Chapter 9. Defending Against Virus Attacks
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
![]() Explain how virus attacks work.
Explain how virus attacks work.
![]() Explain how viruses spread.
Explain how viruses spread.
![]() Distinguish between different types of virus attacks.
Distinguish between different types of virus attacks.
![]() Employ virus scanners to detect viruses.
Employ virus scanners to detect viruses.
![]() Formulate an appropriate strategy to defend against virus attacks.
Formulate an appropriate strategy to defend against virus attacks.
Introduction
Chapter 2 introduced virus attacks and chapter 8 gave more details. In this chapter you will learn more about how virus attacks work and learn how to defend against a virus attack.
One thing already pointed out in Chapter 9 is that the most prevalent danger on the Internet is the computer virus or worm. This is due to the fact that once a virus is released it spreads rapidly and unpredictably. Other attacks, such as DoS, session hacking, and buffer overflow, are generally targeted at a specific system or network. The virus simply spreads to any computer it can get to. It is a fact that any system will eventually encounter a virus. How significantly your network is affected by this encounter is entirely up to you, and the security measures you implement.
Because the virus poses such a significant threat, defending against such attacks is of paramount importance to any network administrator. Unfortunately some administrators feel that simply because they have a virus scanner installed they are safe. This assumption is inaccurate. In this chapter you will learn how virus attacks work and explore some real world examples of virus attacks. Then you will learn more about how antivirus software works and look at a few commercial solutions. You will also learn about appropriate policies your organization can implement to reduce the chance of your systems being infected by a virus. Finally, you will learn about configuration options on other devices (firewalls, routers, etc.) that can help reduce the threat of a virus infection.
Understanding Virus Attacks
Understanding what a virus is, how it spreads, and the different variations are essential for combating virus threats. You will also need to have a firm understanding of how a virus scanner works in order to make intelligent decisions about purchasing a virus scanner for your organization. In this section we will explore these topics in sufficient detail to equip you with the skills needed to establish a solid defense against virus attacks.
What Is a Virus?
Most people are familiar with computer viruses, but may not have a clear definition of what one is. A computer virus is a program that self-replicates. Generally, a virus will also have some other negative function such as deleting files or changing system settings. However, it is the self-replication and rapid spread that define a virus. Often this growth, in and of itself, can be a problem for an infected network. It can lead to excessive network traffic and prevent the network from functioning properly. Recall in Chapter 2 that we discussed the fact that all technology has a finite capacity to perform work. The more a virus floods a network with traffic, the less capacity is left for real work to be performed.
What Is a Worm?
A worm is a special type of virus. Some texts go to great lengths to differentiate worms and viruses, while others treat the worm as simply a subset of a virus. A worm is a virus that can spread without human intervention. In other words, a virus requires some human action in order to infect a machine (downloading a file, opening an attachment, and so on), but a worm can spread without such interaction. In recent years, worm outbreaks have become more common than the standard, nonworm virus.
How a Virus Spreads
The best way to combat viruses is to limit their spread, so it’s critical that you understand how they spread. A virus will usually spread in one of two ways. The most common, and the simplest, method is to read your e-mail address book and e-mail itself to everyone in your address book. Programming this is a trivial task, which explains why it is so common. The second method is to simply scan your computer for connections to a network, and then copy itself to other machines on the network to which your computer has access. This is actually the most efficient way for a virus to spread, but it requires more programming skill than the other method.
The first method is, by far, the most common method for virus propagation. Microsoft Outlook may be the one e-mail program most often hit with such virus attacks. The reason is not so much a security flaw in Outlook as it is the ease of working with Outlook.
There are a number of theories about why Microsoft Outlook is so frequently struck with virus attacks. One explanation is its prevalence in the marketplace. Virus writers wish to cause havoc. The best way to do that is to target the most commonly used systems.
Another reason that Outlook is so often targeted is that writing viruses for it is relatively easy. We previously mentioned the fact that many e-mail applications allow programmers to create extensions to the application. All Microsoft Office products are made so that a legitimate programmer who is writing software for a business can access many of the application’s internal objects and thereby easily create applications that integrate the applications within the Microsoft Office suite. For example, a programmer could write an application that would access a Word document, import an Excel spreadsheet, and then use Outlook to automatically e-mail the resulting document to interested parties. Microsoft has done a good job of making this process very easy, for it usually takes a minimum amount of programming to accomplish these tasks. Using Outlook, it takes less than five lines of code to reference Outlook and send out an e-mail. This means a program can literally cause Outlook itself to send e-mail, unbeknownst to the user. There are numerous code examples on the Internet that show exactly how to do this, free for the taking. For this reason, it does not take a very skilled programmer to be able to access your Outlook address book and automatically send e-mail. Essentially, the ease of programming Outlook is why there are so many virus attacks that target Outlook.
While the overwhelming majority of virus attacks spread by attaching themselves to the victim’s existing e-mail software, some recent virus outbreaks have used other methods for propagation. One method that is becoming more common is for viruses to have their own internal e-mail engine. A virus that has its own e-mail engine does not need to “piggy-back” off of the machine’s e-mail software. This means that, regardless of what e-mail software you use, this virus can still propagate from your machine. Another virus propagation method is to simply copy itself across a network. Virus outbreaks that spread via multiple routes are becoming more common.
Another way a virus can spread is by examining the affected system looking for any connected computers and copying itself to them. This sort of self-propagation does not require user interaction, so the program that uses this method to infect a system is classified as a worm.
Regardless of the way a virus arrives at your doorstep, once it is on your system, it will attempt to spread and, in many cases, will also attempt to cause some harm to your system. Once a virus is on your system, it can do anything that any legitimate program can do. That means it could potentially delete files, change system settings, or cause other harm. The threat from virus attacks cannot be overstated. Some recent virus outbreaks even went so far as to disable existing security software, such as antivirus scanners and firewalls. Let’s take a moment to examine a few virus attacks that are common as of this writing. Examining real-world virus outbreaks provides a firm understanding of how these work. For our purposes we will look at examples of both virus and worm attacks in this section.
The Zafi Worm
The first version of this worm was released only in the Hungarian language, so its spread was somewhat limited. However, by version Zafi.d it was spreading in English. This version of the virus, which purported to be a holiday greeting card, spread widely just before Christmas 2004. The use of the holiday greeting as a subject line for the e-mail significantly increased its chances of being read. Its strategic timing probably lead to its infecting more systems than it otherwise would have. The virus has its own SMTP e-mail engine and sends itself out to as many addresses as it can find. This worm grabs e-mail addresses from a number of different file types it might find on a computer, including HTML, ASP, text files, and others.
Once a system is infected, in addition to e-mailing itself out to e-mail addresses, it attempts to detect antivirus program files on the computer and overwrite them with a copy of itself. This disabling of antivirus software made Zafi.d particularly dangerous. Some versions of Zafi (Kaspersky Labs, 2004) also attempt a DoS attack on the following sites:
A typical Zafi worm e-mail is shown in Figure 9.1.
Mabutu
This virus also has its own built-in e-mail engine and harvests e-mail addresses from text files, HTML files, and other files on the victims’ computers (F-Secure, 2004). You should note how common it is becoming for a virus to:
![]() Have its own built-in e-mail engine, freeing it from dependence upon the victims’ e-mail software.
