Chapter 9. Active Directory Maintenance
Terms you’ll need to understand:
![]() Extensible Storage Engine
Extensible Storage Engine
![]()
Ntds.dit
![]() Active Directory log files
Active Directory log files
![]() Garbage collection
Garbage collection
![]() Tombstoning
Tombstoning
![]() Defragmentation
Defragmentation
![]() Primary restore
Primary restore
![]() Normal restore
Normal restore
![]() Authoritative restore
Authoritative restore
![]() ADSIEdit
ADSIEdit
![]() System state data
System state data
Techniques you’ll need to master:
![]() Backing up Active Directory
Backing up Active Directory
![]() Performing primary, normal, and authoritative restores of AD
Performing primary, normal, and authoritative restores of AD
![]() Using NTDSUtil to move AD data files
Using NTDSUtil to move AD data files
![]() Using NTDSUtil to move AD log files
Using NTDSUtil to move AD log files
Active Directory (AD) is a transactional database. This means that it has built-in recovery techniques that are performed automatically should a system fail because of a hardware problem. It also means that you should know how to both back up and recover the database in the event of failure.
This chapter discusses the structure of the AD, including details of the database and log files used to process updates to the data. We examine how data can be backed up and restored. You will see that the AD replication process can be used to update a domain controller (DC) that has been offline for a period of time. It is also possible to force restored data to be propagated throughout the network via AD replication, even if that data is technically out of date.
Introducing AD Maintenance
Because so many areas of AD operation are automatic, it is easy to think that there is little reason to be concerned about maintenance tasks. However, this assumption would be incorrect. Maintaining the AD database on each DC is an essential task that should be performed regularly. Backup and restore procedures allow you to recover lost or corrupted data.
With regard to maintenance, we will look at four key tasks. Two of these tasks should be scheduled to run on a regular basis. You should also test these procedures periodically to make sure that you can recover from a problem and that you are enjoying optimal performance.
These tasks are as follows:
You can use the backup utility that ships with Windows Server 2003 to back up the AD database. In addition, several third-party utilities are available that can perform the same task (indeed, NTBackup is merely a stripped-down version of Veritas Backup Exec). Whichever tool you decide to use, this task should occur on a regular schedule.
It is possible for the AD database to become corrupt or accidentally deleted. When this occurs, you must restore the database. Generally, you use the same tool you used for your backup to do this. However, some tape formats allow you to use different restore software.
There are two instances when the AD database must be moved. The first is during the offline defragmentation process. This ensures that the process does not corrupt the database. The second instance is performance related. If the hard disk that contains AD is becoming full, you could move the database to prevent it from being corrupted if the disk reached capacity.
Defragmentation increases the performance of both writing data to the database and querying the AD data. It can also be used to reduce the amount of disk space the database takes up.
Active Directory Data Files
Active Directory uses the Extensible Storage Engine (ESE), which was first pioneered in Microsoft Exchange Server. It uses the concept of transactions to ensure that the database does not become corrupted by partial updates and so it can recover in the case of a power failure. Each transaction is a call to modify the database. A modification can be the addition of new data or a change being made to data that is already stored.
For the transactional system to work, the AD database must have associated log files. These log files are used to store modifications before the data is written to the physical database file. We’ll look at how this works in a moment. Before we do that, however, we must define which files are used by the database. Five files make up the AD database system:
• ntds.dit
• edb*.log
• edb.chk
• res1.log
• res2.log
Each of these files has a role to play in ensuring that data can be written to the directory in a safe and recoverable fashion. You should note that these files exist on every DC in your environment. The AD database is not centralized in any way; it exists on each server that is promoted to the role of DC. Each instance must be maintained separately.
ntds.dit
This is the single file that holds all the AD data, including all objects and the schema information. It is the Active Directory database. This file is stored by default in the <systemroot>NTDS folder, although it can be moved.
Remember from Chapter 2, “Planning and Implementing Forests and Domains,” that it is recommended to have the database on a separate physical drive from the log files, both for performance and recoverability reasons. The ntds.dit file works in conjunction with the log files. The .dit extension stands for directory information tree.
edb*.log
The edb*.log file is the transaction log for ntds.dit. The file that is currently being used is called edb.log. When that file reaches a specified size (by default, 10MB), the file gets renamed to edb*****.log, where the asterisks are incremented from 1 upward. When the files are no longer needed, they are deleted by the system. When a backup occurs, the archived logs are purged, so if the drive your log files are stored on is filling up, you can often recover space by performing a backup of AD (if for some reason you are not performing regular backups).
edb.chk
There can be two copies of changes to AD data. The first copy is kept in log files; these changes occur as data is accepted from an administrative tool. The second copy is the database file itself. This checkpoint file keeps track of which entries in the log file have been written to the database file. In the case of failure, Windows Server 2003 uses this file to find out which entries in the log file can safely be written out to a database.
res1.log and res2.log
Essentially, res1.log and res2.log are two placeholders that exist simply to take up space. In the event that the drive that the log files are stored on runs out of space, the AD replica can become inoperable. It is far better for the DC to shut down gracefully. These two files, each 10MB in size, exist to prevent a DC from being unable to write to the log files. If a DC runs out of disk space, AD can be sure that it has at least 20MB of space to write out any necessary log data before shutting down.
