Chapter 7. Virtual Private Networks
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
![]() Use a virtual private network (VPN).
Use a virtual private network (VPN).
![]() Use point-to-point tunneling protocol (PPTP) as an encryption tool for VPNs.
Use point-to-point tunneling protocol (PPTP) as an encryption tool for VPNs.
![]() Use layer 2 tunneling protocol (L2TP) as an encryption tool for VPNs.
Use layer 2 tunneling protocol (L2TP) as an encryption tool for VPNs.
![]() Add security and privacy to a communication using IPSec.
Add security and privacy to a communication using IPSec.
![]() Understand and evaluate VPN solutions.
Understand and evaluate VPN solutions.
Introduction
Earlier chapters focus primarily on security within a network. However, what happens when remote users want to log on to a network versus a remote user simply accessing a Web server or FTP server on the network? This process involves a remote user, perhaps an entire remote office, connecting to the network and accessing resources just as if she were on your local network. This clearly presents significant security issues.
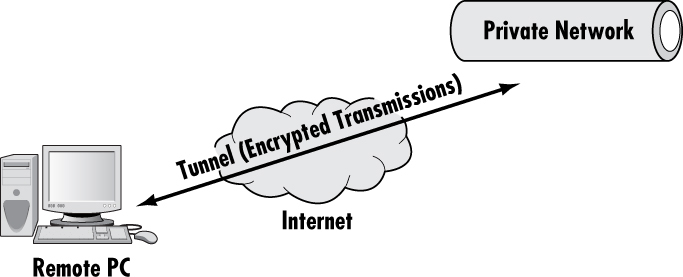
Virtual private networks (VPNs) are becoming a common way to connect remotely to a network in a secure fashion. A VPN creates a private network connection over the Internet to connect remote sites or users together. Instead of using a dedicated connection such as leased lines, a VPN uses virtual connections routed through the Internet from the remote site or user to the private network. Security is accomplished by encrypting all the transmissions.
A VPN allows a remote user network access just as if she were local to the private network. This means not only connecting her to the network as if she were local but also making the connection secure. Because most organizations have many employees traveling and working from home, remote network access has become an important security concern. Users want access, and administrators want security. The VPN is the current standard for providing both.
Basic VPN Technology
To accomplish its purpose, the VPN must emulate a direct network connection. This means it must provide both the same level of access and the same level of security as a direction connection. To emulate a dedicated point-to-point link, data is encapsulated, or wrapped, with a header that provides routing information allowing it to transmit across the Internet to reach its destination. This creates a virtual network connection between the two points. The data being sent is also encrypted, thus making that virtual network private.
Internet Week (Salamone, 1998) gives an excellent definition of a VPN: “a combination of tunneling, encryption, authentication, and access control technologies and services used to carry traffic over the Internet, a managed IP network, or a provider’s backbone.”
A VPN does not require separate technology, leased lines, or direct cabling. It is a virtual private network, which means it can use existing connections to provide a secure connection. In most cases it is used over normal Internet connections. Basically the VPN is a way to “piggy back” over the Internet to create secure connections. Figure 7.1 illustrates a VPN.
A variety of methods are available for connecting one computer to another. With dial-up Internet connections, for example, the user’s modem dials the Internet service provider’s number, where it connects to one modem in a group of modems called a modem bank. This connection is not secure and is not even designed to mirror direct network connections. If the user is using a high-speed access (such as cable or DSL), the difference is one of speed only—the fundamental fact that the connection is neither dedicated nor secure has not changed.
This sort of arrangement is generally acceptable for an ISP. The customers connecting merely want a conduit to the Internet and do not need to connect directly or securely to a specific network. However, this setup is inadequate for remote users attempting to connect to an organization’s network. In such cases the private and secure connection a VPN provides is critical.
Individual remote users are not the only users of VPN technology. Many larger organizations have offices in various locations. Achieving reliable and secure site-to-site connectivity for such organizations is an important issue. The various branch offices must be connected to the central corporate network through tunnels that transport traffic over the Internet.
