This, the sixth and final lecture in this series on the history of cryptology, will be devoted to a presentation of the events of importance in that history from the end of World War I to the end of World War II. It would be entirely too ambitious a project even to attempt to compress within a lecture of only fIfty minutes all that should or could be told in that segment of our history. Briefly, however, it can be said that the most significant events during that quarter of a century were directly concerned, firstly, with the advances made in the production of more complex mechanical, electrical, and electronic cryptographic apparatus and, secondly, with the concomitant advances in the production of more sophisticated cryptanalytic apparatus in order to speed up or to make possible the solution of enemy communications produced by these increasingly complex cryptographic machines. These two phases are interrelated because, to use a simple analogy, cryptography and cryptanalysis represent the obverse and reverse faces of a single coin.
As to advances in the development and use of more effective cryptographic apparatus, I will only note at this point a comment that General Omar Bradley of World War II fame makes in his very interesting book, A Soldier's Story:[21]
Signal Corps officers like to remind us that "although Congress can make a general, it takes communications to make him a commander."
It is presumptuous to amend General Bradley's remark, but this is how I wish he had worded it:
Signal Corps officers like to remind us that "although Congress can make a general, it takes rapid and secure communications to make him a good commander."
This will in fact be the keynote of this lecture. In other words, communications security, or COMSEC, will be its main theme and the one I wish to emphasize.
But before we take up the cryptographic history of the years between 1918 and 1946, perhaps a bit more attention must be devoted to events and developments of cryptanalytic significance or importance during this period. By far the most spectacular and interesting of these are the ones that were so fully and disastrously disclosed by the various investigations conducted by the Army and Navy very secretly while World War II was still in progress, and both secretly and openly after the close of hostilities. The investigations were intended to ascertain why our army and navy forces in Hawaii were caught by surprise by the sneak attack on Pearl Harbor by the Japanese on the morning of 7 December 1941. They were also intended to ascertain and pin the blame on whoever was responsible. I don't think I should even attempt to give you my personal opinion on these complex questions, which were studied by seven different boards within the services and finally by the Joint Congressional Committee on the Investigation of the Pearl Harbor Attack. I mentioned the latter investigation in my first lecture and now will add to what I said then. The committee began its work early in September 1945 with secret hearings, but on seventy days between 15 November 1945 and 31 May 1946, open hearings were conducted, in the course of which some 15,000 pages of testimony were taken and a total of 183 exhibits received, incident to an examination of forty-three witnesses. In July 1946 the committee put out a final report of 580 pages containing its findings, conclusions and recommendations. The report was accompanied by a set of thirty-nine volumes of testimony and exhibits. The report was really not a single report: there was one by the Majority (signed by six Democratic and two Republican members), and one by the Minority (signed by two Republican members). The Minority Report was not nearly as long as that of the Majority, but it brought into focus certain troublesome points that still form the subject of acrimonious discussions and writings by those who believe the attack was "engineered" by President Roosevelt and that certain authorities in Washington were as culpable as were the principal commanders in the Army and the Navy in Hawaii.
For this lecture, however, it is an interesting fact that both the Majority and Minority Reports contain glowing tributes to the role played by COMINT before and during our participation in World War II. In my first lecture, I presented a brief extract in this regard, taken from the Majority Report;[22] but here is what the Minority Report says on the subject:[23]
Through the Army and Navy intelligence services extensive information was secured respecting Japanese war plans and designs, by intercepted and decoded Japanese secret messages, which indicated the growing danger of war and increasingly after November 26 the imminence of a Japanese attack.
With extraordinary skill, zeal, and watchfulness the intelligence services of the Army Signal Corps and Navy Office of Naval Communications broke Japanese codes and intercepted messages between the Japanese Government and its spies and agents and ambassadors in all parts of the world and supplied the high authorities in Washington reliable secret information respecting Japanese designs, decisions, and operations at home, in the United States, and in other countries. Although there were delays in the translations of many intercepts, the intelligence services had furnished to those high authorities a large number of Japanese messages which clearly indicated the growing resolve of the Japanese Government on war before December 7, 1941.
Although references to COMINT abound in the Report of the Majority as well as in the Report of the Minority, there are also many references having to do with COMSEC in both reports, as well as in the thirty-nine accompanying volumes of testimony and exhibits. Some technical misconceptions with regard to those subjects are there, too, and it is quite comprehensible that there should be some on the part of laymen, but to encounter a serious one in a book by an experienced high-level commander in World War II is a bit disconcerting. Listen to this paragraph from a recent book by General Wedemeyer, who was one such commander:[24]
The argument has been made that we could not afford to let the Japanese know we had broken their code. But this argument against a Presidential warning does not hold water. It was not a mere matter of having broken a specific code; what we had done was to devise a machine which could break any [author's emphasis] code provided it was fed the right combinations by our extremely able and gifted cryptographers. The Japanese kept changing their codes throughout the war anyway. And we kept breaking them almost as a matter of routine.
I don't know where General Wedemeyer obtained his information about that wonderful machine he mentions. I imagine that there are many other persons who think there is such a machine because of all they hear and see about those marvelous "electronic brains" which are capable of performing such amazing feats in solving all kinds of problems. I dare say I won't be wrong in assuming that many of you do indeed wish there were such a machine as that mentioned by General Wedemeyer. Nobody doubts that electronic digital computers can do lots of things in cryptologic research, and many persons speculate on the role they may play in their possible applications in connection with research in future wars.
But let's leave such speculations, interesting as they may be, and continue with our history of past applications. Let's first dispose of some comments in the COMINT area of that history, not only on the events preceding the Pearl Harbor attack, but also on the military, naval, and air operations which ensued in the Pacific as well as in the European Theater.
You will recall that in my first lecture I called to your attention an article that appeared in the 17 December 1945 issue of Time and that was based upon a letter the late General Marshall wrote to Governor Dewey, Republican candidate for president in the 1944 campaign. Here's how the two principals looked at that time (fig. 102). In the letter, which was written on 27 September 1944 and hand-carried by Colonel Carter W. Clarke, a high-level officer in Army G-2, to Governor Dewey, General Marshall begged the governor to say nothing during the campaign about a certain piece of very vital information which had become known to the governor, it having been "leaked" to him by persons unknown and unauthorized to disclose it. The information dealt with the fact that U.S. government authorities had been reading Japanese codes and ciphers before the attack on Pearl Harbor. The points which General Marshall wanted to convey were not only that the "leaked" information was true, but also that, much more important, (1) the war was still in progress; (2) the Japanese were still using certain of the pre-Pearl Harbor cryptosystems; and (3) the U.S. government was still reading highly secret Japanese messages in those systems, as well as highly secret messages of other enemy governments. Therefore, it was absolutely vital that Governor Dewey not use the top secret information as political ammunition in his campaign.
After merely glancing over the first two paragraphs of the letter, Governor Dewey handed it back to Colonel Clarke with the comment that he did not wish to read any further, whereupon there was nothing for Colonel Clarke to do but return immediately to Washington. General Marshall then made certain changes in the opening paragraphs of the letter, and again Colonel Clarke hand-carried it to the Governor, who then read the whole of it. In my first lecture I said that I might later give further extracts from Time's account of this episode, but there isn't time. Instead, however, I've put the whole account in Appendix I to the present lecture. The Marshall-Dewey correspondence is so important in cryptologic history that I have deemed it useful to put the whole of it in Appendix II.
The information disclosed during the various official investigations of the attack on Pearl Harbor, so far as concerns the important COMINT achievements of the Army and the Navy before and after that attack, was classified information of the very highest security level, and the disclosures were highly detrimental to our national security. Much has been written about them since the end of hostilities, and although all of that formerly top secret information is now in the public domain, fortunately very few details of technical significance or value can be found therein. Hints and even blunt statements about the great role played by COMINT in U.S. military, naval, and air operations are found in books and articles published by U.S. government officials and American officers, as well as by officers of the beaten Japanese, German, and Italian armed forces. In the interests of brevity, I will cite only a few examples.[25]
As regards disclosures by U.S. government officials and officers, I can begin with those of the late Mr. Cordell Hull, who was secretary of state at the time of the Pearl Harbor attack. In his memoirs are many references (over a dozen) to the contents of intercepted and solved Japanese Foreign Office messages.[26] The late Mr. Henry L. Stimson, secretary of war at that time, makes clear references in his autobiography to COMINT successes and our failure to use them prior to the attack.[27] Dr. Herbert Feis, who was Mr. Hull's advisor on international economic affairs from 1937 to 1943, and who from 1944 to 1946 was Mr. Stimson's Special Consultant, has a good deal to say about the role played by "Magic" in a book written as a member of the Institute for Advanced Study, at Princeton[28] Admiral Kimmel, one of the two commanders in Hawaii at the time of the attack, in defending himself in his book, cites many "Magic" messages.[29] And Major General Sherman Miles, head of G-2 at the time of the attack, has much to say about "Magic" in an article published in 1948.[30] As regards disclosures by former enemy officers, the following are of particular interest because they concern the Battle of Midway, which is considered the one that turned the tide of war in the Pacific from a possible Japanese victory to one of ignominious defeat:
If Admiral Yamamoto and his staff were vaguely disturbed by the persistent bad weather and by lack of information concerning the doings of the enemy, they would have been truly dismayed had they known the actual enemy situation. Postwar American accounts make it clear that the United States Pacific Fleet knew of the Japanese plan to invade Midway even before our forces had sortied from home waters. As a result of some amazing achievements by American intelligence, the enemy had succeeded in breaking the principal code then in use by the Japanese Navy. In this way the enemy was able to learn of our intentions almost as quickly as we had determined them ourselves.
* * * * * *
The distinguished American Naval historian, Professor Samuel E. Morison, characterized the victory of United States forces at Midway as "a victory of intelligence." In this judgment the author fully concurs, for it is beyond the slightest possibility of doubt that the advance discovery of the Japanese plan to attack was the foremost single and immediate cause of Japan's defeat.
Viewed from the Japanese side, this success of the enemy's intelligence translates itself into a failure on our part – a failure to take adequate precautions for guarding the secrecy of our plans. Had the secret of our intent to invade Midway been concealed with the same thoroughness as the plan to attack Pearl Harbor, the outcome of this battle might well have been different. But it was a victory of American intelligence in a much broader sense than just this. Equally as important as the positive achievements of the enemy's intelligence on this occasion was the negatively bad and ineffective functioning of Japanese intelligence.[31]
It is the second extract above which is of special interest to us at the moment, and, in particular, the portion that refers to "the negatively bad and ineffective functioning of Japanese intelligence." The author is, I think, a bit too severe on the Japanese intelligence organization. I say this because their cryptanalysts were up against much more sophisticated cryptosystems than they dreamt of, or were qualified to solve. In fact, even if they had been extremely adept in cryptanalysis, it would have been of no avail – U.S. high-level communications were protected by cryptosystems of very great security.
This brings us to a phase of cryptology that is of highest importance – the phase that deals with communications security, or COMSEC, and I shall confine myself largely to its development and historical background in our armed forces. The background is a very broad one because it should include the background of the developments of each of the three components of COMSEC, viz, (1) cryptosecurity, (2) transmission security, and (3) physical security of cryptomaterials. But since time is limited and because I think you would be more interested in the phases pertaining to cryptosecurity, I will omit further references to the other two components or to the history of their development. And even in limiting the data to cryptosecurity, I will have opportunity only to give some of the highlights of the development of the items that comprise our present cryptomaterials, omitting comments on the history of the development and improvement of our techniques, procedures, and practices, all of which are extremely important.
I shall begin the story with a definition that you will find in any good English dictionary, a definition of the word "accident." You will get the point of what may seem to you right now to be merely another of my frequent digressions from the main theme, but if it be a digression I think you will nevertheless find it of interest. The word "accident" in Webster's Unabridged Dictionary is defined as follows:
1. Literally, a befalling;
An event that takes place without one's foresight or expectation; an undesigned, sudden, and unexpected event.
