Chapter 5. Asset Management
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
![]() Assign information ownership responsibilities.
Assign information ownership responsibilities.
![]() Develop and use information classification guidelines.
Develop and use information classification guidelines.
![]() Understand information handling and labeling procedures.
Understand information handling and labeling procedures.
![]() Identify and inventory information systems.
Identify and inventory information systems.
![]() Create and implement asset classification policies.
Create and implement asset classification policies.
Is it possible to protect something if we do not know how much it is worth and how sensitive it is? Until we classify the information, how do we know the level of protection required? Unless we determine the value to the organization, how can we decide the amount of time, effort, or money that we should spend securing the asset? Who is responsible for making these decisions? How do we communicate the value of our information assets to our employees, business partners, and vendors?
Identification and classification of information assets and systems is essential to the proper selection of security controls to protect against loss of confidentiality, integrity, and availability (CIA):
![]() A loss of confidentiality is the unauthorized disclosure of information.
A loss of confidentiality is the unauthorized disclosure of information.
![]() A loss of integrity is the unauthorized or unintentional modification or destruction of information.
A loss of integrity is the unauthorized or unintentional modification or destruction of information.
![]() A loss of availability is the accidental or intentional disruption of access to or use of information or an information system.
A loss of availability is the accidental or intentional disruption of access to or use of information or an information system.
In this chapter, we will be looking at the various methods and rating methodologies that organizations use to define, inventory, and classify information and information systems. We will examine public and private sector classification systems that are used to communicate value and handling instructions. We will determine who is responsible for these activities. Lastly, we will put these best practices into policy.
Information Assets and Systems
What exactly is an information asset and why protect it? An information asset is a definable piece of information, stored in any manner, that is recognized as having value to the organization. Information assets include raw, mined, developed, and purchased data. If the information is damaged, compromised, or stolen, the consequences could include embarrassment, legal liability, financial ruin, and even loss of life.
Examples of organizational information include the following:
![]() Data stores or warehouses of information about customers, personnel, production, sales, marketing, or finances.
Data stores or warehouses of information about customers, personnel, production, sales, marketing, or finances.
![]() Intellectual property (IP) such as drawings, schematics, patents, music scores, or other publications that have commercial value.
Intellectual property (IP) such as drawings, schematics, patents, music scores, or other publications that have commercial value.
![]() Operational and support procedures.
Operational and support procedures.
![]() Research documentation or proprietary information based on experimentation or exploration.
Research documentation or proprietary information based on experimentation or exploration.
![]() Strategic and operational plans, processes, and procedures that uniquely define the organization.
Strategic and operational plans, processes, and procedures that uniquely define the organization.
Information systems are the supporting players. Information systems provide a way and a place to process, store, transmit, and communicate the information. These systems are generally a combination of hardware and software assets and associated services. Information systems can be garden-variety off-the-shelf products or highly customized equipment and code. Support services may be technical services (voice communication and data communication) or environmental (heating, lighting, air conditioning, and power). The location of information systems may be “on premises,” at a contracted data center, or in the cloud.
Who Is Responsible for Information Assets?
This brings us to the question of ownership. Every information asset must be assigned an owner. The success of an information security program is directly related to the defined relationship between the data owner and the information. In the best-case scenario, the data owner also functions as a security champion enthusiastically embracing the goals of CIA.
In Chapter 3, “Information Security Framework,” we defined information ownership as being liable and responsible for protecting the information and the business results derived from using that information. For example, you have a medical file at your doctor’s office that may contain your medical history, digital scans, lab results, and physician notes. The clinicians in the office use that information to provide you with medical care. Because the information is all about you, are you the owner? No. The medical staff uses the information to provide care, so are they the owner? No. The information owner is the one responsible for protecting the confidentiality of your medical record, ensuring the integrity of the information in your records, and making sure that it is available to the clinicians whenever you need care. In a small medical practice, the owner is generally a physician. In a clinic or hospital, the owner is a member of senior management. Although it may seem obvious that every information asset needs an owner, it is not always apparent who should be or who is willing to assume the responsibility of ownership.
The Role of the Data Owner
The ISO 27002:2013 standard recommends that we have a policy that specifically addresses the need to account for our information assets and to assign an owner to the asset. The goal of an Information Ownership policy is to ensure that appropriate protection is maintained. Owners should be identified for all major information assets and given the responsibility for the safeguarding of the information system. The owner is responsible for the security of the asset. Data owner responsibilities include the following:
![]() Defining the asset
Defining the asset
![]() Assigning value to the asset
Assigning value to the asset
![]() Defining the level of protection required
Defining the level of protection required
![]() Deciding who should have access to the asset
Deciding who should have access to the asset
![]() Delegating day-to-day security and operational tasks
Delegating day-to-day security and operational tasks
![]() Ongoing governance
Ongoing governance
However, the owner is not the one who will be tasked with implementing security controls. That responsibility can be delegated to the information custodians such as system administrators.
The Role of the Information Security Officer
The information owner is accountable for the protection of the information asset. The information custodian is responsible for managing the day-to-day controls. The role of the Information Security Officer (ISO) is to provide direction and guidance as to the appropriate controls and to ensure that controls are applied consistently throughout the organization. Whereas information owners and custodians focus on specific information assets, the ISO is responsible for the security of the entire organization. As such, the office of the ISO is the central repository of security information. The ISO publishes the classification criteria, maintains the information systems inventories, and implements broad strategic and tactical security initiatives.
