The Following CompTIA Security+ Exam Objectives Are Covered in This Chapter:
3.1 Understand security concerns and concepts of the following types of devices
Firewalls
Routers
Switches
Wireless
Modems
RAS (Remote Access Server)
Telecom / PBX (Private Branch Exchange)
VPN (Virtual Private Network)
IDS (Intrusion Detection System)
Network Monitoring / Diagnostics
Workstations
Servers
Mobile Devices
3.2 Understand the security concerns for the following types of media
Coaxial Cable
UTP / STP (Unshielded Twisted Pair / Shielded Twisted Pair)
Fiber Optic Cable
Removable Media
Tape
CD-R (Recordable Compact Disks)
Hard Drives
Diskettes
Flashcards
Smartcards
3.3 Understand the concepts behind the following kinds of Security Topologies
Security Zones
DMZ (Demilitarized Zone)
Intranet
Extranet
VLANs (Virtual Local Area Network)
NAT (Network Address Translation)
Tunneling
3.4 Differentiate the following types of intrusion detection, be able to explain the concepts of each type, and understand the implementation and configuration of each kind of intrusion detection system
Network Based
Active Detection
Passive Detection
Host Based
Active Detection
Passive Detection
Honey Pots
Incident Response
3.5 Understand the following concepts of Security Baselines, be able to explain what a Security Baseline is, and understand the implementation and configuration of each kind of intrusion detection system
OS / NOS (Operating System / Network Operating System) Hardening
File System
Updates (Hotfixes, Service Packs, Patches)
Network Hardening
Updates (Firmware)
Configuration
Enabling and Disabling Services and Protocols
Access Control Lists
Application Hardening
Updates (Hotfixes, Service Packs, Patches)
Web Servers
E-mail Servers
FTP (File Transfer Protocol) Servers
DNS (Domain Name Service) Servers
NNTP (Network News Transfer Protocol) Servers
File / Print Servers
DHCP (Dynamic Host Configuration Protocol) Servers
Data Repositories
Directory Services
Databases

The devices, primarily hardware, that form a network infrastructure are an essential part of the security of that network. Familiarity with each of the common devices in this section is important for the Security+ exam.
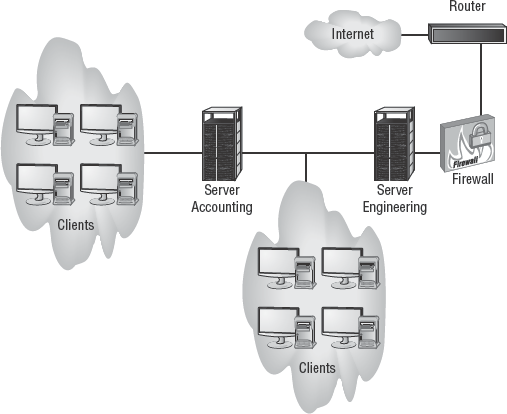
A network is constructed of a wide range of components, including computers, wiring, routers, firewalls, and so on (see Figure 3.1). A clear understanding of these components and their security implications is foundational to understanding security in general. This section examines the security issues of several common networking components.
A firewall is a hardware or software component designed to protect one network from another (see Figure 3.2). Often, firewalls are deployed between a private trusted network and a public untrusted network (such as the Internet) or between two networks that belong to the same organization but are from different departments. Firewalls provide protection by controlling traffic entering and leaving a network.
Firewalls manage traffic using filters. A filter is just a rule. If a packet meets the identification criteria of a rule, then the action of that rule is applied. If a packet doesn't meet the criteria of a rule, then no action from that rule is applied, and the next rule is checked.
Firewalls usually have lots of filters, which are defined in a priority order. The first rule to match criteria with a packet defines the action to take against that packet; no other subsequent rules are checked. Thus, the first rule to apply to a packet is the only rule applied to a packet.
Filter lists are created with the most specific and detailed rules first, followed by successively more general rules, until a final default universal rule is reached, which specifies denial. Therefore, if a packet fails to meet the criteria of any earlier rule, the last "deny" rule will always be used. This way, only packets meeting the custom defined filters or rules are allowed to cross the security barrier.
There are three basic types of firewalls, plus an additional form (stateful inspection) that combines the features of the first three:
- Packet filter
A packet filter firewall filters traffic based on basic identification items found in a network packet's header. This includes source and destination address, port numbers, and protocols used. Packet-filtering firewalls operate at the Network layer (layer 3) of the OSI model. They can also be called common routers.
- Circuit-level gateway
A circuit-level gateway firewall filters traffic by monitoring the activity within a session between an internal trusted host and an external untrusted host. This monitoring occurs at the Session layer (layer 5) of the OSI model. This type of firewall ensures that the packets involved in establishing and maintaining the circuit (a virtual circuit or session) are valid and used in the proper manner.
- Application-level gateway
An application-level gateway firewall filters traffic based on user access, group membership, the application or service used, or even the type of resources being transmitted. This type of firewall operates at the Application layer (layer 7) of the OSI model. Such a firewall can be called a proxy.
- Stateful inspection firewall
A stateful inspection firewall combines features of the three basic firewall types and includes the ability to understand the context of communications across multiple packets and across multiple layers. Thus a stateful inspection firewall can make more intelligent and complex filtering decisions based on higher-order information. One of the key functions of this type of firewall is to ensure that each packet is part of an established TCP communication session. All rogue, or unassociated, packets are blocked.
The first step in effectively designing, deploying, and implementing a firewall is to design or develop a firewall policy: a security policy that focuses on the purposes, uses, functions, and security of the firewalls in an organization. This policy clearly defines how the firewall should filter traffic and the types of traffic that should be blocked or allowed.
Most firewalls are deployed with at least two network interfaces. Such firewalls are called dual-homed (see Figure 3.3) or multi-homed (for two or more NICs). Dual- or multi-homed firewalls provide a clear security distinction between one network and another; thus packets must successfully pass the filters of a firewall in order to move from one network to another. In this manner, firewalls provide strong and reliable security.
Some firewalls with three or more network interfaces can manage access to multiple networks simultaneously. One common deployment uses one of these additional network interfaces to connect to a demilitarized zone (DMZ). The DMZ hosts publicly accessible servers, such as web or FTP. The firewall provides secured but public access to the DMZ, but it prevents unauthorized access to the private network. If such a multi-homed firewall is compromised, only the systems in the DMZ are directly threatened or exposed.
When a port is opened in a firewall to allow a virtual private network (VPN) connection to take place, keep in mind that all encrypted data will pass through the firewall without being inspected or filtered. A firewall, unless it's the intended communication partner, is unable to view and inspect the contents of encrypted data.
