

A system of insight for digital business
We started this book by reviewing current IT infrastructure deployments and the most pressing problems that they present, and the need to better align IT with business requirements. In this chapter, we further explore how the z13 can help establish an infrastructure that matters, with improved ability to rapidly respond to business needs: agile, flexible, resilient, and secure.
This chapter describes the following topics:
5.1 Integrated hybrid infrastructures
IBM z Systems has long been an integrated diverse platform, with specialized hardware, and dedicated computing capabilities. Recall, for instance, in the mid-1980s, the IBM 3090, and its vector facility (occupying a separate frame). Or note that the cryptographic processors and all the I/O cards, which are specialized dedicated hardware, run non z Systems code on specialty processors. This design allows z Systems processor units (PUs) to concentrate on application’s computational tasks, while specialized processors take care of the other tasks, thus providing more value for the money through lower cost of effective computation of application data,
All of these specialized hardware components have been seamlessly integrated within the mainframe for over a decade. IBM extended, where possible, the same integration and simplification philosophy to other servers outside of the mainframe platform, creating a logical environment of shared resources capable of handling diverse workloads.
It might seem that increased flexibility inevitably leads to increased complexity. However, it does not need to be that way. IT operational simplification greatly benefits from the z13 intrinsic autonomic characteristics and the ability to consolidate and reduce the number of system images. There are also benefits from management best practices and products that were developed and are available for the mainframe, in particular for the z/OS and Linux on z Systems environments.
5.1.1 A cornerstone of a smart IT infrastructure
An important point is that the z Systems stack consists of much more than just a system. This claim can be made because of the total systems view that guides z Systems development. The z Systems stack is built around services, systems management, software, and storage. It delivers a complete range of policy-driven functions, pioneered and most advanced in the z/OS environment. It includes the following functions:
•Access management: Authenticates and authorizes who can access specific business services and associated IT resources.
•Use-management: Drives maximum utilization of the system. Unlike other classes of servers, z Systems are designed to run at 100% utilization all the time, which is based on the varied demands of its users.
•Availability: Clustering can be used to achieve 99,999% availability at the application level (often referred to as the “five nines”).
•Just-in-time capacity: Delivers more processing power and capacity when needed.
•Virtualization security: Enables clients to allocate resources on demand without fear of security risks.
•Enterprise-wide operational management and automation: Leads to a more autonomic environment.
IBM z13 is the result of the IBM sustained and continuous investment and development policies. Commitment to IBM systems design means that z13 brings all this innovation while helping clients to optimize their current investment in the mainframe and improve the economics of IT.
A number of enterprises are reaching the limits of available physical space and electrical power at their data centers. The extreme virtualization capabilities of the z13 enable the creation of dense and simplified infrastructures that are highly secure and can lower operational costs. They are, therefore, the most powerful tools available to reduce cost (including cost of energy) and complexity in enterprise data centers.
Further simplification is possible by using the HiperSockets1 and z/VM virtual switch functions. These functions can be used, at no additional cost, to replace physical routers, switches, and their cables, while eliminating security exposures and simplifying configuration and administration tasks. In actual simplification cases, measured at customer sites, cables were reduced by 97%
In the following sections, we describe how these capabilities play a key role in cloud computing. The following capacity range and flexibility features and benefits translate into a flexible infrastructure that is based on an integrated heterogeneous environment, on which a wide range of workloads can be seamlessly deployed and managed:
•A processor equally able to handle compute-intensive and I/O-intensive workloads
•Specialty engines for improved price/performance
•Extreme virtualization
•Secure access to data (and the network)
•Additional platforms and the Unified Resource Manager
5.2 Benefiting from a smart infrastructure
When distilled to a single central theme, embracing a heterogeneous infrastructure and creating an ensemble has the single objective of providing an optimized infrastructure.
In this smart infrastructure, multiple workloads can be deployed across heterogeneous environments and managed under a common umbrella. The computing resources of different hardware platforms are managed as a single view with these characteristics
•Tuned for the task and optimized across the infrastructure
•Managed end-to-end for flexible delivery of high value services, in a cloud-like manner
•Designed for enterprise-wide real-time data modeling
Adopting this smarter infrastructure and extracting benefit from it can be done gradually, and does not require disruptive moves such as those popularized under the names lift and shift and rip and replace. In the IBM solution, protection of the client’s investment in all IT aspects is maximized.
The IT infrastructures of clients are all unique, differing in areas such as virtualization, monitoring, and automation. A single approach does not fit all; there are multiple points of entry to the adoption of an integrated, heterogeneous, virtualized infrastructure.
Figure 5-1 shows a simplified view of a progressive adoption process, where building blocks are added to achieve an enterprise class infrastructure for heterogeneous workload deployment. Again, notice a resemblance with cloud computing.