Garbage Collection
Garbage collection is the process in which old data is purged from AD. Because all DCs in a Windows Server 2003 network act as peers, deleting objects is a little more difficult than it might first appear. If an administrator wants to delete a user object from the network, he or she can press the Delete key. However, how will Windows Server 2003 make sure that all DCs in the enterprise are aware that this deletion is taking place? If the deletion happens in real-time, it can’t. Hence, the use of tombstoning.
Data is never immediately deleted from AD. Instead, the object’s attributes are deleted and the object is moved to a special container called Deleted Objects. The object is then assigned a tombstone. By default, this tombstone is 60 days, although it can be changed. The tombstone means that the physical deletion of the object will occur by the configured interval. This gives AD time to replicate this change to all DCs. It also means that the deletion can take place at around the same time, no matter how distant the DCs may be.
Garbage collection also defragments the database by using the online defragmentation process. We will take a closer look at defragmentation in a moment.
Note
To change the interval for garbage collection, you must use the ADSIEdit tool included with Windows Server 2003. Connect to the Configuration container and edit the garbageCollPeriod and tombstoneLifetime attributes. By default, the period is 60 days. This is displayed in ADSIEdit as <not set>. Be careful about setting the value too low; this can prevent your restores from working because you cannot restore a DC from a backup that is older than the tombstone period. Microsoft recommends leaving the value set at the default.
Performing Backups
A Windows Server 2003 DC can be backed up while it is online, thereby minimizing disruption. It is not enough to back up only the database and log files. Instead, you must back up the system state data.
System state data is a collection of data that makes up a functioning AD infrastructure. It includes the AD database, along with other folders and files. These files collectively can be used to recover from even the most catastrophic failure. System state data includes the following:
• AD database file
• SYSVOL folder
• System startup files (Ntdetect.com, Ntldr, and Bootsect.dat)
• COM+ Class Registration database
• Certificate Services database
Not all these may exist on your server; for instance, the Certificate Services database is an optional component. You need all these folders because, in one way or another, they support the server.
The SYSVOL folder is a shared folder that exists on all DCs. This folder is used to replicate Group Policy Object (GPO) data and logon scripts. The Class Registration database is composed of component services that are installed on a system.
You can back up the system state data without buying third-party utilities. To do this, use the built-in backup utility and follow these steps:
1. Select Start, All Programs, Accessories, System Tools, Backup. When you do this, an informational screen appears. Click the Advanced Mode link.
2. This displays the main Backup/Restore window, as shown in Figure 9.1. Click the Backup tab.
Figure 9.1. Welcome Screen for Backup/Restore utility.

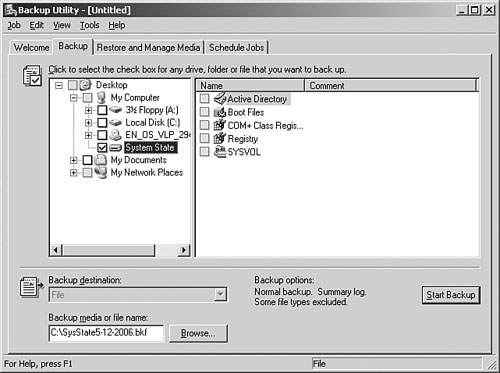
3. When you are on the Backup page, select System State, as shown in Figure 9.2. You also have the option at the bottom left to choose your backup destination, which is the media, such as a file or a tape drive. If you are backing up to file, you can specify a file location or browse to an existing file, or choose a tape in your medial pool to back up to.
Figure 9.2. Selecting System State.
Tip
Designing and implementing a full-blown backup solution is beyond the scope of this book and the exam, so if concepts such as media pools and backup sets are unfamiliar, you will want to refer to materials for the 70-290 exam.
4. You will see an informational screen next, as shown in Figure 9.3. You have the options of turning your backup selections into a schedule as well as deciding whether to append or overwrite an existing backup. When you have made your selections, click Start Backup.
Figure 9.3. Backup Job Information screen.

Note
You might be familiar with the concept of an emergency repair disk (ERD) from previous versions of Windows. Note that this feature is not part of the Windows Server 2003 operating system. The functionality has been replaced by Automated System Recovery (ASR).
Recommendations for Backing Up Data
You can’t restore a DC fully if you do not have a backup of the system state data. However, even having that data might not be enough if an entire server has been lost in, say, a flood. Make sure you are also backing up all other folders and disk drives on the server periodically. To do this, you can use the built-in backup tool or a third-party utility.