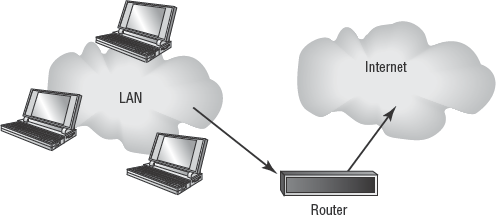
A router (see Figure 3.4) is used to connect several network segments. Routers enable traffic from one network segment to traverse into another network segment (see Figure 3.5). However, the traffic must pass through the router's filters in order to make the transition. A common router is basically a packet filtering firewall. Routers direct traffic based on a routing table and grant or deny access using access control lists (ACLs), such as rules or filters. The routing table informs the router which direction to transmit a received packet based on the best-known pathway (route).
Routers can manage traffic for both inbound and outbound communications. An ingress filter is a traffic filter on packets coming into a secured area from outside (inbound communications). They're the best defense against IP spoofing attacks. An ingress filter should drop any packet received from an outside source that claims to have originated from an inside source.
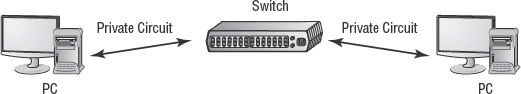
A switch (see Figure 3.6) is like an intelligent multi-port repeater. It receives signals in one port and transmits them out the port where the intended recipient is connected. Switches can be used to connect individual systems or subnets together. They're often used to create virtual LANs (VLANs).
Note
See section "3.3 Security Topologies," for a discussion of VLANs.
Switches are good defenses against sniffing attacks. A switch transmits messages only on those specific network links between the source and destination systems. A sniffer could only intercept traffic that happened to be transmitted on the segment it was connect to. Thus, using switches instead of hubs is a great defense against sniffing.
The Security+ exam focuses on 802.11 and related wireless networking technologies. This includes WTLS, WEP, WAP, 802.11x, related vulnerabilities, and site surveys.
Note
Wireless communications are discussed in more detail in Chapter 2, "Communication Security," in section "2.6 Wireless."
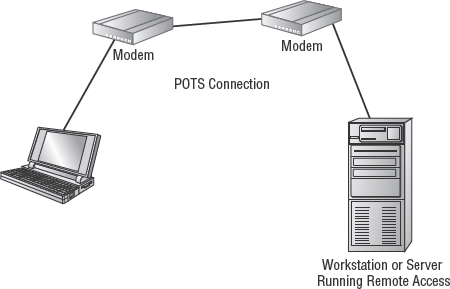
A modem (see Figure 3.7) is a device that creates a network communication link between two computers (or networks) over a telephone line. Modems are one of the slowest remote connection methods still widely supported by operating systems. Most connections are limited to a maximum throughput of 56Kbps. However, since portable systems can use them to connect to corporate offices using any available telephone line, modems will probably be around for years to come.
A common security protection added to dial-in modems is callback: a feature that disconnects the remote user immediately after authentication and then calls the remote user back at a predefined number. Callback ensures that the authenticated user is located at the correct phone number before access to the network is granted.
War dialing is a common attack against dial-in modems on a company network. Such an attack dials all the numbers in a prefix range in order to locate modems connected to computer systems. Once attackers locate a modem that answers a computer call, they can focus their efforts on breaking through the logon security barrier.
A Remote Access Server (RAS) is a network server that supports connections from distant users or systems. RAS systems often support modem banks, VPN links, and even Terminal Services connections.
Note
The various types of RAS connections are discussed in Chapter 2, in section "2.1 Remote Access Technologies."
A private branch exchange (PBX) (also known as telecom), shown in Figure 3.8, is a computer- or network-controlled telephone system. PBXs are deployed in large organizations; they offer a wide range of telephone services, features, and capabilities including conference calls, call forwarding, paging, call logging, voicemail, call routing, and remote calling.
Remote calling is the ability to dial in to a PBX system from outside and then access a dial tone in order to place a call. The second call can be long distance, and all toll charges are accumulated on the PBX system, not on the user's telephone. This is a commonly attacked feature of PBX systems.
Methods to secure PBX systems include the following:
Disabling maintenance features
Changing all default passwords, accounts, and access codes
Enabling logging
Restricting long-distance calling
A Virtual Private Network (VPN) is a communication tunnel between two entities across an intermediary network. In most cases, the intermediary network is an untrusted network, such as the Internet, and therefore the communication tunnel is also encrypted.
Note
Virtual Private Networks (VPNs) are discussed in Chapter 2 in section "2.1 Remote Access Technologies."
An IDS can detect malicious activity that occurs within the network (it doesn't cross the firewall) and activity that is able to pass through the firewall. Intrusion Detection Systems (IDSs) are discussed in detail later in this chapter, in section 3.4.
Network monitoring and diagnostics are terms for watching the activity of an environment, looking for problems, abnormalities, intrusions, or security policy violations. This topic was discussed in Chapter 1, "General Security Concepts," in section "1.7 Understanding Auditing."
In addition to the coverage in Chapter 1 we need to mention Simple Network Management Protocol (SNMP), which is a protocol and problem-management solution. SNMP was designed as a network health-monitoring solution that allowed centralized management of a network environment. SNMP can gather audit-like data on a network level, such as throughput, bandwidth utilization, packet sizes, protocols in use, CPU utilization, open TCP sessions, IP configuration, free disk space, and so on. This information is reported back to the central management console, where the health of the network and individual components is evaluated. SNMP operates over UDP port 161.
Workstations are the computer systems that people use to interact with a network. Workstations are also called clients, terminals, or end-user computers.
Access to workstations should be restricted to authorized personnel. One method to accomplish this is to use strong authentication, such as two-factor authentication with a smartcard and a password or PIN.
Servers are the computer systems on a network that support and maintain the network. Servers provide services or share resources with the network. They require greater physical and logical security protections than workstations because they represent a concentration of assets, value, and capabilities. End users should be restricted from physically accessing servers, and they should have no reason to log on directly to a server—they should interact with servers over a network through their workstations.
A mobile device is any computer device that doesn't need to be permanently connected to a cable. These may include wireless devices as well as portable systems that can be connected to or disconnected from the network via a cable (such as notebook computers).
Wireless devices, a.k.a. mobile devices, were discussed in Chapter 2, in section "2.6 Wireless."
- Types of firewalls
The three basic types of firewalls are packet filtering, circuit-level gateway, and application-level gateway. A fourth type combines features from these three and is called a stateful inspection firewall.
- Routers
Routers enable traffic from one network segment to traverse into another network segment. However, the traffic must pass through the router's filters in order to make the transition.
- Switches
A switch is like an intelligent multi-port repeater. It received signals in one port and transmits them out the port where the intended recipient is connected. Switches are often used to create VLANs.
- Modems
A modem is a device that creates a network communication link between two computers (or networks) over a telephone line. Modems are often secured using callback. They're often attacked using war dialing.
- PBX
A Private Branch Exchange (PBX) (also known as telecom) is a computer- or network-controlled telephone system. Protections for PBX include disabling maintenance features, changing defaults, logging, and restricting long-distance calling.
