Today, therefore, a commander must ensure that his troops always know what they are being asked to do, and how that fits into the larger plan. I have always insisted that before a battle the essentials of the plan are known right through the chain of command, and finally down to the rank and file. The troops must know how a commander is going to fight the battle and what they are to play in it; this must be explained to them by word of mouth, for that counts far more than the written word.
And then when the battle has been won, and the troops see that the battle has gone as the commander said it would be, their confidence in the high command will be very great.
This confidence is beyond price.
Military commentator and correspondent from Thoughts on War, 19441

Captain Liddell Hart
Introduction
Captain Liddell Hart’s words have never been truer than when looking to create strict access restrictions for a business’ digital solutions. Every time a login screen is made available to the wider audience, it is like sending troops into war, with the Internet representing the battle fields.
Consequently, it is essential that everyone knows the importance of strict access control and how secure access credential management practices assist a digital business to fight their battles.
Secure access management is a team effort.
Background
The process of granting or denying specific requests to:
- 1)
obtain and use information and related information processing services; and
- 2)
enter specific physical facilities (e.g., federal buildings, military establishments, border crossing entrances).
NIST SP800-12 Rev. 1 (An Introduction to Information Security)3
The process of permitting or restricting access to applications at a granular level, such as per-user, per-group, and per-resources.
NIST SP800-113 (Guide to SSL VPNs)4
The process of granting access to information technology (IT) system resources only to authorized users, programs, processes, or other systems.
NIST SP800-47 (Security Guide for Interconnecting Information Technology Systems)5
How access to the cryptographic devices or applications are to be authorized, controlled, and validated to request, generate, handle, distribute, store, use and/or destroy keying material. Any use of authenticators, such as passwords, personal identification numbers (PINs) and hardware tokens, should be included. For example, in PKI cryptographic applications, role and identity-based authentication and authorization, and the use of any tokens should be described.
NIST SP 800-57, Part 2 (Recommendation for Key Management)6
A way of limiting access to a system or to physical or virtual resources. In computing, access control is a process by which users are granted access and certain privileges to systems, resources, or information.
In access control systems, users must present credentials before they can be granted access. In physical systems, these credentials may come in many forms, but credentials that can't be transferred provide the most security.
All these definitions state the requirement for limiting and managing access to systems, applications, buildings, rooms, and so on to only authorized personnel.
However, as simplistic as this may appear, secure access management continues to be highly problematic for today’s digital business and, as a result, is increasingly being leveraged by criminals as a successful attack vector.
Why is this? Simply put, it is because it relies on a securely configured and managed backend operation (e.g., Active Directory and User Access Management) and consumer/user secure password management.
Let’s face it; secure access management can prove exceedingly difficult to manage and may become an inconvenience for the consumer/user. This then impacts their experience, which can then affect the convenience and usability of the digital interfaces – which, by addressing this often, makes them increasingly vulnerable and favored as a potential attack vector.