Information Classification
The objective of an information classification system is to differentiate data types. The value of an information classification system is to enable organizations to safeguard CIA based on content. The natural outcome of the classification process is instructions on who can access the asset, how the asset is to be used, what security measures need to be in place, and ultimately the method in which the asset should be destroyed or disposed of. Classification systems have their genesis in two seminal security models designed in the 1970s for the U.S. military: Bell-Lapadula and Biba. Both models are based on the assumption that an information system may contain information that requires different levels of security and that users of various clearance levels would be accessing the information system. The objective of the Bell-Lapadula model is to ensure confidentiality by restricting read access to data above what a user has permission to read and to restrict write access to data at a level below in order to minimize potential exposure. This is generally expressed as “no read up, no write down.” The objective of the Biba model is to ensure data integrity. The Biba model restricts users from reading data at a lower level and writing information to a higher level. The theory is that data at a lower level may be incomplete and/or inaccurate and if read could unduly influence what is written at a higher level. This is generally expressed as “no read down, no write up.” The implementation of Bell-Lapadula, Biba, and subsequent models required that a structured data classification system be developed.
Classification systems are now used in the private sector, the government, and the military. A financial institution will allow a teller to view general account information and cash checks of reasonable amounts. That same teller is not allowed to view information about internal bank assets and most definitely cannot access systems that would allow her to transfer millions of dollars. A hospital will allow a lab technician to access patient demographics and physician instructions but will not allow him to read or edit the complete patient record. The military, based on national security concerns, makes decisions to whom and how to make information accessible. They certainly do not want battle plans shared with the enemy. In fact, the military is a vivid example of an organization that relies extensively on a well-defined classification system. They classify not only information systems but people as well. Military and supporting civilian personnel are assigned clearance levels. The clearance level of the individual must match the classification of the data in order to be granted access. In this section, we are going to examine different approaches to information classification.
How Does the Federal Government Classify Data?
Let’s start with looking at how federal agencies categorize information and systems and then compare how the private sector classifies information. The United States government has enormous amounts of data and has a vested responsibility in protecting the CIA of the information and information systems. To this end, federal guidelines require that federal agencies categorize information and information systems. Federal Information Processing Standard 199 (FIPS-199) requires that information owners classify information and information systems as low, moderate, or high security based on CIA criteria. The generalized format for expressing the security category (SC) of an information type is as follows: The SC of information type = {(confidentiality, impact), (integrity, impact), (availability, impact)}, where the acceptable values for potential impact are low, moderate, high, or not applicable:
![]() Low potential impact means the loss of CIA could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
Low potential impact means the loss of CIA could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
![]() Moderate potential impact means the loss of CIA could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
Moderate potential impact means the loss of CIA could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
![]() High potential impact means the loss of CIA could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
High potential impact means the loss of CIA could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
Confidentiality Factors
Information is evaluated for confidentiality with respect to the impact of unauthorized disclosure as well as the use of the information. Federal guidelines suggest that agencies consider the following:
![]() How can a malicious adversary use the unauthorized disclosure of information to do limited/serious/severe harm to agency operations, agency assets, or individuals?
How can a malicious adversary use the unauthorized disclosure of information to do limited/serious/severe harm to agency operations, agency assets, or individuals?
![]() How can a malicious adversary use the unauthorized disclosure of information to gain control of agency assets that might result in unauthorized modification of information, destruction of information, or denial of system services that would result in limited/serious/severe harm to agency operations, agency assets, or individuals?
How can a malicious adversary use the unauthorized disclosure of information to gain control of agency assets that might result in unauthorized modification of information, destruction of information, or denial of system services that would result in limited/serious/severe harm to agency operations, agency assets, or individuals?
![]() Would unauthorized disclosure/dissemination of elements of the information type violate laws, executive orders (EOs), or agency regulations?
Would unauthorized disclosure/dissemination of elements of the information type violate laws, executive orders (EOs), or agency regulations?
Integrity Factors
Information is evaluated for integrity with respect to the impact associated with unauthorized modification or destruction. Federal guidelines suggest that agencies consider the following:
![]() How does unauthorized or unintentional modification of information harm agency operations, agency assets, or individuals?
How does unauthorized or unintentional modification of information harm agency operations, agency assets, or individuals?
![]() What is the impact of actions taken, decisions made based on modified information, or if the modified information is disseminated to other organizations or the public?
What is the impact of actions taken, decisions made based on modified information, or if the modified information is disseminated to other organizations or the public?
![]() How does unauthorized or unintentional destruction of information harm agency operations, agency assets, or individuals?
How does unauthorized or unintentional destruction of information harm agency operations, agency assets, or individuals?
![]() Does modification/destruction of elements of the information type violate laws, EOs, or agency regulations?
Does modification/destruction of elements of the information type violate laws, EOs, or agency regulations?
Availability Factors
Information is evaluated for availability with respect to the impact of disruption of access to or use of the information. Federal guidelines suggest that agencies consider the following:
![]() How does the disruption of access to or use of information do harm to agency operations, agency assets, or individuals?
How does the disruption of access to or use of information do harm to agency operations, agency assets, or individuals?
![]() What is the impact of destruction and/or permanent loss of information?
What is the impact of destruction and/or permanent loss of information?
![]() Does disruption of access to or use of elements of the information type violate laws, EOs, or agency regulations?
