Chapter 1. Introduction to Ransomware
Ransomware is a blanket term used to describe a class of malware that is used to digitally extort victims into payment of a specific fee. In this book we want to give you a high-level introduction to the concept of ransomware and then dig deeply into the methods you would take to protect yourself from this scourge. In this first chapter we will cover a bit of the history of ransomware as well as give an overview of the ransomware attack chain.
At its heart, this form of digital extortion can be broken down into two major types, and then subdivided based on the families they represent. The two major forms of ransomware are those that encrypt, obfuscate, or deny access to files, and those that restrict access or lock users out of the systems themselves. These threats are not limited to any particular geography or operating system, and can take action on any number of devices. Everything from your Android devices, iOS systems, or Windows systems all are at risk of this type of exploitation via ransomware. Depending on the target, the method of compromise of the device may be different, and the final actions taken would be limited by the device capability itself, but there are also recognizable patterns that many extortionists follow.
Ransomware’s Checkered Past
Historically, ransomware dates back to an original piece of malicious code, known as AIDS, written in 1989 by Joseph Popp. That original malicious code would replace AUTOEXEC.BAT on infected systems, and would allow for 90 reboots of the system prior to hiding all of the directories and claiming to encrypt the files themselves. However, upon further analysis it was found that only the filenames themselves were scrambled using basic symmetric key cryptography that was ultimately defeated and removed via programs known as AIDSOUT and CLEARAID. More information on the original AIDS trojan can be found in Jim Bates’ work on the subject published in the Virus Bulletin.1
The method of payment that most digital extortionists request today is cryptocurrency, typically Bitcoin, but this is not the only payment method requested. A number of prepaid voucher services like MoneyPak, Ukash, or PaySafe are also used by criminals.
Ransomware really went out of fashion in the late ’90s and didn’t begin to return to prominence until 2005. The availability of more complex encryption schemes, along with more available system-side computing power, helped usher in this new era of ransomware, which has continued to accelerate. As of 2016, it is considered one of the most prevalent forms of attack against computer systems, requiring limited exposure to vulnerabilities and minimal reconnaissance on target. One of the more familiar variants, CryptoWall (currently defunct), was estimated to have accrued $18,000,000 by the middle of June 2015. Figure 1-1 shows a screen shot of one of the more recent CrytpoWall payment screens.

Figure 1-1. Sample of a CryptoWall payment screen
Anatomy of a Ransomware Attack
Now that the history lesson is over, let’s talk about how ransomware attacks are executed. Figure 1-2 shows the basic anatomy of a ransomware attack.

Figure 1-2. Anatomy of a ransomware attack
Deployment
Phase one of a ransomware attack is the installation of the components that are used to infect, encrypt, or lock the system.
There are a few different methods by which the original files that are used as part of the attack are downloaded to the system:
- Drive-by download
- Occurs when a system automatically downloads a piece of malware or spyware without the end user’s knowledge.
- Strategic web compromise
- (A subset of a drive-by download most often used when a particular target or target demographic has been chosen.) Strategic web compromises are also called watering-hole attacks. These rely on strategic reconaissaince of the end users, and are often reserved for more specific targeted attacks.
- Phishing emails
- May be widespread, untargeted spam or specially crafted to your organization or industry. These emails may include attachments or provide links to malicious websites.
- Exploiting vulnerabilities in Internet-accessible systems
- In this case scanning networks, or blatantly scouring the Internet looking for exploitable vulnerabilities, vs. user initiated actions, like the preceding methods.
Each of the above methods has specific methods to defend against them, though the first three of the four require some form of user interaction and rely on an end user to interact with and or enable the downloader. The fourth method, exploitation of vulnerabilities, is much more methodical and is done as part of a larger attack against a whole organization. If strategic web compromises are the older method used for targeted attacks, vulnerability exploitation is the more modern method for large-scale, targeted attacks.
To prevent drive-by downloaders and strategic web compromises, using browser protection is a good start; but because these threats are constantly morphing, you will need something that doesn’t solely rely on file signatures. This is where edge sandboxing and bare-metal detonation come into play.
What Are These Techniques?
Edge sandboxing is when the border ingress and egress systems take any files traversing them and place them into a virtual environment for execution. This creates a “sandbox,” or safe virtual environment, for any potential malware to execute and perform its malicious intent. However, this is not always effective because more complicated forms of the malicious code can recognize when it is loaded onto an virtual sandbox and choose to not execute, thereby avoiding detection. This is where another strategy is useful.