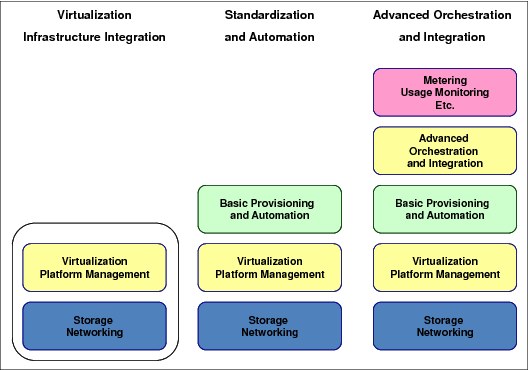
Figure 5-1 Enterprise class heterogeneous platform deployment building blocks
Workloads
Successfully deploying workloads across such an infrastructure requires not only knowledge of application requirements and behavior, but also might affect the enterprise’s operational procedures and methodologies, and even the organization.
Understand the terms application and workload:
Application A computer program or a set of computer programs that are dedicated to perform a defined computational work.
Workload An application (load) runs on a computer to perform a set of functions (work), and requires computing resources to perform these functions.
Workloads require computing resources, which can be classified as the following functions:
•CPU
•Memory
•I/O (networking, storage, and other devices; for instance, graphics devices)
I/O handling also uses a certain amount of CPU and memory resources, but the functions are highly specialized for the type of actions (I/O) that are performed.
Each application function requires a certain amount of the previously mentioned resources. In principle, every type of computer, regardless of the architecture employed (for instance, z Systems, IBM POWER, or System x) provides the three types of resources and can (also in principle) perform the same tasks. Thus, a workload is the work that is performed that uses a certain amount of computing resources to run the functions of an application.
Each application has a specific workload profile that is determined by the type resources needed computational (CPU, memory) or data movement (I/O) and their variation with time. Throughout the evolution of computing platforms, applications have been developed to use the platform characteristic features (CPU, memory, I/O). Historically, in certain cases, a platform is changed or adapted to better suit the application needs. An example might be the continuous evolution of the z Systems platform and the design of the reduced instruction-set computer (RISC) architecture.
The two basic types of application-required resources result from the two most important performance objectives:
•Response time: The ability to return results in a specified time
•Throughput: The amount of data that can be processed in a specified time interval
In addition, data and service reliability have driven the evolution of platforms by adding specific mechanisms and tools to achieve the desired results. These characteristics are the measurable parameters enabling the establishment of a service level agreement (SLA).
Platform design is improved to serve application requirements more effectively and safely. Thus, specialized engines that do specific tasks have been developed. Such examples include (but are not limited to) the following features:
•I/O coprocessors, which are designed to offload the main processors from the I/O-related tasks
•Specialized cryptographic co-processors, which are designed to offload the computational intensive mathematical functions required to encrypt and decrypt data
•Specialized co-processors for accelerating compressing and decompressing of data
•Specialized units inside the processor core, such as the binary-coded decimal (BCD) arithmetic logic unit or vector units
•Special purpose units, such as the IBM DB2 Analytics Accelerator, for accelerating complex queries such as those in data warehousing workloads
These improvements have been driven by the necessity of reserving the CPU execution capabilities for the core work of the application (main data computation). The diversity of the business needs and platforms also has determined two approaches for application design:
•Custom code
•Commercial off the shelf (COTS) code
Across industries, we see various applications with their specific workload profiles that run on various platforms. Historically, the choice of a platform has been determined by two major aspects:
•Platform availability (development costs always must consider this aspect)
•Platform fit-for-the-purpose
The use of programming tools, such as compilers, has greatly contributed to application portability (the ability to run on several platforms). However, because of the diversity of application workload profiles, not all platforms can run the same workload with the same efficiency.
Moreover, depending on the industry and business requirements, an application that might perform the same core functionality, might have more non-functional requirements. Examples include specific data security and availability, that cannot be obtained in a cost-effective manner on all available platforms.
Examples are as follows:
•In banking, there are components across retail and wholesale banking that employ several architectures to run, but the core of most banking applications relies on z Systems and z/OS.
•Insurance typically maintains claims processing on z Systems but reaches out to the Internet for interaction with consumers, using Linux, UNIX, Power, and x86. Fraud detection can benefit from exploiting the vast amounts of data managed by z Systems, using z Systems based computing.
•The public sector is relying more on the web-based capability to reach out to citizens and improve the rate of return for taxes, accurate payment of social benefits, election process, and even census-based reporting. Here, too, fraud detection and tax evasion can benefit from the capabilities of z Systems.
•The retail industry can effectively use a heterogeneous infrastructure (for instance, by benefiting from large I/O capacity of z Systems to implement large databases, using business intelligence to characterize a company’s clients).
•Airline reservation systems are one example of extreme online transaction processing. IBM z13 provides the z/TPF operating system and application environment specifically for this situation. Another example of z/TPF utilization is in banking with credit card and ATM processing.
The workloads tend to follow well-established technology and infrastructure patterns, such as the following applications:
•Core applications (for example, database engines)
•Multitier web serving
•Data warehouse/data mining
Attributes of workload components
Each workload pattern is typically made up of components that have distinct characteristics and requirements. The components are woven together with application programs and middleware to enable a business process to achieve business objectives.