The greater the number of digital applications that rely on sensitive information, the greater the appeal for today’s criminals. Additionally, the greater the number of digital interfaces and web/cloud-based applications, the increasingly difficult it is for the consumer/user to commit the access credentials to memory.
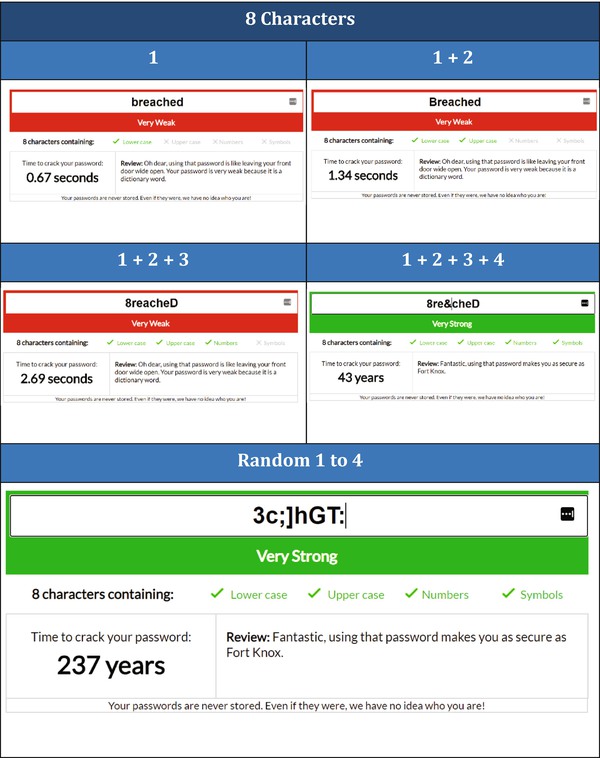
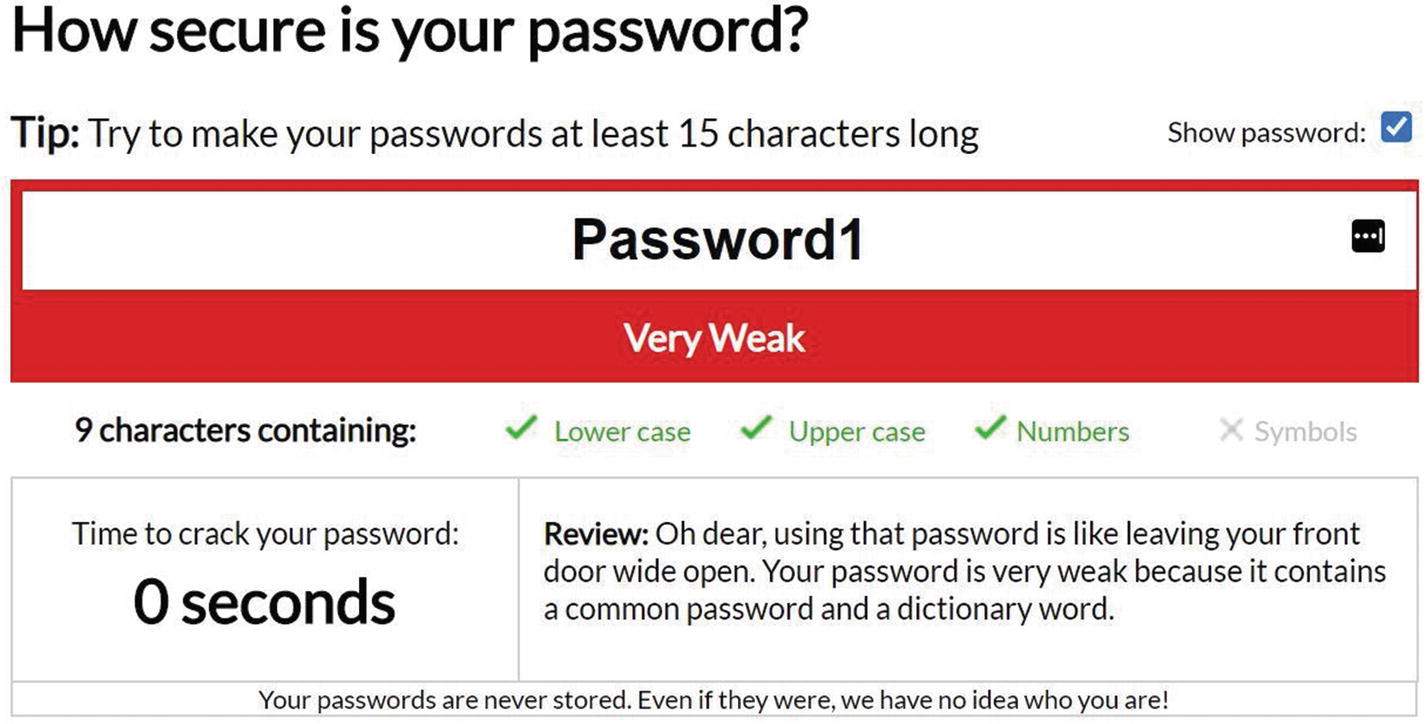
It has become increasingly difficult for consumers and end users to commit their strong access credentials to memory (e.g., passwords, PINs, answers to security questions, etc.), and, as a result, they are either reusing the same “strong password” across multiple logins, are creating sequential passwords (e.g., P@ssword1, P@ssword2, Password3, etc.), or are using easy-to-remember passwords.
Length
The minimum password length that should be required depends to a large extent on the threat model being addressed. Online attacks where the attacker attempts to log in by guessing the password can be mitigated by limiting the rate of login attempts permitted.
For example:
Payment Card Industry Data Security Standards (PCI DSS)Minimum of seven characters
Complexity
Composition rules are commonly used to increase the difficulty of guessing user-chosen passwords. Research has shown, however, that users respond in very predictable ways to the requirements imposed by composition rules.
Consequently, the difficulties faced by the consumers/end users in maintaining secure password management make these an extremely rewarding attack vector for today’s criminals.
A mix of characters:- 1.
Lowercase
- 2.
Uppercase
- 3.
Numbers
- 4.
Symbols (special characters)
Password Comparisons
|
Defending from the Enemy at Your Gates
Camp Bastion location

Enemy at the gates?
Your organization still needs to remain operational, requiring assets to move in and out of the badlands, while preventing the enemy from gaining unauthorized access to your environment and valuable assets.
Consequently, ensuring strict access restrictions are enabled and maintained becomes an essential part of an effective Protective Security strategy, which requires robust Backend and Frontend Operations.
Securing Backend Operations
The effective utilization of access control systems to prevent unauthorized access to business assets while allowing the managed access of approved individuals, who have a legitimate business need to access these business assets
This requires an effective “gate keeper” process (Backend Operations) to manage and monitor the access control system while ensuring that the “keys” (passwords, proximity cards, etc.) and additional authentication requirements (e.g., multifactor authentication (MFA)) are only established for authorized individuals (Frontend Operations).
Effective Backend Operations need to be formalized through documented policies and procedures, with all responsible personnel knowing how these policies apply to their role, in support of these Backend Operations.
The objective of the Backend Operations is to strictly restrict access to sensitive business assets, to monitor its effectiveness, and to respond to any ABNORMAL activities.
Account Management
Account types are identified and selected based upon legitimate support of business missions/functions, and account managers are assigned to ensure conditions for group and role membership are established, including specifics for authorized users, and ensure all access requires formal approval.
The account managers are responsible for the creation, enablement, modification, disablement, and removal of the live accounts and for actively monitoring the use of the accounts (being proactive rather than reactive).
Department managers will work with the account managers to ensure that accounts are disabled when no longer needed (e.g., termination/transfer), and access is granted based on strict need to know/access criteria.