Using VPN technology for site-to-site connectivity enables a branch office with multiple links to move away from an expensive, dedicated data line and to simply utilize existing Internet connections.
Using VPN Protocols for VPN Encryption
Multiple ways exist to achieve the encryption needs of a VPN. Certain network protocols are frequently used for VPNs. The two most commonly used protocols for this purpose are point-to-point tunneling protocol (PPTP) and layer 2 tunneling protocol (L2TP). The part of the connection in which the data is encapsulated is referred to as the tunnel. L2TP is often combined with IPSec to achieve a high level of security. IPSec is discussed in more detail later in this chapter.
PPTP
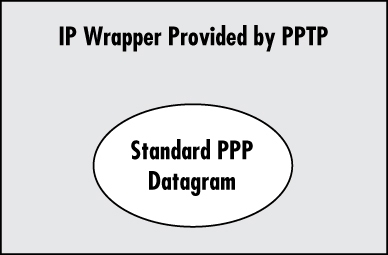
PPTP is a tunneling protocol that enables an older connection protocol, PPP (point-to-point protocol), to have its packets encapsulated within Internet Protocol (IP) packets and forwarded over any IP network, including the Internet itself. PPTP is often used to create VPNs. PPTP is an older protocol than L2TP or IPSec. Some experts consider PPTP to be less secure than L2TP or IPSec, but it consumes fewer resources and is supported by almost every VPN implementation. It is basically a secure extension to the point-to-point protocol (PPP). See Figure 7.2.
PPTP was originally proposed as a standard in 1996 by the PPTP Forum—a group of companies that included Ascend Communications, ECI Telematics, Microsoft, 3Com, and U.S. Robotics. This group’s purpose was to design a protocol that would allow remote users to communicate securely over the Internet.
Although newer VPN protocols are available, PPTP is still widely used in part because almost all VPN equipment vendors support PPTP. Another important benefit of PPTP is that it operates at layer 2 of the OSI model (the data link layer), allowing different networking protocols to run over a PPTP tunnel. For example, PPTP can be used to transport IPX, NetBEUI, and other data.
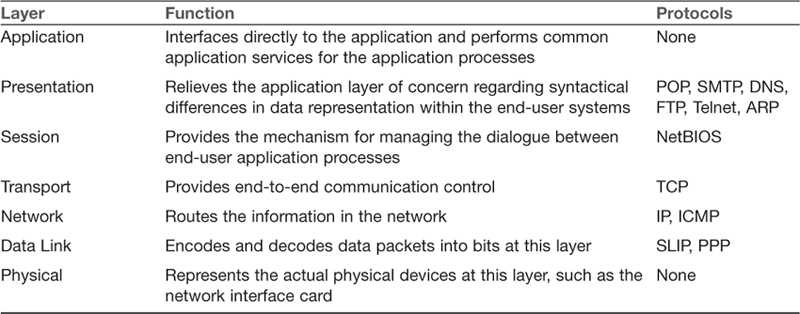
The OSI model, short for Open Systems Interconnect model, is a standard description of how networks communicate. It describes the various protocols and activities, and delineates how they relate to each other. This model is divided into seven layers, as shown in Table 7.1.
PPTP supports two generic types of tunneling: voluntary and compulsory. In voluntary tunneling, a remote user dials into a service provider’s network and a standard PPP session is established that enables the user to log on to the provider’s network. The user then launches the VPN software to establish a PPTP session back to the PPTP remote-access server in the central network. This process is called voluntary tunneling because the user initiates the process and has the choice of whether to establish the VPN session. Although it’s not advisable, the user could simply use a standard PPP connection without the benefits of a VPN.
In a compulsory tunneling setup the only connection available to the host network is via a VPN. A simple PPP connection is not available, only the full PPTP connection, forcing users to use a secure connection. From a security standpoint this option is preferred.
PPTP Authentication
When connecting users to a remote system, encrypting the data transmissions is not the only facet of security. You must also authenticate the user. PPTP supports two separate technologies for accomplishing this: Extensible Authentication Protocol (EAP) and Challenge Handshake Authentication Protocol (CHAP).