Have its own built-in e-mail engine, freeing it from dependence upon the victims’ e-mail software.
![]() Derive e-mail addresses from sources other than the victims’ address books.
Derive e-mail addresses from sources other than the victims’ address books.
![]() Disable the virus scanner of the infected machine, thus allowing even more viruses to infect that machine, a particularly disturbing trend.
Disable the virus scanner of the infected machine, thus allowing even more viruses to infect that machine, a particularly disturbing trend.
Once the virus is installed, it will change the registry so that it is loaded at startup. It will also try to connect to one of several IRC (Internet relay chat) servers. It will use these connections to send information about the infected computer.
Bropia
This worm had been circulating the Internet for months before new variations were seen in February 2005. This worm spreads via MSN Messenger. It may also be able to spread using Windows Messenger. It drops a variant of the Rbot worm family, Win32.Rbot.BPR. Many variations of the Rbot worm actually open a backdoor on the target system allowing intruders access. It then attempts to send this file using MSN Messenger to all active MSN contacts. The recipient has to accept and open the file to get infected by the worm. Three factors make this worm interesting. First, it spreads through instant messaging. As instant messaging and chat rooms become more widely used, you can expect to see more viruses and worms that affect them. Second, it drops two worms on the affected machine: its own, and a second worm that it has in its payload. This two-pronged attack makes it more difficult to defend against. That second worm is C:osm.exe (a variant of W32.Spybot.Worm). The third interesting aspect of this virus is the number of variations—more than a dozen so far. This is important for two reasons:
![]() They indicate that more virus writers are producing versions of this virus.
They indicate that more virus writers are producing versions of this virus.
![]() The different variations make it more difficult to detect and avoid the virus.
The different variations make it more difficult to detect and avoid the virus.
Santy
The Santy worm exploits a vulnerability in bulletin boards and online forums that are written with the very popular phpBB software, using the Google search engine to find vulnerable servers. It does not infect end user computers.
The worm is written in the Perl scripting language. As previously mentioned, the worm uses the Google search engine to look for hosts that have phpBB software in use. It accomplishes this by searching for URLs that contain the string viewtopic.php. In order to get varied results with different searches, the worm uses a random string in the search as well.
If a suitable URL is found, the worm then attempts to exploit a vulnerability in phpBB software. This vulnerability, known as the Highlight Vulnerability, can be used to execute arbitrary code on the server running a vulnerable version of phpBB. If it successfully infects the target server, all affected Web pages will be replaced with a simple message stating, “This Site is Defaced.”
The Virus Hoax
In recent years a new virus phenomenon has become more common—the virus hoax. Rather than actually writing a virus, a person sends an e-mail to every address he has. The e-mail claims to be from some well-known antivirus center, and warns of a new virus that is circulating that might damage the user’s computer. Often the e-mail instructs people to delete some file from their computer to get rid of the virus. The file, however, is not really a virus but part of a computer’s system. The jdbgmgr.exe virus hoax used this scheme. It encouraged the reader to delete a file that was actually needed by the system. Surprisingly, a number of people followed this advice and not only deleted the file, but promptly e-mailed their friends and colleagues to warn them to delete the file from their machines.
Jdbgmgr Hoax
This particular virus hoax is perhaps the most well known and well examined. You will see some mention of it in almost any comprehensive discussion of viruses. The jdbgmgr.exe virus hoax (Vmyths.com, 2004) encouraged the reader to delete a file that was actually needed by the system. The typical message looked like this:
I found the little bear in my machine because of that I am sending this message in order for you to find it in your machine. The procedure is very simple:
The objective of this e-mail is to warn all Hotmail users about a new virus that is spreading by MSN Messenger. The name of this virus is jdbgmgr.exe and it is sent automatically by the Messenger and by the address book too. The virus is not detected by McAfee or Norton and it stays quiet for 14 days before damaging the system.
The virus can be cleaned before it deletes the files from your system. In order to eliminate it, it is just necessary to do the following steps:
1. Go to Start, click Search.
2. In the Files or Folders option write the name jdbgmgr.exe.
3. Once you have found that file, delete it.
Jdbgmgr.exe is actually the Microsoft Debugger Registrar for Java. Deleting it may cause Java-based programs and Web applets not to function properly.
Tax Return Hoax
This hoax first surfaced in 2003. The essential point of the e-mail was to make the recipient think that submitting federal taxes in the United States via the Internet was not safe (McAfee Virus Hoax Listings, 2003). The fact was that such online submissions were perfectly safe and usually resulted in much faster refunds for the taxpayer. The e-mail body looked something like this:
Fortunately this particular hoax did not cause any actual damage to the infected machine. However, it did dissuade victims from using a valuable and efficient service, online tax return processing, thus causing a great deal of inconvenience for the victim. You should remember this incident when we discuss information warfare in Chapter 14. This e-mail hoax was clearly designed to erode confidence in a government service.
The W32.Torch Hoax
This hoax, like most others, causes no direct harm but can become a huge annoyance — the Internet equivalent of a prank phone call. Unlike the jdbmgre.exe hoax, it does not encourage you to delete files from your system. However it does induce a fair amount of concern in recipients. In this hoax a message is sent stating the following:
NEW VIRUS DESTROYS HARDWARE
A new virus found recently is capable of burning the CPU of some computers and even causing damage to the motherboard. Yes, it’s true, this virus damages the hardware of your computer. The virus, called w32.torch, uses the winbond w83781d chip, present in most modern motherboards, which is responsible for controlling the speed of the CPU and system fans. The infection takes place using the well-known Microsoft DCOM net-trap Vulnerability, and when installed, the virus spreads to other computers in the local network using this method. Reverse-engineering the virus code, we find no evidence of code other than that responsible for the CPU burnout. The virus turns off the high temperature detection in the BIOS (already disabled by default) and then slowly decreases the speed of the fans, leading the system to a deadly increase of the internal temperature. If you feel that your computer is becoming “quiet,” it’s better to check it out because it may be stopping, and you may have only a few minutes left to disconnect it. The virus contains the text “Moscow Dominates - out/27/03” which is shown in the tray of some machines based on their IP address, perhaps indicating Soviet origin. There is no payload set to activate on this date, but it may be an indication that something is supposed to happen on this day. Some antiviruses already detect it, check if yours is up to date.
To date, there have not been any viruses that directly damage hardware.
Virus Scanners
The most obvious defense against viruses is the virus scanner. A virus scanner is essentially software that tries to prevent a virus from infecting your system. Usually it scans incoming e-mail and other incoming traffic. Most virus scanners also have the ability to scan portable media devices such as floppy drives. Most people are aware, in a general way, of how virus scanners work. In this section you will learn in more detail how scanners operate.
In general, virus scanners work in two ways. The first method is that they contain a list of all known virus files. Generally, one of the services that vendors of virus scanners provide is a periodic update of this file. This list is typically in a small file, often called a .dat file (short for data). When you update your virus definitions, what actually occurs is that your current file is replaced by the more recent one on the vendor’s Web site.
