CompTIA Security+ Exam Objectives Covered in This Chapter:
2.1 Recognize and understand the administration of the following types of remote access technologies
802.1x
VPN (Virtual Private Network)
RADIUS (Remote Authentication Dial-In User Service)
TACACS (Terminal Access Controller Access Control System)
L2TP / PPTP (Layer Two Tunneling Protocol / Point to Point Tunneling Protocol)
SSH (Secure Shell)
IPSEC (Internet Protocol Security)
Vulnerabilities
2.2 Recognize and understand the administration of the following email security concepts
S/MIME (Secure Multipurpose Internet Mail Extensions)
PGP (Pretty Good Privacy) like technologies
Vulnerabilities
SPAM
Hoaxes
2.3 Recognize and understand the administration of the following Internet security concepts
HTTP/S (Hypertext Transfer Protocol / Hypertext Transfer Protocol over Secure Sockets Layer)
SSL / TLS (Secure Sockets Layer / Transport Layer Security)
Instant Messaging
Vulnerabilities
Packet Sniffing
Privacy
Vulnerabilities
Java Script
ActiveX
Buffer Overflows
Cookies
Signed Applets
CGI (Common Gateway Interface)
SMTP (Simple Mail Transfer Protocol) Relay
2.4 Recognize and understand the administration of the following directory security concepts
SSL / TLS (Secure Sockets Layer / Transport Layer Security)
LDAP (Lightweight Directory Access Protocol)
2.5 Recognize and understand the administration of the following file transfer protocols and concepts
S/FTP (File Transfer Protocol)
Blind FTP (File Transfer Protocol) / Anonymous
File Sharing
Vulnerabilities
Packet Sniffing
8.3 Naming Conventions
2.6 Recognize and understand the administration of the following wireless technologies and concepts
WTLS (Wireless Transport Layer Security)
802.11 and 802.11x
WEP / WAP (Wired Equivalent Privacy / Wireless Application Protocol)
Vulnerabilities
Site Surveys

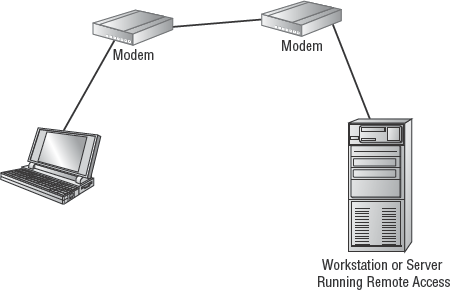
The full name of this section from the Security+ objectives list is "Recognize and understand the administration of the following types of remote access technologies." As networks grow, it becomes more common for them to support remote connections, whether dial-up, wireless WAN, or virtual private network (VPN); see Figure 2.1. The access control and protection issues involved in managing and administering remote access connections are generally termed communications security. In this section, we explore the foundational concepts and security issues of remote access connectivity.
Note
For more information on this topic, refer to Chapter 3 of the Security+ Study Guide, Second Edition, by Sybex
Networks exist to share resources. In order to share resources, all entities on a network must share a common protocol. But in order for the protocol to function, a communication medium must be in place to provide support for the transfer of that protocol and its hosted communication data between one system and another. Often that medium is a network cable, such as a 10BaseT or twisted-pair cable. However, the communication medium could be wireless, a VPN link, a dial-up link, a terminal services link, or even a remote control link. In any case, understanding the technology and the security implications of each of these communication media is an essential part of the Security+ exam.
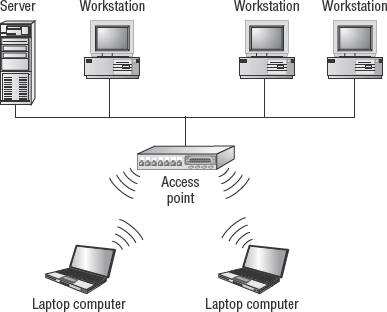
The IEEE 802.1x protocols are a collection of wireless protocol standards. Most modern wireless network communications follow the specifications outlined by the 802.1x standard. There are two widely used wireless standards: 802.11 and 802.16. However, the Security+ exam only focuses on 802.11 and related wireless networking technologies. Figure 2.2 shows a laptop PC (a network client) using a wireless access card to communicate with the rest of the network through a wireless access point and to a wireless server that offers Internet connectivity.
Note
The bulk of the content for wireless communications is covered in section "2.6 Wireless."
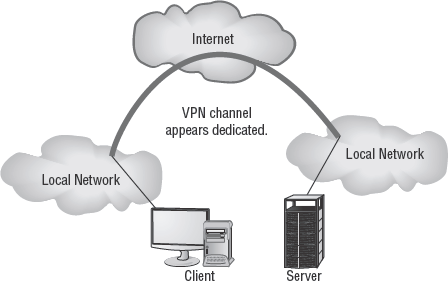
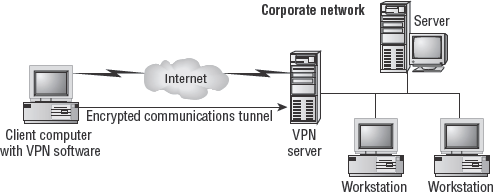
A virtual private network (VPN) is a communication tunnel between two entities across an intermediary network. In most cases, the intermediary network is an untrusted network, such as the Internet, and therefore the communication tunnel is also encrypted. VPNs can be used to connect two networks across the Internet (see Figure 2.3) or to allow distant clients to connect into an office LAN across the Internet (see Figure 2.4). Once a VPN link is established, the network connectivity for the VPN client is exactly the same as a LAN connected by a cable connection. The only difference between a direct LAN cable connection and a VPN link is speed.
VPNs are often the best solution to allow remote users to access resources on a corporate LAN. They have a number of advantages:
They eliminate the need for expensive dial-up modem banks.
They do away with long-distance toll charges.
They allow any user anywhere in the world with an Internet connection to establish a VPN link with the office network.
They provide security for both authentication and data transmission.
VPN links are established using VPN protocols. There are several VPN protocols, but the three you should recognize are Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), and Internet Protocol Security (IPSec).
Note
These protocols are discussed in detail later in this section.
Sometimes VPN protocols are called tunneling protocols. This naming convention is designed to focus attention on the tunneling capabilities of VPNs.
VPNs work through a process called encapsulation. As data is transmitted from one system to another across a VPN link, the normal LAN TCP/IP traffic is encapsulated (encased, or enclosed) in the VPN protocol. The VPN protocol acts like a security envelop that provides special delivery capabilities (for example, across the Internet) as well as security mechanisms (such as data encryption).
When firewalls, intrusion detection systems, antivirus scanners, or other packet-filtering and -monitoring security mechanisms are used, you must realize that the data payload of VPN traffic won't be viewable, accessible, scannable, and so on, since it's encrypted. Thus, in order for these security mechanisms to function against VPN transported data, they must be placed outside of the VPN tunnel to act on the data after it has been decrypted and returned back to normal LAN traffic.
VPNs provide four critical functions:
- Access control
Restricts users from accessing resources on a network
- Authentication
Proves the identity of communication partners
- Confidentiality
Prevents unauthorized disclosure of secured data
- Data integrity
Prevents unwanted changes of data while in transit
As with any type of remote access connection, VPN clients can be authenticated through RADIUS.