In bare-metal detonation, instead of having virtual machines available as the sandbox environment, you have actual physical machines where files get sent to execute. This is obviously much more resource intensive, as it requires you to have available a number of physical systems in a variety of operating systems and architectural configurations. Many companies leverage a third-party security company to do something like this on their behalf. Security companies will often have you leverage their proxy services or their email hygiene services, which will grab all files downloaded, as well as all file attachments. These companies will then execute these files in their data centers on both virtual and physical machines to determine whether they are malicious or not prior to forwarding them on to your end users.
For phishing emails, again, the best place to start is at the border, scanning all inbound attachments and executing them in some form of virtual or bare-metal sandbox before they reach the end user, where additional end-user protection products should check these files again prior to allowing them to be opened. In addition to scanning for maliciousness you could also scan files to see if they’ve been opened before and track links within the emails.
Installation
Once a malicious payload has been delivered to the victim system, the infection begins. The infection is delivered in a variety of ways, no matter what the target system is. One method of installation would actually use the download dropper methodology, where the first file is a small piece of code designed to evade detection and communicate with extortionist’s command-and-control channels. The executable would then receive commands to download the ransomware itself for infection on the compromised system. Once it has landed on the system, the ransomware application will install itself on the system. In the case of a Windows system, it will set keys in the Windows registry that will ensure the malcode starts up every time with the computer. For other systems, it will either take advantage of insecure app stores (typically for Android devices) or stolen or valid application development certificates for iOS. The installation of the ransomware is really where the adversary begins to take hold. Oftentimes, the components are broken down into a variety of scripts, processes, batch files, and other tools in order to avoid detection by signature-based AV scanners.
Jailbreak!
While mobile devices are not a significant target for ransomware, they represent the largest growth area in end-user technologies, and thus we expect to see increases in those devices as targets. However, you should keep in mind that many of your end users (and possibly you as well) have had to jailbreak their phones to side-load unapproved applications. This significantly increases your risk, as you are no longer under the protection of the walled gardens set up by many of the smartphone manufacturers.
In a targeted attack, the installation, obfuscation, code-packing, and exploitation techniques may be more nefarious in an attempt to maximize the ransom. Ransomware would use this initial installation to slowly spread throughout the affected network, installing itself on any number of systems and opening file shares that will then be simultaneously encrypted when instructions are sent in the next phase.
The installation process can be complicated. In many cases, the effective modern variants of cryptoransomware first will leverage some form of macro virus or exploited PDF to get onto the system; they also have been known to use WSF, Java, and Adobe Flash. Once the malware has been downloaded to the system, it will execute its embedded code and then begin to analyze the system to determine if it is on a real machine or in a virtual sandbox as shown in Figure 1-3.2 This is the first-stage dropper.
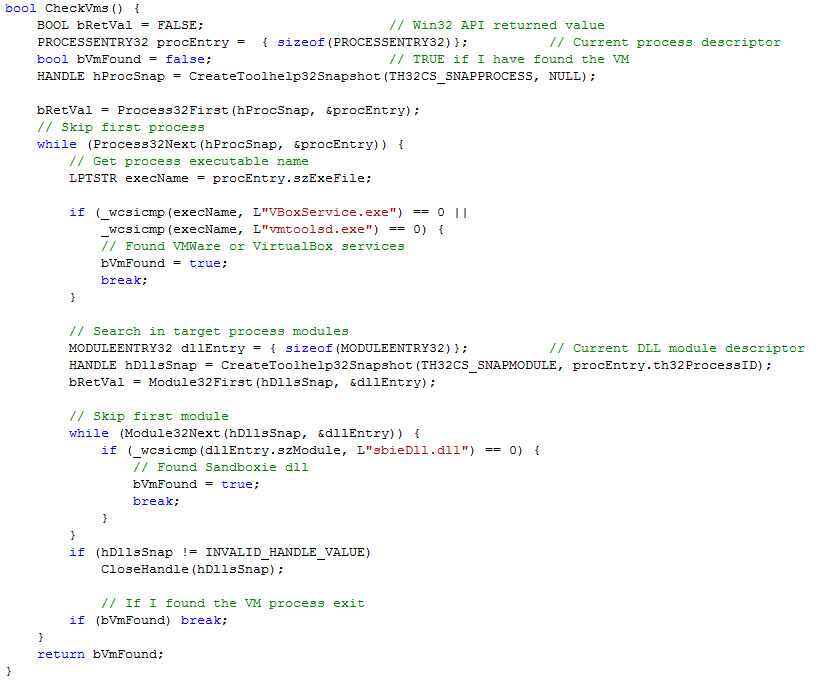
Figure 1-3. Virtual machine check code from CryptoWall2
A second stage then begins if the ransomware determines that it is in a machine worth infecting. If it is, the second process begins, often disguised as a standard Windows process. It is at this point that the malware will make itself more unique, often using an MD5 hash of the computer name or some other unique identifier like a Mac address to ensure the extortionist knows which machine has been compromised.
