Delaying Technologies and Response Technologies
Abstract
This chapter contains information on Reactive Automated Protection Systems, deterrence technologies, deployable barriers, and prejudiced barriers and aggressive systems. The chapter completes with a section on integrating the elements.
REAPS technologies provide the designer with the ability to react to security events. REAPS technologies include intercoms, deployable barriers, and takedown technologies. Intercoms can often stop an attack and send the attacker on away.
Deployable barriers may include vehicle barriers, marine vessel barriers, and pedestrian barriers. Vehicle barriers are rated by their stopping power. They are assigned K and L ratings based on the weight of a vehicle they can stop and how far the vehicle may penetrate past the barrier. Vehicle barriers include rising bollards, rising wedges, semaphore parking gates, cable beams, box beam barriers, and net systems. Vehicle gates include swing gates and rolling doors and gates. Marine vessel barriers include anti-boat barriers and water monitors. Pedestrian barriers include intercoms, lighting, rolling grilles and operable walls, deployable doors, revolving doors, irrigation systems, and fog barriers.
Prejudiced barriers include quick setup and sticky foam barriers, drop chains, acoustic weaponry, high-voltage defense systems, remotely operated weaponry, and deluge systems. REAPS technologies should be carefully vetted for operational, legal, and safety standards.
Introduction
This chapter contains information on reactive automated protection systems (REAPS), deterrence technologies, deployable barriers, and prejudiced barriers and aggressive systems. The chapter completes with a section on integrating the elements.
Reactive Automated Protection Systems
REAPS technologies are agile, automated systems that provide the security console officer with the ability to react in real time to ongoing security incidents. REAPS technologies can interfere with the advance of an attacker and redirect the incident to the advantage of the organization. They range from the subtle (lights and intercoms) to the extreme. REAPS technologies include the sophisticated use of intercoms, automated control of lighting and other facility features, deployable barriers, and in the extreme, it includes takedown technologies. The organization should consult its council before implementing any countermeasure that could cause bodily harm, as some takedown technologies can do. Takedown technologies are normally only appropriate where the risk of injury of the subject is offset by the potential risk of harm to others if the asset is destroyed or misused, such as might be the case with a chemical plant, suspension bridge, or nuclear power plant.
Deterrence Technologies
The first class of REAPS technologies are designed to deter minimally motivated threat actors. These usually include petty criminals, nuisance individuals, most economic criminals, and some political activists. The focus of deterrence technologies is to alter the environment so that it is not conducive to the aggressor to carry out his or her intended activities without the chance of interruption, intervention, or arrest.
Intercoms
From a REAPS standpoint, intercoms give the console officer the ability to intervene immediately on discovery of a security incident. Where an intruder’s determination is manageable, intercom intervention can often stop a security incident and send the intruder away.
Lighting Control and the Control of System Features
For most criminal and nuisance trespasses and intrusions, intruders flee quickly when a darkened area is suddenly flooded with light in every direction around them.
While lights obviously will not be a deterrent during the daytime, a variety of other visual and audio responses can alert the intruder that the security organization is tracking his movements. For example, at a refinery that had seen some nuisance intrusion, pole-mounted video cameras around the perimeter were augmented with high-intensity blue strobe lights and high-decibel klaxons that activate upon detection and confirmation of an intrusion. This is both disorienting and anxiety building for the intruder who in most cases will quickly exit the premises.
Deployable Barriers
For the purposes of brevity, we review a number of REAPS systems together under the heading of deployable barriers. Deployable barriers are used to slow the progress of an attacker once an attack is detected. There are three main types of barriers: vehicle barriers, marine vessel barriers, and pedestrian barriers. This list is by no means exhaustive.
Vehicle Barriers1
Vehicle barriers are typically manufactured either to deter or to prevent an entry and will be rated using the U.S. Department of State Crash Test Certification method. Unrated vehicle barriers should be viewed as being appropriate for deterrence only and not to stop a vehicle. Barriers are rated for their ability to stop a 15,000-lb (6800-kg) vehicle (including its load) at a given speed (the “K” rating), and with a given amount of penetration (the bed of the truck must not penetrate the barrier by more than a given distance– “L” rating). There are three “K” ratings and three “L” ratings:
• K4 barriers are rated to stop a 15,000-lb vehicle going 30 miles per hour (mph) [48 kilometers per hour (kph)].