Does disruption of access to or use of elements of the information type violate laws, EOs, or agency regulations?
Why Is National Security Information Classified Differently?
The Unites States government and military process, store, and transmit information directly related to national security. It is important that everyone who interacts with these data recognize the significance. The first EO specifically defining and classifying government information was issued by President Harry S. Truman in 1952. Subsequent EOs were issued by Presidents Eisenhower, Nixon, Carter, Reagan, Clinton, and Bush. In December 2009, President Barack Obama issued Executive Order 13526 (Classified National Security Information), which revoked and replaced previous EOs:
“This order prescribes a uniform system for classifying, safeguarding, and declassifying national security information, including information relating to defense against transnational terrorism. Our democratic principles require that the American people be informed of the activities of their Government. Also, our Nations progress depends on the free flow of information. Nevertheless, throughout our history, the national defense has required that certain information be maintained in confidence in order to protect our citizens, our democratic institutions, our homeland security, and our interactions with foreign nations. Protecting information critical to our Nation’s security and demonstrating our commitment to open Government through accurate and accountable application of classification standards and routine, secure, and effective declassification are equally important priorities.” (President Barack Obama, December 29, 2009)
The following three special classifications defined in Executive Order 13526 denote special access and handling requirements. Information extraneous to the classification system is considered unclassified. Sensitive But Unclassified (SBU) is a Department of Defense–specific classification category. Authorization to assign classification level is restricted to specific U.S. Government officials:
![]() Top Secret (TS)—Any information or material the unauthorized disclosure of which reasonably could be expected to cause exceptionally grave damage to the national security. Examples of exceptionally grave damage include armed hostilities against the United States or its allies; disruption of foreign relations vitally affecting the national security; the compromise of vital national defense plans or complex cryptology and communications intelligence systems; the revelation of sensitive intelligence operations; and the disclosure of scientific or technological developments vital to national security.
Top Secret (TS)—Any information or material the unauthorized disclosure of which reasonably could be expected to cause exceptionally grave damage to the national security. Examples of exceptionally grave damage include armed hostilities against the United States or its allies; disruption of foreign relations vitally affecting the national security; the compromise of vital national defense plans or complex cryptology and communications intelligence systems; the revelation of sensitive intelligence operations; and the disclosure of scientific or technological developments vital to national security.
![]() Secret (S)—Any information or material the unauthorized disclosure of which reasonably could be expected to cause serious damage to the national security. Examples of serious damage include disruption of foreign relations significantly affecting the national security; significant impairment of a program or policy directly related to the national security; revelation of significant military plans or intelligence operations; compromise of significant military plans or intelligence operations; and compromise of significant scientific or technological developments relating to national security.
Secret (S)—Any information or material the unauthorized disclosure of which reasonably could be expected to cause serious damage to the national security. Examples of serious damage include disruption of foreign relations significantly affecting the national security; significant impairment of a program or policy directly related to the national security; revelation of significant military plans or intelligence operations; compromise of significant military plans or intelligence operations; and compromise of significant scientific or technological developments relating to national security.
![]() Confidential (C)—Any information or material the unauthorized disclosure of which reasonably could be expected to cause damage to the national security. Examples of damage include the compromise of information that indicates strength of ground, air, and naval forces in the United States and overseas areas; disclosure of technical information used for training, maintenance, and inspection of classified munitions of war; and revelation of performance characteristics, test data, design, and production data on munitions of war.
Confidential (C)—Any information or material the unauthorized disclosure of which reasonably could be expected to cause damage to the national security. Examples of damage include the compromise of information that indicates strength of ground, air, and naval forces in the United States and overseas areas; disclosure of technical information used for training, maintenance, and inspection of classified munitions of war; and revelation of performance characteristics, test data, design, and production data on munitions of war.
![]() Unclassified (U)—Any information that can generally be distributed to the public without any threat to national interest. Note: This category is not specifically defined in EO 13526.
Unclassified (U)—Any information that can generally be distributed to the public without any threat to national interest. Note: This category is not specifically defined in EO 13526.
![]() Sensitive But Unclassified (SBU)—This classification is a Department of Defense subcategory and is applied to “any information of which the loss, misuse or unauthorized access to, or modification of might adversely affect U.S. National Interests, the conduct of the Department of Defense (DoD) programs or the privacy of DoD personnel.” Labeling in this category includes “For Official Use Only,” “Not for Public Release,” and “For Internal Use Only.”
Sensitive But Unclassified (SBU)—This classification is a Department of Defense subcategory and is applied to “any information of which the loss, misuse or unauthorized access to, or modification of might adversely affect U.S. National Interests, the conduct of the Department of Defense (DoD) programs or the privacy of DoD personnel.” Labeling in this category includes “For Official Use Only,” “Not for Public Release,” and “For Internal Use Only.”
Who Decides How National Security Data Is Classified?
National security data is classified in one of two ways:
![]() Original classification is the initial determination that information requires protection. Only specific U.S. Government officials who have been trained in classification requirements have the authority to make the classification decisions. Original classification authorities issue security classification guides that others use in making derivative classification decisions. Most government employees and contractors make derivative classification decisions.
Original classification is the initial determination that information requires protection. Only specific U.S. Government officials who have been trained in classification requirements have the authority to make the classification decisions. Original classification authorities issue security classification guides that others use in making derivative classification decisions. Most government employees and contractors make derivative classification decisions.
