Chapter 10. Defending Against Trojan Horses, Spyware, and Adware
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
![]() Describe Trojan horses.
Describe Trojan horses.
![]() Take steps to prevent Trojan horse attacks.
Take steps to prevent Trojan horse attacks.
![]() Describe spyware.
Describe spyware.
![]() Use anti-spyware software.
Use anti-spyware software.
![]() Create anti-spyware policies.
Create anti-spyware policies.
Introduction
Chapter 2 introduced Trojan horses and the threat they pose to a network and chapter 8 expanded upon that. Trojan horse programs are a common threat for any system connected to the Internet. They are a particular problem if your users download software, screen savers, or documents from the Internet. Trojan horses are not quite as widespread as virus attacks or DoS attacks, but they are certainly a real threat to your systems. In order to have a secure network you must take steps to protect your network from Trojan horse attacks. In this chapter you will learn about some well known Trojan horse attacks and steps you can take to reduce the danger from these attacks.
In the past few years spyware has become an increasingly dangerous problem for computer users, both at home and in organizations. Many Web sites now drop spyware, or its close relative, adware, onto users’ systems whenever the users open the Web site. Aside from the obvious threat to information security, these applications consume system resources. In this chapter we will examine the threats posed by spyware as well as methods you can use to combat them.
Trojan Horses
As Chapters 2 and 8 explained, a Trojan horse is an application that appears to have a benign purpose but actually performs some malicious function. This subterfuge is what makes these applications such a dangerous threat to your system. The Internet is full of useful utilities (including many security tools), screen savers, images, and documents. Most Internet users do download some of these things. Creating an attractive download that has a malicious payload is an effective way of gaining access to a person’s computer.
One defense against Trojan horses is to prevent all downloading, but that is not particularly practical. The wonder and value of the Internet is the easy access it provides to such a wide variety of information—restricting that access in such a draconian manner subverts one of the most important reasons for giving employees Internet access. Instead of using such a heavy-handed tactic, you will learn other ways to protect your systems from Trojan horses.
Once you have a Trojan horse on your system, it may perform any number of unwanted activities. Some of the most common actions Trojan horses take include:
![]() Erasing files on a computer
Erasing files on a computer
![]() Spreading other malware, such as viruses. Another term for a Trojan horse that does this is a dropper.
Spreading other malware, such as viruses. Another term for a Trojan horse that does this is a dropper.
![]() Using the host computer to launch Distributed Denial of Service (DDoS) attacks or send spam
Using the host computer to launch Distributed Denial of Service (DDoS) attacks or send spam
![]() Searching for personal information such as bank account data
Searching for personal information such as bank account data
![]() Installing a back door on a computer system. This means providing the creator of the Trojan horse easy access to the system, such as creating a username and password she can use to access the system.
Installing a back door on a computer system. This means providing the creator of the Trojan horse easy access to the system, such as creating a username and password she can use to access the system.
Of the items on the above list, installing back doors and executing distributed denial of service attacks are probably the most frequent results of a Trojan horse attack, though installing spyware and dropping viruses are becoming much more common as well.
Identifying Trojan Horses
In this section you will first learn about some well-known Trojan horse attacks that have occurred in the past. This will give you an idea of how these applications actually work. You will then explore some of the methods and procedures you can implement to ameliorate the danger.
Back Orifice
This rather crudely named Trojan horse is perhaps the most famous of the Trojan horses. Back Orifice is a remote administration system that allows a user to control a computer across a TCPIP connection using a simple console or GUI application. Some users download it thinking it is a benign administrative utility they can use. Others download it without even realizing they are downloading it. Back Orifice gives the remote user as much, if not more, control of the target machine than the person who downloaded it.
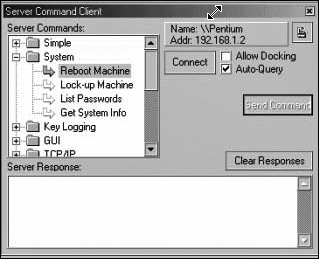
Back Orifice is small and entirely self-installing. Simply executing the server on any Windows machine installs the server. Back Orifice can also be attached to any other Windows executable, which will run normally after installing the server. In other words it can be attached to a legitimate program the user downloads, thus installing Back Orifice in the background. Even more insidious is the fact that Back Orifice does not show up in the task list or close-program list. This program is also launched every time the computer is started. The remote administrative screen that Back Orifice provides the intruders is shown in Figure 10.1. This figure should give you some idea of just how much an intruder can do to your system with this utility.
If you are already infected with Back Orifice (or wish to check to see if you are), going through the registry is the best way to remove it:
1. Click Start.
2. Click Run, and then type Regedit.
3. Using the + to expand the branches, locate the following key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunServices
4. Double-click on the (default) “key.” This opens a dialog box that shows the key and its current value (Value data), which is “.exe.” Select this key and press Delete (not Backspace), and then click OK.
