Domain 4 Questions
- Ryan is concerned about integrity attacks against his organization's sales database. Which one of the following SQL commands is least likely to result in an integrity issue?
A. SELECT
B. INSERT
C. UPDATE
d. DELETE
- Which one of the following technologies is not commonly used as part of a single sign-on (SSO) implementation?
A. OAuth
B. IPSec
C. OpenID
D. SAML
- Consider the statistics shown in the following table for a biometric authentication system. What is the system's FRR based upon for this data?

Figure 4.1
A. 1%
B. 2%
C. 8%
D. 16%
- In an authentication system using the mandatory access control (MAC) model, who determines what users may access an object?
A. The user
B. The object owner
C. The system administrator
D. The system
- TJ is designing the authentication system for an online gambling website that is restricted for use by residents of a single US state. What type of access control should TJ implement to ensure that his organization does not run afoul of the law?
A. Role-based access control
B. Multifactor authentication
C. Token-based authentication
D. Location-based access control
- Thelma is configuring a new web server running Apache. Apache requires an account to read the files contained in the /var/www directory. What type of account should Thelma use for this access?
A. Root account
B. Guest account
C. Service account
D. Administrator account
- Helen's organization has a password policy that does not enforce complexity requirements. What is the major disadvantage of this approach?
A. Attackers can use social engineering to extract simple passwords from users.
B. Attackers can easily brute force passwords that are short.
C. Attackers can easily brute force passwords that draw from a limited character set.
D. Attackers may use reverse hashing to decrypt simple passwords.
- Victoria is implementing an authentication system where the user is asked to speak a predefined passcode into a microphone. The system then verifies that the speaker's voice matches their enrollment sample and that the passcode is correct. How many authentication factors are at play in this scenario?
A. Zero
B. One
C. Two
D. Three
- Lila is concerned about the security of a database table that contains Social Security Numbers. The organization needs to maintain this information for tax reporting purposes, but Lila wants to make sure that the database administrators are unable to access this very sensitive field. Which one of the following security controls would best meet Lila's need?
A. Database activity monitoring
B. Field-level hashing
C. Database access controls
D. Field-level encryption
- Which one of the following account types should be assigned the highest priority for account activity logging?
A. Temporary user accounts
B. Guest accounts
C. Service accounts
D. Standard user accounts
- Colleen's company would like to manage administrator credentials by creating them in such a manner that nobody has knowledge of the root password for a system and the password is stored in an electronic vault. What mechanism should Colleen implement to ensure that administrators are not locked out of the system in the event of an access control failure?
A. Emergency access procedure
B. Redundant passwords
C. Give a manager the passwords
D. Multifactor authentication
- Which one of the following assertions can NOT be made by validating the card authentication certificate on a US government PIV card?
A. The holder of the credential is the same individual the card was issued to.
B. The card has not expired.
C. The card has not been revoked.
D. The card was issued by an authorized entity.
- Carla is examining a point-of-sale terminal and sees the prepopulated login screen shown here. What type of account is most likely being used in this scenario?
Figure 4.2
A. Privileged account
B. Shared account
C. Guest account
D. Superuser account
- Wanda is concerned about the likelihood of privilege creep in her organization. Which one of the following activities is likely to uncover the most comprehensive listing of privilege creep situations that can then be remediated?
A. Permission auditing
B. Usage auditing
C. Policy review
D. User termination audit
- Tim is a member of several NTFS groups and is attempting to access a file stored on an NTFS volume. The set of permissions that apply from each of his group memberships are shown here. What is the end result of these permissions when Tim attempts to access the file?

Figure 4.3
A. Tim can't read or write to the file.
B. Tim can read the file but not write to it.
C. Tim can write to the file but not read it.
D. Tim can both read and write the file.
- What network port is used for communications related to the Kerberos authentication process?
A. UDP port 636
B. TCP port 88
C. UDP port 88
D. TCP port 636
- Paula is reviewing her organization's account management life cycle. She is paying particular attention to the timeliness of account management activities and would like to prioritize areas that have the greatest risk. Which one of the following activities should be her highest priority?
A. Access modifications
B. Onboarding
C. Access reviews
D. Offboarding
- Nancy is configuring a user account and is setting the permissions that are shown here. What type of permissions is Nancy setting?
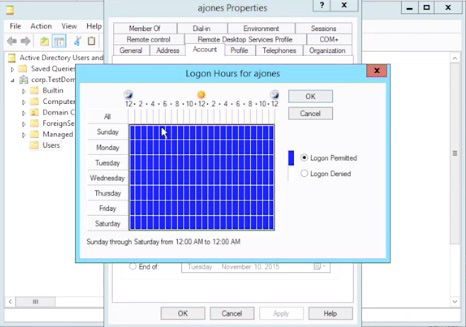
Figure 4.4
A. Location-based restrictions
B. Content-based restrictions
C. Role-based restrictions
D. Time-based restrictions
- When using CHAP authentication, what does the server send to the client in the second step of the handshake?
A. Password
B. Hash
C. Challenge
D. Certificate
- Barry is reviewing the password settings on his Windows domain and discovers that the domain is set to expire passwords every 60 days. Which one of the following actions should Barry take to align his organization with industry best practices?
A. Remove the password expiration period.
B. Extend the password expiration period to 180 days or more.
C. Shorten the password expiration period to 30 days or less.
D. No action is necessary.
- Brian is implementing geofencing as a component of his access control system. What type of control is he implementing?
A. Role-based access control
B. Group-based access control
C. Location-based access control
D. Time-based access control
- Molly's organization has a shared account that they use to provide access to vendors. What is the primary security objective that is sacrificed using this model, assuming that the password is not shared with unauthorized individuals?
A. Integrity
B. Least privilege
C. Confidentiality
D. Accountability
- Review the Google Authenticator screenshot shown here. What protocol is being used to generate passcodes by this software token?

Figure 4.5
A. LOTP
B. HOTP
C. KOTP
D. TOTP
- Which one of the following biometric technologies is most likely to be affected by a person's race?
A. Facial recognition
B. Fingerprint recognition
C. Iris recognition
D. Hand geometry
- When digital certificates are used for the authentication of a user to a server, what is the primary purpose of the digital certificate?
