CHAPTER 13
INSTALLATION AND OPERATIONS
This chapter examines the activities needed to install an information system and successfully convert an organization to using it. It also discusses post-implementation activities, such as system support, system maintenance, and project assessment. Installing the system and making it available for use from a technical perspective is relatively straightforward. However, the training and organizational issues surrounding the installation are more complex and challenging because they focus on people, not computers.
OBJECTIVES
- Be familiar with the system installation process
- Understand different types of conversion strategies and when to use them
- Understand several techniques for managing change
- Be familiar with post-installation processes
CHAPTER OUTLINE
- Introduction
- Cultural Issues and Information Technology Adoption
- Conversion
- Change Management
- Post-Implementation Activities
- Applying the Concepts at CD Selections
- Summary
INTRODUCTION
It must be remembered that there is nothing more difficult to plan, more doubtful of success, nor more dangerous to manage than the creation of a new system. For the initiator has the animosity of all who would profit by the preservation of the old institution and merely lukewarm defenders in those who would gain by the new.
—Niccolò Machiavelli, The Prince, 1513
FIGURE 13-1 Implementing Change
Although written almost 500 years ago, Machiavelli's comments are still true today. Managing the change to a new system—whether it is computerized or not—is one of the most difficult tasks in any organization. Because of the challenges involved, most organizations begin developing their conversion and change management plans while the programmers are still developing the software. Leaving conversion and change management planning to the last minute is a recipe for failure.
In many ways, using a computer system or set of work processes is much like driving on a dirt road. Over time, with repeated use, the road begins to develop ruts in the most commonly used parts of the road. Although these ruts show where to drive, they make change difficult. As people use a computer system or set of work processes, those systems or work processes begin to become habits or norms; people learn them and become comfortable with them. These systems or work processes then begin to limit people's activities and make it difficult for them to change because they begin to see their jobs in terms of these processes rather than of the final business goal of serving customers.
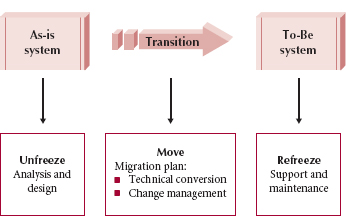
One of the earliest models for managing organizational change was developed by Kurt Lewin.1 Lewin argued that change is a three-step process: unfreeze, move, refreeze (Figure 13-1). First, the project team must unfreeze the existing habits and norms (the as-is system) so that change is possible. Most of system development to this point has laid the groundwork for unfreezing. Users are aware of the new system being developed, some have participated in an analysis of the current system (and so are aware of its problems), and some have helped design the new system (and so have some sense of the potential benefits of the new system). These activities have helped to unfreeze the current habits and norms.
The second step is to help the organization move to the new system via a migration plan. The migration plan has two major elements. One is technical, which includes how the new system will be installed and how data in the as-is system will be moved into the to-be system; this is discussed in the conversion section of this chapter. The second component is organizational, which includes helping users understand the change and motivating them to adopt it; this is discussed in the change management section of this chapter.
The third step is to refreeze the new system as the habitual way of performing the work processes—ensuring that the new system successfully becomes the standard way of performing the business function it supports. This refreezing process is a key goal of the postimplementation activities discussed in the final section of this chapter. By providing ongoing support for the new system and immediately beginning to identify improvements for the next version of the system, the organization helps solidify the new system as the new habitual way of doing business. Post-implementation activities include system support, which means providing help desk and telephone support for users with problems; system maintenance, which means fixing bugs and improving the system after it has been installed; and project assessment, evaluating the project to identify what went well and what could be improved for the next system development project.
Change management is the most challenging of the three components because it focuses on people, not technology, and because it is the one aspect of the project that is the least controllable by the project team. Change management means winning the hearts and minds of potential users and convincing them that the new system actually provides value.
Maintenance is the most costly aspect of the installation process, because the cost of maintaining systems usually greatly exceeds the initial development costs. It is not unusual for organizations to spend 60 to 80 percent of their total IS development budget on maintenance. Although this might sound surprising initially, think about the software you use. How many software packages do you use that are the very first version? Most commercial software packages become truly useful and enter widespread use only in their second or third version. Maintenance and continual improvement of software is ongoing, whether it is a commercially available package or software developed in house. Would you buy software if you knew that no new versions were going to be produced? Of course, commercial software is somewhat different from custom in-house software used by only one company, but the fundamental issues remain.
Project assessment is probably the least commonly performed part of system development but is perhaps the one that has the most long-term value to the IS department. Project assessment enables project team members to step back and consider what they did right and what they could have done better. It is an important component in the individual growth and development of each member of the team, because it encourages team members to learn from their successes and failures. It also enables new ideas or new approaches to system development to be recognized, examined, and shared with other project teams to improve their performance.
In this chapter, we describe deploying the new system through the process of transitioning from the old to the new system (i.e., conversion). Next, we describe issues related to managing the changes necessary to adapt to the new business processes. Finally, we describe issues related to placing the system into production (i.e., post-implementation activities). However, before we address these issues, we describe how the cultural issues affect the deployment of a new system.
CULTURAL ISSUES AND INFORMATION TECHNOLOGY ADOPTION2
Cultural issues are one of the things that are typically identified as at least partially to blame when there is a failure in an organization. Cultural issues have been studied at both organizational and national levels. In previous chapters we discussed the effect that cultural issues can have on designing the human–computer interaction and physical architecture layers (see Chapters 10 and 11) and the management of programmers (Chapter 12). The cultural dimensions identified by Hall and Hofstede included speed of messages, context, time, power distance, uncertainty avoidance, individualism versus collectivism, masculinity versus femininity, and long- versus short-term orientation.3 In this chapter, we describe how these dimensions can affect the successful deployment of an information system that supports a global information supply chain.
Hall's first dimension, speed of messages, has implications for the development of documentation (see Chapter 12) and training approaches (see later in this chapter). In a culture that values “deep” content, so that members of the culture can take their time to thoroughly understand the new system, simply providing an online help system is not going to be sufficient to ensure the successful adoption of the new information system. However, in a culture that prefers “fast” messages, an online help system could be sufficient.
Hall's second dimension, context, also affects the adoption and deployment of a new system. In high-context cultures, it is expected that the new information system will be placed into the entire context of the enterprise wide system. Members of this type of society expect to be able to understand exactly where the system fits into the firm's overall picture. Again, like the speed of messages dimension, this affects the training approach used and the documentation developed.
Hall's third dimension, time, can also effect the adoption and deployment of a new system. In a polychronic time culture, the training could need to be spread out over a longer period of time, when compared to a monochronic time culture. In a monochromic time culture, interruptions would be considered rude. Consequently, training could be accomplished in a small set of intense sessions. However, with a polychronic time culture, because interruptions may occur frequently, maximum flexibility in setting up the training sessions may be necessary.
Hofstede's first dimension, power distance, addresses how power issues are dealt with in the culture. For example, if a superior in an organization has an incorrect belief about an important issue, can a subordinate point out this error? In some cultures, the answer is a resounding no. Consequently, this dimension could have major ramifications for the successful deployment of an information system. For example, in a culture with a high power distance, the deployment of a new information system is dependent on the impression of the most important stakeholder (see Chapter 2). Therefore, much care must be taken to ensure that this stakeholder is pleased with the system. Otherwise, it might never be used.
Hofstede's second dimension, uncertainty avoidance, is based on the degree to which the culture depends on rules for direction, how well individuals in the culture handle stress, and the importance of employment stability. For example, in a high-uncertainty-avoidance culture, the use of detailed procedures manuals (see Chapter 12) and good training (see later in this chapter) can reduce the uncertainty in adopting the new system.
Hofstede's third dimension, individualism versus collectivism, is based on the level of emphasis the culture places on the individual or the collective. The relationship between the individual and the group is important for the success of an information system. Depending on the culture's orientation, the success of an information system being transitioned into production can depend on whether the focus of the information system will benefit the individual or the group.
Hofstede's fourth dimension, masculinity versus femininity, addresses how well masculine and feminine characteristics are valued by the culture. Some of the differences that could affect the adoption of an information system include employee motivational issues. In a masculine culture, motivation would be based on advancement, earnings, and training, whereas in a feminine culture, motivations would include friendly atmosphere, physical conditions, and cooperation. Depending on how the culture views this dimension, different motivations might need to be used to increase the likelihood of the information system being successfully deployed.