• K8 barriers can stop the attack vehicle at 40 mph (65 kph).
• K12 barriers can stop the attack vehicle at 50 mph (80 kph).
• L1 barriers will allow the attack vehicle to penetrate not less than 20 and not more than 50 ft.
• L2 barriers will allow the attack vehicle to penetrate not less than 3 and not more than 20 ft.
• L3 barriers will not allow the cargo area of an attack vehicle to penetrate more than 3 ft.
Thus, a K4/L1 barrier can stop a 15,000-lb vehicle at 30 mph within 20–50 ft, and a K12/L3 barrier will stop the same vehicle at a speed of 50 mph with no more than 3 ft of penetration of the bed of the truck (Fig. 15.1).

Rising Bollards
Many manufacturers make bollards that rise out of the pavement to deter or prevent vehicular entry to an area. Bollards are useful in areas where it is desirable to permit pedestrian entry while limiting the entry of vehicles. Rising bollards are available in a vast array of cosmetic and mechanical design. Typically, rising bollards are either electric motor driven or hydraulic, although pneumatic bollards still exist. Rise time is typically 2 seconds to full height and 2 seconds down again. Rising bollards are usually capable of lifting a vehicle, so careful design and use is indicated to avoid such occurrences. When it does occur, it will usually be an ambassador’s limousine that will be captured. Murphy’s law indicates that the ambassador will be in the back seat with his wife and children or with another ambassador or a head of state (Fig. 15.2).

Rising Wedges
Rising wedges (also known as phalanx barriers) are the mainstay of serious vehicle stopping systems. Like rising bollards, they deploy in approximately 2 seconds and can take out a vehicle on top. Many phalanx barriers are K12/L3 rated. Phalanx barriers have wonderful psychological value. They send the message. If the message does not get through, they are one of the few barriers that can withstand a multiple vehicle attack in which one vehicle is used to clear the barrier and a second and sometimes third vehicle carry the bomb payload (Fig. 15.3).

Semaphore Parking Gates
Semaphore parking gates are commonly found at the entrance to car parks and car lots. They are a psychological barrier. They will not stop any serious attack. They will not even stop drunk or confused patrons. However, they can cause a fair amount of damage to a car’s paint (Fig. 15.4).

Cable Beams
Cable beam barriers are the killer bunny of semaphore arms. They look warm and fuzzy but they sure have a painful bite. Although they are not K/L rated, a good one can stop a 10,000-lb attack vehicle at 27 mph or a 6000-lb vehicle at 40 mph. These are useful in tight spots where a large, fast attack vehicle could not likely maneuver well, such as a parking lot. At slower speeds, they do a good job. Cable beams can either swing up or to the side of the road (Fig. 15.5).

Box Beam Barriers
Box beam barriers are similar to cable beam barriers but they are able to stop larger attack vehicles traveling at higher speeds. These are typically custom fabricated and counterbalanced. They are very heavy (several tons) and are often manually operated because motors for them are very expensive. These are normally used in areas where local fabrication costs are low enough to make them viable. I use them extensively in third-world environments. Although I have never submitted one for K/L rating, the math supports a K12/L3 rating on better designs.
Net Systems (Grab barriers)
USR Inc. manufactures a barrier that deploys fast and is effective against all types of vehicles (motorcycles to tandem trailers) as well as pedestrians. It presents as a web fabric made of high strength aircraft cable and, unlike other barriers, is effective as both a vehicle and a pedestrian barrier. Also unlike other barriers, it is designed to achieve its stopping results without fatal injuries in most cases. (All bets are off if the offender has a weapon and your people do too.) The grab barrier is available in K4, K8, and K12 ratings. The barrier can be configured for either industrial or cosmetic installations (Fig. 15.6).

Swing Gates
Swing gates are used in low-security environments in which a psychological barrier is appropriate for vehicle traffic, and they make a useful pedestrian barrier. In most cases, they are not capable of stopping a vehicle.
Rolling Doors and Gates
Rolling doors and gates roll down to close and up into a spiral at the top to open. These are a psychological barrier and present little defense against entry.