The full name of this section from the Security+ objectives list is "Understand the security concerns for the following types of media."Media is a collection of both network communication links as well as commonly recognized removable media types. Understanding each of these types of components and how they affect security is an important part of the Security+ exam.
This section discusses the security implications of network cabling and removable media. You should be familiar with each of these components.
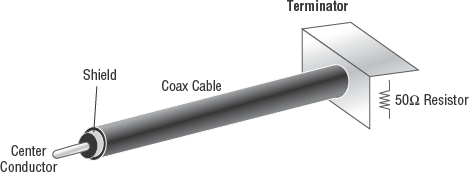
Coaxial cable (see Figure 3.9), commonly known as coax, is type of cable that uses a center conductor surrounded by an insulation sheath, which is surrounded by a metal braid that serves as the second conductor. This conductor, in turn, is surrounded by a final insulation covering. Coax cable used in networking is similar to that used to by cable television.
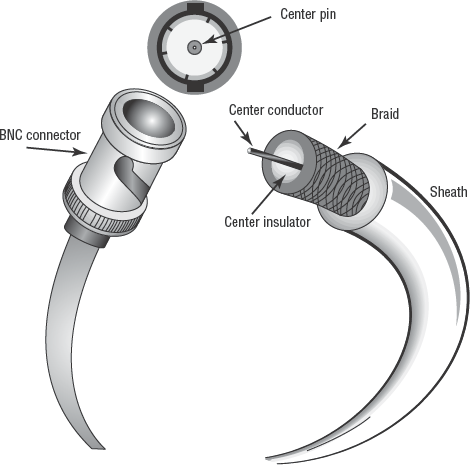
Networking coax cable comes in two forms: 10Base2 and 10Base5. 10Base2, also known as ThinNet, supports communications of 10Mbps, is a baseband form of connection, and has a maximum usage length of 185 meters (hence the 2, which is 1.85 hectometers rounded up). 10Base5, also known as ThickNet, supports communications of 10Mbps, is a baseband form of connection, and has a maximum use length of 500 meters. ThinNet uses BNC connectors (see Figure 3.10) to connect directly to a NIC or networking device. ThickNet uses vampire taps (see Figure 3.11) to connect to an external attachment unit interface (AUI), which is connected to a NIC or networking device.
Common problems with coax cable include bending it past its minimum arc radius, which breaks the center conductor; deploying it past its maximum use length, which causes attenuation (loss of signal strength due to excess cable length); and failing to properly terminate the cable (see Figure 3.12), which results in an inability to support communications.
Twisted pair is the most common form of networking cable. It looks similar to a telephone cable, but twisted pair cabling has more wires, and its RJ-45 connector is slightly larger than the RJ-11 or RJ-14 connectors used by telephone cables. Twisted pair cabling is known as 10BaseT. It supports 10Mbps of throughput, is a baseband form of connection (see Figure 3.13), and has a maximum use length of 100 meters. The T in the name indicates that the cable conductors are twisted rather than the maximum use length as was the case for 10Base2 and 10Base5.
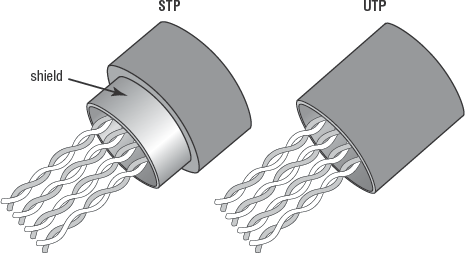
There are two forms of 10BaseT wiring: unshielded twisted pair (UTP) and shielded twisted pair (STP) (see Figure 3.14). The only difference between the two is that STP has a metal foil insulator wrapped around it just nder its exterior plastic sleeve. This provides STP with a slightly greater resistance to electromagnetic interference (EMI) and reduces the effect of EMI on other cables.
Higher throughput forms of twisted pair include 100BaseT and 1000BaseT, which are 100Mbps (megabit Ethernet) and 1Gbps (gigabit Ethernet) respectively.
UTP and STP are commonly categorized according to their ability to support various speeds of throughput (bandwidth) for communications. Table 3.1 shows the common UTP/STP cable specifications.
Generally, twisted pair wiring is more susceptible to EMI than coax, with UTP the more vulnerable of the two. Twisted pair wiring is also vulnerable to excess cable length, which causes attenuation.
Table 3.1. Common UTP/STP Cable Specifications
Category | Speed | Usage |
|---|---|---|
Category 1 | Voice-grade cable | Used strictly for telephone and modems. |
Category 2 | 4Mbps speed | Used extensively in older mainframe systems. |
Category 3 | 10Mbps Ethernet | Used in 10BaseT networks. |
Category 4 | 16Mbps | Used extensively in Token Ring networks. |
Category 5 | 1,000Mbps | Used in 10-, 100-, and 1,000BaseT and similar networks. The most common wiring in newer networks. |
Category 6 | 1,000Mbps | Used in high-speed network installations. Not yet common. |
Category 7 | 1Gbps | Used in very-high-speed network installations. Not available—a proposed standard. |
Fiber optic cable (see Figure 3.15) uses pulses of light instead of electric pulses to transmit data. Thus, fiber optic cable isn't susceptible to EMI. It's also considered invulnerable to most eavesdropping and interception attacks.
Fiber optic cabling offers throughputs in excess of 1Gbps and has maximum deployment lengths of 2km to 26km. The drawbacks of fiber optic cabling include its expense; the difficulty of installing it; and its susceptibility to breakage due to cable stress, stretching, and bending.
Removable media drives are generally considered both a convenience and a security vulnerability. The ability to add and remove storage media to a computer system makes it more versatile. However, it also makes it vulnerable to data theft and malicious code planting.
Removable media include the electronic, logical, or digital storage mechanisms listed in the following sections as well as printed materials. Any time media is no longer needed, it should be properly destroyed to prevent disclosure of sensitive and confidential information to unauthorized entities. For example, failing to destroy printouts or burned CDs may provide dumpster-diving attackers with treasures.
Tape is a form of removable media commonly used for backup purposes. It's a form of sequential storage, so data elements are written and read in sequential order rather than semirandomly as with hard drives. Tape media often support larger storage capacities than most removable media, excluding hard drives. This makes them suited for backup operations.
Backups will be covered in more detail in Chapter 5, "Operational/Organizational Security," in section "5.2 Disaster Recovery."
The topic of CD-Rs or recordable compact disks includes the wide range of optical media that can be written to. This includes CDR, CD-RW, DVD-R, and DVD-RW (plus numerous other variants). Writable CDs and DVDs are often inappropriate for network backups due to their size (a maximum of 650 MB or ∼4 GB), but they're often useful for personal (home) or client level backups. However, the data on a CD isn't protected and thus is vulnerable to unauthorized access if you don't maintain physical control over the media.