The fifth dimension, long- versus short-term orientation, deals with how the culture views the past and the future. In East Asia, long-term thinking is highly respected, whereas in North America and Europe, short-term profits and the current stock price seem to be the only things that matter. Based on this dimension, all the political concerns raised previously in this text become very important. For example, if the local culture views success only in a short-term manner, then any new information system that is deployed to support one department of an organization may give that department a competitive advantage over other departments in the short run. If only short-run measures are used to judge the success of a department, then it would be in the interest of the other departments to fight the successful deployment of the information system. However, if a longer-run perspective is the norm, then the other departments could be convinced to support the new information system because they could have new supportive information systems in the future.
Obviously, when reviewing these dimensions, we can see they interact with each other. The most important thing to remember from an IT perspective is that we must be careful not to view the local user community through our eyes; in a global economy, we must take into consideration the local cultural concerns for the information system to be deployed in a successful manner.
CONVERSION4
Conversion is the technical process by which a new system replaces an old system. Users are moved from using the as-is business processes and computer programs to the to-be business processes and programs. The migration plan specifies what activities will be performed when and by whom and includes both technical aspects (such as installing hardware and software and converting data from the as-is system to the to-be system) and organizational aspects (such as training and motivating the users to embrace the new system). Conversion refers to the technical aspects of the migration plan.
There are three major steps to the conversion plan before commencement of operations: Install hardware, install software, and convert data (Figure 13-2). Although it may be possible to do some of these steps in parallel, usually they must be done sequentially at any one location.
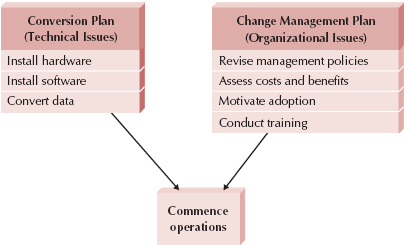
FIGURE 13-2 Elements of a Migration Plan
The first step in the conversion plan is to buy and install any needed hardware. In many cases, no new hardware is needed, but sometimes the project requires new hardware such as servers, client computers, printers, and networking equipment. It is critical to work closely with vendors who are supplying needed hardware and software to ensure that the deliveries are coordinated with the conversion schedule so that the equipment is available when it is needed. Nothing can stop a conversion plan in its tracks as easily as the failure of a vendor to deliver needed equipment.
Once the hardware is installed, tested, and certified as being operational, the second step is to install the software. This includes the to-be system under development and, sometimes, additional software that must be installed to make the system operational. At this point, the system is usually tested again to ensure that it operates as planned.
The third step is to convert the data from the as-is system to the to-be system. Data conversion is usually the most technically complicated step in the migration plan. Often, separate programs must be written to convert the data from the as-is system to the new formats required in the to-be system and store it in the to-be system files and databases. This process is often complicated by the fact that the files and databases in the to-be system do not exactly match the files and databases in the as-is system (e.g., the to-be system may use several tables in a database to store customer data that were contained in one file in the as-is system). Formal test plans are always required for data conversion efforts (see Chapter 12).
Conversion can be thought of along three dimensions: the style in which the conversion is done (conversion style), what location or work groups are converted at what time (conversion location), and what modules of the system are converted at what time (conversion modules). Figure 13-3 shows the potential relationships among these three dimensions.
Conversion Style
The conversion style is the way users are switched between the old and new systems. There are two fundamentally different approaches to the style of conversion: direct conversion and parallel conversion.
Direct Conversion With direct conversion (sometimes called cold turkey, big bang, or abrupt cutover), the new system instantly replaces the old system. The new system is turned on and the old system is immediately turned off. This is the approach that we are likely to use when we upgrade commercial software (e.g., Microsoft Word) from one version to another; we simply begin using the new version and stop using the old version.
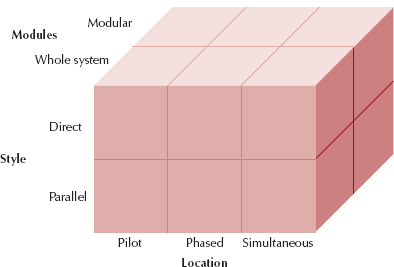
FIGURE 13-3 Conversion Strategies
Direct conversion is the simplest and most straightforward. However, it is the most risky because any problems with the new system that have escaped detection during testing can seriously disrupt the organization.
Parallel Conversion With parallel conversion, the new system is operated side by side with the old system; both systems are used simultaneously. For example, if a new accounting system is installed, the organization enters data into both the old system and the new system and then carefully compares the output from both systems to ensure that the new system is performing correctly. After some time period (often one to two months) of parallel operation and intense comparison between the two systems, the old system is turned off and the organization continues using the new system.
This approach is more likely to catch any major bugs in the new system and prevent the organization from suffering major problems. If problems are discovered in the new system, the system is simply turned off and fixed and then the conversion process starts again. The problem with this approach is the added expense of operating two systems that perform the same function.
Conversion Location
Conversion location refers to the parts of the organization that are converted when the conversion occurs. Often, parts of the organization are physically located in different offices (e.g., Toronto, Atlanta, Los Angeles). In other cases, location refers to different organizational units located in different parts of the same office complex (e.g., order entry, shipping, purchasing). There are at least three fundamentally different approaches to selecting the way different organizational locations are converted: pilot conversion, phased conversion, and simultaneous conversion.
Pilot Conversion With a pilot conversion, one or more locations or units or work groups within a location are selected to be converted first as part of a pilot test. The locations participating in the pilot test are converted (using either direct or parallel conversion). If the system passes the pilot test, then the system is installed at the remaining locations (again using either direct or parallel conversion).
Pilot conversion has the advantage of providing an additional level of testing before the system is widely deployed throughout the organization, so that any problems with the system affect only the pilot locations. However, this type of conversion obviously requires more time before the system is installed at all organizational locations. Also, it means that different organizational units are using different versions of the system and business processes, which can make it difficult for them to exchange data.
Phased Conversion With phased conversion, the system is installed sequentially at different locations. A first set of locations is converted, then a second set, then a third set, and so on, until all locations are converted. Sometimes there is a deliberate delay between the different sets (at least between the first and the second), so that any problems with the system are detected before too much of the organization is affected. In other cases, the sets are converted back to back so that as soon as those converting one location have finished, the project team moves to the next and continues the conversion.
Phased conversion has the same advantages and disadvantages of pilot conversion. In addition, it means that fewer people are required to perform the actual conversion (and any associated user training) than if all locations were converted at once.
CONCEPTS IN ACTION: 13-A Too Much Paper (Part 1)
The South Dakota Department of Worker's Compensation was sinking under a load of paper files. As a state agency that oversees that employees are treated fairly when they are injured on the job, the agency had a plethora of paper files and filing cabinets. If a person (or company) called to see the status of an injury claim, the clerk who received the call would have to take a message, get the paper file, review the status, and call the person back. Files were stored in huge filing cabinets and were entered by year and case number (e.g., the 415th person injured in 2008 would be in a file numbered 08-415). But most people did not remember their file number and would give a name, address, and date of injury. The clerk would look in a spiral notebook for the last name around the date that was given and then find the file number to retrieve the folder. Some folders were small—possibly a minor cut or minor injury that was taken care of quickly and the employee was back to work. Other folders could be very large, with medical reports from several doctors verifying the extent of the injury (such as an arm amputation). A digital solution was suggested; reports could be submitted online using a secure website. Medical reports could be submitted electronically, either as a.pdf file or as a faxed digital file. This solution would also mean that the clerk taking the phone call could query the database by the person's name and access the information in a matter of seconds.
Questions
- The digital solution was going to change the work process of filing injury claims, interacting with people who filed the claims (or companies) wanting to see the status of the claim, and with the process of claims. What might this mean from a work-flow analysis?
- In many ways, this was a business process reengineering solution. The proposal was to throw out the old process for a completely electronic version. What might a systems analyst do in the data-gathering stage?
Simultaneous Conversion Simultaneous conversion, as the name suggests, means that all locations are converted at the same time. The new system is installed and made ready at all locations; at a preset time, all users begin using the new system. Simultaneous conversion is often used with direct conversion, but it can also be used with parallel conversion.
Simultaneous conversion eliminates problems with having different organizational units using different systems and processes. However, it also means that the organization must have sufficient staff to perform the conversion and train the users at all locations simultaneously.
Conversion Modules
Although it is natural to assume that systems are usually installed in their entirety, this is not always the case.
Whole-System Conversion A whole-system conversion, in which the entire system is installed at one time, is the most common. It is simple and the easiest to understand. However, if the system is large and/or extremely complex (e.g., an enterprise resource-planning system such as SAP or PeopleSoft), the whole system can prove too difficult for users to learn in one conversion step.