Sliding Gates
Some installations require sliding gates. These are available in a variety of types, with the least expensive being chain-link or estate-type fence fabric on a rolling frame. Box frame gates can be fabricated that present as a more formidable barrier, although most of these are not K/L rated.
Serious stopping power is available in the form of true K/L-rated steel fabricated sliding gates. These take major gate operators because the mass to move is significant and it requires much power to get them moving and stopped when fully open or closed. Typically, the robust K/L-rated sliding gate operators are included with the gate (Fig. 15.7).

Air Bags
Esoteric developers are reportedly working on an air bag system to stop vehicles. These would be deployed virtually instantaneously at a full-height vehicle portal and would trigger upon detection of a fast-approaching vehicle or manually.
Inventive Systems
It is possible to create a variety of other vehicle defense systems using common materials applied in unusual ways. For example, a roadway trench can become a barrier with the use of a grille (cattle guard) fabricated with explosive bolts to cause the grille to collapse into the trench upon approach of a known threat.
Marine Vessel Barriers
Anti-Boat Barriers
Deployable anti-boat barriers are floating obstacles that can be reeled into place across a berthing basin or waterway on demand. They are capable of stopping small craft and act as a visual deterrent. They are typically deployed by boat but can be deployed by reeled cable that sits on the bed of the basin.
Water Monitors
Water monitors are an adaptation of firefighting equipment that serve as an effective deterrent or to fend off attackers in a small craft. The volume of water that can be deployed against a small craft is capable of turning it away or sinking it. Water monitors can be controlled remotely and aimed by video camera on the monitor or by a synchronized pan/tilt/zoom camera.
Pedestrian Barriers
Pedestrian barriers range from the totally inoffensive (intercoms to challenge a subject verbally) to the extreme (ballistic weaponry).
Intercoms
Intercoms are the most basic and inoffensive barrier. When an intrusion is detected, the first step is to assess the seriousness of the offense. The combination of video and intercom is a very good way to do this. A console officer can quickly determine the capabilities and motivation of an intruder using a brief and standardized interview procedure. Intercoms act as a psychological barrier to low-motivated aggressors.
Lighting
When it is determined that an intruder’s motivation is to ignore directions over an intercom, the console officer can remotely turn off all available lighting in an unoccupied building. This is very useful indoors in buildings in which there are no windows, such as in the anchorage building of a suspension bridge. Unless the attacker is carrying a flashlight, he or she is quite literally “in the dark.” The console officer, of course, will be equipped with a quantity of low-cost infrared-illuminated indoor video cameras. The intruder cannot see, but the officer can see the intruder. The console officer can then return to the intercom and will likely find that the attention of the offender has been captured.
Alternatively, outdoors, turning on all available lighting sends the message that it will be difficult for the intruder to acquire cover from a patrolling officer. The point of lighting manipulation is to make the subject feel exposed.
Rolling Grilles and Operable Walls
Deployable grilles and operable walls are available in a variety of styles, from steel grilles to folding operable walls and movable walls. When motorized, these can be deployed rapidly to present a wall where the intruder was pretty sure a passage used to be. This a good place for another intercom and camera. Deployable grills and operable walls might have prevented many deaths and injuries both in the Mumbai attack on the Taj Hotel by the Pakistani terrorist group Lashkar e-Taiba where 31 people were killed, and in the Samali terrorist organization Al Shabab attack on the Westgate Mall in Nairobi which resulted in 72 deaths. (Fig. 15.8).

Deployable Doors
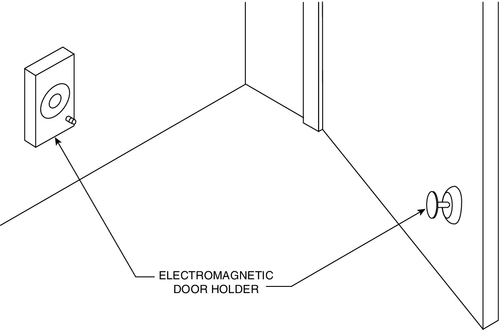
Automating critical passage doors or simply placing those doors on magnetic holders can cause the doors to release and close in a locked condition. The addition of magnetic locks with an intrusion override can prevent travel in either direction, making an effective barrier. Intrusion overrides require a fire authority variance and a safety switch at the console (Fig. 15.9).