EAP
EAP was designed specifically with PPTP and is meant to work as part PPP. EAP works from within PPP’s authentication protocol. It provides a framework for several different authentication methods. EAP is meant to supplant proprietary authentication systems and a variety of authentication methods to be used, including passwords, challenge-response tokens, and public key infrastructure certificates.
CHAP
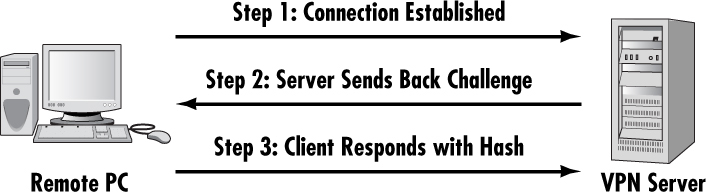
CHAP is actually a three-part handshaking (a term used to denote authentication processes) procedure. After the link is established, the server sends a challenge message to the client machine originating the link. The originator responds by sending back a value calculated using a one-way hash function. The server checks the response against its own calculation of the expected hash value. If the values match, the authentication is acknowledged; otherwise, the connection is usually terminated. This means that the authorization of a client connection has three stages. Figure 7.3 illustrates them.
What makes CHAP particularly interesting is that it periodically repeats the process. This means that even after a client connection is authenticated, CHAP repeatedly seeks to re-authenticate that client, providing a robust level of security.
L2TP
Layer 2 tunneling protocol is an extension or enhancement of the point-to-point tunneling protocol that is often used to operate virtual private networks over the Internet. Essentially, it is a new and improved version of PPTP. As its name suggests, it operates at the data link layer of the OSI model (like PPTP). Both PPTP and L2TP are considered by many experts to be less secure than IPSec. However, seeing IPSec used together with L2TP to create a secure VPN connection is not uncommon.
L2TP Authentication
Like PPTP, L2TP supports EAP and CHAP. However, it also offers support for other authentication methods, for a total of five:
![]() EAP
EAP
![]() CHAP
CHAP
![]() MS-CHAP
MS-CHAP
![]() PAP
PAP
![]() SPAP
SPAP
EAP and CHAP were discussed in the previous section. The following section discusses the remaining three.
MS-CHAP
As the name suggests, MS-CHAP is a Microsoft-specific extension to CHAP. Microsoft created MS-CHAP to authenticate remote Windows workstations. The goal is to provide the functionality available on the LAN to remote users while integrating the encryption and hashing algorithms used on Windows networks.
Wherever possible, MS-CHAP is consistent with standard CHAP. However, some basic differences between MS-CHAP and standard CHAP include the following:
![]() The MS-CHAP response packet is in a format designed for compatibility with Microsoft’s Windows networking products.
The MS-CHAP response packet is in a format designed for compatibility with Microsoft’s Windows networking products.
![]() The MS-CHAP format does not require the authenticator to store a clear-text or reversibly encrypted password.
The MS-CHAP format does not require the authenticator to store a clear-text or reversibly encrypted password.
![]() MS-CHAP provides authenticator-controlled authentication retry and password-changing mechanisms. These retry and password-changing mechanisms are compatible with the mechanisms used in Windows networks.
MS-CHAP provides authenticator-controlled authentication retry and password-changing mechanisms. These retry and password-changing mechanisms are compatible with the mechanisms used in Windows networks.
![]() MS-CHAP defines a set of reason-for-failure codes that are returned in the failure packet’s message field if the authentication fails. These are codes that Windows software is able to read and interpret, thus providing the user with the reason for the failed authentication.
MS-CHAP defines a set of reason-for-failure codes that are returned in the failure packet’s message field if the authentication fails. These are codes that Windows software is able to read and interpret, thus providing the user with the reason for the failed authentication.
