure AD Connect on the internal network and configuring it to replicate the AD DS users to the Azure AD tenant.
Assign a Microsoft 365 license (or individual Intune and Azure AD Premium licenses) to the SCCM client users.
In the Configuration Manager console in SCCM, enable the Automatically Register New Windows 10 Domain Joined Devices With Azure Active Directory Client setting.
In the Azure portal, enable MDM Automatic Enrollment for some or all the Windows 10 devices on the network.
In the Configuration Manager console, run the Co-management Configuration Wizard and enable the Automatic Enrollment Into Intune setting
Note: Pilot Deployments
As with all new technology implementations, Microsoft recommends a small pilot deployment for evaluation purposes before any product is rolled out to an entire enterprise.
The implementation of the co-management infrastructure is somewhat different for an enterprise seeking to co-manage new Windows 10 workstations deployed by an OEM or by using Windows Autopilot but does not provide users with hybrid AD DS/Azure AD identities. Administrators must deploy a cloud management gateway on the internal network and obtain a public SSL certificate for it, configure Intune to install the SCCM client agent on the new computers, and configure the clients to use the gateway.
Once the co-management setup is completed, SCCM and Microsoft Intune work together with AD DS and Azure AD, as shown in Figure 3-28.
FIGURE 3-28 System Center Configuration Manager and Microsoft Intune co-management
In the Co-management Configuration Wizard, it is also possible to select the workloads to be managed by Microsoft Intune, although administrators can also do this at any time after co-management is implemented. All the workloads remain managed by SCCM until they are explicitly shifted to Intune instead. The SCCM co-management feature supports the transfer of the following workloads to Intune:
Compliance policies Specify the configuration settings and policies that the device must observe before it can be granted conditional access to network resources.
Windows Update policies Enable administrators to define policies for Windows 10 feature and quality update deployments to devices using Windows Update for Business.
Resource access policies Provide the management of devices’ Wi-Fi, virtual private network (VPN), email, and certificate settings.
Endpoint Protection Provide management over all the Windows Defender antimalware features on Windows 10 devices.
Device configuration Provides management authority for device management settings, including those included in the Resource access policies and Endpoint protection workloads. Despite transferring this workload to Intune, it is still possible to configure device settings in Configuration Manager, such as settings in SCCM that have not yet been implemented in Intune.
Office click-to-run apps Provide management authority for all the Office 365 applications.
Client apps Provide application deployment capability. Transferring this workload to Intune enables devices to install applications from Intune, using the company portal, or from SCCM, using Software Center, as shown in Figure 3-29.
FIGURE 3-29 The Client App workload in a co-managed environment
Security usage scenarios
Management of the various types of endpoints presents administrators with a variety of issues that they must address, including the following:
User-owned devices When workers use their own devices, administrators must define a policy specifying what degree of control the organization will have over the devices and what company resources the devices will be permitted to access. This can be a difficult task because, while the organization must protect its resources, users are often unwilling to turn over full control of their property to the company. Windows Intune provides administrators with both Mobile Device Management (MDM) and Mobile Administration Management (MAM) capabilities, which provide different levels of management control to suit the needs of the organization and the users.
Mobile device networking Mobile users often connect to outside wireless networks, such as those in coffee shops and other businesses, which are unsecured by the enterprise. This leaves the devices open to the possibility of intrusion by outside persons, exposing them to potential threats that can jeopardize the device, the data stored on it, and the enterprise network. Administrators can use Microsoft Intune or other tools to create and enforce mobile device policies that require devices to have the malware prevention tools, software updates, and other forms of protection needed to repel the threats.
Device loss or theft Any mobile device is liable to be lost or stolen, with the accompanying danger that any sensitive data stored on the device might be compromised. There might also be users who leave the company under less-than-friendly circumstances, taking their personal devices with them. In some cases, the cost of replacing the device hardware can be less than that of identifying the data that has been lost and re-creating it. Administrators must prepare for these situations by devising a Microsoft Intune policy that can exercise remote protection of the organization’s resources, even when the mobile device is in hostile hands.
