CHAPTER 8
The Consumerization of IT
Arguing with a fool proves there are two.
—Doris M. Smith1
Let me start this chapter with the following statement about the consumerization of IT that is so often repeated by my colleagues in the IT industry: “It's a challenge that adds risk and, in many cases, costs to an organization's IT governance and overall management of technology.”
Consumer Devices Permeate the Corporate World
Consumer devices are impacting IT departments and organizations today with a rapid pace of adoption. Not long ago, IT organizations and CIOs were able to stand their ground in not allowing personal devices on the trusted corporate network. Today the proposition has turned 180 degrees, in favor of the consumer and not IT and legal executives.
According to Forrester Research, consumerization is the dominant force in smartphone and mobile device selection today; it has a simple definition:
- The device choice is made by the employee, not the organization or IT.
- The confirmation that employees are willing to assume some of the burden, if not all of it, for costs and support of the devices they choose to use in their personal lives and now at work.2
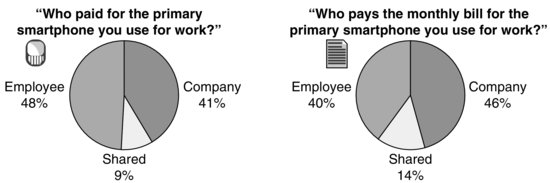
Forrester reported in a recent survey of 1,751 U.S. workers that bring your own device (BYOD) is real, with large percentages of employees paying for both the device acquisition (48 percent) and service (40 percent) but only 14 percent sharing ongoing usage costs with their employers through a reimbursement or stipend model (see Exhibit 8.1).3
Consumer devices come in a variety of shapes and forms. The most common devices, from some of most innovative and exciting manufacturers, include the following:
- Tablet computers. Apple's iPad leads the way on this front. Google's Nexus 7 device is a competitive challenger, followed by tablets from Amazon (Kindle), Samsung (Galaxy) and Research in Motion (BlackBerry Playbook). Hewlett-Packard has reemerged into this market with the announcement of the ElitePad 900 Windows 8 tablet. Nokia Corporation is set to release a Windows 8 tablet in 2013 that will be available on the AT&T network. Tablets come in a variety of shapes, sizes, and operating systems, ranging from Windows to Google's Android to Apple's iOS. It is precisely the variation of vendor and operating system mix that can make these devices costly and difficult to support for IT departments today.
- Laptops. Traditional laptops are still the mobile computing device of choice for power users who travel frequently. I've yet to see a tablet fully replace a well-equipped laptop for hard-core work, but it may be coming in the future, likely via a laptop-tablet hybrid.
- Laptop-tablet hybrid. Hewlett-Packard's Envy X2 is an 11-inch tablet that comes with a keyboard dock with some high-end features like Beats Audio, pen support, and a high-resolution display. Microsoft also introduced the Surface hybrid running the Windows 8 operating system. I expect more hybrid devices to hit the market in the coming months and years.
- Smartphones. All one needs to do is search for “smartphone” on any search engine to see the myriad of vendors, products, features, and operating systems within this space. Today's smartphones, previously called PDAs, are highly functioning minicomputers that do voice, data, applications, and video. They are the most common mobile device in the market today, with a staggering growth rate. I'll highlight some specific trends for smartphones later in this section, since they continue to be the predominant mobile computing choice today for both consumers and business professionals.
This market is extremely fierce and competitive and relies heavily on consumers to upgrade their equipment or model when a newer model becomes available and hits the shelves. I need not go beyond the Apple iPhone to highlight this behavior. My own children have upgraded their smartphone models as they have been improved.
There are essentially three schools of thought on how to deal with the onslaught of consumer devices today:
The effect of adding consumer devices to the corporate world typically means the following:
- Device selection affects the platforms (e.g., device, operating system, security, and ease of integration) that IT may integrate with the systems and information to be competitive and support the organization's information needs. One of the benefits of standardization (including with mobile devices) is that IT can ensure that the devices deployed will be properly supported by and integrated into the organization's systems. Letting consumers and staffers select their devices of choice doesn't always ensure that possibility.
