The primary risk for any privileged access is the activity performed via that access. As a security professional you must ask the following questions: Was the activity appropriate? Did the user make a mistake? Or did a threat actor perform something potentially malicious using elevated credentials? Unless you are sitting over someone’s shoulder and have the expertise to monitor the activity, there are plenty of gaps in the traditional security model to review this activity and verify every session, every command, and all the information downloaded or displayed on the screen. Reviewing all activity is a daunting task, but luckily, technology and automation exist to help address this challenge. Based on these use cases, let us explore the requirements for any privileged access monitoring performed within an environment.
Session Recording
An inline video capturing system that records monitor output before displaying on a screen. This technology typically also bundles OCR (optical character recognition) to scrape the screen for keywords and text in the display. This technology requires hardware on the video side of servers and is normally not viable for cloud or virtualized technologies.
An end-user agent or browser plug-in that captures the screen or session based on activity. The results are cached or streamed to a central server for review and processing. This approach requires agent technology to be deployed and does not manage out-of-band connectivity that can circumvent recording technologies.
A proxy technology that is protocol-aware to provide agentless screen recording of an active remote session. This approach supports segmentation and requires access to be routed through the proxy for a successful connection. All recordings are, therefore, recorded by the proxy, not stored on the end user’s asset, and do not require hardware modifications, except for the introduction of the proxy itself.

Session Recording Playback
Regardless of the technological approach, the goal is the same: to review privileged session activity to sensitive data and systems. While this approach alone does not stop the activity of the threat actor, it documents their activity beyond the bounds of normal operations. The recording of privileged activity can be used for forensics and, when properly configured, can help identify a threat. This will be discussed further in the “Session Auditing” section later in this chapter.
In addition, if the session recording system is advanced enough, automation can enable more proactive responses to inappropriate behavior. For example, advanced rules can be configured to trigger onscreen output to perform mitigation activities, such as sending an alert, locking or terminating the session itself, or disabling the associated user account. While this functionally requires a mature and advanced setup, it steps up the game should a threat actor attempt to maintain a persistent presence by running specific commands or downloading information.
Finally, when discussing regulatory compliance with auditors, session recordings meet the basic requirements of documenting the privileged activity of appropriate use and privileged user attestation reports.
Keystroke Logging
An inline physical device via USB or PS2 to capture keystrokes from a keyboard. These devices can store the information locally, or have a software or network component to upload the captured information. There is no physical solution for wireless keyboards that connect via Bluetooth or proprietary dongle.
An end-user agent that captures keystrokes. This is a common approach, but needs to be whitelisted and not confused with malware that performs keystroke logging as well. This approach works with all wired and wireless keyboard technologies since the agent captures all input device data.