You must be a member of the Administrators, Backup Operators, or Server Operators group before you can back up data. These are built-in groups; if you do not want to use them, you must assign permissions yourself.
The backup utility built in to Windows Server 2003 can only be used locally when backing up system data. This means it cannot be configured from a single server to back up system data on all DCs in your enterprise. For this reason alone, you might want to consider purchasing a utility that offers more features if you have more than a very small network with only a single DC.
Windows Server 2003 Automated System Recovery (ASR)
Windows Server 2003 has a new tool that can be used for system disaster recovery. Automated System Recovery (ASR) is a two-part system-recovery tool that includes ASR backup and ASR restore. ASR should be a last resort in system recovery, used only after you have exhausted other options such as Safe Mode Boot and Last Known Good. This is a feature that was first introduced with Windows XP and now can be used to recover a machine from complete disaster.
Restoring AD
Depending on the backup options you have implemented in your environment, you might have three methods to choose from when restoring a Windows Server 2003 DC. If you have performed a backup by following the steps outlined in the previous section, you could perform a restore operation with the built-in backup tool.
When you perform a restore, you have three options: a primary restore, a normal restore, or an authoritative restore. We will take a closer look at these options in a moment.
Note
Be careful about performing restores when utilizing external trusts. The password on an external trust is renegotiated by Windows Server 2003 every 7 days. If a restore is performed that is older than this (for example, 14 days), you should reestablish the trust.
Alternatively, you can rely on AD replication to take care of updating a new DC. In this scenario, a failed DC is reinstalled from scratch. After the DC is online, it updates itself via normal replication techniques. This would occur automatically and would not require any additional administrative tasks. Because this is a simple process, we won’t discuss it any further in this chapter.
Note
To perform a restore at a DC, you must be able to log on with the local administrator password. This password is stored in the local SAM, and not within Active Directory. In Windows Server 2003, it is now possible to change the local Administrator password from within NTDSUtil. Because the local Administrator password allows for AD restores, it should be kept confidential.
Normal Restore
The normal restore (formerly called the nonauthoritative restore) is the simplest form of restore when you are using backup media. A normal restore is a nonauthoritative restore and is a restore of data from backup. Because the data will probably be out of date (presumably, some changes were made to the data in AD after the last backup), normal AD replication processes make sure that the missing data elements are updated. This type of restore is called nonauthoritative because the restored data is subordinate to the “live” data in Active Directory. In other words, a normal restore results in the restoration of data that is in turn overwritten or updated through replication by the “authoritative” data already live from Active Directory. Naturally, you would need to have at least one other functioning DC in order to perform this type of restore.
This would be a common practice if a hard disk failure had taken place. If a hard disk fails, the server might become inoperable. You would simply replace the failed hardware, perform a normal restore, and then wait for AD replication to bring the DC up to date. This process is faster than reinstalling the server and promoting it to a DC with dcpromo.exe, because less data will have to be replicated to the restored DC. It is important that if you restore to new hardware that the old machine never comes back online. It would have the same computer name in Active Directory as the new domain controller, which would cause a conflict and potential data corruption in addition to causing problems with basic AD functionality.
Performing a normal restore is fairly simple. However, you cannot restore AD data while it is in use. For this reason, the server must be taken offline before a restore can happen. To do this, follow these steps:
1. Restart the server, pressing F8 during startup. The Advanced Startup Options are displayed.
2. Select Directory Services Restore Mode. This starts the server, but it does not start AD.
3. Log in to the server using the Active Directory Restore Mode password. This is stored locally on each DC and can be different for each DC in your enterprise.
4. Use the backup tool to restore the system state data.
5. Restart the DC.
After the server has been restarted, it is updated by its replication partners. An integrity check also takes place, and various indexes on AD data are rebuilt. This places a temporary additional load on the server during boot time.
Authoritative Restore
The authoritative restore can be used to restore individual pieces of AD. This is useful if an error has taken place and an object has been deleted by mistake. Let’s look at an example to clarify this process. An administrator is working with the AD Users and Computers tool, and he accidentally deletes an organizational unit (OU). The OU contained user objects, and they are deleted as well. Because this change was accepted by a DC, it will be replicated to all AD replicas in the enterprise. If nothing is done, this mistake will eventually be replicated to all the DCs in the environment.
If the OU contained a small number of accounts, it might not be a problem to simply re-create it; however, if a large number of user objects were involved, it could take some time. An authoritative restore allows an administrator to restore the deleted OU from backup. When an authoritative restore takes place, the Update Sequence number (USN) of the object is, by default, incremented by 100,000 each day since the last backup. The USN is a value AD assigns to all objects and attributes, and uses to determine whether an object or attribute needs to be replicated to other domain controllers. Because the USN is higher than the copy currently held by the DC’s replication partners, the restored object is assumed to be the most up-to-date copy. This change is then forced out to all other DCs via normal AD replication processes.