Based on the workload attributes (characteristics), we can identify the following main types:
•Transaction processing and database (OLTP):
– High transaction rates
– High quality of service
– Peak workloads
– Resiliency and security
•Analytics and high performance:
– Compute or I/O intensive
– High memory bandwidth
– Floating point and vector processing (SIMD2)
– Scale-out capable (horizontal scalability)
•Business applications:
– Scale up (vertical scalability)
– High quality of service
– Large memory footprint
– Responsive infrastructure
•Web, collaboration, and infrastructure management:
– Highly threaded (SMT3)
– Throughput-oriented
– Scale out capable
– Lower quality of service
From an architectural perspective, it is critical to deploy workload components on the server technology that offers the best fit and is most effective in satisfying their requirements. Thus, multiple platforms might be appropriate. In a more synthetic approach, the workloads might be characterized as the following types:
•Shared data and multiple work queues (OLTP, for example, or large batch jobs)
•Parallel data structures (HPC and Analytics)
•Highly threaded (for example, business applications)
•Small discrete applications
In addition, today’s applications can rarely be classified as only one of those types. See Figure 5-2 on page 142. In most cases, an application consists of components with varying requirements and workload profiles. Thus, proper platform choice is key in obtaining the results (SLA) that you want.
For example, a monothread batch job requires fast movement of data through the processor, and does not, of itself, use any multi-threading capabilities that a platform might have. Thus, the higher the CPU speed, the faster the job is processed. Conversely, a highly threaded application (web services, for example) performs better on a multi-threaded capable platform.
With z13, and in addition to the advanced workload management capabilities of z/OS, the IBM z Unified Resource Manager also offers workload management capabilities of zBX environments:
•For virtual servers on POWER7 blades, through the PowerVM hypervisor.
•For System x in the zBX, by using a function in the KVM hypervisor, known as cgroups. This allows monitoring the availability of workload resources to satisfy a defined workload service level policy. The Unified Resource Manager will use cgroups by assigning cgroup to virtual servers and dynamically managing the CPU share of a virtual server based on policy goals.
Figure 5-2 shows an image of workload characterization.
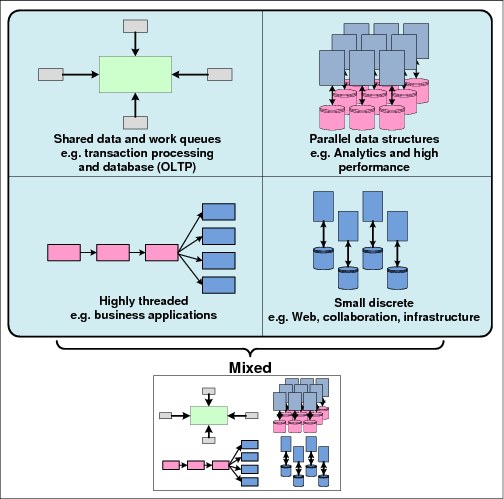
Figure 5-2 Workload characterization
The z13 is the platform of choice for the integration of the new generations of applications with existing applications and data. They truly are cornerstones of a smart IT infrastructure.
5.3 Cloud, analytics, mobile, social, and security
IBM mainframes traditionally provide an advanced combination of reliability, availability, security, scalability, and virtualization. The IBM z13 extends these capabilities into heterogeneous resources and are optimized for today’s business needs. The IBM z13 continues the evolution of the mainframe, building upon the z/Architecture definitions as the mainframe system that is optimized for the digital era.
IBM z13 is an integrated, highly scalable computer system. It allows many different pieces of work to be handled at the same time, sharing the same information as needed, with protection, and handling very large amounts of information for many users, with security, and without users experiencing any failures in service.
The IBM z13 is emerging as a choice platform for cloud computing. Cloud technologies can improve the integration of people, processes, and technology to help businesses run more cost effectively while also supporting business growth and innovation. Cloud is the infrastructure model of the digital era, and z13 provides the infrastructure to support all dimensions of cloud service deliveries. z/OS and Linux on z Systems are the foundations of the most secure and scalable private, public, and hybrid cloud infrastructures.
The z13 is the trusted enterprise platform for integrating data, transactions, and insights. Enterprises typically use traditional integer, floating point, string, and XML character-based data. The amount of data is increasing exponentially, and IT shops need to respond quickly to the diversity of data. Therefore, an aspect that is becoming more important is for customers to do computations and analytics closer to the data. The z13 supports new analytics workloads and offers new and improved capabilities for mathematical optimization of complex models for deeper analytics insights. For the last three generations, z Systems has changed its capabilities in analytics compute processing, such as superscalar, out of order, compiler improvements and precision floating point. Single-instruction, multiple-data (SIMD), simultaneous multithreading (SMT), and large memory provide the next phase of enhancements to business and IT analytics transaction processing and compute-intensive competitiveness on z Systems.
The z13 continues to reinvent enterprise IT for digital business. The mobile revolution is changing how people interact and organizations are transforming their business processes to address an increasing demand for mobile capabilities in a dynamic and agile marketplace. The z13 is designed and enabled for a mobile generation. High performance, large-scale, and intelligent I/O and security enhancements on the z13 support transaction growth in the mobile world. New technologies that improve throughput and response time enable organizations to provide rapid data and transaction service to their customers.
