In this chapter, we will cover some of the most important cryptography libraries that can be used within .NET and C# applications. Choosing a cryptography library, especially one that is open source, represents a sensitive task compared to the .NET Framework itself. You need to be sure of what you are doing and know what kind of data you are using. Relying upon an open source project for a security aspect could lead to significant security incidents if there are bugs in the open source project that can be used by an attacker.
In the following sections, we will cover these libraries: NSec [1], Bouncy Castle [2], Inferno [3], and SecureBlackbox [4].
NSec
NSec [1] is one of the most modern and easy to use cryptographic libraries for .NET Core. The library is based on Libsodium [5].
Modern approach. Libsodium offers a small set of cryptographic algorithms and primitives. The nice thing about NSec and Libsodium compared to other libraries is the support of features such as X25519, Ed25519, and ChaCha-Poly1305. The performance and how the features are implemented within NSec are based on a modern .NET API which is developed based on types Span<T> and ReadOnlySpan<T>.
Extremely easy to use. It is very useful and easy to use. The elegance and reliability of NSec means it’s easy to implement. It offers support for the type data model, which is designed with respect for keys and shared secrets, based on dedicated classes instead of empty byte arrays. This helps developers avoid using a key within a wrong algorithm.
Secure. The mission of NSec is to make the cryptographic primitives as easy as possible.
Fast. NSec and Libsodium are very fast during their cryptographic processes. There is no allocation memory for the heaps. NSec is designed to avoid any kind of memory allocations or non-useful copies.
Agile. Most of the algorithms implemented in NSec are derived from a tiny set of base classes. The purpose is to provide a productive way of writing code against the algorithm interfaces instead of a specific algorithm.
In the following examples, you’ll see how NSec works and how easy it is to use. The NSec uses with success some features from C# 8.0 and they are very easy to spot and understand.

NSec output
Ed25519 Signature
NSec Installation
NSec.Cryptography NuGet package
Using dotnet CLI:
Using Visual Studio:
Using a reference in the *.csproj file:
Bouncy Castle
Bouncy Castle is one of the most important and well-known libraries. It contains an implementation in C# of cryptographic algorithms and protocols.
“Support for parsing and generate PKCS-12 files” [7].
“X.509: Support for V1 and V3 certificates (generating and parsing). Also, V2 CRLs and certificates based on the attributes” [7].
“PBE algorithms supported by PbeUtilities” [7].
“Signature algorithms supported by SignerUtilities” [7].
“Symmetric key algorithms: AES, Blowfish, Camellia, CAST5, CAST6, ChaCha, DES, DESede, GOST28147, HC-128, HC-256, IDEA, ISAAC, Noekeon, RC2, RC4, RC5-32, RC5-64, RC6, Rijndael, Salsa20, SEED, Serpent, Skipjack, TEA/XTEA, Threefish, Tnepres, Twofish, VMPC and XSalsa20” [7].
“Symmetric key modes: CBC, CFB, CTS, GOFB, OFB, OpenPGPCFB, and SIC (or CTR)” [7].
“Symmetric key paddings: ISO10126d2, ISO7816d4, PKCS-5/7, TBC, X.923, and Zero Byte” [7].
“Asymmetric key algorithms: ElGamal, DSA, ECDSA, NaccacheStern and RSA (with blinding)” [7].
“Asymmetric key paddings/encodings: ISO9796d1, OAEP, and PKCS-1” [7].
“AEAD block cipher modes: CCM, EAX, GCM and OCB” [7].
“Digests: GOST3411, Keccak, MD2, MD4, MD5, RIPEMD128, RIPEMD160, RIPEMD256, RIPEMD320, SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA3, Tiger, and Whirlpool” [7].
“XOFs: SHAKE” [7].
“Signer mechanisms: DSA, ECDSA, ECGOST3410, ECNR, GOST3410, ISO9796d2, PSS, RSA, X9.31-1998” [7].
“Key agreement: Diffie-Hellman, EC-DH, EC-MQV, J-PAKE, SRP-6a” [7].
