
Appendix B: Risk assessment and management
This appendix contains basic information about several broadly known and used approaches to the assessment and management of risk. It is not intended to be a comprehensive study of the subject, but rather to provide an awareness of some of the methods in use.
B.1 DEFINITION OF RISK AND RISK MANAGEMENT
Risk may be defined as uncertainty of outcome, whether a positive opportunity or negative threat. It is the fact that there is uncertainty that creates the need for attention and formal management of risk. After all, if an organization were absolutely certain that a negative threat would materialize, there would be little difficulty in determining an appropriate course of action. Likewise, if an organization could be guaranteed that the positive opportunity would be realized, then its path would be clear. Managing risks requires the identification and control of the exposure to those risks which may have an impact on the achievement of an organization’s business objectives.
Every organization manages its risk, but not always in a way that is visible, repeatable and consistently applied to support decision-making. The purpose of formal risk management is to enable better decision-making based on a sound understanding of risks and their likely impact on the achievement of objectives. An organization can gain this understanding by ensuring that it makes cost-effective use of a risk framework that has a series of well-defined steps. Decision-making should include determining any appropriate actions to take to manage the risks to a level deemed to be acceptable by the organization.
A number of different methodologies, standards and frameworks have been developed for risk management. Some focus more on generic techniques widely applicable to different levels and needs, while others are specifically concerned with risk management relating to important assets used by the organization in the pursuit of its objectives. Each organization should determine the approach to risk management that is best suited to its needs and circumstances, and it is possible that the approach adopted will leverage the ideas reflected in more than one of the recognized standards and/or frameworks.
In this appendix the following approaches to managing risks are briefly explained:
![]() Management of Risk (M_o_R)
Management of Risk (M_o_R)
![]() ISO 31000
ISO 31000
![]() ISO/IEC 27001
ISO/IEC 27001
![]() Risk IT.
Risk IT.
B.2 MANAGEMENT OF RISK (M_O_R)
Management of Risk (M_o_R) is intended to help organizations put in place an effective framework for risk management. This will help them take informed decisions about the risks that affect their strategic, programme, project and operational objectives.
M_o_R provides a route map of risk management, bringing together principles, an approach, a process with a set of interrelated steps and pointers to more detailed sources of advice on risk management techniques and specialisms. It also provides advice on how these principles, approach and process should be embedded, reviewed and applied differently depending on the nature of the objectives at risk.
The M_o_R framework is illustrated in Figure B.1.
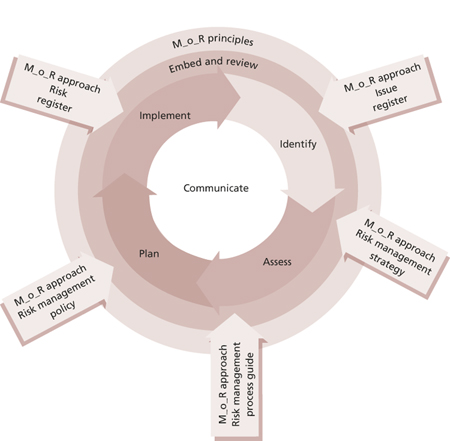
Figure B.1 The M_o_R framework
The M_o_R framework is based on four core concepts:
![]() M_o_R principles Principles are essential for the development and maintenance of good risk management practice. They are informed by corporate governance principles and the international standard for risk management, ISO 31000: 2009. They are high-level and universally applicable statements that provide guidance to organizations as they design an appropriate approach to risk management as part of their internal controls.
M_o_R principles Principles are essential for the development and maintenance of good risk management practice. They are informed by corporate governance principles and the international standard for risk management, ISO 31000: 2009. They are high-level and universally applicable statements that provide guidance to organizations as they design an appropriate approach to risk management as part of their internal controls.
![]() M_o_R approach Principles need to be adapted and adopted to suit each individual organization. An organization’s approach to the principles needs to be agreed and defined within a risk management policy, process guide and strategies.
M_o_R approach Principles need to be adapted and adopted to suit each individual organization. An organization’s approach to the principles needs to be agreed and defined within a risk management policy, process guide and strategies.
![]() M_o_R process The process is divided into four main steps: identify, assess, plan and implement. Each step describes the inputs, outputs, tasks and techniques involved to ensure that the overall process is effective.
M_o_R process The process is divided into four main steps: identify, assess, plan and implement. Each step describes the inputs, outputs, tasks and techniques involved to ensure that the overall process is effective.
![]() Embedding and reviewing M_o_R Having put in place an approach and process that satisfy the principles, an organization should ensure that they are consistently applied across the organization and that their application undergoes continual improvement in order for them to be effective.
Embedding and reviewing M_o_R Having put in place an approach and process that satisfy the principles, an organization should ensure that they are consistently applied across the organization and that their application undergoes continual improvement in order for them to be effective.
There are several common techniques which support risk management, including a summary risk profile. A summary risk profile is a graphical representation of information normally found in an existing risk register, and helps to increase the visibility of risks. For more information on summary risk profiles and other M_o_R techniques, see Management of Risk: Guidance for Practitioners (OGC, 2010).