Then the stage-two dropper may now also run a series of scripts to ensure any native Windows protections are disabled, which could include turning off shadow copy features on files and volumes, turning off system recovery features using something like BCDEdit, and finally killing any anti-malware software and logging functions on the system.
After that, the next phase will occur. Once the ransomware has established itself in a common Windows process like svchost.exe, it will begin the command-and-control phase.
Command-and-Control
All actions require some form of command-and-control systems to effectively determine the next actions to take. This is the same in traditional warfare as it is in cyberspace; therefore, ransomware requires some form of communication channel to be established to ensure these communications can occur. Think about it this way: without receiving orders, it is possible you could have a piece of ransomware on your computer right now lying dormant, waiting for orders.
In a ransomware attack, once the malicious code is deployed and installed, it will begin to reach out to its command servers, looking for instructions. These instructions will be any number of specific requests. They include everything from identifying the types of files they should target for encryption, how long they should wait to begin the process, and whether they should continue to spread prior to beginning the process. In some ransomware variants, they will also report back a significant volume of system information, including IP address, domain name, operating system, installed browsers, and anti-malware products. This information could help a criminal organization determine not only who they have infected, but also if they managed to hit a high-value target, thereby suggesting this compromise be used for more nefarious purposes than a simple ransomware infection.
Command-and-control channels vary with the different variants and families of malware. In some cases, these can be as simple as web-based communications leveraging an unencrypted HTTP protocol to complicated systems that leverage embedded TOR services to connect. The more complex systems like TOR make it even more difficult to trace the exact location of the criminals participating in the extortion, and indeed some of the ransomware variants actually install TOR clients on end-points to ensure they have secure communications.3
Handshake and key exchange
In virtually all cases of ransomware, the malicious code that has been deployed on the victim system is a client, and the command-and-control server operated by the criminal adversary is exactly that, a server. The client that has been placed on your system will ensure it is communicating with the correct bad guy’s server through a prearranged handshake protocol. This handshake protocol is different for every ransomware family, which is a collection of ransomware that acts in a similar manner and often funded by the same criminal organization. However, at its core, it is how criminals identify the variant of the malware executed, as well as the system that they have infected. The identification and validation process is used to confirm that the system indeed has been infected and that it is not part of a larger sting operation being run by international law enforcement or security companies. In some cases, like with the CryLocker ransomware, this is done using a unique method, sending everything packaged as a portable network graphics (PNG) file to an album on a legitimate website, in this case, Imgur. Once the client and server have agreed that they are indeed a prearranged working pair, the next step is the key generation and exchange. Depending on the complexity of the ransomware, this could be anything from a poorly executed simple symmetric key cypher to a complex RSA 4,096-bit encryption algorithm. The key exchange occurs, and the private key is held on the criminal servers while the public key is delivered to the encrypting component of the malcode that has installed on the victim system. In some instances you may get lucky, as some of the less complex ransomware variants do not generate a unique key every time, and the use of public decryptors could reverse the encryption, but this has become less common.
Destruction
At this point the key that will be used to render the files on the system locked or encrypted is now active and ready for use by the malware on the victim device. All the files that have been identified by the command-and-control processes will begin to be encrypted by the malcode. This could include anything from all forms of Microsoft Office documents to JPGs, GIFs, and any number of other file types. Some variants not only encrypt the files, but also the filenames, making it even more difficult for you to know how far the attackers have gotten and which files you have lost.