“MACs: CBCBlockCipher, CFBBlockCipher, CMAC, GMAC, GOST28147, HMac, ISO9797 Alg. 3, Poly1305, SipHash, SkeinMac, VMPCMAC” [7].
“PBE generators: PKCS-12, and PKCS-5 - schemes 1 and 2” [7].
“OpenPGP (RFC 4880)” [7].
“Cryptographic Message Syntax (CMS, RFC 3852), including streaming API” [7].
“Online Certificate Status Protocol (OCSP, RFC 2560)” [7].
“Time Stamp Protocol (TSP, RFC 3161)” [7].
“TLS/DTLS client/server up to version 1.2, with support for the most common ciphersuites and extensions, and many less common ones. Non-blocking API available” [7].
Elliptic curve cryptography.
Bouncy Castle Examples
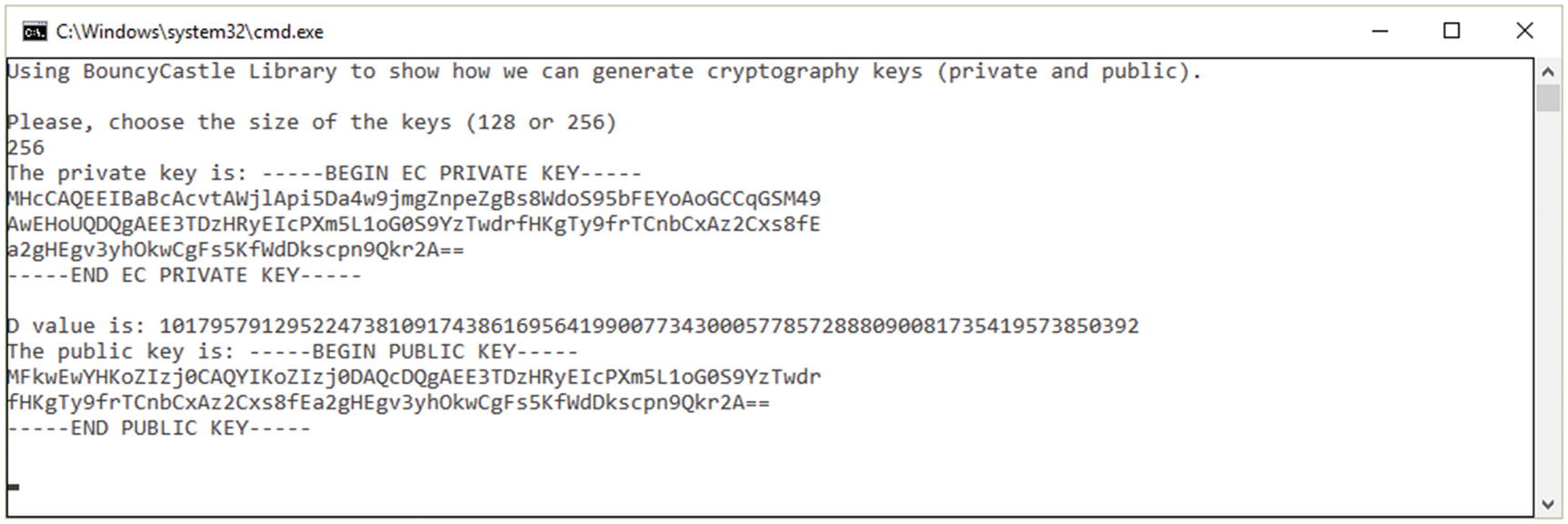
Generating cryptography keys using BouncyCastle
AES – Encryption with CBC Mode and PKCS5/7 Padding
The next three examples (see Listing 9-3, Listing 9-4 and Listing 9-5) show how to deal with key agreement and exchange algorithms.
Basic Agreement with an Agreed Value
Agreement Using PRF
Working with an Agreement Based on X9.63 KDF
Bouncy Castle Installation
Bouncy Castle NuGet package
Using dotnet CLI:
Using Visual Studio:
Using a reference in the *.csproj file:
Inferno
Inferno is another interesting cryptographic library for .NET developed using C#. It offers a unique elegance in writing the code and the performances obtained during processing the code are quite promising.