Hard drives are usually thought of as the permanent internal storage devices of a computer. This is true, but hard drives are also available in removable formats. These include hard drives that are plugged into the case or attached by SCSI, USB, or IEEE 1394 (FireWire) connections with their own external power supply connections.
Diskettes, or floppies, are removable media that can store only a small amount of data (about 1.4MB). However, even though they're small, they represent a significant security threat to a protected environment if they get into the wrong hands.
A flashcard, or memory card, is a form of storage that uses EEPROM-like memory chips in a small form-factor case. Flashcards often use USB connectors or are themselves inserted into devices like MP3 players and digital cameras. Some flashcards are almost as small as a quarter and are therefore easy to conceal.
Smartcards can be used for a wide variety of purposes. They can be used as an authentication factor (specifically, "something you have"). When used as such, the smartcard hosts a memory chip that stores a password, PIN, certificate, private key, or digital signature. The authentication system uses this stored data item used to verify a user's identity. Smartcards are used as an authentication mechanism by networks, portable computers, PDAs, satellite phones, PKI devices, and more. A smartcard can even function as a credit card (like the American Express Blue card).
A smartcard can also be used as a storage device. Most smartcards have a very limited amount of storage, but sometimes being able to move a few kilobytes of data is all someone needs to steal something of great value. Account numbers, credit card numbers, or a user's private key are all small items that can be very valuable.
- Cable interference
Copper-based cables—coax and twisted pair—are vulnerable to EMI. Fiber optic cable isn't.
- Cable eavesdropping
Copper-based cables—coax and twisted pair—are vulnerable to eavesdropping. Fiber optic cable isn't.
- Removable media
Removable media include the electronic, logical, or digital storage mechanisms listed here as well as printed materials. Any time media is no longer needed, it should be properly destroyed to prevent disclosure of sensitive and confidential information to unauthorized entities.
- Smartcards
Smartcards can be used as an authentication factor (Something You Have). When used as such, the smartcard hosts a memory chip that stores a password, PIN, certificate, private key, or digital signature.
The full name of this section from the Security+ objectives list is "Understand the concepts behind the following kinds of Security Topologies."Knowing how to use security topologies to manage assets of different values is an essential tool in designing, implementing, and sustaining a secure environment.
Security topologies are areas, whether physical or logical, that have different levels of security, privacy, protection, sensitivity, or capabilities. The following sections discuss the key security topologies covered on the Security+ exam.
Security zones are additional divisions or segments of a basic LAN-to-Internet connection that allow for supplementary layers of security and control (see Figure 3.16). Each security zone is an area of a network that has a single defined level of security. That security may focus on authorized access, preventing access, protecting confidentiality and integrity, or limiting traffic flow. Different security zones usually host different types of resources with different levels of sensitivity.
The Security+ exam focuses on three specific zones: DMZ, intranet, and extranet.
A demilitarized zone (DMZ) (see Figure 3.17) is an area of a network that is designed specifically for public users to access. Access to a DMZ is usually controlled or restricted by a firewall and router system. The DMZ acts as a buffer network between the public untrusted Internet and the private trusted LAN. If the DMZ as a whole or individual systems within the DMZ are compromised, the private LAN is unaffected and uncompromised.
A DMZ gives an organization the ability to offer information services, such as Web, FTP, and e-mail, to both the public and internal clients without compromising the security of the private LAN. Often a DMZ is deployed through the use of a multihomed firewall. Such a firewall has three interfaces: one to the Internet, one to the private LAN, and one to the DMZ.
An intranet (see Figure 3.18) is any private LAN that uses the same protocol and information services as the Internet. Thus, any private network that uses TCP/IP and offers services such as Web, FTP, e-mail, and so on is an intranet.
An extranet (see Figure 3.19) is an intranet that functions as a DMZ for business-to-business transactions. It allows an organization to offer specialized services to business partners, suppliers, distributors, or customers. Extranets are based on TCP/IP and often use the common Internet information services, such as Web, FTP, and e-mail. Extranets aren't accessible to the general public.
A virtual local area network (VLAN) consists of subnets that are logically created out of a single physical network. They're often created using switches (see Figure 3.20). Basically, the ports on a switch are numbered; each port is assigned the designation VLAN1 by default. By assigning ports other designations, such as VLAN2 or VLAN3, you can create additional virtual networks.
VLANs function in much the same way as traditional subnets. In order for communications to travel from one VLAN to another, the switch operates as a router to control and filter traffic between its VLANs.
VLANs are used to logically segment a network without altering its physical topology. They're easy to implement, have little administrative overhead, and are a hardware-based solution.
VLANs let you control and restrict broadcast traffic and reduce a network's vulnerability to sniffers. Broadcast traffic isn't automatically forwarded from one VLAN to another, and the sniffer can only see traffic on the segment to which it's connected. This feature of a switch to block broadcasts between VLANs helps protect against broadcast storms. A broadcast storm is a flood of unwanted broadcast network traffic.
In order for systems to communicate across the Internet, they must have an Internet-capable TCP/IP address. Unfortunately, leasing a sufficient number of public IP addresses to assign one to every system on a network is expensive. Plus, assigning public IP addresses to every system on the network means those systems can be accessed (or at least addressed) directly by external benign and malicious entities. One method around this issue is to use network address translation (NAT) (see Figure 3.21).
NAT converts the private IP addresses of internal systems found in the header of network packets into public IP addresses. It performs this operation on a one-to-one basis: Thus a single leased public IP address can allow a single internal system to access the Internet. Since Internet communications aren't usually permanent or dedicated connections, a single public IP address could effectively support three or four internal systems if they never needed Internet access simultaneously. So, when NAT is used, a larger network only needs to lease a small number of public IP addresses.
NAT provides several benefits:
It hides the IP addressing scheme and structure from external entities.
It serves as a basic firewall by only allowing incoming traffic that is in response to an internal system's request.
It reduces expense by requiring fewer leased public IP addresses.
Closely related to NAT is port address translation (PAT), which allows a single public IP address to host up to 65,536 simultaneous communications from internal clients (a theoretical maximum, practically you should limit the number to 10 or less in most cases). Instead of mapping IP addresses on a one-to-one basis, PAT also uses the TCP port numbers to host multiple simultaneous communications across each public IP address.
The use of the term NAT in the IT industry has come to include the concept of PAT. Thus, when you hear or read about NAT, you can assume that the material is referring to PAT. This is true for most Microsoft Windows operating systems and services; it's also true of the Security+ exam.
Using a special protocol, such as a VPN protocol, to create a communication pathway, known as a tunnel, across an intermediary, often untrusted, network. The concept of tunneling is the basis of VPNs.
Note
Tunneling is discussed in Chapter 2, in section "2.1 Remote Access Technologies."
- Security zones
A security zone is an area of a network that has a single defined level of security. That security may focus on authorized access, preventing access, protecting confidentiality and integrity, or limiting traffic flow. Different security zones usually host different types of resources with different levels of sensitivity.
