Objectives
This chapter completes the coverage (which was partially completed in Chapters 5 and 6) of the following Microsoft-specified objective for the Designing a Microsoft Windows 2000 Directory Services Infrastructure exam:
The purpose of this objective is to get you familiar with the new Windows 2000 security features. There's a vast number of new and different security mechanisms in Windows 2000. It is essential that you know and understand these features as you plan and design a Windows 2000 directory services integration.
Outline
Public Key Infrastructure (PKI)
Perspective on the Exam Objective
Study Strategies
Read as much as possible about Kerberos. This chapter contains a bit more than an overview, but to really get a good handle on this complex authentication protocol, you should read the outside resource material suggested at the end of this chapter.
Read as much as possible about PKI. Again, this chapter gives you some level of detail, but you will serve yourself well to read the suggested material at the end of this chapter for a more in-depth understanding.
Make sure that you do Exercise 7.2 to get an idea of how to install Certificate Services. We recommend you even take that exercise further and set up a standalone root CA and a subordinate CA.
Security in an organization is essential for protecting the organization's data and other intelligence that may be in demand external to the organization. There has also been recent need to further secure areas of the internal network from current or past employees. All it takes is one disgruntled employee to reveal a secret to a competitor.
To create an effective security plan, you must consider every aspect of security. We'll emphasize securing Active Directory since directory services is the focus of this book. We'll open this chapter with some insight as to why security is so important, and how the Internet has exposed some companies' assets to the world without them even knowing it.
Determining what an organization has implemented in terms of security can be a daunting task. For this reason, it is important to solicit the help of the internal team (if it exists) responsible for securing the network.
We'll focus on Windows 2000 and its top-notch security infrastructure and when appropriate discuss how some implementations of NT security map up to Windows 2000. We'll discuss security in the areas of authentication, Active Directory, data transmissions, and the Internet.
We'll close with a section on configuring security in the enterprise using the built-in Windows 2000 security toolset and Group Policy Objects.
OLC is a company created by the Indiana Bureau of Motor Vehicles to provide a new service to licensed drivers. This new service provides drivers the opportunity to renew licenses and license plates over the Internet. OLC is an extension of the Indiana Bureau of Motor Vehicles and therefore shares the bureau's records database.
The pressure from a newly elected "high-tech" governor to provide these services caused the OLC development team to rush delivery of the system. In doing so, it did not implement adequate security and has recommended to OLC that the bureau implement new security features.
"There is no certificate-based security on this Web site. All traffic goes through port 80 and is unencrypted. This is true for all personal information, license numbers, credit card info—everything."
"When you have the government pressuring you to get something done, well, you get it done. This new "high-tech" guy in charge now unfortunately knows just enough about technology to be dangerous. If he'd give us the initiatives and let us manage the development the right way, we'd make him look a lot better."
The system was developed using Active Server Pages (ASP) and Dynamic HTML (DHTML), which work together to provide user interface functionality, and an ODBC connection to the state's UNIX-based Informix database. The entire Web system runs on a Windows NT 4.0 platform and uses a TCP/IP connection (via ODBC) to the database.
"My responsibility is to pull data from the Informix database and process it. I use an IP connection to the UNIX side and have to log on to both the UNIX OS and the Informix database. Seems a little too secure to me!"
"Wow! I registered both cars in a matter of 10 minutes. That sure beats sitting in the BMV office for three hours. I don't know why anyone would ever use the offices anymore—I really don't. This system is awesome. One thing that concerns me is I didn't see that little padlock icon I see on other sites where I use my credit card. I sure hope nobody stole my credit card number while I was doing this bit of business with the state government."
OLC would like to move the Windows NT 4.0 platform to Windows 2000 to take advantage of several security enhancements. Because internal OLC employees need to connect to the Informix database to query for new records, they must log on to the UNIX environment with different usernames and passwords. OLC would like to provide single sign-on services to its employees.
"We've been patiently waiting for Microsoft to release Windows 2000. Looks like the time is finally here. We are going to take advantage of the early adopters program and implement Windows 2000 throughout our organization."
"We're allowing OLC to do just about anything they want. I am really happy with my counterpart over there and truly believe he will do the best thing. Because we see the way people get their renewals and registrations changing to a computer-based operation, we've reallocated 50% of our funds to OLC."
Although measures were taken to make the code in the system secure, none were taken to secure the Web site or any data transmissions. OLC would like to provide authentic and secure connections for licensed drivers as they utilize the online services. Additionally, data connections and transmissions within the OLC offices must be secured at all times to prevent any possibility of eavesdropping.
"I want to make sure that even if someone did penetrate our internal network, he couldn't decipher what was traveling across the wire. To do that, we plan to require secured connections between all computers. For our external visitors—the drivers of Indiana—we want to make sure that everything they transmit is guarded."
Performance is not too much of a concern in the OLC environment. New state-of-the-art servers and networking backbone are in place and working at optimal efficiency.
Since a team of developers wrote all code internally, OLC can easily maintain the system itself. All code must be checked in and out using Visual Source Safe, and standard code maintenance procedures are in place.”
"I am working on cross-training the OLC Administration team on the UNIX toolset for the administration and maintenance of the UNIX environment. I am scheduled to assist in the implementation of Windows 2000 and in doing so should be cross-trained on the Windows 2000 security toolsets."
Encryption systems, firewalls, and other security-related devices are extremely important in defining infrastructure security, but the most critical component is the server operating system. There are several variables, such as cost, maintainability, and impact on the business environment that must be weighed as corporations implement security plans across the network.
The Internet is driving organizations to open up and interact with vendors, partners, and customers using new and often unproven technologies. To remain competitive, corporations quite often end up trading a well-thought-out security plan for just simply getting a server on the Internet to do eCommerce, a risk that could end up costing quite a bit more than the amount of profit the Internet can generate.
This drastic change in business is what causes some to expose too much of the wrong information to the wrong people. To implement a solid security plan, a security implementer must always be of the mindset that a hacker is out there, looming, waiting to break in and steal vital confidential documents. Companies such as OLC that are under pressure to deliver that new product or service swiftly often underestimate the value of security.
Disgruntled employees are dangerous. They know the environment and the people within it, and could cause harm without the proper precautions in place. Take, for example, the case of Iva Bincanned, a network administrator who has been with a company for a number of years. She developed relationships with other employees and was generally liked among her peers. When she was given a pink slip due to downsizing, she became very angry and wanted revenge. Because she was an administrator, it was easy for her to create a backdoor account she could use to access the network. When the other network administrators deleted her account, they did not delete her backdoor account. Iva dialed up the night she was let go, logged right onto the system, and proceeded to delete everything she had access to. She had given that account domain admin permissions.
Cases similar to Iva's happen every day. That's why security is so critical. Could this have been prevented? Probably.
Security begins with the authentication process. Within Windows 2000, the authentication process starts with interactive logon. Interactive logon is the process of identifying a security principal (a user) against a domain or local machine account. Windows 2000 handles the security principal's security credentials transparently after a single successful logon. The transparent process is referred to as network authentication, a process by which Windows 2000 confirms security principals' identities with network resources.
Note
Security Principal . Microsoft uses the term security principal to describe any entity that can initiate action. So, human users are considered security principals, and so are computers and services.
Windows 2000 authentication supports three core protocols: NT LAN Manager (NTLM), Kerberos, and Secure Sockets Layer/Transport Layer Security (SSL/TLS).
The NTLM authentication protocol exists in Windows 2000 for the primary purpose of authentication with previous versions of Windows. NTLM is the core authentication protocol for Windows NT 3.5x and 4.0. You should determine whether you're going to carry on with support for NTLM, because you do have the opportunity to remove it from a Windows 2000 environment. When deciding whether to keep NTLM around, use Table 7.1 as a roadmap.