5. Close Regedit and reboot your machine.
6. Go to your command prompt and type del c:windowssystemexe~1.
Anti-Spyware 2011
Anti-Spyware 2011 is a Trojan that can infect Windows client machines including XP, Vista, and Windows 7. This Trojan poses as an anti-spyware program. It actually disables security-related processes of antivirus programs, while also blocking access to the Internet, which prevents updates. After this program is on your computer it will alter the Windows registry so it is in the startup group. While the machine is infected the user will receive a number of false security messages. This is not a new program; there were almost identical previous versions such as XP anti-spyware.
Internet Explorer Trojan Horse
In 2003 a Trojan horse that specifically targeted Microsoft’s Internet Explorer began circulating the Internet. This Trojan program changes the DNS configuration on the Windows machine so that requests for popular Web search engines like Google and Alta Vista bring the Web surfer to a Web site maintained by the hackers, according to warnings from leading security companies (Roberts, 2003).
This attack relies on a vulnerability problem of Internet Explorer. This flaw allows Web sites, e-mails, or newsgroup messages to download and execute a file on your system without your knowledge. Microsoft released a patch for this vulnerability. The most difficult problem with this particular Trojan horse was that the patch released for it by Microsoft actually had additional security flaws. The following Web site will actually test to see if your browser is vulnerable to either of these problems: Secunia: http://secunia.com/vulnerability_scanning/personal/.
NetBus
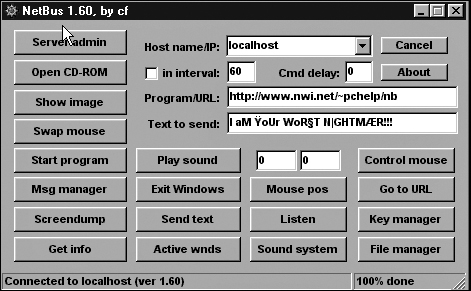
The NetBus Trojan is quite similar in effect to Back Orifice. A NetBus worm tries to infect target machines with the NetBus Trojan. This tool is a remote administration tool (often called a RAT), much like Back Orifice. NetBus, however, operates only on port 20034. It gives the remote user complete control of the infected machine, as if he were sitting at the keyboard and had full administrative rights. The NetBus administration screen is shown in Figure 10.2. You can see that the intruder can accomplish a variety of high-level tasks on the infected machine.
It is a simple matter to check whether your computer is infected with NetBus. Simply go to your command prompt and telnet with one of the following commands. If you get a response, you are probably infected. Use of the Loop back command:
telnet 127.0.0.1 12345
telnet 127.0.0.1 12346
If you are infected, then removal is best accomplished via the registry by following these steps:
1. Using regedit.exe find the key HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices.
2. Delete the key 666.
3. Reboot the computer.
4. Delete the file SKA.EXE in the Windows system directory.
Shamoon
Shamoon is a computer virus discovered in 2012 designed to target computers running Microsoft Windows in the energy sector. Symantec, Kaspersky Lab, and Seculert announced its discovery on August 16, 2012. It is essentially a data-stealing program that seems to target systems in energy companies.
Linux Trojan Horses
It is common to find proponents of non-Microsoft operating systems touting the superior security of their systems. It is true that there are certain features in many Microsoft products that seem to favor usability over security. However, it has been the contention of some security experts that much of the apparently better security for non-Microsoft operating systems stems from the fact that they have a much smaller share of the PC market and are therefore less attractive targets to the creators of malware. As these operating systems become more popular, we will see more attacks focused on them. In fact there have already been Trojan horses aimed specifically at Linux.
There are a number of utilities available for Linux. Most ship with Linux distributions, but it is common for Linux users to download updates to these from the Internet. The util-linux file is one such download that includes several essential utilities for Linux systems. A Trojan horse was placed in the file util-linux-2.9g.tar.gz on at least one FTP server between January 22, 1999, and January 24, 1999. This Trojan horse could have been distributed to mirror FTP sites. It is impossible to tell how many mirror sites had this file or how many users downloaded it. The age of this Trojan horse should tell you that threats to Linux system are nothing new. With the growing popularity of Linux you should expect to see even more.
This particular Trojan horse was a classic back door Trojan. Within the Trojan horse util-linux distribution, the program /bin/login was altered. The changes included code to send e-mail to the Trojan horse creator that contained the host name and log on information of users logging in. The distributors of the legitimate util-linux package updated their site with a new version; however, it is impossible to determine how many systems installed the Trojan version or how many systems were compromised as a result.
