14.1. Learning from Your Network
NAC truly is the first solution that allows you to coordinate the information available on all your many network and security elements into one single location so that you can establish access control policies based not only on user identity and endpoint security posture, but also on each user's behavior while he or she is attached to the network.
New standards, such as the TNC's IF-MAP protocol (discussed in Chapter 13), have opened the doors to this level of coordination. While these standards take root and an increasing number of vendors adopt them, you'll have access to many new types of enforcement and policies, allowing you to extract additional value from your NAC implementation through extension to other products. The following sections discuss some examples of how your NAC deployment can benefit from extension to include other products.
14.1.1. IDP/IPS integration
Intrusion detection and prevention (IDP), or intrusion prevention systems (IPS), have become increasingly popular in recent years, especially when vendors respond to early challenges in the NAC market, such as perceived deployment and usability difficulties. Many large organizations have now fully deployed IDP/IPS, but prior to NAC, those solutions were somewhat limited in their abilities to prevent new attacks from occurring against the corporate network. You can configure all IPS sensors to drop malicious or otherwise unwanted traffic on the network. For example, if a particular endpoint launches an attack against an application server in a corporate datacenter and the IPS detects that traffic as malicious, the IDP/IPS can respond by dropping the traffic as configured in its policies. Although that response is sufficient, for certain situations, you might want to go even further in order to prevent future attacks on the network. NAC can help you to take information from your IDP/IPS device, and use it to take action on end user access as a result of attacks or other unwanted behavior.
If you have your IDP device fully integrated with your NAC solution (some solutions on the market can do this level of integration), the IDP continues to perform its core function — detecting network traffic and dropping unwanted packets. The NAC integration, however, allows the IDP/IPS to forward details of the unwanted traffic (including severity, IP address of the user, and attack signature) to the NAC solution. When it receives this information, NAC can take action on the associated end user or endpoint. NAC might respond by placing the user in quarantine, disabling the user's session, or even disabling the user's account (depending on the policies set by the administrator). Figure 14-1 illustrates how a NAC and IDP/IPS combined solution might look in a corporate network.
The type of integration shown in Figure 14-1 allows for a full coordination between a NAC solution that has a great deal of visibility into user and device identity and an IDP/IPS solution that has a great level of visibility into traffic and behavior on the network.
Figure 14.1. An example NAC/IPS integration.

14.1.2. Security incident and event management integration
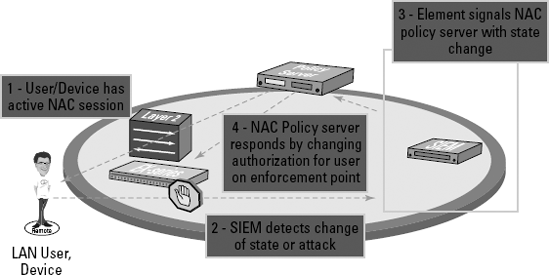
Security incident/information and event management (SIEM) products have become more popular in recent years, and many vendors have entered this market. These products can coordinate a wealth of information from devices on your network, making a SIEM product a very logical integration or extension point for your NAC deployment.
NOTE
A SIEM product can collect logs from a variety of devices, correlating that information so that it can effectively determine events, attacks, or other anomalies on the network. A SIEM product provides information that allows IT administrators to investigate these events and potential vulnerabilities further, possibly taking corrective action to solve issues before hackers exploit those issues. SIEM products leverage tools such as flow and event correlation in order to provide threat and vulnerability analysis that network administrators and security personnel can view.
Just like with IDP/IPS (discussed in the preceding section), SIEM products are limited in how they can prevent detected attacks from continuing to occur after the products discover the attacks. NAC can come to the rescue by offering the ability to protect against further unwanted behavior, extracting more power and value from your SIEM investment. With the appropriate integrations, you can funnel events from your SIEM directly into the NAC policy server. By combining with NAC, you can take similar actions with SIEM that you can with IDP/IPS. Depending on the severity and type of attack, you might take actions ranging from temporary end-user quarantine to disabling the end user's account so that he or she can't log in again until after the administrator conducts further investigation. The combined solution gives you a much more powerful combination than the two solutions standing on their own.