Note
It is assumed that more than 100,000 changes have not been made to the restored data since the backup took place.
The process for performing an authoritative restore is somewhat different from the process outlined for a normal restore. After you have restored the system state data, you must not restart the computer. Instead, perform these additional steps:
1. Open a command prompt. Type ntdsutil and press Enter.
2. Type authoritative restore and press Enter.
3. Type restore subtree <distinguished name>, where <distinguished name> is the full path to the object. For an OU called Finance in a domain called HCSNET.COM, this would be OU=finance, DC=HCSNET, DC=COM.
4. Type quit. Type quit again and press Enter to exit NTDSUtil.
5. Restart the DC.
Note
The one exception to the capability to do authoritative restores is when you want to restore objects stored in the Schema partition. The Schema is “owned” by the Schema Master operations master. To restore the schema, you must restore the Schema Master. Any changes made since the backup was performed are lost.
Primary Restore
What would you do if you were faced with a situation where you only had a single DC, and it failed, causing you to have to do a restore? A normal restore would not work because there would be no other DCs available to bring the restored DC back to current. Likewise, an authoritative restore is not designed to restore all of AD, but rather specific data that has been deleted. For this scenario, you have to perform what is called a primary restore. A primary restore is used to rebuild the first DC of a domain from backup when no other DCs still exist and you want to rebuild from backup rather than creating the domain over from scratch. To perform a primary restore, perform the following steps as a member of the local Administrators group.
1. Restart your DC in Directory Services Restore Mode.
2. Start the Backup utility.
3. On the Welcome screen, click Advanced Mode.
4. On the Advanced Mode screen, click the Restore and Manage Media tab, choose the data to restore, and then click Start Restore.
5. In the Warning dialog box, click OK to the warning that displays.
6. In the Confirm Restore dialog box, click Advanced.
7. In the Advanced Restore Options dialog box, click When Restoring Replicated Data Sets, Mark the Restored Data as the Primary Data for All Replicas, and then click OK twice.
8. Click close on the Restore Progress dialog box.
9. Click Yes to the Backup Utility dialog box.
Moving the AD Database
Because AD is a transactional database, you are able to benefit from some of the standard optimization techniques employed with this type of system. One of the most common suggested techniques is to move the database file to a separate physical hard disk from the log files.
Moving the database to a different physical hard disk from the log files prevents disk contention. The log files are being written to constantly, which means the hard disk heads are fairly busy. When a query is made against the AD database, the heads have to move to read from ntds.dit. This contention reduces performance of the disk subsystem.
Note
Moving ntds.dit does not mean you should pay less attention to the need to protect your data. Your DCs should be running RAID configured disks. Even with a single RAID array, you cannot ensure that the database file and log files are on different physical hard disks. If you decide to move the database file to a different disk, it is recommended that this disk has either RAID-1 (disk mirroring) or RAID-5 enabled.
You can move the database with the NTDSUtil command-line utility. For this to work, you must have booted your server in Directory Services Restore Mode. Remember that for most of the major database-maintenance tasks (other than performing a backup), you must have booted the server into this mode.
Following are the steps for moving the database file to another hard disk:
1. Restart the server, pressing F8 during startup. The Advanced Startup Options appear.
2. Select Directory Services Restore Mode. This starts the server, but it does not start AD.
3. Log in to the server using the Directory Services Restore Mode password. This is stored locally on each DC and can be different for each DC in your enterprise.
4. Open a command prompt. Type ntdsutil and press Enter.
5. Type files and press Enter.
6. Type move db to <drive><folder>, where <drive> and <folder> make up the full path to the new location. Press Enter.
7. Type quit and press Enter. Then type quit again and press Enter to exit.
8. Restart the DC.
These commands do not simply move the database file; they also update the Registry so it points to the new location. Simply moving the file will cause the DC to fail.
Note
If you want to move the log files, enter move logs to <drive><folder> instead of move db to <drive>/<folder> in the preceding steps. This moves the log files and also updates the Registry.
Defragmenting the AD Database
Fragmentation has existed on personal computers for many years. The AD database suffers from it just like any other file. Fragmentation of the AD database occurs during the normal operation of a DC. Put simply, as database entries are made and then deleted, gaps can occur in the database file. These gaps cause subsequent records to be written randomly across the hard disk sectors, which reduces performance. Read and write operations are much faster if the database reads and writes are made to consecutive sectors of the disk. This is because the disk head moves much less if the sectors are contiguous.
Windows Server 2003 includes a defragmentation program that works at the file level to make sure each file is written to consecutive sectors of the disk. The defragmentation utility for AD goes one step further and reorders records within the database file.
Fragmentation within a database occurs in the same way that fragmentation of files occurs. As an example of how this works, imagine that an object is created within AD. This data is written to 150 consecutive sectors of the hard disk. Two properties of the object are then deleted. The properties’ data was stored in sectors 50, 51, 90, and 99. New data is then written to the database. This data requires four sectors. Because it takes the first available sectors, it ends up in sectors 50, 51, 90, and 99. This data is now fragmented. It will take longer to retrieve this data than it would if the sectors that contained the data were consecutive.