PAP
Password Authentication Protocol (PAP) is the most basic form of authentication. With PAP, a user’s name and password are transmitted over a network and compared to a table of name-password pairs. Typically, the passwords stored in the table are encrypted. However, the transmissions of the passwords are in clear text, unencrypted, the main weakness with PAP. The basic authentication feature built into the HTTP protocol uses PAP. Figure 7.4 shows this authentication. This method is no longer used and is only presented for historical purposes.
SPAP
Shiva Password Authentication Protocol (SPAP) is a proprietary version of PAP. Most experts consider SPAP somewhat more secure than PAP because the username and password are both encrypted when they are sent, unlike with PAP. Figure 7.5 illustrates this protocol.
Because SPAP encrypts passwords, someone capturing authentication packets will not be able to read the SPAP password. However, SPAP is still susceptible to playback attacks (that is, a person records the exchange and plays the message back to gain fraudulent access). Playback attacks are possible because SPAP always uses the same reversible encryption method to send the passwords over the wire.
L2TP Compared to PPTP
L2TP is actually the convergence of the layer 2 forwarding protocol (developed by Cisco) and PPTP (discussed in the previous section). The development of L2TP was spurred on by perceived shortcomings in PPTP. One of those shortcomings was that PPTP only supports public IP addresses. Many dial-up networking services support only registered IP addresses, which limits the types of applications that are implemented over VPNs. In other words, only the public IP addresses registered with interNIC are acceptable. Given that many VPNs ultimately connect with an internal server that might use a private IP address, this presents some limitations. L2TP supports multiple protocols and unregistered and privately administered IP addresses over the Internet.
Another important improvement in L2TP over PPTP is that it uses IPSec for encryption, whereas PPTP only uses Microsoft Point-to-Point Encryption (MPPE). MPPE is actually a version of DES (discussed in Chapter 6, “Encryption Fundamentals”) and as such is secure enough for most situations. However, most experts consider IPSec to be more secure. Table 7.2 provides a comparison of PPTP to L2TP.
Windows NT only supports PPTP, but Windows 2000 and later versions also support L2TP, making it an attractive option for Windows network administrators because it supports more network connection and authentication options and is more secure.
IPSec
Internet Protocol Security (IPSec) is a technology used to create virtual private networks. IPSec is a security used in addition to the IP protocol that adds security and privacy to TCP/IP communication. IPSec is incorporated with Microsoft operating systems as well as many other operating systems. For example, the security settings in the Internet Connection Firewall that ships with Windows XP enables users to turn on IPSec for transmissions. IPSec is a set of protocols developed by the IETF (Internet Engineering Task Force; www.ietf.org) to support secure exchange of packets. IPSec has been deployed widely to implement VPNs.
IPSec has two encryption modes: transport and tunnel. The transport mode works by encrypting the data in each packet but leaves the header unencrypted. This means that the source and destination address, as well as other header information, are not encrypted. The tunnel mode encrypts both the header and the data. This is more secure than transport mode but can work more slowly. At the receiving end, an IPSec-compliant device decrypts each packet. For IPSec to work, the sending and receiving devices must share a key, an indication that IPSec is a single-key encryption technology. IPSec also offers two other protocols beyond the two modes already described. Those protocols are AH (Authentication Header) and ESP (Encapsulated Security Payload).
AH and ESP use the same algorithms to encrypt the data. AH also provides optional anti-replay protection, which protects against unauthorized retransmission of packets, a process to which SPAP is vulnerable. Anti-replay protection prevents packets from being rerouted to a destination other than the intended one, a valuable security feature for a VPN. The authentication header is inserted into the packet between the IP header and packet contents.
AH, by itself, protects only the packet’s origin, destination, and contents from tampering. It does not hide the sender or protect the data. If data is intercepted and only AH is used, the message contents can be read. In essence, the AH is part of the tunneling portion of the VPN helping to establish the dedicated virtual connection. ESP is used to protect the actual data.
In addition to ESP and AH, IPSec also uses IPComp and IKE. IPComp, or IP payload compression, provides a way to compress packets before encryption by ESP. IKE, or Internet Key Exchange, manages the exchange of encryption keys. For communication between distant locations, VPNs must provide ways to negotiate keys in secrecy. IKE makes this possible.