“[random]: CryptoRandom (.NET Random done right)” [9]
“[ciphers]: AES-256 only (fast, constant-time, side-channel-resistant AES-NI)” [9]
“[hi-level]: AEAD (AES-CTR-HMAC). Streaming AEAD (EtM Transforms)” [9]
“ [ciphers-misc]: AES-CTR implementation (CryptoTransform) “ [9]
“[ciphers-misc]: AEAD (AES-CBC-HMAC)” [9]
“[hash]: SHA2 hash factories (256, 384, 512). SHA-384 is recommended (default)” [9]
“[hash]: SHA1 hash factory (mostly for legacy integration)” [9]
“[mac]: HMAC2 (.NET HMAC done right)” [9]
“[mac]: HMAC-SHA1, HMAC-SHA2 factories” [9]
“[kdf]: HKDF, PBKDF2, SP800_108_Ctr. Any HMAC factory is supported” [9]
“[otp]: TOTP” [9]
Inferno Examples
Encryption, Decryption, and Authentication Functions
Working with Hash
Using HMAC
Dealing with a DSA
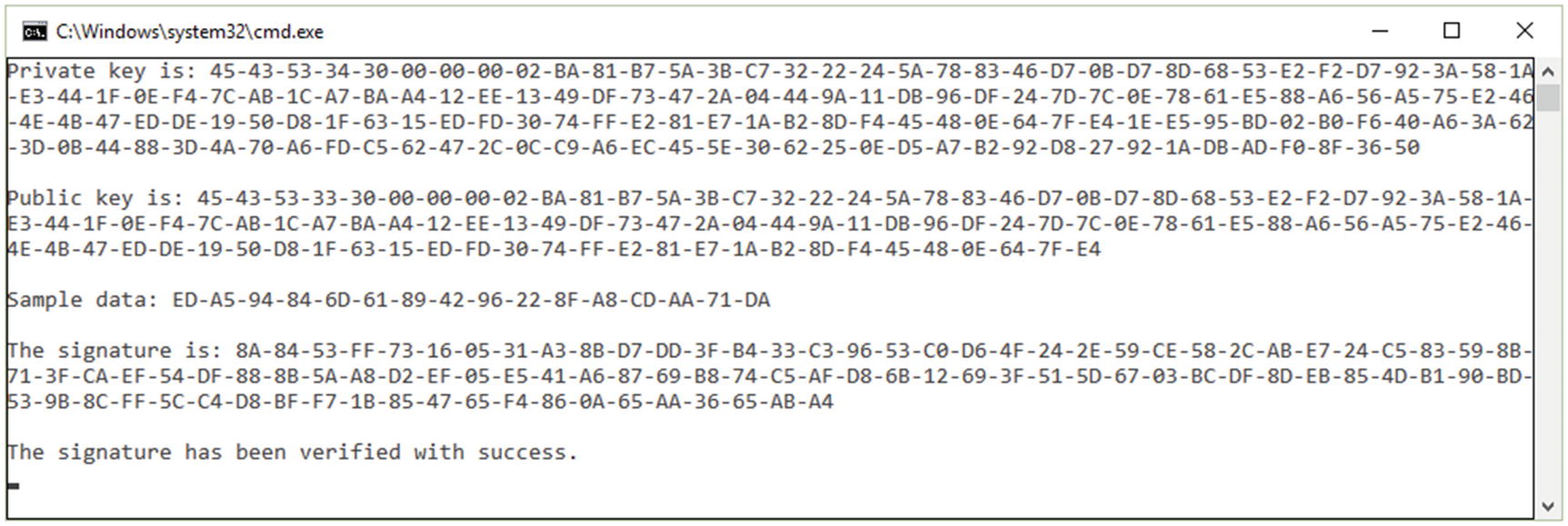
The output
Inferno Installation
Inferno NuGet package
Using dotnet CLI:
Using Visual Studio:
Using a reference in the *.csproj file:
SecureBlackbox
SecureBlackbox is one of the most comprehensive sets of tools and classes for dealing with digital security and security for a network.