Modular Conversion When the modules5 within a system are separate and distinct, organizations sometimes choose to convert to the new system one module at a time—that is, using modular conversion. Modular conversion requires special care in developing the system (and usually adds extra cost). Each module either must be written to work with both the old and new systems or object wrappers (see Chapter 7) must be used to encapsulate the old system from the new. When modules are tightly integrated, this is very challenging and therefore is seldom done. However, when there is only a loose association between modules, module conversion is easier. For example, consider a conversion from an old version of Microsoft Office to a new version. It is relatively simple to convert from the old version of Word to the new version without simultaneously having to change from the old to the new version of Microsoft Excel.
Modular conversion reduces the amount of training required to begin using the new system. Users need training only in the new module being implemented. However, modular conversion does take longer and has more steps than does the whole-system process.
Selecting the Appropriate Conversion Strategy
Each of the three dimensions in Figure 13-3 is independent, so that a conversion strategy can be developed to fit in any one of the boxes in this figure. Different boxes can also be mixed and matched into one conversion strategy. For example, one commonly used approach is to begin with a pilot conversion of the whole system using parallel conversion in a handful of test locations. Once the system has passed the pilot test at these locations, it is then installed in the remaining locations using phased conversion with direct cutover. There are three important factors to consider in selecting a conversion strategy: risk, cost, and the time required (Figure 13-4).
Risk After the system has passed a rigorous battery of unit, system, integration, and acceptance testing, it should be bug free…maybe. Because humans make mistakes, nothing built by people is ever perfect. Even after all these tests, there might still be a few undiscovered bugs. The conversion process provides one last step in which to catch these bugs before the system goes live and the bugs have the chance to cause problems.
Parallel conversion is less risky than is direct conversion because it has a greater chance of detecting bugs that have gone undiscovered in testing. Likewise, pilot conversion is less risky than is phased conversion or simultaneous conversion because if bugs do occur, they occur in pilot test locations whose staff are aware that they might encounter bugs. Because potential bugs affect fewer users, there is less risk. Likewise, converting a few modules at a time lowers the probability of a bug because there is more likely to be a bug in the whole system than in any given module.
How important the risk is depends on the system being implemented—the combination of the probability that bugs remain undetected in the system and the potential cost of those undetected bugs. If the system has indeed been subjected to extensive methodical testing, including alpha and beta testing, then the probability of undetected bugs is lower than if the testing was less rigorous. However, there still might have been mistakes made in the analysis process, so that although there might be no software bugs, the software might fail to properly address the business needs.
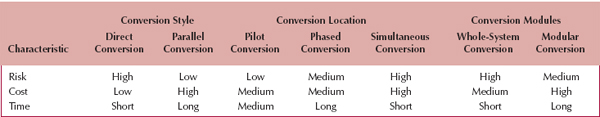
FIGURE 13-4 Characteristics of Conversion Strategies
Assessing the cost of a bug is challenging, but most analysts and senior managers can make a reasonable guess at the relative cost of a bug. For example, the cost of a bug in an automated stock market trading program or a heart–lung machine keeping someone alive is likely to be much greater than a bug in a computer game or word processing program. Therefore, risk is likely to be a very important factor in the conversion process if the system has not been as thoroughly tested as it might have been or if the cost of bugs is high. If the system has been thoroughly tested or the cost of bugs is not that high, then risk becomes less important to the conversion decision.
Cost As might be expected, different conversion strategies have different costs. These costs can include things such as salaries for people who work with the system (e.g., users, trainers, system administrators, external consultants), travel expenses, operation expenses, communication costs, and hardware leases. Parallel conversion is more expensive than direct cutover because it requires that two systems (the old and the new) be operated at the same time. Employees must then perform twice the usual work because they have to enter the same data into both the old and the new systems. Parallel conversion also requires the results of the two systems to be completely crosschecked to make sure there are no differences between the two, which entails additional time and cost.
Pilot conversion and phased conversion have somewhat similar costs. Simultaneous conversion has higher costs because more staff are required to support all the locations as they simultaneously switch from the old to the new system. Modular conversion is more expensive than whole-system conversion because it requires more programming. The old system must be updated to work with selected modules in the new system, and modules in the new system must be programmed to work with selected modules in both the old and new systems.
Time The final factor is the amount of time required to convert between the old and the new system. Direct conversion is the fastest because it is immediate. Parallel conversion takes longer because the full advantages of the new system do not become available until the old system is turned off. Simultaneous conversion is fastest because all locations are converted at the same time. Phased conversion usually takes longer than pilot conversion because once the pilot test is complete all remaining locations are usually (but not always) converted simultaneously. Phased conversion proceeds in waves, often requiring several months before all locations are converted. Likewise, modular conversion takes longer than whole-system conversion because the models are introduced one after another.
YOUR TURN: 13-1 Developing a Conversion Plan
Suppose you are leading the conversion from one word processor to another at your university. Develop a conversion plan (i.e., technical issues only). You have also been asked to develop a conversion plan for the university's new Web-based course registration system. How would the second conversion plan be similar to and different from the one you developed for the word processor?
CONCEPTS IN ACTION: 13-B U.S. Army Installation Support
Throughout the 1960s, 1970s, and 1980s, the U.S. Army automated its installations (army bases, in civilian terms). Automation was usually a local effort at each of the more than 100 bases. Although some bases had developed software together (or borrowed software developed at other bases), each base often had software that performed different functions or performed the same function in different ways. In 1989, the army decided to standardize the software so that the same software would be used everywhere. This would greatly reduce software maintenance and also reduce training when soldiers were transferred between bases.
The software took four years to develop. The system was quite complex, and the project manager was concerned that there was a high risk that not all requirements of all installations had been properly captured. Cost and time were less important because the project had already run four years and cost $100 million.
Therefore, the project manager chose a modular pilot conversion using parallel conversion. The manager selected seven installations, each representing a different type of army installation (e.g., training base, arsenal, depot) and began the conversion. All went well, but several new features were identified that had been overlooked during the analysis, design, and construction. These were added and the pilot testing resumed. Finally, the system was installed in the rest of the army installations using a phased direct conversion of the whole system.
—Alan Dennis
Questions
- Do you think the conversion strategy was appropriate?
- Regardless of whether you agree, what other conversion strategy could have been used?
CHANGE MANAGEMENT6
In the context of a systems development project, change management is the process of helping people to adopt and adapt to the to-be system and its accompanying work processes without undue stress. There are three key roles in any major organizational change. The first is the sponsor of the change—the person who wants the change. This person is the business sponsor who first initiated the request for the new system (see Chapter 2). Usually, the sponsor is a senior manager of the part of the organization that must adopt and use the new system. It is critical that the sponsor be active in the change management process because a change that is clearly being driven by the sponsor, not by the project team or the IS organization, has greater legitimacy. The sponsor has direct management authority over those who adopt the system.
The second role is that of the change agent—the person(s) leading the change effort. The change agent, charged with actually planning and implementing the change, is usually someone outside of the business unit adopting the system and therefore has no direct management authority over the potential adopters. Because the change agent is an outsider, he or she has less credibility than do the sponsor and other members of the business unit. After all, once the system has been installed, the change agent usually leaves and thus has no ongoing impact.
The third role is that of potential adopters, or targets of the change—the people who actually must change. These are the people for whom the new system is designed and who will ultimately choose to use or not use the system.
In the early days of computing, many project teams simply assumed that their job ended when the old system was converted to the new system at a technical level. The philosophy was “build it and they will come.” Unfortunately, that happens only in the movies. Resistance to change is common in most organizations. Therefore, the change management plan is an important part of the overall installation plan that glues together the key steps in the change management process. Successful change requires that people want to adopt the change and are able to adopt the change. The change management plan has four basic steps: revising management policies, assessing the cost and benefit models of potential adopters, motivating adoption, and enabling people to adopt through training (see Figure 13-2). However, before we can discuss the change management plan, we must first understand why people resist change.
Understanding Resistance to Change7
People resist change—even change for the better—for very rational reasons. What is good for the organization is not necessarily good for the people who work there. For example, consider an order-processing clerk who used to receive orders to be shipped on paper shipping documents but now uses a computer to receive the same information. Rather than typing shipping labels with a typewriter, the clerk now clicks on the print button on the computer and the label is produced automatically. The clerk can now ship many more orders each day, which is a clear benefit to the organization. The clerk, however, probably doesn't really care how many packages are shipped. His or her pay doesn't change; it's just a question of which the clerk prefers to use, a computer or typewriter. Learning to use the new system and work processes—even if the change is minor—requires more effort than continuing to use the existing, well-understood system and work processes.