- DMZs
A demilitarized zone (DMZ) is an area of a network that is designed specifically for public users to access. The DMZ is a buffer network between the public untrusted Internet and the private trusted LAN. Often a DMZ is deployed through the use of a multihomed firewall.
- Intranets
An intranet is any private LAN that uses the same protocol and information services as the Internet.
- Extranets
An extranet is an intranet that functions as a DMZ for business-to-business transactions. Extranets let organizations offer specialized services to business partners, suppliers, distributors, or customers.
- VLANs
Switches are often used to create virtual LANs (VLANs)—a logical creation of subnets out of a single physical network. VLANs are used to logically segment a network without altering its physical topology. They're easy to implement, have little administrative overhead, and are a hardware-based solution.
- NAT
NAT converts the IP addresses of internal systems found in the header of network packets into public IP addresses. It hides the IP addressing scheme and structure from external entities. NAT serves as a basic firewall by only allowing incoming traffic that is in response to an internal system's request. It reduces expense by requiring fewer leased public IP addresses, and it allows the use of the private IP addresses (RFC 1918).
- RFC 1918
RFC 1918 defines the ranges of private IP addresses that aren't routable across the Internet: 10.0.0.0–10.255.255.255 (10/8 prefix), one Class A range; 172.16.0.0–172.31.255.255 (172.16/12 prefix), 16 Class B ranges; and 192.168.0.0–192.168.255.255 (192.168/16 prefix), 255 Class C ranges.
The full name of this section from the Security+ objectives list is "Differentiate the following types of intrusion detection, be able to explain the concepts of each type, and understand the implementation and configuration of each kind of intrusion detection system."Intrusion detection is the ability to detect security violations occurring across the network or individual systems.
Intrusion detection is an important security capability. Intrusion Detection Systems (IDS) are considered complementary security solutions to firewalls (see Figure 3.22). An IDS can detect malicious activity that occurs within the network (it doesn't cross the firewall) and activity that is able to pass through the firewall.
The most common problem with an IDS, excluding misconfiguration, is the occurrence of false positives. A false positive occurs when legitimate traffic or user activity is mistaken for intruder activity.
There are two primary forms or types of IDS: network based and host based.
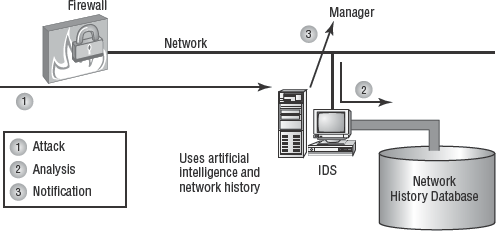
A network based IDS (Figure 3.23) watches network traffic in real time. It monitors network traffic patterns, scans packet header information, and may examine the contents of packets to detect security violations or attacks. A network-based IDS is reliable for detecting network-focused attacks, such as bandwidth-based Denial of Service (DoS) attacks.
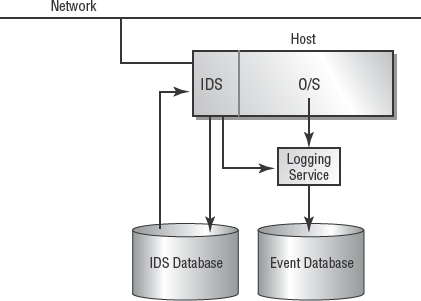
A host-based IDS (Figure 3.24) watches the audit trails and log files of a host system. This type of IDS is limited to the auditing and logging capabilities of the host system (which includes the operating system and installed applications and services). A host-based IDS can detect problems only if sufficient information is captured by the host's auditing capabilities. It's reliable for detecting attacks directed against a host, whether they originate from an external source or are perpetrated by a user locally logged in to the host.
As we've just explained, an IDS is an automated system that either watches activity in real time (network-based IDS) or reviews the contents of audit logs (host-based IDS) in order to detect intrusions or security policy violations. There are two common forms of IDS detection mechanisms: signature detection and anomaly detection. Signature detection (see Figure 3.25) compares event patterns against known attack patterns (signatures) stored in the IDS database. Anomaly detection (Figure 3.26) watches the ongoing activity of the environment and looks for abnormal occurrences. In other words, anomaly-detection IDS is trained on normal activity—it looks for anything that isn't normal.
An IDS (Figure 3.27) with active detection and response is designed to take the quickest action to reduce the potential damage caused by an intruder. This response may include shutting down the server or just the affected service or disconnect suspicious connections (Figure 3.28 and 3.29).
An IDS with passive detection and response will take no direct action against the intruder; instead it may increase the amount of data being audited and recorded and notify the administrators about the intrusion. IDS is good at detecting DoS attacks; exploitation of bugs, flaws, or hidden features; and port scanning. It isn't reliable for detecting spoofed e-mail.

Figure 3.29. IDS instructing the firewall to close port 80 for 60 seconds to thwart an Internet Information Server (IIS) attack
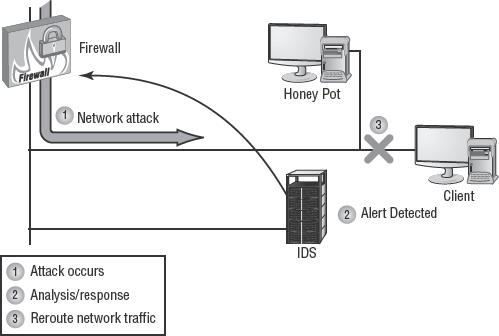
A honey pot (Figure 3.30) is a fictitious environment designed to fool and lure attackers and intruders away from the private secured network. A honey pot is often deployed as a buffer network between an untrusted network, such as the Internet, business partners, or a DMZ, and the private network.
The honey pot looks and acts like a real system or network, but it contains no valuable or legitimate data or resources. Intruders may be fooled into wasting their time attacking and infiltrating a honey pot instead of your actual network. All the activity in the honey pot is monitored and recorded.
The purpose of deploying a honey pot is to provide an extra layer of protection for your private network and to gather sufficient evidence for prosecution against malicious intruders and attackers. A honey pot can often gather sufficient information to determine the identity of the intruder; the type of data, resource, or system being attacked or focused on; and the methods and tools of attack.
When a security breach or perimeter violation is detected, incident response must be initiated. The goal of a planned and documented incident response is to limit the amount of damage caused by the incident, to recover the environment as quickly as possible, and to gather information about the incident and the perpetrator in order to prevent a reoccurrence and pursue legal prosecution.
Note
Evidence gathering and forensics are discussed in Chapter 5 "Operational/Organizational Security", in section "5.6 Forensics."
The best way to respond to security violations is to have an incident response plan to follow. This plan defines and describes the procedures to perform in the event of an incident. One of the first steps that should occur when an incident is detected or suspected is to contact the incident response team, which will then follow the procedures in the incident response plan.