Every virus scanner I have ever personally examined also allows you to configure it to periodically download the latest such updates. It is critical that, no matter which virus scanner you choose, you configure it to automatically update itself.
The antivirus program then scans your PC, network, and incoming e-mail for known virus files. Any file on your PC or attached to an e-mail is compared to the virus definition file to see whether there are any matches. With e-mail, this can be done by looking for specific subject lines and content. Known virus files often have specific phrases in the subject line and the body of the messages they are attached to. Yet viruses and worms can have a multitude of headers, some of which are very common, such as re:hello or re:thanks. Scanning against a list of known viruses alone would result in many false positives. Therefore, the virus scanner also looks at attachments to see whether they are of a certain size and creation date that matches a known virus or whether it contains known viral code. The file size, creation date, and location are the telltale signs of a virus. Depending on the settings of your virus scanner, you may be prompted to take some action, the file may be moved to a quarantined folder, or the file may simply be deleted outright. This type of virus scanning works only if the .dat file for the virus scanner is updated, and only for known viruses.
Another way a virus scanner can work is to monitor your system for certain types of behavior that are typical of a virus. This might include programs that attempt to write to a hard drive’s boot sector, change system files, alter the system registry, automate e-mail software, or self-multiply. Another technique virus scanners often use is searching for files that stay in memory after they execute. This is called a Terminate and Stay Resident (TSR) program. Some legitimate programs do this, but it is often a sign of a virus.
Many virus scanners have begun employing additional methods to detect viruses. Such methods include scanning system files and then monitoring any program that attempts to modify those files. This means the virus scanner must first identify specific files that are critical to the system. With a Windows system, these include the registry, the boot.ini, and possibly other files. Then, if any program attempts to alter these files, the user is warned and must first authorize the alteration before it can proceed.
It is also important to differentiate between on-demand virus scanning and ongoing scanners. An ongoing virus scanner runs in the background and is constantly checking a PC for any sign of a virus. On-demand scanners run only when you launch them. Most modern antivirus scanners offer both options.
Virus Scanning Techniques
Now that you have learned the general strategies virus scanners use, let’s take a more detailed look at specific virus scanning techniques employed by various virus scanners.
E-mail and Attachment Scanning
Since the primary propagation method for a virus is e-mail, e-mail and attachment scanning is the most important function of any virus scanner. Some virus scanners actually examine your e-mail on the e-mail server before downloading it to your machine. Other virus scanners work by scanning your e-mail and attachments on your computer before passing it to your e-mail program. In either case, the e-mail and its attachments should be scanned prior to your having any chance to open it and release the virus on your system. This is a critical difference. If the virus is first brought to your machine, and then scanned, there is a chance, however small, that the virus will still be able to infect your machine. Most commercial network virus scanners will scan the e-mail on the server before sending it on to the workstations.
Download Scanning
Anytime you download anything from the Internet, either via a Web link or through some FTP program, there is a chance you might download an infected file. Download scanning works much like e-mail and attachment scanning, but does so on files you select for downloading.
File Scanning
Download and e-mail scanning will only protect your system against viruses that you might get downloading from a site, or that come to you in e-mail. Those methods will not help with viruses that are copied over a network, deposited on a shared drive, or that are already on your machine before you install the virus scanner.
This is the type of scanning in which files on your system are checked to see whether they match any known virus. This sort of scanning is generally done on an on-demand basis instead of an ongoing basis. It is a good idea to schedule your virus scanner to do a complete scan of the system periodically. I personally recommend a weekly scan, preferably at a time when no one is likely to be using the computer.
It does take time and resources to scan all the files on a computer’s hard drive for infections. This type of scanning uses a method similar to e-mail and download scanning. It looks for known virus signatures. Therefore this method is limited to finding viruses that are already known and will not find new viruses.
Heuristic Scanning
This is perhaps the most advanced form of virus scanning. This sort of scanning uses rules to determine whether a file or program is behaving like a virus, and is one of the best ways to find a virus that is not a known virus. A new virus will not be on any virus definition list, so you must examine its behavior to determine whether it is a virus. However, this process is not foolproof. Some actual virus infections will be missed, and some non-virus files might be suspected of being a virus.
The unfortunate side effect of heuristic scanning is that it can easily lead to false positives. This means that it might identify a file as a virus, when in fact it is not. Most virus scanners do not simply delete viruses. They put them in a quarantined area, where you can manually examine them to determine whether you should delete the file or restore it to its original location. Examining the quarantined files rather than simply deleting them all is important because some can be false positives. In this author’s personal experience, false positives are relatively rare with most modern virus scanners.
As the methods for heuristic scanning become more accurate, it is likely that more virus scanners will employ this method, and will rely on it more heavily. Right now it offers the most promise for the greatest protection for your system. However the various algorithms used in heuristic scanning are relatively new, and time and research is required to realize their full potential.
Active Code Scanning
Modern Web sites frequently embed active codes, such as Java applets and ActiveX. These technologies can provide some stunning visual effects to any Web site. However, they can also be vehicles for malicious code. Scanning such objects before they are downloaded to your computer is an essential feature in any quality virus scanner. Also recall from Chapter 8 we discussed altering your browser to prompt you before executing any such active code on a Web site. Combining that browser configuration with an antivirus software package that scans for active code can significantly reduce the chances of your being infected with this sort of virus.
Instant Messaging Scanning
Instant message scanning is a relatively new feature of virus scanners. Virus scanners using this technique scan instant messaging communications looking for signatures of known virus or Trojan horse files. In recent years the use of instant messaging has increased dramatically. It is now frequently used for both business and recreational purposes. This growing popularity makes virus scanning for instant messaging a vital part of effective virus scanning. If your antivirus scanner does not scan instant messaging, then you should either avoid instant messaging or select a different antivirus package.
Most commercial virus scanners use a multi-modal approach to scanning. They employ a combination of most, if not all, of the methods we have discussed here. Any scanner that does not employ most of these methods will have very little value as a security barrier for your system.
Commercial Antivirus Software
There are a number of antivirus packages available for individual computers and for network-wide virus scanning. We will examine some of the more commonly encountered antivirus software here. It is important that you consider the following factors when purchasing a virus scanning solution for your own organization or recommending a solution to a client:
![]() Budget: Price should not be the only, or even the most important, consideration, but it certainly must be considered.
Budget: Price should not be the only, or even the most important, consideration, but it certainly must be considered.
![]() Vulnerability: An organization with diverse users who frequently get e-mail from outside the organization or download from the Internet will need more antivirus protection than a small homogeneous group that uses the Internet only intermittently.
Vulnerability: An organization with diverse users who frequently get e-mail from outside the organization or download from the Internet will need more antivirus protection than a small homogeneous group that uses the Internet only intermittently.
![]() Skill: Whoever will ultimately use the product must be able to understand how to use it. Are you getting a virus scanner for a group of tech-savvy engineers or a group of end users who are unlikely to be technically proficient?
Skill: Whoever will ultimately use the product must be able to understand how to use it. Are you getting a virus scanner for a group of tech-savvy engineers or a group of end users who are unlikely to be technically proficient?
![]() Technical: How does the virus scanner work? What methods does it use to scan? How often are the .dat files updated? How quickly does the vendor respond to new virus threats and release new .dat files?
