2 Literature Survey on Data Aggregation Techniques Using Mobile Agent and Trust-Aware in Wireless Sensor Network
Neelakshi Gupta, Tripti Sharma, and Nitin Mittal
Contents
2.2.3 Topology-Based Protocols
2.2.4 Reliable Routing Protocols
2.3 Data Aggregation Approaches
2.5 Mobile Agent-Based Clustering
2.6.1 Single Itinerary Planning
2.6.2 Multi-Itinerary Planning
2.1 Introduction
In recent research into Wireless Sensor Networks (WSNs), trust-aware data aggregation using a mobile agent is the new challenge. This network is made up of small sensor nodes, which contribute to the communication of data [1]. WSN is application specific, therefore, it has the ability to deploy thousands of small sensor nodes, which can assemble themselves and are capable of collecting data from their surroundings and route the data to the sink node by either single hops or multiple hops [2]. Sensor nodes constitute different units, known as the communication unit, sensor unit, processor unit, and energy unit, as shown in Figure 2.1. Sensor units collect data from their surroundings and send them to the processor unit. In the processor unit, data are processed and saved for future use. The processed data from the processor unit are then forwarded to the communication unit, which is accountable for communicating the particulars from node to node. The main job of the energy unit is to keep a check on residual energy in the nodes. A sensor node has limited onboard storage, processing, power, and radio capacities, due to its limited size. Therefore, WSNs necessitate efficacious mechanisms to utilize limited resources and to resolve associated problems. Routing is one of these mechanisms that elongates the network lifespan by lessening energy consumption in communication. Figure 2.1 shows the architecture of the sensor node.

WSN is widely used in many fields, such as precision agriculture, environmental applications, smart transportation, health care applications, smart buildings, military applications, and many more. When a sensor network is used for military applications, continuous monitoring is essential to keep a check on movement of the enemy “like” mass destruction security assistance, etc. WSN is also very useful in health applications as it can remotely monitor the patients and checks their heart rate and blood pressure, transmitting this information to a WSN doctor. Table 2.1 summarises the applications of WSN.
TABLE 2.1
Summary of Various WSN Applications with Their Characteristics
Application |
Characteristics |
Precision agriculture [3] |
Data under observation include humidity, temperature, soil depth, crop information, soil information, etc. |
Information about coal mining, air pollution, forest fire detection, cyclones, earthquakes, volcano eruption, water quality parameters (pH levels, ammonia concentrations, and water levels) |
|
Monitors air traffic, traffic congestion areas, targeting vehicles that are violating traffic rules. |
|
Monitors the fitness level and exercise level of the patient. It is used in different biomedical applications, such as continuous ECG monitoring. |
|
Checking on different functionalities, like household appliances, biometric applications, and home security |
|
Monitors the movement of enemies at border areas, nuclear detection monitoring, secret communications in military applications. |
Energy saving is a challenging task for researchers, as more energy is consumed during data transmission. The consumption of energy also depends on other factors, like the redundancy of transmitted data, traffic flow of data packets, and communication bandwidth [18]. In WSNs, sensor nodes are not able to send data directly to the sink node, as fewer nodes lie at some distance from the sink. If they do so, then nodes which lie far away from the sink will die out earlier, as compared with the other nodes. Therefore, multi-hop communication is used, where all nodes send their data to their next-nearest node till they reach the sink node. The process of collecting and transmitting data from the nodes to the sink node is called the data aggregation process. Data aggregation is an important process, because its aims are to collate data from different sources. Different approaches for data aggregation include tree-based, multipath, cluster-based, hybrid, centralized, and in-network data aggregation approaches, which are studied with respect to different performance parameters, such as energy efficiency, data accuracy, latency, overhead, network lifetime, and scalability of the sensor network.
Research has pursued data aggregation techniques to lower the energy consumption in WSNs. In the past few years, protocols like Low-Energy Adaptive Clustering Hierarchy (LEACH), Power-Efficient Gathering in Sensor Information System (PEGASIS) and many more have been proposed by researchers to boost energy efficiency and to extend the network lifetime. For increasing the scalability of networks efficiently, hierarchical architecture is the preferred one. In this protocol, the holistic network is divided into layers, with nodes of an individual layer playing the same role. Clustering-based protocols are preferred, because they are energy-efficient methods. In clustering, there are two main parts: cluster members and a cluster head (CH). The selection of the CH depends on the estimated energy left in the node. The main responsibility of a CH is to remove redundancy and make transmission successful by reducing data traffic. The CH aggregates data from its cluster members and transmits it to the base station (BS). Thus, the process of clustering is divided into three different steps: selection of CH, formation of cluster, and data transmission.
The main drawback of clustering is the random distribution of the CH and the greater energy consumption by the CH, using single-hop communication. In addition, unequal load balancing occurs during data transmission in multi-hop communication with the BS. An alternative approach to gathering information from the nodes of network is with the help of a mobile agent (MA). Data aggregations with the help of MAs satisfy the requirement of energy efficiency and network lifetime. MA is a self-adaptive type of middleware technology, which moves autonomously in a network without any pre-installed requirements.
The use of MA in the context of WSN has various applications, like data aggregation, target tracking, reprogramming, healthcare, image querying, and intrusion detection, etc. When the MA is dispatched from the BS, it follows one of two itineraries, namely single itinerary planning (SIP) or multi-itinerary planning (MIP). Different algorithms of SIP have been compared and their findings and disadvantages will be discussed in this chapter. Various MIP algorithms, which describe the number of MAs required on the basis of partition, will also be discussed.
Further research has been pursued on external and internal attacks. Two principal methods of providing security in WSN have been proposed, namely cryptography and intrusion detection system (IDS). Cryptography is well suited to foreign attacks, but it fails to manage domestic attacks. IDSs are used to reveal malicious nodes in the network. IDS is a complex process, which follows a certain set of norms, with which the results should be examined. Thus, to ensure the security of WSN, trust-aware management has been introduced over the past few years. It calculates the value of trust of the nodes, which is further used in different processes of WSN, such as data aggregation and data routing. A detailed study of trust-aware management is discussed in the following sections.
The remaining sections of this chapter are structured as follows. A detailed survey of routing protocols is described under Section 2.2. Various data aggregation and clustering techniques are described in Sections 2.3 and 2.4. The drawbacks of clustering and the introduction of MA, along with their itineraries, are given in Sections 2.5 and 2.6. The importance of trust in WSN is discussed in Section 2.7. In the Conclusions, different research strategies are compared and discussed.
2.2 Routing Protocols in WSN
Different routing protocols are described in this section. Routing is the foremost parameter in the design of WSN. Researchers classify routing protocols into four different categories: network structure, communication model, topology-based protocols, and reliable routing protocols. Figure 2.2 shows the detailed taxonomy of routing protocols [19].