Table 7.1. Considerations for Removing NTLM
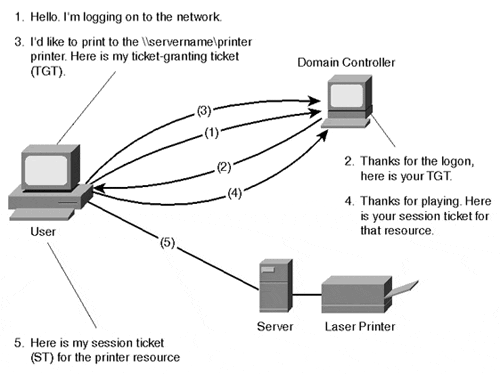
Figure 7.1 graphically represents the NTLM authentication process.
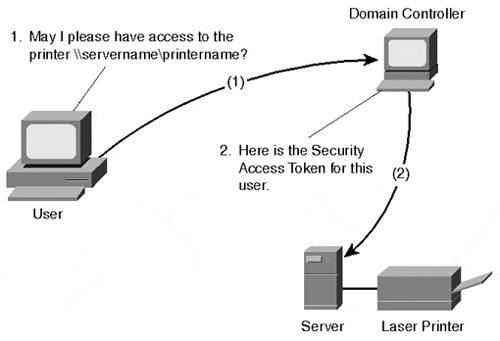
Figure 7.1. The NTLM authentication process is based on security access tokens granted by the domain controller each time access to a resource is needed.
Note
Kerberos Authentication in Windows 2000 . The Kerberos implementation in Windows 2000 conforms to Internet RFC-1510.
Kerberos is the default Windows 2000 authentication protocol. An entire book could be written about it. This section, as long as it may be, is really just a detailed overview of the protocol's implementation. We'll cover features of Kerberos throughout this chapter and, by its end, you should have a good understanding at where it fits within the security and authentication architecture of Windows 2000, as well as how it provides authentication services outside Windows 2000.
MIT Kerberos version 5 replaces NTLM as the default authentication protocol for Windows 2000. Kerberos is an industry-standard protocol that is supported by a wide variety of platforms. The Kerberos protocol defines the interactions between clients and its authentication service, the Key Distribution Center (KDC). The KDC uses Active Directory as its accounts database. The benefits of using Kerberos are as follows:
Faster session establishment. . An application server does not need to connect to a domain controller to validate credentials and authenticate a client. This enhances the scalability of application servers and allows them to concentrate on providing application services, not authenticating users.
Delegation of authentication. . This is the ability for one back-end server to impersonate a client and make connections with other back-end servers on behalf of that client.
Transitivity. . Users can authenticate anywhere in a domain tree because of the distributed nature of Kerberos and its KDCs. The KDCs in each domain trust tickets issued by other KDCs in the tree.
The name Kerberos comes from the Greek mythological figure "Cerberos," a fierce, three-headed dog that guarded the gates of the underworld. The three heads of Cerberos map to the three pieces of Kerberos: client, server, and trusted intermediary (the KDC).
Kerberos is a shared secret authentication protocol. This means that if only two people know a secret, then either person can verify the identity of the other by confirming that the other person knows the secret. For example, suppose Lea wants to send Rex a message, and Rex wants to make sure that message is from Lea before he acts on it. They decide to use a password to solve this issue. If Lea can somehow let Rex know she knows the password without flat-out telling him, the process is easy. The problem is that this can't be done securely. The logical way is to send the password bundled with the message, but then anybody sniffing the wire can intercept it. She could encrypt it, but would have to send the decryption key for Rex to unlock it, which would defeat the purpose.
Kerberos secret key cryptography solves this issue. Rather than sharing a password, communicating clients share a cryptographic key that only the two of them know. They use the knowledge of this key as verification of one another's identity. The only question remaining is how do Lea and Rex agree on a secret key? The answer is a trusted intermediary known as the Key Distribution Center.
The Key Distribution Center (KDC) is a service that runs on a secure server. In Windows 2000, the KDC runs on every domain controller. It manages a database of all security principals within its realm— the Kerberos equivalent of a Windows 2000 domain. Along with other information about security principals, the KDC stores a cryptographic key known only by the security principal and the KDC. This long-term key is used in exchanges between the security principal and the KDC. It is typically derived via a one-way hashing function based on the users password. This long-term key is returned by the KDC to the requesting client in the form of a ticket-granting ticket.
A ticket-granting ticket (TGT) is a special type of session ticket used for access to the KDC's services.This TGT contains an encrypted copy of the user's long-term session key that is derived at logon time by the KDC and is sent to the client's cache during the logon process. This TGT may be used to authenticate quickly with the KDC should a client need to replace an expired session ticket, or request a new one. The TGT saves time and resources by forcing the KDC to do a database lookup of the username and return its long-term session key only once, at logon time.
When a client (Lea) wishes to talk to a server (Rex), the request (TGT) is sent to the KDC. The KDC distributes a short-term session key to the client. Lea and Rex will use this session key for their conversation.
Note
Authenticator . In protocols that use secret key encryption, a client wanting to gain access to a server or service must present information in the form of an authenticator encrypted in the secret key. This authenticator must be unique and different every time the protocol is executed. Time can be considered a good authenticator.
The data structure used to return the session key to the client is called a session ticket. The session ticket is comprised of the client's copy of the session key encrypted with the secret key that the KDC shares with the client. The server's copy of the session key is embedded, along with information about the client, in the session ticket. The entire session ticket is then encrypted with the key that the KDC shares with the server. This session ticket is then cached on the client workstation and may be used to directly authenticate with the server until it expires.
To continue the example, when Lea wants to talk to Rex now, she sends a request to the trusted authority, the KDC, which returns her a session ticket. Upon receipt, Lea extracts her copy of the session key and stores it in volatile cache (when Lea goes to sleep, she forgets everything!). To talk to Rex, she sends him the session ticket (which is still encrypted with the server's secret key), and an authenticator, which is encrypted with the session key. The ticket and authenticator together become Lea's qualifying credentials in talking to Rex.
When Rex receives a request to talk from someone claiming to be Lea, he decrypts the session ticket using his secret key. Once decrypted, he extracts the session key and uses it to decrypt Lea's authenticator. Rex will know that the request to talk came from who the sender is claiming to be if he is able to decrypt everything successfully. If so, he and Lea establish a connection and begin their conversation. Figure 7.2 describes this entire process.
The beauty of using session tickets is that the server has absolutely no responsibility in terms of remembering session tickets. It is totally on the client to retain the session ticket in its cache until the ticket expires. Another benefit is that session tickets are reusable, so every subsequent time a user needs to communicate with a server, it can use the cached copy of the session ticket for that server, as shown in Figure 7.3.
Note
SSPI . The Security Support Provider Interface defines Windows security APIs for network authentication.
Kerberos is fully integrated with the Windows 2000 security architecture for authentication and access control. WinLogon, the initial Windows domain logon service, uses the Kerberos security provider to obtain an initial Kerberos ticket. Other services, such as the redirector, use the Windows 2000 Security Support Provider Interface (SSPI) when they need to connect to the Kerberos security provider.

Figure 7.3. Once a session ticket has been issued, subsequent connections to the server only require the client to present its session ticket for that server.
Warning
Authorization Data . Keep in mind that authorization data is application service specific and does not support user authorization in heterogeneous environments.
Kerberos v5 contains an encrypted field for applications to use for authorization data in the session ticket. Windows 2000 uses the authorization data to carry SIDs for user and group membership. The server-side Kerberos security provider uses this authorization data to build security access tokens, which represent the user on the system. It can then use this data to impersonate the client before attempting to access local resources protected by ACLs.