![]() Derivative classification is the act of classifying a specific item of information or material based on an original classification decision already made by an authorized original classification authority. The source of authority for derivative classification ordinarily consists of a previously classified document or a classification guide issued by an original classification authority.
Derivative classification is the act of classifying a specific item of information or material based on an original classification decision already made by an authorized original classification authority. The source of authority for derivative classification ordinarily consists of a previously classified document or a classification guide issued by an original classification authority.
How Does the Private Sector Classify Data?
There are no legally mandated private sector data classifications so organizations are free to develop a classification system appropriate to their organization. Commonly used classifications include Legally Protected, Confidential, Internal Use, and Public. Information owners are responsible for classifying data and systems. Based on the classification, information custodians can apply the appropriate controls and, importantly, users know how to interact with the data.
![]() Protected—Data that is protected by law, regulation, memorandum of agreement, contractual obligation, or management discretion. Examples include non-public personal information (NPPI), such as social security number, driver’s license or state-issued identification number, bank account or financial account numbers, payment card information (PCI), which is credit or debit cardholder information, and personal health information (PHI).
Protected—Data that is protected by law, regulation, memorandum of agreement, contractual obligation, or management discretion. Examples include non-public personal information (NPPI), such as social security number, driver’s license or state-issued identification number, bank account or financial account numbers, payment card information (PCI), which is credit or debit cardholder information, and personal health information (PHI).
![]() Confidential—Data that is essential to the mission of an organization. Loss, corruption, or unauthorized disclosure would cause significant financial or legal damage to the organization and its reputation. Examples include business strategies, financial positions, employee records, upcoming sales or advertising campaigns, laboratory research, and product schematics.
Confidential—Data that is essential to the mission of an organization. Loss, corruption, or unauthorized disclosure would cause significant financial or legal damage to the organization and its reputation. Examples include business strategies, financial positions, employee records, upcoming sales or advertising campaigns, laboratory research, and product schematics.
![]() Internal Use—Data that is necessary for conducting ordinary company business. Loss, corruption, or unauthorized disclosure may impair the business or result in business, financial, or legal loss. Examples include policy documents, procedure manuals, non-sensitive client or vendor information, employee lists, or organizational announcements.
Internal Use—Data that is necessary for conducting ordinary company business. Loss, corruption, or unauthorized disclosure may impair the business or result in business, financial, or legal loss. Examples include policy documents, procedure manuals, non-sensitive client or vendor information, employee lists, or organizational announcements.
![]() Public—Information that is specifically intended for the public at large. Public information requires discretionary treatment and should be cleared for release prior to public distribution. This category includes annual reports, product documentation, list of upcoming trade shows, and published white papers.
Public—Information that is specifically intended for the public at large. Public information requires discretionary treatment and should be cleared for release prior to public distribution. This category includes annual reports, product documentation, list of upcoming trade shows, and published white papers.
If the appropriate classification is not inherently obvious, a conservative approach is generally used and the data is classified in the more restrictive category.
Can Information Be Reclassified or Even Declassified?
Over a period of time, the need to protect information may change. An example of this can be found in the auto industry. Prior to a new car introduction, the design information is considered confidential. Disclosure would have serious ramifications to the automaker. After introduction, the same information is considered public and is published in the automotive manual. The process of downgrading sensitivity levels is known as declassification.
Conversely, organizations may choose to strengthen the classification level if they believe that doing so is for the benefit of the organization or required by evolving regulations. For example, in 2013, HIPAA regulations were extended to cover data maintained by business associates. In this case, business associates need to revisit the classification of data they access, store, process, or transmit. The process of upgrading a classification is known as reclassification. If the information owner knows ahead of time when the information should be reclassified, then that date should be noted on the original classification label (for example, “Confidential until [date]”). At the time an organization is establishing the criteria for classification levels, it should also include a mechanism for reclassifying and declassifying information. This responsibility may be assigned to the information owner or subject to an internal review process.
Labeling and Handling Standards
Information owners classify information in order to identify the level of protection necessary. As we defined in Chapter 2, “Policy Elements and Style,” standards serve as specifications for the implementation of policy and dictate mandatory requirements. Handling standards dictate by classification level how information must be stored, transmitted, communicated, accessed, retained, and destroyed. Labeling is the vehicle for communicating the assigned classification to information custodians and users.
Why Label?
Labels make it easy to identify the data classification. Labels can take many forms: electronic, print, audio, and visual. Information may need to be labeled in many ways, depending on the audience. The labels you are probably most familiar with are safety labels. You recognize poison from the skull-and-crossbones symbol. You instinctively know to stop when you see a red stop sign. You know to pull over when you hear a police siren. In order to protect information, classification level labels need to be as clear and universally understood as a skull-and-crossbones symbol or a stop sign. Labels transcend institutional knowledge and provide stability in environments that experience personnel turnover.
In electronic form, the classification should be a part of the document name (for example, “Customer Transaction History–PROTECTED”). On written or printed documents, the classification label should be clearly marked on the outside of the document as well as in either the document header or footer. Media, such as backup tapes, should be clearly labeled with words and (where appropriate) symbols.
Why Handling Standards?
Information needs to be handled in accordance with its classification. Handling standards inform custodians and users how to treat the information they use and the systems they interact with. Handling standards generally include storage, transmission, communication, access, retention, destruction, and disposal, and may extend to incident management and breach notification.