Only access to these assets will be enabled using a valid authorization (e.g., unique ID, assigned password/PIN/biometrics, proximity access card, etc.) and for the intended use, based upon defined business missions/functions.
- Avoid the unnecessary use of privileged accounts for duties that can be achieved through standard access. Access should be based upon the principle of “least privilege.”12
If it is convenient for the employer, it can prove convenient to the opportunist attacker.
Logical and physical access should strictly enforce access restrictions based upon approved authorizations.
- Unsuccessful access attempts/logins
- End user difficulties or something more sinister, for example:
An attempted brute-force13 attack
- System use/misuse
Using a fire extinguisher to prop open a physical access control barrier
- Logins outside a user’s normal times or from an unexpected location.
Are the actions deemed acceptable or expected?
Are the actions unusual for that end user’s role?
- Remote access
- Is this usual for this end user?
Location
Time
Duration
- Wireless access
Is this an authorized device accessing via wireless?
- Mobile devices
Is this an authorized mobile device?
- Use of external information systems
Are the activities what you would expect of this end user?
All end users should receive an appropriate level of training (appropriate to their roles) to ensure that they understand the importance they play (as key custodians) in safeguarding their access, what is expected of them, and how they should report any suspicious activities or potential loss/compromise of their access credentials (keys).
Whether this is an automated logical access control system (e.g., Active Directory) or physical electronic automated access control system (EAACS), it is essential that the logs are subjected to periodic sampling reviews to help in the proactive identification of potential ABNORMAL activities, compromised access credentials, or misuse of end user privileges.
How easily and quickly could you identify unusual physical access activity or malicious attempts to circumvent the physical access controls?
Do you proactively monitor the access logs for both your physical and logical access control systems?
Are you solely reliant on the logical and access control systems to enforce access restrictions?
Do you appreciate the value that the access control (physical and logical) system logs provide to your organization in helping to identify the ABNORMAL?
- How frequently do you carry out audits of your access control (physical and logical) system logs?
Periodic sampling?
- After the event/incident audit trails?
Who might have done what and when?
Frontend Operations
Working in harmony with the Backend Operations, any individual who is deemed to be approved for authorized access owns a shared responsibility to ensure that the “keys to the gate” remain protected and that they respect the fact that they are a target for criminals.
Access credential management
End user account management
End user device management
End user acceptable use
Eavesdropping management

Frontend Operations
Today’s criminals have recognized that most organizations have trust in their employees and as a result may pay less attention to monitoring their “trusted assets.” Consequently, these “trusted assets” are regarded as opportunist attack vectors that the criminals can use to evade or undermine a business’ defensive efforts.
Enticing an employee to click a malicious link or download some harmful software
- Providing unauthorized access to sensitive data through careless habits, for example:
- Having a sensitive conversation in a public place
Overhearing
- Accessing sensitive data on a mobile device in a public place
Overseeing
Being careless with or struggling to maintain their secure and robust keys, which allow them authorized access to the valued business assets
Accessing sensitive areas via insecure network environments
Being unaware of the dangers of publishing far too much personal or sensitive data on social media websites, which (much like pieces of a jigsaw puzzle) are collected up and pieced together by the criminals
- Being overtrusting and helpful of people, resulting in them bypassing the access control measures to allow unauthorized access
- Let’s face it; it is not in most people’s nature to challenge others or to be untrusting of others.

DNV-GL 3 pillars
It is no longer appropriate just to expect the Frontend Operations to run efficiently and effectively without some investment of time and resources to identify the specific risks to the Frontend and to provide proportionate mitigation controls to reduce these risks to within acceptable tolerances and to act as a complement to the Backend Operations.

Privacy protection screens
- Password must meet strong criteria:
- Lengthy string
15 characters or more
- Must include a combination of
Uppercase characters
Lowercase characters
Numbers
Symbols (special characters)
- Must be changed frequently:
Every 30 calendar days (20 working days)
- Must not be a previously used password.
Not the same as the one used in the past four passwords.
Passwords must not be written down.
Passwords must not be commonly cracked passwords (as depicted in Figure 13-917).

Commonly cracked passwords
Consequently, while the end user is struggling to remember and manage this and all the other access credentials (typically more than 40), they end up doing the following:
Creating memorable corresponding strings
Reusing the same “strong” passwords across multiple logins
Creating convenient passwords that are easy to compromise
As a business, you need to allow the Frontend Operations to interact with the “badlands,” providing the opportunity to use these interfaces as a “mule” to help deliver malicious payloads or to act as a conduit to gain unauthorized access to the inner sanctums.
Adjusting the access credential requirements (as per the NIST guidance18) or providing the Frontend Operations with supporting technical solutions (e.g., password managers19)
Providing additional protective measures
Providing suitable levels of training to help them to be a more effective contribution to Frontend Operations
Two/Multifactor/Strong Customer Authentication
- 1.
Something you know (e.g., password, PIN, etc.)
- 2.
Something you have (e.g., token, smart card, etc.)
- 3.
Something you are (e.g., fingerprint, retinal scan, etc.)
By employing two or more of these requirements to meet the two-factor authentication (2FA),20 multifactor authentication (MFA),21 or strong customer authentication (SCA),22 you are providing an additional barrier to the opportunist criminals. Rather than just needing to compromise the passwords, they need to compromise the other authentication elements.