So why do people accept change? Simply put, every change has a set of costs and benefits associated with it. If the benefits of accepting the change outweigh the costs of the change, then people change. And sometimes the benefit of change is avoidance of the pain that might be experienced if the change were not adopted (e.g., if you don't change, you are fired, so one of the benefits of adopting the change is that you still have a job).
In general, when people are presented with an opportunity for change, they perform a cost–benefit analysis (sometime consciously, sometimes subconsciously) and decide the extent to which they will embrace and adopt the change. They identify the costs of and benefits from the system and decide whether the change is worthwhile. However, it is not that simple, because most costs and benefits are not certain. There is some uncertainty as to whether a certain benefit or cost will actually occur; so both the costs of and benefits from the new system need to be weighted by the degree of certainty associated with them (Figure 13-5). Unfortunately, most humans tend to overestimate the probability of costs and underestimate the probability of benefits.
There are also costs and, sometimes, benefits associated with the actual transition process itself. For example, suppose we found a nicer house or apartment than our current one. Even if we liked it better, we might decide not to move simply because the cost of moving outweighed the benefits from the new house or apartment itself. Likewise, adopting a new computer system might require us to learn new skills, which could be seen as a cost to some people or as a benefit to others, if they perceived that those skills would somehow provide other benefits beyond the use of the system itself. Once again, any costs and benefits from the transition process must be weighted by the certainty with which they will occur (see Figure 13-5).

FIGURE 13-5 The Costs and Benefits of Change
Taken together, these two sets of costs and benefits (and their relative certainties) affect the acceptance of change or resistance to change that project teams encounter when installing new systems in organizations. The first step in change management is to understand the factors that inhibit change—the factors that affect the perception of costs and benefits and certainty that they will be generated by the new system. It is critical to understand that the real costs and real benefits are far less important than the perceived costs and perceived benefits. People act on what they believe to be true, not on what is true. Thus, any understanding of how to motivate change must be developed from the viewpoint of the people expected to change, not from the viewpoint of those leading the change.
CONCEPTS IN ACTION: 13-C Understanding Resistance to a DSS
One of the first commercial software packages I developed was a DSS to help schedule orders in a paper mill. The system was designed to help the person who scheduled orders decide when to schedule particular orders to reduce waste in the mill. This was a very challenging problem—so challenging, in fact, that it usually took the scheduler a year or two to really learn how to do the job well.
The software was tested by a variety of paper mills over the years and always reduced the amount of waste, usually by about 25 percent but sometimes by 75 percent when a scheduler new to the job was doing the scheduling. Although we ended up selling the package to most paper mills that tested it, we usually encountered significant resistance from the person doing the scheduling (except when the scheduler was new to the job and the package clearly saved a significant amount). At the time, I assumed that the resistance to the system was related to the amount of waste reduced: the less waste reduced, the more resistance because the payback analysis showed it took longer to pay for the software.
—Alan Dennis
Questions
- What is another possible explanation for the different levels of resistance encountered at different mills?
- How might this be addressed?
Revising Management Policies
The first major step in the change management plan is to change the management policies that were designed for the as-is system to new management policies designed to support the to-be system. Management policies provide goals, define how work processes should be performed, and determine how organizational members are rewarded. No computer system will be successfully adopted unless management policies support its adoption. Many new computer systems bring changes to business processes; they enable new ways of working. Unless the policies that provide the rules and rewards for those processes are revised to reflect the new opportunities that the system permits, potential adopters cannot easily use it.
Management has three basic tools for structuring work processes in organizations.8 The first are the standard operating procedures (SOPs) that become the habitual routines for how work is performed. The SOPs are both formal and informal. Formal SOPs define proper behavior. Informal SOPs are the norms that have developed over time for how processes are actually performed. Management must ensure that the formal SOPs are revised to match the to-be system. The informal SOPs will then evolve to refine and fill in details absent in the formal SOPs.
The second aspect of management policy is defining how people assign meaning to events. What does it mean to “be successful” or “do good work”? Policies help people understand meaning by defining measurements and rewards. Measurements explicitly define meaning because they provide clear and concrete evidence about what is important to the organization. Rewards reinforce measurements because “what gets measured gets done” (an overused but accurate saying). Measurements must be carefully designed to motivate desired behavior. The IBM credit example (Your Turn 3-2) illustrates the problem when flawed measurements drive improper behavior (when the credit analysts became too busy to handle credit requests, they would find nonexistent errors so they could return them unprocessed).
A third aspect of management policy is resource allocation. Managers can have clear and immediate impacts on behavior by allocating resources. They can redirect funds and staff from one project to another, create an infrastructure that supports the new system, and invest in training programs. Each of these activities has both a direct and symbolic effect. The direct effect comes from the actual reallocation of resources. The symbolic effect shows that management is serious about its intentions. There is less uncertainty about management's long-term commitment to a new system when potential adopters see resources being committed to support it.
YOUR TURN: 13-2 Standard Operating Procedures
Identify and explain three standard operating procedures for the course in which you are using this book. Discuss whether they are formal or informal.
Assessing Costs and Benefits
The next step in developing a change management plan is to develop two clear and concise lists of costs and benefits provided by the new system (and the transition to it) compared with the as-is system. The first list is developed from the perspective of the organization, which should flow easily from the business case developed during the feasibility study and refined over the life of the project (see Chapter 2). This set of organizational costs and benefits should be distributed widely so that everyone expected to adopt the new system should clearly understand why the new system is valuable to the organization.
The second list of costs and benefits is developed from the viewpoints of the different potential adopters expected to change, or stakeholders in the change. For example, one set of potential adopters may be the frontline employees, another may be the first-line supervisors, and yet another might be middle management. Each of these potential adopters, or stakeholders, may have a different set of costs and benefits associated with the change—costs and benefits that can differ widely from those of the organization. In some situations, unions may be key stakeholders that can make or break successful change.
Many systems analysts naturally assume that frontline employees are the ones whose set of costs and benefits are the most likely to diverge from those of the organization and thus are the ones who most resist change. However, they usually bear the brunt of problems with the current system. When problems occur, they often experience them firsthand. Middle managers and first-line supervisors are the most likely to have a divergent set of costs and benefits and, therefore, resist change because new computer systems often change how much power they have. For example, a new computer system may improve the organization's control over a work process (a benefit to the organization) but reduce the decision-making power of middle management (a clear cost to middle managers).
An analysis of the costs and benefits for each set of potential adopters, or stakeholders, will help pinpoint those who will likely support the change and those who might resist the change. The challenge at this point is to try to change the balance of the costs and benefits for those expected to resist the change so that they support it (or at least do not actively resist it). This analysis could uncover some serious problems that have the potential to block the successful adoption of the system. It may be necessary to reexamine the management policies and make significant changes to ensure that the balance of costs and benefits is such that important potential adopters are motivated to adopt the system.
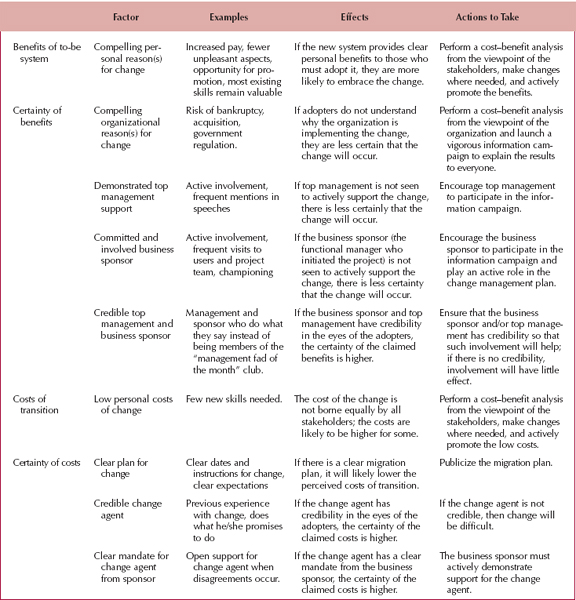
Figure 13-6 summarizes some of the factors that are important to successful change. The first and most important reason is a compelling personal reason to change. All change is made by individuals, not organizations. If there are compelling reasons for the key groups of individual stakeholders to want the change, then the change is more likely to be successful. Factors such as increased salary, reduced unpleasantness, and—depending on the individuals—opportunities for promotion and personal development can be important motivators. However, if the change makes current skills less valuable, individuals might resist the change because they have invested a lot of time and energy in acquiring those skills, and anything that diminishes those skills may be perceived as diminishing the individual (because important skills bring respect and power).