AD defragmentation can occur in two modes: online mode and offline mode. These are defined in the following sections.
Online Defragmentation
Online mode means that the server remains online while the process takes place. The online defragmentation method is slower than offline defragmentation because the DC must service requests while the defragmentation is taking place, and it offers fewer benefits than offline defragmentation—most significant is that it does not reduce the disk space consumed by the database by purging “white space” (unused space).
Online defragmentation is an automatic process that kicks off, by default, every 12 hours. This method is part of the garbage-collection process discussed in the “Garbage Collection” section earlier in this chapter. Full defragmentation can take place with this method, but the size of the AD database file will never be reduced. The records in the database are moved so they exist on contiguous sectors, but even if there is a lot of empty space in the database file (for instance, after a mass deletion process), the space will not be returned to the file system.
Offline Defragmentation
Offline mode offers greater benefits, but the DC must be taken offline. Because this process is more vulnerable to being corrupted through an unexpected power failure or hardware issue, an offline defragmentation never occurs on the live database file. Instead, a copy of the database is made, and the defragmentation occurs against the copy. When defragmentation is complete, you must archive the current version of ntds.dit that is being used and move the defragmented version into its place.
Note
Do not delete the old copy of ntds.dit until the DC has been rebooted and proven to work with the new defragmented file.
Offline defragmentation is the only way to return space from the database to the file system. This is useful after you have performed mass deletions in the database. By default, if you have a database that contains 50MB of data, and 50% of that data is deleted, the file remains at 50MB. The only way to return the 25MB to the file system is to perform an offline defragmentation.
Performing an Offline Defragmentation
You must use the NTDSUtil command-line utility to perform an offline defragmentation. For the process to run, you must reboot your server and bring it up in Directory Services Restore Mode. The steps for performing an offline defragmentation are as follows:
1. Restart the server, pressing F8 during startup. The Advanced Startup Options are displayed.
2. Select Directory Services Restore Mode. This starts the server, but it does not start AD.
3. Log in to the server using the Directory Services Restore Mode password.
4. Open a command prompt. Type ntdsutil and press Enter.
5. Type files and press Enter.
6. Type compact to <drive><folder>, where <drive> and <folder> are the location where the compacted file will be stored. Press Enter.
7. After the process is complete, a new ntds.dit file will exist at this location. Type quit and press Enter. Type quit and press Enter again to exit NTDSUtil.
8. Copy the new ntds.dit file over the old version of ntds.dit.
9. Restart the DC.
Recommendations for AD Database Maintenance
The first recommendation for maintaining an AD database is to do it! Make sure that you understand which options are available to you and that they are scheduled to be performed on a regular basis. You should be especially careful of changing the default settings for the tombstone lifetime. This is 60 days by default, and reducing this time frame can prevent you from being able to restore system state data that is past the tombstone lifetime. (Think of this as a sell-by date; you cannot use the backup if the sell-by date—that is, the tombstone lifetime—has expired.)
You should separate the AD database file from the log files. This prevents disk contention and increases the performance of a DC.
Keep in mind that you do not have to perform an offline defragmentation regularly. Instead, you should rely on the online defragmentation process. You should perform an offline defragmentation only if you think you can compact the database and return a significant amount of space back to the file system. This happens when mass deletions have taken place or when a server that used to be a Global Catalog server will now operate simply as a DC.
Monitoring Active Directory
Restoring Active Directory data after the event of a failure is still, even with all the correct processes and tapes in place, a harrowing experience. The purpose of monitoring is twofold. First, monitoring helps you maintain performance over time. It should alert you to dips in performance, allowing for proactive maintenance. Monitoring can also help you in investigating problems on your system, such as sudden failures of hardware components.
Active Directory, and some of its ancillary services, relies heavily on replication. Replication can be defined as the process of making domain controllers (DC) consistent. It should be noted that there are two areas of replication that must be working for a reliable Windows Server 2003 environment: Active Directory Replication and the File Replication Service.
As mentioned earlier in this chapter, AD is a database. Properties within that database, when they are updated, must be replicated within the environment. This type of replication is commonly called Active Directory replication.
At the same time, there are services that rely on AD that store data that is not part of the database. An example of this is Group Policy. Group Policy is actually made up of two sets of data. The first is called the Group Policy Container (GPC). The GPC data is stored within AD and is therefore replicated using standard AD replication processes. Associated with this data are objects called Group Policy Templates (GPTs). These are physical files. For instance, they might be .reg files that store changes that must be applied to the Registries on client machines.
GPTs are stored in SYSVOL on every DC within a domain. All instances of SYSVOL must be kept consistent (a Group Policy cannot be applied if only one or the other of these two items, the GPC or the GPT, exists at a DC). Replication of the GPT data is performed not by AD replication but by the File Replication Service (FRS).