Hence, often, an undesigned and unforeseen occurrence of an afflictive or unfortunate character; a mishap, resulting in injury to a person or damage to a thing; a casualty; as, to die by an accident.
There are further definitions of the word, but what I've given is sufficient for our purposes. But why define the word? What has it to do with COMSEC?
During our participation in World War II, the president of the United States, accompanied by many of his highest-level military, naval, and civilian assistants, journeyed several times half way around the world. He and they journeyed in safety; neither he nor they met with an "accident." Here's a picture taken at the Casablanca Conference in January 1943 (fig. 103). Imagine the disaster, it would have been if the plane carrying this distinguished group had been shot down and lost in the Atlantic or the Mediterranean. On the other hand, in April 1943 Admiral Isoroku Yamamoto, Commander in Chief of the Combined Fleet of the Japanese Imperial Navy, started out on what was to be just an ordinary inspection trip but turned out to be a one-way trip for him. Here's a good picture of the admiral (fig. 104), who was the architect of the attack on Pearl Harbor. His death was announced in an official Japanese Navy communique stating that the admiral "had met a glorious end while directing operations in a naval engagement against superior enemy forces." But we know that this was simply not true; Admiral Yamamoto "met with an accident." Some bright person – I think it was the late Jimmy Walker, when mayor of New York City – has said that "accidents don't just happen – they are brought about." Jimmy Walker's comment was true in this case at least; Admiral Yamamoto did not die by accident; he died because our navy knew the schedule of his trip down to the very last detail so that it was possible to set up an ambush with high degree of success. Here is the story as told in an interesting manner by Fleet Admiral William F. Halsey, USN, in his book entitled Admiral Halsey's Story.[32]
I returned to Noumea in time to sit in on an operation that was smaller but extremely gratifying. The Navy's code experts had hit a jackpot; they had discovered that Admiral Isoroku Yamamoto, the Commander-in-Chief of the Imperial Japanese Navy, was about to visit the Solomons. In fact, he was due to arrive at Ballale Island, just south of Bougainville, precisely at 0945 on April 18. Yamamoto, who had conceived and proposed the Pearl Harbor attack, had also been widely quoted as saying that he was ftlooking forward to dictating peace in the White House at Washington." I believe that this statement was subsequently proved a canard, but we accepted its authenticity then, and it was an additional reason for his being No.3 on my private list of public enemies, closely trailing Hirohito and Tojo.
Eighteen P-38's of the Army's 339th Fighter Squadron, based at Henderson Field, were assigned to make the interception over Buin, 35 miles short of Ballale. Yamamoto's plane, a Betty, accompanied by another Betty and covered by six Zekes, hove in sight exactly on schedule and Lt. Col. Thomas G. Lamphier, Jr., dove on it and shot it down in flames. The other Betty was also shot down for good measure, plus one of the Zekes. . . We bottled up the story, of course. One obvious reason was that we didn't want the Japs to know that we had broken their code. . . . Unfortunately, somebody took the story to Australia, whence it leaked into the papers, and no doubt eventually into Japan.... But the Japs evidently did not realize the implication any more than the tattletale; we continued to break their codes.
But lest you get the impression that enemy intelligence agencies had no success at all with secret communications of U.S. armed forces, let me tell you that they did have some success and, in certain instances, very significant success. There is not time to go into this somewhat disillusioning statement, but I can say that as a general rule the successes were attributable not to technical weakness in U.S. cryptosystems, but to their improper use in the case of certain low-level ones, by unskilled and improperly or insufficiently trained cryptographic clerks. I may as well tell you right now that this weakness in cryptocommunications has been true for a great many years, for centuries as a matter of fact, because as long ago as 1605 Francis Bacon, who wrote the first treatise in English on cryptology, made the following comment:[33]
This Arte of Cypheringe, hath for Relative, an Art of Discypheringe; by supposition unprofitable; but, as things, are of great use. For suppose that Cyphars were well managed, there bee Multitudes of them which exclude the Discypherer. But in regarde of the rawnesse and unskillfulness of the handes, through which they passe, the greatest Matters, are many times carryed in the weakest Cyphars.
When electrical, particularly radio, transmission entered into the picture, additional hazards to communications security had to be taken into account, but many commanders failed to realize how much valuable intelligence can be obtained merely from a study of the procedures used in the transmission of messages as well as from a study of the direction and flow of radio traffic, the call signs of the transmitting and receiving stations, etc., all without solving the communications even if they were in cryptic form. Following are two paragraphs extracted from a document entitled German Operational Intelligence, published in April 1946 by the German Military Document Section, a Combined British, Canadian, and U.S. Staff:
Signal intelligence (i.e., communication intelligence or COMINT) was a chief source of information in the German Army. In the eastern theater, where there was offensive warfare primarily, the signal intelligence service was well-organized with well-defined purposes, efficient personnel, and adequate equipment. In the course of the campaign, it was reorganized to exploit to the fullest the success already experienced, and, by 1943, there existed a complete and smoothly functioning machine sufficient to meet all demands. (p. 8.)
* * * * * * *
Most of their signal intercept success came from low-echelon traffic. Armored and artillery radio nets passing operational traffic were followed closely and were one of the chief sources of signal intelligence. Artillery radio nets were given first coverage priority. Apart from messages intercepted in code or in clear, signal procedure, peculiarities of transmitting, and characteristics of Allied radio operators provided enormous assistance in helping to evaluate signal information. The Germans noticed that call signs were often the same for a unit over long periods and that even frequencies remained unchanged for weeks at a time. (p. 8.)
A great many examples of intercepted messages of tactical content are cited in the aforementioned document, which is replete with information of deep interest, although the document was originally issued with the lowest security classification then in use (U.S. "Restricted"; British-Canadian "FOR OFFICIAL USE ONLY"). I wish there were time to quote at greater length from this useful brochure.
Coming directly now to the history of the development of our cryptomaterials themselves, I hardly need reiterate what was pointed out in previous lectures as to the profound effect of the advances in the science and art of electrical communications in the twentieth century. Those advances had a direct effect upon military communications and an indirect effect upon military cryptology. Hand-operated ciphers and, of course, code books became almost obsolete because the need for greater and greater speed of cryptographic operations became obvious in order to match as much as possible the very great increase in the speed of communications brought about by inventions and improvements in electric wire and radiotelegraphy. The need for cryptographic apparatus and machines thus very soon became quite obvious, but it took quite some time to satisfy that need in a manner that could be considered to give adequate security for military communications.
The history of the invention and development of cryptographic devices, machines, and associated apparatus and material is long and interesting. Let us begin with a resumé of the earliest items of importance in that history.
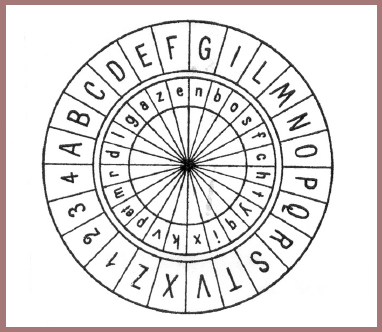
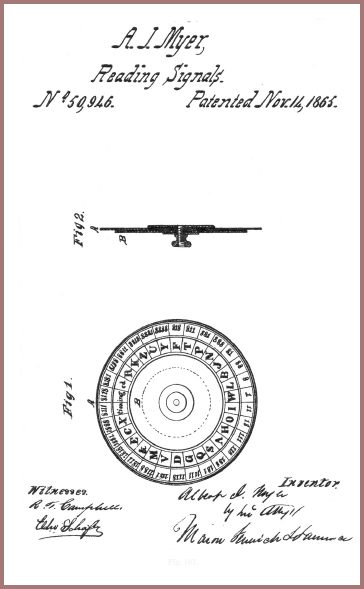
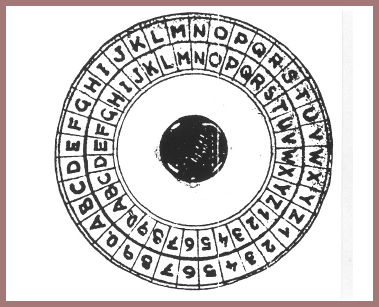
Until the advent of electronic cipher machines, most cryptographic apparatus and devices were built upon or around concentric circular rotating members such as cipher wheels, cipher disks, etc. A very early, perhaps the earliest, picture of such a device appears in a treatise by an Italian cryptologist named Alberti, whose Trattati in Cifra was written in Rome about 1470. It is the oldest tract on cryptography the world now possesses. Here's a photo of Alberti's disk (fig. 105), but I won't take the time to explain it except to say that the digits 1, 2, 3, 4 were used to encipher code groups and to call your attention to the fact that the letters of the cipher or revolving alphabet were in mixed order. In Porta's book, first published in 1563 in Naples, there appear several cipher disks; in the copy which was given me as a gift by Colonel Fabyan, they are still in working condition. Here is a picture of one of them (fig. 106). In this version the device uses symbols as cipher characters. And apparently nobody thought up anything much better for a long, long time. It seems, in fact, that not only did no one think up anything new or even some improvements on the original Alberti or Porta disks, but those who did any thinking at all on the subject merely "invented" or "reinvented" the same thing again, and that happened repeatedly in successive generations. For instance, in Lecture No. IV of this series you were shown a picture of the cipher disk "invented" by Major Albert Myer, the first Chief Signal Officer of the U.S. Army, who obtained a patent on his invention in 1865. Here's a picture of the patented disk (fig. 107) and the explanation of the invention (fig. 108). You may also remember that signalmen of the Confederate Signal Corps mechanized the old Vigenère Square and put it out in the form of a cylinder (see figures 65 and 66 of Lecture No. IV). The cipher disk used by the Signal Corps of the U.S. Army from 1910 to 1920, that is, during the period including our participation as a belligerent in World War I, was nothing but a white celluloid variation of the original Alberti parchment disk of the vintage of 1470 (except that it was even simpler than its progenitor, because in the latter the cipher alphabets produced were mixed alphabets whereas in the Signal Corps disk, the cipher alphabets are simple reversed standard sequences (fig. 109). We all know that it generally takes a pretty long time to get a patent through the U.S. Patent Office, but the ancient device was patented in 1924 by S.H. Huntington (fig. 110): here you can see a great improvement over the Signal Corps version – a blank is added to both sequences so that the space between words could be enciphered. Indication of word space, as you have learned, is a fatal weakness if seen in the cipher text; in the Huntington device the spaces between words would be enciphered, but the cipher text would have space signs, although they would not correspond to the actual spaces between words in the plain text. In the Huntington device, the space signs in the cipher text would be a bit misleading but not to an experienced cryptanalyst, who would soon realize that they do not actually represent "word space" in the plain text.
It is interesting to note that in 1936, during the days when the German National Socialists were banned as an organization in Austria, the Nazis used this variation of the old disk – it had ten digits on both the outer and the inner sequences for enciphering digits (fig. 111).