The z13 system enables the integration of social technology throughout business processes. Organizations are incorporating social media platforms and realizing value in connecting employees, suppliers, and customers. In a global marketplace, virtual interactions can lead to more efficient and effective results. Communications can be accelerated as teams worldwide become more connected with enterprise collaboration tools, independent of time zones. Software such as IBM Connections and IBM Sametime® are components of the IBM Platform for Social Business, the industry’s most comprehensive portfolio to support social technology.
The z13 offers the highest level of security certification for commercial server applications. As the world continues to become more digitized and interconnected, doors to emerging security threats and vulnerabilities continue to open. Cybersecurity attacks have become more sophisticated, with new motivations, and increasing speed and dexterity. The z13 offers the most secure and reliable computing platform through auditable protection of data, simplification of management and compliance, and capability for security analytics. The security strategy is to combine processor-based cryptography and encryption, with firmware and operating system enhancements, to ensure no attack vectors are exploited to compromise the security and integrity of the system.
5.3.1 Cloud computing
“Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction.”4 A cloud can be public, private, or a hybrid of both. With cloud computing, the application can be running on a server anywhere in the world. That flexibility is why it is changing the way companies provide services to their clients and suppliers.
Figure 5-3 shows the IBM Cloud Computing Reference Architecture (CCRA5), which defines the fundamental architectural elements that constitute a cloud computing environment. A requirement is that all of these infrastructure components be managed from a single, central Common Cloud Management Platform with the ability to place instances of each cloud service on the corresponding infrastructure. This requirement perfectly fits the z13 based heterogeneous infrastructure, with its end-to-end management capabilities for flexible delivery of high-value services.
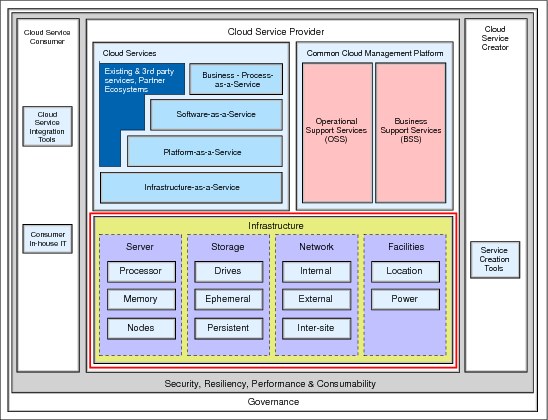
Figure 5-3 The IBM Cloud Computing Reference Architecture infrastructure details
Virtualization is the foundation for cloud, and the benefits of consolidation and virtualization are widely accepted by the IT community. Adding standardization and automation to a virtualized environment enables IT optimization for cloud computing. Workflow orchestration, monitoring, and metering for accounting are other major components of cloud computing.
Deploying a cloud infrastructure is not a simple process, but there is a defined path that can be followed. Figure 5-4 depicts the path from standard managed services to cloud.
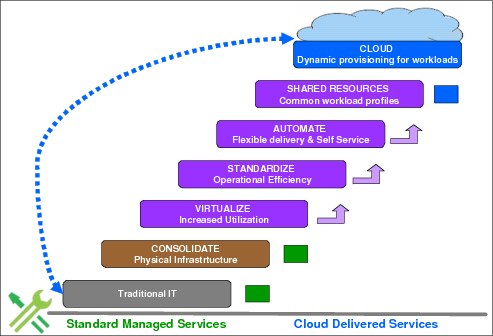
Figure 5-4 Cloud delivered services
Because z13, with its “shared everything infrastructure,” offers a fully virtualized system, integrating a cloud computing deployment as part of the existing IT optimization strategy and roadmap becomes easier. Table 5-1 summarizes potential benefits of cloud computing.
Table 5-1 Benefits with cloud computing
|
Virtualization
|
Standardization
|
Automation
|
|
Higher utilization
Economy-of-scale benefits
Lower capital expense
Lower operating expense
|
Easier access
Flexible pricing
Reuse and sharing
Easier integration
|
Faster cycle times
Lower support costs
Optimized utilization
Improved compliance
Optimized security
Better user experience
|
Cloud computing on z13 builds on the industry’s leading virtualization technology that uses virtualization, standardization, and automation to free operational budget for new investments. This technology also allows you to optimize new investments for direct business benefits. IBM z13 provides the following features:
•A highly scalable heterogeneous pool of virtualized resources that are managed in a single system
•On-demand activation, allocation, prioritization, and retiring of resources, and automation of service delivery
•Maximizing utilization of resources for improved return on investment (ROI) and lower cost of service delivery
•Increased levels of security, resiliency, and manageability to create a cloud environment that is enterprise ready
•More processing capacity, multithreading, and larger memory to consolidate different applications with less physical infrastructure.