Technical: How does the virus scanner work? What methods does it use to scan? How often are the .dat files updated? How quickly does the vendor respond to new virus threats and release new .dat files?
All of these factors must be considered when selecting antivirus solutions. Too often security experts simply recommend a product they are familiar with without doing significant research. This section introduces a variety of antivirus solutions and the benefits of each.
McAfee VirusScan
McAfee is a well-known antivirus vendor. This company offers solutions for the home user and large organizations. All of McAfee’s products have some common features, including e-mail scanning and file scanning. They also scan instant messaging traffic.
McAfee scans e-mail, files, and instant messaging for known virus signatures, and uses heuristic methods to locate new worms. Given the growing use of worms (in contrast with traditional viruses), this is an important benefit. McAfee offers a relatively easy download and install, and you can get a trial version from the company’s Web site. We will take a look at features of the home version, which functions similarly to the enterprise version.
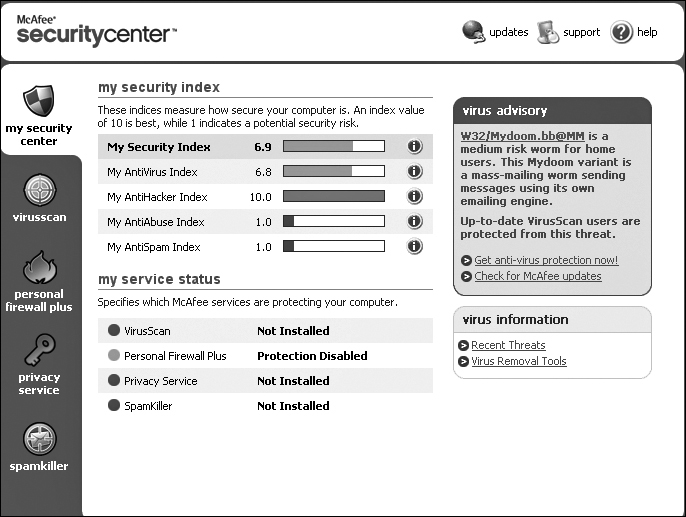
Figure 9.2 shows the main screen of the McAfee antivirus software. You can see that McAfee has an integrated management screen for multiple security products, including its firewall and antivirus products. The main screen displays a security index for your computer, listed by category. You can get a detailed analysis for each security rating by clicking on the security index.
Select virusscan>Options to select what you wish to scan, how you wish to scan, and when you wish to scan. Figure 9.3 shows the Options dialog box. You can choose to scan inbound files, e-mail, instant messages, and so on. You can also choose to schedule scans to occur at set times, and then select whether you wish to scan the entire machine.
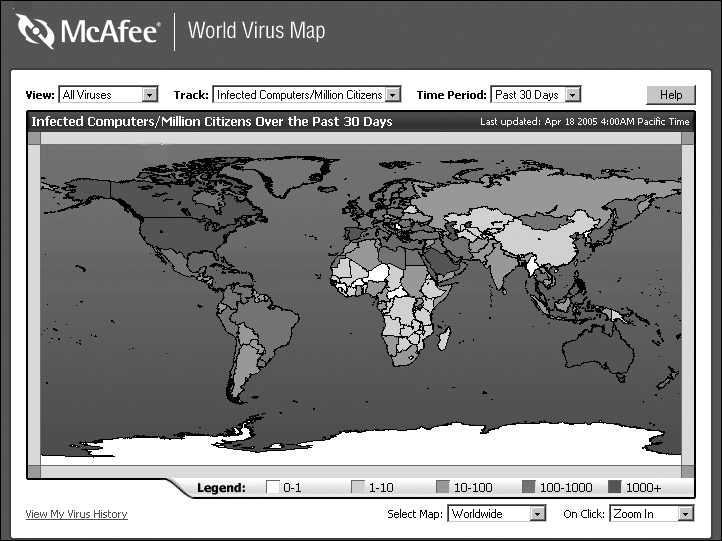
Of particular interest is the McAfee virus world map, shown in Figure 9.4. This is a map of virus activity currently going on in the world. This can be invaluable information for a security professional, particularly if your organization is geographically widespread.
This map is quite useful. You can select all viruses, or only the top 10. You can also choose to view by a specific geographical area any computers infected per million users, or how many files are infected per million users. If you click on any area of the map you will zoom down to that geographical area. You can continue to zoom until you are viewing individual cities, allowing you to find out a great deal about virus infections in any geographical region.
If you consider the four criteria we listed previously—budget, vulnerability, skill, and technical — McAfee rates quite well:
![]() It is very affordable.
It is very affordable.
![]() Different versions are available for different levels of vulnerability.
Different versions are available for different levels of vulnerability.
![]() It is relatively easy to use, requiring only limited skill to utilize.
It is relatively easy to use, requiring only limited skill to utilize.
![]() It is technically a very good scanner, using multiple modalities to scan for viruses. It also has interesting added features such as the virus infection map.
It is technically a very good scanner, using multiple modalities to scan for viruses. It also has interesting added features such as the virus infection map.
These features make McAfee a good choice for home users as well as corporate networks.
Norton AntiVirus
Norton AntiVirus is also a widely known vendor of antivirus software. You can purchase Norton solutions for individual computers or for entire networks. Norton offers e-mail and file scanning, as well as instant messaging scanning. It also offers a heuristic approach to discovering worms and traditional signature scanning. Recent versions of Norton AntiVirus have also added anti-spyware and anti-adware scanning, both very useful features. An additional interesting feature of Norton AntiVirus is the pre-install scan. During the installation the install program scans the machine for any virus infections that might interfere with Norton. Because it is becoming more common to find virus attacks that actually seek to disable antivirus software, this feature is very helpful.
While Norton, like most antivirus vendors, offers versions for individual PCs and for entire networks, the individual version has a free trial version you can download and experiment with for 15 days without any charge. We will briefly examine this product to illustrate how Norton AntiVirus products function.
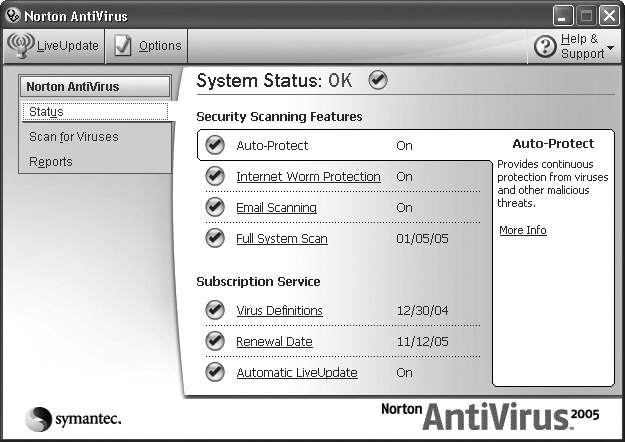
When you download the product, you get a self-extracting executable. Simply double-click on that in either Windows Explorer or My Computer, and it will install itself with very little interaction from you. When you launch Norton, the initial screen, shown in Figure 9.5, gives you valuable information. It lets you know what sorts of scans are turned on, when the last full system scan was done, and when the last update of virus definitions was accomplished. This is quite critical information. If your virus definitions have not been updated recently, then you simply are not protected against the newest viruses. Knowing when the last full system scan was done tells you how safe your computer currently is. Of course, you will also need to know what types of scans are turned on in order to know what threats Norton is protecting you against.