A. To convey a signed copy of the server's public key
B. To convey a signed copy of the user's private key
C. To convey a signed copy of the user's public key
D. To convey a signed copy of the server's private key
- Tina is designing a recovery mechanism for her organization's authentication system and provides each user with a card containing several one-time use passwords for use in the event their smartphone app malfunctions. What type of authentication factor are these one-time passwords?
A. Something you have
B. Something you know
C. Somewhere you are
D. Something you are
- Taylor is accessing a website that would like to access information stored in her Google account. The site makes a request to access that information using the OAuth protocol. In this scenario, who is the OAuth resource owner?
A. Taylor
B. Google
C. Website
D. Both Google and the website
- What is the primary feature that distinguishes a smart card from other types of access card?
A. Presence of a magnetic stripe
B. Presence of an integrated circuit
C. The requirement to enter a PIN or password
D. Compatibility with biometric authentication
- Corey would like to implement a multifactor authentication system for physical access to his data center. He is currently using a fingerprint scanner. Which one of the following would be the best second authentication technique to use in combination with the fingerprint scanner?
A. Voiceprint analysis
B. Security question
C. ID card
D. Retinal scan
- Consider the US government personal identity verification (PIV) card shown here. When the individual presents a card to an appropriate system for verification, what element allows the validator to verify the identity of the PIV user?

Figure 4.6
A. Encryption certificate
B. Card authentication certificate
C. Digital signature certificate
D. PIV authentication certificate
- Barry is troubleshooting authentication problems for his organization's VPN. The VPN uses a RADIUS backend for authentication and Barry would like to monitor this traffic. What ports are associated with RADIUS?
A. UDP ports 1812 and 1813
B. TCP ports 1812 and 1813
C. UDP ports 1433 and 1521
D. TCP ports 1433 and 1521
- Ken would like to configure his organization's password security policy to be in line with current NIST guidelines. What is the minimum password length that Ken should require to be consistent with those guidelines?
A. 6 characters
B. 8 characters
C. 12 characters
D. No minimum
- Which of the following services are supported by the TACACS+ protocol?
A. Authentication, authorization, and accounting
B. Authentication only
C. Authentication and authorization
D. Authentication and accounting
- Which one of the following techniques is the least secure approach to a "something you have" authentication factor?
A. SMS message
B. Physical token
C. Smartphone app
D. Smartcard
- Erin would like to assess the impact of several overlapping Windows GPOs and determine the effective result of those policies. Which tool is best suited for this task?
A. dcpromo
B. gpedit
C. gpresult
D. gpupdate
- Roger uses his fingerprint to unlock his laptop. What authentication factor was used in this example?
A. Biometric authentication
B. Token-based authentication
C. Location-based authentication
D. Knowledge-based authentication
- Which one of the following biometric access control mechanisms generally takes the longest time to recognize a user?
A. Fingerprint scan
B. Iris scan
C. Facial recognition
D. Retinal scan
- Before accessing a wire transfer website, Harry's bank requires that he provide a password, a security PIN, and answer several security questions. How many distinct authentication factors is this system using?
A. 0
B. 1
C. 2
D. 3
- Tim recently set the attribute shown here on a group of Windows user accounts. His organization has the following security requirements:
1. Passwords must be at least 10 characters.
2. Passwords must contain characters from three different character classes.
3. Passwords may not contain the user's account name.
Which of these requirements are met by the setting shown here?

Figure 4.7
A. Requirements 1 and 2
B. Requirements 2 and 3
C. Requirements 1, 2, and 3
D. Requirements 1 and 3
- Carl would like to implement a recertification process for vendors with accounts allowing access to systems in his organization. What access management control can best facilitate this?
A. Password complexity
B. Account expiration
C. Least privilege
D. Job rotation
- Which one of the following protocols is considered secure for use in an authentication system without the use of any compensating controls?
A. PAP
B. MS-CHAP
C. MS-CHAP v2
D. Kerberos
- Which one of the following is a large-scale federated identity management solution that is widely used mainly in academic institutions?
A. Kerberos
B. Shibboleth
C. OAuth
D. OpenID Connect
- Martin is concerned about the misuse of legitimate privileges by employees, otherwise known as the insider threat. Which one of the following activities would best serve as a control against this threat?
A. Privilege auditing
B. Usage auditing
C. Multifactor authentication
D. Credential management
- Lisa is evaluating a set of Group Policy Objects that have been applied to a Windows account. Which one of the following policies will be processed first?
A. Organizational Unit policy
B. Site policy
C. Domain policy
D. Local policy
- Tom is designing a password reset mechanism for his organization and would like to require a personal visit to a help desk. Which one of the following statements is not correct?
A. Users should be permitted to reset passwords in person.
B. Users reporting to the help desk should be asked for proof of identification.
C. Use of a help desk reset approach is burdensome on both users and staff.
D. Users reporting to the help desk should provide an old, expired password if possible.
- Which one of the following is a best practice for the management of privileged accounts on a server?
A. Privileged accounts should be shared between administrators.
B. Administrative users should have both privileged and unprivileged accounts.
C. Privileged accounts should not be protected by passwords.
D. Privileged accounts should be exempted from standard password management practices.
- Frank would like to set his organization's password length requirements to align with industry best practices. What should he set as the maximum password length?
A. 8 characters
B. 16 characters
C. 255 characters
D. No maximum
- Greg is designing authentication controls for a system that is accessed by employees in branch offices. There is no need for mobile or remote users to access the system. What authentication factor could Greg implement to prevent users from accessing the system remotely?
A. Something you have
B. Something you are
C. Somewhere you are
D. Something you know
- Which one of the following is an implementation of a mandatory access control system?
A. SELinux
B. NTFS
C. Google Drive
D. Mac OS X
- Taylor works for an organization that experiences high turnover in employees, particularly at their call center and retail stores. She would like to implement an access control system that minimizes work. Which one of the following actions will best reduce the workload on the access management team while maintaining security?
A. Implement group-based access control
B. Implement a permissive access control model
C. Implement mandatory access control
D. Implement personalized access control for each employee
- In a normal RADIUS authentication session, what is the first message that's sent by the client to the server?
A. Access-Reject
B. Access-Request
C. Access-Challenge
D. Access-Accept
- Tom is deciding whether to implement a standard account naming practice for his organization. Which one of the following statements best reflects the accepted best practices regarding this topic?