2.2.1 Network Structure
The network structure can be defined in accordance with the distribution of the sensor nodes. It can also be defined on the basis of the type of connection between the nodes, and by the routing method used to transfer the information. It can be classified as follows:
- a) Flat Routing Protocols. In flat-based protocols, all nodes of the sensor network are at the same level within it. It is a multi-hop routing technique [20] (Table 2.2).
- b) Hierarchical Routing Protocols. The whole network is divided into a small group of nodes called clusters, in which the CH is chosen, depending on the residual energy. When clusters are created in a sensor network, it results in an extended network lifetime, and improved energy efficiency and stability [31]. Different hierarchical routing protocols have been studied, and they are compared with respect to different parameters in Table 2.3.
TABLE 2.2
Comparison of Various Flat Routing Protocols
Routing Protocol |
Classification |
Data Aggregation |
SPIN [21] |
Negotiation |
Yes |
DD [22] |
Data-centric |
Yes |
Rumour routing [23] |
Data-centric |
No |
Gradient-based routing [24] |
Data-centric |
Yes |
Constrained Anisotropic Diffusion Routing (CADR) [25] |
Data-centric |
No |
Energy-Aware Routing (EAR) [26] |
Data-centric |
Yes |
Minimum Cost-Forwarding Algorithm (MCFA) [27] |
Data-centric |
No |
Active Query-Forwarding In-Sensor network (ACQUIRE) [28] |
Data-centric |
Yes |
Sequential Assignment Routing (SAR) [29] |
QoS-based |
Yes |
Energy-Aware Data-Centric Routing (EAD) [30] |
Data-centric |
Yes |
TABLE 2.3
Comparison between Hierarchical Routing Protocols

2.2.2 Communication Model
In these protocols, more data can be transferred within the energy available in the node. The protocols for this category can also achieve the theoretical optimum in point-to-point and broadcast networks with respect to dissemination rate and energy use. The controversy associated with this communication model is that the data transmission ratio is not high. Therefore, the delivery of data to the destination is uncertain.
- i) Query-Based Protocols. In this category, destination or sink node will broadcast an inquiry to find specific events among WSN. A particular node, which meets the query, will respond to the destination node from where the query was generated.
- ii) Coherent-Based Protocols. Data are transported after applying the data processing techniques, such as removing redundancy. Coherent processing is performed on the data to achieve energy-efficient routing.
- iii) Non-Coherent Protocols. In these protocols, the nodes process raw data themselves before forwarding them for further processing within the network.
- iv) Negotiation-Based Protocols. These protocols use metadata negotiations for reducing redundant network transmissions.
2.2.3 Topology-Based Protocols
These are based on topology with all nodes of the network in three ways, e.g., reactive, proactive and hybrid protocol. The protocols used in this category are described as follows:
- i) Location-based Routing Protocols. When using information about the position of nodes within the network, nodes are distinguished. The CH aggregates data from all its cluster members, removes the redundancy, and transmits the data into the BS.
- ii) Mobile Agent-Based Routing Protocols. MA is a middleware technology which migrates within the network for the collection of data. It works autonomously and intelligently. It overcomes the traditional client–server model.
2.2.4 Reliable Routing Protocols
These protocols are more resistant to network failures as a result of either realisation of load balancing routes or of satisfactory specific Quality of Service (QoS) metrics, such as delay, energy, and bandwidth. The protocols defined for this category are as below:
- i) Multipath-Based Protocols. They prefer to use multiple paths in comparison with using a single path, because, when a particular route has failed, it can opt for an alternative path. These protocols will increase the robustness and fault tolerance of the network.
- ii) QoS-Based Protocols. The network must balance energy utilisation with data quality. Each time a sink node requires data from nodes of a sensor network, the transmission must meet explicit quality levels. Also, it should take care of QoS parameters, such as delay, bandwidth, energy, etc.
2.3 Data Aggregation Approaches
Energy utilisation is the prime concern in sensor networks, as sensor nodes cannot send data to the BS directly. Sometimes, redundancy is increased by the neighbouring sensor nodes, which results in congestion at the BS, which becomes loaded with enormous amounts of data. As a consequence, it is necessary that redundancy is removed at some intermediary levels, which can result in a reduction in the number of data packets, which are forwarded to the BS. Reducing traffic at the BS saves energy and bandwidth. This approach is known as data aggregation [45]. It increases the lifetime of the network by decreasing the total data transmissions. The multi-hop approach is used to forward the sensed data to the CH. The CH uses either a traditional wired network or a fixed wireless medium to deliver the aggregated data to the BS. There are various approaches to data aggregation: the tree-based approach, centralised approach, in-network approach, cluster-based approach, and the multi-path approach.. Figure 2.3 describes the various data aggregation approaches.

Clustering is the most efficient data aggregation approach. It extends the network lifetime by reducing energy consumption. With the help of clustering, direct interaction among sensor nodes and the BS is decreased, which results in removed redundancy and reduced energy consumption.
2.4 Clustering in WSN
WSN is application oriented but, still, these networks suffer from several restrictions like energy constraints, limited battery capacity, etc. Nodes in the sensor network have less power and range, so cannot communicate directly with a sink node, if it is located at some distance away. If a sensor node tends to communicate directly with a distant sink node, it will give rise to greater use of energy resources, which results in network failure. Thus, to boost the lifetime of the network, the clustering technique is used. The selection of CH depends on the energy resources and it coordinates activities inside and outside the cluster. It also removes redundancy from the data gathered from other cluster members.
A number of clustering schemes have been proposed in recent years. These schemes inform the selection of CHs and the aggregation of data into clusters with network design. To reduce energy consumption of the sensor node during communication, various methods have been proposed. Clustering is defined as one of the main approaches to the development of protocols, which are effective, efficient, and scalable in WSNs. In clustering, the sensors of a network are grouped into small clusters, and each cluster is earmarked to a CH. After a certain interval of time, sensor nodes send the data to the CH, and it is the role of the CH to forward the data to the BS. Some benefits of clustering are listed below:
- 1. Clustering sustains the bandwidth for communication.
- 2. Clustering can balance the level of topology of the sensor network and reduce overhead traffic, with decreased overall maintenance costs.
- 3. It controls repetition of the substituted information between the nodes.
- 4. It helps to extend the life of the network.
- 5. Energy utilisation is decreased by management of the sleep cycle.
- 6. Fewer data packets are sent over the network.
- 7. Clustering prevents resending, reduces data repetition in the covered domain, and collisions are avoided.
A popular routing-based protocol based on clustering is LEACH, which is subdivided into rounds; in each respective round, the CH role is circulated between nodes, to maintain balance. With the intension of optimising energy use in the network, nodes are selected in terms of CH circularity and randomness. Based on the principle of proximity, normal nodes, which are referred to as cluster members, are a part of the corresponding CH. The main drawback of LEACH is that the CH selection is based upon probability, rather than the surplus energy of the nodes. Therefore, sometimes the wrong CH is selected, which has a small amount of energy, and, as a result, the CH dies out early. Table 2.4 shows a comparison of different parameters of LEACH and its variants [46–49]. The LEACH variants exhibit improved functioning than the standard LEACH protocol.