Revolving Doors
Revolving doors can be used for positive access control and serve as an effective deterrent against illicit entry. They can also be locked to prevent the progress of an intruder.
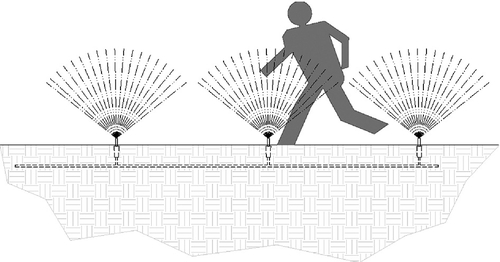
Irrigation Systems
Irrigation systems make a surprising barrier to outdoor intruders. Only the most determined intruders will proceed across a field of sprinklers. If the intruder does proceed, at least you know he or she is motivated (Fig. 15.10).
Fog Barriers
Smokecloak™ is a glycol-based visual barrier that can fill an area with an impenetrable fog within seconds, rendering anyone in it fully incapable of seeing anything. The barrier dissipates over a period of approximately 15 minutes and is effective when lights-out is not enough. An intruder cannot see his hand in front of his face, let alone anything else. It effectively blinds the intruder, even in daylight, making his progress painfully slow, and that is usually toward wherever he imagines the exit to be.
Prejudiced Barriers and Aggressive Systems
Prejudiced barriers can cause harm to the subject of deployment. Prejudiced barriers should typically only be used to protect assets that have the potential to cause great harm to the surrounding community if not properly contained. Examples include nuclear power plants, nuclear arms stockpiles, and chemical weapons stockpiles and other weapons of mass destruction. It is recommended that the organization seek the opinion of its legal counsel before acquiring or using any kind of prejudiced barrier. Some governments deem certain other assets worthy of the use of prejudiced barriers, such as national gold depositories. Ft. Knox in the United States is an example of a facility that makes use of prejudiced barriers to protect its critical assets.
Quick Setup Foam Barriers
Specialized applications call for a foam barrier. Rigid foam is deployed by combining two separate chemicals into a single nozzle, which sets up into a self-hardening block in the shape of the containment area. This can block and trap (and even encapsulate) the aggressor. Sticky foam has been developed at Sandia National Laboratories but is not yet commercially available; it is a single-component chemical that is dispensed from a pressure vessel to block the adversary’s path. The more the adversary fights with the sticky foam, the more sticky and tenacious the foam acts against him or her. See the section on dispensable barriers in Mary Lynn Garcia’s Design and Evaluation of Physical Protection Systems2 for a more detailed discussion of sticky foam.
Drop Chains
These are used for small, confined spaces such as the cable-splay room of a suspension bridge. The cable-splay room is the room in the anchorage of the bridge where the large main suspension cable splits out into many smaller cables that together make up the large main cable. Each of these smaller cables is anchored deep into reinforced concrete. The main suspension cable is especially vulnerable to cutting attacks in the cable-splay room. It is possible to position a large quantity of heavy chain links (about ceiling to knee length) in the cable-splay room from the ceiling in an array approximately 6 in. on center. These are held in place by two trays that are themselves held in place by explosive bolts. If the intruder makes it to the asset, the console officer blows the bolts and the chains drop in a manner that defies anyone in the room to stand up, let alone wield any kind of cutting tool. Properly designed, drop chains can be deployed without causing great bodily harm to the intruder.
Aggressive Systems
Aggressive systems reach out and touch forceful aggressors with force-on-force.
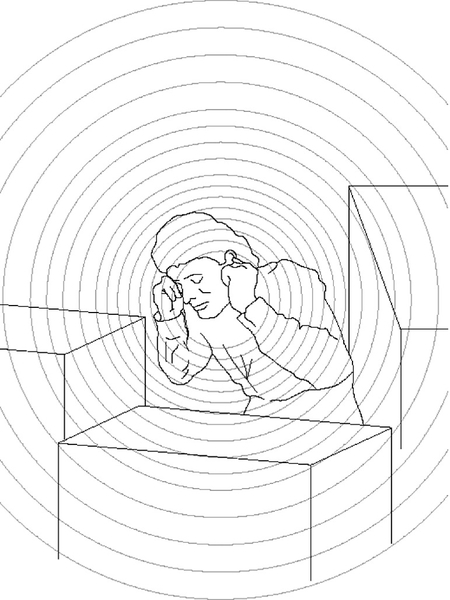
Acoustic Weaponry
The human body is sensitive to infrasonic sounds. Tigers are reported to be able to emit a stunningly loud 18-Hz roar immediately before attacking, stunning their prey. Sperm whales reportedly emit high-volume infrasonic pulses, disabling squid from making a quick getaway.