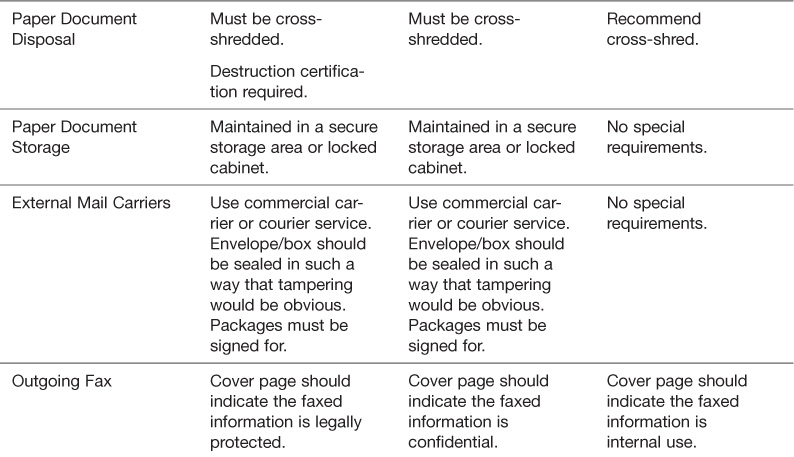
As illustrated in Table 5.1, it is important that handling standards be succinctly documented in usable format. The handling standards should be introduced during the orientation period and reintroduced as part of an Acceptable Use Policy and Agreement.
Information Systems Inventory
As amazing as it may seem, many organizations do not have an up-to-date inventory of information systems. This happens for any number of reasons. The most prevalent is a lack of centralized management and control. Departments within organizations are given the autonomy to make individual decisions, bring in systems, and create information independent of the rest of the organization. Corporate cultures that encourage entrepreneurial behavior are particularly vulnerable to this lack of structure. Another reason is the growth of corporations through acquisitions and mergers. Sometimes companies change so rapidly it becomes nearly impossible to manage information effectively. Generally, the plan is to consolidate or merge information and systems, but in reality, they often end up cohabitating.
What Should Be Inventoried?
Putting together a comprehensive physical inventory of information systems is a major task. The critical decision is choosing what attributes and characteristics of the information asset you want to record. The more specific and detailed the inventory, the more useful the inventory will be. Bear in mind that over time your inventory may have multiple purposes, including being used for criticality and risk analysis, business impact, and disaster recovery planning insurance coverage, and business valuation.
![]() Computer equipment—Mainframe computers, servers, desktops, laptops, tablets, and smartphones
Computer equipment—Mainframe computers, servers, desktops, laptops, tablets, and smartphones
![]() Printers—Printers, copiers, scanners, fax machines, and multifunction devices
Printers—Printers, copiers, scanners, fax machines, and multifunction devices
![]() Communication and networking equipment—IDS/IPSs, firewalls, modems, routers, access points, cabling, DSU/CSUs, and transmission lines
Communication and networking equipment—IDS/IPSs, firewalls, modems, routers, access points, cabling, DSU/CSUs, and transmission lines
![]() Storage media—Magnetic tapes, disks, CDs, DVDs, and USBs
Storage media—Magnetic tapes, disks, CDs, DVDs, and USBs
![]() Infrastructure equipment—Power supplies, air conditioners, and access control devices
Infrastructure equipment—Power supplies, air conditioners, and access control devices
Software Assets
Software assets are programs or code that provide the interface between the hardware, the users, and the data. Software assets generally fall into three categories:
![]() Operation system software—Operating systems are responsible for providing the interface between the hardware, the user, and the application. Examples include Microsoft Windows, Apple iOS, Linux, Unix, and FreeBSD.
Operation system software—Operating systems are responsible for providing the interface between the hardware, the user, and the application. Examples include Microsoft Windows, Apple iOS, Linux, Unix, and FreeBSD.
![]() Productivity software—The objective of productivity software is to provide basic business functionality and tools. Examples include the mobile apps, the Microsoft Office Suite (Word, Excel, Publisher, and PowerPoint), Adobe Reader, Intuit Quick Books, and TurboTax.
Productivity software—The objective of productivity software is to provide basic business functionality and tools. Examples include the mobile apps, the Microsoft Office Suite (Word, Excel, Publisher, and PowerPoint), Adobe Reader, Intuit Quick Books, and TurboTax.
![]() Application software—Application software is designed to implement the business rules of the organization and is often custom developed. Examples include programs that run complex machinery, process bank transactions, or manage lab equipment.
Application software—Application software is designed to implement the business rules of the organization and is often custom developed. Examples include programs that run complex machinery, process bank transactions, or manage lab equipment.
Asset Inventory Characteristics and Attributes
Each asset should have a unique identifier. The most significant identifier is the device or program name. Although you may assume that the name is obvious, you’ll often find that different users, departments, and audiences refer to the same information, system, or device differently. Best practices dictate that the organization chooses a naming convention for its assets and apply the standard consistently. The naming convention may include the location, vendor, instance, and date of service. For example, a Microsoft Exchange server located in New York City and connected to the Internet may be named MS_EX_NYC_1. A SQL database containing inventory records of women’s shoes might be named SQL_SHOES_W. The name should also be clearly labeled on the device. The key is to be consistent, so that the names themselves become pieces of information. This is, however, a double-edged sword. We risk exposing asset information to the public if our devices are accessible or advertise them in any way. We need to protect this information consistent with all other valuable information assets.