TABLE 2.4
Comparison of LEACH and its Variants

2.5 Mobile Agent-Based Clustering
Earlier research proposed clustering as a prime technique for achieving energy efficiency in WSN. This is because clustering allows the sensor nodes to gather the data at a single node, the CH, which forwards the data to BS, rather than allowing every single sensor node to send the data to the BS. The clustering evolves from the LEACH protocol, which uses three phases: CH selection, the formation of the cluster, and data forwarding via the CH. Clustering, in itself, suffers drawbacks, like random distribution of CH, greater energy consumption by the CH in single-hop communication with the BS, or unequal load balancing in multi-hop communication with the BS. Another approach to aggregate information from the sensor nodes is with the help of a mobile agent (MA) [59].
MA can migrate within technology that can migrate within a sensor network, and perform the assigned task such as data aggregation, data fusion, etc. It replaces the traditional client–server approach because of its different benefits. Table 2.5 shows a comparison between the traditional–client server model and the mobile agent model.
TABLE 2.5
Comparison between Traditional Client–Server Model and Mobile Agent Model
Traditional Client–Server |
Mobile Agent-Based |
Congestion of traffic |
Reduces network load |
Hot-spot problem |
Mobility of server/sink |
Not flexible according to application |
Application oriented |
More energy usage |
Less consumption of energy |
Lifetime of the network is shortened |
Enhanced network lifetime |
Not dynamic |
Dynamic |
Not scalable |
Scalability is possible |
Less reliable |
More reliable |
The MA has great advantages, such as short time of execution. This is because each and every node contributes effort to data aggregation. When the MA dispatched by the server in the network, it visits and collects interesting data, and aggregates it. The aggregated data is forwarded to the server by the MA. A number of MA-based networks have been developed by various researchers.
2.6 MA Itineraries in WSNs
There are different uses of MA in the context of WSN, for different applications, such as data aggregation, reprogramming, healthcare, intrusion detection, etc. The performance of all these applications is entirely dependent on the route followed by an MA. The itineraries for MA can be designed by either choosing single itinerary or multiple itineraries.
2.6.1 Single Itinerary Planning
A single agent is dispatched from the BS, when using Single Itinerary Planning (SIP). Two different heuristic algorithms have been proposed [60]: (i) Local Closest First (LCF), which looks at the subsequent node with the shortest distance from the current node; and (ii) Global Closest First (GCF), which looks at the node which is next to the sink. A third routing protocol is the MA-based directed diffusion protocol (MADD) [61]. MADD is near-identical to LCF, and they are differentiated only on the basis that, in MADD, the MA selects the node which is farthest from the sink as the first node. Hence, these three routing protocols (LCF, GCF, and MADD) are not complicated to follow, but are not capable of being upscaled, because the distance between the source node and destination node determines the route.
In [62], two algorithms were designed to accomplish energy-efficient itineraries, namely the itinerary designed for minimum energy for first-source selection (IEMF), and the itinerary designed for minimum energy algorithm (IEMA). IEMF follows the round-robin method for tentatively by choosing the first source node to be visited according to estimated communication cost. Then, the LCF algorithm is applied to the rest of the source nodes. Such a process proposes various itineraries for candidates, each route contributing to energy costs. Afterwards, the IEMF selects the route with the lowest energy cost. IEMA is an iterative version of IEMF, i.e., IEMA defines the sequence by which the unused source nodes are visited as the first source node. Rather than searching for global network information, LCF looks for the adjacent MA hop, which depends on the MA’s current position. In addition, LCF, GCF, IEMF, and IEMA algorithms are developed using a SIP with degraded conduct in a wide network.
2.6.2 Multi-Itinerary Planning
SIP performs well for a small-scale network but it fails in large-scale networks, because of the following drawbacks:
- i) As there is only one MA, which has to take a tour of hundreds of nodes within the network for data collection, this network suffers from long delays.
- ii) There is a possibility that MA can be lost during migration to several nodes.
- iii) The size of the data packet is increased when it aggregates from node to node and consumes more energy.
- iv) As MA accumulates more and more data, its reliability decreases.
MIP overcomes these drawbacks by sending multiple MAs. Thus, MIP can be defined as an itinerary in which more than one MA is dispatched by the server in the network. The determination of the best possible route for MA is inspired by the arrangement of a global network in a large-scale network in which the MIP approach takes place. For calculations of the required number of Mas, along with their paths, the near-optimal itinerary design (NOID) algorithm was introduced in [63]. The distance between source nodes is the main parameter used in cost–weight calculations. This distance is calculated based on the minimum spanning tree (MST). Thus, it acts as a compromise to balance, so that the MA first visits a source node with inadequate energy (where the MA data are less).
However, the BST–MIP algorithm is differentiated from the NOID due to the fact that, at some stage in weight calculation in a totally connected graph (TCG), which indicates that all source nodes in a particular sub-tree should be considered as a group, it makes use of a balance factor [64]. The balance factor is used to get a flexible control between energy costs and task duration. A genetic algorithm (GA), based on MIP, was designed to be used to calculate the desired number of MAs, along with their MIP itineraries [65].
The idea behind GA-MIP is to determine the required number of MAs and their allocated source nodes, with the help of a two-tier coding method, based on GA. This coding acts as a gene that involves a series array (sequence) and a set array (group). The series array accommodates segments corresponding to a number of source nodes, associated with a MA. Each number of source arrays corresponds to source nodes for each segment. Each iteration uses two basic GA operations (crossover and mutation) and a fitness function for the selection of better genes. Despite good delay and energy consumption performances, GA-MIP also has a high computational complexity because of the need to maintain global network information in each iteration. In this GA-MIP referred to above, the geographical information of nodes and the cost of the MA itinerary are the main parameters which are used to determine the itineraries for the optimal number of MAs.
The greatest information in the greater memory based MIP (GIGM-MIP) algorithm takes geographical information into account in order to define useful number of MAs, along with their itineraries and data size in each partition [66]. The k-means clustering in GIGM-MIP tends to split the network into different clusters (partitions). The GIGM-MIP algorithm considers the data size of the source nodes for each cluster after partitioning the network. This data size determines the number of MAs allocated to a particular partition, so that each cluster is allocated more than one MA. The node with the largest free payload data is then assigned to the MA which has the maximum data size in comparison with the other nodes. This process is reiterated until all the MAs have almost the same size of payload data.
With this solution, a balance is maintained between the transported data and the distributed MAs, and it leads to a decrease in energy consumption. To find out the desired number of MAs and their itineraries, an immune-inspired algorithm is proposed, which is also called the Clonal Selection Algorithm for MIP (CSA-MIP) [67]. It uses the same two-level method of coding as the GA-MIP method. The difference between CSA-MIP and the previous MIP is that it uses an evolutionary two-stage search process for identifying overall search capabilities, with a different assigned mutation operator at each stage. While using these search methods, the solutions obtained from it result in variability in the number of MAs. In addition, the imbalance is decreased when the desired number of sensor nodes is assigned to each MA. This situation may give rise to increased chances of achieving better solutions (Table 2.6).