There must also be a compelling reason for the organization to need the change; otherwise, individuals become skeptical that the change is important and are less certain it will, in fact, occur. Probably the hardest organization to change is an organization that has been successful because individuals come to believe that what worked in the past will continue to work. By contrast, in an organization that is on the brink of bankruptcy, it is easier to convince individuals that change is needed. Commitment and support from credible business sponsors and top management are also important in increasing the certainty that the change will occur.
FIGURE 13-6 Major Factors in Successful Change
The likelihood of successful change is increased when the cost of the transition to individuals who must change is low. The need for significantly different new skills or disruptions in operations and work habits can create resistance. A clear migration plan developed by a credible change agent who has support from the business sponsor is an important factor in increasing the certainty about the costs of the transition process.
Motivating Adoption
The single most important factor in motivating a change is providing clear and convincing evidence of the need for change. Simply put, everyone who is expected to adopt the change must be convinced that the benefits from the to-be system outweigh the costs of changing.
There are two basic strategies to motivating adoption: informational and political. Both strategies are often used simultaneously. With an informational strategy, the goal is to convince potential adopters that the change is for the better. This strategy works when the cost–benefit set of the target adopters has more benefits than costs. In other words, there really are clear reasons for the potential adopters to welcome the change.
Using this approach, the project team provides clear and convincing evidence of the costs and benefits of moving to the to-be system. The project team writes memos and develops presentations that outline the costs and benefits of adopting the system from the perspective of the organization and from the perspective of the target group of potential adopters. This information is disseminated widely throughout the target group, much like an advertising or public relations campaign. It must emphasize the benefits and increase the certainty in the minds of potential adopters that these benefits will actually be achieved. In our experience, it is always easier to sell painkillers than vitamins; that is, it is easier to convince potential adopters that a new system will remove a major problem (or other source of pain) than that it will provide new benefits (e.g., increase sales). Therefore, informational campaigns are more likely to be successful if they stress reducing or eliminating problems rather than focusing on providing new opportunities.
The other strategy for motivating change is a political strategy. With a political strategy, organizational power, not information, is used to motivate change. This approach is often used when the cost–benefit set of the target adopters has more costs than benefits. In other words, although the change might benefit the organization, there are no reasons for the potential adopters to welcome the change.
The political strategy is usually beyond the control of the project team. It requires someone in the organization who holds legitimate power over the target group to influence the group to adopt the change. This may be done in a coercive manner (e.g., adopt the system or you're fired) or in a negotiated manner, in which the target group gains benefits in other ways that are linked to the adoption of the system (e.g., linking system adoption to increased training opportunities). Management policies can play a key role in a political strategy by linking salary to certain behaviors desired with the new system.
In general, for any change that has true organizational benefits, about 20 to 30 percent of potential adopters will be ready adopters. They recognize the benefits, quickly adopt the system, and become proponents of the system. Another 20 to 30 percent are resistant adopters. They simply refuse to accept the change and they fight it, either because the new system has more costs than benefits for them personally or because they place such a high cost on the transition process itself that no amount of benefits from the new system can outweigh the change costs. The remaining 40 to 60 percent are reluctant adopters. They tend to be apathetic and will go with the flow to either support or resist the system, depending on how the project evolves and how their coworkers react to the system. Figure 13-7 illustrates the actors who are involved in the change management process.
The goal of change management is to actively support and encourage the ready adopters and help them win over the reluctant adopters. There is usually little that can be done about the resistant adopters because their set of costs and benefits may be divergent from those of the organization. Unless there are simple steps that can be taken to rebalance their costs and benefits or the organization chooses to adopt a strongly political strategy, it is often best to ignore this small minority of resistant adopters and focus on the larger majority of ready and reluctant adopters.
FIGURE 13-7 Actors in the Change Management Process
Enabling Adoption: Training
Potential adopters might want to adopt the change, but unless they are capable of adopting it, they won't. Careful training enables adoption by providing the skills needed to adopt the change. Training is probably the most self-evident part of any change management initiative. How can an organization expect its staff members to adopt a new system if they are not trained? However, we have found that training is one of the most commonly overlooked parts of the process. Many organizations and project managers simply expect potential adopters to find the system easy to learn. Because the system is presumed to be so simple, it is taken for granted that potential adopters should be able to learn with little effort. Unfortunately, this is usually an overly optimistic assumption.
Every new system requires new skills, either because the basic work processes have changed (sometimes radically in the case of BPR; see Chapter 3) or because the computer system used to support the processes is different. The more radical the changes to the business processes, the more important it is to ensure the organization has the new skills required to operate the new business processes and supporting information systems. In general, there are three ways to get these new skills. One is to hire new employees who have the needed skills that the existing staff does not. Another is to outsource the processes to an organization that has the skills that the existing staff does not. Both these approaches are controversial and are usually considered only in the case of BPR when the new skills needed are likely to be the most different from the set of skills of the current staff. In most cases, organizations choose the third alternative: training existing staff in the new business processes and the to-be system. Every training plan must consider what to train and how to deliver the training.
What to Train What training should you provide to the system users? It's obvious: how to use the system. The training should cover all the capabilities of the new system so users understand what each module does, right? Wrong. Training for business systems should focus on helping the users to accomplish their jobs, not on how to use the system. The system is simply a means to an end, not the end in itself. This focus on performing the job (i.e., the business processes), not using the system, has two important implications. First, the training must focus on the activities around the system as well as on the system itself. The training must help the users understand how the computer fits into the bigger picture of their jobs. The use of the system must be put in context of the manual business processes as well as of those that are computerized, and it must also cover the new management policies that were implemented along with the new computer system.
Second, the training should focus on what the user needs to do, not what the system can do. This is a subtle—but very important—distinction. Most systems provide far more capabilities than the users will need to use (e.g., when was the last time you wrote a macro in Microsoft Word?). Rather than attempting to teach the users all the features of the system, training should instead focus on the much smaller set of activities that users perform on a regular basis and ensure that users are truly expert in those. When the focus is on the 20 percent of functions that the users will use 80 percent of the time (instead of attempting to cover all functions), users become confident about their ability to use the system. Training should mention the other little-used functions but only so that users are aware of their existence and know how to learn about them when their use becomes necessary.
One source of guidance for designing training materials is the use cases. The use cases outline the common activities that users perform and thus can be helpful in understanding the business processes and system functions that are likely to be most important to the users.
CONCEPTS IN ACTION: 13-D Too Much Paper (Part 2)
Some clerks at the South Dakota Department of Worker's Compensation (see Concepts in Action 13-A) were afraid that the digital solution might not work. What if they could not find an electronic file on the computer? What if a hard drive crashed or files were accidentally deleted? What if they could not retrieve the electronic file?
Question
In terms of organizational feasibility and adoption, what might an analyst do to convince these clerks to adopt the new technology?
How to Train There are many ways to deliver training. The most commonly used approach is classroom training, in which many users are trained at the same time by the same instructor. This has the advantage of training many users at one time with only one instructor and creates a shared experience among the users.
It is also possible to provide one-on-one training, in which one trainer works closely with one user at a time. This is obviously more expensive, but the trainer can design the training program to meet the needs of individual users and can better ensure that the users really do understand the material. This approach is typically used only when the users are very important or when there are very few users.
Another approach that is becoming more common is to use some form of computer-based training (CBT), in which the training program is delivered via computer, either on CD or over the Web. CBT programs can include text slides, audio, and even video and animation. CBT is typically more costly to develop but is cheaper to deliver because no instructor is needed to actually provide the training.
Figure 13-8 summarizes four important factors to consider in selecting a training method: cost to develop, cost to deliver, impact, and reach. CBT is typically more expensive to develop than one-on-one or classroom training, but it is less expensive to deliver. One-on-one training has the most impact on the user because it can be customized to the user's precise needs, knowledge, and abilities, whereas CBT has the least impact. However, CBT has the greatest reach—the ability to train the most users over the widest distance in the shortest time—because it is much simpler to distribute than classroom and one-on-one training, simply because no instructors are needed.
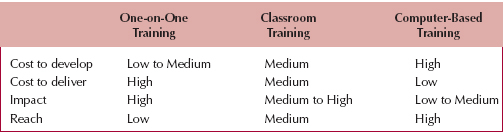
FIGURE 13-8 Selecting a Training Method
Figure 13-8 suggests a clear pattern for most organizations. If there are only a few users to train, one-on-one training is the most effective. If there are many users to train, many organizations turn to CBT. We believe that the use of CBT will increase in the future. Quite often, large organizations use a combination of all three methods. Regardless of which approach is used, it is important to leave the users with a set of easily accessible materials that can be referred to long after the training has ended (usually a quick reference guide and a set of manuals, whether on paper or in electronic form).