- Mobile device selection usually affects the demands for computers in the organization. Once the gates are open to BYOD for mobile computing, the most common push for expansion is into the computers the employees use in their workday. Thus, bringing in a personal iPhone may result in a request for a nonstandard Macintosh computer next.
- The willingness of employees to absorb some or all of the costs affects the budgeting and expense reimbursement process within organizations—in many cases, making more work for the accounting department. With a central IT standard, the IT department typically pays for the device acquisition and usage, centrally budgets for those expenses, and either centrally pays for those services on a monthly basis or charges the departments with some frequency. A BYOD policy that puts all of the expenses on the employee is the easiest to implement from a cost perspective. Sharing expenses can have profound effects on how organizations budget and pay for services, often requiring each department to budget for its portion of mobile device usage and for accounting to process many more transactions per month than just one associated with a central IT standard method. As a result, there are hidden costs, many of them labor-associated, with a cost-sharing BYOD program that involves labor and time for budgeting and reimbursements. I've said, “Nothing is free, and if it is, it won't last forever” before. It applies here as well, especially for organizations that get involved in partial reimbursement for personal mobile device purchase and use.4
The following positions and recommendations discussed in a variety of articles highlight just how much consumerization of IT and BYOD is having an effect on managing technology and security in organizations today.
Consumerization Pros
- According to a recent Forrester Research report, “The days of IT-controlled smartphone deployments are over. Consumerization is the dominant force in smartphone selection.”5
- According to a CIO magazine article, BYOD shifts the costs to the employee and away from the employer, in some cases as much as $80 per month per device. The article cited a recent survey of 600 U.S. IT and business leaders that found the following:
- “A staggering 95 percent” of respondents permit employee-owned devices in the workplace.
- Mobile devices are even happening behind closed and trusted network doors. Juniper Networks reported more than 4,000 users and professionals.
- Virtualization giant VMWare went “all-in” with BYOD smartphones for its employees.
- The most surprising finding in the report was that 41 percent of all respondents who use their personal device for work are doing so without permission from the company.6
- Worker satisfaction and flexibility is increased by BYOD because employees get to use the devices they want.7
- The devices are typically more cutting-edge and feature-rich in a consumerization or BYOD environment where employees can opt for the latest device as soon as it's released onto the market.8
Consumerization Cons
- Device compatibility with systems is not controllable by IT.9
- There are often hidden administrative costs (e.g., budgeting, expense tracking, or legal) associated with implementing a BYOD policy.10
- “There are issues of compliance and ownership when it comes to data” for mandates such as PCI-DSS, the Health Insurance Portability and Accountability Act (HIPAA), or the Gramm-Leach-Billey Act (GLBA).11
- Security and device management is more challenging and costly for IT departments as a result of a nonstandard or expanded standard with BYOD.
The result, according to Gartner Research, is that the consumerization trend is “driving IT shops crazy.” The report states that “the number of devices coming in the next few years will outstrip IT's ability to keep the enterprise secure.” In addition, MDM software is helpful to monitor and manage which devices have access to certain applications, but it is “not a secure enough approach.” DLP software may be one of the more promising tools in the future to help organizations protect their data in the rapid trend to allow personal devices in the corporate world.12
Growth Trends for Mobile Computing
Market share is important in today's computing environment, especially the mobile platform and device market. In the first edition of Straight to the Top, I noted that software developers write to the market share. This is still true, and it has been highlighted with some dizzying reversal of fortunes (and market share) for some of the mobile device vendors selling their wares. Just a few years ago, Research in Motion (RIM), which makes the BlackBerry smartphone, was at the top of the corporate world and could do no wrong. That was also when most CIOs wouldn't even consider allowing a personal device to penetrate their corporate networks to access systems and data within their control.