TABLE 2.6
Comparison of Different Algorithms of MA Itineraries

2.7 Trust-aware WSN
The MA-based data aggregation provides efficient and effective data aggregation, based on the MA itinerary. In addition to the migration of these energy-efficient MAs, another important matter of interest is the safety of MA in terms of malicious or compromised nodes. The topic of trust is an open and current field in WSN. A number of trust schemes have been surveyed and studied from different perspectives. When MA encounters a malicious node, a false reprogramming can be done by it which, in turn, results in corruption of the network, stopping the functioning of the MA, etc.
In the past few years, trust management has become included in the literature for assessing the node’s trust value, based on the functional behaviour of the protocol. This assessed or calculated trust value can also be used for decision making with respect to data routing, data aggregation, and intrusion detection [68]. Two approaches to data aggregation in a trust-aware network are suggested in [69], where the first is the aggregation input collection and the second one is an inconsistency check. Data are aggregated at regular intervals of time, where the data are checked for inconsistency, if there is any need to calculate the trust of nodes.
Another secure algorithm for selecting the CH is achieved by calculating the weight of each node, with the intention of confirming that the minimum energy utilised is used for safe selection. The node’s weight combines different metrics, including trust metrics (node behaviour), which assists the decision to select the CH, which means that the node will never be a malicious one [70].
The trust metric is conclusive and permits the proposed algorithm to prevent the selection of a CH by any malicious node in the area, even if the remaining parameters support it. Other node metrics are also studied, which includes waiting time, degree of connectivity, and the distance between the nodes. The CH selection, using the weights of members’ nodes, is completed. MAEF is proposed, which is based on energy- and fault-conscious data aggregation in WSN. MA is sent to the selected CH, and this CH is chosen on the basis of the highest node density [71]. MA only visits selected CHs to collect data, which show improvements in network life, and also in energy consumption.
2.8 Summary and Conclusions
Today, the WSNs have immensely expanded their vital role in data-efficient selection and transport of data to destinations. The utilisation of energy resources is a critical issue for the networks, particularly in wireless networks, which are characterised by shorter battery lives. The complexity and dependence of corporate operations performed on WSNs require efficient routing techniques and protocols to ensure network interlinking and information routing, with the least energy expenditure. In this paper, the attention is given to the energy-efficient protocols, associated with WSNs.
With the requirements of the next generation of wireless networks and personal communication systems, a new type of system, based on the MA, has been developed. MA offers a unique and promising solution to increase the efficiency of energy use while aggregating data, with this agent-based approach being the most promising one for solving the data problem of WSN.
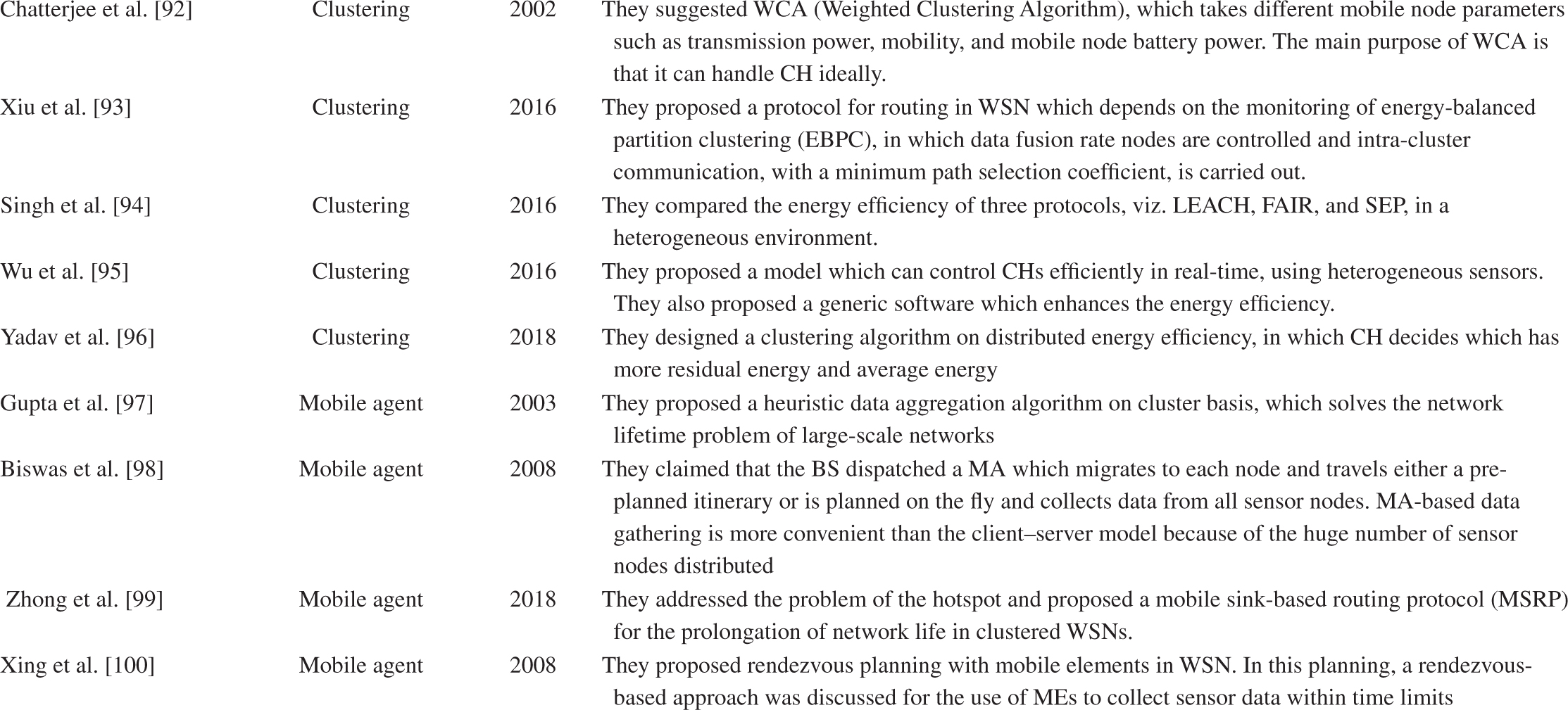
This approach can easily eliminate redundancy in data, with only the relevant specific data being transferred to the sink. MA will visit the network for data aggregation by two types of itineraries planned by the BS. It can follow either the single itinerary planning or multi-itinerary planning route. This paper also discussed trust metrics, issues related to the construction of a WSN, and issues dealing with trust management. There is no standard model available which can be used in current trust systems to offer safety or resilience to attacks. The designers are trying to solve the problem of trustworthiness from various angles. Future trust management research will focus on a generalised, scalable, and reconfigurable model of trust, which is accessible to different distributed computing systems, which deal with malicious and non-malicious nodes, while processing the data. Such a development will improve security problems in a better way and can meet the application demands of the consumer. Table 2.7 summarises the literature related to data aggregation, clustering, mobile agents, and trust-aware.