A. Organizations should adopt standard naming conventions to make account identification easier.
B. Organizations should not adopt standard naming conventions because it makes account names easy to guess.
C. Organizations should not adopt standard naming conventions because it facilitates social engineering.
D. Organizations should not adopt standard naming conventions because it violates the principle of security through obscurity.
- In a discretionary access control (DAC) system, who is primarily responsible for assigning permissions to access objects for a user?
A. User
B. Object owners
C. System administrator
D. The system itself
- What type of access control is performed by a standard network firewall?
A. Role-based access control
B. Rule-based access control
C. Mandatory access control
D. Attribute-based access control
- Group Policy Objects (GPOs) are components of what access control system?
A. Active Directory
B. Kerberos
C. RADIUS
D. TACACS+
- Tonya is considering the use of a voice recognition system for authentication purposes. She is concerned about the use of recordings to fool the system. What technology can she include in her design to best reduce the risk of this type of attack?
A. Passcode
B. Hashing
C. Encryption
D. Challenge/response
- Helen recently moved from the marketing department to the sales department and retained the permissions that were assigned to her previous job, despite the fact that they are no longer necessary. What security principle does this violate?
A. Security through obscurity
B. Separation of duties
C. Two-person control
D. Least privilege
- Brenda is assisting a user who is traveling on business and is unable to access a critical system. Brenda is able to access the system herself and the user was able to access it last week from the office. The user is connected to the VPN and is still having the same issue. What type of access restriction is most likely in place?
A. Role-based restriction
B. Time-based restriction
C. Location-based restriction
D. Content-based restriction
- This diagram shows the results of testing the accuracy of a biometric authentication system. What characteristic is designated by the arrow?
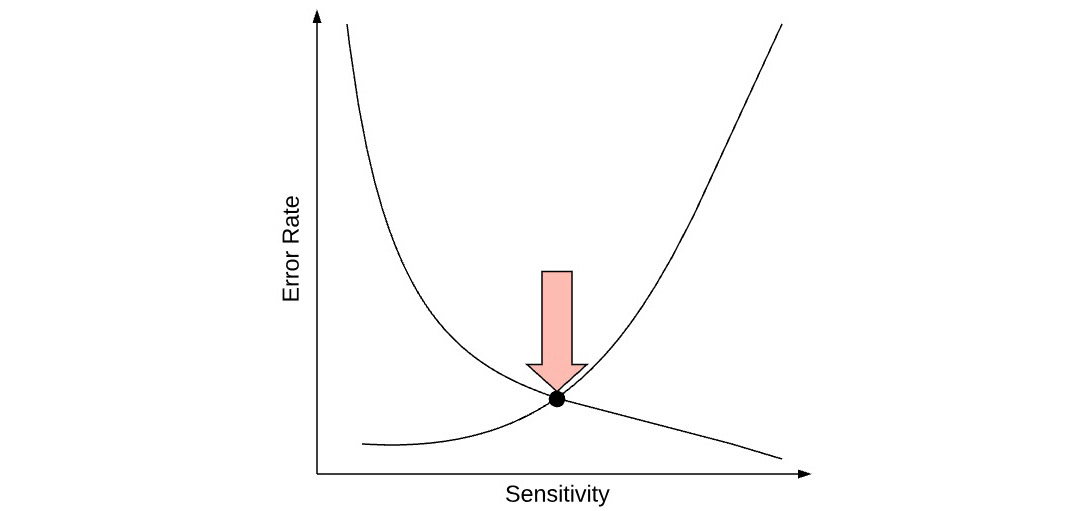
Figure 4.8
A. FAR
B. CER
C. FRR
D. IRR
- When using an attribute-based access control (ABAC) model, what attributes are available to the authorization system for analysis?
A. User and system attributes only
B. User attributes, system attributes, and environmental attributes
C. User attributes only
D. System attributes only
- Which one of the following principles describes the basic concept of access control that should be enforced by every network firewall?
A. Explicit deny
B. Implicit deny
C. Implicit allow
D. Explicit allow
- In a Kerberos authentication scheme, the client sends an authenticator to the ticket-granting server (TGS) when requesting a service ticket. How does the client encrypt this authenticator?
A. The client encrypts the authenticator with the client's private key.
B. The client encrypts the authenticator with the TGS public key.
C. The client encrypts the authenticator with the TGS session key.
D. The client does not encrypt the authenticator.
- In a network using 802.1x authentication, which device normally contains the 802.1x supplicant?
A. Authenticator
B. End-user system
C. Authentication server
D. Service server
- When you enter a password into a system, what activity are you engaged in?
A. Authentication
B. Identification
C. Authorization
D. Accounting
- Randi is configuring authentication for a SQL Server database and would like to ensure that user accounts are disabled when they leave the organization. Which one of the following approaches would best meet her requirement?
A. Windows authentication
B. SQL server authentication
C. Mixed mode authentication
D. No authentication
- Brent is the CISO for Sorin Sprockets, a manufacturer of industrial products. He is designing a federated authentication system where users from Domer Industries, one of his organization's suppliers, will use their accounts to access systems in the Sorin Sprockets domain. Which one of the following statements is correct about this relationship?
A. There must be a transitive trust relationship between Domer Industries and Sorin Sprockets.
B. Domer Industries must have a trust relationship with Sorin Sprockets.
C. There must be a two-way trust relationship between Domer Industries and Sorin Sprockets.
D. Sorin Sprockets must have a trust relationship with Domer Industries.
- Which one of the following authentication protocols is an appropriate protocol for performing administrator authentication on network devices?
A. STACACS
B. XTACACS
C. TACACS
D. TACACS+
- Ryan attempts to log in to AcmeSocial, a social networking website. The website allows him to log in with his HMail account through the use of SAML authentication. In this scenario, who is the SAML principal?
A. Both HMail and Acme Social
B. AcmeSocial
C. HMail
D. Ryan
- During what stage of the account management life cycle should a user receive their first exposure to security awareness training?
A. Onboarding
B. Deprovisioning
C. Renewal
D. Privilege assignment
- What protocol is normally used for communication between an authenticator and authentication server on a network using 802.1x authentication?
A. XTACACS
B. TACACS
C. RADIUS
D. TACACS+
- Thomas is configuring the security for a specialized computing system that will be used in a high-security environment. This system will assign tags to each file based upon their classification and users will only be able to access information that matches their security clearance. What type of security model is Thomas implementing?
A. ABAC
B. DAC
C. MAC
D. RBAC
- Which one of the following statements about iris recognition technology is incorrect?