If you select Scan for Viruses on the left, you are given a number of options, shown in Figure 9.6. You can scan floppy disks, removable media, hard drives, or particular files and folders. The larger the area you select to scan, the longer the scan will take.
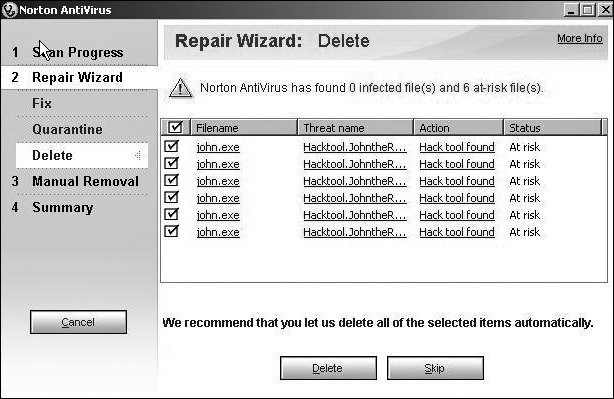
When a scan is done, Norton lists all suspect files and gives you the option of quarantining, deleting, or ignoring them, as shown in Figure 9.7. A fascinating aspect of Norton is that it also detects many common hacking tools. In Figure 9.7, you can see that Norton identified John the Ripper, a common password cracker, as a hacking tool. This can be quite useful because any hacking tools on your machine that you did not put there can be a sign that your machine has been hacked and that the hacker is continuing to use your machine. The intruder may even be using your machine to launch attacks on other machines.
On the main Norton screen there is also an important option labeled Reports. It gives you access to the virus encyclopedia maintained by Norton, as well as a report of all scans done. In an organizational setting you should probably periodically print and file this report. This provides valuable information for an audit. When you run any of these reports, it documents the scans you did, for what viruses, and when you did them. These can be kept so that during any future audits you can easily verify the steps you have taken to prevent virus infections.
Again, if you consider the four criteria we listed previously—budget, vulnerability, skill, and technical—Norton also rates quite well:
![]() It is very affordable. McAfee and Norton are both similarly priced.
It is very affordable. McAfee and Norton are both similarly priced.
![]() Different versions are available for different levels of vulnerability. Most commercial antivirus vendors offer a range of products for different situations.
Different versions are available for different levels of vulnerability. Most commercial antivirus vendors offer a range of products for different situations.
![]() Its graphical interface makes configuring and using Norton as easy as performing the same tasks with McAfee.
Its graphical interface makes configuring and using Norton as easy as performing the same tasks with McAfee.
![]() It is technically a very good scanner, using multiple modalities to scan for viruses. The fact that it also picks up hacking tools, in addition to viruses, is an added benefit.
It is technically a very good scanner, using multiple modalities to scan for viruses. The fact that it also picks up hacking tools, in addition to viruses, is an added benefit.
Like McAfee, Norton is a solid choice for both home and business users. It provides an easy to use tool that is also quite effective.
Avast! Antivirus
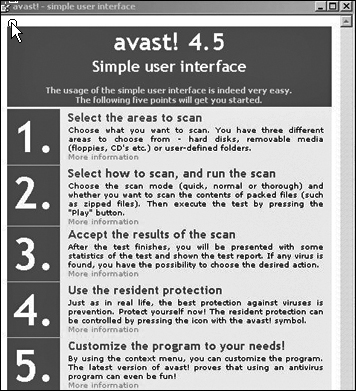
This product is offered for free for home, noncommercial uses. You can download the product from the vendor’s Web site: www.avast.com/. You can also find professional versions, versions for Unix or Linux, and versions specifically for servers. Of particular interest is that this product is available in multiple languages including English, Dutch, Finnish, French, German, Spanish, Italian, and Hungarian. Figure 9.8 shows the main Avast! screen.
If you download it, you can see that Avast! opens up with a tutorial. This feature, combined with the fact that the home version is free, makes this a very attractive tool for the novice home user. The multilanguage and multioperating system supports make it attractive to many professionals. When it finds a virus, it sounds an alarm and then a voice states “Warning: There is a virus on your computer.” However, when I scanned my PC with Avast!, it did not detect the older hacking tools as items of concern, unlike Norton.
Let’s use our four criteria we listed previously—budget, vulnerability, skill, and technical—to evaluate Avast!:
![]() It is free, making it more affordable than either Norton or McAfee.
It is free, making it more affordable than either Norton or McAfee.
![]() There is a commercial version of Avast! for enterprise settings.
There is a commercial version of Avast! for enterprise settings.
![]() It also has a graphical interface making it easy to use, and the fact that it initially launches with a tutorial makes it ideal for the novice.
It also has a graphical interface making it easy to use, and the fact that it initially launches with a tutorial makes it ideal for the novice.
![]() It is a reasonably good scanner. However, it lacks added features such as McAfee’s virus map and Norton’s ability to pick up hacking tools.
It is a reasonably good scanner. However, it lacks added features such as McAfee’s virus map and Norton’s ability to pick up hacking tools.
For a commercial setting you should probably use Norton or McAfee. However, Avast! is a good choice for the small office or home user. The fact that it is free means there is absolutely no reason why anyone should ever go without a virus scanner.