TABLE 2.7
Survey Related to Data Aggregation, Clustering, Mobile Agent and Trust-Aware





2.9 Future Scope
The relevant literature suggests some unique ideas, covering most of the areas of WSN, such as clustering, data aggregation, mobile agents, MA itineraries and trust-aware protocols. Many of the topics which are presented in this chapter are open for new discussions and for further research. This literature survey is intended for all who work with WSNs and related fields, to keep up with progress in the field. One of the most-important current topics in WSN is trust-aware, which needs to be explored in more detail. In trust-aware, a malicious node has to be detected by calculating the trust value before the data aggregation process is run. It is preferred over traditional cryptography methods because it has minimal computational cost.
Bibliography
- 1. J.A. Stankovic (2008). Wireless sensor networks, IEEE Computer, 41(10), 92–95.
- 2. K. Yang (2014). Wireless sensor networks. In: Principles, Design and Applications. Signals and Communication Technology, Springer.
- 3. Xin Dong, Mehmet C. Vuran, and Suat Irmak (2013). Autonomous precision agriculture through integration of wireless underground sensor network with center pivot irrigation systems. In: Ad Hoc Networks, Elsevier, 1975–1987.
- 4. Vendula Hejlova and Vit Vozenilek (2013). Wireless sensor network components for air pollution in urban environment: Criteria and analysis for their selection, Wireless Sensor Networks, 5, 229–240.
- 5. Kavi K. Khedo, Rajiv Perseedoss, and Avinash Mungur (2010). A wireless sensor network Air pollution monitoring system, International Journal of Wireless and Mobile Networks, 2(2), 31–45.
- 6. B. Kechar, N. Houache, and L. Sekhri (2013). Using wireless sensor network for reliable forest fire detection, 3rd International conference on sustainable energy information technology, Procedia Computer Science,19, 794–801.
- 7. Yunus E. Aslan, Ibrahim Korpeoglu, and Ozgur Ulusoy (2012). A Framework for use of wireless sensor network in forest fire detection and monitoring, Computers, Environment and Urban Systems, 36(6), 614–625.
- 8. A. Pascale, M. Nicoli, F. Deflorio, B. Dalla Chaira, and U. Spagnolini (2012). Wireless sensor network for traffic management and road safety, IET Intelligent Transportation Systems, 6(1), 67–77.
- 9. Rahat Ali Khan, Shakeel Ahmed Shah, Muhammad Abdul Aleem, and Zulfiqar Ali Bhutto (2012). Wireless sensor networks: A solution for smart transportation, Journal of Emerging Trends in Computing and Information Science, 3(4), 566–571.
- 10. J. Guevara, F. Barrero, E. Vargas, and J. Becerra (2011). Environmental wireless sensor network for road traffic application, IET Intelligent Transportation Systems, 6(2), 177 –1186.
- 11. Reza S. Dilmaghani, Hossein Bobarshad, M. Ghavami, S. Choobkar, and Charles Wolfe (2011). Wireless sensor networks for monitoring physiological signals of multiple patients, IEEE Transactions on Biomedical Circuits and Systems, 5(4), 347–356.
- 12. Joao Martinho, Luis Prates, and Joao Costa (2014). Design and Implementation of a wireless multi parameter patient monitoring system, Procedia Technology, 17, 542–549.
- 13. S. Nagender Kumar, C.M. Subas and, Sean Dieter Tebje Kelly (2015). WSN - Based smart sensors and actuator for power management in Intelligent Buildings, IEEE/ASME Transactions on Mechatronics, 20(2), 564–571.
- 14. Sherine M. Abd EI-Kader Basma, and M. Abdelmonim (2013). Smart home designs using wireless sensor networks and biometric technologies, International Journal of Application or Innovation in Engineering and Management, 2(3), 413–429.
- 15. Hanne Grindvoll, Ovidiu Vermesan, Tracey Crosbie, Roy Bahr, Nashwan Dawood, and Gian Marco Revel (2012). A wireless sensor network for intelligent building energy management based on multi communication standards – A case study, Journal of Information Technology in Construction, 17, 43–61.
- 16. L. Louise, T. Mylene, D. Mathieu, and P. Glenn (2011). Tiered wireless sensor network architecture for military surveillance application. In: SENSORCOMM 2011: The Fifth International Conference on Sensor Technologies and Applications, 288–294.
- 17. G. Padmavathi, D. Shanmugapriya, and M. Kalaivani (2010). A study on vehicle detection and tracking using wireless sensor networks, Wireless Sensor Networks, 2(2), 173–185.
- 18. K. Sohraby, D. Minoli, and T. Znati (2007) Wireless Sensor Networks: Technology, Protocols, and Applications, NJ: Wiley Interscience: A John Wiley & Sons Publication.
- 19. M. MehdiAfsar, H. Mohammad, and N. Tayarani (2014). Clustering in sensor networks: A literature survey, Journal of Network and Computer Applications, 46, 198–226.
- 20. P. Arce, J. Guerri, A. Pajares, and O. Lazaro (2008). Performance evaluation of video streaming over ad hoc networks of sensors using FLAT and hierarchical routing protocols, book, Mobile Networks and Applications 13, 324–336.
- 21. F. Bokhari (2011). Energy-efficient QoS-based routing protocol for wireless sensor networks, Parallel and Distributed Computing, Department of Computer Science, Lahore University of Management Sciences, 70(8), 849–885.
- 22. C. Intanagonwiwat, R. Govindan, and D. Estrin (2000). Directed diffusion: A scalable and robust communication paradigm for sensor networks. In: Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, 56–67.
- 23. D. Braginsky and D. Estrin (2002). Rumor routing algorithm for sensor networks. In: Proceedings of the First Workshop on Sensor Networks and Applications (WSNA), Atlanta, GA.
- 24. C. Schurgers and M.B. Srivastava (2001). Energy efficient routing in wireless sensor networks, in the MILCOM. In: Proceedings of the on Communications for Network-Centric Operations: Creating the Information Force, McLean, VA.
- 25. M. Chu, H. Haussecker, and F. Zhao (2002). Scalable information-driven sensor querying and routing for ad hoc heterogeneous sensor networks, The International Journal of High Performance Computing Applications, 16(3), 207–219.
- 26. S. Guo and O.W.W. Yang (2007). Energy-aware multicasting in wireless ad hoc networks: A survey and discussion, Computer Communications, 30(9), 2129–2148.
