Chapter 2. Access Virtualization: Providing Universal Access
What Is Access Virtualization?
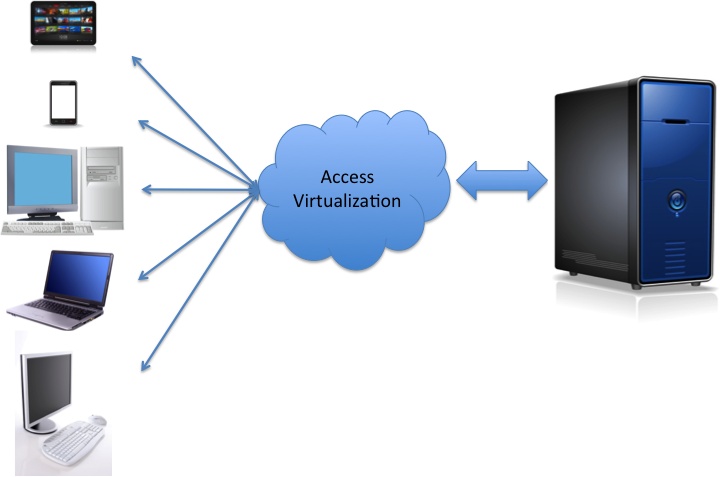
As we dive deeper into the model (see Figure 2-1), we start to understand how a virtual environment is created. Access virtualization hardware and software are designed to place access to applications and workloads in a virtual environment. The user interface, the business rules processing (the series of steps that make an application work), the data, and the storage management functions reside back in the network on a server. The server supporting this processing could be a Blade PC, a Blade Server, a virtual server, or a physical server. This technology allows “any place, any time, any device” computing.
As with other virtualization technologies, access virtualization has a long track record of success. The earliest forms of access virtualization were developed by mainframe suppliers, such as IBM, Burroughs (now part of Unisys), RCA, and others, to allow clusters of terminals to access applications running in the data center.
In 1983, the Massachusetts Institute of Technology (MIT) partnered with IBM and Digital Equipment Corporation (now part of HP) in the Athena Project. The goal was to create a campus-wide computing environment. One of the products of that collaboration was the X-Windows system. X-Windows, now available for UNIX, Linux, Windows, and many mainframe environments, is another early example of access virtualization.
Windows has been the center of intense development of access virtualization as well. Citrix, Microsoft, and the X-Windows community have been offering virtual access to Windows applications since the late 1980s.
Today, this type of virtualization is often used in conjunction with various forms of processing virtualization, which will be examined in Chapter 4. It is also an important component of desktop virtualization, virtual desktop infrastructure (VDI), and some forms of cloud computing, such as Software as a Service (SaaS). Desktop virtualization and VDI will be considered in Chapter 9.
What Does Access Virtualization Do?
As shown in Figure 2-2, access virtualization inserts itself into the flow of communications from devices such as the following:
Terminals
Desktop PCs
Laptop PCs
Netbooks
Tablets
Thin clients
Smartphones
Other network-enabled intelligent devices, such as a point-of-sale device or laboratory instrument
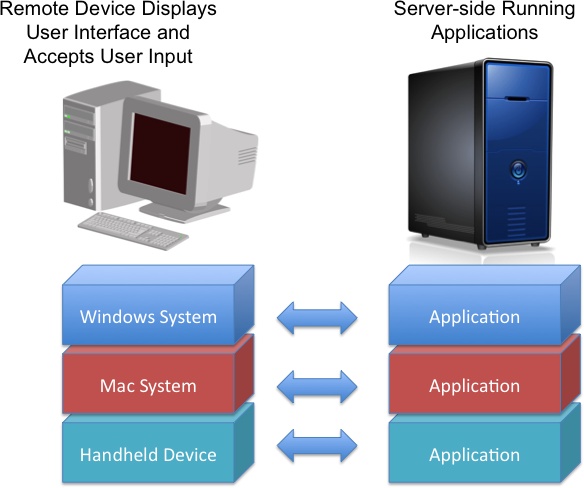
Access virtualization technology makes it possible for the remote device to display the user interface of a remote application and accept keyboard, mouse, and other input from the user.