As you can see IPSec is actually comprised of four protocols:
![]() AH
AH
![]() ESP
ESP
![]() IPComp
IPComp
![]() IKE
IKE
More details about IPSec are available at
![]() Microsoft IPSec http://technet.microsoft.com/en-us/network/bb531150.aspx
Microsoft IPSec http://technet.microsoft.com/en-us/network/bb531150.aspx
![]() The Internet Engineering Task Force IPSec Web site: http://datatracker.ietf.org/wg/ipsec/charter/
The Internet Engineering Task Force IPSec Web site: http://datatracker.ietf.org/wg/ipsec/charter/
![]() IPSec for Free BSD: www.netbsd.org/Documentation/network/ipsec/#getting_started
IPSec for Free BSD: www.netbsd.org/Documentation/network/ipsec/#getting_started
SSL
A new type of firewall uses SSL (Secure Sockets Layer) or TLS (Transport Layer Security) to provide VPN access through a web portal. Essentially, TLS and SSL are the protocols used to secure Web sites. If you see a website beginning with HTTPS, then traffic to and from that website is encrypted using SSL or TLS.
In some VPN solutions the user logs in to a website, one that is secured with SSL or TLS, and is then given access to a virtual private network. However, visiting a website that uses SSL or TLS does not mean you are on a VPN. As a general rule most websites, such as banking websites, give you access only to a very limited set of data, such as your account balances. A VPN gives you access to the network, the same or similar access to what you would have if you were physically on that network.
Implementing VPN Solutions
Regardless of which protocols you use for your VPN, you must implement your choice in some software/hardware configuration. Many operating systems have built-in VPN server and client connections. These are generally fine for small office or home situations. However, they might not be adequate for larger scale operations in which multiple users connect via VPN. For those situations, a dedicated VPN solution might be necessary. This section discusses some of those solutions.
Cisco Solutions
Cisco offers VPN solutions, including a module (http://www.cisco.com/en/US/products/sw/secursw/ps2308/index.html) that can be added to many of their switches and routers to implement VPN services. It also offers client-side hardware (www.cisco.com/en/US/products/sw/secursw/ps5299/index.html) that is designed to provide an easy-to-implement yet secure client side for the VPN.
The main advantage of this solution is that it incorporates seamlessly with other Cisco products. Administrators using a Cisco firewall or Cisco routers might find this solution to be preferable. However, this solution might not be right for those not using other Cisco products and those who don’t have knowledge of Cisco systems. However, many attractive specifications for this product include the following:
![]() It uses 3DES encryption (an improved version of DES).
It uses 3DES encryption (an improved version of DES).
![]() It can handle packets larger than 500 bytes.
It can handle packets larger than 500 bytes.
![]() It can create up to 60 new virtual tunnels per second, a good feature if a lot of users might be logging on or off.
It can create up to 60 new virtual tunnels per second, a good feature if a lot of users might be logging on or off.
Service Solutions
In some cases, especially with large WAN VPN situations, you might not want to invest the time, energy, and cost to establish, secure, and monitor VPN connections. You can contract this entire process, the setup and the administration, to VPN vendors. ATT provides this service for many companies.
Service solutions have the advantage of not requiring any particular VPN skill on the part of the internal IT department. A department that lacks these specific skill areas but wants to implement a VPN might find that using an outside service is the right solution.
Free S/WAN
The Free S/WAN product (www.freeswan.org/) is an open-source VPN solution available for Linux operating systems. As an open-source product, one of its biggest advantages is that it is free. Free S/WAN uses IPSec, making it a highly secure VPN solution.
Free S/WAN supports either remote users logging on via VPN, or site-to-site connections. It also supports wireless connections. However, it does not support NAT (Network Address Translation, the new alternative to proxy servers).
Other Solutions
Clearly many possible VPN solutions are available. A simple Google or Yahoo! search for “VPN Solutions” generates many responses. You encounter the following VPN solutions most frequently. You must examine your organization’s specific data usage requirements to determine the most appropriate VPN solution.
