This chapter covers two important attacks, the buffer overflow attack and the brute force attack, which are frequently employed against C++ applications and programs.
A special category of attackers will use applications/programs or devices to launch brute force or buffer overflow attacks. Their methods evaluate different combinations of words for confirmation forms. In some cases, the attackers attempt to corrupt web applications through a scanning process for sessions IDs, for example. The attacker’s goals include stealing data, corrupting destination machines with malware, and asking for a specific amount of money. Some of the attackers perform brute force attacks physically as a personal choice. Today, most brute force and buffer overflow attacks are performed by bots.
Don’t use data or information that could be found online.
Use as many characters as possible.
Use combinations of letters, numbers, and special characters (e.g. symbols).
Don’t use common patterns (e.g. qwerty).
Use different passwords for each user account.
Change the password at frequent intervals (e.g. every two months).
Use and generate long and strong passwords. If you don’t have an idea for one, use a password generator (e.g. key generation from KeyPass).
Implement multifactor authentication [1].
Use biometrics if possible [2].
Brute Force Attack
A brute-force attack represents a complex attack in which the attacker will submit many passwords or passphrases with the goal of guessing the correct one. Each password or passphrase is checked one-by-one by the attacker until the correct one is found. Also, the attacker may guess the key. The key is generally created from the password by using a function for key derivation. This process is known as an exhaustive key search.
Attacks based on rainbow tables: A rainbow table is a predefined and precomputed table. The goal is to reverse the process of the cryptographic hash capacities.
Attacks based on reversing brute-force attacks: The attack is based on using a general password or a specific set of passwords against multiple usernames.
Credential attacks: The attack uses sets of passwords-usernames against a variety of websites.
Hybrid brute-force attacks: The attack is used to figure out what password variety is used to succeed. After, it proceeds with a general process for dealing with checking different varieties.
Brute-force attack on a Caesar cipher: The example (see Figure 21-1 and Listing 21-1) is based on a Caesar cipher. The example is chosen as the first case of showing a brute-force attack due to its simplicity.