- 27. F. Ye, A. Chen, S. Lu, and L. Zhang (2001). A scalable solution to minimum cost forwarding in large sensor networks. In: Proceedings of the 10th International Conference on Computer Communications and Networks (ICCCN ’01), Scottsdale, Ariz, 304–309.
- 28. N. Sadagopan et al. (2003). The ACQUIRE mechanism for efficient querying in sensor networks. In: The Proceedings of the First International Workshop on Sensor Network Protocol and Applications, Anchorage, Alaska.
- 29. K. Sohrabi, J. Gao, V. Ailawadhi, and G. Pottie (1999). Protocols for self-organization of a wireless sensor network, IEEE Personal Communications, 7(5), 16–27.
- 30. K. Akkaya and M. Younis (2005). A survey of routing protocols in wireless sensor networks. The Elsevier Ad Hoc Network Journal, 3(3), 325–349.
- 31. D. Xu and J. Gao (2011). Comparison study to hierarchical routing protocols in wireless sensor networks. In: International Conference on Environmental Science and Information Application Technology (ESIAT), 595–600.
- 32. W. Heinzelman, A. Chandrakasan, and H. Balakrishnan (2011). Energy-efficient routing protocols for wireless microsensor networks. In: Proceedings of the 33rd Hawaii International Conference System Sciences (HICSS), Maui, HI.
- 33. A. Manjeswar, D.P. Agrawal, and TEEN (2001). A protocol for enhanced efficiency in wireless sensor networks. In: Proceedings of 1st International Workshop on Parallel and Distributed Computing Issues in Wireless Networks and Mobile Computing, San Francisco, CA, 189.
- 34. A. Manjeshwar, D.P. Agrawal, and APTEEN (2002). A hybrid protocol for efficient routing and comprehensive information retrieval in wireless sensor networks. In: Proceedings of the International Parallel and Distributed Processing Symposium (IPDPSí02), IEEE, 1530–2075.
- 35. S. Lindsey, C.S. Raghavendra, and PEGASIS (2002). Power Efficient gathering in sensor information systems. In: Proceedings of the IEEE Aerospace Conference, Big Sky, MT.
- 36. O. Younis and S. Fahmy (2004). HEED: A Hybrid, Energy-Efficient, Distributed clustering approach for Ad Hoc sensor networks, IEEE Transactions on Mobile Computing, 3(4), 366–379.
- 37. Naveen Sharma and Anand Nayyar (2014). A comprehensive review of cluster based energy efficient routing protocols for wireless sensor networks,International Journal of Application or Innovation in Engineering & Management (IJAIEM), 3(1), 441–453.
- 38. L. Qing, Q. Zhu, and M. Wang (2006). Design of a distributed energy-efficient clustering algorithm for heterogeneous wireless sensor networks, Computer Communications, 29(12), 2230–2237.
- 39. P. Ding, J. Holliday, and A. Celik (2005). Distributed energy efficient hierarchical clustering for wireless sensor networks. In: Proceedings of the IEEE International Conference on Distributed Computing in Sensor Systems(DCOSS’05), Marina Del Rey, CA.
- 40. S. Jung, Y. Han, and T. Chung (2007). The concentric clustering scheme for efficient energy consumption in the PEGASIS. Proceedings of the 9th International Conference on Advanced Communication Technology, Gangwon-do, Korea,12(14), 260–265.
- 41. Janvi A. Patel and Yask Patel (2018). The clustering techniques for wireless sensor networks: A review. In: Proceedings of the 2nd International Conference on Inventive Communication and Computational Technologies (ICICCT 2018), Coimbatore, India, 147–151.
- 42. D. Koutsonikola, S. Das, H.Y. Charlie, and I. Stojmenovic (2010). Hierarchical geographic multicast routing for wireless sensor networks, Wireless Networks, 16(2), 449–466.
- 43. Y. Xu, J. Heidemann, and D. Estrin (2001). Geography-informed energy conservation for ad-hoc routing. In: Proceedings of the Seventh Annual ACM/IEEE International Conference on Mobile Computing and Networking, 70–84.
- 44. S. Misra and R. Kumar (2017). An analytical study of LEACH and PEGASIS protocol in wireless sensor network. In: 2017 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS).
- 45. H. Tan and K. Ibrahim (2003). Power efficient data gathering and aggregation in wireless sensor networks, ACM SIGMOD Record, 32(4), 66–71.
- 46. S. Madden, M. Franklin, J., Hellerstein, and W. Hong (2002) TAG: A Tiny Aggregation Service for Ad- hoc Sensor Networks, Boston, MA: OSDI.
- 47. M. Lee and V.W.S. Wong (2005) An energy-aware spanning tree algorithm for data aggregation in wireless sensor networks. In:IEEE Pac Rim 2005, Victoria, BC, Canada.
- 48. L. Gatani, G. Lo Re, and M. Ortolani (2006). Robust and efficient data gathering for wireless sensor networks. In: Proceeding of the 39th Hawaii International Conference on System Sciences.
- 49. Noritaka Shigei, Hiromi Miyajima, Hiroki Morishita, and Michiharu Maeda (2009). Centralized and distributed clustering methods for energy efficient wireless sensor networks. In: Proceedings of the International MultiConference of Engineers and Computer Scientists 2009 Vol I Imecs 2009, Hong Kong.
- 50. H. Khattab, A. Al-Shaikh, and S. Al-Sharaeh (2018). Performance comparison of LEACH and LEACH-C protocols in wireless sensor networks. Journal of ICT Research and Applications, 12(3), 219.
- 51. J. Gnanambigai, N. Rengarajan, and K. Anbukkarasi (2012). Leach and its descendant protocols: A survey, International Journal of Communication and Computer Technologies (IJCCT), 1(3), 15–21.
- 52. P. Manimala and R. Senthamil Selvi (2013). A survey on leach energy based routing protocol, International Journal of Emerging Technology and Advanced Engineering (IJETAE), 3(12), 657–660.
- 53. A. Braman and G.R. Umapathi (2014). A Comparative Study on Advances in LEACH Routing Protocol for Wireless Sensor Networks: A survey, International Journal of Advanced Research in Computer and Communication Engineering (IJARCCE), 3( 2), 5683–5690.
- 54. R. Kaur, D. Sharma, and N. Kaur (2013). Comparative analysis of leach and its descendant protocols in Wireless Sensor Network,International Journal of P2P Network Trends and Technology (IJPNTT), 3(1), 51–55.
- 55. M. Ahmad Jan and M. Khan (2013). A survey of cluster-based hierarchical routing protocols, IRACST, International Journal of Computer Networks and Wireless Communications (IJCNWC), 3(2), 138–143.
- 56. V. Kumar, S. Jain, and S. Tiwari (2011). Energy efficient clustering algorithms in wireless sensor networks: A survey, International Journal of Computer Science Issues (IJCSI), 8(5), 259–268.