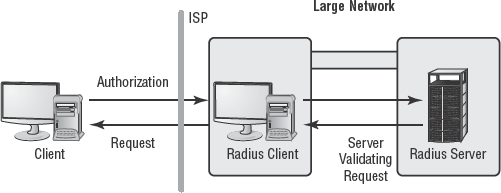
Remote Authentication Dial-In User Service (RADIUS) is a centralized authentication system. It's often deployed to provide an additional layer of security for a network. By offloading authentication of remote access clients from domain controllers or even the remote access server itself to a dedicated authentication server such as RADIUS, you can provide greater protection against intrusion for the network as a whole. RADIUS can be used with any type of remote access, including dial-up, VPN, and terminal services.
RADIUS is known as an AAA server. AAA stands for authentication, authorization (or access control), and auditing. RADIUS provides for distinct AAA functions for remote access clients separate from those of normal local domain clients. RADIUS isn't the only AAA server, but it's the most widely deployed.
When RADIUS is deployed, it's important to understand the terms RADIUS client and RADIUS server, both of which are depicted in Figure 2.5.The RADIUS server is obviously the system hosting the RADIUS service. However, the RADIUS client is the Remote Access Server (RAS), not the remote system connecting to RAS. As far as the remote access client is concerned, it only sees the RAS server, not the RADIUS server. Thus, the RAS server is the RADIUS client.
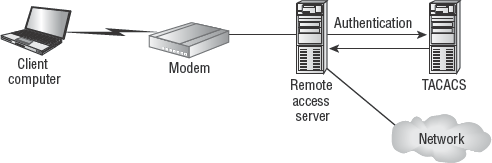
Terminal Access Controller Access Control System (TACACS) is another example of an AAA server. TACACS is an Internet standard (RFC 1492); however, Cisco's proprietary implementations of XTACACS and TACACS+ have quickly gained in popularity. TACACS is a centralized remote access authentication solution (Figure 2.6) similar to RADIUS; it uses ports TCP 49 and UDP 49.
Layer 2 Tunneling Protocol (L2TP) and Point to Point Tunneling Protocol (PPTP) are widely used VPN protocols. PPTP was originally developed by Microsoft. Cisco and Microsoft worked together in creating L2TP (based on Cisco's L2F and Microsoft's PPTP). Since its development, L2TP has become an Internet standard (RFC 2661) and is quickly becoming widely supported.
Both L2TP and PPTP are based on Point-to-Point Protocol (PPP) and thus work well over various types of remote access connections, including dial-up. L2TP can support just about any networking protocol. PPTP is limited to IP traffic. L2TP uses UDP port 1701, and PPTP uses TCP port 1723.
PPTP can use any of the authentication methods supported by PPP, including the following:
Challenge Handshake Authentication Protocol (CHAP)
Extensible Authentication Protocol (EAP)
Microsoft Challenge Handshake Authentication Protocol version 1 (MS-CHAP v.1)
Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v.2)
Shiva Password Authentication Protocol (SPAP)
Password Authentication Protocol (PAP)
Note that PPTP can provide data encryption only when MS-CHAP v.2 is employed for authentication.
L2TP can rely on PPP and thus on PPP's supported authentication protocols. But L2TP also supports other authentication and encryption protocols, such as Internet Protocol Security (IPSec). Although it isn't required, L2TP is most often deployed using IPSec.
Secure Shell (SSH) is a secure replacement for Telnet, rlogon, rsh, and rcp. SSH can be called a remote access or remote terminal solution. It consists of an SSH server component and an SSH client component. SSH offers a means by which a command-line, text-only interface connection with a server can be established over any distance. Through the SSH connection, you can perform any command-line or scriptable activities. See Figure 2.7.
SSH transmits both authentication traffic and data in a secured encrypted form. Thus, no information is exchanged in clear text. This makes SSH a secure alternative to Telnet, which transmits both authentication credentials and data in clear text. SSH operates over TCP port 22.
Internet Protocol Security (IPSec) is both a stand-alone VPN protocol and a module that can be used with L2TP. You can use IPSec in dial-up or network-to-network connections. When it's employed over dial-up, it usually functions as the encryption protocol in an L2TP link. IPSec by itself is more suitable for network-to-network connections across normal LAN connections, high-speed WAN links, and the Internet.
IPSec isn't a single protocol but rather a collection of protocols. Two of the primary protocols of IPSec are Authentication Header (AH) and Encapsulating Security Payload (ESP). AH provides authentication of the sender's data; ESP provides encryption of the transferred data as well as limited authentication.
IPSec operates at the OSI Model layer 3 (the Network layer). IPSec operates over TCP ports 50 and 51. Thus, if an IPSec tunnel is to cross a firewall, these ports must be opened.
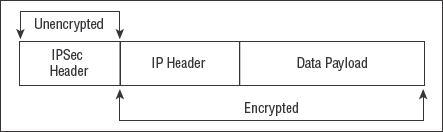
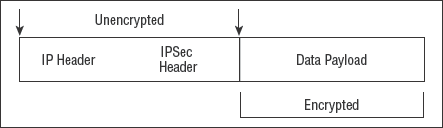
IPSec can operate in two modes: tunnel mode and transport mode. In tunnel mode (see Figure 2.8), IPSec provides encryption protection for both the payload and message header by encapsulating the entire original LAN protocol packet and adding its own temporary IPSec header. In transport mode (see Figure 2.9), IPSec provides encryption protection for just the payload and leaves the original message header intact. Tunnel mode should be used when you're connecting over an untrusted network.
IPSec provides for encryption security using symmetric cryptography. This means communication partners use shared secret keys to encrypt and decrypt traffic over the IPSec VPN link. One of the mechanisms used by IPSec to manage cryptography is Internet Key Exchange (IKE); it ensures the secure exchange of secret keys between communication partners in order to establish the encrypted VPN tunnel.
IPSec also uses Internet Security Association and Key Management Protocol (ISAKMP), which is known as a security association manager. A security association is the agreed-upon method of authentication used by two entities. Without a common method of authentication, a VPN link can't be established. So, ISAKMP is used to negotiate and provide authenticated keying material (a common method of authentication) for security associations in a secured manner. The four major functional components of ISAKMP are
Authentication of communications peers
Threat mitigation
Security association creation and management
Cryptographic key establishment and management
Every communications technology, mechanism, or solution is vulnerable to one thing or another. With the implementation of cryptography to provide security through encryption, many forms of communication have become more reliable and now offer dependable protection. When encryption is involved, the issue often distills down to the algorithm in use and the length of the key. Obviously, using algorithms such as DES, which have been broken, offers weaker security. Likewise, using shorter keys allows a brute-force attack to be more successful.
Outside of the technologies involved with communications, there will always be the weakness of social engineering against the people involved in using those connections. Ultimately, no matter how strong the technology, without reliable physical access control and sufficient employee training, security is little more than a fading wish.
- VPNs
A virtual private network (VPN) is a communication tunnel between two entities across an intermediary network. In most cases, the intermediary network is an untrusted network, such as the Internet, and therefore the communication tunnel is also encrypted.
- Recognize VPN protocols.
PPTP, L2TP, and IPSec are VPN protocols.
- RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a centralized authentication system. It's often deployed to provide an additional layer of security for a network. A RADIUS client is the RAS server.