Infected devices Mobile devices that become infected with malware while connected to outside networks can bring that infection into the enterprise, damage documents, and pass the infection along to other systems. Administrators must classify all mobile devices connecting to the enterprise network as potential threats and protect them using tools such as Windows Defender and System Center Endpoint Protection.
Device data synchronization While data stored in the Microsoft cloud is replicated to multiple data centers for protection, mobile devices working outside the company premises might not always be connected to the cloud. Therefore, when users work with company documents while offline, any revisions they make to the documents are not saved to the cloud or backed up until they next connect to a network. Therefore, this revised data can be lost if the device is damaged, lost, or stolen before it next connects to the cloud.
Password changes One of the more common tasks for help desk personnel and administrators is the need to change users’ passwords. This task is even more common when Azure AD Identity Protection is configured to require a password change when their authentication-based risk levels reach a certain value. Self Service Password Reset (SSPR) enables users who have been successfully authenticated to change their own passwords, rather than require the intervention of an administrator.
Addressing common threats
Risk management is a highly specialized undertaking that is heavily dependent on the type and sensitivity of the information to be protected and the nature of the threats to which the network is most vulnerable. For example, an organization that consists mostly of IT professionals will not be overly susceptible to phishing attacks because they have more awareness of them and experience with them. On the other hand, an organization of users with little or no IT expertise will be far more vulnerable to this particular threat and will have to expend more effort in trying to prevent this type of attack.
Microsoft 365 includes a wide variety of security tools that make it possible to predict, prevent, and react to many different kinds of threats. Many of these tools are discussed individually, both in this chapter and elsewhere in this book. The nature of each tool’s function is explained in relation to the types of threats it addresses. However, Microsoft recently announced an effort to organize Microsoft 365’s security components under the single name Microsoft Threat Protection, which places the tools into the following five categories:
Identities Tools that authenticate, authorize, and protect the accounts of standard users and privileged administrators, such as Windows Hello, Azure Active Directory Identity Protection, Privileged Identity Management, Azure Advanced Threat Protection, and Microsoft Cloud App Security
Endpoints Tools that protect user devices and sensors from the effects of loss, theft, and attack, such as Microsoft Intune, System Center Configuration Manager, Windows 10, Microsoft Advanced Threat Analytics, and Windows Defender Advanced Threat Protection
User data Tools that analyze documents and messages for sensitive or malicious content, such as Exchange Online Protection, Azure Information Protection, Data Loss Prevention, Windows Defender Advanced Threat Protection, Office 365 Advanced Threat Protection, Office 365 Threat Intelligence, and Microsoft Cloud App Security
Cloud apps Tools that protect Software as a Service (SaaS) applications like Office 365 and their data, such as Exchange Online Protection, Office 365 Advanced Threat Protection, and Microsoft Cloud App Security
Infrastructure Tools that provide protection to servers, both physical and virtual; databases; and network, such as Azure Security Center, Microsoft Advanced Threat Analytics, and SQL Server
However, Microsoft Threat Protection is meant to be more than just a list of individual tools. Microsoft 365 also gathers information from all these security components and accumulates them in a single Microsoft 365 security center, as shown in Figure 3-30.