Some of the elements commonly found in an incident response plan include:
Documenting everything, include anything seen on screen
Making backup copies of all affected files, often using a bit-level drive image duplication process
Collecting all audit logs (often by creating copies) and securing them against alteration
It's important not to log off the system or shut down the computer, since these actions may damage or alter evidence.
In the process of responding to an incident, an important goal is to contain the problem. Containment means to limit the scope of damage and to prevent other systems or resources from being negatively affected. Containment is especially important when the incident includes virus infection, remote control access, a Trojan horse, a logic bomb, or the use of hacker tools. Malicious use of these components may leave residual elements that are activated at a later time.
Depending on the type of incident (for example, an intrusion attack across a Internet link), the incident response team may choose to disconnect or terminate a network segment or ISP connection. Once an incident has been contained, the incident response team is responsible for documenting the incident and making recommendations about how to improve the environment to prevent a reoccurrence. A final step in incident response is to evaluate the response plan and procedures and improve them as necessary.
- Network-based IDS
A network-based IDS watches network traffic in real time. It's reliable for detecting network-focused attacks, such as bandwidth-based DoS attacks.
- Host-based IDS
A host-based IDS watches the audit trails and log files of a host system. It's reliable for detecting attacks directed against a host. whether they originate from an external source or are being perpetrated by a user locally logged in to the host.
- Detection mechanisms
Signature detection compares event patterns against known attack patterns (signatures) stored in the IDS database. Anomaly detection watches the ongoing activity of the environment and looks for abnormal occurrences.
- Response methods
An IDS with active detection and response is designed to take the quickest action to reduce potential damage caused by an intruder. This response may include shutting down the server or the affected service or disconnecting suspicious connections. An IDS with passive detection and response takes no direct action against the intruder; instead it may increase the amount of data being audited and recorded and notify the administrators about the intrusion.
- Honey pots
A honey pot is a fictitious environment designed to fool and lure attackers and intruders away from the private secured network. The purpose of deploying a honey pot is to provide an extra layer of protection for your private network and to gather sufficient evidence for prosecution against malicious intruders and attackers.
- Incident response
The goal of a planned and documented incident response is to limit the amount of damage caused by an incident, to recover the environment as quickly as possible, and to gather information about the incident and the perpetrator in order to prevent a reoccurrence and pursue legal prosecution.
The full name of this section from the Security+ objectives list is "Understand the following concepts of Security Baselines, be able to explain what a Security Baseline is, and understand the implementation and configuration of each kind of intrusion detection system."This section discusses the various aspects of security baselines and system hardening as listed on the Security+ objectives list.
A security baseline is a standardized minimal level of security that all systems in an organization must comply with. This lowest common denominator establishes a firm and reliable security structure on which to build trust and assurance. The security baseline is defined by the organization's security policy. It may include requirements of specific hardware components, operating system versions, service packs, patches/upgrades, configuration settings, add-on applications, service settings, and more.
The basic procedures for establishing a security baseline or hardening a system are as follows:
Remove unneeded components, such as protocols, applications, services, and hardware (including device drivers).
Update and patch the operating system and all installed applications, services, and protocols.
Configure all installed software as securely as possible.
Impose restrictions on information distribution for the system, its active services, and its hosted resources.
Documentation is an important aspect of establishing a security baseline and implementing security in an environment. Every aspect of a system, from design to implementation, tuning, and securing, should be documented. Failing to have sufficient documentation is often the primary cause of difficulty in locking down or securing a server. Without proper documentation, all the details about the operating system, hardware configuration, applications, services, updates, patches, configuration, and so on must be discovered before security improvements can be implemented. With proper documentation, a security professional can quickly add to the existing security without having to reexamine the entire environment.
Creating or defining a baseline requires that you examine three key areas of an environment: the operating system, the network, and the applications. The following sections examine issues related to security baseline establishment for these areas.
Operating system hardening is the process of reducing vulnerabilities, managing risk, and improving the security provided by or for an operating system. This is usually accomplished by taking advantage of an operating system's native security features and supplementing them with add-on applications, such as firewalls, antivirus software, and malicious-code scanners.
Hardening an operating system includes protecting the system from both intentional directed attacks and unintentional or accidental damage. This can include implementing security countermeasures as well as fault-tolerant solutions for both hardware and software. Some of the actions that are often included in a system hardening procedure include :
Deploy the latest version of the operating system.
Apply any service packs or updates to the operating system.
Update the versions of all device drivers.
Verify that all remote-management or remote-connectivity solutions that are active are secure. Avoid FTP, Telnet, and so on.
Disable all unnecessary services, protocols, and applications.
Remove or securely configure Simple Network Management Protocol (SNMP).
Synchronize time zones across the network and time clock with an official Internet time server.
Configure event viewer log settings to maximize capture and storage of audit events.
Rename default accounts.
Enforce strong passwords on all accounts.
Force password changes on a periodic basis.
Restrict access to administrative groups and accounts.
Hide the last-logged-on user's account name.
Enforce account lockout.
Configure a legal warning message that's displayed at logon.
If file sharing is used, force the use of secure sharing protocols or use VPNs.
Use a security and vulnerability scanner against the system.
Scan for open ports.
Disable Internet Control Message Protocol (ICMP) functionality on publicly accessible systems.
Consider disabling NetBIOS.
Configure auditing.
Configure backups.
Two aspects of operating system hardening that should not be overlooked are the file system and updates.
The file system in use on a system greatly affects the security offered by that system. A file system that incorporates security, such as access control and auditing, is a more secure choice than a file system without incorporated security. One great example of a secured file system is the Microsoft New Technology File System (NTFS). NTFS was first deployed under Windows NT, but it's now found in Windows 2000, Windows XP, and Windows Server 2003. It offers file- and folder-level access permissions and auditing capabilities. An example of a file system that doesn't include security is File Allocation Table (FAT or FAT32); FAT and FAT32 have no security features.
Security is always a moving target. A system that is secure today may be vulnerable tomorrow. New methods of attacks, new attack tools, new viruses, new weaknesses, accidents in your environment, and much more can cause new risks, threats, and vulnerabilities at any time. Staying vigilant against new security issues is essential in today's business environment. One method to stay as secure as possible is to install updates from vendors.
Vendor updates to operating systems, applications, services, protocols, device drivers, and any other software are the absolute best way to protect your environment from known attacks and vulnerabilities. Not all vendor updates are security related, but any error, bug, or flaw that can be exploited to result in damaged data, disclosure of information, or obstructed access to resources should be addressed.
The best procedure to keep your systems updated is as follows:
Watch vendor websites for information about updates.
Sign up for newsletters, discussion groups, or notifications.
Download all updates as they're made available.
Test all updates on nonproduction systems.
Document changes to your test systems and plan the implementation on production systems.
Back up production systems before implementing updates.
Implement updates on production systems.
Evaluate the effect of the updates on the production systems.
If negative effects are discovered, roll back the update.