- TACACS
Terminal Access Controller Access Control System (TACACS) is a centralized remote access authentication solution similar to RADIUS. TACACS uses ports TCP 49 and UDP 49.
- PPTP
Point to Point Tunneling Protocol (PPTP) is based on PPP, limited to IP traffic, and uses TCP port 1723. PPTP supports PAP, SPAP, CHAP, EAP, and MS-CHAP v.1 and v.2.
- L2TP
Layer Two Tunneling Protocol (L2TP) is based on PPTP and L2F, supports any LAN protocol, uses UDP port 1701, and often uses IPSec for encryption.
- SSH
Secure Shell (SSH) is a secure replacement for Telnet, rlogon, rsh, and rcp. It can be called a remote access or remote terminal solution. SSH encrypts authentication and data traffic, and it operates over TCP port 22.
- IPSec
Internet Protocol Security (IPSec) is both a stand-alone VPN protocol and a module that can be used with L2TP. IPSec can be used in dial-up or network-to-network connections. It operates at the OSI Model layer 3 (the Network layer) over TCP ports 50 and 51.
- AH and ESP
IPSec isn't a single protocol, but rather a collection of protocols. Two of the primary protocols of IPSec are Authentication Header (AH) and Encapsulating Security Payload (ESP). AH provides authentication of the sender's data; ESP provides encryption of the transferred data as well as limited authentication.
- Understand tunnel mode and transport mode.
In tunnel mode, IPSec provides encryption protection for both the payload and the message header by encapsulating the entire original LAN protocol packet and adding its own temporary IPSec header. In transport more, IPSec provides encryption protection for just the payload and leaves the original message header intact.
- IKE
Internet Key Exchange (IKE) ensures the secure exchange of secret keys between communication partners in order to establish the encrypted VPN tunnel.
- ISAKMP
Internet Security Association and Key Management Protocol (ISAKMP) is used to negotiate and provide authenticated keying material (a common method of authentication) for security associations in a secured manner. The four major functional components of ISAKMP are authentication of communications peers, threat mitigation, security association creation and management, and cryptographic key establishment and management.
- Recognize communication vulnerabilities.
Every communications technology, mechanism, or solution is vulnerable to one thing or another. With the implementation of cryptography to provide security through encryption, many forms of communication have become more reliable and now offer reliable protection. When encryption is involved, the issue often distills down to the algorithm in use and the length of the key.
The full name of this section from the Security+ objectives list is "Recognize and understand the administration of the following email security concepts."E-mail is the most widely used communication vehicle on the Internet. However, it has also become one of the primary delivery mechanisms for malicious code and social-engineering attacks. Understanding e-mail security issues is essential to the Security+ exam.
Note
For more information on this topic, refer to Chapters 3 and 8 of the Security+ Study Guide, Second Edition, by Sybex
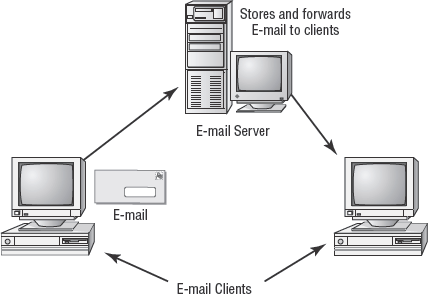
Internet-based e-mail relies primarily on a single protocol: Simple Mail Transport Protocol (SMTP). In Figure 2.10, SMTP has proven itself over the last 20+ years as a reliable e-mail delivery system. However, it has one significant flaw: its nearly complete lack of security. SMTP doesn't offer encryption for transmitted messages. Thus, any and all e-mail can be snooped and examined. As e-mail becomes the basis for business communications, clear text communication is no longer a viable option. Fortunately, SMTP supports add-on capabilities that bring encryption and other security services to e-mail. SMTP operates over TCP port 25.
Other protocols are involved with a complete e-mail solution. Post Office Protocol (POP) and Internet Message Access Protocol (IMAP) are used to pull e-mail from an e-mail server down to a client, but they aren't involved in moving e-mail across the Internet. POP operates over TCP port 110, and IMAP operates over TCP port 143. E-mail is natively insecure. Thus, several encryption options have been developed to add security to e-mail used over the Internet. Two of the most common solutions are S/MIME and PGP.
Secure Multipurpose Internet Mail Extensions (S/MIME) is an Internet standard for encrypting e-mail. Many e-mail security products are based on the S/MIME standard. S/MIME takes the standard MIME element of e-mail, which enables e-mail to carry attachments and higher-order textual information (fonts, color, size, layout, and so on), and expands this to include message encryption. S/MIME uses RSA (an asymmetric encryption scheme) to encrypt and protect e-mail.
S/MIME works by taking the original message from the server, encrypting it, and then attaching it to a new blank e-mail as an attachment. The new blank e-mail includes the sender's and receiver's e-mail addresses, to control routing of the message to its destination. The receiver must then strip off the attachment and decrypt it in order to extract the original message. When e-mail encryption is used, confidentiality is protected.
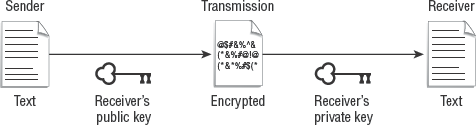
As shown in Figure 2.11, the basic process is as follows:
The sender encrypts the message with the recipient's public key.
The message is sent to the recipient.
The recipient decrypts the message using the recipient's private key.
Note
As you'll learn in Chapter 4, "Basics of Cryptography," in an asymmetric cryptography solution, each communication entity has its own private and public key pair. Anything encrypted with the public key can only be decrypted with the corresponding private key, and vice versa.
The process of encrypting e-mail isn't complex; however, it's cumbersome in implementation. Fortunately, an S/MIME add-on package for an e-mail client automates the process. The only restriction to the S/MIME e-mail solutions is that all communication partners must have compatible S/MIME products installed and use a common or compatible source for their asymmetric encryption key pairs.
S/MIME includes the capability to digitally sign e-mails; however, this isn't a widely employed feature. Pretty Good Privacy's (PGP) digital signature feature is much more popular.
Pretty Good Privacy (PGP) is another e-mail security and encryption product that functions in much the same way as S/MIME. PGP was developed by Phillip R. Zimmerman in 1991. It has widespread popularity with the general public as well as corporations that wish to use secured private e-mail. PGP uses RSA or Diffie-Hellman asymmetric cryptography solutions. It's similar to S/MIME, but it's a proposed e-mail security standard of its own known as PGP/MIME.
Another popular feature of PGP is digital signatures. A digital signature is a means by which PGP users can sign their e-mails so that both PGP and non-PGP using recipients can see the text or body of the message. However, a PGP recipient can then verify or authenticate the message by testing the signature. Digital signatures provide a means to verify the source of a message; this is known as nonrepudiation. The digital signature also includes a hash value of the message and allows the recipient to verify that the integrity of the message hasn't been violated while in transit.
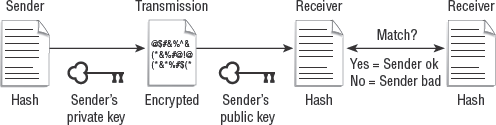
The process of using a digital signature is more complex than encrypting a message. It requires not only a shared asymmetric cryptography solution between the communication partners, but also that both parties use the same hashing algorithm. The procedure for employing a digital signature is as follows (see Figure 2.12):
The sender creates a hash of the original message.