An asset description should indicate what the asset is used for. For example, devices may be identified as computers, connectivity, or infrastructure. Categories can (and should) be subdivided. Computers can be broken down into domain controllers, application servers, database servers, web servers, proxy servers’ workstations, laptops, tablets, smartphones, and smart devices. Connectivity equipment might include IDS/IPSs, firewalls, routers, satellites, and switches. Infrastructure might include HVAC, utility, and physical security equipment.
For hardware devices, the manufacturer name, model number, part number, serial number, and host name or alias should be recorded. The physical and logical addresses should also be documented. The physical address refers to the geographic location of the device itself or the device that houses the information. This should be as specific as possible. For example, APPS1_NYC is located at the East 21st Street office’s second floor data center. The logical address is where the asset can be found on the organization’s network. The logical address should reference the host name, the Internet Protocol (IP) address, and, if applicable, the Media Access Control (MAC) address. Host names are “friendly names” given to systems. The host name may be the actual name of the system or an alias used for easy reference. The IP address is the unique network address location assigned to this system. Lastly, the MAC address is a unique identifier assigned to network connectivity devices by the manufacturer of the device.
Software should be recorded by publisher or developer, version number, revision, the department or business that purchased or paid for the asset number, and, if applicable, patch level. Software vendors often assign a serial number or “software key,” which should be included in the record.
Last but not least, the controlling entity should be recorded. The controlling entity is the department or business that purchased or paid for the asset and/or is responsible for the ongoing maintenance and upkeep expense. The controlling entity’s capital expenditures and expenses are reflected in its budgets, balance sheets, and profit and loss statements.
Removing, Disposing Of, or Destroying Company Property
Company assets should be accounted for at all times. If company property needs to move from its assigned location or be destroyed, there should be an asset management procedure. Documentation should be maintained so that at any time an audit will account for the location and possession of every piece of equipment or information. Asset disposal and destruction is discussed in Chapter 7, “Physical and Environmental Security.”
Summary
You may have heard the phrase “security through obscurity.” This phase implies that there is a proportional relationship between keeping an asset hidden and its safety. The problem with this concept is that it is not practical, or even desirable, to keep our information and systems locked up. Information assets have value to the organization and are often used in day-to-day operations to accomplish its mission. The inverse to “security through obscurity” is “security through classification and labeling.” The best way to protect an information asset or system is to identify the confidentiality, integrity, and availability (CIA) requirements and then apply the appropriate safeguards and handling standards. The process of identification and differentiation is known as classification. Information owners are responsible for properly identifying and classifying the information for which they are responsible. Information custodians are tasked with implementing security controls.
FISMA requires that federal agency information owners classify their information and information systems as low, moderate, or high security based on criteria outlined in the FIPS-199. Information is evaluated for confidentiality with respect to the impact of unauthorized disclosure as well as the use of the information, integrity with respect to the impact associated with unauthorized modification or destruction, and availability with respect to the impact of disruption of access to or use of the information. Five special classifications are reserved for national security–related information that denotes special access and handling requirements: Top Secret, Secret, Confidential, Unclassified, and Sensitive But Unclassified (SBU). The process of downgrading a classification is known as declassification. The process of upgrading a classification is known as reclassification.
There are no comparable classification requirements for the private section. However, multiple state and federal statutes require all organizations to protect specific categories of information. The broadest category is non-public personal information (NPPI). NPPI is information considered to be personal in nature, subject to public availability, and if disclosed is an invasion of privacy. It is common for private sector organizations to adopt a three- or four-tier classification system that takes into account legal, privacy, and business confidentiality requirements. Labeling is the vehicle for communicating the assigned classification to information custodians and users. Handling standards inform custodians and users how to treat the information they use and the systems they interact with.
Information systems provide a way and a place to process, store, and transmit information assets. It is important to maintain an up-to-date inventory of hardware and software assets. Hardware assets are visible and tangible pieces of equipment and media. Software assets are programs or code that provides the interface between the hardware, the users, and the data. Descriptors may include what the asset is used for, its location, the unique hardware identification number known as a MAC address, the unique network identifier known as an IP address, host name, and domain name.
Organizational Asset Management policies include Information Ownership, Information Classification, Handling and Labeling Requirements, and Information Systems Inventory.
Test Your Skills
Multiple Choice Questions
1. Which of the following terms best describes a definable piece of information, stored in any manner, that is recognized as having value to the organization?
A. NPPI
B. Information asset
C. Information system
D. Classified data
2. Information systems __________, __________, and __________ information.
A. create, modify, and delete
B. classify, reclassify, and declassify
C. store, process, and transmit
D. use, label, and handle
3. Information owners are responsible for which of the following tasks?
A. Classifying information
B. Maintaining information
C. Using information
D. Registering information
4. Which of the following roles is responsible for implementing and maintaining security controls?
A. Information owner
B. Information vendor
C. Information user
D. Information custodian
5. FIPS-199 requires that federal government information and information systems be classified as ____________.
A. Low security
B. Moderate security
C. High security
D. None of the above
6. Information classification systems are used in which of the following organizations?
A. Government
B. Military
C. Financial institutions
D. All of the above
7. FIPS requires that information be evaluated for _____________requirements with respect to the impact of unauthorized disclosure as well as the use of the information.