Summary
Virtual private networks are secure connections over the Internet that enable remote users and sites to connect to a central network. You can use PPTP, L2TP, or IPSec to create a VPN. IPSec is considered the most secure of the three. Administrators creating a VPN protocol should consider how the packets are encrypted, what sort of authentication is used, and whether the current hardware and software supports that technology.
Test Your Skills
Multiple Choice Questions
1. PPTP is an acronym for which of the following?
A. Point-to-point transmission protocol
B. Point-to-point tunneling protocol
C. Point-to-point transmission procedure
D. Point-to-point tunneling procedure
2. What does L2TP stand for?
A. Level 2 transfer protocol
B. Layer 2 tunneling protocol
C. Level 2 tunneling protocol
D. Level 2 transfer protocol
3. PPTP is based on what earlier protocol?
A. SLIP
B. L2TP
C. IPSec
D. PPP
4. At what layer of the OSI does PPTP operate?
A. Physical
B. Network
C. Data link
D. Transport
5. What is the difference between voluntary and compulsory tunneling in PPTP?
A. Only voluntary tunneling allows the user to choose which network to connect to.
B. Only compulsory tunneling forces the user to send his password.
C. Only voluntary tunneling allows standard PPP/non-VPN connection.
D. Only compulsory tunneling forces 3DES encryption.
6. Which authentication protocols are available under PPTP?
A. MS-CHAP, PAP, SPAP
B. EAP, CHAP
C. PAP, EAP, MS-CHAP
D. SPAP, MS-CHAP
7. Which of the following is an important security feature in CHAP?
A. It periodically re-authenticates.
B. It uses 3DES encryption.
C. It is immune to IP spoofing.
D. It uses AES encryption.
8. Which authentication protocols are available with L2TP that are not available with PPTP?
A. MS-CHAP, PAP, SPAP
B. EAP, CHAP
C. PAP, EAP, MS-CHAP
D. SPAP, MS-CHAP
9. Which of the following is generally considered the least secure?
A. PAP
B. SPAP
C. MS-CHAP
D. X-PAP
10. What is the primary vulnerability in SPAP?
A. Weak encryption
B. Playback attacks
C. Clear text passwords
D. No hash code
11. What encryption does PPTP use?
A. MPPE
B. IPSec
C. 3DES
D. AES
12. Which of the following is a weakness in PPTP?
A. Clear text passwords
B. No encryption
C. Used only with IP networks
D. Not supported on most platforms
13. What protocols make up IPSec?
A. AH, IKE, ESP, IPComp
B. AH, PAP, CHAP, IPComp
C. IPComp, MS-CHAP, PAP, AH
D. AH, SPAP, CHAP, IPComp
14. What is the difference between transport mode and tunnel mode in IPSec?
A. Only transport mode is unencrypted.
B. Only tunneling mode is unencrypted.
C. Only tunneling mode does not encrypt the header.
D. Only transport mode does not encrypt the header.
15. What advantage does AH have over SPAP?
A. AH uses stronger encryption.
B. AH protects the data as well as the header.
C. AH is not susceptible to replay attacks.
D. None; SPAP is more secure.
16. What protects the actual packet data in IPSec?
A. AH
B. ESP
C. SPAP
D. CHAP
17. What is the purpose of IKE?
A. Key exchange
B. Packet encryption
C. Header protection
D. Authentication
Windows XP has an easy-to-use VPN Wizard that allows you to set up your XP machine as a VPN server.
1. Click Start, and then select Control Panel.
2. In the Control Panel, select Network Connections.
3. In the Network Connections window, choose Create a New Connection, which launches the Welcome to the New Connection Wizard.
4. Click Next on the first screen of the wizard.
5. On the Network Connection Type screen, choose the Set Up an Advanced Connection option.
6. On the Advanced Connection Options screen, select the Accept Incoming Connection, and click Next.
7. On the Devices for Incoming Connections screen, select the optional devices on which you want to accept incoming connections.