A compromised username and password, via a phishing email, will not allow unauthorized access to the accounts.
Note.
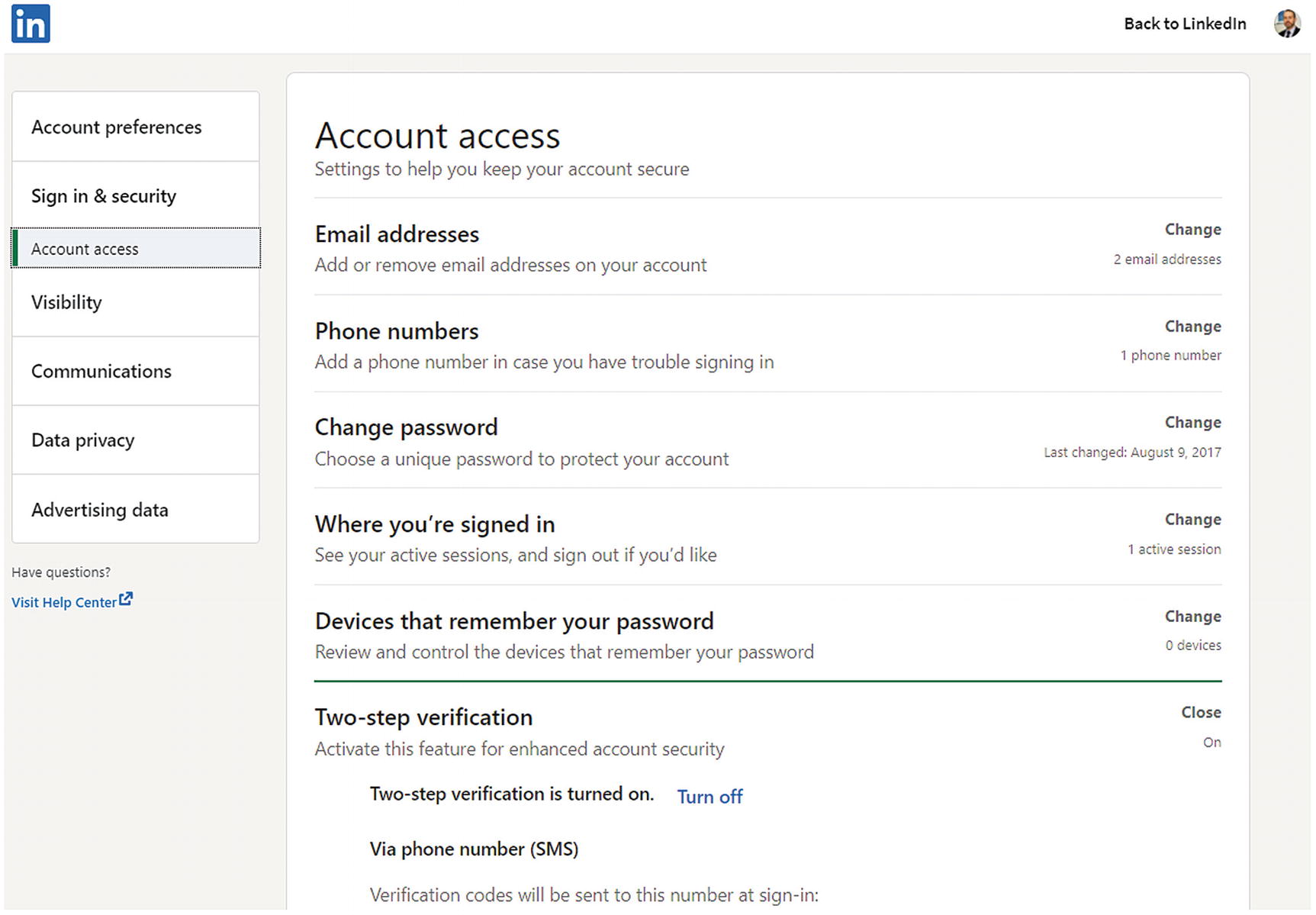
LinkedIn two-step verification setting
If it is easy and convenient for the user, it is likely to be easy and convenient for the opportunist attacker.
Military Comparison
RAF Brize Norton
RAF Marham
RAF Leeming
RAF Oakhanger
RAF Aldergrove, Northern Ireland
RAF Linton On Ouse
RAFO Thumrait, Oman
Whether this was controlling the access at the main gate of the establishment or an internal access gate or an aircraft apron,25 the principles were the same. Ensure that the individual could be identified (RAF Form 1250/MOD 90 identity card) and was authorized to access the environment (e.g., access control list, “PIT” tag exchange, etc.).
Sir, please do not confuse your rank, with my authority!
I would have been an extraordinarily rich man.
Consequently, I have endless tales providing the value of effective access restrictions, ranging from some of the incidents that occurred in Camp Bastion (potential suicide bomber, local national caught in the perimeter fence line, etc.), as mentioned in my book about Payment Card Security (PCI DSS: An Integrated Data Security Standard Guide26).
However, rather than focus on retelling the same accounts, I will focus on my first role as a Counter Intelligence operative, where I not only had oversight responsibilities for the main access/egress but also had responsibility for maintaining the internal strict access restrictions.
This was enabled using various security graded buildings, rooms, and containers. Where there was a need to retain hardcopy media, containing sensitive data assets, these needed to be retained securely but made accessible to those who had a legitimate need to access the data.