Extortion
After the files have been encrypted, the victims are shown a screen that tells them how they have been compromised. Extortionists use any number of methods to enforce payment. Some ransomware variants will allow you to decrypt one file for free to prove that there is a key to your system. Other variants have escalating payments, where the price you will need to pay before the key is deleted increases with time. The typical cost for unlocking a system is between $300 and $500 worth of bitcoins, but some of the variants targeting corporations have costs that reach into the tens of thousands of dollars. Some of the more recent variants actually delete files in order to up the ante and scare you into more paying the ransom more quickly. If you pay, there is no guarantee that the key they provide to you will decrypt your files. Additionally, there is no guarantee that the ransomware itself will be removed. In fact, savvy adversaries would use the speed by which you would pay the initial ransom along with any additional information discovered by the malware within the network itself to determine what their next targets within your network should be, which could include backups, network attached storage, or other operational systems that are key to your business operations. They then will use an increased and accelerated ransom to keep you paying.
Destruction Phase
The destruction phase requires a closer look. The destruction phase, as mentioned previously, could be to deny access to the system or to encrypt the files.
File Encryption
The crypto ransomware that we see today uses advanced algorithms to encrypt files on your device or network and comes in two basic flavors: symmetric key and asymmetric key encryption. For the extortionist, each method has distinct advantages and disadvantages. Some of the more complex variants take advantage of both encryption types to overcome the weaknesses of the other.
How Do They Choose What to Encrypt?
Each ransomware variant makes some choices in what files it will encrypt. This can be as simple as performing a search for all files of a particular type on the device to more complicated processes that evaluate the overall entropy of a file in its prior shadow versions, or even systems that leverage the number of times a file was recently accessed. In the first case, if you have any mapped network drives, those too will end up being searched for and encrypted. In the latter case, aggressive backup regimens and antivirus scanning could actually point the ransomware to files that should be targeted.
Symmetric Key Encryption
Malware that uses symmetric key encryption often uses the device itself to generate the key that is leveraged in the encryption process. The use of symmetric key encryption ensures that fewer system resources are used while the malware is encrypting the files. This minimization of performance overhead by the ransomware not only helps reduce detection chances by process monitoring software, but effectively uses the CPU resources of the infected system. Using a small key generated on the device can minimize performance overhead and maximize the volume of files you are encrypting, leveraging the system’s own CPU against it. Another advantage of using symmetric key encryption is that a unique key is generated for every system that is infected, and thus ransomware extortionists can determine which deployments have been successful and which have not been. Additionally, this allows the encryption process to happen on- or offline. This then requires the computer to get back online and send the key to the adversary so they can begin the ransom clock. The key used for encryption is removed form the device and returned to the extortionist. This is done so that they can hold this key to receive their ransom. In order to do this, the ransomware must wait for the computer to get back online. Once it establishes an Internet connection, and the key is transmitted to the criminal, the clock will typically begin.
A major disadvantage of symmetric key encryption is that is can be defeated. It is possible for a user to pull the key from active memory and use this to decrypt the files on the system while it is offline. This means if you have been hit by a variant of malware that uses symmetric key encryption, it is entirely possible for you to decrypt the files yourself.
In order to do this you must first access the volatile memory of the system performing the encryption. This can be done using any number of tools. Traditionally forensics tools would be used to gain direct access to the RAM. One such tool is msramdump, this is a Linux system on a bootable USB that takes advantage of the fact that the DRAM in most systems is still live for anywhere from a few seconds to a few minutes after power loss, so long as you have ECC turned off (often known in BIOS as “quick boot mode”). You would insert the USB into the affected system, reboot the computer, and dump the RAM to the stick. These are known as “cold boot attacks.” Once you have acquired this memory, you can use a tool like Volatility to access the memory dump and begin to search for key-sized message blocks, which, although slow, would be effective at finding your keys unless they have been fragmented.
Using Volatility
To get started, you should become familiar with a few Volatility commands including malfind, yarascan, svcscan, and ldrmodules. The Python commands to engage these are:
python vol.py -f zeus.vmem malfind -p 1724 Volatile Systems Volatility Framework 2.1_alpha
Additionally, there are a number of resources where you can get sample memory files to analyze.
You would also use these tools to look for software artifacts that would identify the system of encryption used, which would help you find the keys necessary to decrypt your files. However, pure symmetric key encryption techniques are rarely used anymore due to the ability of end users to circumvent the ransom using the techniques described.4 Volatility is a tool for exacting any number of informational datasets from the code. It can be used with other types of encryption leveraging its more expansive command set.