The first significant improvement on the old cipher disk was that made by Sir Charles Wheatstone in 1867, when he invented a cipher device which he called The Cryptograph. He described it in a volume entitled The Scientific Papers of Sir Charles Wheatstone, published in 1879 by the Physical Society of London. Here is a picture of the Wheatstone device in my private collection (fig. 112). What Sir Charles did was to make the outer circle of letters (for the plain text) comprise the twenty-six letters of the alphabet, plus one additional character to represent "space." The inner circle, for cipher equivalents, contains only the twenty-six letters of the alphabet, which can be disarranged in a mixed sequence. Two hands, like the hour and minute hands of a clock, are provided, and they are under control of a differential gear mechanism, so that when the long or "minute hand" is advanced to make a complete circuit of the letters on the outer circle, the short or "hour hand" advances one space or segment on the inner circle. In figure 112, for example, the plaintext letter G is represented by the cipher letter A, that is, Gp = Ac. If the long hand is now advanced in a clockwise direction for one revolution, Gp will be represented no longer by Ac but by Gc" the letter immediately to the right of Ac on the inner circle. In encipherment the long hand is always moved in the same direction (clockwise, for example), and its aperture is placed successively over the letters on the outer circle according to the successive letters of the plaintext message, the cipher equivalents being recorded by hand to correspond with the letters to which the short hand points on each encipherment. In this way, identical letters of the plain text will be represented by different and varying letters in the cipher text, depending upon how many revolutions of the long hand intervene between the first and subsequent appearances of the same plaintext letter. Thus, with the alphabets shown in figure 112, and with the initial setting Gp =Ac, the word "reference" would be represented in cipher as follows:
REFERENCE
XZZZBGQAM,
in which it will be seen that repeated letters in the plain text are represented by different letters in the cipher text. Correspondents must naturally agree upon the mixed alphabet used in the inner circle and the initial positions of the two hands at the beginning of the encipherment of a message. In decipherment, the operator moves the long hand again clockwise, until the hour hand points to the cipher letter in the plaintext letter that is seen through the aperture at the end of the long hand on the outer circle. Thus, in the case of the example given above, the cipher letters XZAABGQAM will be found to represent the word REFERENCE.
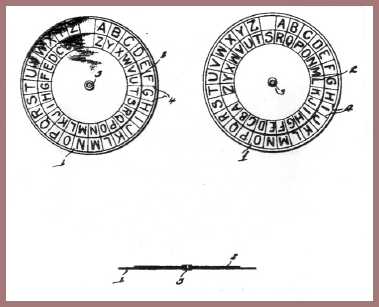
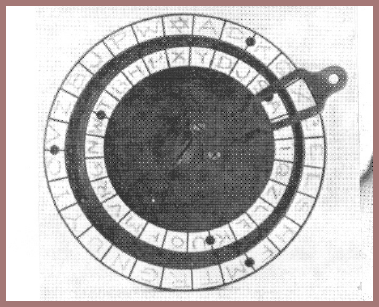
During World War I, sometime in 1917, the British army resuscitated Wheatstone's cryptograph and improved it both mechanically and cryptographically. Here's a picture of the device (fig. 113), in which it will be seen that there are now no longer the "minute" and "hour" hands but a single hand with an opening or window that simultaneously disclosed both the plain and the cipher letters. When the single hand is turned, the inner circle of segments, which are made of a substance upon which letters may be written in pencil or in ink is advanced eccentrically and against a similarly made outer circle of segments. In this improvement on the original Wheatstone device, both sequences of letters are now mixed sequences. Making the outer circle also a mixed sequence added a considerable degree of security to the cipher. When it was proposed that all the Allied armies use this device for field cryptocommunications and its security had been approved by British, French, and American cryptologists (both at GHQ-AEF and at Washington), an opportunity to agree or disagree with the assessment of these cryptologists was given me while still at Riverbank. I was able to show that the modified Wheatstone cryptograph was still insufficiently secure for military purposes, and the devices, thousands of which had been manufactured and issued, were withdrawn. If you are interested in the method of solution I used, you will find it in Riverbank Publication No. 20, entitled Several Machine Ciphers and Methods for their Solution (1918). A better method of solution was devised by me about 1923.
Some years later, and almost by sheer good fortune, I learned that a cipher machine was in the museum of a small town in Connecticut named Hamden. I was interested and wrote to the curator of the museum, requesting that he lend the device for a short period to me as principal cryptanalyst of the War Department. Imagine my astonishment and pleasure when I unpacked the box upon its receipt and found a device, beautifully made and encased in a fine mahogany case, with its inventor's name, Decius Wadsworth, and the date, 1817, engraved on the face of the machine, which was nothing but another version of the Wheatstone Cryptograph. Here's a picture of it (fig. 114). There are good reasons to believe that the model was made by Eli Whitney. Mechanically, it was similar to the British modification, except that the outer sequence had thirty-three characters, the inner, twenty-six, so that the differential gear instead of operating on the ratio of 27 to 26 was now on the ratio 33 to 26. Thus, Colonel Decius Wadsworth, who was then the first Chief of Ordnance of the U.S. Army, had anticipated Wheatstone by over sixty years in this invention. He also anticipated the British army cryptologists of World War I by a whole century in their modification of Wheatstone's original, because in the Wadsworth device, too, there was only one hand and both alphabets could be made mixed sequences. This is very clearly shown in figure 115 as regards the outer sequence, and I believe the inner one could also be disarranged, but the picture does not clearly show this to be the case, so that I am not sure as to this point. I returned the device a good many years ago, and it is now on display in the Eli Whitney Room of the New Haven Historical Society's Museum.
The next device I bring to your attention is shown in figure 116, a device invented by a French army reservist, Commandant Bazeries, who for some ten years valiantly but unsuccessfully tried to get the French army to adopt it. He included a description of his device, which he called his "Cryptographe Cylindrique" or "cylindrical cryptograph," in a book published in 1901 in Paris.[34] He had, however, previously described his device in an article entitled "Cryptographe à 20 Rondelles - alphabets (25 lettres par alphabet)," published in 1891.[35] In this device there is a central shaft on which can be mounted twenty numbered disks on the peripheries of which are differently mixed alphabets of twenty-five letters each. The disks can be assembled in some prearranged or key sequence on the shaft, from left to right, but they can be revolved thereon and then locked into position on the shaft by pushing in the locking disk at the extreme left. The first twenty letters of the plain text of a message are first aligned, as seen in figure 116 (JE SUIS INDÉCHIFFRABLE = "I am indecipherable"); the disks are then locked into position so that the whole assembly can be turned; and as cipher text one may select anyone of the other twenty-four rows of letters, which are recorded then by hand on paper. Then the next twenty plaintext letters are aligned, one of the other twenty-four rows of letters selected and recorded, etc. To decipher a message, the disks having been assembled on the shaft in accordance with the prearranged or key sequence, one takes the first twenty cipher letters, aligns and then locks them into position, and then turns the whole cylinder, searching for a row of letters which form intelligible text. There will be one and only one such row, and the plaintext letters are recorded. Then the next twenty letters of cipher are aligned, etc.
Another French cryptologist, the Marquis de Viaris, soon showed how messages prepared by means of the Bazeries cylindrical cipher could be solved.[36] Maybe that is why Bazeries wasn't too successful in his attempt to get the French army to adopt his device. But in the United States there were apparently none who encountered either what Bazeries or de Viaris wrote on the subject. Captain Parker Hitt, U.S. Army, whom I have mentioned in a previous lecture, in 1915 invented a device based upon the Bazeries principle but not in the form of disks mounted upon a central shaft. Instead of disks, Hitt's device used sliding strips. Here is a picture of his very first model (fig. 117), which he presented to me sometime in 1923 or 1924. But I first learned about his device sometime in 1917 while still at Riverbank and solved one challenge message put up by Mrs. Hitt, a Riverbank guest for a day. In meeting the challenge successfully (which brought a box of chocolates for Mrs. Friedman from Mrs. Hitt), I didn't use anything like what I could or might have learned from de Viaris, because at that time I hadn't yet come across the de Viaris book. I solved the message by guessing the key Mrs. Hitt employed to arrange her strip alphabets. She wasn't wise to the quirks of inexperienced cryptographic clerks: she used RIVERBANK LABORATORIES as the key, just as I suspected she would. The device she brought with her was an improved model: the alphabets were on paper strips, and the latter were glued to strips of wood, as seen in figure 118.
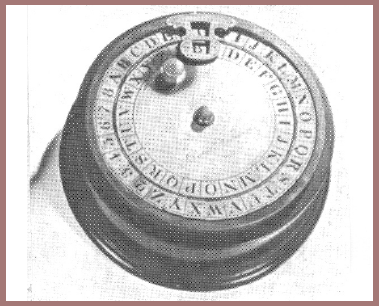
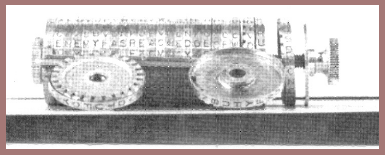
Captain Hitt brought his device to the attention of the then Major Mauborgne, whom I have also mentioned in a previous lecture and who was then on duty in the Office of the Chief Signal Officer in Washington. There is some question as to whether it was Hitt who first brought his device to Mauborgne's attention; Mauborgne later told me that he had independently conceived the invention and, moreover, had made a model using disks instead of strips. I have that model, a present from General Mauborgne many years later. It is made of very heavy brass disks on the peripheries of which he had engraved the letters of his own specially devised alphabets. In 1919, after my return to Riverbank from my service in the AEF, Mauborgne sent Riverbank the beginnings (the first twenty-five letters) of a set of twenty-five messages enciphered by his device and alphabets. He also sent the same data to Major Yardley, in G-2. Nobody ever solved the messages, even after a good deal of work and even after Mauborgne told us that two consecutive words in one of the challenge messages were the words "are you." Many years later I found the reason for our complete lack of success, when I came across the plain texts of those messages in a dusty old file in one of the rooms occupied in the old Munitions Building by the Office of the Chief Signal Officer. Here is a picture of the beginnings of the first six messages (fig. 119). Mauborgne, when I chided him on the unfairness of his challenge messages, told me that he had not prepared them himself – he had an underling (Major Fowler was his name, I still remember it!) prepare them. In our struggles to solve the challenge messages, we had assumed they would contain the usual sorts of words found as initial words of military messages. It was the complete failure by Riverbank and G-2 to solve the challenge messages that induced Mauborgne to go ahead with the development of his device. It culminated in what became known as Cipher Device, Type M-94. Here is a picture of it (fig. 120). That device was standardized and used for at least ten years in the United States by the Army, the Navy, the Marine Corps, the Coast Guard, the intelligence operations of the Treasury Department, and perhaps by other agencies.
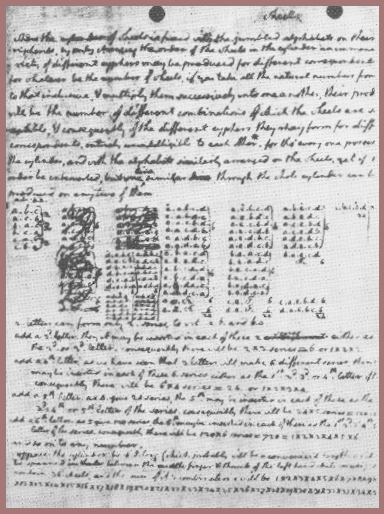
In 1922, a wartime colleague, the late Captain John M. Manly (professor and head of the Department of English at the University of Chicago) brought to my attention a photostat of two pages of a holographic manuscript in the large collection of Jefferson Papers in the Library of Congress. It described his invention entitled "The Wheel Cypher," and figure 121 is a picture of the second page showing Jefferson's basis for calculating the number of permutations afforded by the set of thirty-six wheels of his device. He didn't attempt to make the multiplication; he didn't have an electronic digital computer – for the total number is astronomical in size. Jefferson anticipated Bazeries by over a century, and the Hitt-Mauborgne combination by almost a century and a half.