The sender encrypts the hash with the sender's private key.
The sender attaches the encrypted hash to the original message and sends it to the recipient. (Note: the original message is in clear text form.)
The recipient strips off the encrypted hash.
The recipient decrypts the hash using the sender's public key.
The recipient generates a hash of the received original message (without the attached encrypted hash).
The recipient compares the generated hash with the extracted hash from the sender. If they match, the recipient knows the message hasn't changed and the message is from the identified sender.
Tip
See Chapter 4 to learn more about asymmetric cryptography and hashing.
E-mail allows for fast, efficient communications across the Internet. There are more e-mail addresses than there are actual Internet users, because many people have multiple e-mail addresses whether by chance or by choice. E-mail offers individuals and companies alike a means to communicate without paying any type of per-message fee (such as with snail mail) and allows message to be delivered in seconds rather than days. However, these abilities of e-mail also make it ripe for exploitation by those with malicious or at least nonbenevolent intentions. Some examples include spam and hoaxes, which are discussed in the following sections.
Note
E-mail relaying is also another important issue. That topic is discussed at the end of section "2.3 Internet Security."
Because e-mail is so widely used, it has become the most prevalent delivery vehicle for malicious code such as viruses, logic bombs, and Trojan horses. To combat this threat, you should deploy an antivirus scanner to scan e-mail content and attachments. You should even consider stripping or blocking e-mail attachments (especially those with known extensions of scripts or executables) as they enter your network (on an e-mail gateway, firewall, and so on).
E-mail servers should also check for invalid, corrupted, or malformed messages. An e-mail message with a corrupted MIME header can cause an unprepared e-mail server to crash or freeze. Thus, attackers can use invalid e-mail formats as a method of waging a Denial of Service (DoS) attack against your e-mail systems. By keeping e-mail servers properly updated and deploying antivirus scanners and e-mail filters, you can avoid most of the problems and attacks associated with e-mail.
Spam is any type of e-mail that is undesired and/or unsolicited. Think of spam as the digital equivalent of junk mail and door-to-door solicitations.
Note
Some studies have shown that nearly half of all e-mail now consists of spam.
Spam is a problem for numerous reasons:
Some spam carries malicious code such as viruses, logic bombs, and Trojan horses.
Some spam carries a social-engineering attack (also known as hoax e-mail).
Unwanted e-mail wastes your time while you sort through it looking for legitimate messages.
Spam wastes Internet resources: storage capacity, computing cycles, and throughput.
The primary countermeasure against spam is an e-mail filter. An e-mail filter is a list of e-mail addresses, domain names, or IP addresses where spam is known to originate. If a message is received from one of the listed spam sources, the e-mail filter blocks or discards it. Some e-mail filters are becoming as sophisticated as antivirus scanners. These e-mail filters can examine the header, subject, and contents of a message to look for key words or phrases that identify it as a known type of spam, and then take the appropriate actions to discard or block the message.
However, e-mail spam filters are problematic. Just because a message includes key words that are typically found in spam doesn't mean that every message with those words is spam. Some legitimate, if not outright essential, messages include spam words. One method of addressing this issue is for the spam-filtering tool to place all suspected spam messages into a quarantine folder. Users can peruse this folder for misidentified messages and retrieve them.
Another important issue to address when managing spam is spoofed e-mail. A spoofed e-mail is a message that has a fake or falsified source address. When an e-mail server receives an e-mail message, it should perform a reverse lookup on the source address of the message. If the source address is fake or nonexistent, then the message should be discarded.
A hoax is an e-mail message that includes incorrect or misleading information. This is a written or static form of social-engineering attack. Hoaxes are common and widespread because they expertly prey on human nature. If e-mail recipients aren't prepared for hoaxes, they can be easily caught up in them or persuaded by them. Hoaxes may inform you of intended court cases or legislation and encourage you to support one side or the other with a donation. They may warn you of a quickly spreading virus and provide details on how to sanitize your computer, such as deleting certain files or editing the Registry. Hoaxes also include chain letters that promise good fortune, bypassing of bad luck, or accumulation of wealth by passing the message on to others.
Although a hoax isn't the same as a virus, in that it causes no direct damage, it often ends up causing nearly as much damage as a virus would. When ignorant users follow the instructions of a hoax—especially those that instruct readers to delete files or alter their system configuration via the Registry—the users usually end up damaging their operating system so severely as to require a reinstall or restoration from backup. Even if the damage isn't immediately or obviously severe, sometimes the instructions in a hoax open up vulnerabilities so that real viruses, remote-control hacker tools, or other forms of malicious code can gain access.
Your primary weapon against hoaxes is education and awareness. E-mail users should be on the lookout for any message that promises the unlikely, seems too good to be true, or has dire warnings that require immediate action.
When you receive a message that you think might be a hoax, whether intentional or not, do the follow:
Notify your network administrator when you receive a suspected hoax.
Check with your antivirus vendor for confirmation of malicious code–related issues.
Check with your antivirus vendor for e-mail hoax–related issues (most maintain a database of hoaxes).
Find at least three other reliable, public, trusted sources to corroborate any message, especially if it involves legal or monetary issues.
Don't forward any message to others if the message specifically directs you to do so. If there is a legitimate security issue spreading across the Internet, the security watchdogs will respond and inform the public appropriately.
Never follow the directions in an e-mail from an unknown or untrusted source. Always validate procedures from a trusted, reliable source (such as Microsoft, a software vendor, an antivirus vendor, or your ISP).
If you discover a hoax, especially one that isn't already cataloged in your antivirus vendor's hoax database, send the vendor a copy so it can inform others. Be sure to contact the vendor and ask how to submit examples of hoaxes; don't just forward the message.
- SMTP
Simple Mail Transport Protocol (SMTP) moves e-mail messages across the Internet from sender to recipient. It doesn't include native encryption. It operates over TCP port 25.
- POP and IMAP
Post Office Protocol (POP) and Internet Mail Access Protocol (IMAP) are used to pull e-mail from an e-mail server down to a client. POP operates over TCP port 110. IMAP operates over TCP port 143.
- S/MIME
Secure Multipurpose Internet Mail Extensions (S/MIME) is an Internet standard for encrypting and digitally signing e-mail. It uses RSA (an asymmetric encryption scheme) to encrypt and protect e-mail.
- PGP
Pretty Good Privacy (PGP) is used to encrypt and digitally sign e-mail messages. It uses RSA or Diffie-Hellman asymmetric cryptography solutions.
- Understand e-mail as a malicious code delivery vehicle.
E-mail is the most prevalent delivery vehicle for malicious code such as viruses, logic bombs, and Trojan horses. Deploy an antivirus scanner to scan e-mail content and attachments, and block e-mail attachments (especially those with known extensions of scripts or executables).
- E-mail DoS attacks
E-mail servers should check for invalid, corrupted, or malformed messages. An e-mail message with a corrupted MIME header can cause an unprepared e-mail server to crash or freeze.
- Spam
Spam is undesired or unsolicited e-mail. It's a problem for numerous reasons. First, some spam is the carrier for malicious code such as viruses, logic bombs, and Trojan horses. Second, some spam is the carrier of a social-engineering attack (hoax e-mail). Third, unwanted e-mail wastes your time while you're sorting through it looking for legitimate messages. Fourth, spam wastes Internet resources such as storage capacity, computing cycles, and throughput.