Today, RIM is hanging on for its life. It is not totally down and out, but market share has absolutely turned against the company, and it is the market share that developers still consistently write toward. Blackberry 10, released in January 2013, is RIM's last chance to regain market share and stay alive. Just the other day, I was having a conversation with a cloud security vendor who also had a DLP product, and I asked about support for the BlackBerry. The answer was “Not yet, and we're not sure if we'll press ahead with the product on the BlackBerry in the future.” I asked what order the vendor developed its products for and the answer was swift: iOS (Apple), Android (Google), and Microsoft as the distant third. Interestingly enough, that's very close to the current market share leaders in order.
Global mobile phone and smartphone usage is also rising rapidly, accelerating the effects of the consumerization of IT impact on organizations around the world with 6.1 billion phone subscriptions, and approximately 1 billion of these are advanced smartphones.13
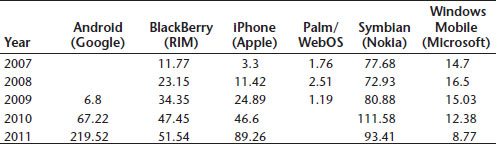
The explosive growth affects several key vendors, some of which are on the rise while others are reducing their market share percentages. Exhibit 8.2 shows mobile growth by vendor from 2007 to 2012. Google's Android devices and Apple's iPhone experienced the most significant growth.14
Exhibit 8.2 Smartphone Sales Trends
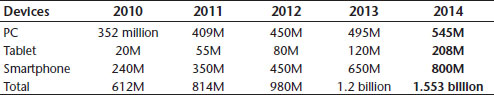
In looking at the projected worldwide sales of Internet access devices, including tablets and smartphones, between 2010 and 2014, tablets are expected to grow tenfold, from 20 million to 208 million (see Exhibit 8.3). Smartphones continue a more linear growth pattern, from 240 million devices in 2010 to a projected 800 million, a threefold increase. Laptops and computers are projected to maintain a slow and steady increase, from 352 million in 2010 to 545 million in 2014.15 What's interesting is that regardless of the significant trends in mobile computing, with smartphones leading the way as the device of choice, laptops and computers hold their own in a clear second place, on the way to 1.5 billion mobile devices by 2014.
Exhibit 8.3 Tablet vs. Smartphone vs. PC Growth Trends
When comparing the adoption of Google Android versus Apple's iOS shipments from the launch of each product, Android demonstrates the clear lead with four times adoption when compared to the iPhone.16
According to Gartner, Android operating system devices command a 72.4 percent market share as of Q3, 2012, followed by Apple's iOS (13.9 percent), RIM (5.3 percent), Bada (3 percent), Symbian (2.6 percent), and Microsoft (2.4 percent).17 IT advisory firms and research I've followed indicate that the predominance of smartphone market share, up to 90 percent, will be shared by Android devices, Apple, and Microsoft. Whether RIM can challenge Microsoft for third place is still a question, but I've invested a little bit of money, holding out hope as a BlackBerry fan.
Even toy manufactures are getting in on the mobile computing craze. Toys “R” Us unveiled a $150 tablet for children called the Tabeo that features a seven-inch screen and a Wi-Fi connection and comes preloaded with 50 kid-friendly applications.18
Behavior changes in the market are fueling the shift into mobile computing. Some recent examples are the following:
- McDonald's. The fast-food chain's customers in Paris, France, can now pay for products using a smartphone or a tablet computer, a strategy that could spread across the chain's 33,000 or more locations, if the results are positive.19
- Nordstrom. Clothing retailers like Nordstrom have plans to go completely mobile in its stores, outfitting employees with Apple iPod Touches and other devices capable of taking credit cards. Nordstrom is looking to benefit by reclaiming valuable floor space that is currently devoted to registers.20
- Grocery stores and food companies. According to the Wall Street Journal, U.S. food companies are reaching children by embedding their products and messages in “simple and enticing games for touch-screen phones and tablets.”21 Companies are deploying games such as Cookie Dough Bites Factory, Super Pretzel Factory, and Icee Maker that kids download and play, in an attempt to influence buying patterns through their parents when they go shopping. The cost associated with making a game that's downloaded hundreds of thousands of times, compared to traditional advertising runs in print and television, is allowing the companies to experiment with new methods to reach customers and prospects, potentially at a lower acquisition cost.