Portal of Doom
This Trojan horse is also a back door administration tool. It gives the remote user a great deal of control over the infected system. The actions remote users can take, if they get control of your system via Portal of Doom, include but are not limited to:
![]() Opening and closing the CD Tray
Opening and closing the CD Tray
![]() Shutting down the system
Shutting down the system
![]() Opening files or programs
Opening files or programs
![]() Accessing drives
Accessing drives
![]() Changing the password
Changing the password
![]() Logging keystrokes
Logging keystrokes
![]() Taking screen shots
Taking screen shots
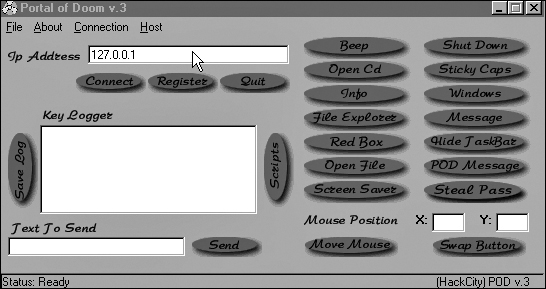
Portal of Doom is quite similar to Back Orifice and NetBus. It is easy to use and has a graphical user interface, as you can see in Figure 10.3.
You can manually remove this Trojan horse with the following steps:
1. Remove the String key in the registry located at HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices.
2. Use the task manager to shut down the process for ljsgz.exe. If you cannot shut it down, then reboot the machine. Now that you have altered the registry, the ljsgz.exe program will not start up again.
3. Delete the file ljsgz.exe from the Windows system directory.
Symptoms of a Trojan Horse
It is difficult to determine whether your system is the victim of a Trojan horse. There are a number of symptoms that might indicate that you have a Trojan horse. Assuming, of course, that you or another legitimate user are not making these changes, such symptoms include:
![]() Home page for your browser changing
Home page for your browser changing
![]() Any change to passwords, usernames, accounts, etc.
Any change to passwords, usernames, accounts, etc.
![]() Any changes to screen savers, mouse settings, backgrounds, etc.
Any changes to screen savers, mouse settings, backgrounds, etc.
![]() Any device (such as a CD door) seeming to work on its own
Any device (such as a CD door) seeming to work on its own
Any of these changes are symptoms of a Trojan horse and indicate your system is probably infected.
Why So Many Trojan Horses?
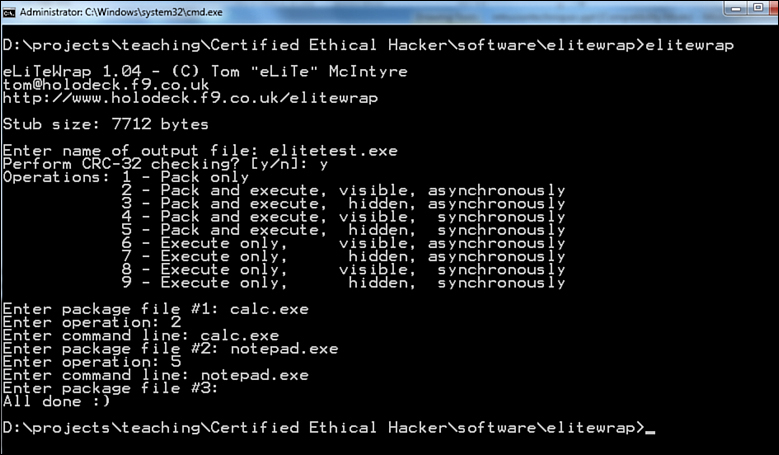
Why do we see so many Trojan horses? I actually wonder why we don’t see more. A variety of tools are available on the Internet, for free, that allow one to create a Trojan horse. One simple example is EliteWrapper, which you can download for free after searching on Google. It is a simple command-line tool that is remarkably easy to use:
1. Open a command window.
2. Navigate to the folder you put EliteWrapper in.
3. Make sure two programs are in the folder (one carrier program and the other the program you want to attach).
4. Type in the filename you want to run that is visible.
5. Type in the operation:
1 - Pack only
2 - Pack and execute, visible, asynchronously
3 - Pack and execute, hidden, asynchronously
4 - Pack and execute, visible, synchronously
5 - Pack and execute, hidden, synchronously
6 - Execute only, visible, asynchronously
7 - Execute only, hidden, asynchronously
8 - Execute only, visible, synchronously
9 - Execute only, hidden, synchronously
6. Goto the command line.
7. Type in the second file (the item you are surreptitiously installing).
8. Type in the operation.
9. When you’re done with the files, press Enter.
EliteWrapper is only one example. Many other tools are available on the Internet that will allow you to create Trojan horses. This tool can be used in a classroom setting, if you make sure that the two programs are actually innocuous and are used only for demonstration purposes. This program should show you how easily one can create a Trojan horse and why you should be careful downloading programs and utilities.
Preventing Trojan Horses
We have looked at several real-world Trojan horses, which should give you a good understanding of how they work. The real question is how do you prevent your systems from being exploited by a Trojan horse? The answer is a hybrid approach using both technological measures and policy measures.