String generation for a brute-force attack: The example (see Figure 21-2 and Listing 21-2) shows how basic string generation can be done with the goal of creating complex lists and dictionaries that can be used during brute-force attacks.
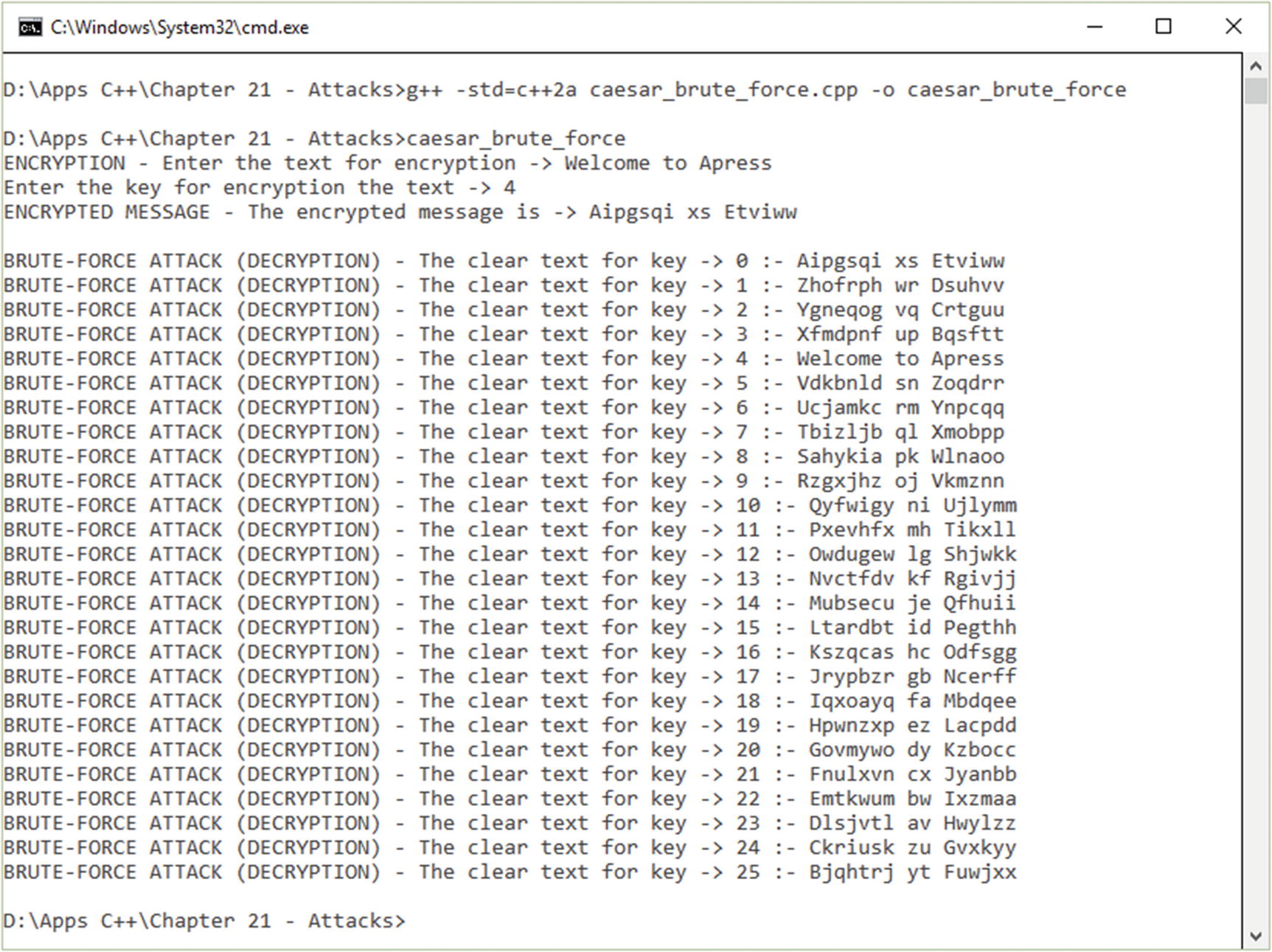
Running the brute-force attack
Brute Force Attack on a Caesar Cipher

Basic string generation for a brute-force attack (different states of generating strings)
Basic String Generation Source Code
Buffer Overflow Attack
A buffer represents a temporary area that is used for storing data. At the moment when more data is placed by the programs or system processes, an extra data overflow will occur.
In a buffer-overflow attack , the extra data being stored can store specific instructions to take actions designed by hackers or malicious users. As an example, the data could trigger an event (function or process) to destroy files or reveal private data about users.
The attacker uses a buffer overflow to get an advantage from a program that is being executed and is waiting for user interaction. There are two types of buffer overflows: stack-based and heap-based. In a heap-based overflow, it is very difficult to launch and execute attacks based on flooding the memory space reserved for the program and its execution. In a stack-based overflow, the exploitation of the applications and programs is done on the memory stack, which is the memory space used to store the input data from the user.
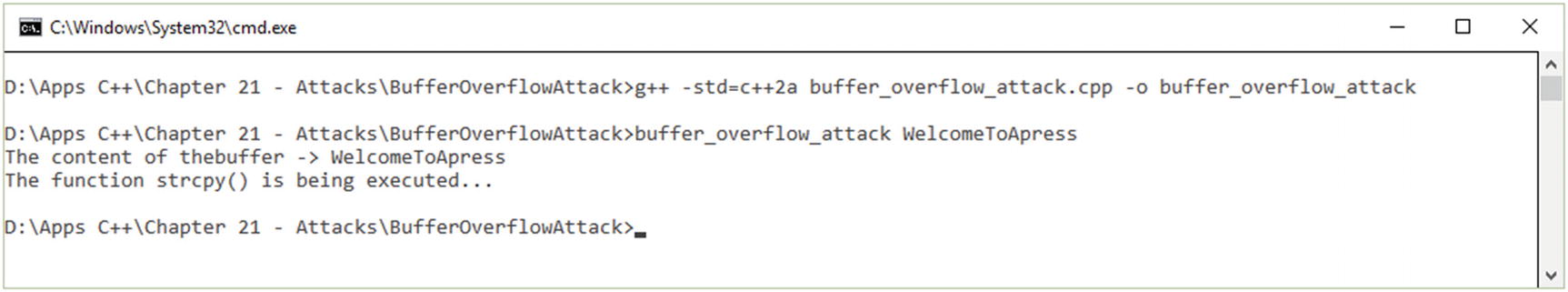
Buffer overflow execution
Implementation of the Buffer Overflow Example
Conclusion
Understanding the brute-force and buffer overflow attacks
Understanding the main concepts that form the basics of designing such attacks
Understanding the limitations between stack-based and heap-based buffer overflows
References
- [1]
M. I. Mihailescu and S. Loredana Nita, “Three-Factor Authentication Scheme Based on Searchable Encryption and Biometric Fingerprint” in 2020 13th International Conference on Communications (COMM). Bucharest, Romania, 2020, pp. 139-144, doi: 10.1109/COMM48946.2020.9141956.
- [2]
M. I. Mihailescu, S. L. Nita, and V. C. Pau. “Applied Cryptography in Designing e-Learning Platforms” in 16th International Scientific Conference “eLearning and Software for Education.” Bucharest, Apr. 2020, vol. 2, pp. 179–189, doi: 10.12753/2066-026X-20-108.