- Commerce. Square's card reader, which charges a small percentage per swipe, is exploding onto the mobile device market, allowing small and medium-size businesses to take credit on the go. My taxi driver now has one, and so do several small businesses in my area. However, the system is compatible only with Android and Apple's iOS, not BlackBerry. Remember market share?
These are just a few examples. There are hundreds more like them. Organizations are using technology—specifically, mobile, cloud, and social media—to increase revenue, lower costs, learn more about their customers, and reach them through the devices and channels on which they want to interact.
Forrester Research offers the following predictions on mobile computing:
- One billion consumers will have smartphones by 2016. U.S. consumers alone will have 257 million of them, along with 126 million tablet computers.
- Apple, Google, and Microsoft will account for more than 90 percent of the platforms used in smartphones and tablets worldwide.
- Carriers will compete for wireless spectrums that support 5.8 billion public Wi-Fi hot spots.
- Of the projected 257 million smartphone users in the United States, 200 million will use their personal devices at work.
- Mobile spending will reach $1.3 trillion as the mobile application market reaches $55 billion in 2016. At an average price of $2.43 per application, the growth will explode to $56 billion in 2015 as more owners tap into applications.
- Business spending on mobile projects will grow by 100 percent by 2015.22
Get ready for the continuation of a wild ride. Now let's talk about how organizations are going to manage all of these devices in the future. It's called mobile device management, or MDM.
Increasing Costs and Security
Mobile device use and security are increasing with the combination of BYOD and IT department deployment. Newer smartphones that have the ability to access rich graphical and video information are using far more bandwidth than before and increasing the usage costs as a result—potentially for both personal and corporate assets. Telecommunications carriers are deploying more sophisticated networks to handle current and anticipated growth in data, including large volumes of video as more and more people use their smartphones to watch their movies or highlights from the evening news.
Mobile devices are the primary means by which individuals access their personal and corporate e-mail, use social networking sites, videoconference with their friends, use GPS services for travel, get their news, and even still make phone calls. According to the leading Internet security firm Websense, “Your social media identity may prove more valuable to cybercriminals than your credit.”23 Since more mobile devices today are both personal and corporate, the security risks include corporate data as well as personal data. The Web statistics and highlights are troubling for security, especially for the U.S. user, for the following reasons:
- The United States is the top country for phishing attacks.
- The United States is the top country hosting malware.
- The United States is the top country for malware redirects to other sites.
- Mobile devices are “subject to threats accessing web and e-mail content, and humans remain the weakest security link in the chain.” It is reported that 51 percent of users turn off device passwords and security controls on their mobile devices.
- Since the Android platform is an open operating system where anyone can contribute an update, the environment is rife with security concerns. Of the 200,000 Android applications analyzed by Websense Labs, noticeable percentages were found to have malicious intent.
- Data loss and theft remain the primary security concerns to reduce risk with lost or stolen devices.24
Several different strategies are emerging and available on the market to help organizations deal with mobile security. Device management software, security awareness training for staff, device passwords, content filters that extend to mobile devices, and DLP technologies are some viable opportunities. No one solution or approach will guarantee the security of confidential and personal data. I'd like to focus on one of the more important tools within IT departments to make devices more secure: MDM.