Two additional fields, implemented as Boolean flags, are used in the delegation of authentication features supported by Kerberos. The proxy and forwarding fields in session tickets can be set to allow servers to obtain session tickets for other servers on behalf of the client.
Kerberos v5 is implemented for a variety of operating platforms and can be used to provide a single point of authentication in a heterogeneous and distributed environment. This interoperability is based on the following characteristics:
Identification of users through a common authentication protocol by principal name.
Ability to define trust relationships between Kerberos realms (equal to Windows 2000 domains) and to generate ticket referral requests between realms.
RFC-1510 compliant implementations.
Support for Kerberos version 5 security token formats for exchanges and context establishment as defined by the IETF. (See RFC-1964 for more information.)
It is possible for Windows 2000 clients to authenticate to non-Windows 2000 Kerberos KDCs and vice versa. Clients that obtain initial Kerberos TGTs from a KDC in a non-Windows 2000 domain (realm) use the Kerberos referral process to request a session ticket from a Windows 2000 KDC. This referral ticket is created by inter-realm trust relationships. This process occurs when the Kerberos security provider on a Windows 2000 KDC attempts to find authorization data to generate a token. This data is likely not available when security principals authenticate to non-Windows 2000 Kerberos realms.
In our OLC case study, when internal Windows 2000 users need to access the Informix database on the UNIX platform, the Windows 2000 KDC will recognize that resource exists on the UNIX side and will refer client requests to a UNIX realm KDC via a trust relationship. The UNIX KDC then will generate session tickets for the Informix database.
Windows 2000 implements extensions to the Kerberos protocol to provide for public key authentication. The public key authentication allows clients to request an initial TGT using a private key. To answer this request, the KDC uses a public key obtained from an X.509 certificate stored with the user object in Active Directory.
These user certificates should be issued from a trusted Certificate Authority (CA), such as VeriSign's Digital IDs or Microsoft Certificate Server. After the initial private key authentication succeeds, standard Kerberos protocols for obtaining session tickets are used to connect the client to network services. This enhancement allows for interactive logon using smart cards. It is based on a draft specification submitted to the IETF working group for review. It is the objective of Microsoft, as well as several other third parties interested in public key technology, that the draft specification be amended to the industry-standard Kerberos specification.
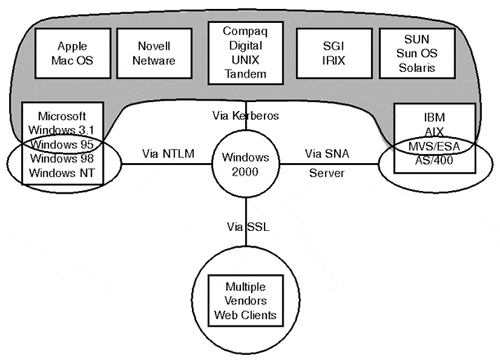
A huge benefit to having an industry standard protocol as the core for authentication and security is the ability to step outside the Windows 2000 platform by creating trust relationships with other platforms. Operating platforms that support the MIT Kerberos v5 protocol are illustrated in Figure 7.4.
Establishing the cross-platform trust with Kerberos is relatively easy, provided all the pieces are in place on both sides. The administrator creates a trust relationship between the Windows 2000 KDC and the other platform's KDC, which are in different realms. The Kerberos tickets are provided via cross-realm referrals. The Windows 2000 administrator simply sets up user accounts with rights and permissions for the incoming users to use, and that's it.
One downfall to SSO with Kerberos in a heterogeneous environment is the management of the connection. Some of the things that are managed in the background under Windows 2000 need to be manually handled in this environment. For example, when a trust is established in a heterogeneous environment, the administrator must manually synchronize keys between Active Directory and the other platform's KDC. Additionally, the administrator loses the single set of administration tools and a single repository for SSO information.
The final core authentication protocol is Secure Sockets Layer/ Transport Layer Security (SSL/TLS). Windows 2000 uses SSL/TLS and X.509 certificates to provide mutual authentication, message integrity, and confidentiality. The Windows 2000 implementation of SSL/TLS supports logon through the use of smart cards, and is used to protect connections on unsecured networks.
Support for public key certificate-based authentication allows client applications to connect to secure Windows 2000 services as a proxy for users that don't have a domain account. A single Windows 2000 account can be used to provide secure access to one or many external users.
This means businesses can easily and securely share information with certain individuals from other organizations. You may recall our section on vendor, partner, and customer relationships in Chapter 3, "Analyzing the Results of the Business Assessment." This authentication protocol is what takes advantage of the single digital identity (domain account) associated with a customer, partner, or vendor. By authenticating users external to the company in essentially the same way that internal employees are authenticated—that is, against Active Directory—administrators have a single point of administration.
We've already broached the topic, so we'll segue into Public Key Infrastructure. PKI is a capability, not a "thing." It's important that we clear up that common misconception from the get-go.
The purpose of PKI is to make it easy for businesses to use public key cryptography. Get into the mindset of thinking PKI as soon as you hear eCommerce, intranet, Internet, extranet, collaboration, or any other potentially Web-enabled service.
Public key cryptography refers to the use of two keys: a public key designed to be shared, and a private key, which must be guarded. These keys complement each other, meaning that if you encrypt something with your public key, it can only be decrypted with the corresponding private key. This works both ways. Either way, the goal of public key cryptography—the ability to obscure data in such a way that it can only be interpreted by the intended party—is achieved.
Another component of PKI includes digital signing. This task is a way to prove the origin of a piece of data. This does not provide privacy of data.
Public key cryptography provides three core capabilities that are important to businesses. These three capabilities are highlighted using some potential business cases in Table 7.2.
Note
Non-Repudiation . Achieving non-repudiation means having the capability to prove beyond dispute that someone took a particular action.
Table 7.2. Capabilities and Business Use of Public Key Cryptography
Public keys are packaged as digital certificates, which contain a public key and a set of attributes, such as the keyholder's name. These attributes are relative to the keyholder and define the keyholder's identity, what he's allowed to do, and where the certificate is valid. This binding is appropriate because the certificate is digitally signed by the issuing CA to validate its authenticity.
A good analogy when discussing certificates is a standard credit card. Your Visa card contains a unique key in the form of the credit card number. It contains attributes, such as your name and the card's expiration date, and maybe even your picture. A trusted authority issues it, and its authenticity is sealed in the magnetized strip (assuming it cannot be tampered with). Anyone who trusts the issuing bank will allow you to use the card. Of course, how companies determine whether to accept or reject your credit card is where this analogy needs a bit of help.
Note
Intermediate and Subordinate CAs . The structure of the Certificate Authority hierarchy goes from Root to Intermediate to Entity. Microsoft uses the term "subordinate" to describe any CA server that is not at the root level (hence, all Intermediate and Entity CAs). In the general hierarchy, Entity CAs are subordinates of Intermediate CAs, which are subordinates of Root CAs.
Certificate authorities are a hierarchical grouping of public key certificate servers that are responsible for signing digital certificates they issue. This hierarchy can go as deep as needed, although there always will be a finite top level, known as the root. Figure 7.5 presents a certificate authority hierarchy.
The important thing about certificate authorities is that each certificate issued by a CA must be digitally signed and certified by the next higher level of CA. So (referring Figure 7.5) if you had a certificate issued by an entity certificate authority, it would have to be signed by the intermediate certificate authority, which would have to be signed by the root CA.
