Not so long ago, it was much easier to protect your data. Perimeter defenses were in place and meant something, and there were limited pathways to access your organization’s data. Data came in from IT-approved, enterprise-controlled devices and applications. It lived on your servers and in storage arrays. It was protected by walling off the outsiders and trusting your insiders. But IT environments have changed in a big way. Now, data is increasingly collected from applications, users, devices, cloud services, and connected hardware, with dwindling amounts of it under enterprise control. New forms of doing business demand easy access from the outside world. With the emergence of the cloud, your data, users, and applications may not even be on the inside anymore. And “insiders” with access to your data increasingly include third parties who don’t work for your organization at all. The approach to managing the granularity of access to this unstructured data at the file or application layer can be done with privileged access management.
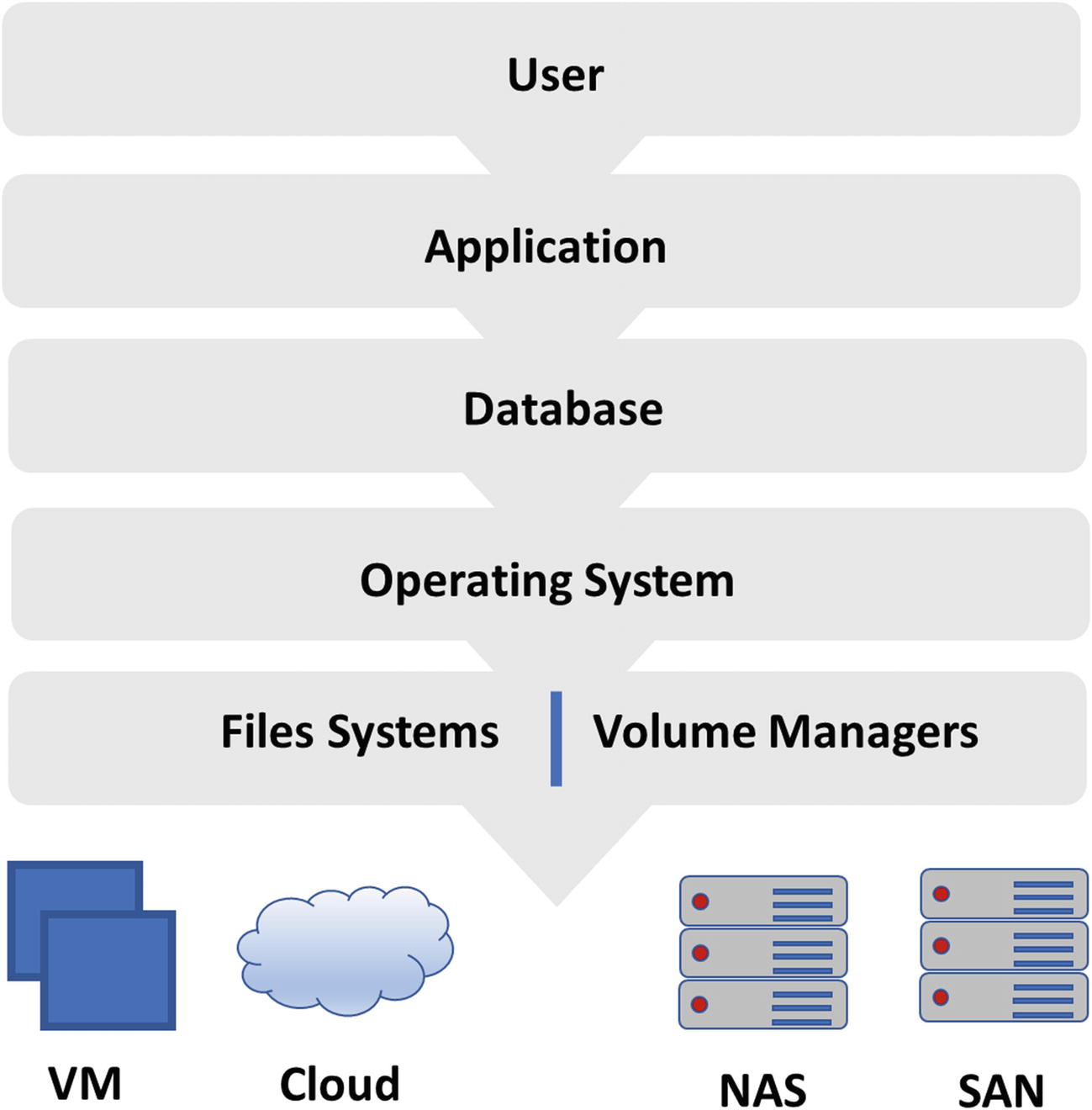
Unstructured Data—Stack Model
Encryption will protect the file’s contents, but not the file itself. A threat actor stealing hundreds of encrypted files is harmless unless they have a method to decrypt the files. Password protection in the application associated with the file (like Microsoft Word or Excel) is insufficient to guard against modern hacking tools. Therefore, it is the keys to decrypt the file (or file system) that become the primary target for a threat actor.