Mobile Device Management
According to CIO magazine, MDM software allows organizations to mandate encryption, set and enforce policies for applications, provision and deprovision applications and data, and even wipe devices clean in the event of a lost or stolen device or a terminated employee. Many in the industry believe that MDM will evolve from controlling the device to controlling the data in a short period of time. In terms of BYOD, MDM can be invaluable to IT departments because they can set up configuration and security to deal only with information and applications that are relevant to the organization. It would be difficult to tell BYOD users that they can't use iCloud or the AppStore on their own devices. Rather, MDM lets IT control the data and applications and make sure that corporate data aren't leaking into personal applications and services like DropBox.25
For BlackBerrys, the BlackBerry Enterprise Server is the gold standard MDM application, with well over 500 individual policies for configuration and enforcement of mobile devices. Despite RIM's one-time leadership in market share and MDM, organizations adopting BYOD and other devices or operating systems need to look to solutions that can secure their information. Forrester highlights the critical functionality needed in today's MDM solutions:
- Scheduled and event-based actions.
- Real-time inventory information on installed applications, security settings, and configuration.
- Remote control.
- Self-service portals.
- Security management, including personal identification number (PIN) enforcement, passwords, data wiping, data encryption, and ActiveSync device restriction (to prevent users from accessing the corporate network without approval from IT).
- Application purchase restrictions.
- Advanced monitoring, alerts, and reporting.26
An entire book could be written on mobile device security, so I'll just conclude this section with vendor and product recommendations from Forrester Research.
Incumbents
- Good Technology
- Microsoft ActiveSync
- RIM
- Sybase
Innovators
- AirWatch
- BoxTone
- MobileIron
- Zenprise
Some of the vendors sell on-premise and hosted solutions. Not all vendors offer mobile platform support for all of the major products, including Android, iOS, BlackBerry, Symbian, Windows Mobile/CE/Phone 7, and WebOS. Please conduct your research carefully and, if possible, pilot an MDM product before you buy it.
I asked my distinguished IT executive advisory team members to provide their insights on the consumerization of IT. Please see their answers in the CIO Survey below on how they are dealing with the growing mobile trend.
- We do not allow personal devices on our infrastructure, so not at this time. It will be a discussion in our governance process as we begin to study the cost, effect, and implications of BYOD on the organization. The governance board will have to make a decision on the cost versus risk of this approach.
- Yes, it does. As people bring more devices to work and demand accessing work information from them, it is becoming a nightmare to manage those devices and the data going through them. We mainly let them access corporate mail systems at the moment through personal devices and don't have any governance methodology yet.
- Definitely. Just a few years ago, most corporate data was housed on corporate resources or devices. That is no longer true. With the need to access data from anywhere, at any time, on any device, security management has changed dramatically. However, I am not sure that the business executive's view on security has changed appropriately. While IT recognizes that corporate data are now housed on many personal devices, I believe many business leaders have a false sense of security about digital information.
- It is the consumerization not only of devices but also of services. DropBox and other commercial file-sharing technologies have made it hard for IT to safeguard data. There is little management and visibility into what is being shared and with whom. Business e-mail is often synchronized, forwarded, or downloaded to personal e-mail accounts. Remote access technologies such as Citrix allow staff to download files to personal devices. USB keys can transfer terabytes of data from business devices to personal devices.
- There may be tools to allow an organization to lock down the computing environment, but the cost to the organization in real dollars, in support costs, and in the resulting lack of flexibility will influence how much risk the organization can accept. Each organization will have to determine its own risk profile and then devise an appropriate level of governance.
- The new age of consumerization will make businesses rethink how they do business and to what degree they want to safeguard their data. This is not an IT decision. IT's role will be to help identify vulnerabilities, educate the business with regard to the risks, and then implement technical solutions to mitigate those risks. In this new world, technical solutions will need to be implemented in conjunction with strategies from the human resources, legal, and finance departments.
- Yes—the biggest issue is security. How do we ensure that personal devices being used to access corporate IT resources will not be infected with viruses and other problems as a result of personal downloads from a myriad of web sites? The way in which we control that is we have arrived at a set of devices that are approved for use: only those devices supplied and secured by the company can be used to access our resources.
- Yes, it can, unless the appropriate tools, policies, and safeguards are in place from inception. CNL was an early adopter of MDM software and has been running it for over 18 months. We're moving toward a BYOD environment, and we do support BYOD when the associates sign a release waiver and allow certain software to be installed on their devices to protect CNL's content.