At least three types of updates are usually discussed as a collective:
- Hotfixes
A hotfix is a single-issue update that corrects a single problem. Hotfixes aren't as thoroughly tested as other updates; they're quickly designed and released to deal with immediate issues and problems. You should install them if you're experiencing the problem they're designed to correct or you're threatened by the vulnerability they're designed to address.
- Service packs
Service packs are collections of hotfixes and other nonreleased updates as a single entity. They're thoroughly tested and generally should be applied to all systems once they're made available. Service packs are cumulative, so you only need to apply the most recent service pack to keep your systems current.
- Patches
A patch is an update that corrects programming flaws that cause security vulnerabilities. Patches are single-issue utilities that are more thoroughly tested than hotfixes.
Network hardening takes the concept of operating system hardening and applies it to the network. In this instance, the network includes those components on each system that support network communications: the NIC, device drivers, and protocols, as well as the network media (cables or wireless) and network devices (routers, switches, hubs, and so on). Every aspect of a network should be as secure as possible to minimize the potential entry points for an intruder or malicious code. By improving the security of the network, you gain security for each individual system.
Network hardening includes the activities of applying firmware updates and managing configuration issues.
The issue of updates for network hardening includes all the information discussed earlier for operating system hardening. You must also consider the issue of updating firmware. Firmware is the software code stored on memory chips in network devices (such as NIC, routers, and switches). This software code is similar to an operating system but is specifically for network devices. Keeping the firmware updated on all devices is an important part of maintaining a network's security.
Proper configuration of systems connected to the network directly affects the security of the overall network. A weak system serves as the weak link in an environment. If one system is compromised, it could lead to the compromise of other systems on the network. It's important to impose strong security on every computer system and device connected to a network. This includes securing systems using the aspects of operating system hardening and application hardening.
In addition to operating system hardening and application hardening, network hardening procedures should include or address the following:
Limit access to network devices to administrators.
Password-protect or account-lock all configuration consoles on network devices.
Restrict and monitor access to logical and physical console access to network devices.
Use secure remote network devices administration tools, such as Secure Shell (SSH), instead of Telnet.
Disable all unneeded network services, applications, and protocols.
Disable all unneeded interfaces or connections.
Close all unused ports.
Use a firewall to monitor and control use of ports at network borders.
Use access control lists on all network border devices to manage access and limit network traffic.
Consider using static routing instead of dynamic routing.
Use updated routing protocols.
Log network activity, especially on network border devices.
Keep all network devices time synchronized.
Securely configure or remove SNMP.
Disabling unnecessary services and protocols will reduce a system's vulnerability to external attacks. This topic is discussed in Chapter 1, in section "1.3 Identify Non-Essential Services."
Application hardening is the task of imposing security on required applications and services. This usually involves tuning and configuring the native security features of the installed software and installing supportive security applications as needed. When you're developing new applications in house, it's also important to include security design, implementation, and integration throughout the development process.
Application hardening is often seen as a subelement of operating system hardening. In fact, many of the same steps and procedures used to lock down an operating system are used to harden an application or service. In addition to the general notion of disabling any unneeded protocols and services, you should also disable any unneeded features, functions, or capabilities of a service or protocol based on the server's role and the capabilities your organization needs.
In addition to the hardening steps already discussed, you should be familiar with the additional steps to secure common roles found on a network. These include:
Web
E-mail
FTP
Domain Name Service (DNS)
Network News Transfer Protocol (NNTP)
File and printer sharing
Dynamic Host Configuration Protocol (DHCP)
Databases
The following sections detail additional steps relevant to the server function that haven't already been included in the previous discussions of operating system, networking, and application hardening.
The issue of updates for application hardening is exactly the same as that for operating system hardening.
Web servers are used to offer web resources to public and/or private visitors. Web communications can be secured by requiring authenticated access instead of anonymous access. Web traffic can be secured by using Secure Sockets Layer (SSL) or Transport Layer Security (TLS) (for more information, see Chapter 2, in section "2.3 Internet Security").
For web servers hosting CGI scripts, the folder hosting those scripts should be executable. No other folder in the web resource folder hierarchy should be executable. Visitors to the website should not have write access to any folder in the web resource folder hierarchy.
Buffer overflow attacks are common against web servers. Once vulnerabilities are discovered in a commonly used web server application, exploitations of those vulnerabilities are quick to spread across the Internet. It's important to keep web server software patched whenever the vendor releases updates.
Even though access to web resources can be anonymous, you can still control access at a file system level using ACLs. Anonymous visitors without the minimum of read access to web resources will be unable to view or access those resources. Likewise, on web servers using authenticated access, only those resources to which the specific user (whether directly or through group memberships) is granted access can be viewed and accessed through the user's web browser.
A common problem with e-mail is that it's the most prevalent distribution mechanism for malicious code on the Internet. Rigid antivirus scanning (see Figure 3.31) and attachment monitoring are necessary to prevent this essential business communication tool from being a serious vulnerability.
To prevent the transmission of e-mails from nonexistent domains (spoofed source addresses), an e-mail server should perform a reverse DNS lookup on all received messages before transmitting or forwarding them.
E-mail should be protected through the use of software and logical security mechanisms as well as an acceptable use policy. The acceptable use policy will reduce the level of user misuse and abuse of the company's e-mail capabilities.
Note
Most of the general e-mail security issues, especially those related to SMTP and encryption, are discussed in Chapter 2.
FTP is used to transfer files to and from a designated FTP server. FTP is often used over the Internet, but it offers no security.
Note
FTP issues are discussed in Chapter 2, in section "2.5 File Transfer Protocols."
Domain Name Service (DNS) resolves human-friendly domain names, like microsoft.com, into IP addresses. The Network layer (layer 3 of the OSI model) uses the IP address to direct network traffic from source to destination. This resolution activity is essential to the proper working of all Internet and intranet communications. DNS is also a critical component of Microsoft's Active Directory.
In many cases, multiple DNS servers are deployed on a network to provide fault tolerance and load balancing. When a change occurs on one DNS system, it's sent to the other servers on the network through a mechanism known as zone transfer. Zone transfers occur automatically and can be initiated manually. Illegal zone transfers can corrupt the DNS database or give an external entity information about the infrastructure of your private network. Zone transfers should be secured so that they only occur between trusted systems and only authorized users can initiate them.
If your company hosts a Network News Transfer Protocol (NNTP) server, you can secure it by allowing only authorized user access. Activity on the NNTP server should be monitored and logged for signs of malicious activity or abuse of the service.
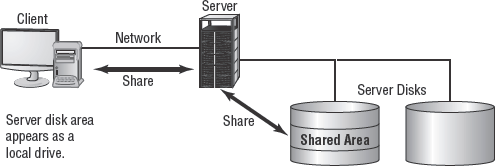
A file server is a network server that offers file access to network clients (see Figure 3.32). An FTP server is an example of a public or Internet file server, but any type of server that users can use to upload and/or download files is a file server. Methods to secure file servers include restricting access to authorized users, logging activity, and imposing quota limits on storage space usage.