Technological Measures
There are several technological measures that can protect your systems from the threat of Trojan horses. These measures are, of course, not a guarantee against Trojan horse attacks, but they can certainly provide a reasonable level of safety:
![]() Recall that NetBus worked using port 20034. This is yet another reason for blocking all unneeded ports on all machines, not just the servers or the firewall. A system that has port 20034 blocked on all servers, workstations, and routers is not susceptible to NetBus. If one of the network machines is infected with NetBus, it would be unusable by the attacker.
Recall that NetBus worked using port 20034. This is yet another reason for blocking all unneeded ports on all machines, not just the servers or the firewall. A system that has port 20034 blocked on all servers, workstations, and routers is not susceptible to NetBus. If one of the network machines is infected with NetBus, it would be unusable by the attacker.
![]() Antivirus software is yet another way to reduce the dangers of Trojan horse attacks. Most antivirus software scans for known Trojan horses as well as viruses. Keeping antivirus software on all machines updated and properly configured can be a great help in preventing Trojan horse infections.
Antivirus software is yet another way to reduce the dangers of Trojan horse attacks. Most antivirus software scans for known Trojan horses as well as viruses. Keeping antivirus software on all machines updated and properly configured can be a great help in preventing Trojan horse infections.
![]() Preventing active code in your browser can also help reduce the risk of Trojan horses. It will prevent users from viewing certain animations, but it can also stop several avenues for introducing a Trojan horse into your systems. At a minimum your browser should be set to warn users and get their approval prior to running any active code.
Preventing active code in your browser can also help reduce the risk of Trojan horses. It will prevent users from viewing certain animations, but it can also stop several avenues for introducing a Trojan horse into your systems. At a minimum your browser should be set to warn users and get their approval prior to running any active code.
![]() You are probably already aware that, as a matter of general computer security policy, you should always give users the minimum privileges they need to perform their job tasks. This policy is particularly helpful with protecting against Trojan horses. If an end user cannot install software on her machine, it is more difficult for her to inadvertently install a Trojan horse.
You are probably already aware that, as a matter of general computer security policy, you should always give users the minimum privileges they need to perform their job tasks. This policy is particularly helpful with protecting against Trojan horses. If an end user cannot install software on her machine, it is more difficult for her to inadvertently install a Trojan horse.
Policy Measures
Technology can go only so far in any facet of computer security, and protecting against Trojan horses is no different. End user policies are a critical part of protecting against Trojan horses. Fortunately, a few simple policies can greatly aid in protecting your system. You will probably note that many of these policies are the same ones used to protect your network from virus attacks.
![]() Never download any attachment unless you are completely certain it is safe. This means that unless you specifically requested an attachment, or at least expected one, and unless that attachment matches what you expected (i.e., is named appropriately, right format, etc.) do not download it.
Never download any attachment unless you are completely certain it is safe. This means that unless you specifically requested an attachment, or at least expected one, and unless that attachment matches what you expected (i.e., is named appropriately, right format, etc.) do not download it.
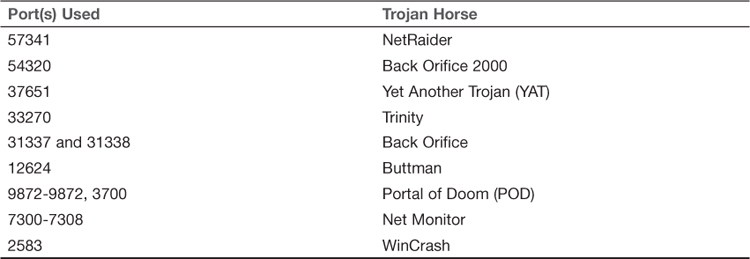
![]() If a port is not needed, close it. Table 10.1 lists ports used by well-known Trojan horses. This list is by no means exhaustive but should give you an idea of just how vulnerable your systems are if you are not shutting down unneeded ports.
If a port is not needed, close it. Table 10.1 lists ports used by well-known Trojan horses. This list is by no means exhaustive but should give you an idea of just how vulnerable your systems are if you are not shutting down unneeded ports.
![]() Do not download or install any software, browser skins, toolbars, screen savers, or animations on your machine. If you require one of these items, have the IT department scan it first to ensure safety.
Do not download or install any software, browser skins, toolbars, screen savers, or animations on your machine. If you require one of these items, have the IT department scan it first to ensure safety.
![]() Be cautious of hidden file extensions. For example, a file you think is an image could be a malicious application. Instead of mypic.jpg, it may actually be mypic.jpg.exe.
Be cautious of hidden file extensions. For example, a file you think is an image could be a malicious application. Instead of mypic.jpg, it may actually be mypic.jpg.exe.