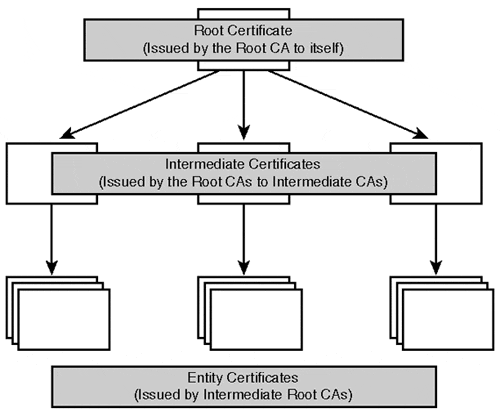
Figure 7.5. The certificate authority hierarchy may go as many levels deep as needed, but will always have a single root.
Windows 2000 provides two types of CAs: Enterprise and Standalone, which are discussed in the following sections.
An Enterprise CA is used at the root of a corporate CA hierarchy. It is typically installed if you will be issuing certificates to users or computers inside an organization that is part of a Windows 2000 domain, and hence require that all requesting users have an appropriate Active Directory-based identity. The requirements for an Enterprise CA are as follows:
Active Directory, because Enterprise CAs use Active Directory to store certificates
Windows 2000 DNS, which is required by Active Directory
Administrative privileges on DNS, Active Directory, and CA servers
Typically, Enterprise CAs are configured to issue certificates only to subordinate Enterprise CAs.
A subordinate Enterprise CA issues certificates to users and computers within an organization. It is not the most trusted CA because it is subordinate to another CA. All subordinate Enterprise CAs within a CA hierarchy are derived from a single Enterprise root CA. subordinate Enterprise CAs require the following:
If you wish to deliver certificates only external to the corporation's directory, you will install a Standalone root CA. These Standalone CAs do not require requesting parties to have Active Directory-based accounts, and in fact will not issue certificates for logon to the directory. Standalone CAs are most commonly used to issue certificates to visitors to a Web site to provide a certain level of authenticity. OLC in the case study, for example, most likely would create a Standalone CA.
The only requirement for a Standalone CA is administrative privileges to the local computer.
As with Subordinate Enterprise CAs, it is a good security measure to create Subordinate Standalone CAs to issue certificates. A Subordinate Standalone CA issues certificates to entities outside a corporation, and requires the following:
An association with a CA that will process its certificate requests; this most likely will be an external commercial CA (such as VeriSign), but also may be a Standalone CA or an Enterprise CA
Administrative privileges on the local server
You can mix and match various levels of Enterprise and Standalone CAs in your organization. You can even have multiple hierarchies—meaning multiple root CAs. Additionally, you can factor in external commercial CAs, such as VeriSign or Thawte.
There are five components that make up a complete PKI. These five components are responsible for creating, validating, transporting, and using the digital certificates that PKI depends on. These components are as follows:
Certificate Authorities (CAs). . There are two additional responsibilities a CA has beyond what we've just discussed. The first is the decision as to what attributes it will include in a certificate and what mechanism it will use to verify those attributes before issuing the certificate. Second, the CA is responsible for issuing Certificate Revocation Lists (CRLs). If an owner's private key has been compromised or the holder is no longer associated with the issuer, the CA adds it to the CRL and publishes it so clients can check it. Once published, every authorization must first check this list before approval.
Certificate Publication Points (CPPs). . CPPs make certificates and CRLs publicly available inside or outside the organization. Publishers can use any kind of directory service, including X.500, LDAP, etc. to accomplish this task. They also can publish and distribute them on smart cards, CDs, Web pages, and so on. The industry standard is clearly LDAP.
Key and Certificate Management Tools. . When were certificates issued? Who holds them? Are there any old certificates? These are all questions organizations need to address with PKI. There is a management tool in Windows 2000 that allows you to manage certificates, CRLs, and more. It's called the MMC, and you hear plenty about it elsewhere in this book.
Public Key-Enabled Applications. . A well-written PKI-enabled application will make use of public key cryptography without the user ever knowing it. A key to the successful implementation of a PKI is in the applications that use it. Microsoft Outlook, IIS, IE, and Money are just a few of the applications that are "PKI-ready" out of the box.
Hardware Support. . PKI hardware is optional. The booming market demand for PKI has driven hardware manufacturers to develop cryptographic hardware, including smart cards, PC cards, and PCI cards that offer cryptographic accelerated processing. Keep your eye on this area of PKI; you'll probably be seeing smart cards in the mainstream within a few years, as well as biometric devices, such as retinal scanners and fingerprint readers.
The Windows 2000 implementation of PKI builds on Microsoft's already robust PKI components. The foundation is built on interoperability, security, flexibility, and ease of use. The primary components of the Windows PKI are as follows:
Certificate Services. . Certificate Services are implemented as a core OS component. The service allows businesses to act as their own CA and issue and manage their own digital certificates.
Active Directory Directory Service. . Active Directory not only provides a central repository for network resources, but also is a PKI publication point.
PKI-Enabled Applications. . Internet Explorer, Microsoft Money, IIS, Outlook, and Outlook Express are all natively PKI enabled. A slew of third-party applications use the Windows 2000 PKI and are also PKI-enabled.
Exchange Key Management Service. . This is a component of the Exchange BackOffice application that allows for the retrieval and archiving of keys used to encrypt mail messages.
Standards bodies, such as the World Wide Web Consortium (W3C), the Internet Engineering Task Force (IETF), and the International Telecommunication Union (ITU) have been working hard with vested interest in promoting the interoperability between multi-vendor implementations of PKI. Microsoft has worked, and continues to work, alongside these impartial bodies to ensure the correct and fully interoperable implementation of the Windows PKI.
Table 7.3 lists the standards, definitions, and justification supported by the Windows 2000 implementation of PKI.
Table 7.3. Windows 2000 Support for PKI Standards
The Windows 2000 implementation of PKI inherits the security features built into Windows 2000. This is made possible because the major PKI components are part of the core OS. Because they rely on widely available, open Internet standards, PKI components reap the benefit of years of experience and maturity. Computer security and cryptography experts, who took significant input from computer, banking, financial, legal, and government experts, developed the security standards listed in Table 7.3. The end result is a rock-solid security infrastructure that meets the demands of real-world needs. Microsoft has been very careful to use mature security and encryption algorithms that have stood the test of time and prolonged public use. Table 7.4 lists Windows 2000's support for cryptographic algorithms.
Because Windows 2000 offers an open security architecture, it integrates well with third-party PKIs. It is important to remember, however, that because of its integration with the OS, the Windows 2000 PKI provides the best, most seamless integration with Active Directory, native security protocols, and other security services.
A fundamental relationship exists between Active Directory and the Windows 2000 security subsystem. Active Directory stores domain security policy information, such as domain-wide password restrictions and system access privileges, both of which have a direct impact on the use of the system. Windows 2000 implements object-based security, in which every object in the directory contains a security descriptor that defines access permissions that are required to read or write the object properties.
The security model provides a uniform and consistent implementation of access control to all domain resources, such as files, users, and printers, based on group membership. Furthermore, because of the tight integration between Active Directory and the security subsystem, the Windows 2000 OS is able to trust the security-related information stored with objects in the directory.
This relationship with security and Active Directory is achieved only by complete integration of Active Directory with the Windows 2000 OS.