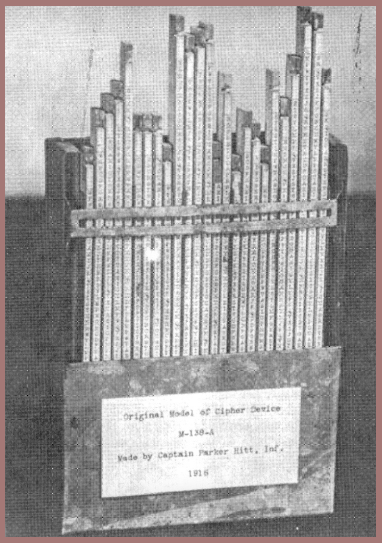
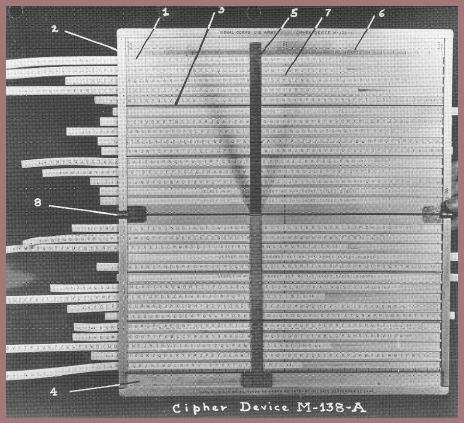
It soon became apparent to both army and navy cryptologists that a great increase in cryptosecurity would be obtained if the alphabets of the M-94 device could be made variant instead of invariant. There began efforts in both services to develop a practical instrument based upon this principle. I won't take time to show all these developments but only the final form of the one adopted by the Army, Strip Cipher Device Type, M-138A (fig. 122). This form used an aluminum base into which channels with overhanging edges were cut to hold cardboard strips of alphabets which could be slid easily within the channels. It may be of interest to you to learn that after I had given up in my attempts to find a firm that would or could make such aluminum grooved devices in quantity, Mrs. Friedman, by womanly wiles and cajolery on behalf of her own group in the Coast Guard, succeeded in inducing or enticing one firm to make them for her. And that's how the first models of strip cipher devices made of aluminum by the extrusion process came about, and how the U.S. Army, by administrative cooperation on an interservice level and technical cooperation on a marital level, found it practical to develop and produce in quantity its Strip Cipher Device, Type M-138A. This was used from 1935 to 1941 or 1942 by the Army, the Navy, the Marine Corps, the Coast Guard, et al., including the Treasury and State Departments. It was used as a back-up system even after the armed services as well as the Department of State began employing much better and more sophisticated cipher machines of high speed and security.
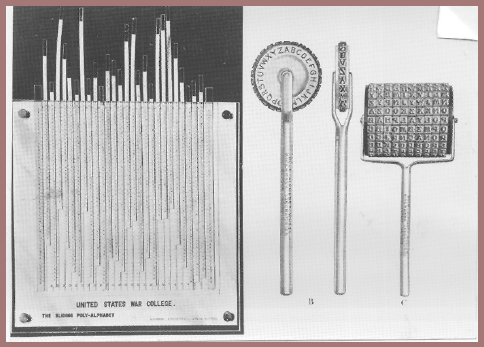
Thus far we have been dealing with cipher devices of the so-called "hand-operated" type. None of them can readily be considered as being "machines," that is, apparatus employing mechanically driven members upon which alphabetic sequences can be mounted so that constantly changing sequences of cipher alphabets are produced. We come now to types of apparatus that can be called machines, and one such machine is shown in figure 123. It is called the Kryha machine, after the name of its German inventor, who unfortunately committed suicide a few years ago, perhaps because the last model of his improved machine failed to impress professional cryptologists. The Kryha has a fixed semicircle of letters against which is juxtaposed a rotatable circle of letters. Both sequences of letters can be made mixed alphabets (the segments are removable and interchangeable on each sequence). The handle at the right serves to wind a rather powerful steel clock spring that drives the rotatable platform on which the letters of the inner circle are mounted. In figure 124 can be seen something of the inner mechanism. The large wheel at the right has segments that are open or closed, depending upon the "setting" or key. This wheel controls the angular displacement or "stepping" of the circular rotatable platform. The initial juxtaposition of the inner or movable alphabet against the outer or fixed one, as well as the composition of these alphabets, is governed by some key or other prearrangement. The cipher equivalents must be recorded by hand. After each encipherment, the button you saw in the center of the panel in figure 123 is pushed down, the inner wheel is advanced 1, 2, 3, 4 . . . steps, depending on the key, and the next letter is enciphered, etc. The pictures I've shown you apply to the latest model of the Kryha; as regards the first model, which came on the market sometime in the 1920s, a German mathematician produced an impressive brochure showing how many different permutations and combinations the machine afforded. Here's a picture of a couple of pages of his dissertation (fig. 125), but even in those days professional cryptanalysts were not too impressed by calculations of this sort. With modern electronic computers such calculations have become even less significant.
Let us now proceed with some more complex and more secure machines. In this next illustration (fig. 126), you see a machine that represents a rather marked improvement by a Swedish cryptographic firm upon the ones shown thus far. It is a mechanico-electrical machine designated as Cryptographe B-21. Here for the first time you see a cryptographic machine provided with a keyboard similar to that on an ordinary typewriter. Depressing a key on this keyboard causes a lamp to light under one of the letters on the indicating bank above the keyboard. At the top of this machine can be seen four wheels in front of two rear wheels. The four front wheels are the rotating elements that drive the two rear wheels; the latter are electrical commutators that serve as connection-changers to change the circuits between the keys of the keyboard and the lamps of the indicating board. There isn't time to discuss in detail the internal works that control the rotating elements and ciphering wheels, of which you'll see a glimpse later, but I must show you the next step in the improvement of such apparatus, which made it possible to eliminate the really tedious job of recording, by hand on paper, the results of operation. This was done by means of associating a type-writer with the cryptocomponent. Here is a picture (fig. 127) that shows the assembly – the B-21 connected to a Remington electric typewriter, modified to be actuated by impulses from the cryptomachine. Of course, it was natural that the next step would be to make the recording mechanism an integral part of the cryptomachine. This you can see in the next picture (fig. 128a), in which the four rotating members referred to in connection with figure 126 and which control the two commutators also mentioned in connection with that figure are seen. The slidebar mechanism, in figure 128b, at the right, is called the "cage" or "barrel," and it controls the displacements of the printing wheel, causing the proper letter to be printed upon the moving tape seen at the front of the machine.
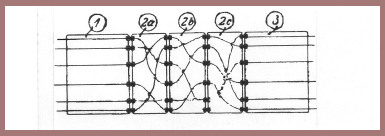
Now we come to some very important new types of electric cipher machines first conceived and developed in Europe but very soon thereafter, and probably independently, also in the United States. In the cryptocomponent of these machines, the electrical paths between the elements representing the plaintext characters and those representing their cipher equivalents are constantly varied by multiple connection-changers with the cryptocomponent. In early European models of this type of machine, the connection-changers consisted of a frame upon which insulated wires were mounted to connect in an arbitrary manner a series of contacts on one side of the frame to a similar number of contacts on the other side of the frame. This frame was slid between two fixed contactbearing members, one on each side of the frame. By sliding the frame between the two fixed members, the paths between the opposite contacts on the latter could be varied as a whole set with a single movement of the sliding frame. A connection changer of this sort is shown in schematic form in figure 129a, where the sliding member 10 slides between fixed members 11 and 12, thus changing the electrical paths between the keyboard and the printing mechanism. The connection-changer 10 is moved to the left or right 1,2,3, . . . positions, as determined by a cam mechanism. We won't go into this type of machine any further because it wasn't long before inventors saw the advantages of using, instead of slideable connection-changers, mechanisms performing a similar function but of a rotatable nature that we now call "electric-rotors," and that rotate, usually step-by-step, between circular, fixed, contact-bearing members called "stators." Rotors and stators of this type are shown in schematic form in figure 128b, there being a left-hand stator labeled 1, three rotors labeled 2a, 2b, 2c, and a right-hand stator labeled 3. The connections leading away from stator 1 toward the left go to the keys of the keyboard; those leading away from rotor 3 toward the right go to the magnets of the printer. About these elements we shall explain some details presently.
In Europe, the first machine using rotors and stators was that developed by a German firm, the Cipher-Machine Company of Berlin, and was appropriately named the ENIGMA. Here's a picture of it, figure 129c, in which you see a keyboard, a set of eight rotors juxtaposed in line, or, as we now generally say, "juxtaposed in cascade," and a printer. This machine was apparently too complicated for practical usage and was superseded by a second model, which also printed and was also unsuccessful. One of the difficulties with these two models was that a multiple switch with many contacts to be made simultaneously was required in order to establish an operative encipher-decipher relationship, so that if in enciphering the letter Dp, for example, the corresponding key on the keyboard is depressed, and a cipher letter, say Fe, is printed; then on deciphering the letter Fe, the corresponding key on the typewriter is depressed, and the plaintext letter Dp will be printed. In this machine this could be done only by making the current for decipherment traverse exactly the same path through the rotors and stators that it had traversed in encipherment. This was the function of the multiple switch shown schematically in figure 129d, in which a machine with only six characters (A to F) is depicted. In the left-hand circuit diagram, Dp is being enciphered and produces Fe; in the right hand circuit diagram Fe produces Dp. But the switching mechanisms 4 and 4′ in figure 129d make things a bit complicated because they are within one switching member that operates in one of two positions, one for encipherment, the other for decipherment, and many contacts must be established in one fell swoop, so to speak. I won't go into further details as to its construction because a clever inventor of that German firm came up with a new idea which greatly simplified matters, in regard not only to the cryptocomponent but also to the indicating mechanism. We may quickly explain how the matter of simplifying the indicating mechanism was accomplished, namely, by eliminating the printer altogether and replacing it with a simple bank of flashlight-type lamps. We'll skip the third model of the ENIGMA, which was only a slightly simpler version of the fourth model, which is shown in figure 130a. This one comprised a keyboard, a bank of indicating lamps, and a set of rotors and stators, but no printer.
In figure 130a is seen the machine with its coverplate down. At the front is the keyboard; above it, the indicator board, consisting of twenty-six lamps beneath glass disks upon which letters have been inscribed. Above the indicator board are seen four oval apertures with covers, through which letters can be seen. To the right of each aperture can be seen the peripheries of four metal scalloped wheels, the first being unmarked but the next three being labeled 1. A switch lever seen at the right can be set to encipher, decipher, or neutral positions. In figure 130b is seen the machine with the coverplate removed, exposing the internal cryptocomponent. Three rotors, labeled 4 in this figure, are seen, and affixed to them are the scalloped metal rings, which are not labeled. A fourth scalloped ring, labeled 11 in figure 130b, is affixed to another rotor like member labeled 8 in that figure. This member looks like an ordinary rotor in this picture but is really a stator of special construction to be described presently.
Perhaps it would be useful at this point to show you what ENIGMA rotors look like and these can be seen in figures 131a-c. In each of these rotors is a circle of twenty-six equally spaced contact pins on one face of the rotor (fig. 131a) and a circle of twenty-six equally spaced contact surfaces on the other face (fig. 131b). Insulated wires connect the contact pins on one face to the contact surfaces on the other face, these connections being made in an arbitrary, systematic, or unsystematic manner, depending on certain circumstances into which we need not go. When the rotors are juxtaposed as seen in figure 131c, the contact pins on one rotor are brought against the contact surfaces on the adjacent rotor, so that an electric current will traverse all three rotors via a certain path. The large scalloped rings are for setting the rotors in alignment manually when they are juxtaposed and rotated to form a portion of the key setting (see E*Z*R in figure 131c). The toothed metal ring seen in figure 131a is associated with a cam mechanism so that a rotor will be advanced one step when the preceding rotor has made a sufficient number of steps to permit a cam to fall into a notch in the ring. Sometimes a complete revolution will be necessary before this happens, depending on the initial key setting. The first rotor immediately to the left of the stator at the extreme right in figure 131b, however, always makes one step with each depression of the key on the keyboard. The advance of the rotors is similar to that of the wheels of a counter like that of the odometer on your automobile.