- 57. A. Yektaparast, F.H. Nabavi, and A. Sarmast (2012). An Improvement on LEACH protocol (Cell-LEACH). In: 14th International Conference on Advanced Communication Technology (ICACT), 992–996.
- 58. N. Sindhwani and R. Vaid (2013). V Leach: AN energy efficient communication protocol for WSN, Mechanica Confab, 2( 2), 79–84.
- 59. M. Chen, T. Kwon, Y. Yuan, and V.C.M. Leung (2006). Mobile agent based wireless sensor networks, Journal of Computers, 1(1), 14–21.
- 60. H. Qi and F. Wang (2001). Optimal itinerary analysis for mobile agent. In: Ad hoc Wireless Sensor Networks, Proceedings of the IEEE, 147–153.
- 61. M. Chen, T. Kwon, Y. Yuan, Y. Choi, and V.C.M. Leung (2007). Mobile agent based directed diffusion in wireless sensor networks, EURASIP Journal on Applied Signal Processing, 2007(1), 036871.
- 62. M. Chen, L.T. Yang, T. Kwon, L. Zhou, and M. Jo (2011). Itinerary planning for energy-efficient agent communications in wireless sensor networks, IEEE Transactions on Vehicular Technology, 60(7), 3290–3299.
- 63. D. Gavalas, A. Mpitziopoulos, G. Pantziou, and C. Konstantopoulos (2010). An approach for near-optimal distributed data fusion in wireless sensor networks, Wireless Networks, 16( 5), 1407–1425.
- 64. M. Chen, W. Cai, S. Gonzalez, and V. Leung (2010). Balanced itinerary planning for multiple mobile agents in wireless sensor networks. In: Proceedings of the 2nd International Conf ADHOCNETS, Victoria, BC, Canada, 416–428.
- 65. W. Cai, M. Chen, T. Hara, L. Shu, and T. Kwon (2011). A genetic algorithm approach to multi-agent itinerary planning in wireless sensor networks, Mobile Network Applications, 16( 6), 782–793.
- 66. I. Aloui, O. Kazar, L. Kahloul, and S. Servigne (2015). A new itinerary planning approach among multiple mobile agents in wireless sensor networks (WSN) to reduce energy consumption’, International Journal Communication Network Information Security, 7(2), 116–122.
- 67. Y.-Cheng Chou and M. Nakajima (2017). A clonal selection algorithm for energy efficient mobile agent itinerary planning in wireless sensor networks. In: Mobile Networks and Applications, New York, NY: Springer, 1–14.
- 68. P.R. Vamsi and K. Kant (2014). Systematic design of trust management systems for wireless sensor networks: A review. In: Fourth International Conference on Advanced Computing & Communication Technologies (ACCT), Rohtak, India, 208–215.
- 69. H. Deng, G. Jin, K. Sun, R. Xu, M. Lyell, and J.A. Luke (2009). Trust-aware in-network aggregation for wireless sensor networks. In: IEEE Global Telecommunications Conference, GLOBECOM 2009, 1–8.
- 70. E. Rehman, M. Sher, S. Hussnain, A. Naqvi, B. Khan, and K. Ullah (2017) Energy efficient secure trust based clustering algorithm for mobile wireless sensor network, Hindawi Journal of Computer Networks and Communications 2017(4), 1–8.
- 71. M.E. Fissaoui, A. Beni-hssane, M. Saadi (2018). Energy Efficient and fault tolerant distributed algorithm for data aggregation in wireless sensor networks, Journal of Ambient and Intelligence and Humanized Computing 10, 569–578.
- 72. Rabindra Bista, Yong-Ki Kim, and Jae-Woo Chang (2009) A new approach for energy-balanced data aggregation in wireless sensor networks. In:IEEE Ninth International Conference on Computer and Information Technology, China, 2.
- 73. Yasir Faheem and Saadi Boudjit (2010). SN-MPR: A multi-point relay based routing protocol for wireless sensor networks, In: IEEE/ACM International Conference On Green Computing and Communications & International Conference on Cyber, Physical and Social Computing, 761–767.
- 74. Miao Zhao and Yuanyuan Yang (2010). Data gathering in wireless sensor networks with multiple mobile collectors and SDMA technique sensor networks. In: The WCNC Proceedings, 1–6.
- 75. Babar Nazir and Halabi Hasbullah (2010). Mobile sink based routing protocol (MSRP) for prolonging network lifetime in clustered wireless sensor network. In: International Conference on Computer Applications and Industrial Electronics (ICCAIE), Kuala Lumpur, Malaysia..
- 76. Chi Yang, Zhimin Yang, Kaijun Ren, and Chang Liu (2011). Transmission reduction based on order compression of compound aggregate data over wireless sensor networks. In: 6th International Conference on Pervasive Computing and Applications (ICPCA), 335–342.
- 77. Songtao Guo and Yuanyuan Yang (2012). A distributed optimal framework for mobile data gathering with concurrent data uploading in wireless sensor networks. In: Proceedings of the IEEE Infocom, 1305–1313.
- 78. Xi Xu, Rashid Ansari, and Ashfaq Khokhar (2013). Power-efficient hierarchical data aggregation using compressive sensing in WSNs. In: IEEE ICC - Ad-hoc and Sensor Networking Symposium, 1769–1773.
- 79. M. Soltani, Michael Hempel, and Hamid Sharif (2014). Data fusion utilization for optimizing large-scale wireless sensor networks. In: IEEE ICC, 2014 - Ad-hoc and Sensor Networking Symposium, 367–372.
- 80. Shiliang Xiao, Baoqing Li, and Xiaobing Yuan (2015) Maximizing precision for energy-efficient data aggregation in wireless sensor networks with lossy links, Ad Hoc Networks, Elsevier,26, 103–113.
- 81. A. Awang and S. Agarwal (2015). Data aggregation using dynamic selection of aggregation points based on RSSI for wireless sensor networks, Wireless Personal Communications, 80(2), 611–633.
- 82. P. Zhong, Y.T. Li, W.R. Liu . Joint mobile data collection and wireless energy transfer in wireless rechargeable sensor networks, Sensors, 17(8), 1–23.
- 83. Runze Wan, Naixue Xiong, Qinghui Hu, Haijun Wang, and Jun Shang (2019). Similarity-aware data aggregation using fuzzy c-means approach for wireless sensor networks, EURASIP Journal on Wireless Communications and Networking, 2019(1), 59.
- 84. Min Chen, Laurence T. Yang, Taekyoung Kwon, Liang Zhou, and Minho Jo (2011). Itinerary planning for energy-efficient agent communications in wireless sensor networks, IEEE Transactions on Vehicular Technology, 60(7), 3290–3299.
- 85. Min Chen, Taekyoung Kwon, Yong Yuan, and Victor Leung . Mobile agent based wireless sensor networks, Journal of Computers, 1(1), 14–21.
- 86. Min Chen, Sergio Gonzalez, and Victor C.M. Leung (2007). Applications and design issues for mobile agents in wireless sensor networks, Wireless Communications, IEEE, 14(6), 20–26.