POST-IMPLEMENTATION ACTIVITIES9
The goal of post-implementation activities is the institutionalization of the use of the new system—that is, to make it the normal, accepted, routine way of performing the business processes. Post-implementation activities attempt to refreeze the organization after the successful transition to the new system. Although the work of the project team naturally winds down after implementation, the business sponsor and sometimes the project manager are actively involved in refreezing. These two—and, ideally, many other stakeholders—actively promote the new system and monitor its adoption and usage. They usually provide a steady flow of information about the system and encourage users to contact them to discuss issues.
In this section, we examine three key post-implementation activities: system support (providing assistance in the use of the system), system maintenance (continuing to refine and improve the system), and project assessment (analyzing the project to understand what activities were done well—and should be repeated—and what activities need improvement in future projects).
YOUR TURN: 13-3 Developing a Training Plan
Suppose you are leading the conversion from one word processor to another in your organization. Develop an outline of topics that would be included in the training. Develop a plan for training delivery.
System Support
Once the project team has installed the system and performed the change management activities, the system is officially turned over to the operations group. This group is responsible for operating the system, whereas the project team was responsible for developing the system. Members of the operations group are usually closely involved in the installation activities because they are the ones who must ensure that the system actually works. After the system is installed, the project team leaves but the operations group remains.
Providing system support means helping the users to use the system. Usually, this means providing answers to questions and helping users understand how to perform a certain function; this type of support can be thought of as on-demand training.
Online support is the most common form of on-demand training. This includes the documentation and help screens built into the system, as well as separate websites that provide answers to frequently asked questions (FAQs), which enable users to find answers without contacting a person. Obviously, the goal of most systems is to provide sufficiently good online support so that the user doesn't need to contact a person, because providing online support is much less expensive than is providing a person to answer questions.

FIGURE 13-9 Elements of a Problem Report
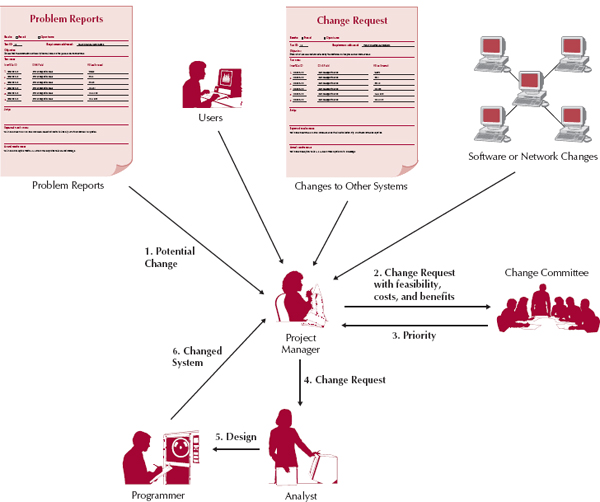
Most organizations provide a help desk that provides a place for a user to talk with a person who can answer questions (usually over the phone but sometimes in person). The help desk supports all systems, not just one specific system, so it receives calls about a wide variety of software and hardware. The help desk is operated by level-1 support staff, who have very broad computer skills and are able to respond to a wide range of requests, from network problems and hardware problems to problems with commercial software and problems with the business application software developed in-house.
The goal of most help desks is to have the level-1 support staff resolve 80 percent of the help requests they receive on the first call. If the issue cannot be resolved by level 1 support staff, a problem report (Figure 13-9) is completed (often using a special computer system designed to track problem reports) and passed to a level-2 support staff member.
The level-2 support staff members are people who know the application system well and can provide expert advice. For a new system, they are usually selected during the implementation phase and become familiar with the system as it is being tested. Sometimes the level-2 support staff members participate in training during the change management process to become more knowledgeable about the system, the new business processes, and the users themselves.
The level-2 support staff works with users to resolve problems. Most problems are successfully resolved by the level-2 staff. However, sometimes, particularly in the first few months after the system is installed, the problem turns out to be a bug in the software that must be fixed. In this case, the problem report becomes a change request that is passed to the system maintenance group (see the next section).
CONCEPTS IN ACTION: 13-E Too Much Paper (Part 3)
The South Dakota Department of Worker's Compensation had legal hurdles to implementing a digital solution to handle workers’ compensation claims (see Concepts in Action 13-A and 13-D). One hurdle was that the previous paper method had physical signatures from employees indicating that they had received treatment or from the doctor indicating that medical treatment was performed.
Question
What legal aspect might arise from only having digital signatures or only electronic or paper copies of documents instead of physical documents?
FIGURE 13-10 Processing a Change Request
System Maintenance
System maintenance is the process of refining the system to make sure it continues to meet business needs. Substantially more money and effort is devoted to system maintenance than to the initial development of the system, simply because a system continues to change and evolve as it is used. Most beginning systems analysts and programmers work first on maintenance projects; usually only after they have gained some experience are they assigned to new development projects.
Every system is “owned” by a project manager in the IS group (Figure 13-10). This individual is responsible for coordinating the system's maintenance effort for that system. Whenever a potential change to the system is identified, a change request is prepared and forwarded to the project manager. The change request is a smaller version of the system request discussed in Chapter 2. It describes the change requested and explains why the change is important.
Changes can be small or large. Change requests that are likely to require a significant effort are typically handled in the same manner as system requests: they follow the same process as the project described in this book, starting with project identification in Chapter 2 and following through installation in this chapter. Minor changes typically follow a smaller version of this same process. There is an initial assessment of feasibility and of costs and benefits, and the change request is prioritized. Then a systems analyst (or a programmer/analyst) performs the analysis, which might include interviewing users, and prepares an initial design before programming begins. The new (or revised) program is then extensively tested before the system is converted from the old system to the revised one.
Change requests typically come from five sources. The most common source is problem reports from the operations group that identify bugs in the system that must be fixed. These are usually given immediate priority because a bug can cause significant problems. Even a minor bug can cause major problems by upsetting users and reducing their acceptance of and confidence in the system.
The second most common source of change requests is enhancement to the system from users. As users work with the system, they often identify minor changes in the design that can make the system easier to use or identify additional functions that are needed. Such enhancements are important in satisfying the users and are often key in ensuring that the system changes as the business requirements change. Enhancements are often given second priority after bug fixes.
A third source of change requests is other system development projects. For example, if the doctor in the appointment problem decided that he or she would like to have a Web-based appointment system that would allow patients to directly interact with the current appointment system, it is likely that other systems, such as billing, would have to be modified to ensure that the two systems would work together. These changes required by the need to integrate two systems are generally rare but are becoming more common as system integration efforts become more common.
A fourth source of change requests is those that occur when underlying software or networks change. For example, new versions of Windows often require an application to change the way the system interacts with Windows or enables application systems to take advantage of new features that improve efficiency. Although users might never see these changes (because most changes are inside the system and do not affect its user interface or functionality), these changes can be among the most challenging to implement because analysts and programmers must learn about the new system characteristics, understand how application systems use (or can use) those characteristics, and then make the needed programming changes.
The fifth source of change requests is senior management. These change requests are often driven by major changes in the organization's strategy or operations. These significant change requests are typically treated as separate projects, but the project manager responsible for the initial system is often placed in charge of the new project.
Project Assessment
The goal of project assessment is to understand what was successful about the system and the project activities (and, therefore, should be continued in the next system or project) and what needs to be improved. Project assessment is not routine in most organizations, except for military organizations, which are accustomed to preparing after-action reports. Nonetheless, assessment can be an important component in organizational learning because it helps organizations and people understand how to improve their work. It is particularly important for junior staff members because it helps promote faster learning. There are two primary parts to project assessment—project team review and system review.
Project Team Review A project team review focuses on the way the project team carried out its activities. Each project member prepares a short two- to three-page document that reports and analyzes his or her performance. The focus is on performance improvement, not penalties for mistakes made. By explicitly identifying mistakes and understanding their causes, project team members will, it is hoped, be better prepared for the next time they encounter a similar situation—and less likely to repeat the same mistakes. Likewise, by identifying excellent performance, team members will be able to understand why their actions worked well and how to repeat them in future projects.
PRACTICAL TIP: 13-1 Beating Buggy Software ![]()
How do you avoid bugs in the commercial software you buy? Here are six tips:
- Know your software: Find out if the few programs you use day in and day out have known bugs and patches, and track the Web sites that offer the latest information on them.
- Back up your data: This dictum should be tattooed on every monitor. Stop reading right now and copy the data you can't afford to lose onto a second hard disk or Web server. We'll wait.