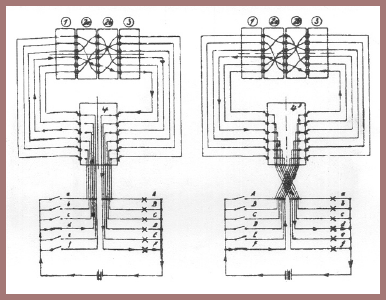
We come now to the matter of simplifying the cryptocomponent of the ENIGMA shown in figure 130b to eliminate the multiple switching mechanism shown in figure 129d, without much loss in security (or so it would seem, at least). Let us see how this simplification was accomplished in the ENIGMA, by showing figure 129d, in connection with the first ENIGMA model. For this purpose I show you now figure 132, in which the encipherdecipher circuitry is clearly seen in a machine having, for illustrative purposes, only three rotors, labeled 1, 2, 3, rotatable between two stators, the one on the left labeled 4, that on the right labeled 5. Stator 4 is fixed or nonrotatable in this model, and it has twenty-six contacts on its left face, only two of which are shown. These contacts are connected fixedly to the keys of the keyboard and to the lamps of the lamp board. Stator 5 is rotatable, but only manually, and it has twenty-six contact surfaces on its right face, only two of which are shown. But in this stator the twenty-six contact surfaces are interconnected in pairs by thirteen insulated wires passing through the member. Thus, a current entering one of the twenty-six contact surfaces on the right face goes through the stator and returns to one of the remaining twenty-five contact surfaces. For this reason it is called a "reflector" and serves to return a current that has come from one of the twenty-six contacts on the fixed stator at the extreme right, then through the rotors and into the reflector via one path, returns through the rotors and back into the stator via a different path, emerging at one of the twenty-five other contacts on the left face of the stator at the extreme right. This circuitry assures that in a particular setting of the machine, if Yp = Zc, for example, then Yp = Zc, that is, the cipher is reciprocal. It also has as a consequence that no letter can be enciphered by itself, that is, Yp, for example, cannot be represented by Yc, no matter what the setting of the cryptocomponent is; this is true of all the other letters of the alphabet in regard to the ENIGMA.
If you like, you may trace the path traversed by the current in figure 132 in encipherment and decipherment, where Zp = Yc and Zp = Yc, but Zp cannot be represented by Zp, nor can Yp be represented by Yc. I have already told you briefly about how the rotors are advanced. In the ENIGMA shown, the total number of encipherments that can be made before the key setting of the machine returns to its original setting, as seen through the windows I referred to a few moments ago when showing you the first picture of the fourth model ENIGMA, is 16,900, viz, 263 – 262, and not 263, for technical reasons I won't go into now.
Power for the electrical circuits is provided by small dry cells in the machine. This model enjoyed a fair degree of financial success, but when Hitler came into power further promotion and sales of the ENIGMA were prohibited. Suffice it to say that it became the basis for machines used by the German armed forces in World War II.
In the United States, in about 1910, a California inventor named Edward H. Hebern (fig. 133) began to develop cipher machines, but he was merely traveling along roads that had this far led other inventors nowhere. In about 1918 he struck out along a new path in America. I don't know whether he independently conceived the idea of a machine using an electric rotor or had in his research come across patents covering very recently invented European electrical cipher machines. At any rate, Hebern's first application for a patent covering a rotor machine, which he called an "electric code," was filed on 31 March 1921, and a patent was issued on 30 September 1924. Figure 134 shows the first machine he had built. You will note that the cryptocomponent had but one rotor, and like the early models of the ENIGMA, it was associated with a printing mechanism, a typewriter operated electrically. Hebern's cipher system was also similar in nature with that of the first two ENIGMA models - a full reversing switch was essential since the electric current had to traverse exactly the same path in decipherment as it had in encipherment. I don't think he ever conceived the idea of using a reflector; perhaps he was too late. At any rate, he never incorporated that idea in any of his machines. Moreover, I don't think he had any idea of the cryptologic advantages and disadvantages of a cryptocomponent using a "single traverse" or "straight through" system of rotors, as compared with one using a "double traverse" or "twice through" system of rotors with a reflector. But we won't go into that here, for it's a pretty involved piece of business.
But Hebern's rotors had a virtue not possessed by those of the ENIGMA machines, and not incorporated in the rotors of the latter, namely, the wirings of the rotors could be readily changed by the user of the Hebern machine, a feature of great importance in cryptosecurity (fig. 135). Hebern interested our navy in his three-rotor model (fig. 136) and as a result of conferences with navy cryptanalysts he built the five-rotor model, which is seen in figure 137. Another very important security feature I have thus far failed to mention about the Hebern rotors was that they could be inserted in a "right-side up" or in an "upside-down" position in the machine, which could not be done with the ENIGMA rotors. The navy liked the five-rotor model, even though it was not a printing machine, assuming properly that this could be added later on. Therefore, the navy placed a purchase order for two such machines on 30 July 1921 and was considering purchasing a rather large number of them later. Lieutenant Strubel, then chief of the Navy's Code and Signal Section of the Office of Naval Communications but now a retired vice admiral, asked me to study the machine for its cryptosecurity. The Navy had but two machines, neither of which could be made available, so I induced the Chief Signal Officer to buy a couple of them for Army study. The order was placed on 7 October 1924. The rotor wirings of the Army's machines were altogether different from those of the Navy, a fact I discovered simply by asking Strubel to encipher a few letters on his machine, using settings I specified. After some study I reported that in my opinion the security of the machine was not as great as the Navy thought. The result was a challenge, which I accepted. The Navy gave me ten messages put up on its machine, and I was successful in solving them. There isn't time to go into the methods used, but if you are interested you can find them described in my brochure entitled Analysis of a Mechanico-Electrical Cryptograph, Part I (1934), Part II (1935).
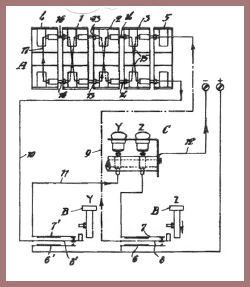
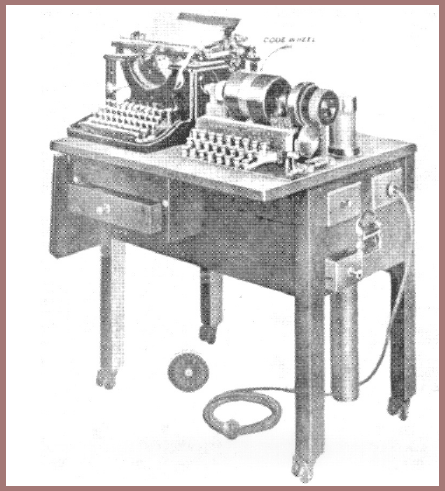
Hebern built several more models for Navy, and these had printing mechanisms associated with them, but Navy dropped negotiations with Hebern when it became obvious that he was not competent to build what Navy wanted and needed. Navy then established its own cryptographic research and development unit at what is now known as the Naval Weapons Plant in Washington. Army developed at the Signal Corps Laboratories at Fort Monmouth a machine known as Converter M-134, and here's an illustration (fig. 138) showing what it looked like. Army and Navy went separate ways in such work for a number of years, but finally, in 1938 or 1939, close collaborating brought as a result an excellent machine that was developed and produced in quantity by the Teletype Corporation in Chicago. This machine was distributed and used very successfully by all our armed forces from 1940 to the end of World War II and for some years thereafter. In accordance with Navy nomenclature, it was designated as the ECM Mark II, ECM standing for "electric cipher machine"; in the Army it was designated as the SIGABA, in accordance with a nomenclature in which items of Signal Corps cryptographic material were then given short titles with the initial trigraph SIG.
The ECM-SIGABA is a rather large machine requiring a considerable amount of electric power and much too heavy to be carried about by a signal operator performing field service. It was safeguarded with extreme care and under strictest security regulations during the whole period of World War II operations. None of our allies was permitted even to see the machine, let alone have it. The British had their own electric cipher machine, which they called TYPEX. In order to facilitate intercommunication between U.S. and British forces, adaptors were developed so that messages could be exchanged in cipher between American and British units. This system of intercommunication worked satisfactorily and securely.
Certain improvements in the method of usage and the development of special components, to be associated with the ECM-SIGABA for automatic decipherment by perforated tapes, were introduced during the wartime employment of these machines. But the ECM-SIGABA as originally developed and produced became obsolete some years after the close of hostilities when newer and better machines developed by NSA cryptologists and engineers replaced them, but not because there were ever any indications that messages enciphered on the machine had been deciphered by the enemy. As a matter of historical fact, it may be stated that all enemy efforts to solve such messages were fruitless, and it is also a fact that no machines were ever captured by the enemy; nor were there ever any suspicions that a machine had been exposed to enemy inspection at any time. Once and only once were there any apprehensions in this regard, when through a careless disregard of specific instructions, a truck and an attached trailer in which this machine and associated material were housed were stolen during the night when parked in front of the headquarters of the 28th Division during the Battle of the Bulge. A great search was instituted, during the course of which a river was diverted, and the trailer, with all its contents intact, was found resting on the former bed of the diverted stream. The episode terminated in court-martial proceedings, and there were no more incidents of this sort. Let me add that such apprehensions as were entertained at the time of this temporary loss of custody of the machine were based not upon the possibility that its usefulness was at an end but upon the fear that the Germans would make "Chinese copies" of it and thus be in a position to turn our very valuable weapon against us.
About five years before the SIGABA was put into service, the Army's need for a small cipher machine for field use became obvious. The strip cipher system was not suitable for this purpose, nor was the Army's first keyboard-operated electrical rotor machine, Converter M-134, suitable, for reasons already indicated in connection with the SIGABA. The sum of $2,000 was allotted by the Army to the Chief Signal Officer for the development of a cipher machine small enough to be suitable for field usage but also affording adequate security. The funds were naturally turned over to the Signal Corps Laboratories (SCL) at Fort Monmouth, New Jersey, for this development. The military director of the laboratories, spurning all proffered technical guidance or assistance from the Signal Intelligence Service (SIS) and deciding that his staff had sufficient know-how without outside assistance, developed a machine that required no electricity, being all mechanical. On its completion the model was sent to the Signal Intelligence Service for a cryptosecurity test. Two short messages were enciphered by the Chief of the SIS, using settings of his own selection. He then handed the messages and the model over to me as technical director, and I turned them over to two of my assistants. The reason for turning over the model with the messages was that it must be assumed that under field conditions machines will be captured. One of the two test messages was solved in about twenty minutes; the other took longer – thirty-five minutes. This test brought an ignominious end to the SCL development, brought about by the failure on the part of the military director of the SCL to recognize that cryptographic invention must be guided by technically qualified cryptanalytic personnel. Unfortunately, all the available funds had been expended on this unsuccessful attempt; none was left for a fresh start on a development with technical guidance from the SIS.
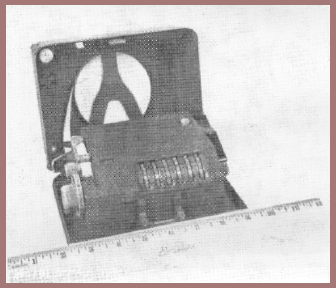
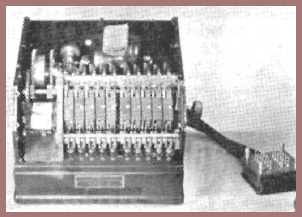
It was about this time that a small mechanical machine which had been developed and produced in quantity by a Swedish engineer in Stockholm named Hagelin (fig. 139) was brought to the attention of the Chief Signal Officer (CSO) of the U.S. Army by a representative of the Hagelin firm. The SIS was asked to look into it, and as technical director, I turned in an unfavorable report on the machine for the reason that although its cryptosecurity was theoretically quite good, it had a low degree of cryptosecurity if improperly used – and practical experience had taught me that improper use could be expected to occur with sufficient frequency to jeopardize the security of all messages enciphered by the same setting of the machine, whether correctly enciphered or not. This was because the Hagelin machine operates on what is termed the key-generator principle, so that when two or more messages are enciphered by the same key stream or portions thereof, solution of those messages is a relatively simple matter. Such solution permits recovery of the settings of the keying elements so that the whole stream can be produced and used to solve messages that have been correctly enciphered by the same key settings, thus making a whole day's traffic readable by the enemy. I tried to assure the CSO that my opinion was not motivated by a factor commonly called "NIH" – "not invented here" but I was overruled by my military superiors, and properly so, because neither the SIS nor the SCL had developed anything that was better than the Hagelin machine, or even as good, with all its mechanical deficiencies and cryptographic weaknesses taken into consideration. Accepting, though somewhat reluctantly, the well-considered directive of the CSO, the SIS pointed out where improvements could be made, and the desired modifications were incorporated in the machine, which became known as the Converter M-209. Over 100,000 of them were manufactured in 1942–1944 by the Smith-Corona Typewriter Company at Groton, New York. Here's an illustration (fig. 140a) showing the machine, which was extensively used by all our armed forces during World War II, and here's another (fig. 140b) showing its internal mechanism. It turned out that under field conditions the fears upon which I had based my personal rejection of the Hagelin machine proved to be fully justified – a great deal of traffic in it was solved by the Germans, Italians, and Japanese. If I was chagrined or suffered any remorse when I learned about the successful enemy attacks on M-209 traffic, those feelings were generated by my sense of having failed myself to think up something better than the M-209 despite the shortsighted attitude of the military director of the SCL.