Asymmetric key encryption
In this method, the attacker would have a public and private key that are used in the encryption process. The public key is used on the infected system to encrypt the files, and the private key is used to decrypt the files. These key pairs make it impossible to use memory forensics to decrypt the files. Instead, you have to rely on brute-force attacks, weaknesses in the encryption algorithms, paying the ransom, or being prepared for the possibility of this kind of attack in the first place. For asymmetric key ransomware there again are two major types of asymmetric encryption: embedded public key and downloaded public key.
Attacker Errors
It is worth noting that all humans are fallible, and thus just like all applications created by an organization, a piece of ransomware itself may have vulnerabilities within its own code. One of the more common occurrences of ransomware author failure is unintentionally including the private key for the malware within the code itself. This makes decryption a somewhat trivial exercise in extracting the private key from the malcode and decrypting the files, much to the chagrin of the criminal.
In ransomware that leverages an embedded public key, the methodology is fairly straightforward and can be initiated whether the computer is online or not. The disadvantage of this technique is that a new public key must be genereated for each attack.
For ransomware that uses a downloaded public key, the encryption process cannot begin until the computer is back online and able to communicate with the attacker’s server to get the public key. The advantage here is that the attacker can leverage different keys pairs for each infection.
Another major advantage of the asymmetric encryption method is that it uses much larger primes in its encryption algorithm, starting at 2,048 bit and higher.
System or Browser Locking
The other method used during the destruction phase is system or browser locking. Instead of physically encrypting the files on the infected system, this type of ransomware makes the infected device or some applications on the device unusable.
For example, the Windows ransomware locker displays a full-screen window that covers the user’s entire desktop. Different variants create this window in different ways, but all of them will limit the user to just this one window. Some of the more complex types of locking ransomware monitor the system’s desktop via a background thread to ensure that it is the only window active. The contents of the windows in locker ransomware are usually location dependant and downloaded as part of the presentation process to ensure that they serve localized content to the victim, as shown in Figures 1-4 and 1-5.

Figure 1-4. Locally served content based on IP geolocation
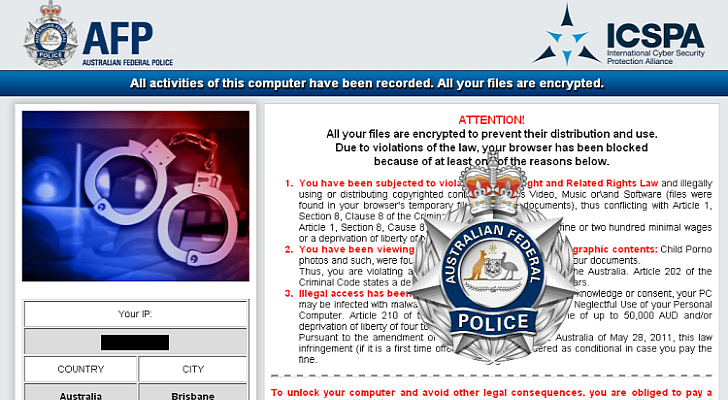
Figure 1-5. Ransomware served to victims in Australia
Once a system has been locked, the ransomware will do any number of things to ensure it maintains persistence on the device, including sending shutdown signals to other processes, issuing kill commands to processes that would be used to end the ransomware executable, and generating a virtual desktop to ensure the end user is unable to break out of the virtual desktops created by the ransomware.
Most browser-locking ransomware is cross-platform. Given that most browser-locking ransomware is client-side, it will be served up by malicious web pages that use JavaScript to pop-up windows on victims’ computers every time they try to close the browser or navigate away from the infected website.
For devices like mobile tablets or phones, the process is similar. An activity window is created by the malware, and the malware regularly checks to ensure that the activity window is displayed. By making these checks in the timespan of milliseconds, it would appear to the human eye that the message is being continuously displayed, not merely restarted. More sophisticated variants will also use the camera on the phone to snap a picture as part of the lock screen as you can see in Figure 1-6.

Figure 1-6. An Android SIM lock screen (notice the device owner’s picture)
The Rapid Growth of Ransomware
Although ransomware has gained attention in the last few years, it has been around since the mid-2000s. Why has it become so big now?