FIGURE 3-30 Microsoft 365 security center
The pages of the Microsoft 365 security center, accessible from the navigation pane on the left, provide the following:
Home Displays a dashboard with configurable tiles that contain status indicators for the security issues most important to a particular administrator or organization
Alerts Displays notifications generated by other Microsoft 365 security tools, including Microsoft Cloud App Security, Office 365 Advanced Threat Protection, Azure Active Directory, and Microsoft Defender Advanced Threat Protection
Reports Provides detailed information on the security status of the network’s identities, devices, data, applications, and infrastructure
Secure score Provides a comprehensive assessment of the enterprise’s current security status in a numerical score out of 1,000
Advanced Hunting Provides access to the analytical tools that can proactively identify potential threats to the network’s identities, messages, data, and devices, such as the Advanced Threat Protection tools for Azure, Office 365, and Microsoft Defender
Classification Provides access to tools for creating classification labels for Microsoft 365’s Information Protection tools
Policies Provides the ability to create policies for a variety of Microsoft 365 tools and purposes, including Advanced Threat Protection, Office 365 alerts, and Cloud App Security
Microsoft 365 also goes beyond the reactive approach to security and provides tools that can be proactive by detecting attacks and other security issues before they occur, or when they have barely begun. The Advanced Threat Protection tools for Azure, Office 365, and Microsoft Defender are all designed to monitor the behavior of users, devices, and other network resources and analyze the information they collect to detect and anticipate suspicious behavior. The intelligence the tools apply to the task is based on the Microsoft Intelligent Security Graph, a web of security relationships that spans the entire network. Microsoft’s Cybersecurity Reference Architecture, shown in Figure 3-31, illustrates these relationships.
FIGURE 3-31 Microsoft Cybersecurity Reference Architecture
Need More Review?: Microsoft Cybersecurity Reference Architecture
For an interactive PowerPoint version of the architecture shown in Figure 3-31, see https://gallery.technet.microsoft.com/Cybersecurity-Reference-883fb54c.
Quick check
Microsoft Intune, functioning on its own, is classified as which of the following types of management tools?
CMT
EMM
UEM
MDM
Quick check answer
Microsoft Intune is considered to be an enterprise mobility management tool (EMM) because it expands on the capabilities of mobile device management (MDM). However, Intune is cloud-based and cannot manage on-premises clients by itself, so it cannot be called a client management tool (CMT) or a unified endpoint management (UEM) tool.
Skill 3.4: Understand the Service Trust Portal and Compliance Manager
For many IT professionals, the prospect of implementing vital services and storing important company information in the cloud is met with a significant amount of trepidation. They might have an instinctive reluctance to trust an IT infrastructure that is not implemented on computers the company owns and housed in their own data centers. They might also hesitate to give up their personal control over those computers and their resources. Also, there might be statutes and standards to which the IT infrastructure must comply, whether because of contracted terms, company policies, or governmental requirements.
Service Trust Portal
Microsoft is aware of these trust issues and has created a central storehouse for information about them, called the Service Trust Portal (STP). STP is a website that is available to everyone at http://aka.ms/stp, although some parts of the site are restricted to registered users of Microsoft 365 and other products. Among the many resources on the site are links to documents in the following categories:
Audit Reports Provide independent audit and assessment reports of Microsoft’s cloud services, evaluating their compliance with standards such as those published by International Organization for Standardization (ISO), Service Organization Controls (SOC), National Institute of Standards and Technology (NIST), Federal Risk and Authorization Management Program (FedRAMP), and General Data Protection Regulation (GDPR)
Documents & Resources Consist of a large library of documents, including white papers, FAQs, compliance guides, penetration test reports, Azure security and compliance blueprints, and other data protection resources
Compliance Manager Assesses and scores an organization’s regulatory compliance, based on multiple published standards
Industries & Regions Provide documents containing compliance information for specific industries, such as education, financial services, government, health care, manufacturing, and retail; and specific countries, including Australia, Czech Republic, Germany, Poland, Romania, Spain, and United Kingdom
Trust Center Links to the Trust Center site, which provides documentation on the means by which Microsoft supports security, privacy, compliance, and transparency in its cloud services
Resources Provide information about Microsoft’s global data centers, security and compliance information for Office 365, and a FAQ list for the Service Trust Portal
My Library Enables users to pin documents from the site onto a separate user page for quick reference later
Compliance Manager
Compliance Manager is a risk assessment tool that enables an organization to track and record the activities they undertake to achieve compliance with specific certification standards. An assessment of an organization’s compliance posture is based on the capabilities of the Microsoft 365 cloud services and the ways that the organization makes use of them, as compared to an existing standard, regulation, or law.
The home page for the Compliance Manager tool contains a dashboard that displays tiles representing the assessments of the Office 365 and Azure components against three different standards, as shown in Figure 3-32. Each tile specifies a cloud service and the standard to which it is being compared. The results of the comparison are stated as a numerical score.