These two replication systems operate using different technologies, and even different topologies. Therefore, for proper monitoring of a Windows Server 2003 environment, you must know what tools are available to monitor them.
Monitoring Active Directory Replication
The Active Directory replication process is fairly complex, and it relies on other systems to make it work. For instance, DNS is an integral part of any Windows Server 2003 deployment, and a failure in DNS will undoubtedly cause problems with AD replication.
There are three main tools you can use to troubleshoot replication problems with AD:
• Event Viewer
• The command-line utility Repadmin
• The graphical user interface tool Replmon
Any one of these tools can be used to troubleshoot issues or to alert you to problems as they develop.
Note
Although you might be familiar with Event Viewer from previous versions of Windows, you should note that it is somewhat more complex in a Windows Server 2003 AD environment. Depending on the services you have installed, there are likely to be many different logs to view. For example, problems might appear in the Directory Services log that actually are a response to a problem somewhere else, such as in DNS. Make sure you look at all relevant logs when troubleshooting.
Event Viewer
Event Viewer contains log files generated by the operating system. The level of detail in the recorded events, and the number of the events themselves, can vary, depending on the level of logging you have turned on.
You can change the level of logging in the Registry. The Registry setting is HKLM, SYSTEM, CurrentControlSet, Services, NTDS, Diagnostics. Four settings can affect the level of logging:
• 0—Disabled
• 1—Minimum Reporting
• 3—Full Reporting
Logging takes processing time, not to mention disk writes. Therefore, it is not a good idea to turn on full reporting unless it is really necessary, such as when you are actively trying to track down an error. For these reasons, the default value is 0 (disabled).
The events recorded in the logs can be exported for reporting and analysis. Common file types are CSV and TXT. These can easily be imported into applications such as Microsoft Excel.
Note
It used to be possible to use a resource kit utility called Dumpel to analyze event logs. However, this tool has not been updated for Windows Server 2003. It is limited in that it can be used only for the Application, System, and Security logs.
Repadmin
Replication Administrator, or Repadmin, is a tool that ships with the resource kit. It has many of the same functions as Replmon, with the added benefit (or negative, depending on your point of view) of being command-line based.
Repadmin allows you to monitor replication, and it complements other console functions. For example, if you want to know whether a DC is a Global Catalog (GC) server, you can either view it in the Active Directory Sites and Services console or use Repadmin (with /options).
Repadmin can provide a lot of information and functions. Among other things it can do the following:
• Give status of the Knowledge Consistency Checker (KCC)
• Provide the last replication event received from a DC’s partner or partners
• Be used to delete objects restored accidentally with an authoritative restore (such as when the tombstone value has been exceeded)
• Disable compression of AD replication data intersite
Repadmin is not a tool you use every day, but it does offer a method of drilling down into the replication process and getting to the heart of a DC’s functions.
Replmon
Replication Monitor is basically the same tool as Repadmin, with the addition of a graphical user interface (GUI). This makes it easier to use while you’re at a server console. Replmon is provided with System Tools in a Windows Server 2003 installation.
Because Replmon has a GUI, some might find it easier to use. When it starts, it displays a standard set of data. This can be useful to give you basic information at a glance. The following information is provided:
• Naming context—Provides the naming contexts supported on the server. If the server is a GC, all naming contexts in the forest are provided.
• Replication partners—Lists the names of the inbound replication partners.
• Icons—A double server icon is an intrasite partner. A server and phone icon is an intersite partner. A mini PC means local server.
• Log entries—The right pane shows the replication history (new entries are added at the end).
Replmon also enables you to see objects that have been tombstoned but not yet deleted. Along with the capability to configure email notification if a connection to a replication partner fails, Replmon represents a useful tool for monitoring AD replication.
Exam Cram Questions
1. Gary has just performed a large number of updates and deletions from Active Directory. This was done because his company has been downsizing, and some divisions are being moved outside of the company. Which of the following procedures should he perform? [Choose the two best answers]
• A. Backing up the AD data.
• B. Defragmenting the AD data.
• C. Moving the AD database.
• D. Nothing. Just wait 24 hours before doing any more administrative work for the replication to settle.
2. Robert has just received an email message from a consultant who is coming in to perform a health check on the network. The consultant has told him that he must be prepared to move the AD database on several domain controllers. What are the reasons why he would want to do this? [Choose the two best answers]
• A. The consultant might be bothered about performance on the domain controller. On at least a few of them, hard disk space is getting low on the partition on which AD is installed. During his last visit, the consultant installed a new set of mirrored disks; these are a better choice for the AD database.
• B. The consultant might be bothered about performance on the domain controller. On at least a few of them, hard disk space is getting low on the partition on which AD is installed. During his last visit, the consultant created a new partition on the RAID-5 controller. This is a better choice for the AD database.