A. integrity
B. availability
C. confidentiality
D. secrecy
8. Which of the following National Security classifications requires the most protection?
A. Secret
B. Top Secret
C. Confidential
D. Unclassified
9. Which of the following National Security classifications requires the least protection?
A. Secret
B. Unclassified
C. Confidential
D. Sensitive But Unclassified (SBU)
10. The Freedom of Information Act (FOIA) allows anyone access to which of the following?
A. Access to all government information just by asking
B. Access to all classified documents
C. Access to classified documents on a “need to know” basis
D. Access to any records from federal agencies unless the documents can be officially declared exempt
11. Which of the following terms best describes the CIA attribute associated with the modification of information?
A. Classified
B. Integrity
C. Availability
D. Intelligence
12. Is it mandatory for all private businesses to classify information?
A. Yes.
B. Yes, but only if they want to pay less taxes.
C. Yes, but only if they do business with the government.
D. No.
13. Which of the following is not a criterion for classifying information?
A. The information is not intended for the public domain.
B. The information has no value to the organization.
C. The information needs to be protected from those outside of the organization.
D. The information is subject to government regulations.
14. Data that is considered to be personal in nature and, if disclosed, is an invasion of privacy and a compromise of security is known as which of the following?
A. Non-personal public information
B. Non-private personal information
C. Non-public personal information
D. None of the above
15. Most organizations restrict access to protected, confidential, and internal-use data to which of the following roles within the organization?
A. Executives
B. Information owners
C. Users who have a “need to know”
D. Vendors
16. Labeling is the vehicle for communicating classification levels to which of the following roles within the organization?
A. Employees
B. Information custodians
C. Contractors
D. All of the above
17. Which of the following terms best describes rules for how to store, retain, and destroy data based on classification?
A. Handling standards
B. Classification procedures
C. Use policies
D. Material guidelines
18. Which of the following terms best describes the process of removing restricted classification levels?
A. Declassification
B. Classification
C. Reclassification
D. Negative classification
19. Which of the following terms best describes the process of upgrading or changing classification levels?
A. Declassification
B. Classification
C. Reclassification
D. Negative classification
20. The impact of destruction and/or permanent loss of information is used to determine which of the following safeguards?
A. Authorization
B. Availability
C. Authentication
D. Accounting
21. Which of the following terms best describes an example of a hardware asset?
A. Server
B. Database
C. Hammer
D. Radio waves
22. Which of the following statements best describes a MAC address?
A. A MAC address is a unique network address.
B. A MAC address is a unique host name.
C. A MAC address is a unique hardware identifier.
D. A MAC address is a unique alias.
23. 10.1.45.245 is an example of which of the following?
A. A MAC address
B. A host name
C. An IP address
D. An IP domain name
24. Code and databases are examples of which of the following?
A. Software assets
B. Proprietary information
C. Internal-use classification
D. Intellectual property (IP)
25. Which of the following terms best describes the act of classifying information based on an original classification decision already made by an authorized original classification authority?
A. Reclassification
B. Derivative classification
C. Declassification
D. Original classification
26. Which of the following types of information would not be considered NPPI?
A. Social security number
B. Date of birth
C. Debit card PIN
D. Home address
27. In keeping with best practices and regulatory expectations, legally protected data that is stored on mobile devices should be _____.
A. masked
B. encrypted
C. labeled
D. segregated
28. Which of the following statements best describes how written documents that contain NPPI should be handled?
A. Written documents that contain NPPI should be stored in locked areas or in a locked cabinet.
B. Written documents that contain NPPI should be destroyed by cross-cut shredding.
C. Written documents that contain NPPI should be subject to company retention policies.
D. All of the above.
29. Which of the following address types represents a device location on a network?
A. A physical address
B. A MAC address
C. A logical address
D. A static address
30. Which of the following statements is true?
A. Small businesses do not need to classify data because it is unusual for a small business to have NPPI.
B. Small businesses do not need to classify data because small businesses do not have regulatory obligations.
C. Small businesses need to classify data because small businesses are responsible for protecting NPPI, employee data, and company data.
D. Small businesses need to classify data because every organization is legally required to have a classification system.
Owners are responsible for the protection of assets. For each of the following assets, assign an owner and list their responsibilities in regard to protecting the asset:
1. The house you live in.
2. The car you drive.
3. The computer you use.
4. The city you live in.
Exercise 5.2: Differentiating Between Ownership and Custodianship
A smartphone is an information system. As with any information system, data ownership and custodianship must be assigned.
1. If a company provides a smartphone to an employee to use for work-related communications:
a. Who would you consider the information system owner? Why?
b. Who would you consider the information system custodian? Why?
2. If a company allows an employee to use a personally owned device for work-related communications:
a. Who would you consider the information system owner? Why?
b. Who would you consider the information system custodian? Why?
c. In regard to protecting data, should there be a distinction between company data and personal data?
Exercise 5.3: Creating an Inventory
You have been tasked with creating an inventory system for the computer lab at your school.
1. For the hardware in the lab, list at least five characteristics you will use to identify each asset.
2. For the software in the lab, list at least five characteristics you will use to identify each asset.
3. Create an inventory template. Use either a spreadsheet or database application.
4. Visit a classroom or lab and inventory a minimum of three hardware and three software assets.
Exercise 5.4: Reviewing a Declassified Document
Go to either http://FOIA.gov or the CIA FOIA Electronic Reading Room at www.foia.cia.gov.