Spyware and Adware
Spyware is a growing problem both for home computer users and for organizations. There is, of course, the risk that such applications might compromise some sensitive information. There is also the problem of these applications simply consuming too much of your system’s resources. Spyware and adware both use memory. If your system has too many such applications, then they can consume so much of your system’s resources that your legitimate software will have trouble running. I have personally seen computers that had so much spyware/adware running that the machine became unusable.
The primary difference between spyware and adware is what they do on your machine. They both infect your machine in the same manner. Spyware seeks to get information from your machine and make it available to some other person. This can be done in a number of ways. Adware seeks to create pop-up ads on your machine. Because these ads are not generated by the Web browser, many traditional pop-up blockers will not stop them.
Both spyware and adware are growing problems for network security and home PC security. This is an important element of computer security software that was at one time largely ignored. Even today, not enough people take spyware seriously enough to guard against it. Some of these applications simply change your home page to a different site (these are known as home page hijackers); others add items to your favorites (or read items from them). Other applications can be even more intrusive.
Identifying Spyware and Adware
Just as virus and Trojan horse threats eventually became well known to security professionals and hackers, there are certain adware and spyware products that are well known in the computer security community. Being aware of specific real world adware and spyware and how such applications function will help you to better understand the threats they pose.
Gator
Gator is perhaps the most widely known adware product. This product is often distributed by being built into various free software packages you can download from the Internet. Once it is on your computer, you will be inundated with various pop-up ads. This company makes a significant profit from selling the ads they display. Because of this profit, they have recently begun suing anti-spyware companies that specifically target Gator. You can find more details on that development from the CNET news Web site: news.com.com/2100-1032_3-5095051.html?tag=nefd_top.
The manufacturer of Gator insists that its product is not spyware and will not send information from your computer. However, the number of pop-up ads you are subjected to can range from merely annoying to a significant productivity drain. For example, the Gator-related product Weather Scope uses 16 megabytes of memory itself. It is very easy for various adware products to use up more than 100 megabytes of your system’s memory, which would produce a noticeable drain on your system’s performance.
There are two ways to remove Gator (other than the use of anti-spyware, which may remove it for you automatically):
Method 1: Add/Remove Programs:
1. Right-click the Gator icon in the System Tray and click Exit.
2. Click the Windows Start button, select Settings, and then Control Panel.
3. Select the Add/Remove Programs icon.
4. Find the entry Gator or Gator eWallet in the list of installed programs. Select it and then click the Remove button.
Method 2: The Registry (useful if Method 1 does not work):
1. Right-click the Gator icon in the System Tray and click Exit.
2. Use regedit to open the registry and select the key HKEY_LOCAL_ MACHINESoftwareMicrosoftWindowsCurrentVersionRun.
3. Find the entry CMESys, GMT, or trickler, and right-click it and click Delete.
4. Restart Windows.
5. Open C:Program FilesCommon Files. Delete the CMEII and GMT folders.
Either method should rid your computer of this piece of adware. In general, manually removing spyware or adware will often require you to use the task manager to stop the running process. Then you will need to scan the hard drive to delete the application and use the regedit tool to remove it from the registry. You can see that this is a rather difficult process.
RedSheriff
RedSheriff is spyware, not adware. This product is loaded as a Java applet embedded in a Web page you visit. Once you visit the Web site, this applet will collect information about your visit such as how long the page took to load, how long you stayed, and what links you visited. This information is sent to the parent company. A number of Internet Service Providers have begun including RedSheriff on their start pages, which are programmed to load every time the user logs on to the Internet. The problem with RedSheriff is twofold:
![]() No one (except the manufacturer) is really certain what data is collected or how it is used.
No one (except the manufacturer) is really certain what data is collected or how it is used.
![]() Many people have a negative reaction to anyone monitoring their Web site usage habits.
Many people have a negative reaction to anyone monitoring their Web site usage habits.
The RedSheriff program is marketed as a reporting tool to measure how visitors use a Web site. You can view the vendor’s own comments at its Web site at http://cexx.org/cache/redsheriff_products.html.
Anti-Spyware
Most antivirus products include anti-spyware. However, you can purchase dedicated anti-spyware software. Anti-spyware is an excellent way to defend against spyware and adware, just as antivirus software defends against viruses and Trojan horses. Essentially, it is software that scans your computer to check for spyware running on your machine. Most anti-spyware works by checking your system for known spyware files. It is difficult to identify specific activities that identify spyware, as you can with viruses. Each application must simply be checked against a list of known spyware. This means that you must maintain some sort of subscription service so that you can obtain routine updates to your spyware definition list.
In today’s Internet climate, running anti-spyware is as essential as running antivirus software. Failing to do so can lead to serious consequences. Personal data and perhaps sensitive business data can easily leak out of your organization without your knowledge due to spyware. You should also keep in mind that it is entirely possible for spyware to be the vehicle for purposeful industrial espionage. In this section we will examine a few popular anti-spyware utilities.