A. Iris recognition technology has a very low false acceptance rate.
B. Iris patterns may be recognized from a distance.
C. Iris patterns change gradually during a person's lifetime.
D. Iris recognition scanners can be fooled by an image of a face.
- Carrie approaches the door to a physical facility and places her finger on a scanner. When she does so, the scanner displays the message "OK" and the door unlocks. Which one of the following steps has not occurred?
A. Authentication
B. Authorization
C. Identification
D. Two-factor authentication
- Yolanda is concerned about brute force attacks against her Windows system. Which one of the following controls is a good security practice that reduces the likelihood of a successful brute force attack?
A. Expire the Administrator account password monthly.
B. Rename the Administrator account.
C. Disable the Administrator account.
D. Encrypt the contents of the Administrator account.
- Which one of the following is a reasonable approach to handling failed authentication attempts against a password-based authentication system?
A. Disabling a user account after three incorrect attempts.
B. Require an exponentially increasing timeout period between login attempts.
C. Lock a user account after five incorrect login attempts.
D. Require 5 seconds between login attempts.
- Riley is securing an application that uses PAP authentication. Which one of the following statements is correct about PAP?
A. PAP can't perform reliable, repeatable authentication.
B. PAP does not encrypt credentials and is insecure.
C. PAP implementations are only possible on Token Ring networks.
D. PAP is widely used for VPN authentication.
- Which one of the following is an example of biometric authentication control?
A. Password
B. Fingerprint scan
C. Smart card
D. Keyfob token
- Gavin is managing the access control system for his organization. Users often change jobs and he would like to select an approach that will make it easy to reassign permissions when users move around the organization. Which access control model is best suited for his needs?
A. MAC
B. ABAC
C. DAC
D. RBAC
- After a user enters an incorrect password, many authentication systems record this activity in an authentication log. What phase of the identity and access management process is taking place?
A. Identification
B. Authentication
C. Accounting
D. Authorization
- Kip is preparing to conduct a privilege usage audit of his organization's database servers. Which one of the following data sources would be least helpful to him in this exercise?
A. Organization chart
B. Database access logs
C. Network firewall logs
D. Asset classification information
- Ron is designing a user awareness program intended to improve password security practices. Of the practices listed here, which poses the greatest risk to organizations?
A. Use of passwords that are more than a year old
B. Use of passwords less than 12 characters long
C. Use of passwords that do not contain special characters
D. Reuse of passwords on multiple sites
- Randy is building a multifactor authentication system that requires users to enter a passcode and then verifies that their face matches a photo stored in the system. What two factors is this system using?
A. Something you know and something you have
B. Something you have and something you know
C. Something you have and something you are
D. Something you know and something you are
- When creating a web application based upon the OAuth 2.0 standard, what authentication protocol is often the simplest choice?
A. Digital certificates
B. RADIUS
C. Kerberos
D. OpenID Connect
- Which one of the following authentication factors is the most difficult to practically implement?
A. Something you are
B. Something you do
C. Something you have
D. Something you know
- Val would like to configure her organization's password security policy to comply with industry best practices. How many passwords should she keep in a password history to prevent password reuse?
A. 0
B. 1
C. 5
D. 8
- Which one of the following devices is most likely to serve as an authenticator in an 802.1x network authentication scenario?
A. Laptop with a wireless connection
B. Desktop with a wired connection
C. Wireless access point
D. RADIUS server
- What type of security card is shown here?

Figure 4.9
A. Proximity card
B. Smart card
C. Magnetic stripe card
D. Common access card (CAC)
- Consider the statistics shown here for a biometric authentication system. What is the system's FAR based upon for this data?
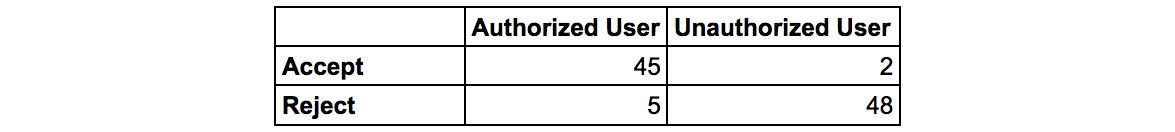
Figure 4.10
A. 2%
B. 4%
C. 5%
D. 10%
- Consider the OpenLDAP password hashes shown here. Which user has the most secure password storage mechanism?
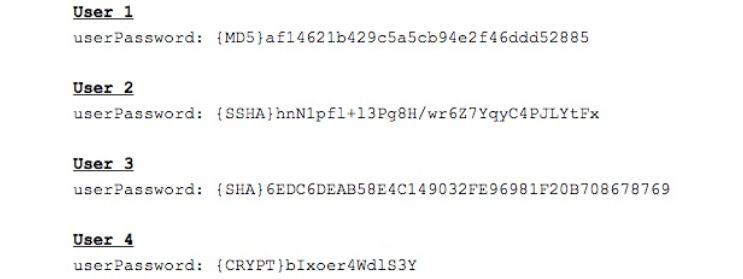
Figure 4.11
A. User 1
B. User 2
C. User 3
D. User 4
- Beth used the sign in with Facebook feature to access a website hosted by The Washington Post. This feature uses SAML-based authentication. In this scenario, what is the role that's being played by The Washington Post?
A. Identity provider
B. User agent
C. Service provider
D. Certificate authority
- In Kerberos authentication, which one of the following components is responsible for verifying that a user's password (or other credentials) is valid and correct?
A. Client
B. AS
C. Service
D. TGS
- Gina is configuring an access control system for a college that will examine a user's identity profile when determining whether to grant access to resources. Students will be granted access to limited files, while faculty and staff will have broader access. Faculty and staff access may be further segmented based upon their department, title, and other identity attributes. What type of access control system is Gina designing?
A. ABAC
B. DAC
C. MAC
D. SLAC
- Consider the transitive trust relationships shown here. Ben has a user account in Domain D. Which domains can Ben use his account in so that he can access resources?

Figure 4.12
A. Domains A, B, C, and D
B. Domain D only
C. Domains A, B, and D only
D. Domains A and B only
- When creating a role-based access control system, what mechanism can best be used to assign permissions to individuals in the same job role?
A. Policy templates
B. Group policy
C. Standard procedures
D. Administrator training
- Jane is seeking to enforce role-based access restrictions in her organization. Which one of the following technologies would allow her to enforce these restrictions across a variety of systems?