- 87. Min Chen, Taekyoung Kwon, and Yanghee Choi (2005). Data dissemination based on mobile agent in wireless sensor networks. In: IEEE Conference on Local Computer Networks (LCN’05), 527–529.
- 88. Chee-Yee Chong and Srikanta P. Kumar (2003). Sensor networks: Evolution, opportunities, and challenges. Proceedings of the IEEE, 91(8), 1247–1256.
- 89. Chien-Liang Fok, Gruia-Catalin Roman, and Chenyang Lu (2005). Mobile agent middleware for sensor networks: An application case study. In: Fourth IEEE International Symposium on Information Processing in Sensor Networks, 382–387.
- 90. Preeti Sethi, Dimple Juneja, and Naresh Chauhan . Exploring the feasibility of mobile agents in sensor networks in non-deterministic environments, International Journal of Advancements in Technology(IJoAT), 1(2), 296–302.
- 91. Francisco Aiello, Fabio Luigi Bellifemine, Giancarlo Fortino, Stefano Galzarano, and Raffaele Gravina (2011). An agent-based signal processing in-node environment for real-time human activity monitoring based on wireless body sensor networks, Engineering Applications of Artificial Intelligence, 24(7), 1147–1161.
- 92. M. Chatterjee, S.K. Das, and D. Turgut (2002). WCA: A weighted clustering algorithm for mobile ad hoc networks, Cluster Computing, 5(2), 193–204.
- 93. Y. Xiuwu, Fan Feisheng Zhou Lixing, and Z. Feng (2016) WSN monitoring area partition clustering routing algorithm for energy-balanced. In: IEEE, 80–84.
- 94. O. Singh, V. Rishiwal, and M. Yadav (2016) Energy trends of routing protocols for H-WSN. In: IEEE.
- 95. M. Wu, H. Liu, and Q. Min (2016) Lifetime enhancement by cluster head evolutionary energy efficient routing model for WSN. In: IEEE, 545–548.
- 96. P. Yadav, V.K. Yadav, and S. Yadavc (2018). Distributed energy efficient clustering algorithm to optimal cluster head by using biogeography based optimization, Materials Today: Proceedings, 5(1), 1545–1551.
- 97. K. Dasgupta, K. Kalpakis, and P. Namjoshi (2003). An efficient clustering-based heuristic for data gathering and aggregation in sensor network. In: Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC, 2003), New Orleans, LA.
- 98. P.K. Biswas, H. Qi, and Y. Xu (2008). Mobile-agent-based collaborative sensor fusion, Information Fusion, 9(3), 399–411.
- 99. P. Zhong and F. Ruan (2018).An energy efficient multiple mobile sinks based routing algorithm for wireless sensor networks in, IOP Conference Series: Materials Science and Engineering, 323, 012029.
- 100. Guoliang Xing, Tian Wang, Zhihui Xie, and Weijia Jia (2008). Rendezvous planning in wireless sensor networks with mobile elements, Mobile Computing, IEEE Transactions On, 7(12), 1430–1443.
- 101. Huan Zhao, Songtao Guo, Xiaojian Wang, and Fei Wang (2015). Energy-efficient topology control algorithm for maximizing network lifetime in wireless sensor networks with mobile sink, Applied Soft Computing, 34(C), 539–550.
- 102. A. Muthu Krishnan, and P. Ganesh Kumar (2015). An effective clustering approach with data aggregation using multiple mobile sinks for heterogeneous WSN, Wireless Personal Communications 90(2), 1–12.
- 103. Deepa V. Jose and G. Sadashivappa (2015). A novel scheme for energy enhancement in wireless sensor networks. In: Computation of Power, Energy Information and Communication (ICCPEIC), International Conference, 0104–0109.
- 104. C. Konstantopoulos, A. Mpitziopoulos, D. Gavalas, G. Pantziou (2010). Effective determination of mobile agent itineraries for data aggregation on sensor networks, IEEE Transactions of Knowledge and Data Engineering, 22(12), 1679–1693.
- 105. H. Deng, G. Jin, K. Sun, R. Xu, M. Lyell, and J.A. Luke (2009). Trust-aware in-network aggregation for wireless sensor networks. In: IEEE Global Telecommunications Conference, GLOBECOM 2009, 1–8.
- 106. E. Rehman, M. Sher, S. Hussnain, A. Naqvi, B. Khan, and K. Ullah (2017). Energy efficient secure trust based clustering algorithm for mobile wireless sensor network, Hindawi Journal of Computer Networks and Communications. doi:10.1155/2017/1630673.
- 107. Rui Wang, Zhiyong Zhang, Zhiwei Zhang, and Zhiping Jia (2018) ETMRM: An energy-efficient trust management and routing mechanism for SDWSNs, Computer Networks Elsevier, 139, 119–135.
- 108. Bibudhendu Pati, Joy Lal Sarkar, and Chhabi Rani Panigrahi (2017). ECS: An energy-efficient approach to select cluster-head in wireless sensor networks, Arabian Journal for Science and Engineering, Springer 42(2), 669–676.
- 109. Fouad Hajji, Cherkaoui Leghris, and Khadija Douzi (2018). Adaptive routing protocol for Lifetime maximization in multi-constraint wireless sensor networks, Journal of Communications and Information Networks, 3(1), 67–83.
- 110. B.M. Khan, R. Bilal, and R. Young (2017). Fuzzy-TOPSIS based cluster head selection in mobile sensor network, Journal of Electrical Systems and Information Technology. doi:10.1016/j.jesit.2016.12.004.
- 111. Govind P. Gupta (2018). Improved cuckoo search-based clustering protocol for wireless sensor networks, Procedia Computer Science, 125, 234–240.
- 112. K. Lingaraj, Rajashree V. Biradar, and V.C. Patil . (2018). Eagilla: An enhanced mobile agent middleware for wireless sensor networks, Alexandria Engineering Journal, Elsevier, 57(3), 1197–1204.
- 113. S. Sasirekha and S. Swamynathan (2017). Cluster-chain mobile agent routing algorithm for efficient data aggregation in wireless sensor network, Journal of Communications and Networks, 19(4), 392–401.
- 114. Chien-Fu Cheng and Yu Chao-Fu (2018). Mobile data gathering with bounded relay in wireless sensor networks, IEEE Internet of Things Journal, 5(5), 3891–3907.
- 115. Mohamed Elshrkawey, Samiha M. Elsherif, and M. Elsayed Wahed (2018). An enhancement approach for reducing the energy consumption in wireless sensor networks, Journal of King Saud University - Computer and Information Sciences, 30(2), 259–267.
- 116. Natasha Ramluckun and Vandana Bassoo (2018). Energy-efficient chain-cluster based intelligent routing technique for wireless sensor networks, Applied Computing and Informatics. doi: 10.1016/j.aci.2018.02.004.