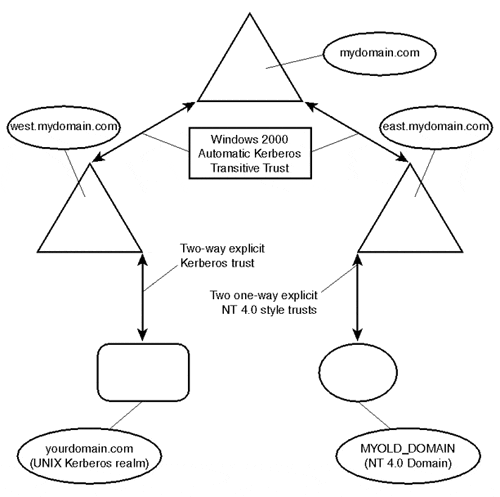
Because Windows 2000 supports the creation of automatic two-way transitive Kerberos trusts between a child domain and its parent domain within a domain tree, the security and management tasks are greatly reduced in this area. With Windows NT 4.0, administrators not only had to manually create the trust and secure it with a password, but also had to manage two distinctly different SAM databases full of user credentials and, in most cases, had to synchronize user accounts and passwords with both domains. With Kerberos authentication under Windows 2000, a user can authenticate across domain boundaries to anywhere within the domain tree or forest without administrative intervention and, most importantly, without needing an account setup on the other domain.
Active Directory does support the creation of one-way manual "explicit" trust relationships. These types of trusts are still required for interoperability with down-level Windows NT domains and with other operating platforms. An explicit trust is required in our case study to integrate the UNIX and Windows 2000 operating systems. Figure 7.6 illustrates Windows 2000 trust relationships.
A highly touted new feature of Windows 2000 and Active Directory is the ability to delegate administrative authority. This process allows administrators to deputize special users or other administrators with granular and specific administrative duties. Granting the technology contact from a business unit the ability to reset passwords for a subset of users in that business unit would be a good example of delegated administration. This person would have no additional administrative powers—just the ability to reset passwords for a specific set of users. Imagine what you could do with this! In Windows NT, the only way to delegate any administrative authority was to give the person or persons requesting authority too much by sticking them in the Domain Admins group (or other built-in group), or to flat-out create another trusted domain. Windows 2000 has fixed that problem and then some by incorporating the Delegation of Administrative Control Wizard. We'll discuss delegation in much more detail in Chapter 12, "Designing an OU and Group Policy Management Structure."
How many times have you as an administrator needed to allow a contractor the right to temporarily create user accounts, or perform some other administrative function, in your Windows NT domain? If you've ever been in that situation, you realized one of Windows NT's downfalls: no granular control. In the case of creating user accounts, it was literally an all-or-nothing Domain Admin role. Not a good position to be in when that contractor you trusted with the Domain Admin permission burns you by doing something stupid!
Note
Active Directory Objects . Every object in Active Directory contains a security descriptor. The security descriptor (SD) contains an Access Control List (ACL) which is a list of entries that grant or deny specific access rights to individuals or groups.
Windows 2000 incorporates an incredibly fine-grained access rights model. This model allows administrators to grant or deny access rights on the ACL of an object at the following levels:
To the object as a whole, which includes all properties of the object
To a grouping of properties, defined by property sets within the object. (Property sets are defined on the property set attribute of a property in the schema.)
To an individual property of the object
By default, when an object is created in Active Directory, the creator of the object is granted uniform read/write access to all properties of the object.
Container objects also provide granular access with respect to who has permission to create child objects. For example, you can define who in the organization can create child objects, such as other containers or user and printer objects. This is a fabulous method of keeping Active Directory clean, because you can allow delegates to create only what they need.
Inheritance of access rights defines how access control defined at higher-level "parent" containers of the directory flows down to "child" containers and then to "leaf" objects. Generally speaking, there are two models for implementing inheritance: dynamic and static.
Dynamic inheritance uses an algorithm to define the implicit and explicit permissions on an object. The explicit permissions are those assigned directly to that object. The implicit permissions are defined to parent containers of the object and are applied to it through inheritance. This greatly simplifies administration by allowing an administrator to effectively change the access permissions on thousands or millions of objects by simply changing them on the parent container of the objects. The drawback to this method is that each and every time a client requests read/write access to an object, Active Directory must dynamically calculate permissions on that object. In a large hierarchical OU structure, this process could slightly degrade performance.
Windows 2000 implements a static form of inheritance and refers to it as Create Time inheritance. This form of inheritance allows you to define the access control information that flows down to child objects of a container. When an object is initially created, Windows 2000 merges the default access rights with the rights that are inherited from the parent container. New access rights applied to parent-level containers may or may not be inherited by the object, depending on the options set within the object.
We'll discuss more about how this all works in Chapter 12.
Because you have such a high degree of flexibility in securing Active Directory, you should take great care in designing a security standard.
As with Windows NT, you should always assign permissions to groups rather than users. The administration of user-level permission assignments, especially in a large corporate environment with several administrators, is cumbersome and simply not a good practice.
In addition to using groups to assign permissions, you should also set a standard for where you assign them. For example, don't make it a practice to assign permissions at the property level. As with user-level permissions, property-level permission assignments can make for an extremely difficult environment to keep a good handle on. You should consider assigning inheritable permissions at the domain level to enforce global security standards, and at the OU level to enforce decentralized security needs. Of course, where you choose to standardize your inheritable permissions will reign heavily on your administrative needs.
Be careful with the Deny permission. It works the same way the No Access permission works in the NTFS file system. A viable use of this permission is to deny a user in a group access to a particular object without removing the user from a group.
Keep a close eye on the users in the organization who have Domain Admin or Enterprise Admin permissions. Only a select group of individuals should have this type of access. Periodically, do a permissions audit to uncover any forgotten permissions assignments.
As with any NOS, change the Domain Admins group members' passwords frequently, and make them difficult to crack.
Your security policy should extend to the data transmissions flowing across the LAN and WAN. In Windows 2000, you can encrypt standard data transmissions using IPsec. IPsec is made up of the following four components:
Encryption and encapsulation
Authentication and anti-replay
Key management and digital certificates
Support for unique digital certificates
IPsec stores its policy information in Active Directory. An IPsec policy consists of rules, filters, and negotiation policies that are retrieved from Active Directory when a system starts. IPsec is disabled by default, so to begin using it, you'll either have to create your own policy or choose from one of the three predefined policies:
Client (Respond Only). . This is used for computers that should not secure communications normally. For example, intranet clients may not require IPsec, unless it is requested by another computer. Implementing this policy on a computer enables it to respond appropriately to requests for secure communications via its default response rule, which tells it to negotiate with computers requesting IPsec. Only the requested protocol and port traffic for the communication is secured.
Server (Request Security). . This policy is used for computers that should normally secure communications, for example, servers that transmit sensitive financial data. If a computer employing this policy accepts unsecured data, it always requests IPsec in subsequent communications from the original sender. If the other computer is not IPsec-enabled, communications will continue unsecured.
Secure Server (Require Security). . This policy is used for computers that always require secure communications—for example, servers that transmit highly sensitive data such as top-secret classified government data. Computers employing this policy will reject incoming unsecured communications requests, and outgoing data is always secured. No unsecured communication is allowed by this policy.
All of the predefined policies are designed for computers that are members of a secure Windows 2000 domain. They may be assigned as is without further action, modified, or used as a template for defining custom IPsec policies.
In our case study, OLC requires secure data transmissions internally. They have the option of using the predefined Secure Server IPsec policy, or customizing their own. Whatever they choose, they must require encryption on all data transmissions.
Similar to the predefined policies, the default response rule for an IPsec policy is provided without need for modification. It may be activated without further action or customized to fit specific needs. It is automatically added to each new IPsec policy you create, but not automatically activated. The purpose of the default rule is to prepare any computers that do not require security to respond appropriately when another computer requests secure communications.
Similar to the predefined rules, predefined filter actions are provided for activation without any need of modification. Like the policies and rules, the filters can be modified to fit specific needs, or used as a template to create additional customized filter actions.