Proxy technology that captures the difference between screen rendering and user input. This approach requires no physical hardware (outside of the proxy) and no local agent to capture explicit user keystrokes. Proxy technologies to capture keystrokes work with the virtual form of keyboard or textual input technology.
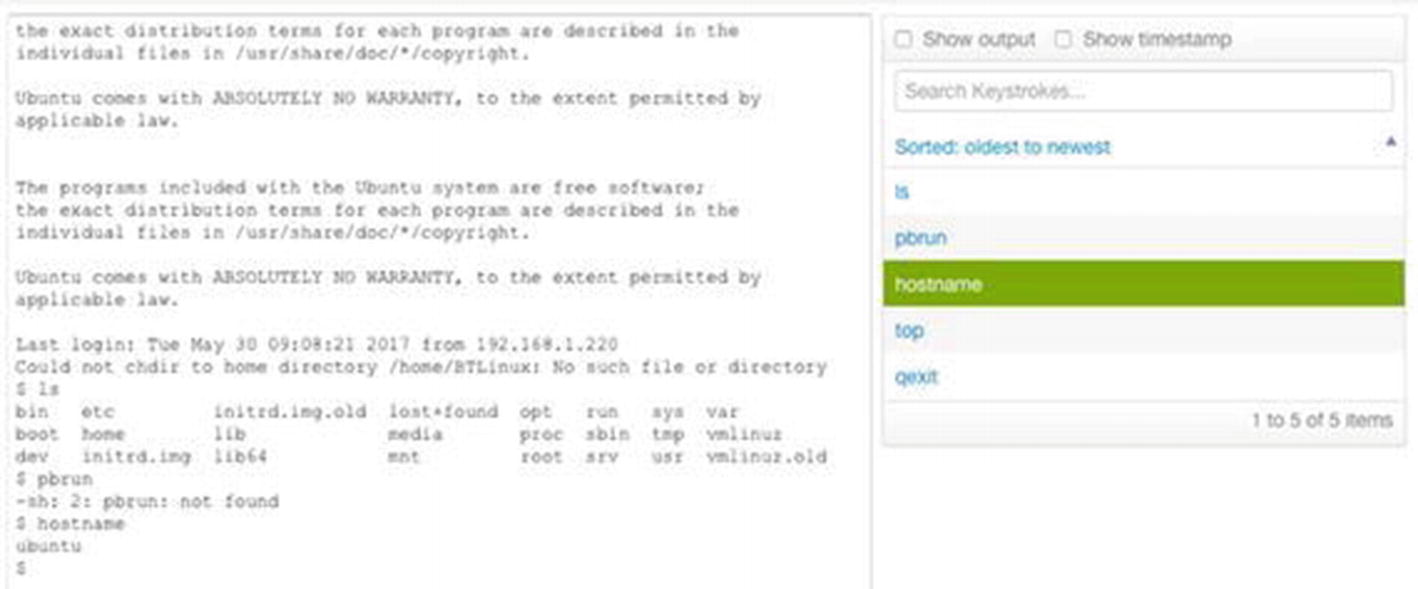
Command-Line Filtering and Command Searching
Application Monitoring
Applications represent a unique challenge for privilege monitoring. Every application is essentially different, even if they share best practices for common menus, buttons, or depend on runtime engines from Oracle Java to Adobe Flash, and even native-compiled code. Session recording can capture mouse movement and screen recording, but reviewing the sessions for a specific button, client utility, or dialog screen banner is labor-intensive without additional technology. There is nothing in native session recording to capture application activity outside of a visual change since the primary input mechanisms are mouse clicks or using a touchscreen. Also, keystroke logging cannot capture mouse clicks outside of x axis and y axis coordinates unless it is aware of the application itself. Due to these problems, the only solutions that work for application monitoring are to have local code present in the form of an agent, dissolvable (temporary) agent, or advanced OCR (optical character recognition) technology. OCR, however, requires post-processing of the recording, may have trouble with fonts, cannot see file paths, and is not viable for real-time alerting. Therefore, the only viable method for application monitoring related to PAM is to use some form of agent technology.
Application monitoring agents, regardless of the delivery mechanism (persistent or dissolvable), monitor for API calls, mouse clicks, and screen changes based on user interaction. The application’s title bar, button names, and menus are all exposed via Windows APIs, for example. When a user interacts, they can be captured and documented on a timeline with the session recording and keystrokes as well. This provides a complete audit trail for forensics or regulatory compliance attestations, and potential malicious activity. Think about our Where’s Waldo example for threat hunting.
For a threat actor, the final vector for data manipulation is under security management. Tools that allow you to manipulate data and continue malicious activity graphically are monitored—even if they use the graphic user interface only for their attack. Buttons and dialogues are typically clearly labeled for data deletion, download, or querying for all programs. Therefore, similar automation techniques to keystroke logging can be used to look for keywords that contain indications of malicious activity. The results can alert security teams, or terminate the session using the same proxy or agent technologies.
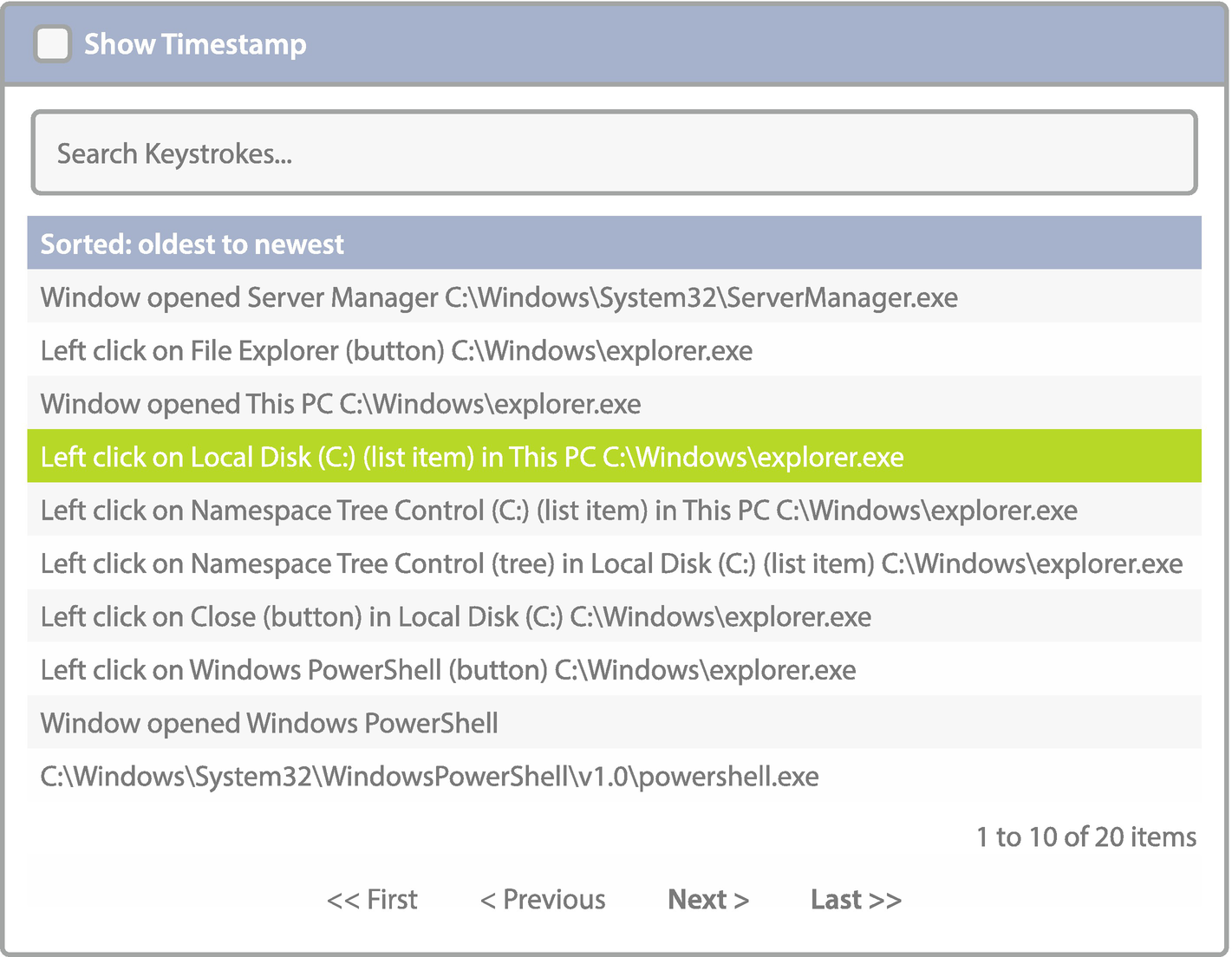
Application Monitoring Using Agent Technology
Session Auditing
Privileged session auditing is a critical reporting requirement for organizations looking to meet regulatory compliance initiatives (discussed in Chapter 20) and provides evidence in support of initiatives, like threat hunting. While most PAM solutions can perform session recording, it is the automated auditing capabilities that allow security teams to remain vigilant and zero in on sessions that have potentially malicious activity, vs. scouring through endless hours of real-time recorded sessions. While just recording the session meets the basics of regulatory compliance requirements stated earlier, truly implementing it in an efficient manner makes all the difference for sustainability.
The account used to launch the session
The source IP address or hostname of the originating session