Building upon all the previous resource management capabilities and core functionality, application-supporting middleware, such as transactional servers, add function to enable existing applications to become cloud accessible, without the need to rewrite and replace them. True to IBM commitment, and similarly to web enablement, applications can become naturally immersed in the cloud, while preserving the client’s investment.
|
CICS Transaction Server support for cloud computing: CICS Transaction Server for z/OS V5.1 provides new application, platform, and policy capabilities that can help clients build private clouds from new and existing CICS applications. This capability is intended to assist CICS clients to deploy new and updated CICS applications faster, more easily, and with greater levels of confidence.
|
The IBM z13 (Figure 5-5 on page 147) enables the following attributes, being the IT industry’s first multi-architecture cloud solution:
•Higher utilization:
– Up to 100% CPU utilization
– Shared everything architecture
– Hosting of thousands of mixed workloads
– Multithreading capability
•Increased productivity:
– Single point of control for a heterogeneous infrastructure at a platform level,
with the Unified Resource Manager
with the Unified Resource Manager
– Efficient, rapid provisioning
– Superior workload management that is enabled with Unified Resource Manager
– Workload optimization with fit for purpose approach
– Collocating applications where industry-leading z/OS transaction and data services run
•More efficient data center:
– Less power and cooling
– Less floor space
– Fewer parts to manage
•Greater reliability and availability:
– Built-in hardware redundancy
– Decades of RAS innovation
– Capacity and backup on demand
– Decades-proven virtualization security protecting sensitive data and critical business processes in the cloud
– Resiliency management and fewer points of failure
•Security:
– Extending z Systems security to a private network across heterogeneous resources
Figure 5-5 shows a z13 for IT optimization, consolidation, and cloud computing.

Figure 5-5 z13 for IT optimization, consolidation, and cloud computing
Quality of service improvements
In an ensemble (Figure 5-5), the qualities for which z Systems are renowned are extended to the non z Systems components of the ensemble, providing support for mission-critical workloads running on the ensemble’s heterogeneous infrastructure. Compared to other heterogeneous infrastructures, the ensemble provides the following benefits:
•Potentially lower the cost of enterprise computing by implementing a single management and policy framework across web serving, transaction, database, and servers
•Simplified operations through integration of multiplatform management capabilities through extended functionality in the well-known mainframe HMC
•Improved infrastructure reliability by extending the mainframe systems management and service to the zBX environment
•Improved service through dynamic resource management of the mainframe to all devices within a multitier architecture
•Simplified and improved infrastructure management through monitoring and management of a heterogeneous solution as a single, logical virtualized solution
•Better alignment of IT with business objectives by managing the platform’s resources in accordance with specified business-service-level objectives
•Improved infrastructure manageability through management of virtual servers as part of the overall deployed business workload
•Dramatically simplified infrastructure, improved application performance, and simplified management by using IEDN, the secure and managed Layer 2 network that connects the zBX blades with the CPC
Cloud computing is one of the key ways to address the challenges of today and build an IBM Smarter Planet®. As more companies embrace cloud computing, z13 becomes the perfect platform for delivering large-scale software as a service (SaaS) application software services.
For more information about cloud on z Systems, see Deploying a Cloud on IBM System z, REDP-4711.
GDPS Virtual Appliance
|
Statement of General Direction1: In the first half of 2015, IBM intends to deliver a GDPS/Peer to Peer Remote Copy (GDPS/PPRC) multiplatform resiliency capability for customers who do not run the z/OS operating system in their environment. This solution is intended to provide IBM z Systems customers who run z/VM and their associated guests, for instance, Linux on z Systems, with similar high availability and disaster recovery benefits to those who run on z/OS. This solution will be applicable for any IBM z Systems announced after and including the zBC12 and zEC12.
|
1 All statements regarding IBM plans, directions, and intent are subject to change or withdrawal without notice. Any reliance on these statements of general direction is at the relying party’s sole risk and will not create liability or obligation for IBM.
Deploying IT environments, based on z Systems that are running only Linux on z Systems is common today. The GDPS Virtual Appliance is a building block of high availability and disaster recover solutions for those environments that do not have nor require z/OS skills.
To reduce IT costs and complexity, many enterprises are consolidating independent servers into Linux images (guests) running on a z Systems platform. Linux on z Systems can be implemented either as guests running under z/VM or native Linux LPARs on z Systems. Workloads with an application server running on Linux on z Systems and a database server running on z/OS are common. Two examples are as follows:
•WebSphere Application Server running on Linux and CICS, DB2 running under z/OS
•SAP application servers running on Linux and database servers running on z/OS
With a multitiered architecture, there is a need to provide a coordinated near-continuous availability and disaster recovery solution for both z/OS and Linux on z Systems.
GDPS Virtual Appliance is a fully integrated continuous availability and disaster recovery solution for Linux on z Systems customers and consists of these items:
•An operating system image
•The application components
•An appliance management layer, which makes the image self-containing
•The APIs and UIs for customization, administration, and operation tailored for the appliance function
The GDPS Virtual Appliance can improve both consumability and time-to-value for customers. For more information, see IBM z13 Technical Guide, SG24-8251.
5.3.2 Analytics on IBM z13
Analytics projects mainly draw on mainframe-based transactional data. However, in the last two decades, analytics solutions have been deployed as departmental applications, based on specific business needs of the requesting department.