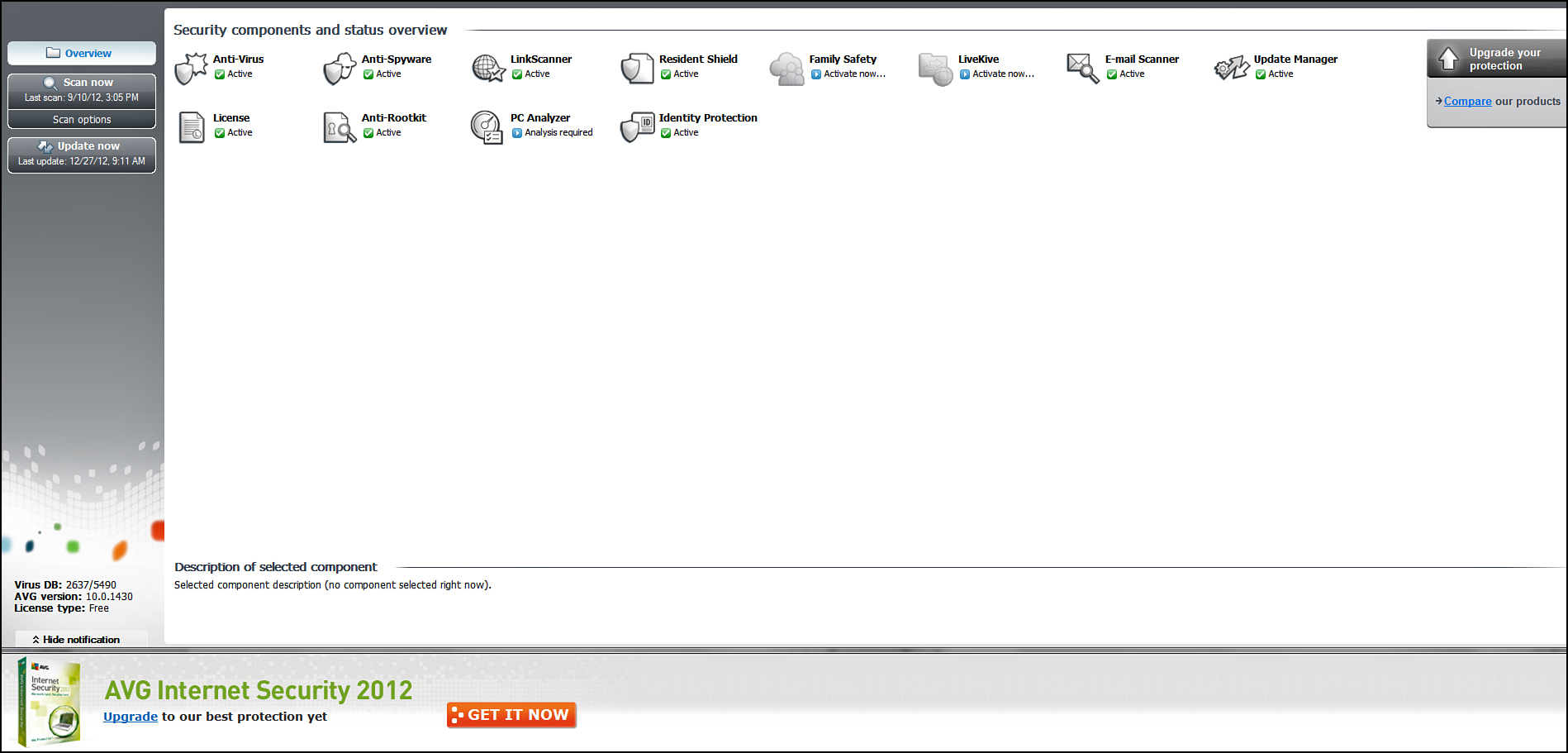
AVG
AVG antivirus has become quite popular. One reason is that there is a free version of it as well as a commercial version. The main screen is shown in Figure 9.9.
AVG is robust and full-featured antivirus software. It integrates with e-mail clients such as Microsoft Outlook and it also filters web traffic and downloads.
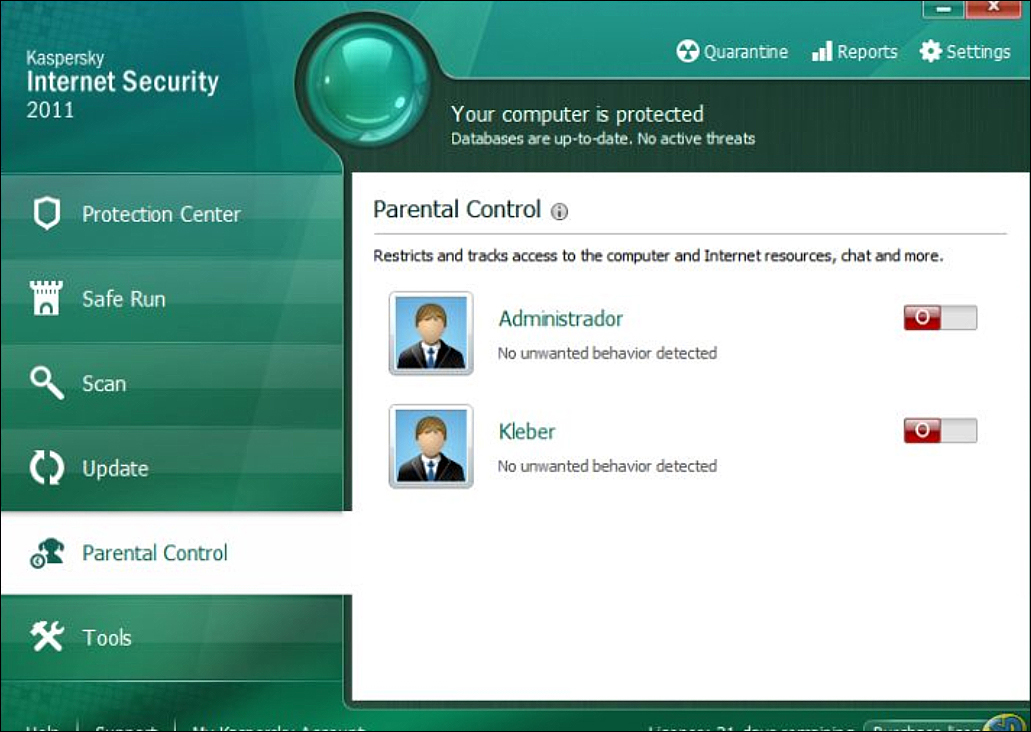
Kapersky
Kapersky has been growing in popularity. It includes business and personal versions. Like most antivirus products it also includes additional features not directly related to detecting viruses. For example, Kapersky includes an encrypted password vault to keep your passwords in, if you want to. You can see a screenshot in Figure 9.10.
Panda
Panda (www.pandasoftware.com) is available in both commercial editions and free versions. The commercial version also comes with anti-spyware. Like Norton and McAfee, you can get a personal firewall bundled with the antivirus software. This product is available in English, French, and Spanish. This wide range of features makes this product a robust and effective solution.
Other Virus Scanners
In addition to McAfee, Norton, Avast!, PC-cillin, and Panda there are a number of other antivirus packages available on the Internet. A simple Web search will reveal a plethora of antivirus products. As a security professional or a network administrator, it is critical that you be comfortable with multiple antivirus solutions and not simply rely on the most popular or widely known solution. It is important that you base decisions about what antivirus software to use on the facts regarding the product (how it works, ease of use, cost, etc.). The most popular product might not be the best product—or the ideal product—for your environment.
Antivirus Policies and Procedures
Examining how virus attacks spread and looking at specific attacks offers a clear picture of the dangers posed by viruses. We have also taken a look at how virus scanners work, including examining some commercial antivirus products. However, antivirus scanners are not the only facet of protecting yourself against viruses. In fact there are situations in which a virus scanner is simply not enough. You will need policies and procedures to complete your antivirus strategy. Policies and procedures are simply written rules that dictate certain actions that administrators and end users should take and other activities they should avoid. The following is a brief examination of appropriate antivirus polices. Policies will be discussed in greater detail in Chapter 11.
![]() Always use a virus scanner. McAfee, Norton, AVG, and Kapersky are the four most widely known and used virus scanners. However, we have also examined other solutions. It costs only about $30 a year to keep your virus scanner updated. It can cost much more to not do it.
Always use a virus scanner. McAfee, Norton, AVG, and Kapersky are the four most widely known and used virus scanners. However, we have also examined other solutions. It costs only about $30 a year to keep your virus scanner updated. It can cost much more to not do it.
![]() If you are not sure about an attachment, do not open it. When you have specifically requested a file from someone, then opening an attachment from that person is probably safe. However, unexpected attachments are always cause for concern.