- E-mail filters
An e-mail filter is a list of e-mail addresses, domain names, or IP addresses where spam is known to originate.
- Spoofed e-mail
A spoofed e-mail is a message that has a fake or falsified source address. When an e-mail server receives an e-mail message, it should perform a reverse lookup on the source address of the message.
- Hoaxes.
A hoax is an e-mail message that includes incorrect or misleading information. This is a written or static form of social-engineering attack. Your primary weapons against hoaxes are education and awareness. Notify your network administrator when you receive a suspected hoax.
The Internet has become a common communication medium for both home users and business users alike. Due to this wide spread dependence on such an insecure network, it is important to specifically impose security on all sensitive, confidential, or private communication transmissions occurring over the Internet. This section focuses on SSL, TLS, HTTP, HTTPS, instant messaging, and the vulnerabilities of these common Internet communication mechanisms.
Note
For more information on this topic, refer to Chapters 3 and 4 of the Security+ Study Guide, Second Edition, by Sybex
The World Wide Web is a vast global ad hoc collection of online information and storefronts. The primary protocol that supports the Web is Hypertext Transfer Protocol (HTTP). HTTP enables the transmission of Hypertext Markup Language (HTML) documents (the base page elements of a website) and embedded multimedia components such as graphics and mobile code (see Figure 2.13). Without HTTP, there would be no Web. However, HTTP is an insecure protocol: it doesn't offer anything in the way of authentication or encryption for web communications. Fortunately, numerous add-on protocols and mechanisms provide these and other security service to the information superhighway.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are used to encrypt traffic between a web browser and a web server. Through the use of SSL or TLS, web surfers can make online purchases, interact with banks, and access private information without disclosing the contents of their communications. SSL and TLS can make web transactions private and secure. While they aren't true VPN protocols, SSL and TLS operate in much the same manner as VPNs.
SSL was originally developed by Netscape, but it quickly became an Internet standard. Currently SSL version 3.0 is in widespread use across the Internet. TLS is based on SSL, but they aren't interoperable. SSL operates over TCP port 443, whereas TLS can operate over TCP port 443 or 80 (as does HTTP).
SSL can also be used to provide encrypted sessions for other application layer protocols, such as Telnet, FTP, and e-mail. SSL functions at layer 5 (the Session layer) of the OSI Model.
When SSL is to be used to secure the communications between a web browser and web server, a six-step handshake process must be completed to establish the secured session:
The client requests a secure connection.
The server responds with its certificate, the name of its certifying authority (issuing CA), and its public key.
The client verifies the server's certificate, produces a session (symmetric) encryption key, encrypts the key with the server's public key, and then sends the encrypted key to the server.
The server unpacks the session key and then sends a summary of the session details to the client encrypted with the session key.
The client reviews the summary and then sends its own summary back to the server, likewise encrypted with the session key.
Once both entities receive a matching session summary, secured SSL communications are initiated.
SSL uses symmetric keys as the session keys. The session keys are available in 40-bit and 128-bit strengths.
HTTP is the standard foundational protocol used on the Web. It operates over TCP port 80. HTTP is a plain text or clear text communication protocol; thus it offers no security or privacy to transactions. When SSL or TLS is used to secure transactions, this is known as Hypertext Transfer Protocol over SSL (HTTPS). You'll be able to recognize when secure web communications are occurring using SSL or TLS because the URL will begin with HTTPS and a locked padlock icon will appear in the status bar at the bottom of the browser window.
It's important not to confuse HTTPS with a similar protocol, Secure HTTP (S-HTTP). S-HTTP isn't in widespread use. The primary differences are that S-HTTP doesn't use SSL, it encrypts individual web page elements rather than the entire web communication session, and it can only be used to support HTTP. Overall, S-HTTP is less secure than HTTPS.
In addition to web pages, SSL can also be used to secure FTP, Network News Transfer Protocol (NNTP), Telnet, and other Application layer TCP/IP protocols. S-HTTP is unable to protect anything other than web traffic.
Instant messaging (IM) is a mechanism that allows for real-time text-based chat between two users located anywhere on the Internet. Some IM utilities allow for file transfer, multimedia, voice and video conferencing, and more. However, unlike many Internet information services, such as the Web, FTP, and e-mail, IM is a peer-to-peer based service. There is no need for a centralized controlling server. This makes IM easy for end users to deploy and use, but it's difficult to manage from a corporate perspective. IM is insecure. It has numerous vulnerabilities, such as susceptibility to packet sniffing, it lacks true native security capabilities, and it provides no protection for privacy.
Instant messaging offers little in the way of security or privacy. Many IM clients are susceptible to malicious code deposit or infection through their file transfer capabilities. Also, IM users are often subject to numerous forms of social-engineering attacks, such as impersonation or convincing a victim to reveal information that should remain confidential (such as passwords).
As the capabilities of the Web and other Internet information services expand, the vulnerabilities seem to increase as well. Nearly every form of communication that occurs over the Internet has a wide range of weaknesses. It's important to keep yourself informed about the relevant problems and issues with communication methods you employ and how to resolve or safeguard against them. Some of these issues include JavaScript, ActiveX, buffer overflows, cookies, signed applets, CGI scripts, and SMTP relays.
JavaScript is a scripting programming language that can be embedded directly into the HTML of a web page. It's executed by the web browser and can be used to perform a wide range of functions, both benign and malicious. Unlike its namesake Java, JavaScript doesn't run in a restricted security zone; rather it has nearly unrestricted access to all system resources. Due to its power and unpredictability, it's generally recommended that you disable the download and execution of JavaScript except from websites you're sure you can trust.
ActiveX is a mobile code technology developed by Microsoft. ActiveX controls or components are stand-alone programs that can be attached to or embedded in web documents to perform a wide range of functions. ActiveX components are executed with the same security privileges as the current user. However, the ActiveX component is saved to the hard drive and can be accessed at a later time, even after you've left the website where it was obtained. Thus, ActiveX can be a significant security issue. It's recommended that ActiveX components not be downloaded or executed except from websites you're sure you can trust. In many cases, web browsers can be configured to always allow, always block, or prompt the user each time an ActiveX component is presented by a website.
A buffer overflow occurs when a program receives input that is larger that it was designed to accept or process. The extra data received by the program is shunted over onto the CPU without any security restrictions; it's then allowed to execute (assuming it's a valid command, script, system call, and so on) with system-level privileges. The result of a buffer overflow can be anything, such as a program crash, a system freeze or crash, opening a port, disabling a service, creating a user account, elevating the privileges of an existing user account, accessing a website, or executing a utility. A clever attacker can do just about anything they wish if they can execute a command or script unrestricted access to a system.
Sometimes a buffer overflow attack can be labeled as a form of Denial of Service (Dos) attack, since a buffer overflow occurs when a system receives more data than it can handle (a bit like a flooding attack). This is especially true when the buffer overflow event results in a system no longer being able to process legitimate data or requests.
Poor programming quality controls and not including input validation checks in software lead to buffer overflow attacks. Unfortunately, there is little commercial software that isn't vulnerable to buffer overflow attacks; web server software is attacked most frequently. Fortunately, buffer overflow vulnerabilities are often easily patched with vendor updates.