Spy Sweeper
This product is available at www.Webroot.com. The vendor offers enterprise wide anti-spyware solutions as well as solutions for individual PCs. Most importantly you can download the software for free, but you will need to register it (and pay for it) in order to get updated spyware definitions. In addition to allowing scanning of your system, Spy Sweeper gives you real-time monitoring of your browser and downloads, and warns you of any changes. For example, if there is a change to your home page, Spy Sweeper asks you to confirm that change before it is committed.
This product’s greatest advantage, however, is that it is simple and easy to use. If the person using the software is a novice, then Spy Sweeper is an excellent choice. Let’s examine just a few features so you can see how it works. The initial screen, shown in Figure 10.5, makes it easy for the novice user to sweep, view quarantined items, update the software, and perform other tasks.
When you run the sweep, you see an ongoing, real time report of what is taking place. This is shown in Figure 10.6. This report tells you how many spyware definitions the application is testing for, how far along it is in the process, and what has been found so far.
Once the sweep is done, the suspect programs/files are identified, and you can elect to restore them, delete them, or quarantine them. Spy Sweeper does not automatically delete them. This is a beneficial feature, as it prevents the accidental deletion of items that might have been misidentified as spyware.
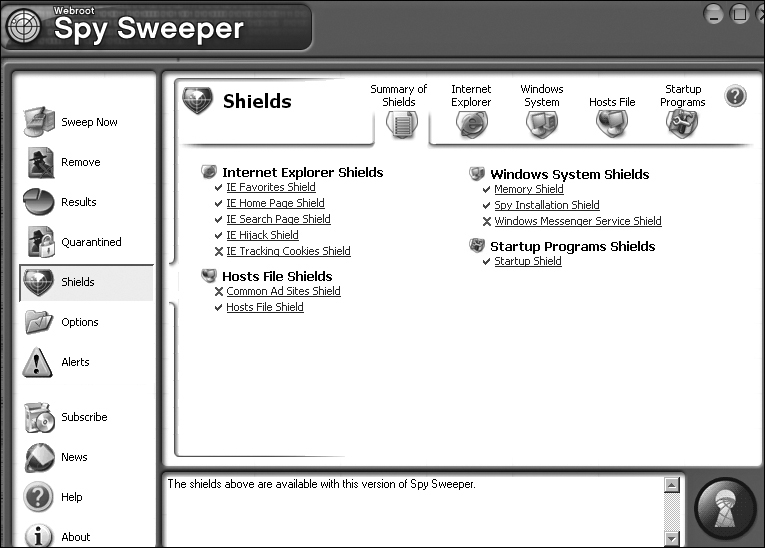
Another interesting feature of Spy Sweeper is the various shields it provides, shown in Figure 10.7. These shields can prevent changes to your Internet Explorer home page, favorites, Windows start up, programs in memory, and more. Most spyware and adware programs will attempt to alter one or more of these items. These shields require your direct approval before any such change can be made.
Zero Spyware
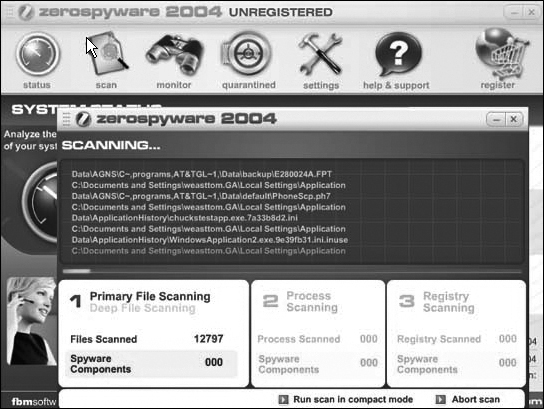
Zero Spyware is similar in function to Spy Sweeper. Like Spy Sweeper, it offers a free trial version that you can download from the company’s Web site. Unlike the other anti-spyware options we have examined, this one has not received much press attention. Also, as you can see in Figure 10.8, its trial version is limited. It does not offer the home page shield or adware shield that the other options offer. It also has fewer scanning options.
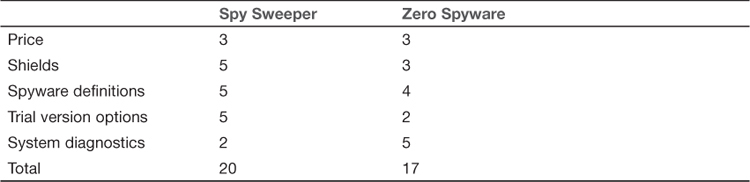
One advantage of Zero Spyware is that it includes a system diagnostics utility not found in the other anti-spyware software packages we have examined. This utility places its results in a Web page, making them easy to view or display. Table 10.2 offers a brief comparison of the three top anti-spyware packages. Each feature is rated on a scale of one to five, with five being the best.
Creating a grid like this can be useful whenever you are evaluating any type of security product. Assigning values to various features and then comparing the total score (as well as most important features) can help you decide which product is right for you.