If you are not sure about an attachment, do not open it. When you have specifically requested a file from someone, then opening an attachment from that person is probably safe. However, unexpected attachments are always cause for concern.
![]() Consider exchanging a code word with friends and colleagues. Tell them to put the code word in the title of the message if they wish to send you an attachment. Without the code word, do not open any attachment.
Consider exchanging a code word with friends and colleagues. Tell them to put the code word in the title of the message if they wish to send you an attachment. Without the code word, do not open any attachment.
![]() Do not believe “security alerts” you are sent. Microsoft does not send out patches in this manner. Go check its Web site regularly, as well as one of the antivirus Web sites previously mentioned.
Do not believe “security alerts” you are sent. Microsoft does not send out patches in this manner. Go check its Web site regularly, as well as one of the antivirus Web sites previously mentioned.
![]() Be skeptical of any e-mail you are sent. Keeping e-mail to official traffic will help reduce your danger. Jokes, flash movies, and so on simply should not be sent on a company e-mail system.
Be skeptical of any e-mail you are sent. Keeping e-mail to official traffic will help reduce your danger. Jokes, flash movies, and so on simply should not be sent on a company e-mail system.
![]() Do not download files from the Internet. If you need a file downloaded, the IT department should do that, carefully scan the file, and then forward it to the user. Now clearly many people will choose to download files, so this admonition is an ideal that is unlikely to be realized. If you feel compelled to download files you should follow two simple rules:
Do not download files from the Internet. If you need a file downloaded, the IT department should do that, carefully scan the file, and then forward it to the user. Now clearly many people will choose to download files, so this admonition is an ideal that is unlikely to be realized. If you feel compelled to download files you should follow two simple rules:
1. Only download from well-known, reputable sites.
2. Download to a machine that is off the network first. Then you can scan that system for viruses. In fact, if you do request your IT department download something for you, this is likely to be the process they use.
These policies will not make a system 100 % virus proof, but they will go a long way in protecting it. Feel free to expand upon them any way you see fit.
Additional Methods for Defending Your System
Installing and running antivirus software and having solid antivirus policies are both very important steps in protecting your system. In fact, many organizations use only these two steps. However, there are other important steps you can take to secure your system against virus attacks:
![]() Set all browsers to block active code (ActiveX, scripts, etc.). Be aware that this will render some Web sites unviewable. A compromise between security and usability would be to set all browsers to warn the user before executing any active code.
Set all browsers to block active code (ActiveX, scripts, etc.). Be aware that this will render some Web sites unviewable. A compromise between security and usability would be to set all browsers to warn the user before executing any active code.
![]() Set all user accounts so that they cannot install software or change browser security settings.
Set all user accounts so that they cannot install software or change browser security settings.
![]() Segregate subnetworks (especially high-risk subnets like college campus labs) and place a firewall that is tightly secured with its own virus scanning between that subnet and the rest of the network.
Segregate subnetworks (especially high-risk subnets like college campus labs) and place a firewall that is tightly secured with its own virus scanning between that subnet and the rest of the network.
Clearly these items are extras. Many organizations do not segregate subnetworks nor do they block users from installing software or changing browser security settings. Many organizations are satisfied with simply installing antivirus scanners and setting up a few policies. However, if you want a truly complete antivirus strategy, these extra steps are part of that complete strategy.
What to Do If Your System Is Infected by a Virus
The unfortunate reality is that no matter what steps you take to prevent virus infections, there is still a chance your system will become infected with a virus. The next question is, what do you do? Some facets of your response will depend upon the severity of the virus and how far it has spread, but generally you need to focus on three things:
![]() Stopping the spread of the virus.
Stopping the spread of the virus.
![]() Removing the virus.
Removing the virus.
![]() Finding out how the infection started.
Finding out how the infection started.
The following sections examine each in detail and explain how to accomplish them.
Stopping the Spread of the Virus
In the event of a virus infection, the first priority is to stop the spread of the infection. How this is done will, of course, depend on how far the virus has spread. If the virus has only affected one machine, you can simply disconnect that machine from the network. However, it is unlikely that you will detect a virus before it has spread beyond a single machine. Given that fact, you will generally wish to follow these steps:
![]() If the infection is on a segment of a WAN, then immediately disconnect from that WAN connection.
If the infection is on a segment of a WAN, then immediately disconnect from that WAN connection.
![]() If the infection is on a subnetwork, immediately disconnect that subnetwork.
If the infection is on a subnetwork, immediately disconnect that subnetwork.
![]() If there are servers with sensitive data that are connected (in any way) to the infected machine (or machines), disconnect those servers. This will prevent loss of sensitive data.
If there are servers with sensitive data that are connected (in any way) to the infected machine (or machines), disconnect those servers. This will prevent loss of sensitive data.
![]() If there are backup devices connected to the infected machine or machines, disconnect them. This will prevent your backup media from becoming infected.
If there are backup devices connected to the infected machine or machines, disconnect them. This will prevent your backup media from becoming infected.
Obviously your goal is to avoid getting a virus on your system. However, should that unfortunate event occur, following these steps can minimize the damage and get your system back up and functioning in a shorter period of time.
Removing the Virus
Once you have isolated the infected machine or machines, the next step is to clean them. If you know the specific virus, then you should be able to remove it by either running an antivirus program, or you should be able to find virus removal instructions on the Internet. In the highly unlikely event that you cannot remove the virus, then you may have no other choice but to format the machine (or machines) and restore them from backups. However, it must be stressed that such a situation is very unlikely.
If you do successfully remove the virus, you will want to scan the machine thoroughly for any other virus infections before reconnecting it to your network. You want to make absolutely certain it is completely clean before putting it back online.
Finding Out How the Infection Started
Once you have contained and removed the virus, the next goal is to see that it does not recur. This is best done by finding out how the virus got onto your system in the first place. To do this, you need to investigate the situation in three ways:
![]() Talk to users of the infected machines and see if anyone opened any e-mail attachments, downloaded anything, or installed anything. Since these are the three most likely avenues for virus infection, they should be checked first.
Talk to users of the infected machines and see if anyone opened any e-mail attachments, downloaded anything, or installed anything. Since these are the three most likely avenues for virus infection, they should be checked first.
![]() Read any online documentation for that specific virus. It will tell you the normal method of propagation.
Read any online documentation for that specific virus. It will tell you the normal method of propagation.
![]() If neither of those avenues tells you what occurred, check any activity logs that machine might have.
If neither of those avenues tells you what occurred, check any activity logs that machine might have.
The key is to find out what went wrong in your current security strategy and correct it.
Summary
Virus attacks, and even virus hoaxes, are arguably the greatest threat to computer networks. The sophistication of virus delivery methods is increasing, with worms becoming more and more common. There are a number of steps you can take to mitigate the dangers posed by computer virus outbreaks.