Although most source data that is fed into the analytics applications is common (shared among various solutions), the results are often not correlated, because they reside in diverse systems and formats (silos).
What seemed initially like a small investment (at individual server and application levels) has evolved into a significant investment when viewed in the aggregate. With many organizations concerned about costs (hardware, software, energy, and labor) and real estate availability (data center), maintaining such a diverse infrastructure can become a mess.
In addition, after the applications follow their lifecycles (design, development and testing, quality assurance, production, disaster recovery), return on investment in the associated infrastructure becomes difficult to evaluate and control.
Data is the most important resource of our clients. The way our clients view and analyze the data increases their competitive advantage:
•Real-time view: the operational systems that house the books of record. These data sources are critical to day-to-day business processes (systems of record).
•Historical view: Data warehouses, marts, and others. These data sources support reporting and predictive model creation.
•Predictive view: Analytics models and software. These are the tools that deliver actionable insights from data.
Business-critical analytics solutions depend on where the source data resides. IBM z Systems servers delivers a single workload-optimized system for both operations and analytics by integrating and managing real-time, historical and predictive views of data.
Real-time analytics-based decisions is a top priority for outperforming organizations, and this requires tight integration with operational data. The following problems are usually encountered when implementing analytics solutions in a silo manner:
•Significant effort is spent for copying and moving data, resulting in veracity and security issues.
•Business does not have access to the most current view (data in systems of record is in constant change).
•Complicated, bifurcated infrastructure requires multiple skill types.
•No single point of management is available.
•Business continuity concerns are an issue.
With keeping data and analyzing it at the source, several advantages can be identified:
•Less movement of data, resulting in higher quality and less risk of loss
•Integration with core systems delivers most accurate view to the business
•Integrated architecture leveraging existing environment
•Single view simplifies management
•Business continuity inherited from core systems
z Systems analytics enables organizations to improve performance and lower cost by bringing the analytic processing to where the data is located (see Figure 5-6 on page 150). Organizations can maximize their current IT investments while adding more functionality, and improved price-performance advantages with z13 over zEC12. With new z13 features, applications can gain increased throughput for distributed operational business intelligence (operational BI), DB2 query workloads, thus saving money (hardware, software, labor).

Figure 5-6 IBM z Systems transaction and analytic processing (hybrid)
By keeping (big) data and analytics applications in the z Systems ecosystem, customers can achieve better information governance while saving money to safeguard data and applications. The following aspects set z Systems apart for information governance:
•Co-location of transactional data and historical data
•Minimizes duplicate copies of the data
•Fewer security intrusion points
•Scalability to leverage a single, consistent copy of the data
•Consistent business rules across the enterprise
IBM z Systems can help achieve the best-in-class consistency of security controls across the data:
•Enterprise-wide security, auditing and compliance
•Real-time monitoring and alerting
•User identification and authentication at all levels
•Access defined down to the cell level
•End-to-end auditing
•Data is secured with cryptography, encryption
In the context of analytics, these features and functions of z13 bring benefit to workloads:
•SIMD: MASS and ATLAS libraries, for z/OS and Linux on z Systems:
– Allow construction of richer, complex analytics models using ISV or IBM software analytics products that exploit SIMD to provide better accuracy of insight
– Allow analytics workloads to be ported from Power Systems and x86 with ease that can accelerate analytics to provide speedy business insight
– Increase programmer productivity of ISV and customer analytics workload development leading to rapid business insight generation for competitive advantage
•SMT: Process more workload in the same amount of time (zIIPs, IFLs)
•Enterprise security (built in, one-of-a-kind cryptographic and encryption functions) maintaining data secure, inside the platform
•Large memory support (z/OS, DB2)
Conclusion
IBM z Systems platform excels as custodian of the data model, providing accurate, secure single copy of information that ensures the veracity of the data for reliable analytics (see Figure 5-7).
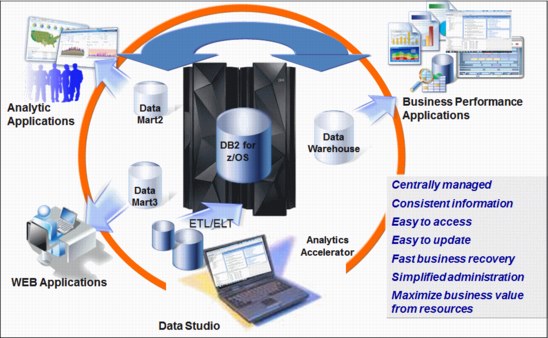
Figure 5-7 Centralized control of decision information
5.3.3 IBM z13 serving mobile and social applications
In today’s mobile era, over 10 billion devices access information. Enterprises are challenged with integrating new mobile services with existing organizational processes, without sacrificing the client’s experience. Figure 5-8 on page 152 depicts a typical environment where access to applications and interaction with the systems is achieved from mobile devices.

Figure 5-8 Typical mobile environment
IBM z Systems provide you with enterprise mobility solutions which can scale to handle the huge number of often unpredictable transaction rates and volumes, deliver proven mobile end-to-end integration with reliability, availability, and security, and ensure that your customer data is protected.