The full extent of the integration depends on the willingness of the SIEM and NAC vendors to work together to support the same standards or APIs that enable the exchange of this information. Because NAC is becoming increasingly popular, many SIEM vendors will likely realize the potential of these types of integrations and begin developing products that support these standards.
Figure 14-2 shows the flow of how such an integration might work in your network.
Figure 14.2. A NAC policy that incorporates SIEM.
14.1.3. Network antivirus integration
Extension of NAC to your network antivirus gateways might make sense for your organization due to the popularity of antivirus in corporate networks. The network antivirus continues to view traffic on the network, scanning for viruses and performing cleaning if and when necessary.
|
But, if the antivirus gateway can react by not only dropping traffic, but also signaling back to the NAC implementation, your organization can accomplish a reactive infrastructure that learns how to adapt to user and machine behavior:
For example, the NAC system might quarantine or disconnect users, as shown in Figure 14-2.
The NAC system could take a more subtle approach, such as initiating an antivirus scan on the endpoint itself.
The NAC system could also ensure that all future traffic from that endpoint be pushed through the network antivirus gateway before it's directed to its destination.
14.1.4. Network inventory/device classification integration
Network inventory is a key piece of many NAC deployments, primarily because so many devices in a given corporate network can't necessarily run required NAC software or authenticate properly into a NAC environment.
Figure 14-3 illustrates how network inventory or device classification solutions might fit into a typical NAC deployment. As shown in Figure 14-3, the policy server in most NAC solutions can adequately handle most managed devices. These devices can typically run some form of NAC software, and the NAC system can scan and authenticate them properly, such as with 802.1X. Typical devices in this category include
Desktop and laptop computers that run various operating systems
Smartphones
PDAs
802.1X-enabled VoIP phones
Figure 14.3. An example inventory and device classification within NAC.
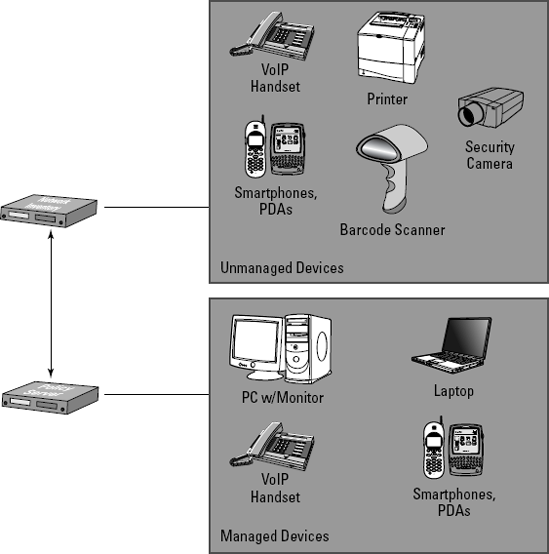
Network inventory solutions come into play when your organization needs to deal with devices that haven't been built to integrate into a NAC solution. Depending on the type of organization you work for, these devices can even outnumber the managed devices in your network. These kinds of devices include older, less advanced
VoIP phones and PDAs
Printers
Scanners
Security cameras
Video-conferencing equipment
HVAC systems
Medical equipment
Many IP-enabled devices on a large corporate network don't have the appropriate software to enable a full NAC authentication.
NOTE
The network inventory solution has to discover these devices, profile them to determine what type of devices they actually are, and then report to the NAC solution its findings so that NAC can make a decision about what level of access it will give the device on the network.
The inventory system absolutely must be able to determine the difference between a true unmanaged device and a managed device posing as an unmanaged device. For example, an unscrupulous user might try to circumvent NAC policies by mimicking a printer on the network if the user knows that NAC gives printers permissive access to the network. The person might mimic a printer by cloning a known printer MAC address, for example. A good network inventory system has the ability to monitor that machine's behavior and classify it as a laptop rather than a printer, meaning that the device won't get on the network until the user has authenticated properly, ending the threat of that user circumventing the NAC policies and skipping the crucial step of authentication and device classification.