Clearly the first step is to use a virus scanner. However, you absolutely must have a firm understanding of how virus scanners work in order to select the appropriate scanner for your situation. There are a variety of commercial and free antivirus solutions. Any security professional should be familiar with several of these. After installing and configuring an antivirus solution, the next step is establishing written policies and procedures. It is critical that you detail exactly how you want end users to use the system tools. Any situation you do not cover in your policies is an opportunity for a virus infection. Finally, you can take even more serious steps including blocking users from installing software, securely configuring the browser, and separating subnetworks in order to limit the spread of any virus that might infect your machines. Combining antivirus software with secure configuration of your systems, routine patching of software, firewalls, and sound security policies results in more complete protection. While the various topics in this book are segmented into chapters, it is critical that you remember that a complete security strategy must have all these elements working together.
Test Your Skills
Multiple Choice Questions
1. In addition to any malicious payload, what is the most common way a virus or worm causes harm to a system?
A. By increasing network traffic and overloading the system
B. By overfilling your inbox
C. By executing a DoS attack on a host
D. By containing a Trojan horse
2. What differentiates a virus from a worm?
A. Worms spread farther than viruses.
B. Worms are more likely to harm the infected system.
C. Worms propagate without human intervention.
D. Worms delete system files more often than viruses do.
3. Which of the following is the primary reason that Microsoft Outlook is so often a target for virus attacks?
A. Many hackers dislike Microsoft.
B. Outlook copies virus files faster.
C. It is easy to write programs that access Outlook’s inner mechanisms.
D. Outlook is more common than other e-mail systems.
4. What is the most common method of virus propagation?
A. On infected floppy disks
B. On infected CDs
C. Through instant messaging attachments
D. Through e-mail attachments
5. Which of the following did the most to contribute to the wide spread of the Zafi.d.worm?
A. It claimed to be from the IRS.
B. It claimed to be a holiday card and was released just prior to a major holiday.
C. It used a script attachment rather than active code.
D. It used active code rather than a script attachment.
6. What was the most dangerous aspect of Zafi.d?
A. It deleted the registry.
B. It tried to overwrite parts of virus scanners.
C. It attempted to overwrite key system files.
D. It sent out information about the infected computer.
7. What was the primary propagation method for the Mabutu virus?
A. It used its own SMTP engine to e-mail itself.
B. It “piggy backed” off of MS Outlook.
C. It was on infected floppy disks.
D. It was attached to Flash animations.
8. What additional malicious activity did the Mabutu virus attempt?
A. It deleted the registry.
B. It tried to overwrite parts of virus scanners.
C. It attempted to overwrite key system files.
D. It sent out information about the infected computer.
9. What was the taxpayer virus hoax?
A. An e-mail that claimed that online tax submissions were infected and unsafe
B. An e-mail that tried to get the victim to send tax checks to a phony address
C. A virus that deleted all tax-related files from the target computer
D. A virus that infected the U.S. Internal Revenue Service in 2003
10. In the context of viruses, what is a .dat file?
A. A file containing system information
B. A file that is infected
C. A file with corrupt data
D. A file with virus definitions
11. What is Heuristic scanning?
A. Scanning using a rules-based approach
B. Scanning based on a virus definition file
C. Scanning only system management areas (registry, boot sector, etc.)
D. Scheduled scanning
12. What is active code scanning?
A. Scanning that is occurring all the time, (i.e. actively)
B. Scanning for active Web elements (Scripts, ActiveX, and so on)
C. Actively scanning for malicious code
D. Actively scanning for worms
13. Which of the following should be the least important consideration when purchasing antivirus software?
A. The type of scanning the software uses
B. How quickly the software updates in response to new viruses
C. How easy it is to configure and use
D. Cost of the software
14. Which of the following is a useful feature in McAfee not found in most other antivirus solutions?
A. It does a pre-installation scan.
B. It starts with a tutorial for new users.
C. Its main screen has a security rating for your system.
D. It uses heuristic scanning.
15. Which of the following is a useful feature in Norton AntiVirus not found in most other antivirus solutions?
A. It does a pre-installation scan.
B. It starts with a tutorial for new users.
C. Its main screen has a security rating for your system.
D. It uses heuristic scanning.
16. Which of the following is a useful feature in Avast! antivirus not found in most other antivirus solutions?
A. It does a pre-installation scan.
B. It starts with a tutorial for new users.
C. Its main screen has a security rating for your system.
D. It uses heuristic scanning.
Exercises
Note: These exercises will have you working with different antivirus products. It is critical that you uninstall one product before installing and using another.
Exercise 9.1: Using McAfee Antivirus
1. Download the trial edition of McAfee Antivirus.
2. Scan your machine.
3. Note what security rating the main McAfee screen gives your PC and the reasons why.
4. Note what the virus detector finds.
5. Experiment with settings and options, particularly scheduling.
Exercise 9.2: Using Norton AntiVirus
Note: If you did all of the projects in Chapter 2, then this first exercise will be familiar. However, here you will be asked to compare Norton with other antivirus solutions.
1. Download the trial edition of Norton AntiVirus.
2. Pay particular attention to the pre-install scan.
3. Scan your machine.
4. Note what the virus detector finds.
5. Experiment with settings and options, particularly scheduling.
Exercise 9.3: Using Avast! Antivirus
1. Download the trial edition of Avast! antivirus.
2. Scan your machine.
3. Examine the initial tutorial. Is it adequate for a novice user?
4. Note what the virus detector finds.
5. Experiment with settings and options, particularly scheduling.
Exercise 9.4: Using PC-cillin Antivirus
1. Download the trial edition of PC-cillin antivirus.
2. Scan your machine.
3. Note any features of PC-cillin that the other virus scanners do not have.
4. Note what the virus detector finds.
5. Experiment with settings and options, particularly scheduling.
Exercise 9.5: Using Panda Antivirus
1. Download the trial edition of Panda antivirus.
2. Scan your machine.
3. Note any features of Panda that the other virus scanners do not have.
4. Note what the virus detector finds.
5. Experiment with settings and options, particularly scheduling.
Projects
Project 9.1: Comparing Antivirus Software
Compare the features of four antivirus packages, paying particular attention to:
1. Items that are unique to one solution.
2. What each scanner picks up (i.e., if they are all used to scan the same folder, do they all detect the same items?).
Project 9.2: Researching a Virus
1. Using various Web resources, find a new virus active in the last 90 days.
2. Describe how the virus propagates, what it does, and how widely it has spread (the McAfee virus map should help you with that).
3. Describe any known damage the virus has caused.
4. Describe measures being taken to combat the virus.
Project 9.3: Antivirus Policies
For this project you need to consult several antivirus policy documents (listed below). You will find some items in common, and some that exist in only some of them. Identify those items in common to all of these sources (thus indicating all the sources find them to be important) and explain why those are so critical.
![]() SANS Institute lab antivirus policies: https://www.sans.org/security-resources/policies/Anti-virus_Guidelines.pdf
SANS Institute lab antivirus policies: https://www.sans.org/security-resources/policies/Anti-virus_Guidelines.pdf
![]() Dr. David Stang’s antivirus policy: vx.netlux.org/lib/static/vdat/virpolic.htm
Dr. David Stang’s antivirus policy: vx.netlux.org/lib/static/vdat/virpolic.htm
![]() East Carolina University’s antivirus policy: http://www.ecu.edu/PRR/08/05/01/
East Carolina University’s antivirus policy: http://www.ecu.edu/PRR/08/05/01/