According to a report prepared for the United Nations in 1978, the frequency of 7 or 8 Hz is thought to be most dangerous to humans. This is the resonant frequency of flesh and theoretically can disrupt or destroy internal organs. At lower volumes, it is certainly able to cause intense discomfort, even making the subject evacuate at both ends.
High-amplitude infrasonic weapons can be created simply by combining two high-volume ultrasonic frequencies at a difference of 8 Hz and aiming them at the desired subject. Because the source transducers are ultrasonic, they can be placed some distance apart and “vectored” onto a single subject in a crowd of people. This creates a compelling wish to be somewhere else. Patents were issued for some acoustic weapons in 1999 and 2000. Experiments on infrasonic weapons in the 1970s by French robotics researcher Dr. Gaverau, without the benefit of the ultrasonic-to-infrasonic conversion, resulted in the test building being shaken to the point of nearly being destroyed, and the researchers were subjected to what they referred to as an “envelope of death.” Gaverau and his team were critically ill for days, with their internal organs experiencing painful spasms as a result of their body cavities having resonated at the deadly frequency. The jury is still out on this one. At the time the first edition of this book was being written, the first commercial acoustic weapon was introduced, called the Long Range Acoustic Device (LRAD)™. Since then the maker of LRAD has added other acoustic weapons and other companies have also developed their own offerings. The LRAD combines two ultrasonic frequencies, creating a third “beat” frequency. Because ultrasonic frequencies are highly directional, and the beat frequency can be any frequency, even ultra low frequencies of 7 to 8 Hz, it is possible to create very high amplitude, very directional, very low frequencies. This is a feat never possible before. In November 2005, pirates off the coast of Somalia who were attempting to fire on a passenger cruise ship were effectively repelled by an LRAD3 (Fig. 15.11)
Usable Acoustic Security Devices
I have successfully addressed gang activity near convenience stores by implementing outdoor speakers playing peaceful symphonic pop elevator music on satellite radio. This drives gangbangers totally nuts. The designer is advised to use bullhorn speakers enclosed in a vandal-deterrent cage. Bullhorns are recommended because they sound very bad, and the vandal-deterrent cage is advised because the gang will likely try to destroy the bullhorn. The music is not offensive to legitimate customers, but it creates an environment that does not support the business model of drug dealers. This has also been used in Australia to good effect to rid public buildings of unwanted gang behavior.4
A Welsh firm makes a near ultrasonic tone generator, amplifier, and piezo speaker that creates a barely audible sound like that of fingernails on a chalkboard. While older people cannot hear it at all due to natural age-related high-frequency hearing loss, it drives young people crazy when they are bathed in that sound for more than a few minutes.5 Young people passing through to and from the business barely notice it. The effect of the sound is cumulative. The longer a young person is in the presence of the sound, the more difficult it becomes to bear it.
High-Voltage Weaponry
Essentially a Tesla coil on steroids, high-voltage weapons are a Taser™ for protecting buildings. Useful to disperse crowds, they emit an attention-getting amount of high voltage at very low amplitude all around the vicinity of the spike transducers.
Another version of this weapon is the spark-gap transmitter. Similar to its portable cousin the stun gun, the spark-gap transducer can be mounted on top of a protective perimeter fence at distances of approximately 10 ft. When an intruder suspected of carrying asatchel charges or improvised explosive devices is detected attempting to make entry through the fence, after a video assessment of the situation and a polite verbal warning through a camera-mounted 30-W bullhorn, if this intruder still is not getting the message, the console officer and his or her supervisor throw a pair of safety switches after selecting the appropriate fence zone, and all the spark gaps along that fence section ignite in a bright array of square waves in the form of high-voltage arcs. If the intruder is carrying explosives and electrically activated detonators, this display of high-voltage can also be accompanied by an explosion in the vicinity of the intruder, followed afterward by a repair of the fence and clean-up on aisle 3. This approach is most appropriate in serious threat environments and in countries in which such methods are approved by the government. This approach is much less expensive than a helicopter gunship and requires less maintenance than automated guns.