• C. The consultant wants to move the database to another machine to facilitate better overall performance.
• D. The consultant wants to perform a database defragmentation. This is best done with a copy of the AD database in case corruption occurs.
3. Lisa is a system administrator for a large bank. While running statistics on her servers, she finds that one of her domain controllers is running extremely low on hard disk space. Currently, it is losing 10MB per week. She calls her manager and he tells her not to worry. He will have a support technician add a new hard disk early next week. Lisa is concerned that the DC will fail before that. Why is the manager confident that this will not be a problem?
• A. The manager is mistaken. With 10MB being consumed every week, it is highly likely that within days, the DC will fail with a lack of disk space.
• B. AD will soon discover that the hard disk is getting full. When it does, it will lock the partition that contains the database, thereby preventing any additional space being consumed.
• C. The manager is correct. AD will send an alert email to all administrators when failure is imminent due to lack of disk space.
• D. The manager is correct. Two files, each consuming 10MB each, are stored along with the AD data files. These files exist to consume disk space should the disks on a DC fail.
4. AD is made up of several files. Which of the following represents the current transaction log used by AD?
• A. edb.chk
• B. ntds.dit
• C. edb.log
• D. edb0000A.log
• E. res1.log
5. Mike is a system administrator for a charitable organization in Washington, DC. He has been cleaning up an inherited AD-based network by clearing out a lot of objects within AD. These deletions constituted about a third of the total AD data. Over the last few days, Mike has been monitoring the ntds.dit file. He is expecting the size of this file to reduce because it now holds a lot less data. However, he has seen nothing yet. Why is this?
• A. When objects are deleted from AD, they are not immediately deleted. Instead, they are assigned a tombstone of 60 days. The size of the file will not be reduced until after this tombstone has expired.
• B. Mike is wasting his time because the file will never reduce in size. The space, once consumed by the objects, simply remains empty space within the database file.
• C. Mike must wait for 24 hours.
• D. Mike should back up and restore the database. This compresses the file.
6. Dennis is a system administrator for a large enterprise. Dennis would like to increase the performance of AD reads and writes. He remembers reading that to do this he should move the AD database to a different physical hard disk from the log files. This is a single hard disk, with the operating system installed on it, along with a RAID-5 array that includes the AD database file. Dennis decides to move the database file to the single hard disk. During a conversation with the IT manager, however, he is told he must not do this. Why was he told this?
• A. His boss does not understand AD. He is wrong; the database should be moved.
• B. Although Dennis will gain some performance benefits from making the move, the lack of data protection in this particular instance means it is not a good idea.
• C. If performance can be gained by moving the database, Windows Server 2003 will do it automatically.
• D. RAID-5 is a superior system. Disk writes and reads on a RAID-5 system are substantially faster than any other RAID system; therefore, the files are best left where they are.
7. Scott is a system administrator who has been performing backups of his system state data every 90 days. After 85 days, a server fails because of a hard disk failure. Scott installs a new hard disk and then reinstalls Windows Server 2003. When this is complete, he intends to restore from his last backup. Scott calls a friend to refresh his mind on the correct steps, and he is surprised when his friend advises him that his backups are too old and that he is better off running Dcpromo. Scott doesn’t agree with this. Who is correct?
• A. Scott is correct. The age of backed-up files does not matter.
• B. The friend is correct. AD has a time limit of 30 days on AD restores. Data that is older than this will be replaced by the AD replication process anyway, so Windows 2003 prevents it from being restored.
• C. Scott is correct. Although the data is old, he can rely on AD replication to clear up any problems that might arise.
• D. His friend is correct. Because the backed-up files are older than the garbage-collection process, Scott could introduce inconsistencies into AD.
8. By default, garbage collection takes place on a system every 60 days. The DCs in Eric’s network have plenty of disk space. In addition, he would like to extend the usefulness of his backups. He decides to change the garbage-collection process to occur every 90 days. Which tool will Eric use?
• A. Eric will use ADSIEdit to change this.
• B. Eric will use NTDSUtil to change this.
• C. Eric must use NTDSUtil and AD Domains and Trusts to change this.
• D. Eric must use AD Domains and Trusts to change this.
9. Moira is a system administrator for an insurance company. Moira accidentally deleted an OU and wants to get it back. Fortunately, she performed a backup of AD one hour before the deletion. Moira starts the DC and does a restore. When she is done, she restarts the server. The server comes back perfectly. However, within 30 minutes, the OU she has just restored is again deleted. Why did this happen?
• A. Although it is possible to get this object back from a restore, it must be an authoritative restore. Moira must have performed a normal restore.
• B. The backup worked fine. However, because the object had previously been deleted, it must now be re-created. This assigns a new SID and allows the object name to be reused.
• C. Once an object is deleted, it is gone forever. Moira should rename one of her current OUs so it is the same as the deleted object.
