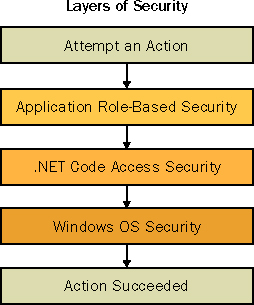
The main difference between code-access security and application-defined role-based security, as presented in Chapter 2, is that code-access security is enforced by the system (namely the .NET runtime), whereas role-based security is implemented by you in your code. Code-access security allows no choice (which is a good thing in this case)—that is, the system automatically determines what your code is allowed to do. Role-based security, on the other hand, is all about choice. You get to choose whether you need to implement role-based security in your application, as well as the extent to which it will be applied throughout your application, if at all.
Code-access security permissions are evaluated independent of application role-based security permissions. To illustrate the relationship between the two types of security, let’s use an example of attempting to take luggage on an airplane. You get to choose the size, shape, and color of the luggage you want to take on a trip. For example, suppose you choose to take a big, yellow suitcase on a business trip. Because the suitcase contains important documents, you decide to carry it with you on the airplane. Your choice of what you want to do with your suitcase ends as soon as you get to airport security. You find that after much force and ingenuity you can’t cram your suitcase through the tiny opening into the X-ray machine. Security personnel quickly step in and point out that because of size restrictions you are not permitted to carry your suitcase onto the airplane. You pull out your business card, present it to the security guard, and explain that you are the president of an important software start-up company. This only serves to infuriate the security guard, who promptly hauls you and your luggage back to the lobby. Defeated, you check in your suitcase at the check-in counter. Your role as president of an important company did nothing to change or preempt the rules that apply to everybody.
Code-access security controls your code much like airport security controls what is allowed to be carried on board an airplane. For example, if your application is not permitted to create a file on disk, the code-access security system will refuse to allow your application to write to disk. A security exception will occur and your application will be halted much like the passenger who is halted and sent back from the airport security checkpoint. The operation will not be allowed no matter who is granted permission by your application’s role-based security system to save the file to disk—even if that person, the president of an important start-up company, was granted the permission by your role-based security model.
It’s possible to make exceptions to the rules. For example, if the head of the United Nations wanted to pass a big, yellow suitcase through security, an exception could be made to allow him to pass through. See Chapter 10 for more information on modifying and deploying security policy updates.
In terms of code-access security, what are determining factors in what your code is allowed to do? You might be surprised to find that your Visual Basic .NET application that runs fine on your local computer terminates with a security exception when deployed and run from a server or from the Internet. We’ll see in the next section that the actions your Visual Basic .NET code is allowed to perform are largely determined by the environment in which your code is run.