A print server is a network server offering a shared network printer for use by network users. Methods to secure print servers include restricting access to authorized users and logging activity. The ability to manage printers, especially to update device drivers, should be restricted to administrators.
Dynamic Host Configuration Protocol (DHCP) is used to assign IP address configuration to systems upon connecting to a network. DHCP allows centralized management of IP addressing schemes. This in turn simplifies administration when subnets, gateways, and DNS server addresses change.
You can secure DHCP servers by limiting DHCP traffic outside of the subnets or networks where it's used. It's especially important to prevent DHCP traffic from leaving your network and entering the Internet. The DHCP protocol functions over TCP ports 67 and 68; these two ports should be blocked on every border device.
A data repository server is any type of server that hosts a service or application that offers resources to users. This includes all the types of servers already mentioned, but the Security+ exam specifically uses this term to refer to directory service servers and database servers.
A directory service server is often called a domain controller or an authentication server. It's responsible for managing access to the resources of a network (Figure 3.33). A directory service is a form of telephone directory for the resources within a network. It includes a list of all servers, clients, users, groups, and shared resources such as files and printers.
Note
Directory services are discussed in Chapter 2, in section "2.4 Directory Security."
A database server hosts a database application where significant amounts of data are stored. Database servers grant users access to the data stored in them through a limited or restricted interface. This interface, sometimes called a view, gives the user access only to those functions they're authorized to perform and only to those elements of data they're authorized to see, view, read, or otherwise interact with. In most cases, user access to databases is indirect. This indirect access mechanism provides environment designers and administrators with an additional layer of security and protection. Through indirect access, you can protect the data in a database from integrity violations as well as confidentiality violations.
- Security baselines
A security baseline is a standardized minimal level of security that all systems in an organization must comply with. This lowest common denominator establishes a firm and reliable security structure upon which to build trust and assurance. The security baseline is defined by the organization's security policy.
- Documentation
Documentation is an important aspect of establishing a security baseline and implementing security in an environment. Every aspect of a system, from design through implementation, tuning, and securing, should be documented. Failing to have sufficient documentation is often the primary cause of difficulty in locking down or securing a server.
- Operating system hardening
Operating system hardening is the process of reducing vulnerabilities, managing risk, and improving the security provided by or for an operating system. This is usually accomplished by taking advantage of the native security features of an operating system and supplementing them with add-on applications, such as firewalls, antivirus software, and malicious-code scanners.
- File system security
The file system in use on a system greatly affects the security offered by that system. A file system that incorporates security, such as access control and auditing, is a more secure choice than a file system without incorporated security.
- Updates
Vendor updates to operating systems, applications, services, protocols, device drivers, or any other software is the absolute best way to protect your environment from known attacks and vulnerabilities. Updates include hotfixes, service packs, and patches. All updates should be tested before deployment in a production environment.
- Network hardening
Network hardening takes the concept of operating system hardening and applies it to the network. In this instance, the network consists of those components on each system that support network communications, which includes the NIC, device drivers, and protocols, as well as the network media (cables or wireless) and network devices (such as routers, switches, hubs, and so on).
- Network configuration security
Proper configuration of systems connected to the network directly affects the security of the overall network. A weak system serves as the weak link in an environment. If one system is compromised, it could lead to the compromise of other systems on the network.
- ACLs on a network
Access control lists (ACLs) for networking hardening are similar to those used to manage access to file resources. You can use ACLs to strictly control which users can communication across the network using the various services, applications, protocols, and ports enabled on the network.
- Application hardening
Application hardening is the task of imposing security on required applications and services. This usually involves tuning and configuring the native security features of the installed software and installing supportive security applications as needed. When you're developing new applications in house, it's also important to include security design, implementation, and integration throughout the development process.
- Web server hardening
You can improve web server security through the use of SSL or TLS. Only CGI folders should have execute permissions. Web servers should be patched against buffer overflow attacks. Web resource access can be controlled through file-level ACLs.
- E-mail server hardening
To prevent the transmission of e-mails from nonexistent domains (spoofed source addresses), an e-mail server should perform a reverse DNS lookup on all received messages before transmitting or forwarding them. E-mail should be protected through the use of software and logical security mechanisms as well as an acceptable use policy.
- DNS server hardening
Illegal zone transfers can corrupt the DNS database or give an external entity information about the infrastructure of your private network. Zone transfers should be secured so that they only occur between trusted systems and only authorized users can initiate them.
Firewalls provide security through what mechanism?
Watching for intrusions
Controlling traffic entering and leaving a network
Requiring strong passwords
Preventing misuse of company resources
A switch can be used to prevent broadcast storms between connected systems through the use of what?
SSL
S/MIME
VLANs
LDAP
Which form of cable media that is least vulnerable to eavesdropping?
Fiber optic
STP
Coax
Wireless
Smartcards are useful for storing all but which of the following types of data?
Digital signatures
Digital certificates
Biometric reference profile
System backups
Which of the following allows the deployment of a publicly accessible web server without compromising the security of the private network?
Intranet
DMZ
Extranet
Switch
Which of the following is not one of the IP address ranges reserved for private use by RFC 1918?
10.0.0.0–10.255.255.255
192.168.0.0–192.168.255.255
169.0.0.0–169.255.255.255
172.16.0.0–172.31.255.255
A network-based IDS is not suitable for detecting or protecting against which of the following?
E-mail spoofing
Denial of Service attacks
Attacks against the network
Attacks against an environment that produce significant traffic
What tool is used to lure or retain intruders in order to gather sufficient evidence without compromising the security of the private network?
Firewall
IDS
Router
Honey pot
Which of the following actions in operating system hardening should come earliest in the process?
Enable secure remote administration.
Remove unneeded services and protocols.
Enable logging and auditing.
Connect the system to the network/Internet.
Illegal or unauthorized zone transfers are a significant and direct threat to what type of network server?
Web
DHCP
DNS
Database
B. Firewalls provide protection by controlling traffic entering and leaving a network.
C. Switches can create VLANs. Broadcast storms aren't transmitted between one VLAN and another.
A. Fiber optic cable is nearly invulnerable to eavesdropping.
D. A smartcard has only a small amount of memory; thus it isn't suited to store system backups.
B. A DMZ provides a network segment where publicly accessible servers can be deployed without compromising the security of the private network.
C. The 169.x.y.z range is the Automatic Private IP Addresses (APIPA) range of addresses that are automatically assigned to Windows clients when a DHCP server isn't reachable.
A. Network-based IDSs aren't suitable for protecting against e-mail spoofing.
D. A honey pot is used to lure or retain intruders in order to gather sufficient evidence without compromising the security of the private network.
B. Removing unneeded services and protocols is an operating system hardening step that should come before any of the other three.
C. Illegal or unauthorized zone transfers are a significant and direct threat to DNS servers.