With this in mind, restrictions and auditing are only governed by local access control lists and role-based access in applications, databases, and operating systems. An administrator can, therefore, have access to any file or volume by merely being an administrator. Users with permissions anywhere in between a standard user and administrator may need access to an application, but limited or no access to the file system that supports it. This is the basis for client-server architecture, or even a modern web application.
Unfortunately, for traditional operating system security controls across Unix, Linux, MacOS, and Windows, root or administrator allows access up and down the stack, and there is no native way to restrict access to it. Your organization may be able to remove user privileges, but as an administrator, you can always grant them back. Once an attacker has root or administrator privileges, it is truly game over, especially when it involves domain administrative rights. There is always a way to circumvent security controls when you are an administrator. Privileged access management (PAM) can control the user’s access, but cannot necessarily control the file system and/or existing processes without taking ownership. This is especially true when the files are shared or stored in the cloud using a file storage solution like DropBox, iCloud, or OneDrive. File system and process control solutions can provide segmentation and encryption to files and directories (like DLP, DCAP, etc.), but cannot control the actual user being authenticated in the first place. Thus, if a threat actor is an administrator, there is probably a way to circumvent these technologies too and, with some effort, gain access to mechanisms protecting unstructured data files.
The solution to the problem utilizes privileged access management on the top of the stack to manage the operating system and applications and native File Integrity Monitoring (FIM) integrated with your PAM solution to strategically monitor and block threats vertically along the traditional layers of the ISO computing model. This implies managing privileges through all the layers—from user authentication to FIM policies that grant or deny access: even as root or administrator. This requires the solutions to work together so any tampering can be correlated between the layers to prevent a compromise. Unfortunately, this only applies to operating systems and file systems that you can control and not necessarily file storage solutions provided as SaaS or IaaS.
User access—from authentication to file access—is managed and monitored.
Applications are run with least privilege to mitigate elevated privilege risks, without access to the supporting data structure.
Databases and applications have passwords managed for automatic rotation and can restrict access, including any automation performed by scripts or tools.
Operating system access is restricted to standard users, commands, tasks, and scripts, and features are elevated on a need-to-use basis with specific privileges.
Individual files associated with commands and scripts are protected separately from tampering using FIM, but assigned or excluded to the same user privileges.
User access in an attack chain can be monitored and mitigated along every horizontal plane in a traditional computing model. This is far deeper than just at the top using a traditional authentication model managing passwords per user access.
Only trusted and authorized users have access to an asset and its supporting data using privilege and FIM technology.
The removal of privileges from the user to the application, and from user to the file system, can be supported in a trusted computing environment across all major operating system platforms.
Protecting unstructured data is a natural extension of privileged access management. It applies the technical controls and policies for privileged use below the operating system to the file system and below access control lists. File Integrity Monitoring (FIM) solutions that integrate with privileged access management provide this vehicle and enable a holistic approach to monitoring any layer a threat actor may use for the exfiltration of information. This includes even blocking an elevated user from accessing files and directories based on FIM policies linked to their PAM profiles.