Remotely Operated Weaponry
Most of the defeat technologies discussed previously are nonlethal, but when the asset value is exceptional or the risk of a successful attack to the public is high, and nothing else will get the job done, one can always rely on guns. At least two manufacturers make remotely operated weaponry. From 7.62-mm to twin 50-caliber guns and a range in between, remotely operated weapons are the final answer to intruders that just will not take no for an answer. These are products that couple a pan/tilt/zoom video camera with an appropriate weapon. These are available in either temporary or permanent installation versions. I have also seen them fabricated on site where budget is a factor and low-cost maintenance personnel are available (third-world countries). These are also deployed in the United States at critical installations.
Deluge Systems
For any environment such as an outdoor shopping mall, where competing gangs of criminal youths could engage in gunfire, nothing can disperse a crowd immediately quite like 10,000 gallons of water in 60 seconds. Afterward, although people are most likely to be upset and drenched, the gunfire will probably have stopped and the perpetrators will likely have fled, thus dissipating the danger and protecting the innocent public.
Coupled with gunshot recognition software, pan/tilt cameras can instantly zoom in on the offender, providing visual verification of the condition requiring action.
Deluge system activation should only be installed after careful consideration and advice from legal counsel, but they may be appropriate for any venue where there is a potential or history of gunfire in public spaces.
Integrating the Elements
It is one thing to find REAPS equipment (that alone can be a difficult task), but it is quite another to appropriately apply it. The reader can contact the author for help in finding this equipment. There are three factors in applying them.
Appropriateness
It is wholly inappropriate to apply lethal or even less than lethal countermeasures in anything but a serious threat environment in which the asset under protection could cause harm (munitions, nuclear reactors, etc.) and in which adequate public safeguards are not possible. The use of any of these systems in an environment in which an innocent could be harmed is completely inappropriate. I have refused to employ them where the government requesting the countermeasure was of questionable moral ethics. They should be used in close consultation with the manufacturer.
Operationally
The operation of such barriers and weapons should be limited to circumstances in which multiple layers of security are in place and the intruder has demonstrated firm determination to proceed toward a goal of harming or destroying a critical asset. Adequate evidence can be achieved by either the amount of force used or the determination with which the intruder continues undeterred by instructions toward the asset. If the attacker uses lethal force, it is arguably appropriate to defend with lethal force. If the intruder continues through other deployed barriers and refuses verbal instructions, it is reasonable to assume he or she will be undeterred by mild measures.
In any case, the system should be configured with adequate operational safeguards to absolutely prevent accidental deployment. This typically requires a deployment action by both an operator and a supervisor or some action by the intruder that is unmistakably hostile and will result in the death of innocents, such as driving a large truck full of explosives toward a Marine barracks compound at 5:00 am at high speed past a guard post.
Safety Systems
For any REAPS technology that could cause bodily harm, it is imperative to build in deployment safety systems. These can be engaged electronically, mechanically, and procedurally.
Electronic Safety Systems
Design REAPS systems to include at least two separate electronic circuits to trigger the system activation. For potentially lethal systems, it is advisable to use at least three triggering systems. These should be activated by totally separate electronic circuits such that no single point of failure could cause any more than one electronic triggering system to activate unintentionally. By separate systems, I do not mean separate dry-contact points on the same circuit board. I mean separate circuit boards on separate power systems with their own battery or uninterruptible power supply backup and with separate communication lines to each individual board. It is advisable to locate the boards in different areas on separate circuit breakers, on separate electrical phases, and, ideally, on separate electrical transformers. The dry contacts should be triggered in series, not in parallel. It is also advisable to protect the conduit within which the triggering circuit runs with a conduit intrusion alarm system. Use only metallic electrical conduit, preferentially rigid, not flexible, and waterproof where appropriate. For fast vehicle capture systems, at least two sets of loops should be used, coupled with optical sensors, if possible, to prevent accidental triggering by an unusual positioning of slow-moving vehicles.