Microsoft Anti-Spyware
Microsoft has recently entered the anti-spyware market. Its Web site can be found at www.microsoft.com/athome/security/spyware/software/default.mspx. It is unclear whether or not Microsoft will charge for the product in the future or bundle it as part of future Windows versions.
As of this writing, there have been no conclusive independent reviews of this product. However, the fact that it is currently free and is made for Windows makes it worth mentioning.
Researching and Comparing Anti-Spyware Products
As with antivirus, firewall, and other security products, there are many anti-spyware alternatives from which to choose. The following Web sites provide either anti-spyware or reviews of anti-spyware software you can use to help you evaluate the various products. Most products are priced from $19.95 to $39.95, and many have free trial editions you can download:
![]() PC MAG anti spyware products http://www.pcmag.com/reviews/antispyware
PC MAG anti spyware products http://www.pcmag.com/reviews/antispyware
![]() IEEE comparing anti spyware products http://ieeexplore.ieee.org/xpl/login.jsp?tp=&arnumber=6030154&url=http%3A%2F%2Fieeexplore.ieee.org%2Fxpls%2Fabs_all.jsp%3Farnumber%3D6030154
IEEE comparing anti spyware products http://ieeexplore.ieee.org/xpl/login.jsp?tp=&arnumber=6030154&url=http%3A%2F%2Fieeexplore.ieee.org%2Fxpls%2Fabs_all.jsp%3Farnumber%3D6030154
![]() Social Compare http://socialcompare.com/en/comparison/the-comparison-of-antispyware-software
Social Compare http://socialcompare.com/en/comparison/the-comparison-of-antispyware-software
![]() PC Magazine anti-spyware reviews: www.pcmag.com/article2/0,4149,1524223,00.asp
PC Magazine anti-spyware reviews: www.pcmag.com/article2/0,4149,1524223,00.asp
![]() Consumer Search Anti spyware http://www.consumersearch.com/anti-spyware-reviews
Consumer Search Anti spyware http://www.consumersearch.com/anti-spyware-reviews
This list is not comprehensive. A simple Web search will find a host of anti-spyware products. However, these are the more commonly used products and you should probably begin your exploration of anti-spyware with them.
Anti-Spyware Policies
As with all aspects of computer security, appropriate policies must be in place in order to protect your system against spyware and adware. Many of these policies are the same as the policies that protect your system from Trojan horses and virus infections.
![]() Never download any attachment unless you are completely certain it is safe. This means that unless you specifically requested an attachment, or at least expected one, and unless that attachment matches what you expected (i.e., is named appropriately, right format, etc.) do not download it.
Never download any attachment unless you are completely certain it is safe. This means that unless you specifically requested an attachment, or at least expected one, and unless that attachment matches what you expected (i.e., is named appropriately, right format, etc.) do not download it.
![]() Make sure your browser is configured to block cookies, or at most to allow cookies for only a very limited time. Cookies store information from a particular Web site, but any Web site you visit can read any cookie on your machine.
Make sure your browser is configured to block cookies, or at most to allow cookies for only a very limited time. Cookies store information from a particular Web site, but any Web site you visit can read any cookie on your machine.
![]() Your browser should be configured to block scripts that run without the user’s awareness.
Your browser should be configured to block scripts that run without the user’s awareness.
![]() Some browsers (Netscape and Mozilla) also offer pop-up blocking. Pop-up ads are often a vehicle for adware. Blocking such ads is critical.
Some browsers (Netscape and Mozilla) also offer pop-up blocking. Pop-up ads are often a vehicle for adware. Blocking such ads is critical.
![]() Never download any application, browser skin, screen saver, or utility from the Internet unless you are completely certain of its safety.
Never download any application, browser skin, screen saver, or utility from the Internet unless you are completely certain of its safety.
![]() Block Java applets, or at least require that the user manually approve them before loading. This will stop RedSheriff and many other spyware utilities.
Block Java applets, or at least require that the user manually approve them before loading. This will stop RedSheriff and many other spyware utilities.
Summary
Both Trojan horses and spyware pose significant dangers to your network. Trojan horses and viruses frequently overlap (i.e., a virus may install a Trojan horse). Virus scanners and appropriate policies are your only protection against Trojan horses. For this reason it is particularly important that you carefully develop and implement your anti-Trojan horse policies.
Spyware and adware are growing problems for computer systems. Spyware can compromise security by revealing details of your system or confidential data on the system. Adware is mostly a nuisance rather than a direct security threat. However as your computer becomes infected with more adware, such programs can eventually drain your system’s resources until your system becomes completely unusable.
You can protect yourself against adware and spyware with a combination of anti-spyware utilities and appropriate policies. There are several anti-spyware tools available, many of which were examined in this chapter.