Mark 4 MCL

MCL use
As the custodian for this estate of MCL, I had the responsibility for carrying out servicing and maintenance of the locks and ensuring that the combinations were periodically changed and an effective recovery process (in case of authorized users forgetting the combination) was established.
Now, much like some of your growing number of applications and systems, to which you need to commit to memory a unique access code or password, some of these containers may only have needed to have been accessed on exceedingly rare occasions.
To access the contents of these secure cabinets, authorized users needed to enter a unique combination (## – ## – ## and opening digits ##, e.g., 21 – 32 – 43 – 75). However, you didn’t want to make these combinations too easy to guess, but they needed to be committed to memory.
BATCO grid
MCL grid
These security containers were only to be used for the storage of sensitive data, and it was prohibited for using the containers for another purpose (segregation of use), that is, secure storage of the Squadron Team Bar funds.
Access to these security containers was strictly restricted, based upon an access control list, provided by the unit security officer (USyO)/branch security officer (BSyO). Other than the scheduled combination changes, the combinations would also be immediately changed when someone had their access revoked (e.g., change of role, termination, etc.) or if compromise was suspected.
Using the same principle, you can make it easier to create and remember secure authentication data, without having to write the passwords down.
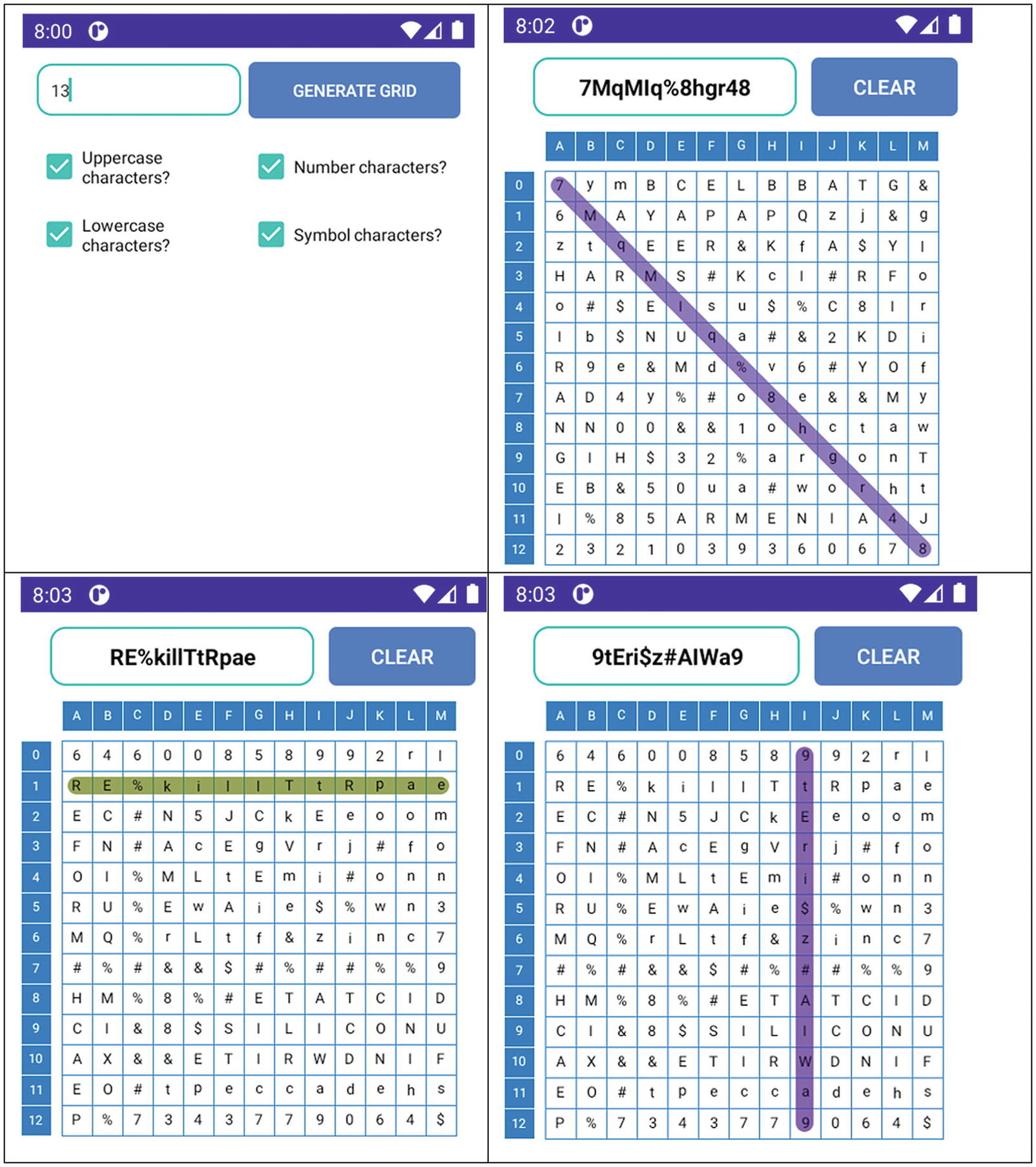
Grid-lock application

MCL maintenance
I have learned many lessons from the management of the MCL property estate, which can be seen to be directly applicable for the enhancement of strict access restriction requirements, used to help safeguard valued business assets.