A. Oracle database permissions
B. NTFS access control lists
C. Cisco access controls lists
D. Active Directory group policy
- John approaches a security guard and hands her the smart card shown here. The guard conducts a physical inspection of the card and pulls up an image of it on her system to verify that it is authentic. How many authentication factors has John successfully completed at this point?

Figure 4.13
A. Zero
B. One
C. Two
D. Three
- Which one of the following is not an example of a privileged account on a server?
A. Shared account
B. Root account
C. Service account
D. Administrator account
- Paul is designing a system that will allow users from Acme Corporation, one of his organization's vendors, to access Paul's accounts payable system using the accounts provided by Acme Corporation. What type of authentication system is Paul attempting to design?
A. Single sign-on
B. Transitive trust
C. Federated authentication
D. Multifactor authentication
- Which one of the following attacks is a critical threat that applies specifically to NTLM authentication?
A. Rainbow table
B. Brute force
C. Pass-the-hash
D. Man-in-the-middle
Domain 4 Answers and Explanations
- A. The INSERT, UPDATE, and DELETE commands all have the ability to modify information in a database, potentially resulting in an integrity violation. The SELECT command is used to retrieve, but not modify, information, so it is unlikely to result in an integrity issue. The use of the SELECT command is more likely to result in a confidentiality issue.
- B. OAuth is commonly used to provide API-based SSO for web applications. OpenID is used for consumer-grade SSO implementations, while SAML is used for enterprise-grade SSO implementations. IPSec is a network security protocol used for VPN connections, among other purposes, but is not associated with SSO implementations.
- A. The false rejection rate (FRR) of a system is calculated by dividing the number of false rejections by the total number of authentication attempts. In this dataset, there are 200 total authentication attempts, of which two were false rejections of an authorized user. Therefore, the false acceptance rate is 1%.
- D. In a mandatory access control (MAC) model, the system determines access authorization based upon the security labels applied to objects.
- D. All of the options presented here are good security practices, and TJ should consider each of them. However, only location-based access control will help prevent TJ's organization from running afoul of the law restricting access to residents of a single state.
- C. Service accounts are used to provide applications with access to resources necessary for the provision of their services. This example clearly calls for a service account. Guest accounts should never be used on a server, barring extenuating circumstances. The web server service should not run with unrestricted root/administrator access.
- C. The major issue with simple passwords is that they are far easier to break in a brute force attack than complex passwords that draw from multiple character classes. Complexity requirements do not affect the minimum length of a password or make passwords less susceptible to social engineering. Reverse hashing is not possible for any password as secure hash functions are not reversible.
- C. This does qualify as multifactor authentication because it is based upon a passcode known only to the user (something you know) and the user's voice (something you are). However, it is not an ideal solution because an attacker could record the user speaking the passcode and replay it to gain access to the system.
- D. Lila should encrypt the Social Security Number field using an encryption key that is not known to the database administrators. Hashing is not a good solution because it would not be possible to reverse the hash and retrieve the SSN for tax reporting purposes. Database access controls would not be effective against a database administrator, who likely has the privileges necessary to bypass those controls. Database activity monitoring might detect unauthorized access but cannot prevent it.
- C. Service accounts are an example of privileged accounts and should be subject to strict logging requirements. Activity from other account types may certainly be logged, but this is not as high a priority as it is for privileged accounts.
- A. Colleen should implement an emergency access procedure to allow access to the passwords. A common way to do this is to require the concurrence of two authorized individuals to retrieve the password from the vault. Providing a manager with the passwords would defeat the design requirement of nobody having knowledge of the password. Multifactor authentication would still require knowledge of the password. Redundant passwords are not a security mechanism.
- A. PIVs contain four digital certificates. The card authentication certificate is used to verify that the PIV credential was issued by an authorized entity, has not expired, and has not been revoked. The PIV authentication certificate is used to verify that the PIV credential was issued by an authorized entity, has not expired, has not been revoked, and that the holder of the credential (YOU) is the same individual it was issued to. The digital signature certificate allows the user to digitally sign a document or email, providing both integrity and non-repudiation. The encryption certificate allows the user to digitally encrypt documents or email.
- B. An account with a generic role-based name, such as cashier, is likely shared among many users. There is no reason to believe that this is a privileged administrator or superuser account. There is also no reason to believe that non-employee guests have access to this account.
- A. Privilege creep occurs when an employee retains permissions from prior jobs after shifting roles within an organization. User termination audits are more likely to turn up examples of accounts that were not deprovisioned than privilege creep. Usage auditing may discover some examples of privilege creep but is designed to uncover privilege misuse. Policy reviews will not discover examples of privilege creep. Permission auditing is the most comprehensive way to discover unnecessary privileges that have been assigned to user accounts.
- B. In NTFS permissions, explicit permissions always take precedence over inherited permissions and deny permissions take precedence over allow permissions. Therefore, in this case, the explicit deny from the manager's group blocks Tim from writing to the file, regardless of any other permissions. Then, the explicit permission assigned to Tim's account to read the file takes precedence over the inherited deny read permission on the accounting group.
- C. Kerberos uses UDP port 88 for authentication-related communications. Port 636 is associated with the secure LDAP (LDAPS) protocol.
- D. The offboarding process is the area of greatest risk to the organization because failure to execute deprovisioning activities in a prompt manner may mean that employees who have left the organization retain access to sensitive information or systems.
- D. In this image, Nancy is setting logon hour restrictions for the ajones account. This is an example of a restriction based upon the time of day.
- C. In the Challenge Handshake Authentication Protocol (CHAP), the client makes an authentication request and the server responds with a challenge message. The client must then combine its password with the challenge message and hash it, providing this hashed response to the server.
- A. The National Institute for Standards and Technology (NIST) issued guidelines for digital identity in 2017 that state that organizations should not set password expiration dates under normal circumstances. Organizations should only require password changes if there are signs of a potential compromise.
- C. Geofencing places specific geographic constraints around access to a system or resource. Therefore, this is an example of location-based access control.
- D. If the password remains known only to authorized individuals, this does not violate the principles of confidentiality or integrity. There is no indication from the scenario that the account has excess privileges, so least privilege is not violated. However, the use of a shared account prevents security staff from determining which individual performed an action, violating the principle of accountability.