A cookie is a tracking mechanism developed for web servers to monitor and respond to a user's serial viewing of multiple web pages. A cookie is often used to maintain an e-commerce shopping cart, focus product placement, or track your visiting habits. However, the benign purposes of cookies have been subverted by malevolent entities. Now, cookies are a common means of violating your privacy by gathering information about your identity, logon credentials, surfing habits, work habits, and much more. A cookie can be easily exploited against a web browser to gather sufficient information about a user to allow the attacker to impersonate the victim online. It's generally recommended that you block cookies from all but the most trusted sites.
One method that helps reduce the number of malicious elements of mobile code downloaded and executed on a system is a mechanism known as applet signing. A signed applet is a piece of mobile code that has been digitally signed using the creator's or owner's certificate. A signed applet clearly indicates to the user the source of the applet. Web browsers can be configured to accept only signed applets or to prompt whenever any applet is offered by a website. It's important to understand that a signed applet only proves the applet's identity or source; it provides no guarantee as to the reliability or quality of the applet. Just because you know where an applet comes from doesn't mean that the applet isn't malicious code or that it won't cause a problem with your computer system.
Common Gateway Interface (CGI) is a mechanism developed early in the life of the Web to allow a web browser to submit information from a user back to a web server for processing by a server-side script or application. Although CGI scripting isn't used as widely as JavaScript or ActiveX today, it's still a default-enabled feature of both web servers and web browsers.
CGI has numerous vulnerabilities, the most prevalent of which is the ability of a user to submit data that results in the script's failure, a buffer overflow attack, or the performance of an unauthorized or unwanted activity (at least from the perspective of the web server owner).
Another issue with CGI is that all directories on the web server that host CGI scripts must be configured to allow web visitors to execute files. If the web server's folder hierarchy isn't properly protected, this could enable a user to upload their own scripts and then execute them.
SMTP relay is the feature or function of an SMTP or e-mail server when it receives an e-mail from a client or other SMTP server and then forwards it on to another SMTP server. The forwarding action is similar to normal network packet routing, in that the purpose is to transmit the e-mail message to its destination. E-mail relaying is an essential part of the success of Internet e-mail, but it can be abused.
E-mail relaying abuse often leads to DoS attacks or spam. Spam (specifically, spoofed spam) is often sent by rogue solicitors who find e-mail servers on the Internet that aren't properly configured to authenticate clients and servers before accepting e-mail. When an SMTP server fails to authenticate clients and servers before accepting e-mail, it's known as an open relay.
When you're deploying and securing an SMTP server, it's important to disable the open relay feature. However, even after an SMTP server has been secured, a clever attacker may be able to reenable relaying using a Trojan horse, buffer overflow, or remote access attack against the system. Thus, it's important to regularly check the performance logs and configuration settings of e-mail servers. One important item to look for is the presence of a universal accept for the relaying of e-mail. For example, on Unix systems, the e-mail server will have a file in the /etc/mail/relay folder that lists all the servers and clients that are authorized to submit e-mail. If this file includes a universal include, which is usually represented by a dot and an asterisk (.*), then delete that entry and reboot the system to force the change to take effect.
- web basics.
The Web uses Hypertext Transport Protocol (HTTP) over TCP port 80 to transmit Hypertext Markup Language (HTML) documents between a web server and a web browser.
- SSL
Secure Sockets Layer (SSL) is used to encrypt traffic between a web server and a web browser. SSL operates over TCP port 443. It uses a six-step handshake process to establish a secure web session. SSL uses 40- or 128-bit symmetric session keys.
- TLS
Transport Layer Security (TLS) is used to encrypt traffic between a web server and a web browser in much the same way as SSL. It operates over TCP port 443 or 80. TLS isn't interoperable with SSL.
- HTTPS
HTTPS is Hypertext Transfer Protocol over SSL. The presence of HTTPS at the beginning of a URL indicates the use of SSL or TLS. HTTPS isn't to be confused with Secure HTTP (S-HTTP).
- Instant messaging
Instant messaging (IM) is a mechanism that allows for real-time, text-based chat between two users located anywhere on the Internet. IM offers little privacy and is susceptible to malicious code deposit, and users are subject to social-engineering attacks. IM communications can be intercepted by packet sniffers.
- JavaScript
JavaScript is a scripting programming language that can be imbedded directly into the HTML of a web page. JavaScript, unlike its namesake Java, doesn't run in a restricted security zone; rather, it has nearly unrestricted access to all system resources. Due to its power and unpredictability, it's generally recommended that you disable the download and execution of JavaScript except from those websites you're sure you can trust.
- ActiveX
ActiveX is a mobile code technology developed by Microsoft. ActiveX components shouldn't be downloaded or executed except from websites you're sure you can trust.
- Buffer overflows.
A buffer overflow occurs when a program receives input that is larger that it was designed to accept or process. The extra data received by the program is shunted over onto the CPU without any security restrictions; it's then allowed to execute. The result of a buffer overflow can be anything, such as a program crash, a system freeze or crash, opening a port, disabling a service, creating a user account, elevating the privileges of an existing user account, accessing a website, or executing a utility.
- Cookies
Cookies are a common means of violating your privacy by gathering information about your identity, logon credentials, surfing habits, work habits, and much more.
- Signed applets
A signed applet is a piece of mobile code that has been digitally signed using the creator's or owner's certificate. A signed applet clearly indicates to the user the source of the applet.
- CGI
Common Gateway Interface (CGI) is the mechanism developed early in the life of the Web to allow a web browser to submit information from a user back to a web server for processing by a server-side script or application. CGI has numerous vulnerabilities, most prevalent of which is the ability for a user to submit data that results in the script's failure, a buffer overflow attack, or the performance of an unauthorized or unwanted activity.
- SMTP relay
SMTP relay is the function of an SMTP or e-mail server when it receives an e-mail from a client or other SMTP server and then forwards it on to another SMTP server. E-mail relaying abuse often leads to DoS attacks or spam.
A directory service is a managed list of network resources. Through the use of a directory service, large networks are easier to navigate, manage, and secure.
Note
For more information on this topic, refer to Chapters 5 and 8 of the Security+ Study Guide, Second Edition, by Sybex
Active Directory from Microsoft and eDirectory (or NDS) from Novel are examples of directory services. Both of these products are based on Lightweight Directory Access Protocol (LDAP). Understanding LDAP is an important part of the Security+ exam.
SSL and TLS are covered earlier, in section "2.3 Internet Security."
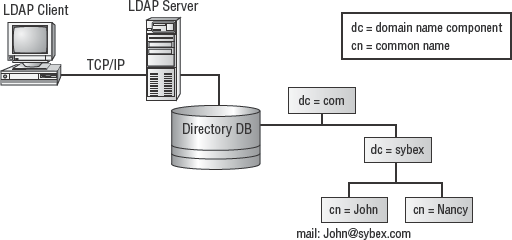
LDAP is a standardized protocol that enables clients to access resources within a directory service. A directory service is a network service that provides access to a central database of information, which contains detailed information about the resources available on a network. LDAP follows the x.500 standard, which defines what a directory service is and how it is to be constructed (at least from a foundational infrastructure perspective). Clients can interact with directory service resources through LDAP by using authentication that is at least a minimum of a username and password.