IBM is the leading platform in systems of record (z/OS). IBM provides easily consumable mobile access to all the data and transactions in z Systems software subsystems (DB2, CICS, IMS, MQ, and others). Customers can create engaging mobile apps today using existing transactions on z Systems. IBM flagship operating system z/OS availability and scalability is crucial for mobile workloads.
IBM is also a key player in systems of engagement (Linux on z Systems). Based on its availability and scalability, z Systems platform can handle mobile workloads. In this context, Linux on z Systems provides an excellent environment for mobile infrastructure. The diagram in Figure 5-9 on page 153 shows a typical deployment of IBM z Systems in a mobile application environment.
The following features benefit the development and running of mobile applications on
IBM z13:
IBM z13:
•SMT: IFLs and zIIPs with software support.
•SIMD: Accelerating computation for analytics.
•Large memory: Provides faster response time to Java and DB2 based applications (in general, any applications that can exploit large amount of in-memory data).
•Enterprise security capabilities: Can help you simplify and improve a complex set of operational security processes. IBM z Systems are designed for the highest level of security for commercial grade platforms.
•High performance communications (network and I/O): SMC-R, FICON Express16s, and so on.
IBM provides the tools to satisfy the lifecycle requirements for mobile application development, including, but not limited to these tools:
•IBM MobileFirst Studio (formerly IBM Worklight Studio) offers leading tools for mobile app development that help maximize code reuse and accelerate development.
•IBM MobileFirst Server6 (formerly IBM Worklight Server) is mobile-optimized middleware that serves as a gateway between applications, back-end systems and cloud-based services.
The IBM MobileFirst Platform provides the following benefits:
•Exploit z Systems platform security and encryption for use by mobile apps.
•Exploit co-location with z/OS data and transactions.
•Easily create new mobile development and production clouds.

Figure 5-9 Mobile applications on IBM z Systems
IBM z Systems address key mobile development and delivery challenges, such as these:
•Fragmentation and developing for multiple mobile platforms:
A highly fragmented set of devices, platforms, languages, and tools complicates development, test, and operations.
IBM response is IBM MobileFirst Studio and IBM Rational Developer for z:
– Seamless integration with z Systems data and transactions.
– Device run time provides mobile device independence.
•Accelerated time to market requirements:
– Accelerated development demands instant provisioning of development servers.
– Spikey mobile traffic demands highly scalable cloud-based infrastructures.
IBM response is cloud offerings:
– Linux on z Systems enables rapid provisioning of dev servers.
– High scalability can handle workload increases
•Connecting apps with existing enterprise systems:
– Apps typically need to leverage existing enterprise services, which must be made mobile-consumable, and remain secure.
– Enterprise systems must be able to instantly provision new services and environments.
IBM response is that z/OS is mobile enabled:
– All z/OS subsystems are mobile-ready, with added consumability enhancements planed.
– DB2 tech preview: MongoDB7 API.
– End to end mobile security.
– High-performance access from Linux on z Systems.
Social
While mobile applications enable customer engagement anytime, anywhere, the huge volume of data generated can also be fed into analytics applications that provide business decisions with the social perspective. Add real-time scoring to your OLTP workload with minimal impact on CPU consumption and response time. z Systems answer this call, drastically reducing analytic latency through in-database scoring combined with support for IBM DB2 Analytics Accelerator (IDAA) based modeling. Real-time scoring (real-time IBM SPSS® scoring in DB2 for z/OS) allows organizations to take next best action within the transaction with minimal CPU impact. Some of the applications that involve social aspects are as follows:
•Social Media Analytics
•Customer sentiment
•Customer identification
•Identification of illegal or suspicious actives
•Employee and customer experiences
Social behavior analysis provides another perspective to business, enhancing business decisions with prediction of future trends and the capability of detecting errors before they may actually occur (fraud detection is one example).
Several examples of applications are as follows:
•IBM SPSS software (Statistical Package for the Social Sciences)
•IBM Employee Experience Suite for Linux on z Systems
•IBM Connections
Conclusion
The role of z Systems in the mobile and social environments can be summarized as follows:
•Build an agile approach to deliver applications.
•Make every transaction secure.
•Use mobile analytics to improve outcomes at every moment.
5.3.4 Security on IBM z13
Analytics, mobile, social, and cloud all have one aspect in common: the need for a platform that has a deeply integrated security stack. This is where IBM z Systems excel. With the threats to business in the current world, including everything from hackers looking to see what they can do, to government backed attacks, IBM z Systems offer a platform with layers of defense to protect your customer data, intellectual property, and your reputation.
This infrastructure is the basis for a platform ideal to support today’s cloud, mobile, analytics, and social networking workloads. With the holistic approach to security, IBM z Systems provide the security foundation for cloud, analytics, mobile, and social applications, as shown in Figure 5-10.
Figure 5-10 Cloud, analytics, mobile, and social, underpinned by security
When the IBM System 360 was first introduced, it had security built into the hardware and operating system with storage protection keys. IBM has continued to build upon the security with processor base encryption, LPAR isolation, operating system protections, network and secure communications, and self-encrypting tape and disk storage solutions. For more information about how to configure and secure operations on a mainframe, see Security on the IBM Mainframe: Volume 1 A Holistic Approach to Reduce Risk and Improve Security, SG24-7803-01.