You should now have a fairly good understanding of the security technology associated with the Windows 2000 Active Directory. Now how do we use and enforce this security throughout the enterprise? The answer lies in the integration of the security configuration toolset with the group policy infrastructure. Group Policy (which will be discussed in more detail in Chapter 12) allows you to establish security policies within Group Policy Objects (GPOs), which may be assigned at the site, domain, or OU levels in Active Directory. That said, the integration of the security configuration toolset with GPOs allows you to propagate centrally managed security policies out to all Windows 2000 computers at a site, domain, or OU level.
Note
Group Policy . Administrators use Group Policy to specify options for managed desktop configurations, software deployment or publication, and more for both computers and users. The security settings extension in Group Policy that we'll focus on here applies to computers only, with the one exception being public-key policies, which may be assigned to a user.
As you've probably figured out by now, pretty much everything is policy-based in Windows 2000. If you skipped learning Windows NT policies because you didn't use them, you're somewhat at a disadvantage, but not totally. The differences between Windows NT policies and Windows 2000 group policy are pretty big in terms of configuration and ease of use, and therefore can be picked up pretty easily.
Security policy defines a security configuration file that is stored as part of a Group Policy Object. You create these files using the Security Configuration Toolset. You can configure several types of security configuration files using the security configuration editor:
Account policies. . Account policies define the policies that affect user accounts. You can configure password, account lockout, and Kerberos policies here. Since workstations and member servers contain local accounts databases, password and account lockout policies can be configured locally as well as domain-wide. Kerberos policies do not apply to local accounts databases. In all cases, domain policies override local account policies.
Local policies. . Can configure local audit policy, user rights, and various configurable security options on a Windows 2000 system.
Event log. . The event log allows you to configure size, access, and retention parameters for application, system, and security logs.
Restricted groups. . You can apply policy to groups that are security sensitive, such as the Administrators group.
System services. . You can now apply security policies to individual system services and grant access to specific users to start, stop, or pause the service (refer to Figure 7.4).
Registry. . You can configure registry key level policies to provide granular control to each key.
File system. . You can configure access permissions for file system objects.
Public key policies. . Can configure encrypted data recovery agents for the Encrypting File System (EFS) domain-wide root and trusted certificate authorities.
IPsec policies. . Can configure the IPsec policies for computers within a given scope.
These policies can work together to form policies with a large and generalized scope, such as a domain-wide policy, or they can be saved as security configuration files with a specific purpose, such as defining a different minimum password length for a subset of users. These security files may then be attached to OUs as Group Policy Objects.
There are three places—local machine, domain, and OU—where policies can be applied, which means they must carry some sort of priority ranking when being applied since a computer may exist in a domain under an OU. The order of precedence for applying security policy is as follows:
Local policy
Domain policy
OU policy
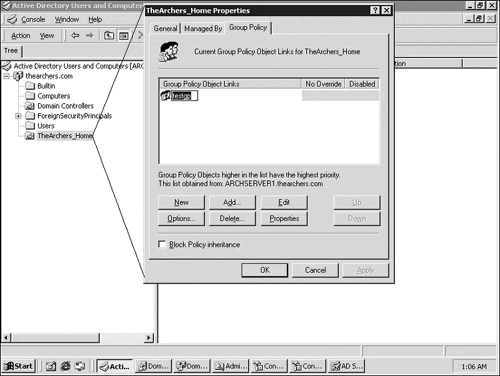
Local policy, which is defined on the computer itself, carries the least precedence. The domain policy sits in the middle, and the OU policy carries the most weight. The domain policy is applied to all computers in a given domain and then any specific OU policies are applied for computers that exist in OUs with defined policies. The net effect of all this is if there are conflicting policies, the domain policy overrides the local machine policy, and the OU policy overrides the domain policy. Figure 7.7 shows a GPO being created for an OU.
It is important to note here that unlike previous versions of Windows NT, Windows 2000 domain policy actually filters down to the workstation level. For example, in Windows NT 4.0 when you had a domain policy that forced the domain password to 15 characters, it was applied only to domain controllers (primary and backup). In Windows 2000, the same domain-wide password policy also applies to your workstations and member servers local accounts database.
Note
Registry Mode . System policy in Registry mode could be run under Windows NT to directly update a computer's registry; however, this was dangerous, and meant that administrators had to use two different modes to complete an update to a policy if they wanted to apply it immediately.
It is no secret that Windows NT system policies were cumbersome to create, implement, and manage. Microsoft has done a superb job in re-engineering policies and integrating them with the core OS in Windows 2000. Do not let the name "Group Policy" fool you. These policies really have nothing to do with groups, other than when you implement them, you typically "group" similar computers or users together in an OU and apply a Group Policy Object to it.
One of the key fundamental differences between NT system policies and Windows 2000 Group Policy is in the way they are applied. With Windows NT System Policies, an administrator uses the System Policy Editor in policy file mode to create an NTCONFIG.POL file and must save it the \SERVERPDC netlogon share. The policy is not applied until the user logs on.
In Windows 2000, Group Policy has one mode that is somewhat of a cross between Policy File mode and Registry mode. Modifications made to a GPO are saved immediately to that GPO, but the change is not immediately implemented on the target machines. Instead, GPOs are refreshed automatically at given intervals during a process called policy propagation. Policy propagation is triggered by the target computer every 5 minutes for domain controllers, and every 60–90 minutes for member servers and workstations. The net benefit of this is in administration. Administrators have only one place to configure policy and one mode to configure policy in. The rest "just happens."
During the initial configuration of Active Directory, the domain security GPO is created and attached to the domain object. The domain security policy is just that: a policy that is applied by default to all computers within a domain. The domain security file describes the following three security policy group settings:
Password policy
Account Lockout policy
Kerberos policy
Step by Step 7.1 will assist you in opening the default domain security policy. You must be logged onto your Windows 2000 domain as an administrator for this to work.
Expand the Account Policy item and then click on one of the three settings to view the default domain security configuration. Figure 7.8 illustrates the domain security policy.
By default, all Active Directory domain controllers are added to the Domain Controllers OU. The domain controller security policy defines the security policy common to all domain controllers in that OU. The default domain controllers security policy is created when the first Active Directory domain controller joins the network. It can be opened in much the same way the default domain GPO can, the only difference being that instead of selecting properties from the domain object, you select properties from the domain controllers OU. Refer to Step by Step 7.1 and make the aforementioned replacement to view the default domain controller GPO.
The most significant settings made in the default domain controller GPO are the user rights assignments. User rights were moved out of the User Manager for Domains (in Windows NT 4.0) and into policy-based administration (in Windows 2000). Audit policy and security options policy are also defined in the default domain controllers GPO. This policy is applied with higher precedence than the default domain policy. Figure 7.9 shows the domain controller security policy settings.
The account policies security area is unique in terms of how it takes place on computers in the domain. All domain controllers receive their account policies from GPOs configured at the domain node, no matter where the domain controllers computer object lies in Active Directory. This is to ensure consistency across the domain for all domain accounts.
As far as workstations and member servers in the domain go, they follow the normal GPO hierarchy with account policy. Remember that Windows 2000 propagates the account policy down to the workstation level, so even the (Windows 2000 Professional) workstations local accounts database adheres to the domain policy.
Note
Local Accounts Policy . It is possible to override the default domain policy on a workstation or member server. To do this, you add a workstation or member server's object to a new OU and apply a GPO to that OU with specific changes to the accounts policy. Because OU GPOs are last to be processed, their settings end up being applied even when previous GPOs contain conflicting settings.
Security is such a wide and deep topic that in order to get a good grasp on it, you need to put it in the right context. Our exam objective states that we need to analyze (existing and planned) security considerations. The content of this chapter has really focused on the major Windows 2000 security features centered around Active Directory because the focus of the exam is on designing a directory services infrastructure. You could argue that a directory services infrastructure really covers a lot more than Active Directory, so it would be in your best interest to read some of the reference material listed at the end of this chapter.