LDAP directory structures are hierarchical data models that use branches like a tree and that have a clearly identified and define root (see Figure 2.14). LDAP operates over TCP ports 389 and 636. It can employ SSL or TLS to provide authentication and data encryption security.
A common activity on the Internet is the exchange of files. Moving files between one system and another can be accomplished using File Transport Protocol (FTP). You should be familiar with the basics about FTP and the secured alternative file transfer solutions.
Note
For more information on this topic, refer to Chapter 3 of the Security+ Study Guide, Second Edition, by Sybex
File Transport Protocol (FTP) is an in-the-clear file exchange solution. It's supported by any computer system using the TCP/IP protocol. An FTP server system is configured to allow authenticated or anonymous FTP clients to log on in order to upload or download files. FTP employs TCP ports 20 and 21 to establish client to server communications; it then uses a randomly selected higher port (above 1023) for file transfers.
The exchange of files is a common practice on the Internet, intranets, and extranets. FTP is platform independent and thus makes file exchanges between different operating systems simple. It's one of the common services deployed in a demilitarized zone (DMZ) (an extension of a private network where Internet users can access services such as Web and e-mail) in order to provide controlled public access to company resources while still allowing internal clients to access the service(s).
Secure FTP (S/FTP) is a secured alternative to standard FTP. Standard FTP sends all data, including authentication traffic, in the clear. Thus, there is no confidentiality protection. S/FTP encrypts both authentication and data traffic between the client and server; it employs SSH to provide secure FTP communications.
Note
Other alternatives to standard FTP are to use FTP over an SSL connection or across a VPN link. Either of these options effectively provides protection for all FTP traffic.
No matter what secure FTP solution is employed, both the server and the client must have the same solution. Otherwise, FTP session establishment and subsequent file transfer communications won't be possible.
Anonymous FTP is a form of nameless logon to an FTP server. Usually, visitors to an FTP site who wish to log on anonymously use the word anonymous as the logon name. They're then prompted to provide their e-mail address as the password, but any text string suffices.
Site administrators should carefully configure FTP servers that allow anonymous access. Anonymous users shouldn't be able to download (or, in many cases, view) any files uploaded by anonymous users. Anonymous upload and upload should only be enabled if absolutely necessary. When possible, don't allow both authenticated and anonymous FTP logons on the same FTP site. Most FTP servers have anonymous FTP enabled by default, so usually it must be specifically disabled in order to limit access to authenticated users.
If FTP upload is allowed, especially when anonymous FTP uploading is allowed, ensure that it isn't possible to access upload folders from a web URL. If you don't take this precaution, web visitors may be able to download files from the FTP site through HTTP, or they may be able to execute uploaded files.
Blind FTP is a configuration of anonymous FTP or authenticated FTP where uploaded files are unseen and unreadable by visitors. Thus, users can upload files but not see the resulting uploads. This ensures that your FTP site isn't overrun by file swappers using your system as a file exchange point. File swappers often exchange illegal (unlicensed) copies of software, music, and movies through unsecured FTP servers. Uploaded files on a blind FTP server become accessible only after the administrator has either changed the files' permissions or moved them into a folder configured to allow downloads.
You can support file sharing by deploying an FTP server that allows visitors to upload and download files. Restricting such a site to authenticated logons ensures than only authorized users gain access to the site. Allowing anonymous connections to a file-sharing FTP server encourages the exchange of illegal copies of software, music, and movies.
FTP is an in-the-clear transmission protocol. It's also a fairly old but standardized protocol. This makes FTP servers vulnerable to packet sniffing and possibly naming convention troubles.
Since all FTP traffic is transmitted in the clear, all FTP traffic is vulnerable to packet sniffing and other forms of eavesdropping. It's important not to use the same user account and password on FTP that is used in a secure environment. Otherwise, if an attacker captures your FTP logon traffic, they also obtain the logon credentials needed to log in to your secured network. Always use a separate and distinct user account for FTP logons.
Not all operating systems or file systems support long filenames. If an FTP server's host operating system and file systems only support the 8.3 naming convention, then uploaded files with longer filenames will be automatically truncated to comply with 8.3 restrictions. Likewise, if an FTP client's host operating system and file systems only support the 8.3 naming convention, then downloaded files with longer filenames will be automatically truncated to comply with 8.3 restrictions. In either case, this can result in files that are hard to locate, or file name conflicts.
- FTP
File Transport Protocol (FTP) is an in-the-clear file exchange solution. An FTP server system is configured to allow authenticated or anonymous FTP clients to log on in order to upload or download files. FTP employs TCP ports 20 and 21.
- S/FTP
Secure FTP (S/FTP)is a secured alternative to standard or basic FTP that encrypts both authentication and data traffic between the client and server. S/FTP employs SSH to provide secure FTP communications.
- Anonymous FTP
Anonymous FTP is a form of nameless logon to an FTP server. Site administrators should carefully configure FTP servers that allow anonymous access.
- Blind FTP
Blind FTP is a configuration of anonymous FTP or authenticated FTP where uploaded files are unseen and unreadable by visitors. Thus, users can upload files but not see the resulting uploads.
- FTP vulnerabilities.
Since all FTP traffic is transmitted in the clear, all FTP traffic is vulnerable to packet sniffing and other forms of eavesdropping. Not all operating systems or file systems support long filenames. If an FTP server's host operating system and file systems only support the 8.3 naming convention, then uploaded files with longer filenames will be automatically truncated to comply with 8.3 restrictions.
The full name of this section from the Security+ objectives list is "Recognize and understand the administration of the following wireless technologies and concepts."Wireless networking has become common on both corporate and home networks. Properly managing wireless networking for reliable access as well as security isn't always an easy or straightforward proposition. This section examines various wireless security issues.
Note
For more information on this topic, refer to Chapter 4 of the Security+ Study Guide, Second Edition, by Sybex
Wireless communication has become an essential part of networking, whether in the home, at the office, or while being mobile about the city. Understanding wireless networking issues and security is an important part of the Security+ exam. This section dsicusses the following wireless communication issues: WTLS, 802.11, WEP, WAP, wireless vulnerabilities, and site surveys.
Wireless Transport Layer Security (WTLS) is the security layer for the Wireless Application Protocol (WAP). It provides the security services of privacy, integrity, and authentication for WAP-supporting networks. WTLS is based on TLS. It provides for encrypted traffic between a mobile device and a WAP gateway (see Figure 2.15). WAP is often deployed to support wireless handheld devices like PDAs and cell phones.
802.11 is the IEEE standard for wireless network communications. Various versions of the standard have been implemented in wireless networking hardware, including 802.11a, 802.11b, and 802.11g. 802.11x is often used to collectively refer to all of these specific implementations as a group, however 802.11 and 802.11x may be used interchangeably when discussing standard wireless issues. Each version offered slightly better throughput: 2 MB, 11 MB, and 54 MB, respectively. The 802.11 standard also defines Wired Equivalent Privacy (WEP), which provides eavesdropping protection for wireless communications.
Wired Equivalent Privacy (WEP) is defined by the IEEE 802.11 standard. It was designed to provide the same level of security and encryption on wireless networks as is found on wired or cabled networks. WEP provides protection from packet sniffing and eavesdropping against wireless transmissions.