IBM Security Framework
These matters of business-driven enterprise security are encapsulated in a concept known as the IBM Security Framework. The IBM Security Framework (Figure 5-11 on page 156) provides a business view of the security posture of an enterprise. Although it is a high level view, it incorporates all that is necessary for consideration. IBM Security Framework can help with these items:
•Enable innovation through security-rich, end-to-end infrastructure and platforms.
•Reduce number and complexity of required security controls.
•Reduce redundant security expenses.
•Improve organizational and operational agility and resiliency.
•Leverage industry expertise to help unify policy management.
•Deliver needed visibility, control, and automation.

Figure 5-11 IBM Security Framework
The security landscape has grown substantially more complex. The evolution of a highly networked, data-intensive computing model has introduced significant security risks to IT infrastructures. Greater interconnectivity and system concentration exacerbates the likelihood of cascading system failures. And, the increasing prevalence of social, mobile, virtualization, and cloud technologies present a profound security challenge.
This increased cost and complexity make traditional data security practices obsolete. More sophisticated threats and higher risk are driving the need for more responsive, context-aware approaches to data security management. To take advantage of new marketplace opportunities while minimizing risks, companies must proactively incorporate security as a business enabler.
The average security breach can cost $5.85M US dollars8 and the cost of protecting an enterprise is much more.
In addition to built-in security and cryptographic features and functions, one important aspect of securing your IT environment is to prevent and eliminate security risks. An important feature of a secure environment is to have the capabilities to analyze security-related data by using powerful analytics that help early detection of security and help predict a breach that is on the verge of happening. Analytics is also key to modern fraud detection and prevention methods.
Data and multitenancy security work together. Mobile security depends on access rules and endpoint protection. IBM z Systems have encryption and secured isolation; network security for the cloud is addressed too. Security for the Internet with SSL transactions and secure coprocessing is delivered with Crypto Express5S.
Today’s social networking generation is more likely to reveal personal data to other parties in venues like social networking sites. Abusing mobility has proven to be an effective means to spread malware. Social engineering through mobile apps puts users and companies they work for in danger.
Many mobile phone makers do not rapidly deploy software patches to devices; malicious apps are often distributed through third-party app markets. Another troubling trend is that some mobile malware can collect a user’s personal information for use in phishing attacks. Mobile attacks are potentially providing an entry into corporate assets.
To effectively detect and prevent security breaches, security intelligence and powerful analytics must be implemented. Such capabilities are provided by IBM InfoSphere® BigInsights™ and IBM Security QRadar®, which also take advantage of traditional mainframe security and the capabilities of IBM z13, such as these examples:
•CPACF and Crypto Express5s
CPACF is designed to improve performance for cryptographic functions. The optional Cryptographic Coprocessor adapter (Crypto Express5) provides new virtualization capabilities and performance increase.
•SIMD allows construction of richer, complex analytics models that use SIMD to provide better accuracy of insight:
– Allows analytics workloads to be ported from IBM Power and x86 with ease and can accelerate analytics to provide speedy business insight.
– Increases programmer productivity of ISV and customer analytics workload development, leading to rapid business insight generation for a competitive advantage.
•SMT: Process more workload (throughput for IFLs).
InfoSphere BigInsights empowers enterprises of all sizes to cost effectively manage and analyze big data: the massive volume, variety, and velocity of data that consumers and businesses create every day. InfoSphere BigInsights helps increase operational efficiency by modernizing your data warehouse environment as a queryable archive, allowing you to store and analyze large volumes of multi-structured data without straining the data warehouse.
IBM QRadar Security Intelligence Platform products provide a unified architecture for integrating security information and event management (SIEM), log management, anomaly detection, incident forensics and configuration and vulnerability management. These products offer advanced threat detection, greater ease of use and lower total cost of ownership.
IBM QRadar Security Intelligence Platform products deliver these features:
•A single architecture for analyzing log, flow, vulnerability, user and asset data
•Near real-time correlation and behavioral anomaly detection to identify high-risk threats
•High-priority incident detection among billions of data points
•Full visibility into network, application and user activity
•Automated regulatory compliance with collection, correlation and reporting capabilities
Conclusion
The IBM Security Framework and the IBM Security Blue are tools to enable the security architect to understand the components and facilities needed to design a secure solution. These tools are useful for all platforms and can be applied to systems hosted on IBM z Systems and to applications which span multiple heterogeneous hardware and software platforms.
1 For a description of HiperSockets, see “HiperSockets” on page 85. The z/VM virtual switch is a z/VM system function that uses memory to emulate network switching hardware.
2 Single-instruction, multiple-data (SIMD): Same instruction that is run on a vector of data
3 Simultaneous multithreading (SMT): More than one thread runs simultaneously in the same processor
4 US National Institute of Standards and Technology: http://csrc.nist.gov/groups/SNS/cloud-computing/index.html
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