- D. The two main technologies that are used to generate one-time passwords are the HMAC-Based One Time Password (HOTP) algorithm and the Time-Based One Time Password (TOTP) algorithm. HOTP passcodes are generated sequentially and do not expire until used. TOTP passcodes are based upon the time of authentication and expire frequently. Google Authenticator uses TOTP expiring passcodes, as shown by the pie chart icons to the right of each code.
- A. Academic studies have demonstrated that the accuracy of facial recognition technology may be significantly affected by a person's race. Ethnicity is less likely to impact other biometric techniques, such as fingerprint recognition, iris recognition, and hand geometry analysis.
- C. When a user presents a digital certificate for authentication purposes, the primary purpose of that certificate is to provide a signed copy of the user's public key.
- A. This is a difficult question, as it is likely that many people will automatically assume that this is a knowledge-based factor because it involves passwords. However, since those passwords are provided on a card, this approach is considered a possession-based approach (something you have). For a reference on this, see page 15 of NIST SP800-63b.
- A. In this scenario, the website would like to access information in Taylor's Google account. This makes Taylor, as the account owner, the resource owner. Google, the service that maintains the account, is the resource provider, and the third-party website is the application.
- B. Smart cards contain an integrated circuit that interactively authenticates with the reader. They do not necessarily contain a magnetic stripe. There is no requirement that a smart card be combined with a PIN/passcode or biometric authentication, although this is often done to achieve multifactor authentication.
- C. Retinal scans and voiceprint analysis are both examples of biometric controls and, when used in combination with a fingerprint scan, would not constitute multifactor authentication. Security questions are a knowledge-based factor but would be difficult to implement for physical access and are generally not a very secure authentication technique due to the ease of a third party discovering correct answers in many cases. ID cards are a "something you have" factor and would be an ideal pairing for the fingerprint scan.
- D. PIVs contain four digital certificates. The card authentication certificate is used to verify that the PIV credential was issued by an authorized entity, has not expired, and has not been revoked. The PIV authentication certificate is used to verify that the PIV credential was issued by an authorized entity, has not expired, has not been revoked, and holder of the credential (YOU) is the same individual it was issued to. The digital signature certificate allows the user to digitally sign a document or email, providing both integrity and non-repudiation. The encryption certificate allows the user to digitally encrypt documents or emails.
- A. RADIUS uses UDP port 1812 for authentication and UDP port 1813 for accounting services. TCP ports 1433 and 1521 are associated with Microsoft SQL Server and Oracle databases, respectively.
- B. NIST's digital identity security guidelines suggest that organizations set a minimum password length of 8 characters for passwords that are memorized by the user (NIST SP 800-63B).
- A. TACACS+ is a AAA protocol. Therefore, it supports authentication, authorization, and accounting services.
- A. SMS-based approaches to authentication are vulnerable to attacks where the attacker hijacks the telephone number associated with an individual and then uses that hijacked number to receive an authentication message. The other techniques listed here are all considered secure.
- C. The gpresult command computes and displays Resultant Set of Policy (RSoP) information for a remote user and computer. This allows administrators to determine the end result of a set of policies that have been applied to a user account.
- A. This use of a fingerprint scan is an example of a measurement of Roger's physical body, or "something you are" authentication. Therefore, it is an example of a biometric authentication technique.
- D. Retinal scans are generally perceived as the slowest and most intrusive biometric technique because they require the individual to make physical contact with an eye scanner. Iris scanning and facial recognition can typically be accomplished from a distance. Fingerprint scanning does require physical contact with the scanner but is generally faster than retinal scanning.
- B. All of the authentication techniques described in this scenario are knowledge-based authentication techniques. Therefore, the only factor being used in this scenario is "something you know."
- B. The passwords must meet complexity requirements settings, which establishes a policy that user passwords must contain characters from three different character classes and that the password may not contain the user's account name or display name. It does not enforce a minimum password length.
- B. Recertification requires that a user's access be renewed periodically to ensure that a business need still exists. The best way that Carl can enforce this is to implement account expiration controls on the vendor accounts and require that the account sponsor recertify the need on a periodic basis to extend the expiration date. Accounts that are not recertified will then be automatically disabled.
- D. Kerberos is a widely used authentication system that is considered secure by modern standards. The Password Authentication Protocol (PAP) is an insecure protocol that does not encrypt passwords as they are transmitted over the network. The Microsoft Challenge Handshake Authentication Protocol (MS-CHAP) and MS-CHAP v2 both have known security vulnerabilities that make them unacceptable for standalone use today.
- B. Shibboleth is an open source federated identity management solution that is most commonly used in academic institutions. OAuth and OpenID Connect are broadly used solutions for web-based authentication. Kerberos is mainly used as an internal authentication solution.
- B. Martin is concerned about the misuse of legitimately assigned privileges. Credential management and privilege auditing activities would turn up improperly assigned privileges but would not identify the misuse of legitimate privileges. The use of auditing, however, analyzes the actual use of privileges and would detect insider misuse.
- D. Group Policy Objects are processed in the following order: local policies are processed first, followed by site GPOs, domain GPOs, and Organizational Unit (OU) GPOs.
- D. The use of a help desk password reset process is burdensome on staff and users but does provide security if users are asked to prove their identity with documentation. Users should never be asked to provide a current or expired password, as this promotes poor password security practices.
- B. It is a standard practice for administrative users to have both privileged and non-privileged accounts. They may use the non-privileged account for routine activities and only use the privileged account when necessary. There is no reason that privileged accounts should not be protected by passwords. They should not be shared by multiple users or exempt from password management policies.
- D. The best source for guidance on passwords and other authentication techniques is NIST Special Publication 800-63B: Digital Identity Guidelines. In the most recent revision of this document, NIST states that users should not be subjected to a maximum password length requirement and should be allowed to choose passwords as lengthy as they would like.
- C. While these are all valid authentication factors, the only one that would implement Greg's location-based requirement is "somewhere you are" authentication, which takes the user's physical location into account. These factors may be used to implement context-based authentication that either blocks user access or requires additional authentication measures based upon location.
- A. Most modern filesystems, including the Windows NTFS, Mac OS X, and cloud services such as Google Drive, allow the owner of objects to set the access permissions for those objects. These are examples of discretionary access control (DAC). Security-enhanced Linux (SELinux) allows the system owner to set authorization based upon security labels. This is an example of mandatory access control.