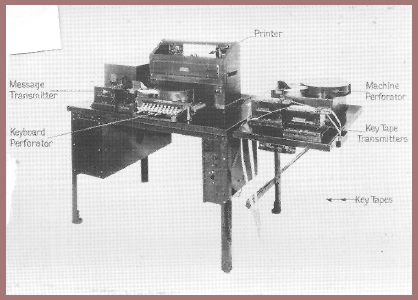
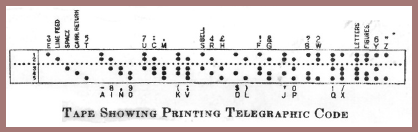
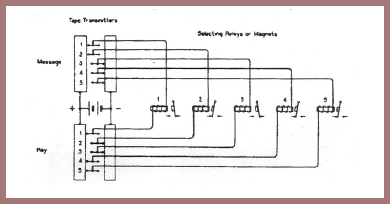
With the introduction of printing telegraph or teleprinting machines for electrical communications, the need became pressing for a reliable and practical cryptographic mechanism to be associated or integrated with such machines. The first apparatus of this sort in the United States, shown in this photo (fig. 141), was that developed by the American Telephone and Telegraph Company in 1918, as a more or less simple but ingenious modification of its ordinary printing telegraph. First, a few explanatory words about the basic principles of the modern teleprinter may be useful. This principle employs what is called the "Baudot Code," that is, a system in which permutations of two different elements taken in groups of five are employed to represent characters of the alphabet. Curiously enough, Francis Bacon was the first to employ such a "code" way back in the early seventeenth century, and I showed you the one he used in Lecture No. II (see figure 31). These two elements in Bacon's "code" were a's and b's; he used but 24 of the 32 permutations available (25=32). For electrical communications the two elements may be positive and negative currents of electricity, or the presence and absence of current, the latter system often referred to as being composed of "marking'" and "spacing" elements, respectively. The illustration in figure 142 depicts the Baudot or "five-unit code" in the form of a paper tape in which there are holes in certain positions transverse to the length of the tape. The holes are produced by a perforating mechanism; the small holes running the length of the tape are "feed-holes" by means of which the tape is advanced step by step. You will note that there are five levels on which the perforations appear. The letter A, for example, is represented by a perforation only on the 1st and 2nd levels, the 3rd, 4th and 5th levels remaining unperforated; the letter I is represented by holes in positions 2 and 3, no holes on the other three levels, etc. The English alphabet uses twenty-six of the thirty-two permutations; the remaining six permutations are used to represent the so-called "stunt characters," which I will now explain. The third and fourth characters from the right-hand end of the tape are two permutations labeled "letters" and "figures," respectively. These are equivalent to the "shift and "unshift" keys on a typewriter keyboard, for "lower" and "upper" case. When the "letters" key is depressed, the characters printed are the twenty-six letters of the alphabet (all capital letters); when the "figures" key is depressed, the characters represented are similar to those printed on a typewriter when the "shift" key is depressed. The second, third, and fourth permutations at the left-hand end of the tape are also stunt characters and represent "line feed," "space," and "carriage return," and they perform electrically in a teleprinter what is done by hand on a typewriter: "line feed" causes the paper on which the message is printed to advance to the next line; "space" does exactly what depressing the space bar on a typewriter does, etc. When there are no holes anywhere across the taps, the character is called a "blank" or "idling" character – nothing happens: the printer does no printing, nor is there any "stunt" functioning by the printer, but the tape merely advances.
In modifying the standard printing telegraph machine to make it a printing telegraph cipher machine, or to put the matter in a slightly different way, in developing the printing telegraph cipher machine, the American Telephone and Telegraph Company was fortunate in having the services of a twenty-three-year old communications engineer named Gilbert S. Vernam (fig. 143), who conceived a brilliant principle and an automatic method for enciphering teleprinter communications. The principle and method turned out to be so useful and valuable, not only in the United States but also internationally, that it has come to bear his name and is often referred to as the "Vernam principle," the "Vernam rule," the "Vernam mod-2 addition," etc. Vernam saw that if in accordance with some general but invariant rule the marking and spacing elements of a five-unit code group were combined one by one with those of another five-unit code group, which would serve as a keying group, and the resultant five-unit group transmitted over a circuit and combined at the receiver with the same keying group in accordance with the same general rule,[37] the final result would be the original character. Vernam conceived the idea early in 1918 or perhaps late in 1917. I have a copy of Vernam's circuit diagram, dated and witnessed on 27 February 1918, but the application for a patent thereon, with his name as inventor, was filed in the U.S. Patent Office on 13 September 1918, and Patent No. 1,310,719 was granted on 22 July 1919, covering the invention entitled a "Secret Signaling System."
The following more detailed description of Vernam's patent on the foregoing cipher system is extracted from a paper[38] written by one of the AT&T Company's engineers [R.D. Parker] who was associated with Mr. Vernam at the time the invention was conceived and who, a few years after retirement from that company, became one of NSA's consultants:
This patent describes an "on-line" system, each character being enciphered, immediately transmitted, and in turn deciphered without delay at the receiving terminal. Thus, characters of a message in perforated tape form are automatically combined with other or key characters which are transmitted over the circuit. At the receiver an identical group of key characters is used to provide signals for combination with the arriving signals, character by character, to produce the original message. The combining rule for these operations disclosed in the patent was one in which like code elements produced "spaces" and unlike elements, "marks," as shown below.
The cipher message tape prepared in this way is unintelligible in form and may be sent to the receiving station by messenger or by mail, or if desired, it may be transmitted by wire or radio and reproduced by another machine perforator at the receiving point. The cipher tape is there run through the message transmitter, where its characters combine with those of a duplicate key tape to reproduce the original message, which will be printed out in page form and in "plain text."
LENGTH OF KEY TAPE
With the system as described above, the key tape must be at least as long as the sum of all the message tapes used with it, as the messages will lose their secrecy to some extent if the key tape is used repeatedly. The use of a short repeating key may give sufficient secrecy for some uses, however.
A roll of tape 8 inches in diameter contains about 900 feet of tape and would serve to encipher about 18,000 words counting five printed characters and a space per word, without repeating the key. If sent at a average speed of 45 words per minute, this number of words would require 400 minutes or nearly 7 hours to transmit.
In order to reduce the amount of key tape required for handling large amounts of traffic, the "double key" system was devised.[39] In this system two key tapes are used, the ends of each tape being glued together to form a loop preferably about seven feet in circumference. The tapes should differ in length by one character or by some number which is not a factor of the number of characters in either tape. A separate transmitter is used for each tape and the characters of the two key tapes are combined, by a method similar to that shown in [figure 144], with those of the message tape to form the cipher message.
The result is the same as though the two key tapes were first combined to produce a long single nonrepeating key, which was later combined with the message tape. This long, single key is not, strictly speaking, a purely random key throughout its length as it is made up of combinations of the two original and comparatively short key tapes. The characters in this key do not repeat in the same sequence at comparatively short regular intervals, however, as would be the case if only one key tape loop were used.
The number of characters in this equivalent single key is equal to the product of the number of characters in the two tape loops, and may easily exceed 600,000 before any part of the key begins to repeat. If proper care is taken to use the system so as to avoid giving information to the enemy regarding the lengths of the two key tape loops or their initial settings and to avoid the possibility of ever reusing any part of the resultant single key, this system is extremely difficult to break even by an expert cryptanalyst having a large number of messages and full knowledge of the construction of the machine and its method of operation.
The foregoing double-key-tape system was placed into operation in 1918 on three start-stop circuits that were used for intercommunication among four stations serving Washington, New York, Hoboken, and Norfolk, and that, according to Parker [see footnote 20 below], "continued in operation for many months, even after the end of the war." In addition, a Signal Corps Company was organized to go to Europe with new equipment for installation of printing-telegraph circuits in France. This Signal Company was about ready to sail when the armistice was signed on November 11, 1918.
On my return to Riverbank in April 1919 upon being demobilized, I became an interested party in a rather warm argument conducted by letters exchanged between Colonel Fabyan, the Chief Signal Officer, the Director of Military Intelligence, and the War Department, regarding the cryptosecurity of the cipher printing telegraph system as used by the Signal Corps. The argument ended by successfully meeting a challenge by the Signal Corps to prove Fabyan's contention. The challenge consisted in sending Fabyan on 6 October 1919, and requesting him to solve, the cipher tapes of about 150 messages selected from one day's traffic in the system. On 8 December 1919 Fabyan sent a telegram to the Chief Signal Officer notifying him that solution had been accomplished. In order to prove that this was true, I sent a perforated cipher message tape to each of the officers named above. In order to decipher these messages, the Chief Signal Officer had to use his own key tapes, thus proving that Riverbank not only had solved the system but had recovered both key tapes that had been employed in enciphering the challenge messages, so that Riverbank was in a position to produce the plain text of any of the latter on request, if further proof of solution were needed or desired. I wrote a monograph on the solution, consisting of a basic paper of twenty-one typewritten pages, an Addendum 1 of ten pages, an Addendum 2 of twenty-five pages, and an Addendum 3 of six pages; a copy of each of these documents was sent to Washington. The solution was accepted with mixed feelings in Washington, especially on the part of Brigadier General Marlborough Churchill, the Director of Military Intelligence, who had signed a letter to the Chief Signal Officer, dated 8 August 1918, prepared by Captain Yardley to the effect that the cipher system in question "is considered by this office to be absolutely indecipherable."[40] General Churchill had the duty and courtesy to write a congratulatory letter to Colonel Fabyan, dated 24 March 1920, the Imal paragraph of which is as follows:
Your very brilliant scientific achievement reflects great credit upon you and your whole personnel. It would be impossible to exaggerate in paying you and Riverbank the deserved tribute for this very scholarly accomplishment.
The paper by Mr. Parker (see footnote 18) closes with the following final paragraph:
Perhaps some day Mr. Friedman will tell of the part that he and the Riverbank Laboratories played in the cryptanalytic phase of this development.
Mr. Parker was not aware that what he suggested had been done not only once but twice. The Ilrst time was immediately after the solution when copies of the writeup mentioned a moment ago had been sent to Washington where they had met the fate that often happens to documents of limited or special technical interest – complete disappearance in the voluminous files of bureaucracy. The second time was soon after the end of hostilities in World War II, when it was discovered that a certain outfit I won't name was using the double-tape keying system for its teleprinter communications. I rummaged through my own files and uncovered the handwritten manuscript of certain parts of what I had written at the close of the successful solution of that system while at Riverbank. My second writeup is a classified document, dated 21 July 1948, the subtitle of which is "Can Cryptologic History Repeat Itself?" It is possible that this writeup can be made available to those of you who are interested in reading it, if proper authority grants permission.