8. On the Incoming Virtual Private Network (VPN) Connection screen, select the Allow Virtual Private Connections option, and click Next.
9. On the User Permissions screen, select the users that are allowed to make incoming VPN connections. Click Next.
10. On the Networking Software screen, click on the Internet Protocol (TCP/IP) entry and click the Properties button.
11. In the Incoming TCP/IP Properties dialog box, place a check mark in the Allow Callers to Access My Local Area Network check box to allow VPN callers to connect to other computers on the LAN. If this check box isn’t selected, VPN callers will be able to connect only to resources on the Windows XP VPN server itself. Click OK to return to the Networking Software screen and then click Next.
12. Click Finish to create the connection on the Completing the New Connection Wizard screen.
13. After the Incoming Connection is complete, right-click on the Connection you made in the Network Connections window and select the Properties.
You now have a VPN server.
Exercise 7.2: Setting up a Windows XP VPN Client
1. Click Start, and then select Control Panel.
2. In the Control Panel, select Network Connections.
3. Open the New Connection Wizard. Click Connect to the Network at My Workplace, and click Next.
4. Click Virtual Private Network Connection, and click Next.
5. Enter a name for this connection, and then click Next.
6. Choose whether Windows will automatically dial the initial connection to the Internet you created previously or let you do that manually. If you use multiple connections to the Internet, you should use manual, but if you always use the same connection you might consider the automatic method.
7. Click Next, and then type in the host name or IP address of your RRAS server. If you don’t know this, check with your IT department. Click Next again, and select My Use Only for this connection. Click Next again and then click Finish to create the VPN connection
8. You can test this by connecting to the server you created in Exercise 7.1.
Exercise 7.3: Setting up a Linux VPN
Linux can vary from distribution to distribution, so consult your particular distribution’s documentation. However, several sources are given for you here in the order I recommend. The first is the easiest to follow:
![]() http://www.techrepublic.com/article/set-up-a-linux-vpn-server-by-following-these-10-steps/
http://www.techrepublic.com/article/set-up-a-linux-vpn-server-by-following-these-10-steps/
![]() vpnlabs.org/linux-vpn.php
vpnlabs.org/linux-vpn.php
Exercise 7.4: Intercepting Packets
Chapter 5 discussed the open-source IDS Snort. One of its modes is to simply intercept and read packets. You will use that in this exercise.
1. Run Snort in packet sniffing mode on your VPN Server.
2. Intercept the incoming packets.
3. Determine whether they are encrypted.
Exercise 7.5: Installing and Configuring Free S/WAN
1. Go to the Web site mentioned in the chapter for Free S/WAN.
2. Download the product to your Linux server.
3. Install and configure according to the product documentation.
This exercise demonstrates that different operating systems can communicate easily over a VPN connection.
1. Using a Linux machine, connect to the Windows VPN server you created in Exercise 7.1.
2. Using a Windows machine, connect to the Linux VPN Server you created in Exercise 7.3 or 7.5.
Projects
Project 7.1: Comparing Authentication Protocols
1. Using the Web or other resources look up each of the authentication protocols mentioned in this chapter.
2. Compare the protocols by pointing out the strengths and weaknesses of each.
3. Which one would you recommend for your school, company, or organization?
4. State the reasons behind your recommendation.
Project 7.2: Internet Key Exchange
1. Using the Web and other resources, look up information on how IKE works.
2. Describe the methods used in keeping the key exchange secure.
3. What are possible weaknesses in the IKE method?
4. Do you consider this a secure method for key exchange?
Project 7.3: Cost Efficiency
Unfortunately, technical strength is not the only criterion by which any solution is judged. Cost must be taken into account. For this project you will do cost estimates. This will require you to research product Web sites and perhaps even call sales representatives.
1. Assume a local area network that is small (under 100 users, 5 servers).
2. Assume 20 remote users, not all connected at the same time.
3. Assume an average of five to eight connections at any given time.
4. Research three solutions that can support this scenario, and report on the cost of each.