- A. The most effective way to implement access controls in this situation is to use group-based access control. This way, every new user is simply added to the appropriate group and then receives the necessary permissions. Permissive access control would violate the security principle of least privilege. Mandatory and personalized access control approaches would increase the burden on staff, rather than reduce it.
- B. The RADIUS Access-Request message is sent by a client to the server requesting RADIUS authentication. The server then normally responds with an Access-Accept or Access-Reject message, depending on whether the authentication was successful or unsuccessful. When a system is using two-factor authentication, the RADIUS server may respond to the client's request with an Access-Challenge message asking for additional authentication.
- A. Security professionals generally agree that the transparency benefits of standard naming conventions outweighs any risks associated with the practice by making it easier to identify users. It is true that naming conventions might make it easier to guess usernames or conduct social engineering, but these risks are generally minimal compared to the benefits of easy user identification.
- B. In a discretionary access control (DAC) system, the owners of individual objects are delegated the authority to grant other users access to those objects. This is the primary means of managing authorization on most modern systems.
- B. Rule-based access control uses a standard set of rules to determine what access is authorized. This is the access control mechanism that's enforced by a firewall, which consults a rule base each time a network connection request is received.
- A. Active Directory uses Group Policy Objects to assign permissions and policy controls to groups of user accounts and systems.
- D. Hashing and encryption are not practical for an interactive system because the human who's speaking cannot perform these operations. The use of a passcode does not protect against this attack if someone is able to record the person saying the passcode. Challenge/response systems prompt the user to answer a simple, randomly generated question, similar to a CAPTCHA. They increase the difficulty of a replay attack.
- D. There is no evidence presented that this violates any separation of duties or two-person control requirements. Security through obscurity is the idea that the details of security controls should be kept secret, which is not an issue in this scenario. The fact that Helen is retaining privileges from a prior position violates the principle of least privilege.
- C. The only factor that changed is the user's location, making a location-based restriction the most likely culprit. This type of restriction can apply even when a user connects to a VPN. We know that it is not a content-based restriction or role-based restriction because the user was able to access the same system when in the office. We can also surmise that it is not likely a time-based restriction because Brenda is able to access the system at the same time.
- B. The accuracy of a biometric authentication system is described using three metrics. The false acceptance rate (FAR) is the frequency at which the system admits a person who should not be admitted. The false rejection rate (FRR) is the frequency at which the system denies access to an authorized user incorrectly. The FAR can be improved by increasing the sensitivity of the system, while the FRR can be improved by decreasing the sensitivity of the system. Because of this, the best measure of accuracy is the crossover error rate (CER), which is the sensitivity point at which FAR and FRR are equal.
- B. When making attribute-based authorization decisions, the ABAC system may analyze user attributes (such as job position or group membership), system attributes (such as the sensitivity level of information processed), and environmental attributes (such as the date or time).
- B. The implicit deny principle is the cornerstone of firewall access control. This principle states that any activity that is not explicitly authorized should be blocked. Explicit allow does describe the way that access is granted, but this is only effective if the firewall uses the implicit deny principle as its foundation.
- C. When a Kerberos client requests a session key, the client creates an authenticator consisting of the client's ID and a timestamp. The client then encrypts this authenticator with the TGS session key, which the client obtained earlier from the authentication server.
- B. In 802.1x authentication, the end user's system contains a component called the supplicant, which initiates the authentication process. The supplicant connects to the authenticator, normally a network switch or wireless access point, that then reaches out to an authentication server to confirm the user's identity. The communication between the authenticator and authentication server normally takes place using the RADIUS and EAP protocols.
- A. Identification occurs when a user makes a claim of identity. This claim is then proven during the authentication phase, through the use of one or more authentication factors, such as a password, smart card, or biometric reading. The system then determines the specific activities that the authenticated user is authorized to engage in by consulting access control lists (ACLs) and other mechanisms and then tracks user access in an accounting system.
- A. Using the Windows authentication mode ties database accounts to domain user accounts and provides the greatest level of assurance that user accounts will be promptly disabled. Both SQL Server authentication and mixed mode authentication allow the use of local accounts that may not be promptly disabled.
- D. Brent is creating a federated authentication system. For this system to function properly, the domain that contains resources (Sorin Sprockets) must have a trust relationship with the domain that contains the user accounts (Domer Industries). While there may also be a trust relationship in the reverse direction (which would create a two-way trust), this is not required for the federation described in the scenario. There are only two domains described here, so there is no need for transitive trust relationships, which would involve three or more domains.
- D. The TACACS+ protocol is an authentication protocol developed by Cisco for use with network devices. It replaced the older TACACS and XTACACS protocols, which should no longer be used. STACACS is not a protocol.
- D. In SAML authentication, the user requesting authentication (Ryan) is the principal. The organization providing the request service (AcmeSocial) is the service provider and the organization providing the login account (HMail) is the identity provider.
- A. Security awareness training should begin at the earliest possible stage of the account management life cycle. Onboarding is this earliest step and should be the first opportunity for security awareness training.
- C. In 802.1x authentication, the end user's system contains a component called the supplicant that initiates the authentication process. The supplicant connects to the authenticator, normally a network switch or wireless access point, that then reaches out to an authentication server to confirm the user's identity. The communication between the authenticator and authentication server normally takes place using the RADIUS and EAP protocols.
- C. In a mandatory access control (MAC) system, such as the one that Thomas is implementing, the system itself sets authorizations based upon object labels. In a discretionary access control (DAC) system, file owners set authorizations for other users. In an attribute-based access control (ABAC) system, authorization is set based upon user attributes. In a role-based access control system (RBAC), authorization is based upon the role of a user in the organization.
- C. Iris recognition technology is a widely used biometric authentication technique because it is nonintrusive and has a low false positive rate. Iris patterns remain stable throughout a person's life and may be scanned from a distance. One disadvantage of this technology is that scanners may be fooled by an image of a person's face.
- D. When Carrie places her finger on the scanner, she is using this as both an identification and authentication technique. The fact that the door opens means that authentication was successful and Carrie was authorized to access the facility. Carrie did not provide a PIN, ID card, or other authentication technique, so this is only single-factor authentication.
- B. Yolanda should rename the Administrator account to prevent brute force attempts to guess the password for that account. Expiring the password would limit the effective length of a successful attack but would not prevent an attack from succeeding. Disabling the Administrator account would prevent legitimate administrative access to the system. Encrypting the contents of the account would not prevent someone from accessing the account.