• D. Moira must wait. AD replication follows a prescribed methodology. Although it looks like the object is deleted, after an hour or so, replication will stop, and the object will be restored again.
10. Duncan is the only IT person for a small music retail store, doing network administration among other IT-related tasks. He performs full backups weekly and daily incremental backups of his sole DC. His DC is running on a workstation class machine without a RAID set for the disks, and the one physical disk the DC contains fails. Even though he only has a single DC, he has to create a large number of customized groups and policies to automate things that Duncan does not want to lose, if possible. How can he restore his only DC?
• A. Duncan should reinstall the OS on a new drive and then perform normal restore of the System State data.
• B. Duncan should reinstall the OS on a new drive and then perform an authoritative restore of the System State data.
• C. Duncan should reinstall the OS on a new drive and then perform a primary restore.
• D. Duncan should reinstall the OS on a new drive and then just run dcpromo and manually re-create his users, groups, and policies.
Answers to Exam Cram Questions
1. A, B. Before performing a defragmentation of the AD database, it is a good idea to perform a backup first. After this is done, a defragmentation can take place. Answer C is incorrect because moving the AD database is a decision made outside of the process being considered here. That is related to performance and/or capacity requirements. Answer D is incorrect because convergence of the changes will happen regardless of whether additional administrative tasks are being performed.
2. A, D. Two of the most common reasons to move the AD database are to optimize performance by moving it to a dedicated physical hard disk and for the purposes of defragmentation. Answer B is incorrect because moving the database to a different partition on a RAID-5 controller does not mean the data is being moved to a different physical hard disk. The DC would still suffer from disk contention. Answer C is incorrect because the correct procedure for creating a new DC is to run Dcpromo.
3. D. There are two files that exist simply to consume disk space. If needed, they are deleted to allow AD to function. Answer A is incorrect because the relatively low weekly consumption, along with the two files, will ensure the server will stay up for more than a week. Answer B is incorrect because there is no built-in function with AD that allows it to lock hard disks if they run out of disk space. Answer C is incorrect because, again, this function does not exist.
4. C. The current transaction log is edb.log. Answer A is incorrect because edb.chk is the checkpoint file, which keeps track of what transactions have been written to the Active Directory database versus transactions that still need to be committed. Answer B is incorrect because ntds.dit is the Active Directory database. Answer D is incorrect because it represents an archived log file. Archived transaction logs follow a similar format, except incrementing in number as the 10MB logs fill. Answer E is incorrect because res1.log is the first reserved log used by Active Directory if disk space gets too low to write additional transaction logs.
5. B. Mike would have to perform an offline defragmentation of the database to gain back the space. Answer A is incorrect because, although tombstoning exists as described, it does not affect the space consumed by the database file. Answer C is incorrect because waiting will not change the end result. Answer D is incorrect because backing up and restoring data will not change the overall file size.
6. B. When considering moving the AD database file, Dennis should consider many factors, not just performance. Answer A is incorrect because moving the database can be a good idea. Answer C is incorrect because Windows Server 2003 will never move the database automatically. Answer D is incorrect because RAID-5, although widely used and effective, is not the fastest performing member of the RAID family for reads and writes.
7. D. You can adjust the garbage-collection process to fit in with a backup schedule. However, you should never attempt to restore data from a backup that is older than the garbage-collection process interval (default, 60 days). Answer A is incorrect because the age of the files does indeed matter. Answer B is incorrect because there is no 30-day limit to restores. Answer C is incorrect because AD replication will not fix the bad data.
8. A. Eric will use ADSIEdit to change the garbage-collection process. Answer B is incorrect because, although NTDSUtil has many uses, changing the garbage-collection interval is not one of them. Answers C and D are incorrect because Active Directory Domains and Trusts is a tool used for domain management and has no role here.
9. A. An authoritative restore would allow the object to be restored and would force it to be replicated out to all other DCs. If this is not done, AD replication will detect that the object has come back and will simply have it removed. Answer B is incorrect because objects can indeed be restored with their original SIDs. Answer C is incorrect because renaming an OU would not restore all the permissions and members that once belonged to the original OU. Answer D is incorrect because replication would not fix this problem without an authoritative restore taking place.
10. C. When no other DCs are available, you perform a primary restore to recover the domain from backup. Answer A is incorrect because a normal restore needs another active DC on the domain in order to recover. Answer B is incorrect because an authoritative restore is designed to restore only a portion of AD and then overwrite other DCs with this restored data. Answer D is incorrect because it would require much more work and is unnecessary when a primary restore would get the domain back to a state shortly before the disk failed.
Need to Know More?
Jones, Don, and Mark Rouse. Windows Server 2003 Delta Guide. Sams Publishing. Indianapolis, IN, 2003. ISBN 0789728494.
Morimoto, Rand, et al. Windows Server 2003 Unleashed. Sams Publishing. Indianapolis, IN. 2003, ISBN 0672321548.