FIGURE 3-32 The Compliance Manager assessments dashboard
Selecting a tile displays a detailed list of the controls tested for the assessment, along with the results for each individual control, as shown in Figure 3-33. The controls are broken down into those for which Microsoft is responsible and those for which the customer is responsible. Each control entry contains a reference to a section or article in the standard that corresponds to the control; information about who tested the control and when; and the results of the test, which is expressed as an individual Compliance Score value.

FIGURE 3-33 A Microsoft Managed Control in Compliance Manager
In the default view of a Compliance Manager assessment, the Microsoft-managed controls are complete with results and compliance scores, but the customer-managed controls are not. It is up to the subscriber to complete these controls and use the guidance and recommendations in each one to finish the assessment and generate an overall score that reflects the compliance of both Microsoft and the organization to the selected standard.
Cloud adoption showstoppers
For any organization contemplating or anticipating a movement to the cloud, there are issues that they must contemplate before making a final decision. It some instances, the company decision-makers might be unsure about whether cloud-based providers can deliver the services that the organization needs. In other cases, there might be no doubt that the cloud can provide the necessary services, but there is indecision about how to actually implement a transition from on-premises to cloud-based services.
Both types of issues can at times be “showstoppers” that prevent a cloud implementation from happening at all. Microsoft has considered many of these critical adoption issues, as shown earlier in the extensive documentation provided in the Service Trust Portal and Company Manager tools. However, sometimes the considerations involved in a cloud transition situation are unique to an industry or an individual company, or are more legal or financial than they are technical, and the solutions must be generated internally rather than provided by a product or service such as Microsoft 365.
The following sections address some of the most common cloud adoption showstoppers and provide approaches that companies can take to address them.
Anticipating performance latency
Can cloud-based services provide the performance levels that the organization is accustomed to achieving with on-premises resources? IT professionals familiar with service issues to which Internet services providers and the Internet itself can be subject might question whether a consistently high level of performance is possible with cloud-based services. The comfortingly consistent performance of an internal cable plant, over which the company has complete control, is a difficult thing to lose. There might be concerns as to whether service outages or periods of increased latency might occur that can affect productivity and damage the company’s reputation with its partners and clients.
When considering any cloud service provider, the potential subscriber should investigate the vendor’s service performance record, both by examining any data they provide and by contacting their other clients. Most providers include a Service Level Agreement (SLA) in their contracts that account for service availability, but potential subscribers should inquire about the possibility of a performance level SLA as well.
An examination of the provider’s hardware infrastructure is recommended as well, to determine where their data centers are located in proximity to the company’s sites. Microsoft has addressed this issue by constructing a global network of data centers and by recommending that Microsoft 365 subscribers perform a detailed examination of their own network infrastructure. This is to ensure that each company location accesses the Microsoft cloud services through the Microsoft Global Network endpoint nearest to their physical location.
Readeraid: Networking Infrastructure and Microsoft 365
For more information on the network infrastructure examination recommended as part of the Microsoft 365 deployment, see the “Phase 1: Networking” section in Chapter 2, “Understand core Microsoft 365 services and concepts.”
Selecting service providers
The process of choosing service providers is, of course, critical to any cloud deployment. One of the first questions to consider is whether to use a single provider for all the services the organization requires or evaluate several providers for individual services. Choosing one provider for everything minimizes the chance of service gaps, but it also creates a single point of failure. The selected provider might also not provide the best price for each of the services needed.
For Microsoft 365 subscribers, of course, there is no choice of providers for the services included in the product, but this does not mean that an organization must use Microsoft for its entire cloud infrastructure. Using multiple providers for various services might enable the company to negotiate the best terms for each one, and it also allows the company to maintain relationships with more than one vendor, so that services can be moved to another provider if the circumstances call for it. However, dealing with multiple cloud service providers requires meticulous planning to ensure that the company receives all the services it needs.