The flow continues to applications or workloads running on the following types of devices:
Physical systems
Virtual systems (virtual desktop, virtual client, or virtual server)
This intervention allows individuals to access applications running anywhere, on any type of system, over nearly any type of network—without devices on either side of the conversation knowing too much about what’s happening on the other side. This type of technology is often used to allow devices to access applications running in virtual processing environments (see Chapter 4 for more information).
When Is Access Virtualization the Right Choice?
When organizations are attempting to achieve the following goals, access virtualization technology is the best choice:
- Greater agility
When organizations need mobile staff members to have the ability to access applications and data from wherever they are and would rather not provide them with a general-purpose system having its own storage, applications, and the like.
- Device independence
When staff members need the ability to access applications and data using many different types of devices, without the organization being forced to rewrite applications or change how or where data is stored.
- Improved availability
When staff members need the ability to access applications and data even if their access-point devices fail or are out of service for some reason. Staff members can simply access needed applications from another device using access virtualization.
- Greater security
When organizations are trying to prevent worms, viruses, and other forms of malware from entering the data center, access virtualization provides an additional level of security. The remote device may not have the ability to store data—making transmission of worms and viruses difficult or impossible. All of the actual application execution (application, database, storage, and other processing) happens remotely.
- Cost reduction
When organizations are doing their best to reduce the costs of provisioning client systems, installing client software, updating client software, and the like, access virtualization makes it possible to do all of this from a central location. It is also possible to fix problems from a central location.
- Access to cloud computing software as a service (SaaS) applications
Some SaaS offerings download a sophisticated client that runs inside of the web browser that runs inside of the remote device. This approach can also be thought of as access virtualization. (Cloud computing, such as software as a service, is not the focus of this book, however.)
Players in the Access Virtualization World
Although there are many players in the access virtualization market, a short summary of the most important suppliers follows:
- Citrix
Citrix offers virtualization technology in a number of different categories. One of the company’s earliest products was called Mainframe. It allowed a number of different types of client systems to access Windows and Solaris (UNIX) applications. Over time, the product was renamed MetaFrame, and it is now known as XenApp.
- Microsoft
Microsoft started including access virtualization capabilities in its operating systems as far back as Windows 95 and Windows NT Server. The company’s technology was not sold separately. The capability was called Microsoft Terminal Services.
- HP, IBM, Sun (now Oracle), and all other suppliers of UNIX
X-Windows has been a standard part of the UNIX operating system since shortly after the Athena Project was completed at MIT. X-Windows Servers, as the client portions of the X-Windows system are called, are available for nearly all client systems.
- Red Hat, SUSE, and all other Linux distributions
Linux has provided capabilities compatible with X-Windows since the first commercial distributions of the software were made available. X-Windows Servers that support UNIX typically will support Linux environments as well.
A Few Examples of Access Virtualization in Use
There are many different environments in which access virtualization can be beneficial. The following list contains only a few examples.
- Health care
Health care regulations, such as the Health Insurance Portability and Accountability Act of 1996 (HIPAA) in the United States, require that health care providers ensure that personal data is not disclosed accidentally. When doctors, nurses, therapists, and other health care workers access patient data, the organization must make sure that patient data is protected. This also means that this data cannot be left on access point devices, such as smartphones, PCs, laptops, or tablets. One way to be certain that these regulations are followed is to make sure that patient data never permanently resides on these devices. Access virtualization products simplify compliance by allowing organizations to keep the applications and their data back in the data center.
- Task-oriented workers
Task-oriented workers often use computers as part of their work. For the most part, they are not interested in how the computers operate. Rather than giving these staff members PCs or laptops, some organizations provide a much simpler device: a thin client, or a PC or laptop set up to run only the access virtualization client. Staff members can easily access the applications and data needed for the task at hand without becoming computer administrators or operators. This approach drastically lowers the administrative costs of system management, software installation, and software updating and it allows support to be provided from a central location.
- Non-computer-focused knowledge workers
Many knowledge workers, such as doctors, attorneys, and managers, use computers as part of their work. They often are not interested in understanding, in any detail, how their systems work. As with the task-oriented workers, organizations often find it easier to provide these staff members with access to centralized computing without putting general-purpose systems on their desks.