- Don't upgrade—yet: It's tempting to upgrade to the latest and greatest version of your favorite software, but why chance it? Wait a few months, check out other users’ experiences with the upgrade on Usenet newsgroups or the vendor's own discussion forum, and then go for it. But only if you must.
- Upgrade slowly: If you decide to upgrade, allow yourself at least a month to test the upgrade on a separate system before you install it on all the computers in your home or office.
- Forget the betas: Installing beta software on your primary computer is a game of Russian roulette. If you really have to play with beta software, get a second computer.
- Complain: Complain: The more you complain about bugs and demand remedies, the more costly it is for vendors to ship buggy products. It's like voting—the more people participate, the better the results.
Source:“Software Bugs Run Rampant,” PC World 17, no. 1 (January 1999): 46.
The project manager, who meets with the team members to help them understand how to improve their performance, assesses the documents prepared by each team member. The project manager then prepares a summary document that outlines the lessons learned from the project. This summary identifies what actions should be taken in future projects to improve performance but is careful not to identify team members who made mistakes. The summary is widely circulated among all project managers to help them understand how to manage their projects better. Often, it is also circulated among regular staff members who did not work on the project so that they, too, can learn from other projects.
System Review The focus of the system review is to understand the extent to which the proposed costs and benefits from the new system identified during feasibility analysis were actually recognized from the implemented system. Project team review is usually conducted immediately after the system is installed while key events are still fresh in team members’ minds, but system review is often undertaken several months after the system is installed because it often takes a while before the system can be properly assessed.
System review starts with the system request and feasibility analysis prepared at the start of the project. The detailed analyses prepared for the expected business value (both tangible and intangible) as well as the economic feasibility analysis are reexamined and a new analysis is prepared after the system has been installed. The objective is to compare the anticipated business value against the actual realized business value from the system. This helps the organization assess whether the system actually provided the value it was planned to provide. Whether or not the system provides the expected value, future projects can benefit from an improved understanding of the true costs and benefits.
A formal system review also has important behavior implications for project initiation. Because everyone involved with the project knows that all statements about business value and the financial estimates prepared during project initiation will be evaluated at the end of the project, they have an incentive to be conservative in their assessments. No one wants to be the project sponsor or project manager for a project that goes radically over budget or fails to deliver promised benefits.
APPLYING THE CONCEPTS AT CD SELECTIONS
In this installment of the CD Selections case, we see how the new system is transitioned from the development team and put into production by the user community. To ensure a smooth transition, Alec and Margaret oversaw the necessary user training, including employees from CD Selections help desk department, and the creation of the necessary, relevant documentation. Looking back over the development of the system, Alec and Margaret evaluate the processes used and the individual development team members to identify lessons learned throughout the process. Finally, they set up a process to maintain the system.
SUMMARY
Cultural Issues and Information Technology Adoption
Given the global business environment, cultural issues become even more important when deploying information systems today. The cultural dimensions that need to be taken into consideration include Hall's speed of messages, context, and time dimensions along with Hofstede's power distance, uncertainty avoidance, individualism versus collectivism, masculinity versus femininity, and long- versus short-term orientation dimensions. Furthermore, these dimensions tend to interact with one another. From an information systems deployment perspective, the most important thing to remember is to take into consideration the local culture before deploying the new system.
Conversion
Conversion, the technical process by which the new system replaces the old system, has three major steps: install hardware, install software, and convert data. Conversion style, the which users are switched between the old and new systems, can be via either direct conversion (in which users stop using the old system and immediately begin using the new system) or parallel conversion (in which both systems are operated simultaneously to ensure the new system is operating correctly). Conversion location—what parts of the organization are converted and when—can be via a pilot conversion in one location; via a phased conversion, in which locations are converted in stages over time; or via simultaneous conversion, in which all locations are converted at the same time. The system can be converted module by module or as a whole at one time. Parallel and pilot conversions are less risky because they have a greater chance of detecting bugs before the bugs have widespread effect, but parallel conversion can be expensive.
Change Management
Change management is the process of helping people to adopt and adapt to the new system and its work processes. People resist change for very rational reasons, usually because they perceive the costs to themselves of the new system (and the transition to it) to outweigh the benefits. The first step in the change management plan is to change the management policies, devise measurements and rewards that support the new system, and allocate resources to support it. The second step is to develop a concise list of costs and benefits to the organization and to all relevant stakeholders. This points out who is likely to support and who is likely to resist the change. The third step is to motivate adoption both by providing information and by using political strategies—using power to induce potential adopters to adopt the new system. Finally, training is essential to enable successful adoption. Training should focus on the primary functions the users will perform and look beyond the system itself to help users integrate the system into their work processes.
Post-implementation Activities
System support is performed by the operations group, which provides online and help desk support to the users. System support has both a level 1 support staff, who answer the phone and handles most of the questions, and level 2 support staff, who follow up on challenging problems and sometimes generates change requests for bug fixes. System maintenance responds to change requests to fix bugs and improve the business value of the system. The goal of project assessment is to understand what was successful about the system and the project activities and what needs to be improved. Project team review focuses on the way the project team carried out its activities and usually results in documentation of key lessons learned. System review focuses on understanding the extent to which the proposed costs and benefits from the new system were actually recognized from the implemented system.
KEY TERMS
- Change agent, 555
- Change management, 547
- Change request, 565
- Classroom training, 563
- Collectivism, 548
- Computer-based training (CBT), 563
- Context, 548
- Conversion, 549
- Conversion location, 550
- Conversion modules, 550
- Conversion strategy, 553
- Conversion style, 550
- Cost, 553
- Direct conversion, 550
- Femininity, 548
- Frequently asked questions (FAQ), 564
- Help desk, 565
- Individualism, 548
- Informational strategy, 561
- Institutionalization, 564
- Level 1 support, 565
- Level 2 support, 565
- Long-term orientation, 549
- Management policies, 558
- Masculinity, 548
- Measurements, 548
- Migration plan, 546
- Modular conversion, 553
- Modules, 552
- Monochronic time, 548
- On-demand training, 564
- One-on-one training, 563
- Online support, 564
- Operations group, 564
- Parallel conversion, 551
- Perceived benefits, 557
- Perceived costs, 557
- Phased conversion, 551
- Pilot conversion, 551
- Political strategy, 561
- Polychronic time, 548
- Post-implementation, 546
- Potential adopter, 556
- Power distance, 548
- Problem report, 565
- Project assessment, 564
- Project team review, 568
- Ready adopters, 561
- Real benefits, 557
- Real costs, 557
- Refreeze, 546
- Reluctant adopters, 561
- Resistant adopters, 561
- Resource allocation, 558
- Rewards, 558
- Risk, 553
- Short-term orientation, 549
- Simultaneous conversion, 552
- Speed of messages, 548
- Sponsor, 555
- Standard operating procedure (SOP), 558
- System maintenance, 564
- System request, 566
- System review, 568
- System support, 564
- Time, 548
- Training, 562
- Transition process, 556
- Uncertainty avoidance, 548
- Unfreeze, 546
- Whole-system conversion, 552
QUESTIONS
- What are the three basic steps in managing organizational change?
- What are the cultural issues of which developers should be aware?
- What are the major components of a migration plan?
- Compare and contrast direct conversion and parallel conversion.
- Compare and contrast pilot conversion, phased conversion, and simultaneous conversion.
- Compare and contrast modular conversion and whole-system conversion.
- Explain the trade-offs among selecting between the types of conversion in questions 4, 5, and 6.
- What are the three key roles in any change management initiative?
- Why do people resist change? Explain the basic model for understanding why people accept or resist change.
- What are the three major elements of management policies that must be considered when implementing a new system?
- Compare and contrast an information change management strategy with a political change management strategy. Is one better than the other?
- Explain the three categories of adopters you are likely to encounter in any change management initiative.
- How should you decide what items to include in your training plan?
- Compare and contrast three basic approaches to training.
- What is the role of the operations group in system development?
- Compare and contrast two major ways of providing system support.
- How is a problem report different from a change request?
- What are the major sources of change requests?
- Why is project assessment important?
- How is project team review different from system review?
- What do you think are three common mistakes that novice analysts make in migrating from the as-is to the to-be system?
- Some experts argue that change management is more important than any other part of system development. Do you agree or not? Explain.
- In our experience, change management planning often receives less attention than conversion planning. Why do you think this happens?
EXERCISES
- Suppose you are installing a new accounting package in your small business. What conversion strategy would you use? Develop a conversion plan (i.e., technical aspects only).
- Suppose you are installing a new room reservation system for your university that tracks which courses are assigned to which rooms. Assume that all the rooms in each building are “owned” by one college or department and only one person in that college or department has permission to assign them. What conversion strategy would you use? Develop a conversion plan (i.e., technical aspects only).