Some questions you may end up seeing on the exam are questions relating to defining a security policy. Security policies must address the following:
Physical and location security
Creating a security policy document
Reacting to security exposure
A security policy includes guidelines and standards whose purpose is to eliminate security breaches that can lead to certain kinds of attacks and threats. Our case study in this chapter is a good example of a company in need of a security policy. OLC provides a great service, but without the proper security in place, the company could be heading for disaster. One thing is for certain; it is extremely difficult to cover all bases of security and implement a completely secure system without trading off some sort of functionality. For this reason, most companies, when forming a security policy, define what security means to them. This could be totally different from what it means to the next company. A security policy will address the following types of questions:
What is acceptable network conduct and what is not?
Who has access to what and why?
Who is responsible for maintaining security policies?
What data needs to be protected and from whom?
How will security incidents be responded to?
Will we have a password change and history policy?
Who will be allowed access to the data center?
Of course, this is not an exhaustive list, but should get you thinking along the right lines.
The Internet is driving the need for increased security in all aspects of the computer network. Smarter software and people in the business means there are smarter hackers on the Internet.
Windows 2000 consists of three types of identity authentication: NTLM, Kerberos, and SSL/TLS. It wants to use Kerberos by default, but can only do so in a pure Windows 2000 environment. NTLM is still around for backward compatibility. Finally, SSL/TLS and X.509 certificates are available for certificate-based authentication.
Windows 2000 contains native support for public key infrastructure (PKI). The following make up the Windows 2000 PKI:
Certificate Services
Active Directory Directory Services
PKI-enabled applications
Exchange Key Management Services
Windows 2000 also includes native IPsec capabilities and has three built-in IPsec security policies that are integrated with the Group Policy.
The default domain and default domain controller security policies can be located by right-clicking the domain name and domain controller OU, respectively, within the Active Directory Users and Computers add-in.
The default domain policy contains settings for account security, such as Kerberos, account lockout policy, and password policy, which are implemented already by default for every computer in the domain. Likewise, the default domain controller security policy contains settings for the local policies on all domain controllers. Local policies define audit policy, user rights assignment, and security options.
Read the related reference material that has been mentioned; it's especially important for this chapter because the topic is so broad. Also, be thinking about how you're going to move your existing environment to Windows 2000 in terms of security. As always, having something real-world to which you can relate the chapter content will provide you great benefit.
This exercise walks you through creating a GPO to specify security settings that will override the domain password security policy for a given OU.
Estimated Time: 10 Minutes
Open the Active Directory Users and Computers utility on your domain controller.
Create a new user in the default Users container. Name this user
Exercise71and make sure you give it the same logon name. You will use this user throughout these exercises. Do not assign this user a password and do not make any changes to the password configuration window.Create an OU by right-clicking the icon for your domain, then selecting New and Organizational Unit.
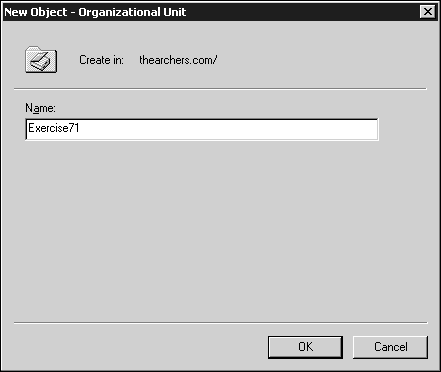
In the Name box (see Figure 7.10), type
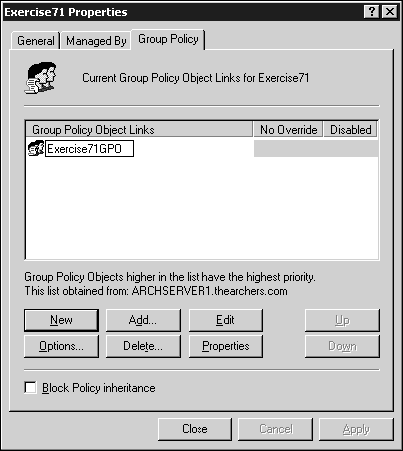
Exercise71and click OK.Right-click the Exercise71 OU and select Properties. Click on the Group Policy tab (see Figure 7.11) and click the New button. Name your new GPO
Exercise71GPO.Click the Edit button to open the Group Policy Editor. Under Computer Settings, expand the Windows Settings folder, then expand Security Settings.
Expand Account Policy to reveal the Password and Account Lockout policies.
Click on the Password Policy (the password policy choices are shown in Figure 7.12) and change the Minimum Password Length to 7 characters.
Change the Passwords Must Meet Complexity Requirements option to Enabled.
Note
Default Password Policy . By default, the password policy is defined in the domain security policy. To open it, right-click the domain object, select Properties, click the Group Policy tab, and edit the default domain policy GPO. Navigate to the password policy area to see the previous defaults.
Close the Group Policy configuration window. Close the Exercise71 OU properties window.
Click on the Users container to display your new user.
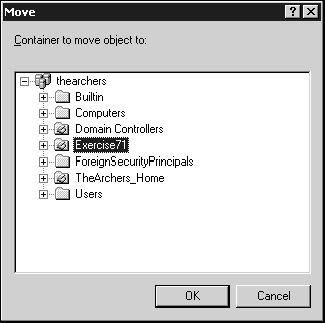
Right-click the Exercise71 user and select Move from the context menu. Choose the Exercise71 OU as the destination, as in Figure 7.13.
Click OK to complete the move and then click on the Exercise71 OU to verify your user is there.
Note
Log on Locally . If you only have one computer and are using it as both the AD server and a "workstation," you'll first need to add the Exercise71 user to the Log on Locally right. You can do this by right-clicking the Domain Controllers OU, selecting Properties, selecting the Group Policy tab, editing the default domain controllers OU, and navigating to the User Rights Assignment local policy.
To see the results of your changes, log on to the Windows 2000 domain as Exercise71. Press Ctrl+Alt+Del and click the Change Password option. Attempt to change your password to something fewer than 7 characters. You should not be allowed. If you are, you may have to wait a bit for the policy settings to take place. Move on to Exercise 7.2 and check back later.
This exercise walks you through the process of setting up a certificate authority for your organization. You must be logged on to a domain controller with administrative privileges and have Internet access for this exercise to work properly.
Estimated Time: 30 Minutes
In the Control Panel Add/Remove programs utility, add Certificate Services from the Add/Remove Windows Components area.
Click Next. Accept the warning about not being able to rename the computer or join/remove it to/from a domain.
In the Certification Authority Type window (see Figure 7.14), select Enterprise Root CA. Click Next.
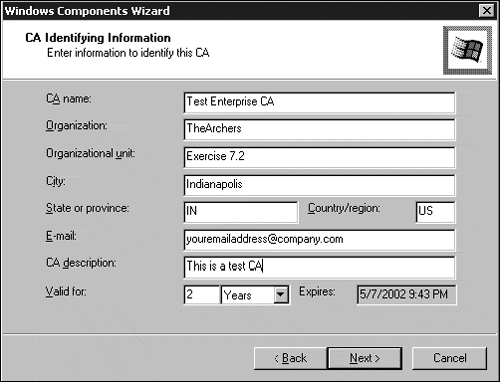
On the CA Identifying Information window, fill in information similar to that in Figure 7.15. The CA name is important because it will identify the CA in Active Directory. Click Next when you're done with this window.