Mechanical Safety Systems
Mechanical safety systems are a backup to electrical safety systems. For example, on drop chain systems, the explosive bolts should be on separate electrical circuits and the bolts should be wired such that all of them must break in order for the chains to drop. By using four separate circuits to drop the exploding bolts, the chains will only drop if all four circuits blow, thus assuring that a single point of failure type of accident does not cause injury.
Procedural Safety Systems
Any lethal or less than lethal REAPS system should also have procedural safety systems. These can include the requirement for both a console officer and a supervisor to trigger lethal systems after verifying intent and capabilities to cause great harm to the protected asset or the organization’s people or the public.
For nonlethal systems, such as deployable doors, gates, and grilles, these measures are not necessary because the deployment of a door is not an unusual or life-threatening event.
Summary
REAPS technologies provide the designer with the ability to react to security events. REAPS technologies include intercoms, deployable barriers, and takedown technologies. Intercoms can often stop an attack and send the attacker on away.
Deployable barriers may include vehicle barriers, marine vessel barriers, and pedestrian barriers. Vehicle barriers are rated by their stopping power. They are assigned K and L ratings based on the weight of a vehicle they can stop and how far the vehicle may penetrate past the barrier. Vehicle barriers include rising bollards, rising wedges, semaphore parking gates, cable beams, box beam barriers, and net systems. Vehicle gates include swing gates and rolling doors and gates. Marine vessel barriers include antiboat barriers and water monitors. Pedestrian barriers include intercoms, lighting, rolling grilles and operable walls, deployable doors, revolving doors, irrigation systems, and fog barriers.
Prejudiced barriers include quick setup and sticky foam barriers, drop chains, acoustic weaponry, high-voltage defense systems, remotely operated weaponry, and deluge systems.
REAPS technologies should be carefully vetted for operational, legal, and safety standards.
Questions and Answers
a. Address the needs of the console officer for communication and awareness.
b. Make the security officer aware of emerging security incidents.
c. Interfere with the advance of an attacker and redirect the incident to the advantage of the organization.
d. None of the above.
2. Where an intruder’s determination is manageable:
a. Proper signage will tell him or her not to enter the facility.
b. Intercom intervention can often stop a security incident and send the intruder away.
c. Neither of the above.
3. The focus of deterrence technologies is to:
a. Alter the environment so that it is not conducive to the aggressor to carry out his or her intended activities without the chance of interruption, intervention, or arrest.
b. Alter the environment so that the intruder cannot proceed toward his or her intended target.
c. Alter the environment so that arrest of the intruder is guaranteed.
d. None of the above.
4. From a REAPS standpoint, intercoms give the console officer:
a. The ability to intervene immediately on discovery of a security incident
b. The ability to talk to persons waiting at a door
c. The ability to talk to persons waiting at a vehicle gate
d. None of the above
5. Barriers are rated for their ability to stop a _____________ vehicle (including its load) at a given speed (the “K” rating), and with a given amount of penetration (the bed of the truck must not penetrate the barrier by more than a given distance– “L” rating).
b. 15,000 lb (6,800 kg)
c. 20,000 lb (9,066 kg)
d. None of the above
6. Which below is not a form of deployable vehicle barrier, capable of stopping a vehicle?
a. Rising bollards, rising wedges
b. Semaphore parking gates and swing gates
c. Cable beams, net systems
d. All of the above
7. Deployable antiboat barriers are ___________ that can be reeled into place across a berthing basin or waterway on demand.
b. Floating obstacles
c. Boat patrols
d. All of the above
8. Deployable grills and operable walls might have prevented many deaths and injuries at which terrorist attacks?
a. Taj Mahal and Westchase Mall
b. Taj Hotel and Westchase Mall
c. Taj Hotel and Westgate Mall
d. None of the above
9. Prejudiced barriers should typically only be used:
a. To protect assets that have the potential to cause great harm to the surrounding community of not properly contained
b. To protect critical assets such as bank safes
c. To protect childcare centers
d. None of the above
10. Remotely operated weapons:
a. Are used only by the military
b. Are only used outside the United States
c. Are the final answer to intruders that just will not take no for an answer
d. None of the above
Answers: 1: c, 2: b, 3: a, 4: a, 5: b, 6: b, 7: b, 8: c, 9: a, 10: c