- Yes. I have not moved to a BYOD model, although we are now more flexible in permitted technologies than before. I am considering a stipend-based store model where employees can procure approved technologies, which they then own, with stipends based on level and minimal retention before the devices can be recycled. Something like that could be a cost savings, minimize frivolous turnover requests, and not conflict with a BYOD strategy. In theory, it could even be used to balance individuals' spending by giving them the option to allocate their stipends as they see fit on furniture upgrades and desktop or mobile technologies, managing within a personal budget. It would be interesting to see if I could get this type of model approved and off the ground.
What Did I Do to Prepare?
I've done the following to prepare for the consumerization of IT:
- Researched adoption trends and metrics for mobile devices today and incorporated the information where appropriate into our IT standards.
- Accepted BYOD but developed some clear parameters for support and financial reimbursement.
- Developed a mobile strategy as part of the IT strategic plan.
- Developed a tablet pilot and focused time and effort on deploying mobile applications developed specifically for mobile devices.
- Investigated MDM tools and forged ahead on implementing a solution.
- Clarified support and SLAs for corporate and personal devices.
- Reshaped the organization's security policy and developed a new incident response plan (IRP) that includes provisions for the loss or theft of sensitive data.
- Retained options for higher levels of security, including DLP.
- Researched MDM solutions before deploying a pilot and installing.
Recommendations
My recommendations for this chapter are as follows:
- Working with your general counsel, develop a risk profile, and adopt the appropriate technologies and policies to meet that profile. Organizations that are willing to consider personal devices and BYOD should do so after a full analysis of the costs and risks. The policy communication should be done through the general counsel and the CIO. Risk is a legal decision, not an IT one. The CIO is responsible for implementing controls to meet the organization's risk profile, not to define it. That's the legal department's job.
- Develop a mobile strategy as part of your IT strategic plan.
- Carefully craft or modify your tablet strategy as part of your mobile strategy and be sure to clarify any intersections with a BYOD plan. I believe laptop-hybrid tablets will emerge as viable options for businesses and larger organizations that are concerned with manageability, security, performance, and, most important, compatibility with legacy and supported applications. Notables include Apple iPad, Dell XPS, and Microsoft Surface. As others enter the market, evaluate them carefully. A safer strategy may end up being a multidevice standard to satisfy user demand while maintaining device management flexibility.
- Develop a security strategy and wrap it around mobile devices (corporate ones and personal ones that contain corporate data). Update your security policies and procedures as necessary and train your staff on the new security risks, including mobile. Security should move from the device to the data.
- Research and deploy MDM tools as part of the toolbox for managing mobile devices, including personal assets not owned by the organization. AirWatch, BoxTone, MobileIron, and Zenprise are top products. Good Technology, Microsoft ActiveSync, RIM, and Sybase are notables. Some of the vendors sell on-premise and hosted solutions. Evaluate what's best for you and your organization. Not all vendors offer mobile platform support for all of the major products, including Android, iOS, BlackBerry, Symbian, Windows Mobile/CE/Phone 7 and WebOS, so check your research carefully and, if possible, pilot an MDM product before you buy it.
- Clarify your support for personal devices and stick to it. Don't set an SLA expectation that you can't meet, especially if you're limited on the number of IT resources to provide tier 1 and tier 2 support.
- Look for simplified internal policies on budgeting and expense allocation for BYOD. There are easy ways and hard ways to do this. The hard ones will reveal themselves through a clear increase in time, labor, and the number of transactions processed by accounting.
- Consider DLP software to alert the organization's key departments (legal, financial, human resources, and IT) about the loss or theft of corporate information—intentionally or unintentionally. Mobile computing is a fast-growing security problem for CIOs and CISOs today.
