Chapter 8. Management for Virtual Environments
What Is Management for Virtual Environments?
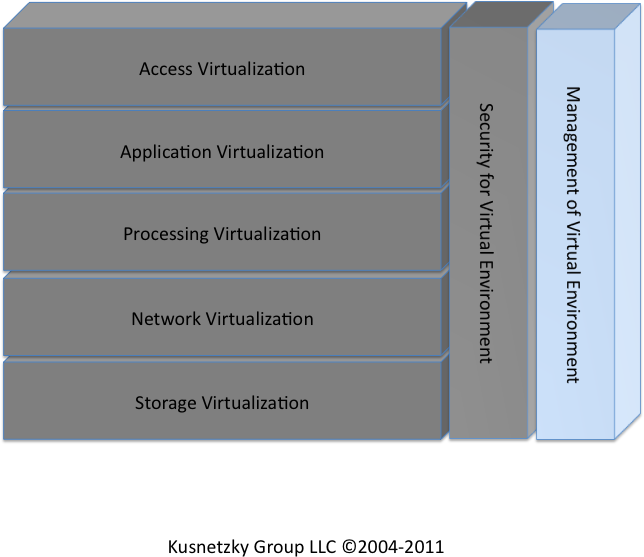
Two segments of the model cut across all of the functional segments. Security and management for virtual environments protect and manage all of the other layers. This time, we’re going to examine management for virtual environments (see Figure 8-1). Management for virtual environments refers to the tools necessary to install virtual environments and to watch, analyze, control, automate, and optimize what they are doing.
As virtual environments become more and more complex, this layer of virtualization technology becomes more and more important. We have already reached a point at which human operators cannot track what is happening in real time and respond before there is a slowdown or failure.
Technology used for management of virtual environments includes the following functions:
Creating virtual environments or components of virtual environments
Provisioning those environments or components
Monitoring their execution
Controlling execution of virtual environments or components
Analyzing execution log data to find configuration, performance, or operational issues
Optimizing use of virtual environments or components
Automating use of virtual environments or components
What Does Management for Virtual Environments Do?
Management for virtual environments guards access to each of the layers of virtualization found in an organization.
- Virtualized client resources
Creation of client-side virtual machine images and setting the proper parameters (virtual memory, number of virtual processors, virtual storage size, etc.)
Installation of operating systems, setting up the proper parameters, and installing updates
Setting user personalization (desktop images, preferred desktop icons, etc.)
Configuring user data
Installation of applications, moving necessary data, and adjusting application configuration settings
- Virtualized server resources
Creation of server-side virtual machine images and setting proper parameters (virtual memory, number of virtual processors, virtual storage size, etc.)
Installation of operating systems, setting up proper parameters, and installing updates
Installation of applications, moving necessary data, and adjusting application configuration settings
Workload management; that is, sending user requests to one of a number of systems depending upon which system has the most available capacity
Automation of virtual environment workloads; that is, staging applications so that they don’t start until the necessary data is available or dealing with an application failure
Managing policies that guide the functioning of the virtual environment; that is, telling the system the requirements of each job, when jobs can run, who is allowed to use them, where they are allowed to run, and performance requirements
Orchestration of server workloads; that is, moving tasks from system to system as required to meet service-level objectives or handle failures
It is best if management for virtualized environments is part of the architecture (that is, part of the plan, rather than added on later). As systems become increasingly complex, they require more and more attention to real-time events.
When Is Management Software for Virtual Environments Needed?
Whenever an organization embarks on the journey to a virtual environment, it is important to also deploy the technology that manages creation of virtual resources, provisions those resources, monitors the environment’s operation, automates functions to reduce the need for manual intervention, and creates an optimal environment that complies with the organization’s service-level goals and other policies.
Players in the Management for Virtual Environments World
A new player in management for virtual environments comes to my attention almost every day. Although there are many players, a short summary of some of the suppliers follows:
- CA
CA has long been a major player in management software. It is natural that, as virtual environments became more popular, CA would enhance its products to manage those environments.
- HP
HP has offered management products for its computing environments for a long time.
- IBM Tivoli
Tivoli has been a management player for many years. It, too, has brought its products into virtual environments.
A Few Examples of Management for Virtual Environments in Use
There are many different environments in which management for virtual environments can be beneficial. The following list contains only a few examples:
- Access virtualization
Management technology provisions clients, monitors usage, and ensures that access is performing properly. Failures and slowdowns are prevented when possible and failover routines are executed when failure occurs.
- Application virtualization
Access to applications and application components is provisioned, monitored, and controlled so that they are configured properly, they run optimally, and slowdowns and failures are prevented. As with access virtualization, failover routines are executed when a failure occurs.
- Processing virtualization
Access to computing resources, regardless of whether they are physical or virtual, is provisioned, monitored, and controlled so that resources are configured properly, they run optimally, and slowdowns and failures are prevented. As with access virtualization, failover routines are executed when a failure occurs.
- Storage virtualization
Storage resources are provisioned, monitored, and controlled so that they are configured properly, they run optimally, and slowdowns and failures are prevented. As with other layers of virtualization, failover routines are executed when a failure occurs.
- Network virtualization
Network resources are provisioned, monitored, and controlled so that they are configured properly, they run optimally, and slowdowns and failures are prevented. As with other layers of virtualization, failover routines are executed when a failure occurs.
- Security for virtual environments
Security services are provisioned, monitored, and controlled so that they are configured properly, they run optimally, and slowdowns and failures are prevented. As with other layers of virtualization, failover routines are executed when a failure occurs.