Test Your Skills
Multiple Choice Questions
1. Which of the following are the two most common things Trojan horse programs do?
A. Launch DDoS attacks and open back doors
B. Install spyware and launch Ping of Death attacks
C. Delete registry keys and alter system files
D. Hijack the home page and delete registry keys
2. What does Back Orifice do to a system?
A. Deletes or corrupts Microsoft Office applications
B. Installs a virus on the infected system
C. Provides a remote user complete administrative access to the machine
D. Launches a DDoS at Microsoft sites
3. Which of the following is the most insidious aspect of Back Orifice?
A. It is small.
B. It spreads via e-mail.
C. It appears to be a legitimate program.
D. It does not show up in the task list.
4. What was the worst aspect of the Internet Explorer Trojan horse of 2003?
A. It corrupted the registry.
B. It deleted system files.
C. The patch for it had security flaws.
D. There was no patch for it.
5. What effect did the util-linux Trojan horse of 1999 have?
A. It sent out login information of users logging in.
B. It deleted or corrupted the registry.
C. It opened up port 1294 for a hacker to use.
D. It used IRC to open a back door to the machine.
6. Which of the following most accurately explains why minimum necessary privileges for a user help protect against Trojan horses?
A. If a user cannot remove programs, then he cannot remove anti-spyware and antivirus software accidentally.
B. If the user cannot install programs, it is less likely that he will install a Trojan horse.
C. If the user cannot install programs, it is completely impossible that he will install a Trojan horse.
D. If the user cannot remove programs, he cannot alter the security settings you have put on his machine.
7. Why are hidden file extensions a security threat?
A. Users might download an image that is really a malicious executable.
B. Users cannot properly organize their systems without knowing accurate file extensions.
C. Virus scanners have trouble with files whose extensions are hidden.
D. Hidden extensions almost always indicate a worm.
8. What is Gator?
A. Adware that is downloaded automatically when you visit certain Web sites
B. Adware that is often attached to free programs found on the Internet
C. Spyware that gathers information about you when you visit a Web site
D. Spyware that gets banking information from your hard drive
A. Adware that is downloaded automatically when you visit certain Web sites
B. Adware that is often attached to free programs found on the Internet
C. Spyware that gathers information about you when you visit a Web site
D. Spyware that gets banking information from your hard drive
10. Manually removing spyware usually requires all but which of the following actions?
A. Formatting the hard drive
B. Removing keys from the registry
C. Reinstalling Windows
D. Reinstalling antivirus software
11. Why is blocking pop-up ads good for security?
A. Pop-up ads reduce productivity.
B. Pop-up ads can be a vehicle for hackers to get into your system.
C. Pop-up ads can be a vehicle for spyware or adware to get into your system.
D. Pop-up ads can corrupt memory on your system.
12. Which of the following is the most likely reason you might wish to restrict Java applets?
A. Java applets can easily be modified to act as spyware.
B. Java applets can delete files on your hard drive.
C. Java applets usually contain viruses.
D. Java applets serve no useful purpose other than virus delivery.
13. Why would you want to restrict cookies?
A. Cookies consume system memory.
B. Cookies take up hard drive space.
C. Any Web site can read any cookie.
D. Cookies are often infected with a virus.
Exercises
Exercise 10.1: Back Orifice
1. Obtain Back Orifice using one of the following Web sites:
![]() http://www.cultdeadcow.com/tools/bo.html
http://www.cultdeadcow.com/tools/bo.html
![]() www.cultdeadcow.com/tools/bo.html
www.cultdeadcow.com/tools/bo.html
2. Install it on a lab computer.
3. Use the remote administration features to alter the target system.
Exercise 10.2: NetBus
1. Obtain NetBus using one of the following Web sites:
![]() www.dark-e.com/archive/trojans/netbus/
www.dark-e.com/archive/trojans/netbus/
![]() www.windowsecurity.com/pages/article.asp?id=453
www.windowsecurity.com/pages/article.asp?id=453
2. Install it on a lab computer.
3. Use the remote administration features to alter the target system.
Exercise 10.3: Spy Sweeper
1. Download Spy Sweeper onto a lab machine (preferably the one with Gator, Back Orifice, etc.).
2. Run the program and note what items it detects, but do not delete them.
Projects
Project 10.1: Impact of Trojan Horses
Using the Web or other resources find out the following facts:
1. How common are Trojan horse attacks?
2. What effects do these have on businesses?
3. What steps do you recommend to help reduce the threat of Trojan horse attacks?
Project 10.2: Impact of Spyware and Adware
1. How common are spyware and adware?
2. What effects do these have on businesses?
3. What steps do you recommend to help reduce the threat of spyware and adware?
Project 10.3: Using Alternative Anti-spyware
1. Download one alternative anti-spyware product (i.e., one we have not examined thoroughly in this chapter).
2. Install it on a lab machine and run it.
3. Compare the results to what you got with Spy Sweeper.