Mr. Parker's paper (see footnote 18) devotes a good deal of space to the contention that the only reason why the double-tape keying method was adopted was that the Signal Corps and specifically its representative, Colonel Mauborgne, "complained about the difficulties that might be experienced in the preparation and distribution of onetime random key tapes and seemed inclined to disapprove of the proposed system because of these difficulties. Since the system, when properly used, seemed obviously to be one that gave absolute secrecy, a discussion arose on the value of the system and on methods that might be devised for the production and distribution of long one-time key tapes having characters arranged at random." Parker points out that the original method of use contemplated the use of long tapes of this nature and that he and his associates felt the problem of producing and distributing long tapes "while presenting a challenge, was not impractical." I am glad to admit they were right, because during World War II and for years afterward tapes of this nature were produced by special machinery (in some cases as many as five copies being perforated and the sections numbered automatically in a single operation.) Distribution of and accounting for the tapes proved practical, too, and aside from an occasional error involving the reuse of a once-used tape, absolutely secure intercommunication by radio printing telegraphy was assured and was used between and among large headquarters where the volume of traffic justified the use of this equipment. The principal advantage was the simplicity of crypto-operations – no rotors to be set, no setup of rotors to be enciphered, no checking of equipment by deciphering the message before transmission, etc.
The AT&T Company Printing Telegraph Cipher equipments purchased by the Signal Corps were withdrawn soon after Riverbank proved the double-key-tape system insecure. The machines went into storage, when in due course most of them were dismantled. But after I left Riverbank at the end of 1920 and had joined the Chief Signal Officer's staff in Washington, I induced the Chief Signal Officer to resuscitate two equipments. These I employed, believe it or not, in compiling codes, called Division Field Codes, for use in training or in an emergency. I won't undertake to explain how I performed this stunt, for it was a stunt, but it worked very successfully. The codes were duly printed, issued, and used until there was no longer any need for codes of this type.
Cipher printing telegraphy was placed upon the shelf and more or less forgotten by Signal Corps communications engineers from 1920 until soon after Pearl Harbor. However, the leading members of the SIS maintained a theoretical cryptanalytic interest in such equipment, and in 1931 there came an opportunity to test such theories as were developed by them when a machine produced by the International Telephone and Telegraph (IT&T) Company evoked the interest of the Department of State as a possible answer to the needs of that department for rapid and secure cryptocommunications by radio. The secretary of state requested the secretary of war to study the machine. which was to be associated with a standard teleprinter, and to study it only from the point of view of security. For this purpose messages enciphered by the chief of the Communications and Records Division of the Department of State were provided. Here are two pictures of the teleprinter attachment (figs. 145a and 145b). It is a source of satisfaction to be able to tell you that the SIS quickly solved the test messages and therefore reported that the machine was quite insecure; but it is with much regret that I must now tell you who invented and developed the machine. It was a retired officer of the Signal Corps, none other than my old friend Colonel Hitt. I was as embarrassed to tell him about the results of our test as he was to force himself to listen to what I had to say about the inadequacies of his brainchild. As is so often the case, when a competent technician has to neglect his technical studies because of the pressure of administrative duties, he unfortunately finds it very difficult to keep abreast of new developments and progress in a field in which he was at one time an expert. The IT&T Company, having spent a great deal of money on the development of a machine that hardly presented any room at all for improvement because the principles underlying it were so faulty, dropped further work on it. Colonel Hitt, I am glad to say, readily survived the disappointment and was well enough in 1942 to be able to return to active duty during World War II and retired a second time at the end of hostilities. He lives a quiet life now, on a small farm near Front Royal, Virginia.
Beginning about 1938, Mr. Frank B. Rowlett, one of my associates, and I kept urging that there was or would be real need for new and improved machines for protecting teleprinter communications. There was a complete lack of interest in such apparatus; but what was perhaps a more important factor in the failure to continue such work in this field was the lack of Signal Corps funds for research and development for such work.
Our more or less sudden entry into World War II after 7 December 1941 immediately brought a great need for cipher printing telegraphy, especially for radio communication, but there was no apparatus for it whatever – not a single one of those AT& T Company machines of 1918–1920 was in existence. But the SIS did have drawings in readiness, and the development of the machines was given as a priority task to the Teletype Corporation, because that firm had proved that it had the necessary know-how when it produced the SIGABA-ECMs for us. The Navy had less need for cipher printing telegraphy than the Army because the use of printing telegraphy by radio was then not practicable for ships at sea. However, the Navy did have a need for such apparatus for its land communications and joined the Army in the procurement thereof. The machines were produced with a remarkable speed by the Teletype Corporation. Most of them were allotted to the Army, a few to the Navy. The Army called the machine the SIGCUM, the Navy called it CSP-1515. Under heavy use in service, improvements were made in regard to both mechanical and electrical features and to methods of keying, the use of indicators, etc. But I must tell you that before those machines became available in quantity there was only one recourse: we went back to the use of double-key-tape method using standard teletype apparatus. The cipher was practically the same as it was in 1920, but we had safer methods of key-tape production and indicators for their use. The SIS and the equivalent unit in the Navy were not happy because operators' errors left messages open to solution, so that when the new cipher machines were ready they were pressed into service as soon as possible, priority given to circuits with heavy traffic.
Cryptographic equipments of the foregoing type fall in the category of apparatus for protecting literal cryptocommunications because the latter employ letters of the alphabet; but apparatus for protecting cifax transmissions, that is, picture or facsimile transmissions, and apparatus for protecting ciphony transmissions, that is, telephonic communications, were also developed. But there isn't time to go into details with regard to machines and apparatus for these last two categories of cryptoequipment, although the history of their development is rather fascinating and very important. I cannot refrain, however, from adding that, in every case except one, the apparatus was produced by commercial research and development firms with direct guidance from the cryptologists of the Army and the Navy. The one exception is, I believe, in the case of the extremely high security ciphony system and equipment developed and built by the AT&T Company. It was called SIGSALY. There were six terminals, each of which cost over $1,000,000. But NSA cryptologists and engineers have produced smaller and better equipments based upon SIGSALY principles, and such equipments are bound to play extremely important roles in any wars in the future.
So much for the history of the developments and progress in cryptographic apparatus at this point. I shall return to that phase of cryptologic history before the close of this lecture. Right now I shall say a few words about the history of the developments and progress in cryptanalytic apparatus.
The solution of modern cryptocommunication systems has been facilitated and, in some cases, made possible only by the invention, development, and application of highly specialized cryptanalytic machinery, including apparatus for intercepting and recording certain types of transmission before cryptanalysis can even be undertaken. One must understand the basic nature of the problem that confronts the cryptanalyst when he attempts to solve one of these modern, very complex cryptosystems. First of all, he must be given the cryptocommunications in a form that makes them visible for inspection and study. Usually they are characters (letters or numbers) in the case of literal communications, or they are electrical signals of a recordable type in the case of cifax or ciphony communications. Next, he must have available to him instrumentalities that will assist him in his analytical work, such as machinery for making frequency counts, comparisons of sequences, etc., and this, in the case of complex systems, must be done at high speed. Cryptanalysis of modern cryptosystems requires testing a very great number of assumptions and hypotheses because sometimes astronomically large numbers of possibilities, Le., permutations and combinations, must be tested one after the other until the correct answer is found. Since the advent of high-speed machinery for such purposes, including electronic digital computers about which so much is being heard and read nowadays, the cryptanalyst isn't discouraged by these astronomically great numbers of possibilities.
Perhaps long before my time, cryptanalysts in Europe discovered that the use of sliding strips of paper could sometimes facilitate reaching a solution to a cryptanalytic problem, but so far as I am aware the very first cryptanalytic aid made in the United States is the one shown in figure 146, which is a picture of what I made at Riverbank and which I called the Polyalphabet. It was useful in solving ciphers which today are regarded as being of the very simplest types. When I came to Washington after leaving Riverbank, I wasn't troubled by a plethora of ideas for cryptanalytic aids – I was preoccupied with devising and inventing cryptographic aids and machines. But I did now and then develop and tryout certain ideas for cryptanalytic aids, frequency counters, comparison or coincidence machinery, and the like. Why didn't I think of IBM machines? I did, but what good did that do? Did the Signal Officer have any such machines – or even one dollar for their rental? You know the answer to that without my spelling it out. There wasn't any use in even suggesting that IBM machines could be of assistance to me – remember, now, that I'm talking about the years from 1921 to 1933, and in the last-named year we were in the depths of a great economic depression. But one day in the summer of 1934 I learned by a devious route (the Army and the Navy were not then sharing secrets) that the Navy Code and Signal Section had an IBM machine or two, and my chagrin was almost unbearable.
Not long afterwards I learned that a certain division of the Office of the Quartermaster General in the Munitions Building had an IBM installation which had been used for accounting purposes in connection with the CCC – the Civilian Conservation Corps, established to provide work and subsistence for young men who could find no jobs in the depression. I also learned that a new officer had just been assigned to head that particular division – and that he just had no use for the newfangled ideas of his predecessor and wanted to get rid of those nasty IBM machines. But the contract with IBM still had some months to run before the lease expired, and either the machines would sit idle or the government would lose money by terminating the contract before the due date of expiration. This annoyed me, but it also gave me an idea, and I wrote the following memorandum:
30 October 1934
Major Akin:
In many years service here I have never once "set my heart on" getting something I felt desirable. But in this case I have set my heart on the matter because of the tremendous load it would lift off all our backs.
The basic idea of using machinery for code compilation is mine and is of several years' standing. The details of the proposed system were developed in collaboration with Mr. Case of the Int. Bus. Machines Corp.
I regard this as one of my most valuable contributions to the promotion of the work for which we are responsible.
Please do your utmost to put this across for me. If you do, we can really begin to do worthwhile cryptanalytic work.
Attached to the memo was a brief explanation amounting to what I've told you about that IBM installation in the Office of the Quartermaster General. Note that I placed the emphasis upon the burden that would be lifted from cryptographic work by using the IBM machinery, thus leaving more time for cryptanalytic work. This was because the responsibilities of the SIS for cryptanalytic operations were at that time restricted purely to theoretical studies. Studies on cryptanalytic work on foreign cryptosystems had been a responsibility of G-2 of the General Staff until 1929, when that responsibility had been transferred to the Chief Signal Officer and the Signal Corps. But the Signal Officer had very little money to use for that purpose, and besides that, the army regulation applicable thereto specifically restricted cryptanalytic operations on foreign communications to wartime. And more to the point was that there was no material to work on even if funds had been available, because the Army had at that time no intercept stations whatever, anywhere in or outside the United States. But that's another story, and I'll proceed to the next point, which is that my memo to Major Akin produced results. Just a half month after I wrote and put it in his "in" basket, I got the machines moved from the Office of the Quartermaster General to my own warren in the Office of the Chief Signal Officer! That memo must have been potent magic.
Once having demonstrated the machines' utility to the Chief Signal Officer, the almost prematurely terminated contract with IBM was renewed – and soon expanded. I don't know how we could have managed without such machines during World War II.
We built or had built for us by IBM and other concerns adaptors to work with standard IBM machines; we constructed or had constructed for us by commercial firms highly specialized cryptanalytic apparatus, machines and complex assemblies of components. Under wartime pressures fantastic things were accomplished, and many were the thrills of gratifying achievement when things that just couldn't be done were done - and were of high importance in military, naval, and air operations against the enemy.
Even were time available, I couldn't show you pictures of some of the high-class gadgets we used; neither is it permissible to say more than I have already said about them, even though it is no longer a deep secret that electronic computers are highly useful in cryptologic work.