The organization should have a complete network infrastructure design before engaging any providers, and a careful comparison of the contracts for the providers is necessary to make sure that all the services called for in the plan are available and accounted for. When adding a new service to an existing cloud-based infrastructure, administrators should compare the new contracts of prospective providers with all the existing contracts that are in force.
The worst-case scenario, in this instance, would be the late realization that a vital infrastructure component is not being supplied by any of the engaged service providers and that none of the providers can supply it. These service gaps can be both expensive and embarrassing to the people responsible.
Avoiding vendor lock-in
Being locked into a single vendor is one of the concerns of many organizations considering a cloud-based infrastructure. Prices and other contract stipulations can change over time, and it might be necessary to switch providers when multiple vendors provide the same services in the future. To prepare for this eventuality, contracts with cloud service providers should always include an exit strategy and language regarding contract novation, whether early or not.
One particularly important concern should be the issue of data reclamation. A large cloud-based enterprise network can generate enormous amounts of data over the course of several years. In the event of a provider switch, the process of reclaiming that data from one provider’s cloud service and moving it to that of another can be extremely lengthy. The organization’s cloud infrastructure plan should account for this eventuality, as should the contracts with both the old and the new providers.
Evaluating vendor robustness
At the time of this writing, the business of providing cloud networking services is dominated by three very large companies, none of which appears to be in danger of failing anytime soon. However, other smaller providers do exist and might offer tempting terms for their services. When considering smaller providers, prospective subscribers should investigate the state of their businesses thoroughly. Decision-makers should weigh the risk of contracting with a small provider—which might conceivably fail sometime in the future—with the business consequences of such a failure, such as possible network downtime and even data loss.
Comparing cost models
Comparing the financial cost of a cloud-based infrastructure with an on-premises one is difficult because they use entirely different models. An on-premises network requires a large outlay for hardware and deployment expenses, but once that cost has been amortized, the network is the property of the company, and the ongoing expense is reduced substantially. A cloud-based infrastructure requires a much smaller initial outlay, but the subscriber fees can be substantial and persist as long as the company uses the service.
There are other cost factors to consider as well. In the on-premises model, the company must plan for future growth and adjust the entire deployment process to account for resources that might not be needed for years. With a cloud-based infrastructure, the subscriber can contract for what services they need right now and add more (or remove) functionality later, whenever it is necessary.
To anticipate the TCO (total cost of ownership) for a cloud-based versus an on-premises network infrastructure, one recommended practice would be to total all necessary expenditures for each model over a period of two to three years. However, the TCO does not necessarily provide the whole picture. The cloud solution can provide other benefits that are more difficult to quantify financially. For example, cloud-subscribed services can be scaled up or down with immediate effect. Typically, cloud providers can deploy new virtual servers, add resources to existing ones, or even supply entirely new services almost immediately. On an on-premises network, an expansion might require the purchase, installation, and deployment of new hardware, which can take weeks or months. Scalability can be an important factor for a company that experiences significant seasonal fluctuations in business.
Securing company data
Arguably the greatest concern for many IT professionals considering a cloud-based network infrastructure is the risk of their data being lost or compromised. Microsoft—and presumably other reputable cloud service providers—note in their service descriptions the mechanisms they use to protect subscribers’ data, such as replicated storage at multiple data centers. Contracts also routinely include an SLA that specifies a guaranteed uptime percentage (99.9 percent, in the case of Microsoft), which all but ensures the availability of the data. However, while the contract might impose a penalty on the provider if they do not meet the terms of the SLA, they will almost certainly not be financially responsible for any losses the subscriber incurs due to downtime.
There is no way around the fact that data stored in the public cloud does have a greater risk of being compromised than data stored on the subscriber’s on-premises servers. To address this risk, Microsoft 365 includes security tools that, when used properly, can help to mitigate the risk of identities being penetrated and data being accessed by unauthorized individuals. However, the burden of applying this protection and of exposing sensitive data to the risk falls on the subscriber in the first place.