- B. Best practices in authentication security dictate that user accounts should be subject to an exponentially increasing login delay after failed login attempts. This greatly reduces the effectiveness of brute force password guessing attacks. Locking out or disabling user accounts after a small number of incorrect logins is likely to cause false positive alerts when users accidentally lock themselves out. This approach also facilitates denial of service attacks where an attacker can easily trigger the lockout mechanism, denying users access to their accounts.
- B. The Password Authentication Protocol (PAP) is a legacy protocol that was commonly used for authentication many years ago but is no longer used today because it does not use encryption to protect passwords in transit. There are no issues with PAP's reliability or use on Ethernet networks, but is it not widely used for any purpose today.
- B. A fingerprint scan is a measurement of an individual's physical characteristics and, therefore, is a biometric security control. Passwords are an example of something you know. Smart cards and keyfobs are examples of something you have.
- D. This situation calls for role-based access control, where authorizations are assigned based upon a user's role in the organization. This approach would allow Gavin to simply change a user's role when they switch jobs and then the permissions would automatically update based upon the user's new role.
- C. Logging is an example of an accounting mechanism, creating an unalterable record of authentication activity. The user already completed the identification and authentication phases and authentication was unsuccessful, so no authorization takes place.
- C. During a privilege usage review, Kip will determine whether any employees misused legitimately assigned privileges. To do this, he would need access logs that detail privilege usage. It would also be helpful for him to have access to an organizational chart to determine employee job roles and asset classification information to identify sensitive assets. Firewall logs aren't likely to be helpful in this situation because he is looking for insider misuse, which would appear to be legitimate activity from a network perspective.
- D. One of the greatest risks to password security occurs when users reuse passwords across multiple sites. If an attacker compromises a third-party site, they may attempt to reuse those passwords on other sites. NIST password security guidelines recommend a minimum password length of 8 characters, so a 12-character password does not pose excessive risk. Those guidelines also call for using non-expiring passwords and not requiring enhanced complexity requirements, such as the use of special characters. These practices reduce the likelihood that users will remember their passwords.
- D. Facial recognition technology is an example of a biometric authentication technique, or "something you are." A passcode is an example of a knowledge-based authentication technique, or "something you know."
- D. OpenID Connect is an authentication protocol built directly on top of the OAuth 2.0 framework, making it the simplest choice for user authentication.
- B. The most commonly used authentication factors are something you know (such as a password), something you have (such as an authentication token or smartcard), and something you are (such as a fingerprint). Behavioral factors, known as something you do, are more difficult to measure and implement effectively.
- A. Current guidance from the National Institute for Standards and Technology suggests that user passwords should not expire as a matter of best practice. Therefore, users should also not be prohibited from reusing prior passwords, unless those passwords are known to be compromised.
- C. In 802.1x authentication, the end user's system contains a component called the supplicant, which initiates the authentication process. The supplicant connects to the authenticator, normally a network switch or wireless access point, that then reaches out to an authentication server to confirm the user's identity. The communication between the authenticator and authentication server normally takes place using the RADIUS and EAP protocols.
- A. This is an example of a proximity card. It lacks the magnetic strip that would be found on a magnetic swipe card or the integrated circuit that would be found on a smart card or CAC.
- A. The false acceptance rate (FAR) of a system is calculated by dividing the number of false acceptances by the total number of authentication attempts. In this dataset, there are 100 total authentication attempts, of which two were false acceptances of an unauthorized user. Therefore, the false acceptance rate is 2%.
- B. User 2's password is stored using the salted SHA algorithm, which is resistant to both brute-force and dictionary attacks. The unsalted MD5 and SHA algorithms are vulnerable to dictionary attacks. The MD5 and CRYPT algorithms are vulnerable to brute force attacks.
- C. In SAML authentication, the user agent is the web browser, application, or other technology being used by the end user. The service provider is the service that the user would like to access. The identity provider is the organization providing the authentication mechanism. The certificate authority issues digital certificates required to secure the connections.
- B. In Kerberos authentication, the authentication server (AS) is responsible for validating user credentials. The ticket granting server (TGS) issues authentication tickets to clients after the authentication server completes this validation. The client then provides authentication tickets to the service as proof of identity, rather than providing the service with authentication credentials directly.
- A. There is not enough information provided to determine whether this system uses mandatory access control (MAC) where permissions are set only by the system or discretionary access control (DAC), where permissions are set by resource owners. We can determine based upon the analysis of the user's identity that this system is using attribute-based access control (ABAC). SLAC is not an access control model.
- A. Ben can access resources in Domain D because his account is located there. He can also access resources in Domain A and Domain B because those domains have direct trust relationships with Domain D. Domain C has a transitive trust relationship with Domain A, which trusts Domain D. Ben can follow this transitive trust relationship and use his account to access resources in Domain C as well.
- B. While all of these techniques may be used to assign user permissions, the best way to achieve this goal is to use a group policy to assign permissions to role-based groups and then add users to the appropriate group(s) for their role.
- D. All of these technologies enable the enforcement of access controls, but most are limited to a specific domain, such as Windows filesystems, Oracle databases, or network access. Active Directory group policies, on the other hand, may apply across a wide variety of Windows-based systems and applications.
- C. While John and the guard are not using the smart capabilities of this card, they have still achieved multifactor authentication. John has presented a physical token (the card) and has also passed a biometric screening when the guard performed facial recognition by comparing him to the photo in her database.
- A. Administrative (or root) accounts are clear examples of privileged accounts due to their superuser privileges. Service accounts also have elevated privilege levels. Shared accounts do not normally have privileged access and should not be used on secured servers.
- C. This type of authentication, where one domain trusts users from another domain, is called federation. Federation may involve transitive trusts, where the trusts may be followed through a series of domains, but this scenario only describes the use of two domains. This scenario only describes use of credentials for a single system and does not describe a multiple-system scenario where single sign-on would be relevant. No requirement is described for the use of multifactor authentication, which would require the use of two or more diverse authentication techniques.
- C. All of these attacks are authentication attacks. Brute force and rainbow table attacks are generic attacks that may be used against any authentication system that stores hashed passwords. Man-in-the-middle attacks are generally used against web applications. Pass-the-hash attacks are specifically effective against NTLM authentication.