Developing security solutions is done in the same way as in NSec or Inferno. The methods and functions are similar to the ones from NSec and Inferno. The differences are very few and are specific to the allocation of buffer arrays.
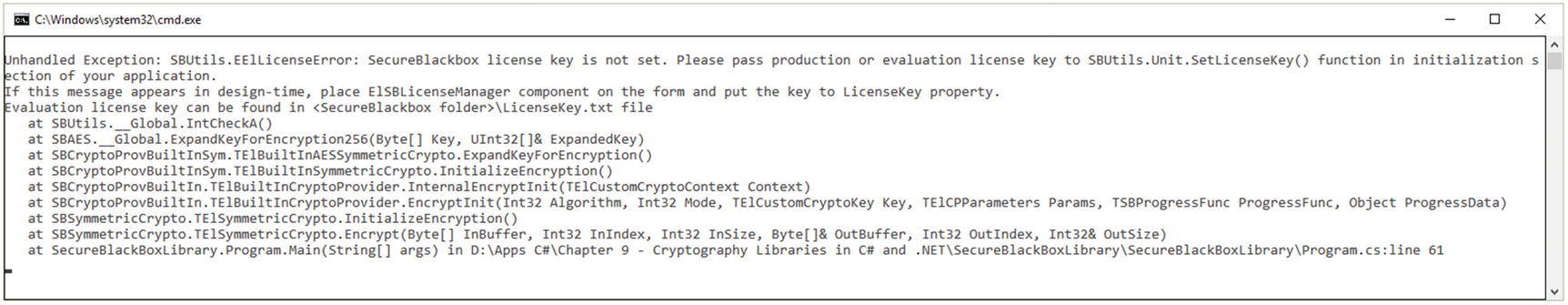
License required to run the example
For testing purposes, for the example from Listing 9-10, the owner of the library can be contacted and they will provide to you with a temporary license key.
Once the license is received (usually it is a text file, such as LicenseKey.txt), two functions can be called and the license as a key parameter to them. The two functions are void SetLicenseKey(ByteArray key) and void SetLicenseKey(string key).
If you need more key licenses at the same time, just call the function(s) several times with different file names. Each license should have a different name.
Example of Symmetric Encryption with SecureBlackbox
SecureBlackbox Installation
SecureBlackbox NuGet package
Using dotnet CLI:
Using Visual Studio:
Using a reference in the *.csproj file:
Conclusion
In this chapter, we covered the most important cryptography libraries (NSec, Bouncy Castle, Inferno, and SecureBlackbox) that can serve as guidance, extra libraries, and tools for achieving the confidentiality, integrity, and authenticity of the data within applications developed by professionals. The criteria used for selecting these libraries are their recognition by other professionals in the field and FIPS and NIST standards.
The libraries can be used in parallel with the System.Security.Cryptography namespace, offering a more exhaustive coverage of the cryptographic primitives.
Bibliography
- [1]
NSec. Available online: https://nsec.rocks/.
- [2]
Bouncy Castle. Available online: https://cryptobook.nakov.com/crypto-libraries-for-developers/c-crypto-libraries.
- [3]
Inferno. Available online: https://nugetmusthaves.com/Package/Inferno.
- [4]
SecureBlackbox. Available online: https://nugetmusthaves.com/Package/SecureBlackbox.
- [5]
Libsodium for .NET. Available online: https://nugetmusthaves.com/Package/libsodium-net.
- [6]
NSec.Cryptography. Available online: www.nuget.org/packages/NSec.Cryptography/20.2.0.
- [7]
Bouncy Castle Features. Available online: www.bouncycastle.org/csharp/index.html.
- [8]
Bouncy Castle NuGet Package. Available online: www.nuget.org/packages/BouncyCastle/.
- [9]
Inferno Features and Project. Available online: https://securitydriven.net/inferno/.
- [10]
Inferno NuGet Package. Available online: www.nuget.org/packages/Inferno/.
- [11]
SecureBlackbox NuGet Package. Available online: www.nuget.org/packages/SecureBlackbox/.
