Chapter 5. Network Virtualization: Controlling the View of the Network
What Is Network Virtualization?
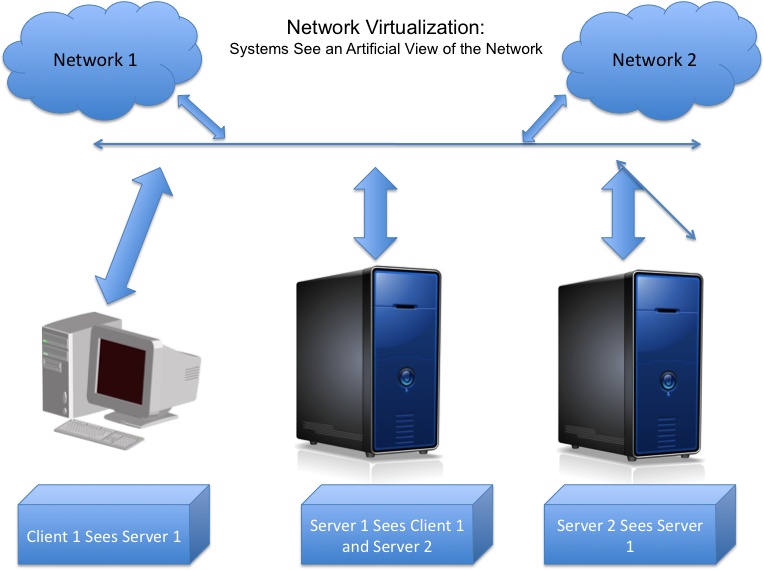
Our journey into the layers of virtualization continues. This time, we’re going to examine the concept of network virtualization (see Figure 5-1). Network virtualization refers to tools used to present an artificial view of the network environment.
Network virtualization often is supported by network routers, network servers, and the like. Systems executing the organization’s applications and workloads may not know this is happening. Client systems and server systems just see the network as presented by those network resources.
This technology, as with other virtualization technologies, was originally developed for mainframe systems in the late 1960s, was recreated on minicomputers (now called midrange machines) in the 1980s, and started appearing on industry-standard systems (X86-based) in the early 1990s. One difference is that network virtualization often was implemented on separate network servers rather than inside the operating systems supporting clients or servers.
This type of virtualization is often used in conjunction with several other types.
What Does Network Virtualization Do?
As shown in Figure 5-2, network virtualization creates an artificial view of the network that hides the physical network from clients and servers. It provides the following functions:
- Network routing
Network traffic directed to remote clients or servers is sent from network to network until it reaches the target systems.
- Network address translation
One network address may actually be used by a number of network clients or servers. A network address translation layer sends network messages from and to the right client or server systems. This means that a network service provider could provide a single Internet protocol address (IP address) for an entire facility and all of the clients and servers in that facility would still be able to send and receive messages to outside resources.
- Network isolation
Clients and servers may only be allowed to see (and thus communicate with) specific systems. This reduces the possibility of the data center becoming infected with worms, viruses, or other malware.
When Is Network Virtualization Required?
When organizations have the following goals, network virtualization technology is the best solution:
- Improving network reliability
When the organization needs constant network access in a data center, two or more physical networks supplied by different providers are typically installed. Network virtualization makes it possible for network communications to fail over from one network to the other in the case of a failure.
- Improving network performance
Increased network throughput can be achieved if several, or perhaps all, outside network communications links are used simultaneously to improve overall network performance as well as to increase network scalability.
- Improving network security
If network security is a key requirement, the data center network can be configured as several secure zones. Only specific network traffic may cross from one zone to another or from the internal network to the external network. This reduces the possibility of clients or servers being infected by worms, viruses, or other malware. It is also possible to allow clients to only see servers they are allowed to access, even though other network resources are available.
Players in the Network Virtualization World
Although there are many players in the network virtualization market, a short summary of some of these suppliers follows:
- Cisco
Cisco offers a number of network servers that perform network virtualization functions.
- HP
HP offers network virtualization functions as part of its general-purpose server operating systems and also offers network servers providing those functions.
- IBM
IBM offers network virtualization functions as part of its general-purpose server operating systems and also offers network servers providing those functions.
- Juniper Systems
Juniper offers a number of network servers that perform network virtualization functions.
A Few Examples of Network Virtualization in Use
There are many different environments in which network virtualization can be beneficial. The following list contains only a few examples:
- Increasing performance or scale of network-centric workloads
A transaction-oriented ecommerce application might overwhelm the capacity of a single network link, so an organization may install many network links from the same or different suppliers. Network virtualization would make optimal use of these resources.
- Data center security
Network virtualization can be used to isolate the internal network from all of the external networks in use. Only authorized network traffic is allowed to enter and leave the data center network.
- High availability/fail over/disaster recovery
Organizations may install network links from many different suppliers. If any link fails, the network virtualization function would reroute messages from the failed network connection to one of the surviving network connections.
- Physical and network resources devoted to department or business unit
Some regulated industries require that sensitive or personal information be maintained on separate systems and networks. Network virtualization makes it possible to segment a single network into multiple independent networks without requiring the organization to install separate wiring and networking equipment.