B.3 ISO 31000
ISO 31000 was published in November 2009 and is the first set of international guidelines for risk management, intended to be applicable and adaptable for ‘any public, private or community enterprise, association, group or individual.’ ISO 31000 is a process-oriented rather than a control-oriented approach to risk management, and provides guidance on a broader, more conceptual basis, rather than specifying all aspects of an organization’s risk assessment and management approach. For example, ISO 31000 does not define how an organization will create risk data or measure risk, nor does it ensure that an organization will include a review of all risk areas relevant to the achievement of their objectives. ISO 31000 was published as a standard without certification.
ISO 31000 defines risk as ‘the effect of uncertainty on objectives’. Risk management should be performed within a framework that provides the foundations and provisions which will embed the management of risk throughout all levels of the organization. ISO 31000 identifies the necessary components of such a framework as:
![]() Mandate and commitment
Mandate and commitment
![]() Design of framework for managing risk
Design of framework for managing risk
![]() Understanding the organization and its context
Understanding the organization and its context
![]() Establishing risk management policy
Establishing risk management policy
![]() Accountability
Accountability
![]() Integration into organizational processes
Integration into organizational processes
![]() Resources
Resources
![]() Establishing internal communication and reporting mechanisms
Establishing internal communication and reporting mechanisms
![]() Establishing external communication and reporting mechanisms
Establishing external communication and reporting mechanisms
![]() Implementing risk management
Implementing risk management
![]() Monitoring and review of the framework
Monitoring and review of the framework
![]() Continual improvement of the framework.
Continual improvement of the framework.
Within this context the risk management process is seen at a high level in Figure B.2.

Figure B.2 ISO 31000 risk management process flow
Once the framework has been established and the context understood, risk assessment is undertaken. This consists of three steps: risk identification, risk analysis and risk evaluation. The risk identification step is intended to create a comprehensive list of risks based on those events that might create, enhance, prevent, degrade, accelerate or delay the achievement of the organization’s objectives. Risk analysis involves developing a full understanding of the risks as an input to risk evaluation and the decisions regarding the plan for treating the risks. Risk evaluation is to make decisions about which risks require treatment and the relative priorities amongst them.
Risk treatment involves the modification of risks using one or more approaches. These approaches are not necessarily mutually exclusive and may include:
![]() Avoiding the risk by deciding not to start or continue with the activity that gives rise to the risk
Avoiding the risk by deciding not to start or continue with the activity that gives rise to the risk
![]() Taking or increasing the risk in order to pursue an opportunity
Taking or increasing the risk in order to pursue an opportunity
![]() Removing the risk source
Removing the risk source
![]() Changing the likelihood
Changing the likelihood
![]() Changing the consequences
Changing the consequences
![]() Sharing the risk with another party or parties (including contracts and risk financing)
Sharing the risk with another party or parties (including contracts and risk financing)
![]() Retaining the risk by informed decision.
Retaining the risk by informed decision.
The approach described in ISO 31000 provides broad scope for each organization to adopt the high-level principles and adapt them to their specific needs and circumstances.
B.4 ISO/IEC 27001
ISO/IEC 27001 was published in October 2005 and is an information security management system (ISMS) standard which formally specifies a management system that is intended to bring information security under explicit management control. While ISO/IEC 27001 is a security standard, not a risk management standard, it mandates specific requirements for security, including requirements relating to risk management. The risk management methods described in this context may be applied to general risk management activities as well.
ISO/IEC 27001 requires that management:
![]() Systematically examines the organization's information security risks, taking account of the threats, vulnerabilities and impacts
Systematically examines the organization's information security risks, taking account of the threats, vulnerabilities and impacts
![]() Designs and implements a coherent and comprehensive suite of information security controls and/or other forms of risk treatment (such as risk avoidance or risk transfer) to address those risks that are deemed unacceptable
Designs and implements a coherent and comprehensive suite of information security controls and/or other forms of risk treatment (such as risk avoidance or risk transfer) to address those risks that are deemed unacceptable
![]() Adopts an overarching management process to ensure that the information security controls continue to meet the organization’s information security needs on an ongoing basis.
Adopts an overarching management process to ensure that the information security controls continue to meet the organization’s information security needs on an ongoing basis.