- Forrester Research and other IT advisory firms have some great research on the usefulness of tablets in the enterprise and whether they can replace or augment the computing gear provided and supported by the IT department. The growth numbers of tablets and smartphones combined with the expected resilience of the laptop computer in the future indicates that there's no holy grail device that will do everything. Forrester Research has some super reports that expose the real and valuable use of tablets like the iPad, their costs, and whether they will be the main device carried by staffers or just one of several, carried along with a smartphone and a laptop. I very often see employees with three devices each: a personal smartphone, a corporate laptop, and a mix of personal and corporate tablets. There is a real cost to having that many devices in the workplace. There's also a higher security risk to loss of confidential data, especially when all of these devices, corporate and personal, are connected to an organization's technical systems.
I'll leave it at that. The research will prove to be some great reading for those who love to jump onto new technologies but not necessarily to have to pay to secure and support them.
Notes
1. Doris M. Smith, Inspiration Quotes, www.inspirational-quotes.info/people.html (accessed October 6, 2012).
2. Ted Schadler, “Consumerization Drives Smartphone Proliferation,” Forrester Research, December 2, 2011.
3. Ibid.
4. Ibid.
5. Ibid.
6. Tom Kaneshige, “CIO Challenge with BYOD: Don't Fall Down the Rabbit Hole,” CIO, May 17, 2012, www.cio.com/article/print/706579 (accessed July 20, 2012).
7. Tony Bradley, “Pros and Cons of BYOD (Bring Your Own Device), CIO, December 21, 2011, www.cio.com/article/print/696971 (accessed July 20, 2012).
8. Ibid.
9. Ibid.
10. Ibid.
11. Ibid.
12. Matt Hamblen, “Consumerization Trend Driving IT Shops Crazy, Gartner Analyst Says,” CIO, May 2, 2012, www.cio.com/article/print/705448 (accessed July 20, 2012).
13. Mary Meeker, “Internet Trends—D10 Conference,” Kleiner, Perkins, Caufield, Byers (KPCB), May 30, 2012, www.kpcb.com/insights/2012-internet-trends (accessed September 1, 2012).
14. Jyoti Patodia, “It's Raining Tablets and Smartphones,” Motley Fool, September 11, 2012, beta.fool.com/jyotiadvisor/2012/09/11/its-raining-tablets-smartphones/11794/ (accessed September 12, 2012).
15. Ibid.
16. Meeker, “Internet Trends—D10 Conference.”
17. Harsh Chauhan, “Which Also-Ran Will Run the Fastest in the Smartphone Race?” The Motley Fool, beta.fool.com/techjunk13/2013/01/02/which-also-ran-will-run-fastest-smartphone-race/20414/?logvisit=y&published=2013-01-02&source=eptcnnlnk0000001 (accessed January 3, 2013).
18. Julianne Pepitone, “Toys R Us Unveils $150 Tablet for Kids,” CNN Money, September 10, 2012, money.cnn.com/2012/09/10/technology/toys-r-us-tablet-kids/index.html (accessed September 9, 2012).
19. Doug Gross, “Fries from Your Phone: McDonald's Testing Mobile Payment App,” CNN, (August 20, 2012), www.cnn.com/2012/08/20/tech/mobile/mcdonalds-mobile-payments/index.html (accessed August 20, 2012).
20. Rolfe Winkler, “Mobile Devices Hit Retail Pay Dirt,” Wall Street Journal, September 18, 2012, C12.
21. Anton Troianovski, “Hook Kids on Mobile Games,” Wall Street Journal, September 18, 2012, A1.
22. Ted Schadler and John C. McCarthy, “Mobile Is the New Face of Engagement,” Forrester Research, February 13, 2012.
23. “Websense Threat Report 2012,” Websense Inc., 13.
24. Ibid, p. 28.
25. Thor Osavsrud, “For BYOD Best Practices, Secure Data, Not Devices,” CIO, July 17, 2012, www.cio.com/article/print/711258 (accessed July 20, 2012).
26. Christian Kane and Benjamin Gray, “Market Overview: On-Premises Mobile Device Management Solutions,” Forrester Research, January 3, 2012.