Timestamps for the duration of the session, from beginning to end
Capturing of all keystrokes entered by the user, with corresponding timestamps
Capturing of screen output seen by the user, even across multiple monitors, including timestamps
Centralization of all captured session auditing data for playback, searching, and auditing with applicable security to protect against future malicious intent
The ability to timestamp views of the session by an auditor and add notes to each reviewed session for future consideration
Has an automated rule engine to interact with the session based on keywords, session attributes, or other activity to isolate malicious activity in real time and alert on any session recordings that need additional auditing
Provide strong encryption for all recorded sessions to ensure there cannot be any tampering of the contents
Archive capabilities to purge or move outdated sessions for backup, forensics, or legal preservation
The ability to export graphical interface results to an OCR (optical character recognition) system for additional processing
The ability to export all data in the form of events to analytics, artificial intelligence, and machine learning solutions for additional behavioral profiling
All of this information provides a complete audit of user activity and allows for a determination for any mistakes or potential wrongdoing.
These are not “nice to have” capabilities for any privileged monitoring solution, they are firm requirements to implement a low-friction solution and minimize the observer effect when recording a user’s sessions.
Remote Access
Remote access is one of the hardest requirements to fulfill when performing privilege monitoring. By definition, privileged remote access eliminates the need for privileged users (vendors, contractors, or even remote employees) to remember or share credentials for the systems they need to access. Credentials can be stored locally in the remote access solution, integrated into a password manager, or manually entered by an end user. The latter defeats the entire purpose of a PAM-based remote access solution and negates the reason it is even included as a requirement.
To integrate privileged remote access with a credential storage solution, the password component must be able to seamlessly and securely inject valid credentials into any session without the end user’s knowledge. In other words, it just works and provides a frictionless experience; the session just starts based on any role- or attribute-based security policy you have deployed.
Also, session auditing represents an additional challenge. Remote access is generally point-to-point. To perform session auditing, a flexible proxy or gateway is needed to route all remote session traffic to perform session recordings. This also must be a seamless user experience, or users will endeavor to circumvent the solution anyway they can.
Integrated or native password management capabilities
Seamless capture of session recordings via a flexible network architecture needed for session auditing
Support of multiple protocols from RDP, SSH, VNC, and HTTP(S)
Secure capabilities to allow communications within a network as well as external connectivity based on personas and roles
Flexible deployment model, on-premise or in the cloud, to support software as a service (SaaS), infrastructure as a service (IaaS), and platform as a service (PaaS) initiatives
Remote access connectivity based on authorized users from common operating systems to mobile devices
Support a complete workflow for ticketing solutions to multi-factor authentication to approve proper access
Remote access and privilege monitoring represent some unique challenges, but with a fully integrated PAM solution, these use cases can be implemented to make the entire user experience simple and rewarding.