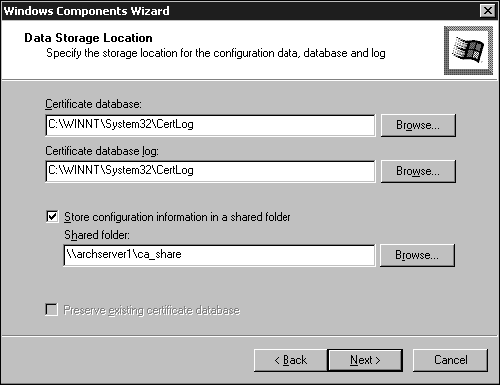
On the Data Storage Location window (see Figure 7.16), note the locations of the certificate database and log files. Then click the check box to allow certificate configuration information to be stored in a shared folder. You can point the management utilities to this location should Active Directory not be available. Click Next when finished. (At this point you may need your Windows 2000 Server CD).
Once the components are configured, click Finish.
To verify that Certificate Services is running, drop to a command window and type
net start. Scroll up to find Certificate Services in the list.To view the certificate configuration, open the Certificate Authority MMC under Administrative Tools (see Figure 7.17).
Note
Installing a Certificate . To install a certificate, you must create a cust om MMC and add the Certificates snap-in. Once you do this, you can utilize that utility to request certificates from your Enterprise root CA, and the Certificate Authority utility to view and manage them.
Kerberos is the default authentication and security protocol in Windows 2000. In short, the process involves the use of session tickets that employ shared secret keys between client and server. See "Kerberos." | |
The trusted intermediary in the Kerberos authentication process is known as the key distribution center (KDC). The KDC is responsible for issuing session tickets to client computers requesting network resources. See "Key Distribution Center." | |
The long-term session key is created at logon time via a one-way hash of the user's password. It is returned from the KDC to the client's cache in a ticket-granting ticket. The TGT is passed back to the KDC for subsequent requests to network resources. See "Key Distribution Center." | |
Windows 2000 employs object attribute inheritance, which allows administrators to assign permissions to parent objects, and have child objects inherit permissions from their parent. See "Inheritance." | |
IPsec stores its policy information in Active Directory. This provides for a single storage location for all security-related information and provides for seamless integration of IP security. See "Windows 2000 Predefined IPsec Policies." | |
Static inheritance is referred to as Create Time inheritance. At the time of an object's creation, Windows 2000 merges default security information with the settings of the parent object. After that, the object may or may not inherit its parent's security information. See "Static Inheritance." | |
Local security policy, domain policy, OU policy. These are the three default security policies and the order in which they are applied. Hence, the OU policy will override any of the previous two. See "Security Policies." | |
Manual trusts must be created to interoperate with down-level Windows NT domains as well as with heterogeneous systems, such as UNIX and IRIS. See "Trust Relationships." | |
A referral process occurs in situations where a request is processed by a KDC in one realm (or domain) for a resource in another realm (or domain). The referral process is simply the re-direction of the request to another KDC. See "Kerberos Interoperability." | |
Windows 2000 supports NTLM, Kerberos, and SSL/TLS authentication. Kerberos is the default and is used whenever possible. NTLM exists for backward compatibility with down-level clients or servers, and SSL/TLS provides secure authentication with X.509 certificates. See "Windows 2000 Authentication." |
C. You should configure the VPs' computers for the Server (Request Security) option. The Client (Respond Only) option should be configured for clients that need to respond appropriately for secure connections. The Secure Server (Require Security) option should be used only if all data transmissions on the network need to be secure. X.509 certificates are issued by Certificate Authorities and are used for secure Internet authentication. See "IPsec for OLC." | |
B. The default domain security policy is created when the first domain controller is added to a domain. It defines account policies in the areas of passwords, account lockout, and Kerberos. The default domain controller security policy defines policy only for domain controllers, and does not define password policy. The registry on domain controllers holds password policy, but is overridden by domain policy. The User Manager for Domains is where password policy was changed in Windows NT. See "Security Policy." | |
C. In Windows 2000, the domain-wide security policy extends to member servers and workstations that are members of the domain. The user may coincidentally have a virus but that's not the technical answer we're looking for! There is no explicit "save" operation when changing policy. See "Security Policy." | |
A. To make changes to any security policy, you should create and assign a GPO to an OU. Since the OU policy is the last to be applied, it will override any other security policy, including the domain-wide security policy. Domain controller security policy does control the audit policy on all domain controllers, but would set it for all objects, not just a subset of users. You should never assign GPOs to a user object—and you won't because you can't! See "Security Policy." | |
D. To assign a non-administrator temporary permission to perform a specific task, use the Delegation of Administrative Control Wizard. For proper implementation, assign the OU containing the objects you want affected a GPO enabling the help desk manager the granular permission needed to perform individual tasks. See "Active Directory and Security." | |
B. A security policy includes guidelines and standards whose purpose is to eliminate security breaches that can lead to certain kinds of attacks and threats. Because of the scope of security, you need to be sure you cover all bases, including physical and location security, creating a security policy document, and how the company should react to security. Options A, C, and D provided viable answers to the question, but focused too much on task-level security measures. See "Security Policies." | |
D. Kerberos is a shared secret key authentication protocol that makes use of a trusted intermediary (the KDC) to generate keys that can be used for secret exchanges between two computers. This secret key provides the ability for each computer to secretly and securely confirm the identity of the other. Answer A describes the Kerberos Key Distribution Center, which is only a part of the core authentication protocol. Answer B describes SSL/TLS authentication using X.509 certificates. The core Kerberos protocol as implemented in RFC-1510 does not support X.509 certificate-based authentication; however, the Microsoft extensions to the protocol do. Answer C describes NTLM authentication, which is the Microsoft proprietary predecessor to Kerberos. See "Kerberos." | |
B. A core business value to using public key cryptography is authentication. Proving to customers that they are at your Web site and not a Web site impersonating yours means customers are satisfied and more at ease with your services. Both Kerberos and NTLM provide authentication services, and IPsec provides for security in data transmissions. See "Public Key Cryptography." | |
C. To control security settings throughout the company, all client computers must be capable of "being controlled." Windows 9x clients are not considered to be secure clients and should be upgraded to Windows 2000 Professional, an OS much more suited to businesses and one that can definitely partake in security plans. Adding the Active Directory patch to the 9x clients would allow them to search Active Directory, but would not do anything to secure them. An upgrade to Windows NT Workstation would provide added security, but would not allow for a centrally controlled security policy to be applied. See Group Policy Versus System Policy and "Security Policies." | |
A. Joseph will be able to see any non-TCP/IP data that is on the network segment he is monitoring. Because OLC's plans were to require IPsec for all internal communications, Joseph will see only encrypted garbage for IP data. Data returned by name resolution servers will be encrypted as well because it is IP data. Because OLC had planned to use the Kerberos authentication protocol, passwords will be encrypted as well. This information is covered throughout this chapter and its case study. |
Microsoft TechNet Articles:
Configuring Enterprise Security Policies. Available on September 1999 and later TechNet CDs.
Windows 2000 Reviewers Guide—Section 3: Addressing Customer Challenges and Requirements. Available on July 1999 and later TechNet CDs.
MS Security Configuration Toolset. Available on January 2000 and later TechNet CDs.
Configuring Enterprise Security Policies. Available on September 1999 and later TechNet CDs.
Windows 2000 Security—Default Access Control Settings. Available on July 1999 and later TechNet CDs.
Windows 2000 Certificate Services. Available on July 1999 and later TechNet CDs.
Microsoft White Papers:
Secure Networking Using Windows 2000 Distributed Security Services
Introduction to the Windows 2000 Public Key Infrastructure
Introduction to Microsoft Windows 2000 Security Services
Single Sign On in Windows 2000 Networks
Encrypting File System
IP Security (IPsec) for Windows 2000
Security Configuration Tool Set
Windows 2000 Kerberos Authentication
Windows 2000 Kerberos Interoperability