It is up to the network’s administrators to assess the sensitivity of the company’s data, classify the data using an agreed-upon taxonomy of sensitivity levels (as discussed in the “Protecting documents” section, earlier in this chapter), and decide what measures they should use to protect the data at each level. Therefore, sn organization that works with extremely sensitive data might choose to store it on-premises, rather than allow it in the cloud at all.
It should also be up to the subscriber to ensure that all data, whether stored in the cloud or on-premises, is backed up on a regular basis, whether the cloud provider includes this service or not. If backups are also to be stored in the cloud, then the best practice would be to use a different provider for the backups, so that the data is stored on a separate network of data centers.
Locating company data
For organizations that are subject to data storage restrictions imposed by their clients or by government entities, the exact locations of a cloud service provider’s data centers can be significant. The Microsoft Azure network is divided into 54 regions (shown in Figure 3-34) and 18 geographies that enable subscribers to maintain their data in places that can honor any specific residency, sovereignty, compliance, or resiliency requirements they might be compelled to observe. This is not necessarily true of all public cloud providers, however, and potential subscribers subject to such restrictions should require providers to include contract language specifying where their data is to be stored.
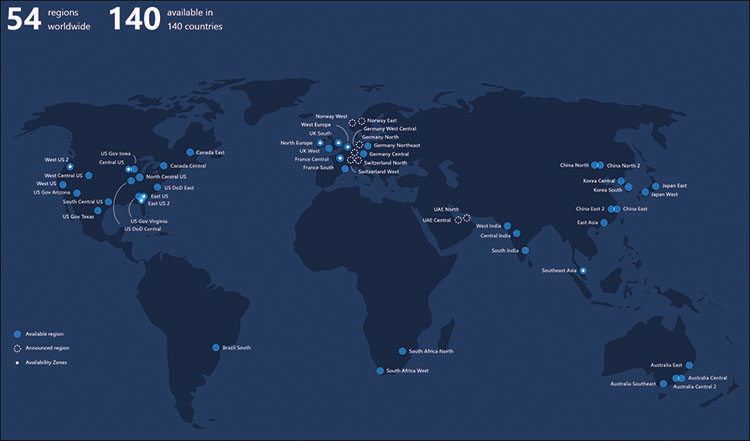
FIGURE 3-34 Map of Microsoft Azure regions
Note: Microsoft Azure Government
Microsoft maintains a dedicated cloud for United States federal, state, and local government agencies and their partners, which is compliant with a large number of government standards, including FedRAMP, NIST 800.171 (DIB), ITAR, IRS 1075, DoD L4, and CJIS. The data centers for this government cloud are all located within the United States and are physically isolated, as are the networks inside them. In addition to the four dedicated U.S. government regions in Iowa, Texas, Arizona, and Virginia shown on the map, there are two other secret U. S. government regions at undisclosed locations.
Obtaining skilled personnel
Because cloud-based services are a relatively new technology, there are not as many skilled administrators and support people for them as there are for traditional on-premises networking technologies. This can mean an enterprise that has an established on-premises network infrastructure but that is considering the addition of or migration to cloud services, the existing IT staff might lack the expertise needed to adequately support the cloud technologies.
One effective way of addressing this issue without replacing all or part of the IT staff is to train or recruit a core cloud network infrastructure design and planning team first. Then that team can function as mentors for the IT personnel that require a reorientation to cloud methodologies.
Transitioning to the cloud
For traditional on-premises network administrators and support personnel, a transition to cloud-based services can be a major rethink in how they do almost everything, and many organizations are reticent to make the change for that reason. Cloud service providers have recognized this, however, and might provide help for subscribers moving into the cloud for the first time.