A secondary benefit of WEP is that it can be configured to prevent unauthorized access to the wireless network. WEP uses a predefined shared secret key; however, rather than being a typical symmetric cryptography solution, the shared key is static and shared among all wireless access points and device interfaces. This key is used to encrypt packets before they are transmitted over the wireless link, thus providing confidentiality protection. A hash value is used to verify that received packets weren't modified or corrupted while in transit; thus WEP also provides integrity protection. Knowledge or possession of the key not only allows encrypted communication but also serves as a rudimentary form of authentication, since without it, access to the wireless network is prohibited.
Wireless Application Protocol (WAP) is often deployed to support wireless handheld devices like PDAs and cell phones. WAP employs WTLS for security. WAP environments function using a WAP gateway between the mobile client and the information server.
Wireless networking has made networking more versatile than ever before. Workstations and portable systems are no longer tied to a cable, but can roam freely around an office or environment—anywhere within the signal range of the deployed wireless access points. However, this freedom comes at the cost of additional vulnerabilities. Wireless networks are subject to the same vulnerabilities, threats, and risks as any cabled network, plus there are the additional issues of distance eavesdropping and packet sniffing as well as new forms of DoS and intrusion.
When you're deploying wireless networks, you should deploy wireless access points configured to use infrastructure mode rather than ad hoc mode. Ad hoc mode means that any two wireless networking devices, including two wireless Network Interface Cards (NICs), can communicate without a centralized control authority. Infrastructure mode means that a wireless access point is required, wireless NICs on systems can't interact directly, and the restrictions of the wireless access point for wireless network access are enforced.
One method used to discover areas of a physical environment where unwanted wireless access might be possible is to perform a site survey.
A site survey is the process of investigating the presence, strength, and reach of wireless access points deployed in an environment. This task usually involves walking around with a portable wireless device, taking note of the wireless signal strength, and mapping this on a plot or schematic of the building. Site surveys should be conducted to ensure that sufficient signal strength is available at all locations that are likely locations for wireless device usage, while at the same time minimizing or eliminating the wireless signal from locations where wireless access shouldn't be permitted (public areas, across floors, into other rooms, or outside the building). A site survey is useful for evaluating existing wireless network deployments, planning expansion of current deployments, and planning for future deployments.
One vulnerability commonly discovered during a site survey is the presence of rogue wireless access points. A wireless access point can be connected to any open network port or cable. Such unauthorized access points usually aren't configured for security or, if they are, aren't configured properly or in line with approved access points. Rogue wireless access points should be discovered and removed in order to eliminate an unregulated access path into your otherwise secured network.
- WTLS
Wireless Transport Layer Security (WTLS) is the security layer for the Wireless Application Protocol (WAP). It provides the security services of privacy, integrity, and authentication for WAP supporting networks. WTLS provides for encrypted traffic between a mobile device and a WAP gateway.
- 802.11 and 802.11x
802.11 is the IEEE standard for wireless network communications. Versions include 802.11a (2 MB), 802.11b (11 MB), and 802.11g (54 MB). The 802.11 standard also defines Wired Equivalent Privacy (WEP).
- WEP
Wired Equivalent Privacy (WEP) is defined by the IEEE 802.11 standard. It was designed to provide the same level of security and encryption on wireless networks as is found on wired or cabled networks. WEP provides protection from packet sniffing and eavesdropping against wireless transmissions. A secondary benefit of WEP is that it can be configured to prevent unauthorized access to the wireless network. WEP uses a predefined shared secret key.
- WAP
Wireless Application Protocol (WAP) employs Wireless Transport Layer Security (WTLS) for security. WAP environments function using a WAP gateway between the mobile client and the information server.
- Site surveys
A site survey is the process of investigating the presence, strength, and reach of wireless access points deployed in an environment. Site surveys should be conducted to ensure that sufficient signal strength is available at all locations which are likely locations for wireless device usage, while at the same time minimizing or eliminating the wireless signal from locations where wireless access shouldn't be permitted.
Which of the following isn't an example of a VPN protocol?
IPSec
L2TP
WTLS
PPTP
Which of the following technologies can be used to add an additional layer of protection between a directory services–based network and remote clients?
SMTP
RADIUS
PGP
VLAN
What TCP port does IMAP function over?
143
25
110
443
What is the first action you should take when you receive an e-mail that describes a removal process to clean your system from a rapidly spreading high-risk virus?
Follow the instructions immediately.
Forward the message to everyone you know.
Open any attachment enclosed with the message.
Report the message to your network administrator.
Which of the following technologies uses a six-step handshake process to establish a secured session between a web server and a web client?
IPSec
TACACS
SSL
S/MIME
Which of the following threats is eliminated when only signed applets are allowed to download through a web browser?
CGI
ActiveX
Cookies
Instant messaging
LDAP operates over what TCP ports?
636 and 389
110 and 25
443 and 80
20 and 21
What is a blind FTP site?
A site where users don't authenticate
A site where all traffic is encrypted
A site where only anonymous access is allowed
A site where users can upload but not download
Which is WTLS part of?
WEP
L2TP
WAP
RADIUS
What is the purpose of a site survey?
Improve wireless signal strength
Eliminate unwanted access locations
Distribute WEP keys
Plan the design of a wired network
C. WTLS is the security component of WAP. It isn't a VPN protocol. IPSec, L2TP, and PPTP are all VPN protocols.
B. RADIUS is a centralized authentication solution that adds an additional layer of security between a network and remote clients. SMTP is the e-mail forwarding protocol used on the Internet and intranets. PGP is a security solution for e-mail. VLANs are created by switches to logically divide a network into subnets.
A. IMAP functions over TCP port 143. SMTP functions over TCP port 25. POP functions over TCP port 110. SSL and TLS function over TCP port 443.
D. This e-mail is likely a hoax. When you receive an e-mail hoax, the first step is to inform your network administrator. Don't follow its directions, forward it to others, or open any attachments.
C. SSL uses a six-step handshake process to establish a secured session between a web server and a web client. IPSec doesn't use a six-step process to establish a secured session between two systems. IPSec is a VPN protocol. TACACS doesn't use a six-step process, nor does it create an encrypted session; TACACS is a centralized authentication system for remote access. S/MIME doesn't use a six-step process, nor does it create an encrypted session; S/MIME is an e-mail encryption solution.
B. If only signed applets are allowed to download through a web browser, then you gain protection from unknown sourced ActiveX components. Applet signing doesn't affect CGI, cookies, or IM.
A. LDAP operates over TCP ports 636 and 389. POP and SMTP operate over TCP ports 110 and 25, respectively. TLS operates over TCP ports 443 and 80 (SSL operates only over TCP port 443; HTTP operates only over TCP port 80). FTP operates over TCP ports 20 and 21.
D. At a blind FTP site, users can upload but not download. An anonymous FTP site is one where users don't authenticate and possibly where only anonymous access is allowed. Only through S/FTP or by using FTP inside SSL or a VPN link is all traffic encrypted.
C. WTLS is part of WAP. WEP is a part of 802.11. L2TP is a VPN protocol. RADIUS is a centralized authentication service for remote clients.
B. The purpose of a site survey is to eliminate unwanted access locations. Site surveys aren't used to improve wireless signal strength, distribute WEP keys, or plan the design of a wired network.