Building BRIDGES
To help demonstrate the value of strict access restrictions, I will now convey this using the BRIDGES acronym for a specific business area of operation.
Business Context
ABC Company has a sales team which is deemed an essential component of their profitability. A primary role of the sales team, as you can well imagine, involves the extensive interaction with customers and their personal details.
Consequently, the organization wants to ensure that the sales team remains safe, secure, and trustworthy, which requires the assurance that this part of the business has a reduced risk for the compromise of the customers’ personal data.
Risk and Resilience
The sales team has proven particularly good at customer relations, but their security culture had not, previously, been regarded as a risk. However, following a review of the sales operations, there were several issues observed regarding their Frontend Operations. This, in turn, could significantly undermine the efforts of the Backend Operations.
For convenience, they would share access credentials into the network-connected business IT systems.
Often, the business IT systems would be left “unlocked” while unsupervised but in the presence of a customer (stranger).
- They would frequently leave customers alone, for periods of time, with uncontrolled access to the payment card reader devices and business IT systems.

Hardware keylogger
Identify and Isolate
The business needs to ensure that all the sales teams receive security awareness training regarding the requirements for restricting access to the payment card devices and business IT systems and the risks that they are presenting by not strictly restricting the access to authorized personnel.

Under-desk IT workstation rack
Detect Anomalies
Having established the strict access restriction controls, it would then be a requirement for the Backend Operations and the sales managers to carry out monitoring for any ABNORMAL activities or contraventions to these mitigation controls.
Govern Processes
Established roles and responsibilities should be developed, which include the strict access restriction requirements. These should be periodically communicated to the sales team members through security awareness training, policies, and procedures.
Where a member of the sales team fails to adhere to the corporate rules, this should be investigated and the offending individual’s mens rea33 or understanding of the rules investigated.
Where there was no evidence of malicious, deliberate, or criminal intent, the individual should receive refresher training. However, disciplinary action should always be a consideration where evidence is discovered.
Evaluate Security Controls
Independent periodic reviews should be established to ensure that all these mitigation access restriction controls remain effective, ensuring that the perceived risks to the sales team operations remain within the business’ risk appetite levels.
Survive to Operate
Many successful business leaders appreciate the value of accepting when times are good but preparing for when bad things happen, and business may be impacted (e.g., COVID-19 pandemic).
Forward-thinking leaders will accept this and will embrace the need to plan contingencies for when such events occur. This is no different with the restriction of access; things will not always go smoothly with the Backend and Frontend Operations, and these gear cogs will get out of sync or become misaligned.
Could unauthorized access lead to further account compromises?
Could a compromised account allow an attacker to move laterally across the network?
Could an attacker use a compromised account to provide them with further credibility to launch further attacks that cause greater damage?
What contingency plans do you have in place to limit this damage?
How quickly could you identify and respond to a compromised end user account or an unauthorized escalation of user privileges?
Reality Bites
There are many accounts spanning throughout historic events that have clearly demonstrated how poor access control practices have undermined the strongest of defenses.
Take, for instance, the fall of the city of Constantinople,34 which had been described as an impenetrable fortress. Despite a formidable array of physical defensive layers, after many failed attempted sieges and hundreds of years, the city was eventually compromised, as the attackers exploited the weakest points – the access/egress gates!
One of the most recent and notable incidents, relating to a compromise of the Frontend Operations, can be seen in the cyber-attack on The North Face.35 The organization’s web-based operations36 had been compromised after the attacker used compromised customer credentials from other data breaches against The North Face customer logins (aka credential stuffing37).
Where customers had reused the same access credentials (Frontend Operations) across multiple accounts, the attackers had been able to use these to compromise their North Face logins. Therefore, The North Face’s Backend Operations had to instigate their “Survive to Operate” activities and reset all their customer logins.38
I have a personal account of an incident which could have been avoided, had the business have listened to my concerns. I had only recently started with an organization that had just moved to Microsoft’s cloud-based Office 365.
I was surprised to discover that they were allowing end user access to their accounts from any device, anywhere in the world, with the only reliance being on the unique user ID (e.g., no conditional access, multifactor authentication (MFA), etc.). However, when I voiced my concerns to the IT Operations Director and the chief information officer, I was basically “shot down in flames,” being informed in no uncertain terms that this was not regarded as a risk, that it was a matter of business convenience, and that the criminals would not be interested in attacking a business-to-business (B2B) organization like theirs.
Clearly, they had not considered the risks and the additional mitigation costs needed for a secure transition to the use of Office 365 and did not want to consider the embarrassment of having to go back to the board members to get approval for the additional costs to mitigate the extra risks that they had overlooked or omitted from their initial business case, for moving the business onto Office 365.
You can probably guess what happened next; this process became convenient for the opportunist criminals!