The key risk management-related steps described in ISO/IEC 27001 include:
![]() Define the risk assessment approach of the organization
Define the risk assessment approach of the organization
![]() Identify a risk assessment methodology that is suited to the ISMS, and the identified business information security, legal and regulatory requirements
Identify a risk assessment methodology that is suited to the ISMS, and the identified business information security, legal and regulatory requirements
![]() Develop criteria for accepting risks and identify acceptable levels of risk
Develop criteria for accepting risks and identify acceptable levels of risk
![]() Identify the risks
Identify the risks
![]() Identify the assets within the scope of the ISMS, and the owners of these assets
Identify the assets within the scope of the ISMS, and the owners of these assets
![]() Identify the threats to these assets
Identify the threats to these assets
![]() Identify the vulnerabilities that might be exploited by the threats
Identify the vulnerabilities that might be exploited by the threats
![]() Identify the impact that losses of confidentiality, integrity and availability may have on these assets
Identify the impact that losses of confidentiality, integrity and availability may have on these assets
![]() Analyse and evaluate the risks
Analyse and evaluate the risks
![]() Assess the business impacts on the organization that might result from security failures, taking into account the consequences of a loss of confidentiality, integrity or availability of the assets
Assess the business impacts on the organization that might result from security failures, taking into account the consequences of a loss of confidentiality, integrity or availability of the assets
![]() Assess the realistic likelihood of security failures occurring in the light of prevailing threats and vulnerabilities, and impacts associated with these assets, and the controls currently implemented
Assess the realistic likelihood of security failures occurring in the light of prevailing threats and vulnerabilities, and impacts associated with these assets, and the controls currently implemented
![]() Estimate the levels of risk
Estimate the levels of risk
![]() Determine whether the risks are acceptable or require treatment using the previously established criteria for accepting risks
Determine whether the risks are acceptable or require treatment using the previously established criteria for accepting risks
![]() Identify and evaluate options for the treatment of risks. Possible actions may include:
Identify and evaluate options for the treatment of risks. Possible actions may include:
![]() Applying appropriate controls
Applying appropriate controls
![]() Knowingly and objectively accepting risks, providing they clearly satisfy the organization’s policies and the criteria for accepting risks
Knowingly and objectively accepting risks, providing they clearly satisfy the organization’s policies and the criteria for accepting risks
![]() Avoiding risks
Avoiding risks
![]() Transferring the associated business risks to other parties, e.g. insurers, suppliers
Transferring the associated business risks to other parties, e.g. insurers, suppliers
![]() Select control objectives and controls for the treatment of risks
Select control objectives and controls for the treatment of risks
![]() Obtain management approval of the proposed residual risks
Obtain management approval of the proposed residual risks
![]() Obtain management authorization to implement and operate the ISMS.
Obtain management authorization to implement and operate the ISMS.
During the implementation and operation of the ISMS, a plan for risk treatment is formulated (identifying the appropriate management action, resources, responsibilities and priorities for managing information security risks) and implemented. ISO/IEC 27001 also calls for the ongoing monitoring and reviewing of the risks and risk treatment and the formal maintenance of the ISMS to ensure that the organization’s goals are met.
This approach is focused specifically on the assets involved in organizational information security, but the general principles can be applied to overall service provision.
B.5 RISK IT
Risk IT is part of the IT governance product portfolio of ISACA that provides a framework for effective governance and management of IT risk, based on a set of guiding principles. Risk IT is about IT risk, including business risk related to the use of IT. The publications in which Risk IT is documented include The Risk IT Framework (ISACA, 2009) and The Risk IT Practitioner Guide (ISACA, 2009) (available from www.isaca.org).
The key principles in Risk IT are that effective enterprise governance and management of IT risk:
![]() Always connect to the business objectives
Always connect to the business objectives
![]() Align the management of IT-related business risk with overall enterprise risk management
Align the management of IT-related business risk with overall enterprise risk management
![]() Balance the costs and benefits of managing IT risk
Balance the costs and benefits of managing IT risk
![]() Promote fair and open communication of IT risk
Promote fair and open communication of IT risk
![]() Establish the right tone from the top while defining and enforcing personal accountability for operating within acceptable and well-defined tolerance levels
Establish the right tone from the top while defining and enforcing personal accountability for operating within acceptable and well-defined tolerance levels
![]() Are continuous processes and part of daily activities.
Are continuous processes and part of daily activities.
The framework provides for three domains, each containing three processes, as shown in Figure B.3. The Risk IT Framework describes the key activities of each process, the responsibilities for the process, information flows between the processes and the performance management of each process.
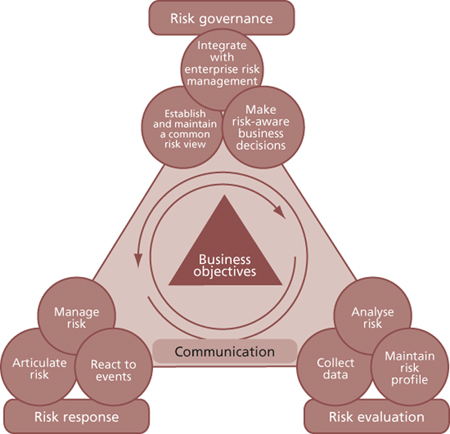
Figure B.3 ISACA Risk IT process framework
Risk governance ensures that IT risk management practices are embedded in the enterprise, enabling it to secure optimal risk-adjusted return. Risk evaluation ensures that IT-related risks and opportunities are identified, analysed and presented in business terms. Risk response ensures that IT-related risk issues, opportunities and events are addressed in a cost-effective manner and in line with business priorities.