Microsoft’s FastTrack program is designed for this exact purpose, providing organizations with a specified number of Microsoft 365 subscribers with a clearly defined path into the cloud and onboarding help, for no additional charge. Microsoft maintains its own FastTrack team, as well as a network of partners that can provide transition assistance by breaking the process down into the following three stages:
Envisioning Provides the subscriber with information about available resources and identifies business-specific scenarios to aid in the creation of an overall cloud deployment and migration plan catered to the organization’s needs
Onboarding Realizes the plan created during the Envisioning phase by configuring the cloud services; migrating files, email stores, and web content; and creating users and groups, as shown in Figure 3-35
Driving value Helps the subscriber to develop efficient administration and maintenance practices and provides ongoing aid to the staff in working with Microsoft 365 technologies and adapting them to the organization’s business model

FIGURE 3-35 The Microsoft 365 FastTrack onboarding process
Not all cloud service providers have a program like this, but some will provide assistance; also, there are third-party consultants who can help an organization deal with issues that arise during the transition to a cloud-based infrastructure. IT professionals who are hesitant to adopt cloud technologies, even after realizing the advantages they provide, have many resources available for assistance.
Summary
The process of creating a security plan for an enterprise is known as risk management.
Microsoft 365 includes security technologies that are divided into four areas: Security Management, Identity-based Protection, Information Protection, and Threat Protection
A comprehensive security implementation must distribute protection among the four primary pillars supporting the enterprise infrastructure: Identity, Documents, Network, and Devices.
An identity is a logical representation of a user in a network environment. To users, an identity is a name that they type to sign on to the network. To administrators, an identity is a collection of attributes associated with a particular individual.
There are three basic means of authenticating an individual’s identity. The individual must supply one or more of the following: something you know, something you are, or something you have.
Unified endpoint management (UEM) is a management platform that can work with both on-premises and cloud-based devices, and be extendable to include new technologies as they develop, such as the Internet of Things (IoT).
To achieve a true Unified Endpoint Management solution with Microsoft products, a combination of System Center Configuration Manager and Microsoft Intune is needed, in an arrangement called co-management.
The Service Trust Portal (STP) is a central storehouse for information about cloud trust and standards compliance issues.
Many company decision-makers are unsure about whether cloud-based providers can deliver the services that the organization needs or unclear about how to actually implement a migration to the cloud. These issues can at times be “showstoppers” that prevent a cloud implementation from happening at all unless solutions are carefully considered.
Thought experiment
In this thought experiment, demonstrate your skills and knowledge of the topics covered in this chapter. You can find answer to this thought experiment in the next section.
Ralph is the Director of the Brooklyn data center at Contoso Corp. The company currently has three office buildings in in the New York area with a total of 600 users. There are data centers in all three buildings, all of which are based on Microsoft server products and managed using System Center Configuration Manager. The three data centers are all jammed with equipment and have no room for further expansion. Ralph is convinced that it would be better for the company to expand into the cloud and purchase Microsoft 365 subscriptions for the 600 users rather than purchase an additional property and build a fourth data center from scratch.
With the cost of real estate and construction in New York being what it is, the financial aspect of a cloud expansion is amenable to the company. However, there is still significant opposition to Ralph’s proposal from the other two data center directors and from the chief technology officer:
None of the IT management staff—including Ralph—have much experience with cloud technologies.
There are fears that storing company data in the cloud will not be secure.
There are concerns that performance of the company’s customer portal—a catalog database that took a great deal of effort to develop—will suffer because of cloud service downtime and Internet latency issues.
Ralph must prepare a presentation that promotes his cloud project and addresses these three concerns. Using what you have learned about cloud service trust and deployment issues, propose a solution for each of the three concerns that Ralph must address at his presentation.
Thought experiment answer
Ralph can address the concerns of the other directors and the CTO in the following ways:
Microsoft’s FastTrack program is designed to provide free support for new cloud subscribers during their infrastructure design and implementation processes, as well as ongoing support for the management staff.
Microsoft 365 includes tools such as Azure AD Identity Protection, Azure Information Protection, and Office 365 Advanced Threat Protection that enable administrators to protect user identities and elevate the security of the company data stored in the cloud based on its sensitivity.
Microsoft contracts include a service level agreement guaranteeing 99.9 percent uptime. The Microsoft 365 deployment process also includes a networking phase in which the company evaluates its Internet access infrastructure to ensure that all Microsoft 365 clients and administrators have sufficient Internet connectivity to access the cloud resources they require on a regular basis.