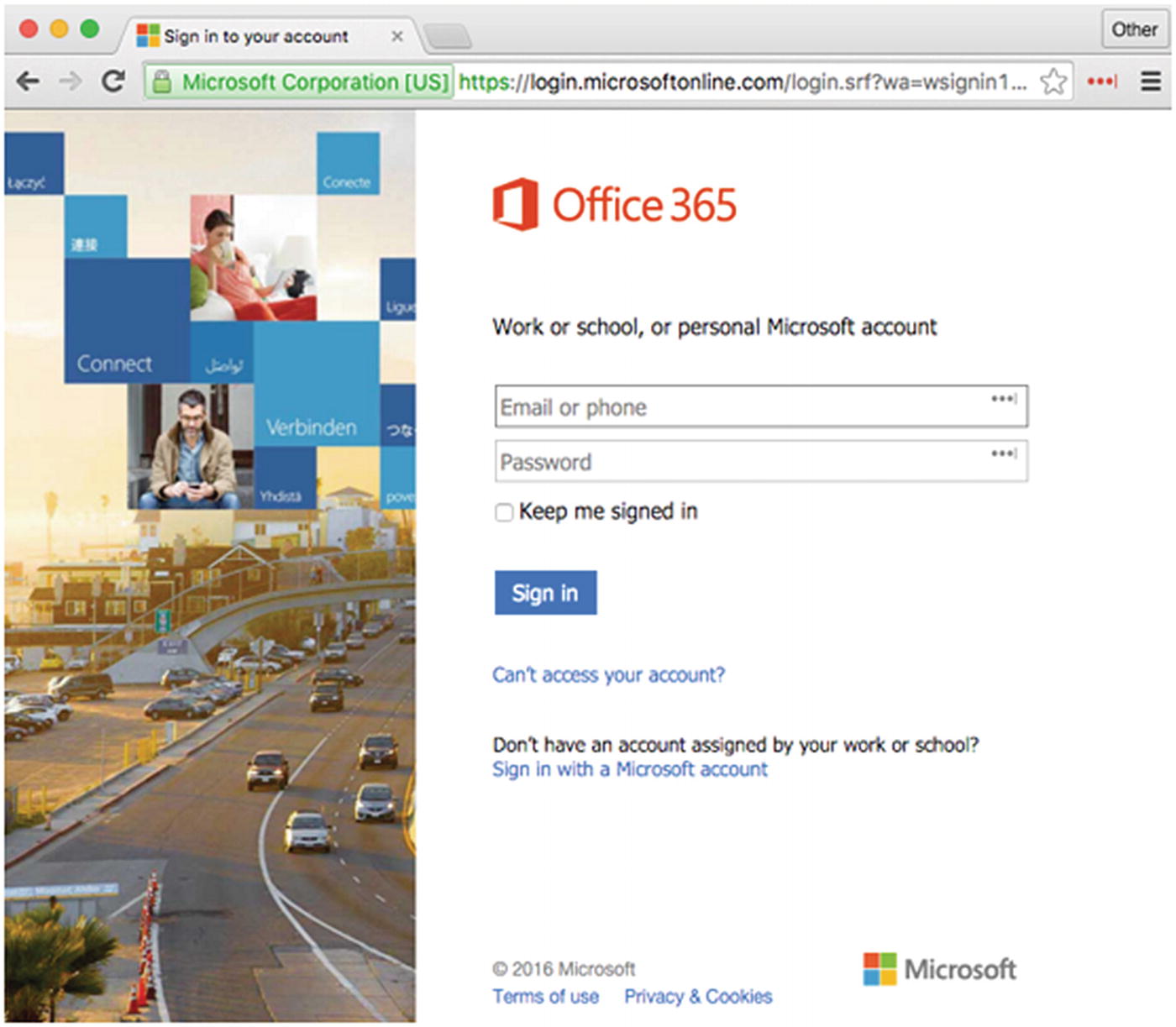
Office 365 login web page
“Deal with it, as I’m too busy!”
Well, the junior assistant then clicked the link and entered their access credentials into the malicious Office 365 web page and clicked the sign-in button. However, they were then greeted with an error page and so just discounted it and carried on with their day.
Exactly 30 days later, less than 5 minutes after logging out of their Office 365 account, an unknown and unauthorized individual logged in to the account (IP address originating from Nigeria) and, using the considerable information available in the business email account, spent around 1 hour sending out more malicious Office 365 emails.
After around 1 hour, they logged out and another logged in, this time with an IP address originating from London, United Kingdom. This activity went on for around 4 hours, that evening (with the attackers even responding to any emails received within this time), until they had sent out over 500 malicious emails.
As soon as this incident had been discovered, the response was to immediately identify any of the business’ employees who could have received this email and to lock their accounts, requiring password resets. However, the distribution list for these malicious emails had not been limited to just the business’ employees, and so an email had to be sent out to all those external recipients to ensure that they were made aware of the issue.
With this incident being regarded as a “near miss” for the organization, the business decision was made to upgrade the end user accounts so that conditional access40 could be enabled.