- Suppose you are installing a new payroll system in a very large multinational corporation. What conversion strategy would you use? Develop a conversion plan (i.e., technical aspects only).
- Consider a major change you have experienced in your life (e.g., taking a new job, starting a new school). Prepare a cost–benefit analysis of the change in terms of both the change and the transition to the change.
- Suppose you are the project manager for a new library system for your university. The system will improve the way students, faculty, and staff can search for books by enabling them to search over the Web, rather than using only the current text-based system available on the computer terminals in the library. Prepare a cost–benefit analysis of the change in terms of both the change and the transition to the change for the major stakeholders.
- Prepare a plan to motivate the adoption of the system in exercise E.
- Prepare a training plan that includes both what you would train and how the training would be delivered for the system in exercise E.
- Suppose you are leading the installation of a new DSS to help admissions officers manage the admissions process at your university. Develop a change management plan (i.e., organizational aspects only).
- Suppose you are the project leader for the development of a new Web-based course registration system for your university that replaces an old system in which students had to go to the coliseum at certain times and stand in line to get permission slips for each course they wanted to take. Develop a migration plan (including both technical conversion and change management).
- Suppose you are the project leader for the development of a new airline reservation system that will be used by the airline's in-house reservation agents. The system will replace the current command-driven system designed in the 1970s that uses terminals. The new system uses PCs with a Web-based interface. Develop a migration plan (including both conversion and change management) for your telephone operators.
- Develop a migration plan (including both conversion and change management) for the independent travel agencies who use the airline reservation system described in exercise J.
- For the A Real Estate Inc problem in Chapters 4 through 12:
- Prepare a plan to motivate adoption of the system.
- Prepare a training plan that includes both what you would train and how the training would be delivered.
- Prepare a change management plan.
- Develop a migration plan.
- For the A Video Store problem in Chapters 4 through 12:
- Prepare a plan to motivate adoption of the system.
- Prepare a training plan that includes both what you would train and how the training would be delivered.
- Prepare a change management plan.
- Develop a migration plan.
- For the gym problem in Chapters 4 through 12:
- Prepare a plan to motivate adoption of the system.
- Prepare a training plan that includes both what you would train and how the training would be delivered.
- Prepare a change management plan.
- Develop a migration plan.
- For the Picnics R Us problem in Chapters 4 through 12:
- Prepare a plan to motivate adoption of the system.
- Prepare a training plan that includes both what you would train and how the training would be delivered.
- Prepare a change management plan.
- Develop a migration plan.
- For Of-the-Month Club problem in Chapters 4 through 12:
- Prepare a plan to motivate adoption of the system.
- Prepare a training plan that includes both what you would train and how the training would be delivered.
- Prepare a change management plan.
- Develop a migration plan.
MINICASES
- Nancy is the IS department head at MOTO Inc., a human resources management firm. The IS staff at MOTO Inc. completed work on a new client management software system about a month ago. Nancy was impressed with the performance of her staff on this project because the firm had not previously undertaken a project of this scale in-house. One of Nancy's weekly tasks is to evaluate and prioritize the change requests that have come in for the various applications used by the firm.
Right now, Nancy has five change requests for the client system on her desk. One request is from a system user who would like some formatting changes made to a daily report produced by the system. Another request is from a user who would like the sequence of menu options changed on one of the system menus to more closely reflect the frequency of use for those options. A third request came in from the billing department.
This department performs billing through a billing software package. A major upgrade of this software is being planned, and the interface between the client system and the bill system need to be changed to accommodate the new software's data structures. The fourth request seems to be a system bug that occurs whenever a client cancels a contract (a rare occurrence, fortunately). The last request came from Susan, the company president. This request confirms the rumor that MOTO Inc. is about to acquire another new business. The new business specializes in the temporary placement of skilled professional and scientific employees and represents a new business area for MOTO Inc. The client management software system will need to be modified to incorporate the special client arrangements that are associated with the acquired firm.
How do you recommend that Nancy prioritize these change requests for the client/management system?
- Sky View Aerial Photography offers a wide range of aerial photographic, video, and infrared imaging services. The company has grown from its early days of snapping pictures of client houses to its current status as a full-service aerial image specialist. Sky View now maintains numerous contracts with various governmental agencies for aerial mapping and surveying work. Sky View has its offices at the airport, where it keeps its fleet of specially equipped aircraft. Sky View contracts with several freelance pilots and photographers for some of its aerial work and also employs several full-time pilots and photographers.
The owners of Sky View Aerial Photography recently contracted with a systems development consulting firm to develop a new information system for the business. As the number of contracts, aircraft, flights, pilots, and photographers increased, the company experienced difficulty keeping accurate records of its business activity and the utilization of its fleet of aircraft. The new system will require all pilots and photographers to swipe an ID badge through a reader at the beginning and conclusion of each photo flight, along with recording information about the aircraft used and the client served on that flight. These records are to be reconciled against the actual aircraft utilization logs maintained and recorded by the hangar personnel.
The office staff was eagerly awaiting the installation of the new system. Their general attitude was that the system would reduce the number of problems and errors that they encountered and would make their work easier. The pilots, photographers, and hangar staff were less enthusiastic, being unaccustomed to having their activities monitored in this way.
- Discuss the factors that might inhibit the acceptance of this new system by the pilots, photographers, and hangar staff.
- Discuss how an informational strategy could be used to motivate adoption of the new system at Sky View Aerial Photography.
- Discuss how a political strategy could be used to motivate adoption of the new system at Sky View Aerial Photography.
- For the Holiday Travel Vehicles problem described in Chapters 5 through 12:
- Prepare a plan to motivate adoption of the system.
- Prepare a training plan that includes both what you would train and how the training would be delivered.
- Prepare a change management plan.
- Develop a migration plan.
- For the Professional and Scientific Staff Management problem described in Chapters 4, and 6 through 11:
- Prepare a plan to motivate adoption of the system.
- Prepare a training plan that includes both what you would train and how the training would be delivered.
- Prepare a change management plan.
- Develop a migration plan.
1 Kurt Lewin, “Frontiers in Group Dynamics,” Human Relations, 1, no. 5 (1947): 5–41; and Kurt Lewin, “Group Decision and Social Change,” in E. E. Maccoby, T. M. Newcomb, and E. L. Hartley (eds.), Readings in Social Psychology (New York: Holt, Rinehart & Winston, 1958), pp. 197–211.
2 A good summary of cultural issues and information systems is Dorothy E. Leidner and Timothy Kayworth, “A Review of Culture in Information Systems Research: Toward a Theory of Information Technology Culture Conflict,” MIS Quarterly 30, no. 2 (2006): 357–399.
3 See Geert Hofstede, Culture's Consequences: Comparing Values, Behaviors, Institutions and Organizations Across Nations, 2nd ed. (Thousand Oaks, CA: Sage, 2001), Geert Hofstede, Gert Jan Hofstede, and Michael Minkov, Cultures and Organizations: Software of the Mind, 3rd ed. (New York: McGraw-Hill, 2010), and Edward T. Hall, Beyond Culture (New York: Anchor Books, 1981).
4 The material in this section is related to the Enhanced Unified Process's Transition phase and the Deployment workflow (see Figure 1-18).
5 In this case, a module is typically a component or a package, i.e., a set of collaborating classes.
6 The material in this section is related to the Enhanced Unified Process's Transition and Production phases and the Configuration and Change Management workflow (see Figure 1-18). Many books have been written on change management. Some of our favorites are the following: Patrick Connor and Linda Lake, Managing Organizational Change, 2nd ed. (Westport, CT: Praeger, 1994); Douglas Smith, Taking Charge of Change (Reading, MA: Addison-Wesley, 1996); Daryl Conner, Managing at the Speed of Change (New York: Villard Books, 1992); and Mary Lynn Manns and Linda Rising, Fearless Change: Patterns for Introducing New Ideas (Boston: Addison-Wesley, 2005).
7 This section benefited from conversations with Dr. Robert Briggs, research scientist at the Center for the Management of Information at the University of Arizona.
8 This section builds on the work of Anthony Giddons, The Constitution of Society: Outline of the Theory of Structure (Berkeley: University of California Press, 1984). A good summary of Giddons's theory that has been revised and adapted for use in understanding information systems is an article by Wanda Orlikowski and Dan Robey: “Information Technology and the Structuring of Organizations,” Information Systems Research 2, no. 2 (1991): 143–169.
9 The material in this section is related to the Enhanced Unified Process's Production Phase and the Operations and Support workflow (see Figure 1-18).