1. Find a document that has been recently declassified.
2. Write a brief report explaining why and when the document was declassified.
Exercise 5.5: Understanding Color-Coded National Security
The Department of Homeland Security uses a color-coded advisory system to communicate threat levels to the public. This is an example of labeling.
1. What colors are used in the Threat Advisory System?
2. What does each of the colors mean?
3. Do you think these labels are an effective way to communicate threat information to the general public? Why or why not?
Projects
Project 5.1: Developing an Email Classification System and Handling Standards
Data classification categories and handling standards are necessary to properly protect information. Email is a good example of an information system that processes, stores, and transmits many different types of information.
1. Develop a three-level classification system for your email communications. Consider the type of emails you send and receive. Take into consideration who should be able to view, save, print, or forward your email. For each classification, decide how you will label your emails to communicate the assigned classification. For each classification, develop handling standards.
2. Multiple information systems are used to process, transmit, store, and back up email. Identify as many systems as possible involved in each step. For each system identified, document the person or position you would expect to be the information system owner. Is it necessary to provide them with a copy of your classification system or handling standards? Why or why not?
3. Sometimes information system owners have different priorities. For example, your Internet service provider (ISP) by law has the right to view/open all documents that are stored on or passed through its systems. The ISP may choose to exercise this right by scanning for viruses or checking for illegal content. Suppose you have sent emails that could cause you harm if they were disclosed or compromised. As the information owner, what are your options?
Project 5.2: Classifying Your School Records
Over time, your school has accumulated a great deal of information about you and your family, including your medical records, finances (including tax returns), transcripts, and student demographic data (name, address, date of birth, and so on). It is important that access to this information be restricted to authorized users.
1. Create a table listing each of these information categories. Classify each one as either Protected, Confidential, Internal Use, or Public.
2. Include in your table a column defining the “Need to Know” criteria. (Hint: This is the reason someone should be granted access to the information.)
3. Even though the information pertains to you, you are not the owner. Include in your table a column listing who you would expect to be the information owner.
4. Choose one of the categories you have listed and find out where the information is actually stored, who is responsible for it, who has access to it, and what policies are in place to protect it. Compare this information with your answers to items 1, 2, and 3 of this project.
Project 5.3: Locating and Using Special Publications
The National Institute of Standards and Technology (NIST) special publications contain a wealth of information applicable to both private and public sector organizations. In this exercise, you will familiarize yourself with locating and using special publications.
1. Download a copy of NIST SP 800-88, R1: Guidelines for Media Sanitization.
2. Read through the document.
3. To whom do they assign ultimate responsibility for media sanitization?
4. Refer to Figure 4-1, “Sanitization and Disposition Decision Flow.” What is the relationship between this chart and classification levels?
5. In regard to media sanitization, explain the differences between clear, purge, and destroy?
References
Regulations Cited
FIPS PUB 199 Standards for the Security Categorization of Federal Information and Information Systems, February 2004, accessed 06/2013, http://csrc.nist.gov/publications/fips/fips199/FIPS-PUB-199-final.pdf.
Freedom of Information Act, official website of the U.S. Department of Justice, FOIA, accessed 06/2013, www.foia.gov/.
Modifications to the HIPAA Privacy, Security, Enforcement, and Breach Notification Rules 45 CFR Parts 160 and 164 Under the Health Information Technology for Economic and Clinical Health Act and the Genetic Information Nondiscrimination Act; Other Modifications to the HIPAA Rules; Final Rule Federal Register, Volume 78, No. 17, January 25, 2013, accessed 06/2013, www.hhs.gov/ocr/privacy/hipaa/administrative/omnibus/.
United States Department of Defense Manual Number 52001.01, Volume 1, February 24, 2012, “Overview, Classification and Declassification,” accessed 06/2013, www.dtic.mil/whs/directives/corres/pdf/520001_vol1.pdf.
United States Department of Defense Manual Number 5200.01, Volume 2, March 19, 2013, “Marking of Classified Information,” accessed 06/2013, www.dtic.mil/whs/directives/corres/pdf/520001_vol2.pdf.
United States Department of Agriculture, Personnel and Document Security Division, “Classification Guidelines and Distribution Controls, Original and Derivative,” accessed 06/2013, www.dm.usda.gov/ocpm/Security%20Guide/S1class/Classif.htm.
Executive Orders Cited
Executive Order 13526: Classified National Security Information. White House Office of the Press Secretary, December 29, 2009, accessed on 06/10/3013, www.whitehouse.gov/the-press-office/executive-order-classified-national-security-information.
Other Research
Hosenball, Mark and Cowan (Reuters). “Edward Snowden, NSA Whistleblower, Says He Acted Out of Conscience to Protect ‘Basic Liberties,’” accessed on 06/10/2013, www.huffingtonpost.com/2013/06/10/edward-snowden-basic-liberties_n_3414824.html.
Radack, Shirley. “Risk Management Framework: Helping Organizations Implement Effective Information Security Programs,” NIST Computer Security Division, accessed 06/2013, http://csrc.nist.gov/publications/.../july2009_risk-management-framework.pdf.
Ross, Ron. “Risk Management Framework,” NIST Computer Security Division, accessed 06/2013, http://csrc.nist.gov/groups/SMA/fisma/.../risk-management-framework-2009.pdf,