To answer that question, we have to look at the results it has achieved. If you think about the success of criminal organizations initially using spam and phishing campaigns to target anybody with misleading applications or fake antivirus (AV) software through today’s cryptoransomware, it’s easy to see that success begets success—when one group sees how much money another is making, it will find a way to do it, too. It is the free market at work in the most anarcho-capitalistic way possible. In fact, markets have arisen that allow for the sale of high-end mature ransomware, thus lowering the barriers to entry for criminal organizations into this lucrative criminal enterprise.
When you have a highly successful form of attack that relies on a combination of human error and technical strength, criminals will figure out a way to use it to make money. The availability of multiple methods to pack the ransomware, to encrypt the systems quickly and quietly whether online or offline, and the ease of hiding one’s tracks when accepting payment have all led rise to the use of ransomware for digital extortion. Additionally, as criminals have realized new methods for deploying and exploiting networked systems, enterprises that need to have access to their data for legal or even life protection reasons are now being targeted. Criminals are no longer settling for 0.5 bitcoins or $100. Instead, they’re charging hundreds or thousands of dollars, knowing that in some cases companies will pay to ensure they are not complicit in the death of a patient or the loss of revenue associated with major outages.
Criminals have also recognized that instead of having to fence stolen goods, it is more effective for them to simply extort end users and corporations directly. In this way, they lower their costs and increase their return on investment.
Other Factors
Increased availability of strong crypto
In February of 2016, Bruce Schneir reported that there were over 567 different choices for strong crypto products.5 This number does not include any open source choices that are considered weak crypto. This increase in availability has made it incredibly easy for criminals to get their hands on these algorithms and use them in their malicious code.
The global availability of cryptocurrency
Bitcoin is the most commonly known cryptocurrency today. Like all crypto currencies, it is a decentralized method of creating currency by which all participants of the currency system maintain a cryptographically encoded ledger of the transactions within the cryptocurrency system. For the most part Bitcoin is a pseudoanonymous cryptocurrency, since it is ultimately possible to follow the blockchain to identify the individuals behind the transaction in many cases. But this isn’t a simple process, and a savvy extortionist can quickly extract money from Bitcoin wallets to gain cash for use in common markets before being tracked.
Dynamic DNS
Dynamic DNS services are used to allow a domain to be moved regularly to a new IP address. These services use the time to live (TTL) of the domain to ensure that a computer regularly checks back for the new IP address when attempting to resolve it as part of a communication channel. By leveraging any number of dynamic DNS solutions, you can quickly move your infrastructure to another hosting site and minimize the risk of missing out on a piece of ransomware checking in. Because these domain addresses are always resolving to new host IPs, the criminal enterprises can regularly move around the Internet in relative safety, as they will always know their malcode can speak to them, but the authorities will have trouble finding where they have hosted their servers for the last five minutes. Originally these services were used by home or small business users who hosted their own web and mail services in their offices but did not own an IP address that was Internet routable and had their IPs changed regularly by their ISP.
One of the reasons dynamic DNS is so effective is the use of domain generation algorithms, or DGAs, by ransomware. DGAs are components of ransomware code that use a specific predefined method for creating a number of communication channels on the fly. These appear as gibberish and would not be something your average end user would go to, however. Because criminals can set up a number of dynamically created DNS entries and point them to their infrastructure, these domains only need to be available for a brief period and can rotate through a series of IP addresses, keeping criminals relatively safe from detection. This creates problems for law enforcement and security companies to track the criminals. An example of Cryptolocker’s original DGA:
def generate_domain(year, month, day): """Generates a domain name for the given date.""" domain = "" for i in range(16): year = ((year ^ 8 * year) >> 11) ^ ((year & 0xFFFFFFF0) << 17) month = ((month ^ 4 * month) >> 25) ^ 16 * (month & 0xFFFFFFF8) day = ((day ^ (day << 13)) >> 19) ^ ((day & 0xFFFFFFFE) << 12) domain += chr(((year ^ month ^ day) % 25) + 97) return domain
Misleading Applications, FakeAV, and Modern CrytpoRansomware
Criminal organizations first started to look to capitalize on malware outside of the traditional stealing of credentials through what some may consider legitimate applications. Oftentimes these misleading applications would pose as antispyware tools or tools for optimizing your systems overall performance. The perpetrators of these misleading applications would claim that they found spyware on your system, that your registry was in disarray, or that you had file and hardware performance issues. They would have you download their applications, “scan” your system for further issues, and then charge you a fee to “resolve” these issues. These fees ranged from $30 to $100, and this often included a license to the downloaded application that did the scanning or enhancement for you. Needless to say, most of these applications didn’t actually do anything, which is not the worst thing that could have happened besides putting you out $100.