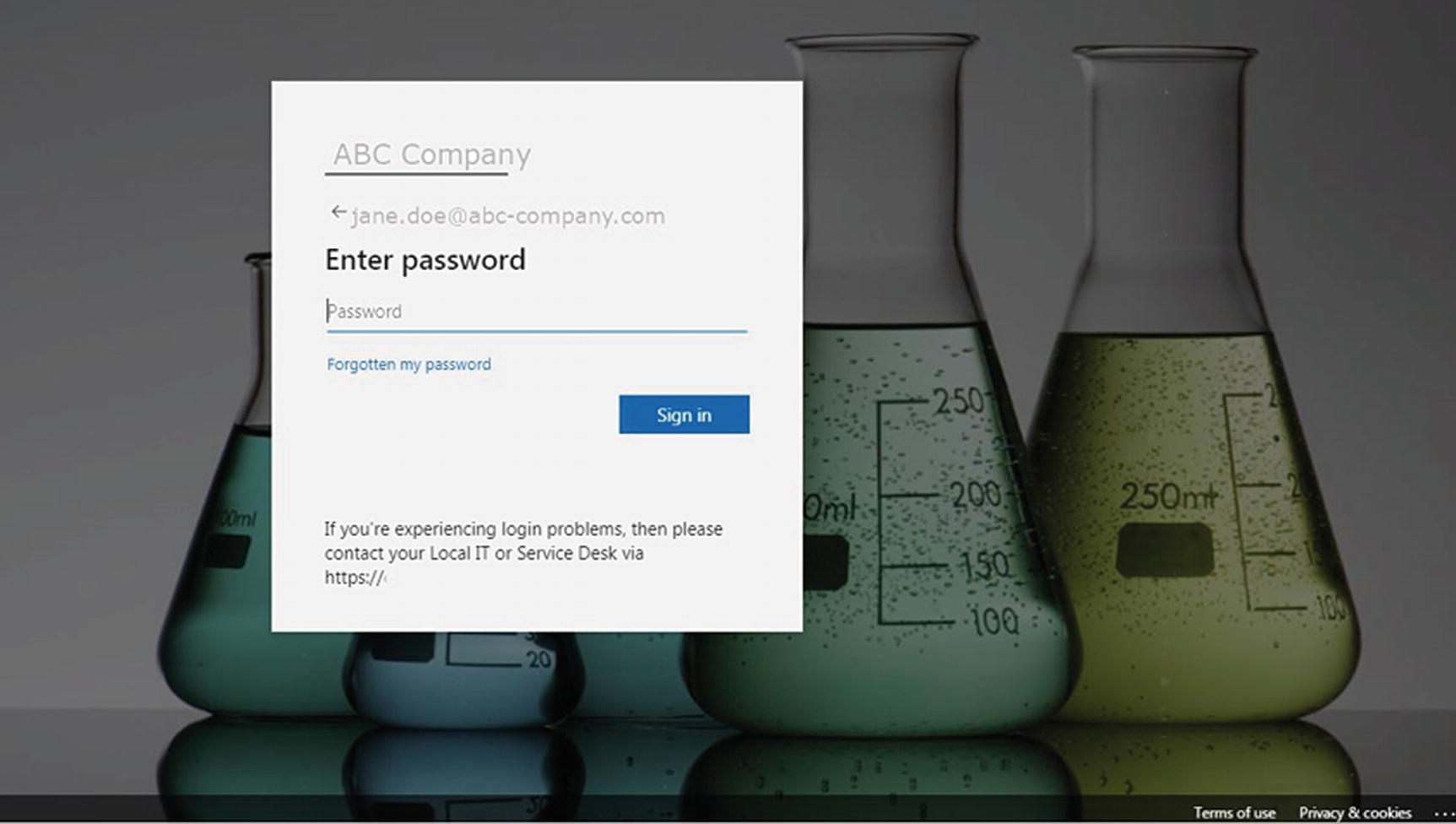
Bespoke Office 365 login web page
However, this did not turn out to be the end of this. It took a considerable length of time to upgrade all the accounts, and the Office 365 was set up to employ single sign-on between the different Microsoft business applications, and some of the board members found changing their account passwords, or not being able to reuse the same “secure password,” a great inconvenience for them.
Approximately 1 week before the conditional access was ready to be implemented (several months later), a payment clerk received several communications, across a few different mediums, purporting to be from three of the board members.
These communications were stressing that there was an urgent invoice, for around $50,000, that needed to be paid immediately. However, in one of the communications, the unknown attackers had made the mistake of addressing the recipient by their surname, when they were on first-name terms. This had made the payment clerk suspicious, resulting in him making a telephone call to the alleged originator of the communication.
Of course, once again, this had been compromised accounts that were being used by the criminals to try and get a fraudulent payment. On discovery, the payment clerk contacted me immediately to raise the alarm.
Having responded and contained the incident, the ensuing investigation revealed that none of the board members could recall having received the initial email and having compromised their accounts, and the access logs did not go back far enough to identify when this compromise may have occurred.
However, it is probably safe to assume that these senior management exceptions to the access restriction rules had allowed them to gain a clandestine persistent presence of their accounts.
Another avoidable “near miss!”
Key Takeaways
Strict access control is an essential component of a defense-in-depth41 model.
An effective access control program should be regarded as an integration between Backend and Frontend Operations.
Backend and Frontend Operations are complementary to each other and should work in harmony with each other.
Restrictions of access should be based on strict role or business requirements.
Access control should include a degree of inconvenience.
Your access control program should implement the principle of least privilege.
- Privileged access should only be used for specific requirements.
Where job functions can be achieved through a standard level of access, these accounts should be used.
Backend Operations should be able to proactively detect ABNORMAL activities.
Frontend Operations are a highly effective additional layer of defense. However, they need to understand what is acceptable and how they should report any difficulties or signs of ABNORMAL activities on their account.
End users should be educated on the risks and receive mentoring on ways to improve the management of their account access credentials.
Any changes to the access control measures should be risk assessed.
Business leaders should consider the benefits of implementing measures to assist with the secure management of the Frontend Operations.