To the layman the exploits of professional cryptanalysts, when those exploits come to light, as, for example, in the various investigations of the attack on Pearl Harbor, are much more fascinating than those of cryptographers, whose achievements in their field appear in comparison to be dull or tedious to the layman. But long consideration of the military importance of COMSEC as against COMINT leads me to return to something I mentioned at the very beginning of this lecture, when I made a statement to the effect that cryptography and cryptanalysis represent the obverse and reverse faces of the same single coin. In closing this lecture, I will expand that statement a bit, and in doing so perhaps formulate a dictum which we may call the law governing the minting and usage of the cryptologic combat coin. It would run something like this:
When an officer is selected to command a fighting unit, an efficient appointing authority gives him and entrusts into his care a top secret, magic talisman of great potency, a coin which is called his cryptologic combat coin, and which, as is usual in the case of all but trick coins, has two faces, a COMINT face and a COMSEC face. When given to him that coin should be in mint condition; it should be bright and shiny on both faces, and he should strive his utmost to keep them both that way. If, to begin with, he is given a coin that is tarnished a bit on both faces, he is really starting out with a great handicap, no matter how good he and his forces are in respect to size, equipment, training, and ability. If he keeps both faces bright and shiny, he stands a good chance of winning a battle even if his forces are inferior in size, etc., compared with those of the enemy. But if he lets either face of his coin become dull from indifference, carelessness, or ignorance, he will almost surely lose the battle, even if his forces are superior in size, etc., compared with those of his enemy.
As a remarkable example of the validity of the foregoing dictum, an example that comes directly from the two Japanese navy officers who wrote Midway: The Battle that Doomed Japan (see footnote 11), let me quote the initial paragraphs of the Preface to their book (p.xiii):
For Japan, the Battle of Midway was indeed a tragic defeat. The Japanese Combined Fleet, placing its faith in "quality rather than quantity," had long trained and prepared to defeat a numerically superior enemy. Yet at Midway a stronger Japanese force went down to defeat before a weaker enemy.
Not only were our participating surface forces far superior in number to those of the enemy, but the initiative was in our hands. Nor were we inferior, qualitatively, in the crucial element of air strength, which played the major role throughout the Pacific War. In spite of this we suffered a decisive defeat such as the modern Japanese Navy had never before experienced or even dreamed possible.
Earlier in this lecture I quoted two other paragraphs from this same book, in which the Japanese authors make perfectly clear the reasons for the loss of the Battle of Midway, reasons which have also been stated by other writers. The cryptologic combat coin our navy entrusted to Admiral Nimitz was highly polished and bright on both sides; the one the Japanese navy entrusted to Admiral Yamamoto was dull on both sides to begin with. Admiral Yamamoto not only didn't know how tarnished it was, but lost his life because of his ignorance a couple of years later. Neither he or his superiors had the experience and knowledge that were necessary to polish up that coin. It took almost ten years for the truth of that dictum I formulated for you a moment ago to become clear to the Japanese navy. Had they taken quick and full advantage of the unfortunate leakage of the vital COMINT facts soon after the Battle for Midway, they could and perhaps would have come to the proper conclusions long before they did. Who knows what the results might have been, and the effect thereof, on the outcome of the war in the Pacific?
Hardly anything of importance in the cryptologic battles of World War II escaped the attention of Winston Churchill, who even way back in 1915, when he was First Sea Lord of the British Navy in World War I, had taken a great interest in cryptology. He made the following final comment on the Battle of Midway, a comment that is impressive in its guarded revelations and in its restraint:[41]
One other lesson stands out. The American Intelligence system succeeded in penetrating the enemy's most closely guarded secrets well in advance of events. Thus Admiral Nimitz, albeit the weaker, was twice able to concentrate all the forces he had in sufficient strength at the right time and place. When the hour struck this proved decisive. The importance of secrecy and the consequences of leakage of information are here proclaimed.
It will probably seem to many of my listeners and readers that I have paid more tributes to the achievements of our navy cryptanalysts in World War II than to those of their army and air force opposite numbers. If I have done so, I can only say in extenuation that three factors are here involved. First, as regards my apparent overlooking of the contributions of the USAF, I need but remind you that it wasn't until after the war was all over that the Army Air Corps became autonomous; before then the technical achievements of cryptanalysts of that Corps were merged with those of the army. Second, as a member of the Army's Signal Intelligence Service, and then the Army Security Agency during World War II, it is fitting that somebody other than I blow the trumpets in celebration of our army's cryptanalytic achievements. All I will say is that they were as important as those of our navy, but for various reasons they have not received much publicity, which is just as well from the point of view of national security. As a matter of fact, the publicity regarding our navy's cryptologic successes comes very largely from former enemy officers and from the various official investigations into the attack on Pearl Harbor, and not from any U.S. Navy personnel. Third, there has been very little leakage with regard to the army's cryptanalytic successes except such as can also be traced back to those Pearl Harbor investigations. General Eisenhower's Crusade in Europe has not one word to say on the subjects of signal intelligence, cryptanalysis, codes, ciphers, or signal security, etc., although he does make a few rather caustic remarks about the failures and errors of his own intelligence staff. General Bradley's book is equally reticent on these subjects, but I cannot refrain from quoting one rather amusing episode having to do with COMSEC:
To identify hills, road junctions, and towns without our giving our plans away in the event of an enemy tap on the wire, I had key features numbered on my war map and gave copies of those numbers to the division commanders. It was a makeshift private code, lax enough to cause Dickson [Bradley's G-2] to worry over the security of our plans.
One morning when I called Major General Terry Allen, he referred to an obscure crossroad by its number in this private code.
"Just a minute, Terry," I said. "I can't find that number on my map."
"Well, listen carefully, Brad," he said. "The enemy may be listening in. I'll say the name of the place as fast as I can."
Dickson overheard this conversation and threw up his hands. "Security wouldn't be much of a problem," he said, "if only there were fewer generals in the army."
General Hap Arnold's book I've mentioned before and have taken one extract from it. There are several others I might have used, but they are not too significant in revelations. One volume in the history of the U.S. Army in World War II, entitled "The Signal Corps," contains a few references to the achievements of the Signal Intelligence Service, but these, too, are not very illuminating. In only one book by a former U.S. army officer, Colonel Robert S. Allen, entitled Lucky Forward: The History of Patton's Third Army,[42] do I find a specific reference to the help SIS gave Patton. In telling about Patton's signal officer, Colonel Hammond, Allen writes:
One of his ace units was the SIS. A radiointerception agency, commanded by Major Charles Flint, a young, trigger-smart expert, it worked closely with G-2 on a dual mission: maintaining a vigilant security check on friendly communications and intercepting enemy messages. The unit performed outstandingly in both fields. Its reports plugged up an unwitting leak from a Mechanized Cavalry source, capable of revealing important troop-movement information to the enemy. And at a critical period in the Battle of Bastogne, the unit broke a German coded message that enabled heavy losses to be inflicted upon the redoubtable 5 Para Division. The SIS was particularly fruitful in breakthroughs and fluid situations when the enemy was on the run and had to use radio.
The foregoing extract is, of course, far from spectacular. Indeed, I imagine that it will hardly bring forth more than a polite yawn from many members of an audience that has already learned about the sensational revelations made during the various Pearl Harbor investigations and about those famous letters that General Marshall wrote to Governor Dewey. But there remains this much more to be said: the achievements of our army's cryptologic units both in Washington and in the field, as well as certain still undisclosed top secret successes of our navy's units ashore and afloat, are locked away in archives, where they will probably remain for a long, long time. More than this I am not at liberty to tell you in this lecture.
With this statement I bring this series to a rather undramatic but I hope meaningful close. I will wind it up by paraphrasing the last sentence of the introduction to that important book The Battle of Midway, from which I have quoted at some length. The introduction was written by Admiral Nobutake Kondo, the senior living commander of the former Imperial Navy, who participated in that battle: I close this series with the hope that my lectures will serve as material for criticism and reflection.
[21] (New York: Henry Holt and Co., 1951), 474.
[22] The 79th Congress, 2nd Session, Senate Document No. 244, (Washington: The Government Printing Office, 1946), 232.
[23] Ibid., 514.
[24] General Albert Wedemeyer, Wedemeyer Reports (New York: Henry Holt and Company, 1958), 430.
[25] A good bibliographical survey of items concerning the attack up to the year 1955 will be found in the following: Louis Morton, Pearl Harbor in Perspective, U.S. Naval Institute Proceedings, Vol. 81, No.4, Whole No. 626, April 1955, 461–8.
[26] The Memoirs of Cordell Hull (New York: The MacMillan Co.), Vol. II, 998, 1013, 1035, 1055, 1056–7, 1060, 1063, 1068, 1074, 1077, 1087, 1092, 1095, 1096, 1099–100.
[27] Henry L.Stimson and McGeorge Bundy, On Active Service in Peace and War (New York: Harper & Brothers, 1947), 391–94, 454–5.
[28] Herbert Feis, The Road to Pearl Harbor (Princeton: The Princeton University Press, 1950), vii, and 219–340, Passim. (See index: under "Magic" on 350.)
[29] Husband E. Kimmel, Admiral Kimmel's Story (Chicago: Henry Regnery Co., 1954).
[30] Sherman Miles, "Pearl Harbor in Retrospect," The Atlantic Monthly, Vol. 182, No. 1, July 1948, 65–72.
[31] Midway, The Battle that Doomed Japan: The Japanese Navy's Story, by Matsuo Fuchida and Matasake Okumiya (Annapolis: U.S. Naval Institute Publication, 1955), 131, and 232. Admiral Morrison actually wrote:
"Midway was a victory of intelligence bravely and wisely applied." See Vol. IV of his History of U.S. Navy Operations in the Pacific: Coral Sea, Midway, and Submarine Actions, May-August 1942. (New York: Little, Brown, 1944), 185. It is interesting to note that Admiral Morrison, in an article entitled "Lessons of Pearl Harbor" published in the Saturday Evening Post, October 28, 1961, concludes, "It was the setup at Washington and at Pearl, not individual stupidity, which confused what was going on. No one person knew the intelligence picture; no one person was responsible for the defense of Pearl Harbor; too many people assumed that others were taking precautions that they failed to take."
[32] Admiral Halsey's Story (New York: McGraw-Hill, 1947), 155–157.
[33] The Two Bookes of the proficience and advancement of Learning, (London, 1605), 61. This book is commonly known as The Advancement of Learning. Some 18 years later Bacon saw no reason to change his comment in his De Augmentis Scientiarum, (London, 1623). In fact, he strengthened it by making it read: "... but the rawness and unskillfulness of Secretaries, and Clarks, in the Courts of Princes, is such that many times the greatest matters are committed to futile and weak Cyphers." (Gilbert Wats' translation, 1640, 270.)
[34] Les Chiffres secrets devoiles.
[35] Comptes Rendus, Marseilles, Vol. XX, 160–65.
[36] L'art de chiffrer et de dechiffrer les depeches secretes, (Paris, 1893), 100.
[37] In this system, which uses only two different symbols or elements, the so-called "binary code," the combining rule is its own inverse.
[38] R. D. Parker, "Recollections Concerning the Birth of One-Time Tape and Printing-Telegraph Machine Cryptography," NSA Technical Journal, Vol. I, No.2, July 1956, 103–14.
[39] By L.F. Morehouse, an A.T. & T. Company equipment engineer. See u.s. Patent No. 1,356,546, "Ciphering System," granted 26 October 1920-W.F.F.
[40] The letter consisting of a single paragraph stated: "1. The mechanical means of enciphering messages with an arbitrary, meaningless running key of 999,000 letters, provided no two messages are enciphered at the same point on the tape as explained to Major Mauborgne, Signal Corps, and Captain Yardley, Military Intelligence Branch, by officials of the American Telegraph and Telephone Company, is considered by this office to be absolutely indecipherable."
[41] The Hinge of Fate, Vol. IV (Boston: Houghton Mifflin Co., 1950), 252–53.
[42] (New York: The Vanguard Press, Inc., 1957), 56. The author makes some quite caustic comments about the failure of the intelligence staffs to make use of the the intelligence they were furnished. They are worth reading.