As more people began to hear about viruses, malware, and spyware, criminal organizations sought to take advantage of the free advertising by the media. They decided to take advantage of household names like Norton, McAfee, and others to create fake antivirus (AV) programs. A fake AV campaign involves a pop up stating that the target’s computer is infected with viruses and needs to be cleaned. The pop up leads to a website where victims pay to download the fake antivirus program. Criminals would often steal logos, color schemes, and other copyrighted materials to ensure the fake AV software looked as real as possible, as you can see in Figure 1-7. While this is really just another subcategory of misleading applications it represented a shift in thinking on behalf of criminals who recognized the business potential of previous criminal organizations and used it to their advantage.
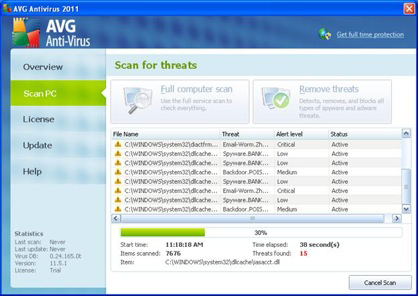
Figure 1-7. A fake AVG AV screen
The fake AV business model mimics the misleading application model and claimed to find a number of spyware, viruses, and trojans on your computer that could only be removed if you upgraded to a paid version of the software. If you paid for the software, the messages would disappear, but after many people started ignoring these messages, the attackers had to figure out a way to up the ante.
This is where the transition to locker ransomware started to occur. If criminals could keep your eyes on the screen and either use scare tactics such as pretending to be from the local police or bullying tactics where they would tell you exactly what criminal gang had locked your system, the ransom would increase. Not only did those percentages of infected machines paying the ransom increase, but the payment size began to creep up as well, moving into the $200 range. As locker ransomware became more prevalent, the reliance on end users to install the malware was removed, and instead the automated installation process became more popular. This not only made it seem like some powerful hacker had taken control of your computer (or some secret branch of the federal police forces), but it also made it more convenient for the criminals—they only needed to compromise one or two popular websites, or run an effective malvertising campaign to get a large number of installations. The larger the number of installations, the better the returns. The scarier the message on the screen, the larger the percentage of returns.
What’s interesting is that the first ransomware was a cryptoransomware variant, and it wasn’t until 2013 when criminals came back to this as the primary source of ransomware income. As anti-malware solutions got better at detecting and removing locking ransomware, criminals needed to find a way to maintain persistence on a system, even while it is powered down, disconnected form the Internet, or even booted to an alternative operating system. This need for persistence led them back to the concept of not necessarily holding the whole computer hostage, but only the information on the system itself. And by no longer being shy about their intentions, they have seen another uptick in their success rates. They have also increased the price for decrypting files to on average $300 in 2016.
Summary
Ransomware has a long and storied past. It has successfully moved from its humble beginnings on 5-1/4″ floppy disks into the modern era using advanced cryptographic techniques; and it targets not only computers, but phones and tablets as well.
Ransomware has increased in popularity because it has been successful. In a world of survival of the fittest, it has adapted and changed to meet the growing demands of its creators. By moving from simple trickery and deception to outright extortion, these criminal organizations are playing on our fears and our need to protect our information. Today criminals have moved on from targeting home users and are focusing on corporate users whose data has significantly more value and who are under extreme regulatory pressure to maintain specific up times and access to protection of key data.
Given the popularity of devices like watches, televisions, refrigerators, and automobiles connected to the Internet, it is only a matter of time before criminals start targeting those devices. Imagine a world where you head out to drive to work, but your fridge was turned off overnight so your cream for your coffee spoiled, and your car won’t start until you pay the ransom to have it unlocked. It’s not that far-fetched and not that far away if we don’t find ways to more effectively protect those devices from criminal actors.
1 Jim Bates’ write-up on AIDS trojan.
2 Andrea Allievi and Earl Carter’s work on CryptoWall is extensive.
3 Lucian Constantin, “Stealthy ransomware ‘Critroni’ uses Tor, could replace Cryptolocker,” IDG News Service, PC World, July 21, 2014.
4 More information on how to use msramdump for extracting DRAM.
5 Bruce Schneier, “Worldwide Encryption Products Survey,” Schneier on Security, February 11, 2016.
